In this walk through, we will be going through the Pyramid of Pain room from Tryhackme. This room will teach us about the Pyramid of Pain and how to utilize this model to determine the level of difficulty it will cause for an adversary to change the indicators associated with them, and their campaign. So, let’s get started.
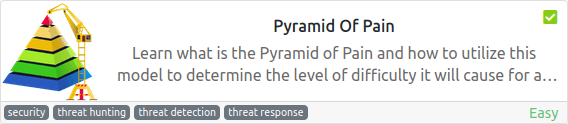
Table of Contents
Task 1 – Introduction
Task 2 – Hash Values (Trivial)
Question 1 – Analyse the report associated with the hash “b8ef959a9176aef07fdca8705254a163b50b49a17217a4ff0107487f59d4a35d” here. What is the filename of the sample?
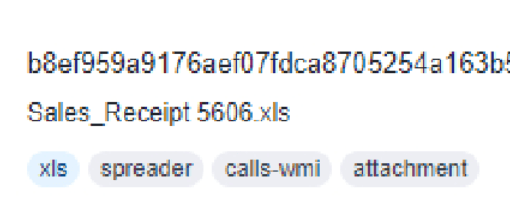
Sales_Receipt 5606.xlsTask 3 – IP Address (Easy)
Question 1 – What IP address does the malicious process (PID 1632) attempt to communicate with?
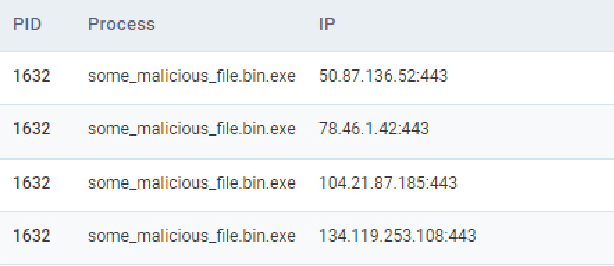
50.87.136.52Question 2 – What is the domain name this malicious process ((PID 1632) attempts to communicate with?
craftingalegacy.com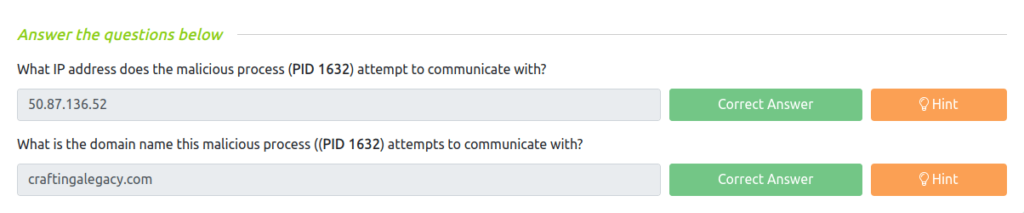
Task 4 – Domain Names (Simple)
Question 1 – Go to this report on app.any.run and provide the first malicious URL request you are seeing, you will be using this report to answer the remaining questions of this task.
craftingalegacy.comQuestion 2 – What term refers to an address used to access websites?
Domain NameQuestion 3 – What type of attack uses Unicode characters in the domain name to imitate the a known domain?
Punnycode attackQuestion 4 – Provide the redirected website for the shortened URL using a preview: https://tinyurl.com/bw7t8p4u
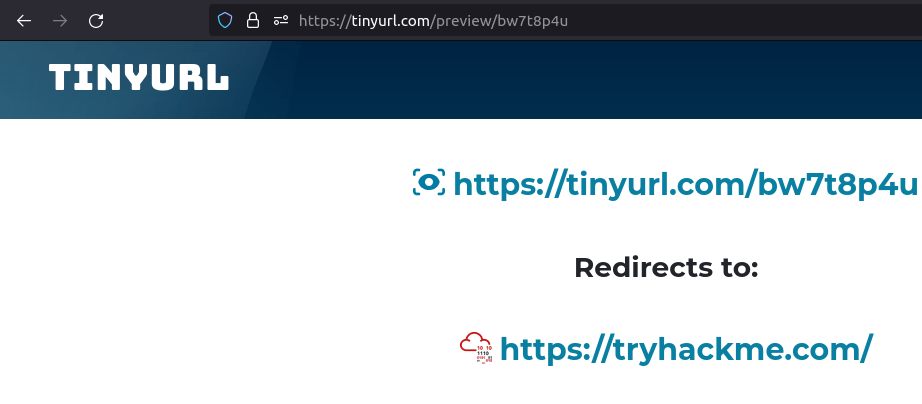
https://tryhackme.com/ 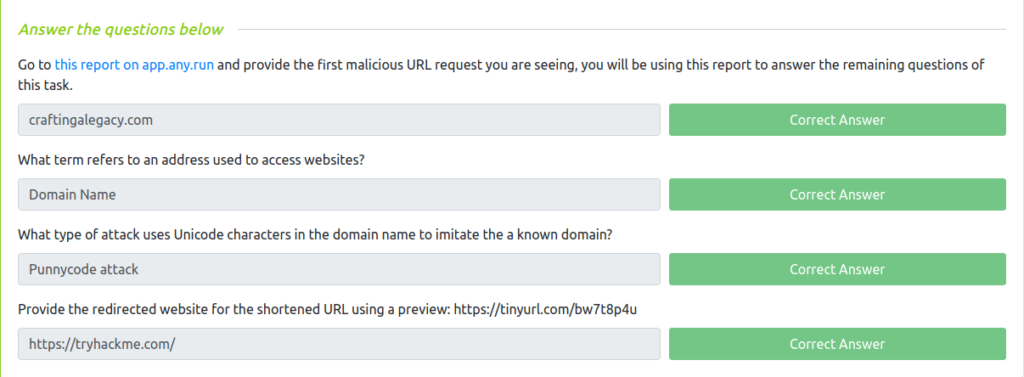
Task 5 – Host Artifacts (Annoying)
Question 1 – A security vendor has analysed the malicious sample for us. Review the report here to answer the following questions.
DoneQuestion 2 – A process named regidle.exe makes a POST request to an IP address on port 8080. What is the IP address?
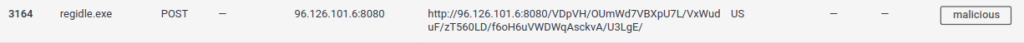
96.126.101.6Question 3 – The actor drops a malicious executable (EXE). What is the name of this executable?
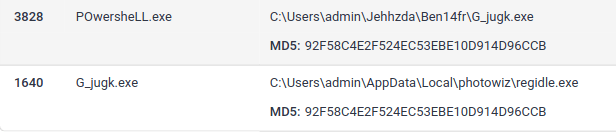
G_jugk.exeQuestion 4 – Look at this report by Virustotal. How many vendors determine this host to be malicious?
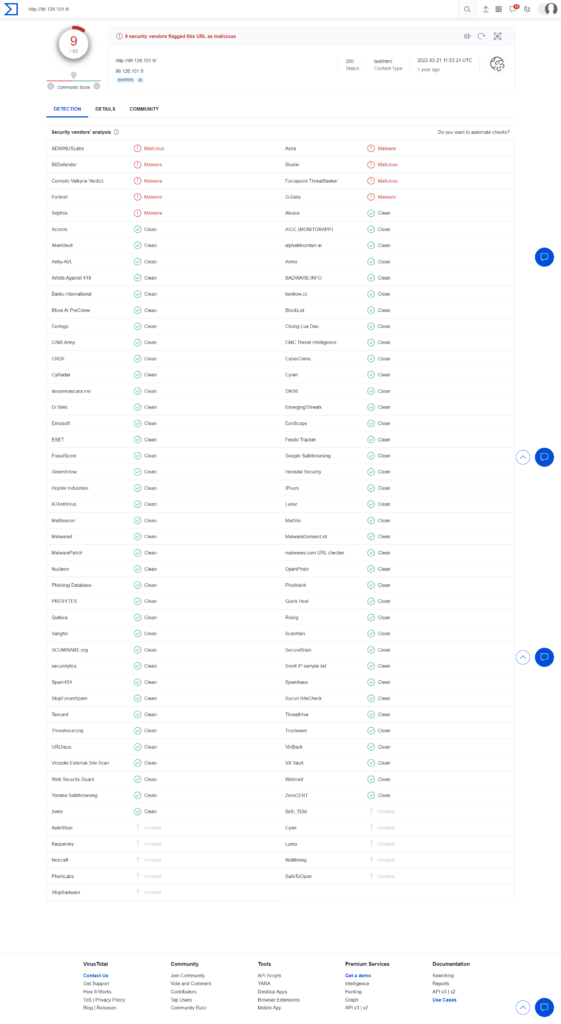
9
Task 6 – Network Artifacts (Annoying)
Question 1 – What browser uses the User-Agent string shown in the screenshot above?
Internet ExplorerQuestion 2 – How many POST requests are in the screenshot from the pcap file?
6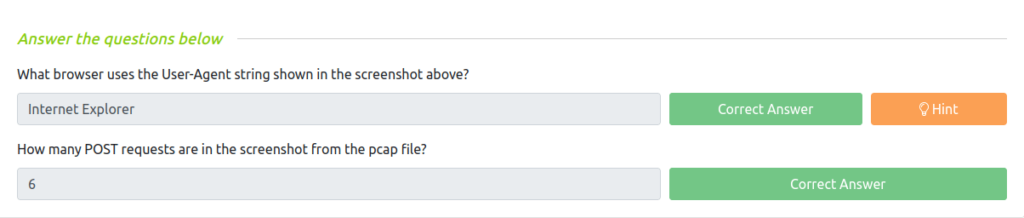
Task 7 – Tools (Challenging)
Question 1 – Provide the method used to determine similarity between the files
Fuzzy hashingQuestion 2 – Provide the alternative name for fuzzy hashes without the abbreviation
context triggered piecewise hashes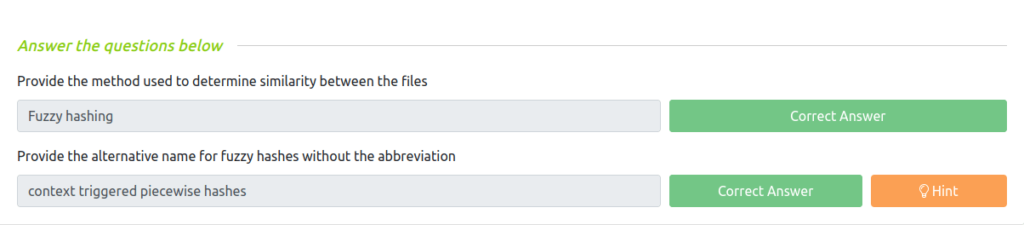
Task 8 – TTPs (Tough)
Question 1 – Navigate to ATT&CK Matrix webpage. How many techniques fall under the Exfiltration category?
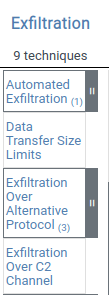
9Question 2 – Chimera is a China-based hacking group that has been active since 2018. What is the name of the commercial, remote access tool they use for C2 beacons and data exfiltration?
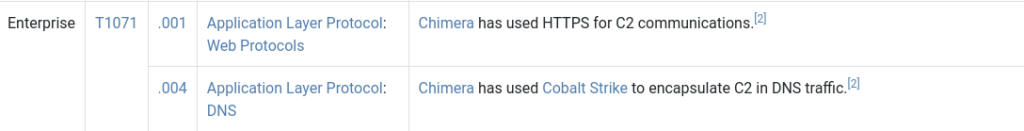
Cobalt Strike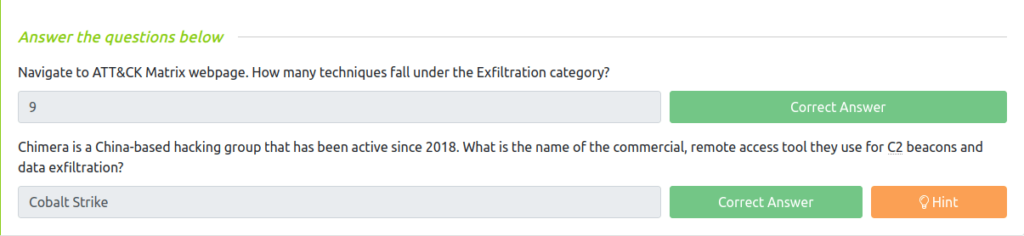
Task 9 – Practical: The Pyramid of Pain
Question 1 – Complete the static site.
Done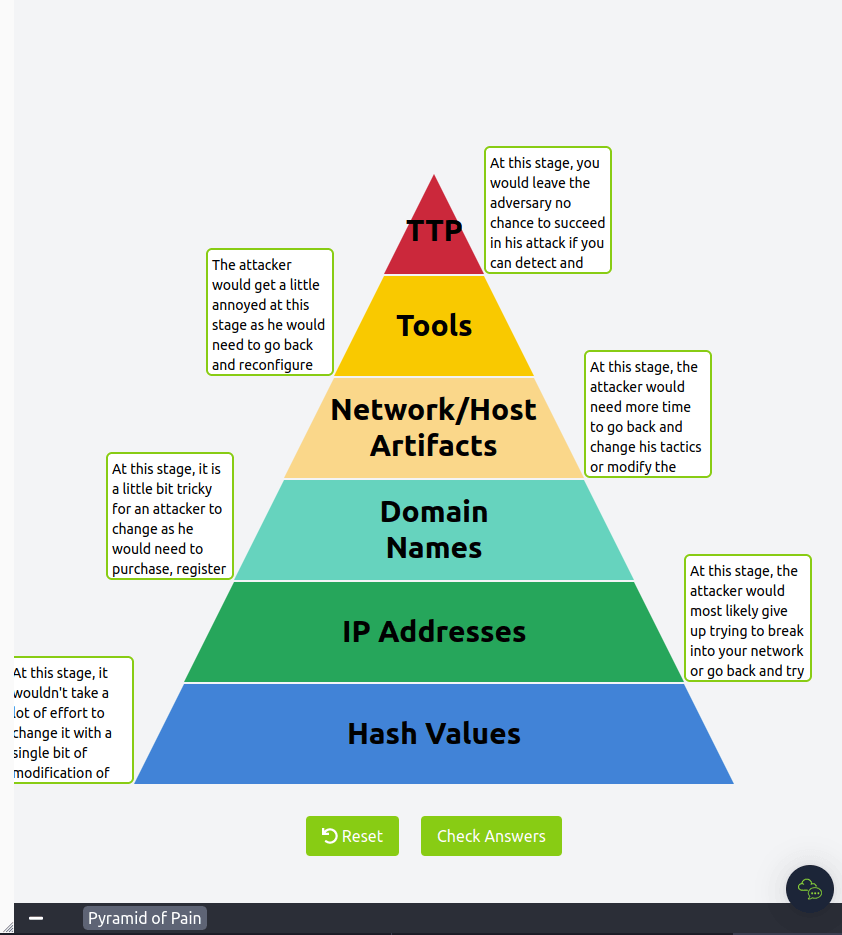
Task 10 – Conclusion
Also Read: Tryhackme – Post-Exploitation Basics
So that was “Pyramid Of Pain” for you. In this room, we have learned what is the Pyramid of Pain and how to utilize this model to determine the level of difficulty it will cause for an adversary to change the indicators associated with them, and their campaign. We have covered topics in the increasing order of difficulty from trivial, easy to annoying and tough. The challenges includes IP address, Hash Values, Domain names, Host and Network artifacts and much more to test the level of pain we can adhere. On that note, i will take your leave and meet you in the next one. So stay tuned and till then, “Hack the planet”.





TASK 9:
Complete the static site. What is the flag?