In today’s digital landscape, the quest for anonymity has become a critical aspect of hacking culture. As Hackers navigate an increasingly monitored online environment, they employ a variety of sophisticated tools and techniques to conceal their identities and evade detection.
Table of Contents
Working of Proxies and TOR:
One of the them is the use of proxies.
A proxy server is like a middleman between our computer and the internet. When we want to visit a website, instead of connecting directly to it, our request goes to the proxy server first. The proxy then sends that request to the website, retrieves the information, and sends it back to you. This process helps keep our identity private because the website only sees the proxy’s address, not ours.
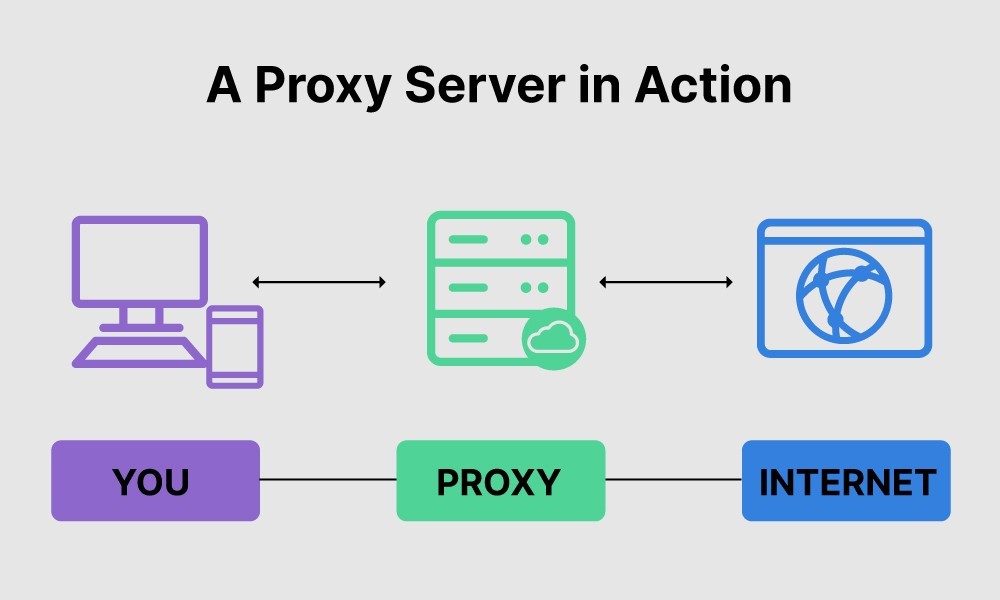
Now that we have understood what proxy is, we can use TOR as our proxy and browse the internet anonymously. Those of you who have no idea about TOR. Let me explain it to you in laymen terms.
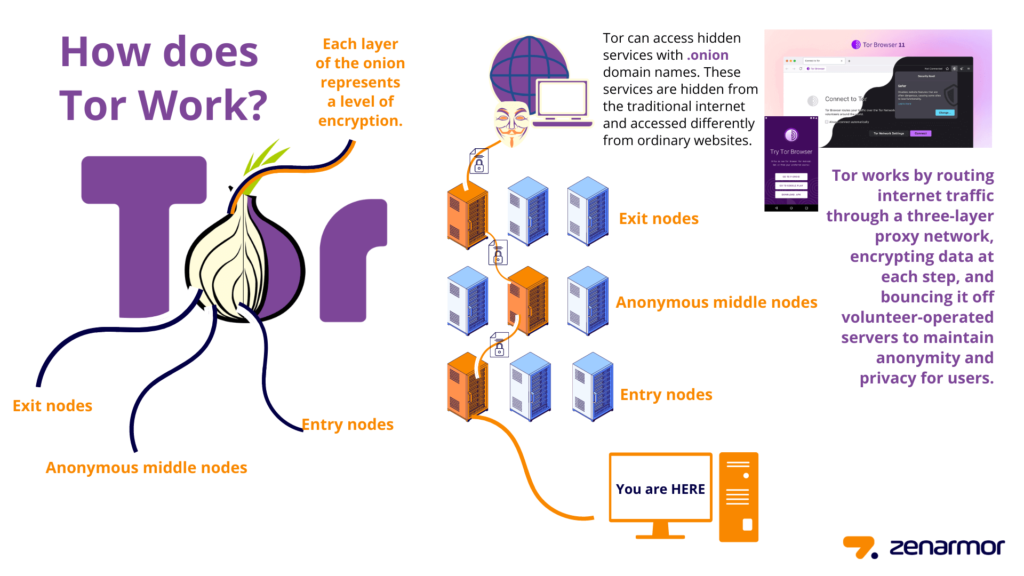
Tor, or “The Onion Router,” is a special tool that helps people browse the internet anonymously. Imagine you want to send a letter, but you don’t want anyone to know who you are or where you’re sending it from. Instead of sending it directly, you give it to a friend who sends it to another friend, and so on, until it reaches the final destination. Each friend only knows the person they got the letter from and the next person to send it to, keeping your identity hidden.
Tor works similarly by routing your internet traffic through multiple servers, called nodes. Each node removes a layer of encryption from your data, like peeling layers off an onion, which is where the name comes from. This process makes it very difficult for anyone—like internet service providers or government agencies – to track your online activities or know your real IP address. People use Tor for various reasons, including privacy protection, accessing restricted content, and communicating safely in oppressive environments.
Become Anonymous with Tornet:
Moving on, To use TOR as our proxy we will use a tool called Tornet. Lets install it on our machine.
Tornet: https://pydigger.com/pypi/tornet
- Install it using pip
sudo pip install tornet
- Start the TOR service.
systemctl enable tor service tor status
- Next we will configure our firefox browser to pass all the traffic through our TOR proxy. For that, Go to settings and make changes in network settings.
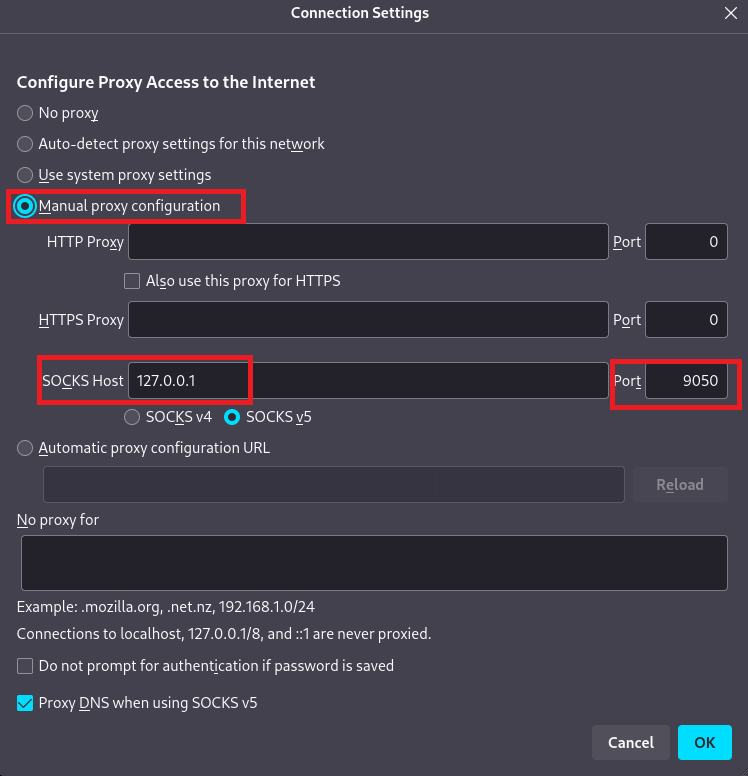
- Set Proxy to Manual proxy. Put “127.0.0.1” on Host section and in port put “9050” as it the default port in which TOR service is running. Now we are ready to go!
- Launch the Tornet tool. We will change the IP address every second so in interval we will use 1, you can use whatever you like and for the count we will use 0 that means the tool will run infinitely giving us a new IP address every second.
sudo tornet --interval 1 --count 0
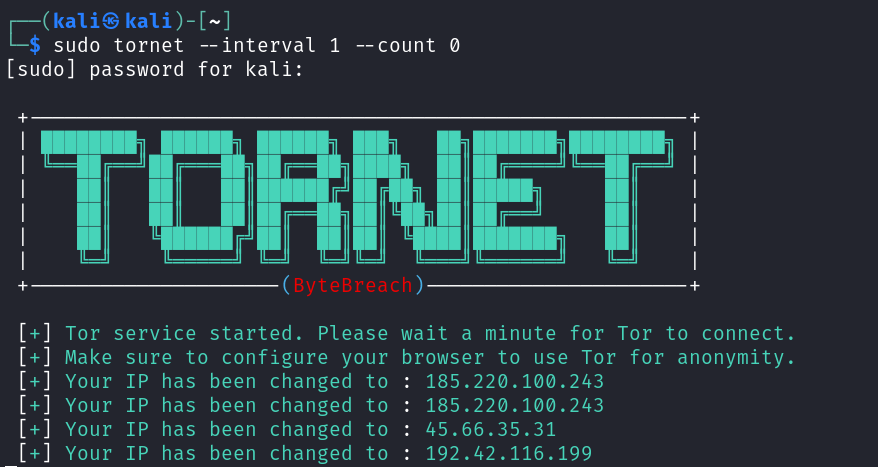
- Now lets check if our IP address has been changed.
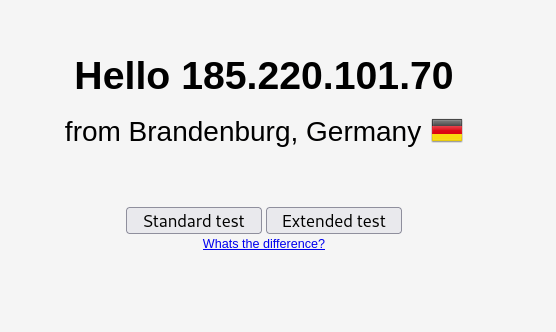
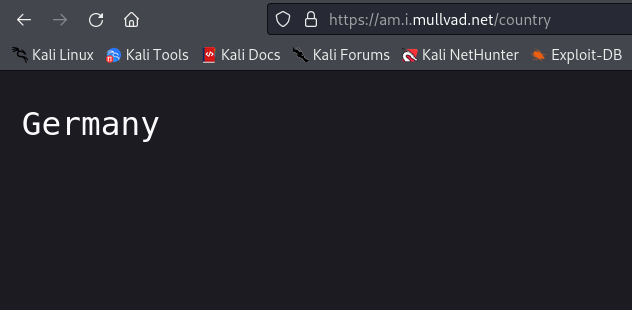
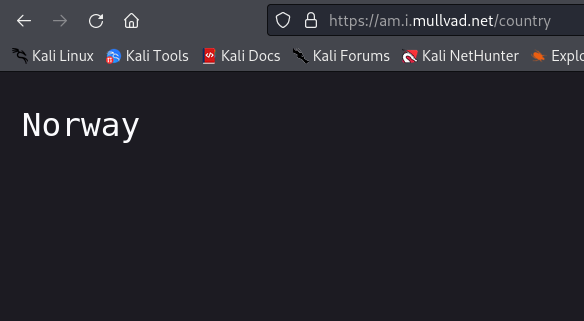
- Great! As per the above screenshots we are able to change our IP address every second, thus making it anonymous and practically impossible to trace.
Also Read: Hacking Windows with Fake Captchas
Conclusion:

In conclusion, the use of tools like Tor and Tornet illustrates the lengths to which hackers and other individuals go to maintain their anonymity while navigating the digital landscape. By employing sophisticated methods such as onion routing and decentralized networks, these tools create layers of encryption that obscure users’ identities and activities from prying eyes. On that note, i will take your leave and will meet you in next one.



Pingback: How to hack Android Phone using Kali Linux
Pingback: How to hack Android Phone using Kali Linux – Hack Warden Blogs
Pingback: How to hack Android Phone using Kali Linux