In this walk through, we will be going through the Insecure Login vulnerability section from Webgoat Labs. We will be exploring and exploiting Insecure Login panels and learn how application are affected because of it. So, let’s get started with the Hacking without any delay.

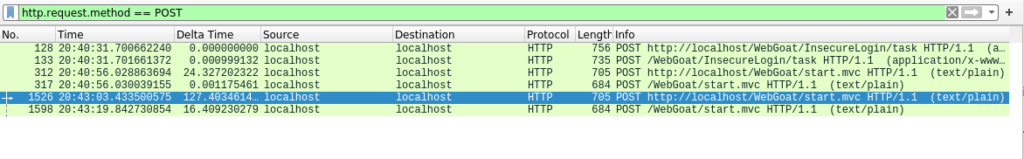
- I started wireshark on my loopback address and used the filter to filter out the HTTP POST request. Following up the HTTP steam of the second last packet gives me my required credentials which were flowing through the wire in plain text.
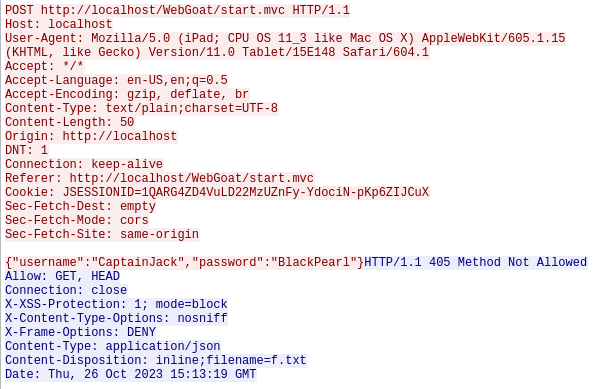
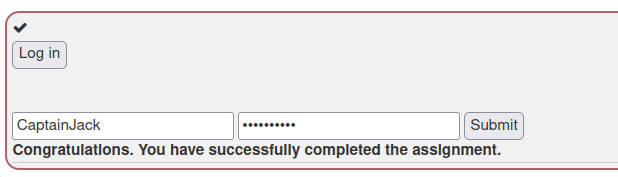
Username: CaptainJack Password: BlackPearl
Also Read: Webgoat – Insecure Deserialization
Conclusion:

So, we finally completed the Webgoat Insecure Login Vulnerability section. Next, we can mitigate these types of attacks by avoiding use of HTTP completely and upgrading to HTTPS or SSL/TLS versions. On that note, i will take your leave and will meet you in next one with another Webgoat vulnerability writeup, till then “Keep Hacking”.




