In this walk through, we will be going through the Red Team Recon room from Tryhackme. This room will teach us how to use DNS, advanced searching, Recon-ng, and Maltego to collect information about your target. On that note, let’s get started.
Table of Contents
Task 1 – Introduction
Task 2 – Taxonomy of Reconnaissance
Task 3 – Built-in Tools
Question 1 – When was thmredteam.com created (registered)? (YYYY-MM-DD)
whois thmredteam.com
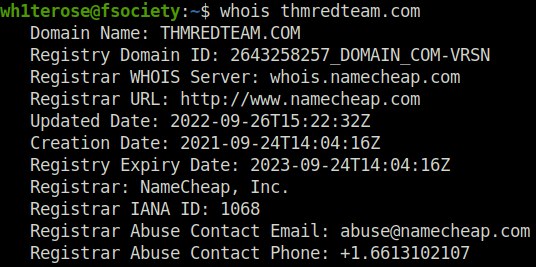
2021-09-24Question 2 – To how many IPv4 addresses does clinic.thmredteam.com resolve?
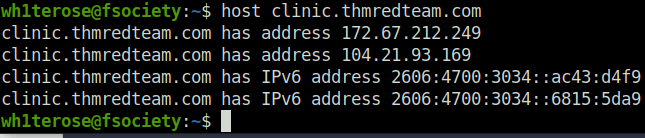
2Question 3 – To how many IPv6 addresses does clinic.thmredteam.com resolve?
2
Task 4 – Advanced Searching
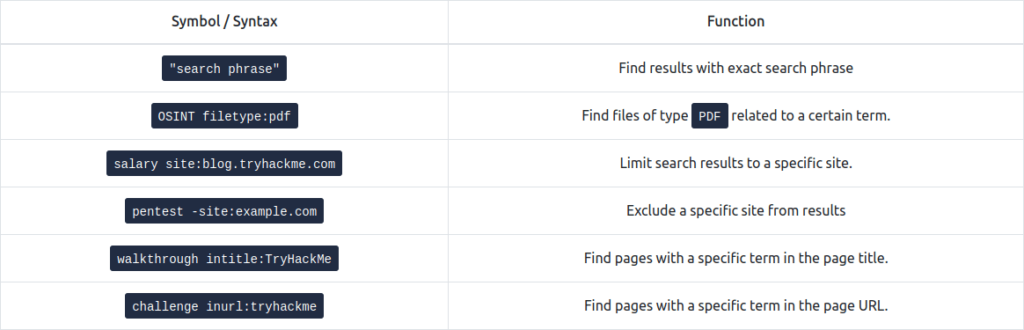
Question 1 – How would you search using Google for xls indexed for http://clinic.thmredteam.com?
filetypeLxls site:clinic.thmredteam.comQuestion 2 – How would you search using Google for files with the word passwords for http://clinic.thmredteam.com?
passwords site:clinic.thmredteam.com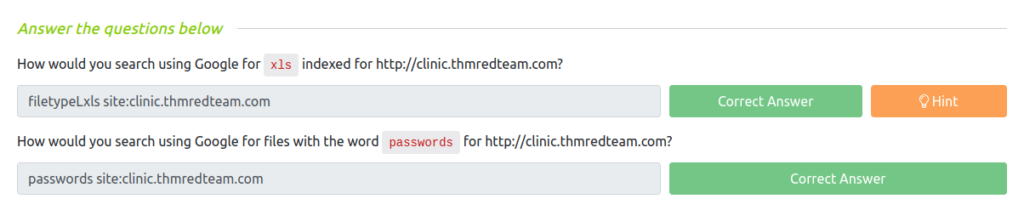
Task 5 – Specialized Search Engines
Question 1 – What is the shodan command to get your Internet-facing IP address?
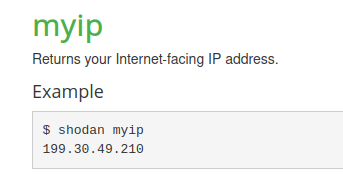
shodan myip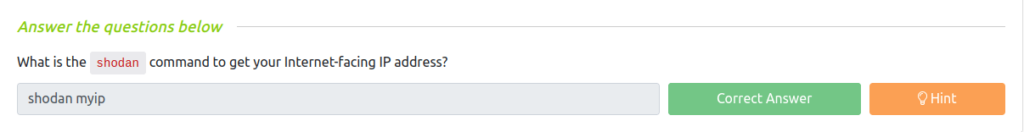
Task 6 – Recon-ng
Question 1 – How do you start recon-ng with the workspace clinicredteam?
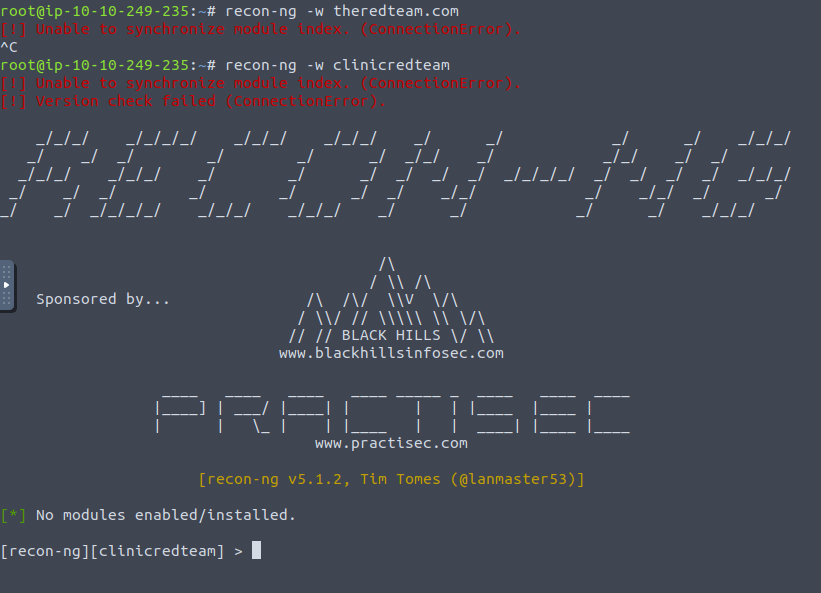
recon-ng -w clinicredteamQuestion 2 – How many modules with the name virustotal exist?
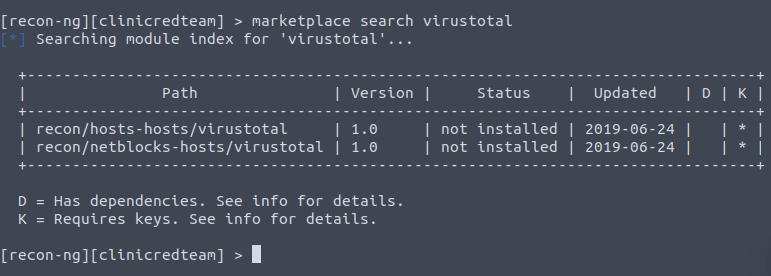
2Question 3 – There is a single module under hosts-domains. What is its name?
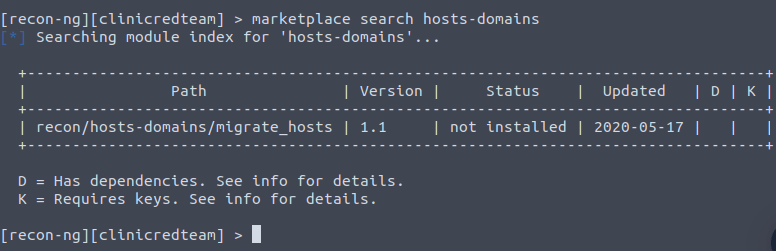
migrate_hostsQuestion 4 – censys_email_address is a module that “retrieves email addresses from the TLS certificates for a company.” Who is the author?
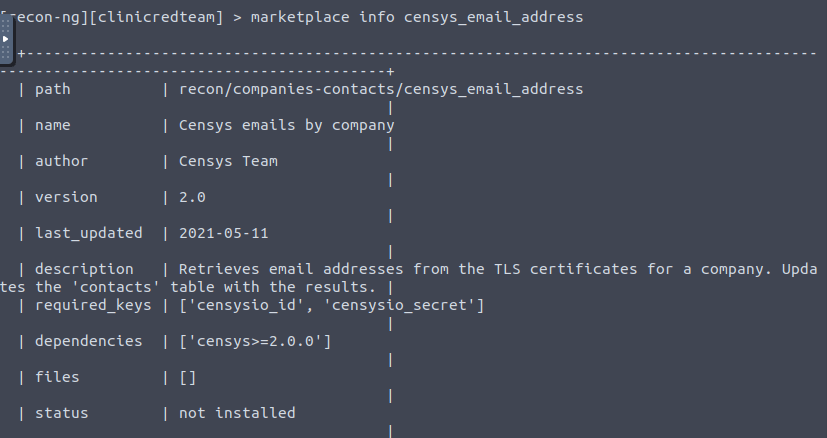
Censys Team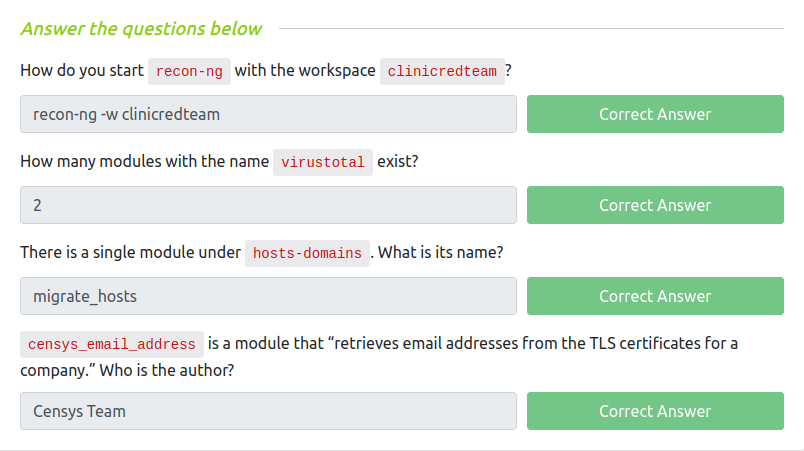
Task 7 – Maltego
Question 1 – What is the name of the transform that queries NIST’s National Vulnerability Database?
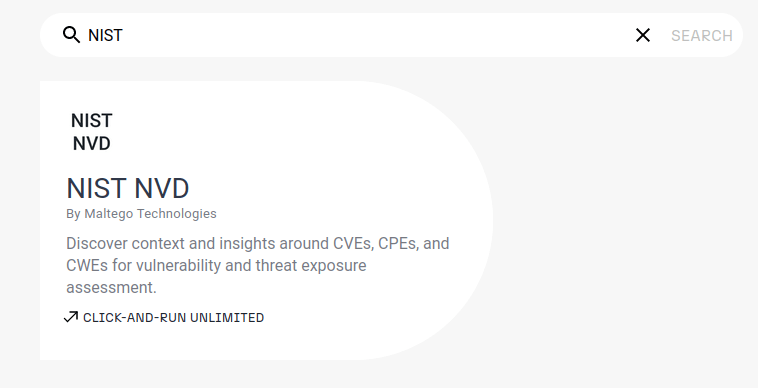
NIST NVDQuestion 2 – What is the name of the project that offers a transform based on ATT&CK?
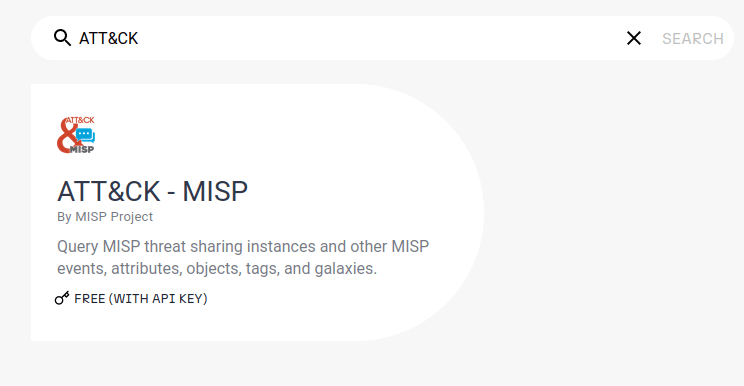
MISP Project 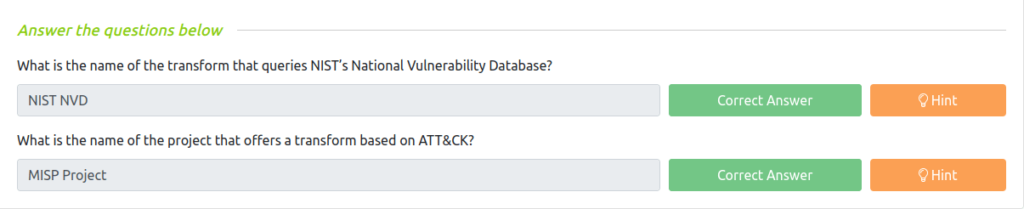
Task 8 – Summary
Also Read: Tryhackme – Red Team Engagements
So that was “Red Team Recon” for you. In this room, we have learned how to use DNS, advanced searching, Recon-ng, and Maltego to collect information about your target. We have covered the taxonomy of reconnaissance, some built in tools like whois, nslookup and traceroute. Further, we got into some Google Dorking and Shodan Searching. At last, we peeked into some of the famous Red Team Recon framework like Recon-ng and Maltego. On that note, i will take your leave and meet you in next one. So stay tuned and till then, “Hack the planet”.




