In this walk through, we will be going through the Diamond Model room from Tryhackme. This room introduces you to the Diamond Model of Intrusion Analysis and how does it work in the real world to map out the relationship between the adversary, victim, infrastructure used and the capabilities of the attacker. So, let’s get started to understand it further.
Task 1 – Introduction
Task 2 – Adversary
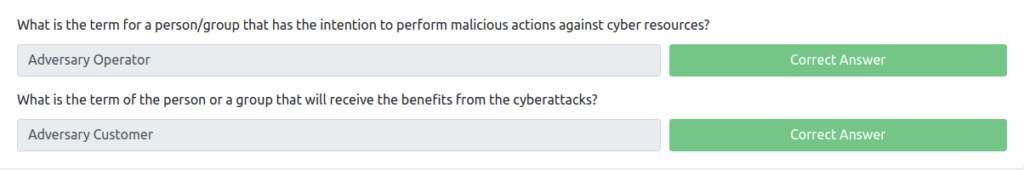
Question 1 – What is the term for a person/group that has the intention to perform malicious actions against cyber resources?
Adversary Operator
Question 2 – What is the term of the person or a group that will receive the benefits from the cyberattacks?
Adversary Customer
Task 3 – Victim
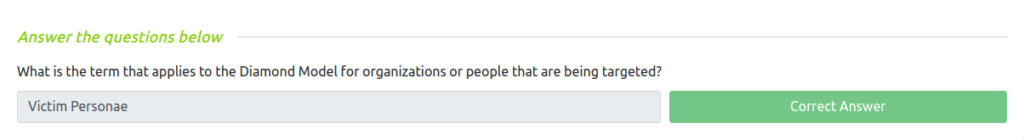
Question 1 – What is the term that applies to the Diamond Model for organizations or people that are being targeted?
Victim Personae
Task 4 – Capability
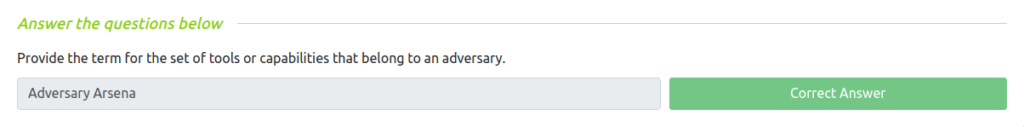
Question 1 – Provide the term for the set of tools or capabilities that belong to an adversary.
Adversary Arsenal
Task 5 – Infrastructure
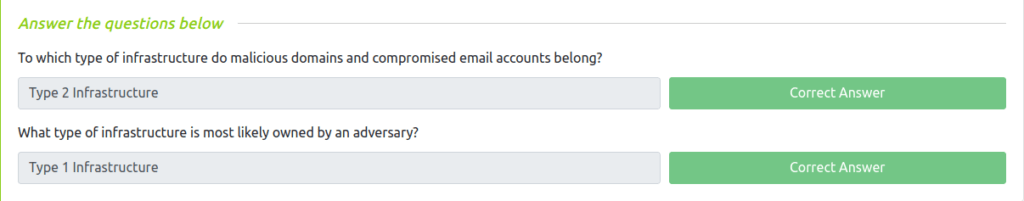
Question 1 – To which type of infrastructure do malicious domains and compromised email accounts belong?
Type 2 Infrastructure
Question 2 – What type of infrastructure is most likely owned by an adversary?
Type 1 Infrastructure
Task 6 – Event Meta Features
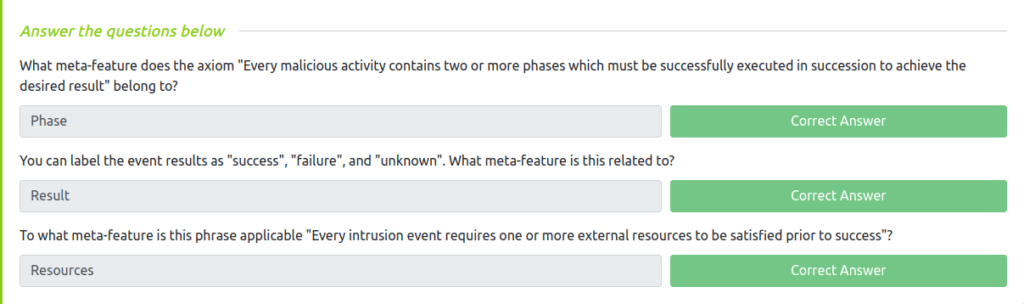
Question 1 – What meta-feature does the axiom “Every malicious activity contains two or more phases which must be successfully executed in succession to achieve the desired result” belong to?
Phase
Question 2 – You can label the event results as “success”, “failure”, and “unknown”. What meta-feature is this related to?
Result
Question 3 – To what meta-feature is this phrase applicable “Every intrusion event requires one or more external resources to be satisfied prior to success”?
Resources
Task 7 – Social-Political Component
Task 8 – Technology Component
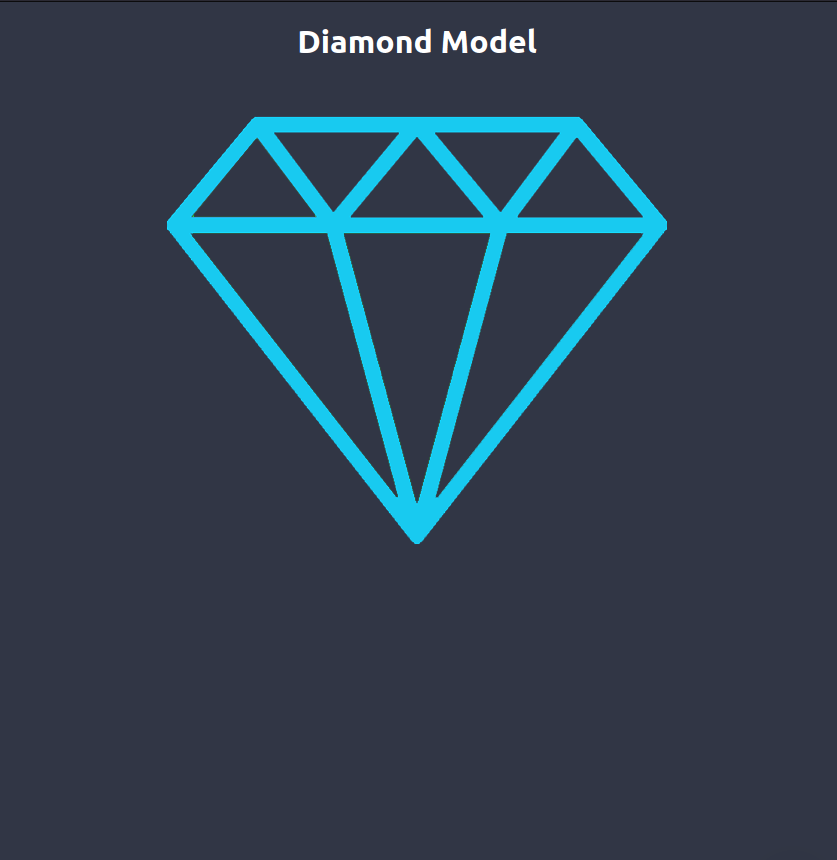
Task 9 – Practice Analysis
Question 1 – Complete all eight areas of the diamond. What is the flag that is displayed to you?
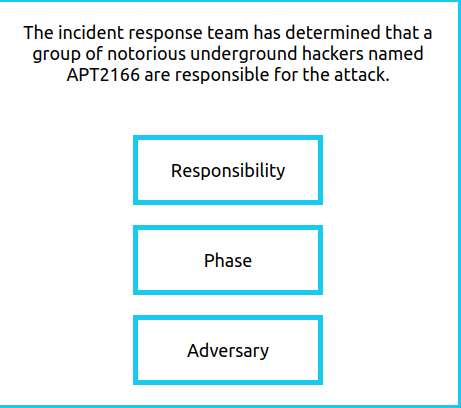
- Adversary
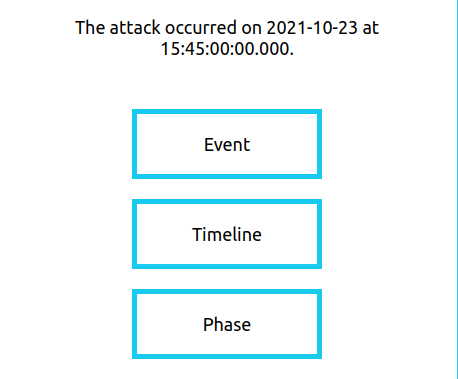
- Timeline
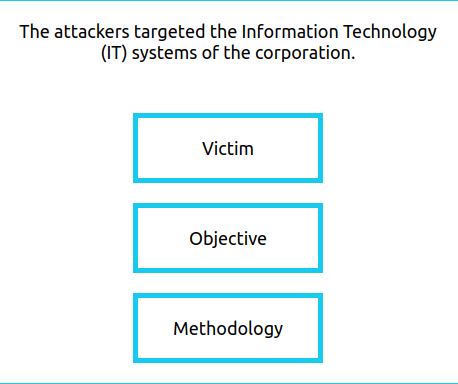
- Victim
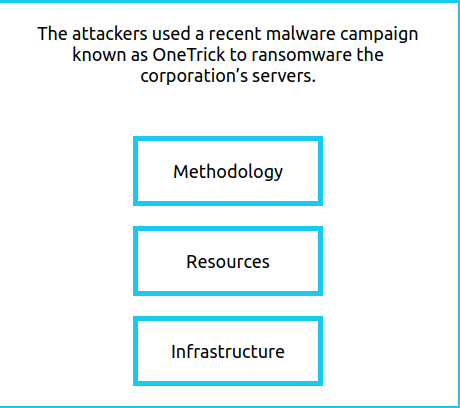
- Resources
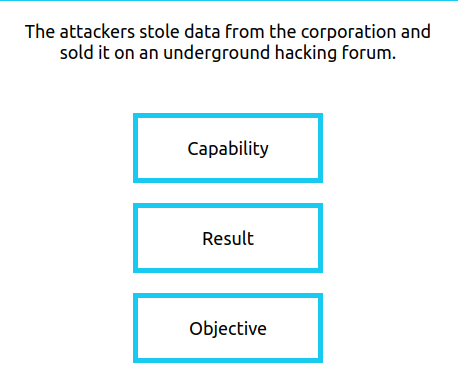
- Result
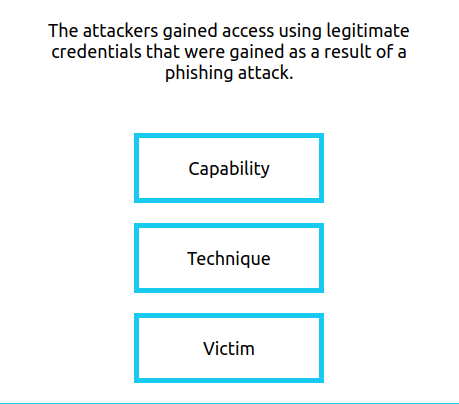
- Capability
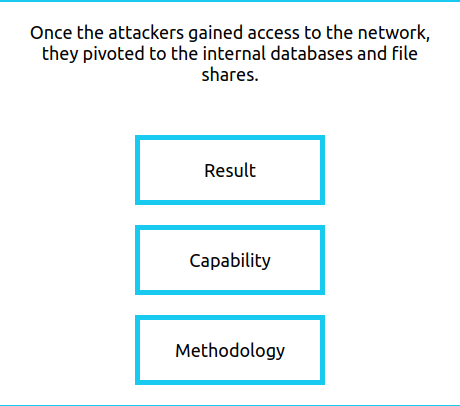
- Methodology
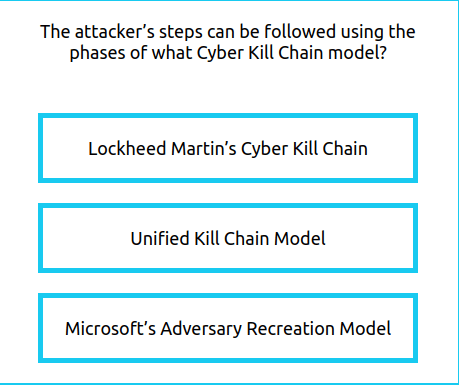
- Lockheed Martin’s Cyber Kill Chain
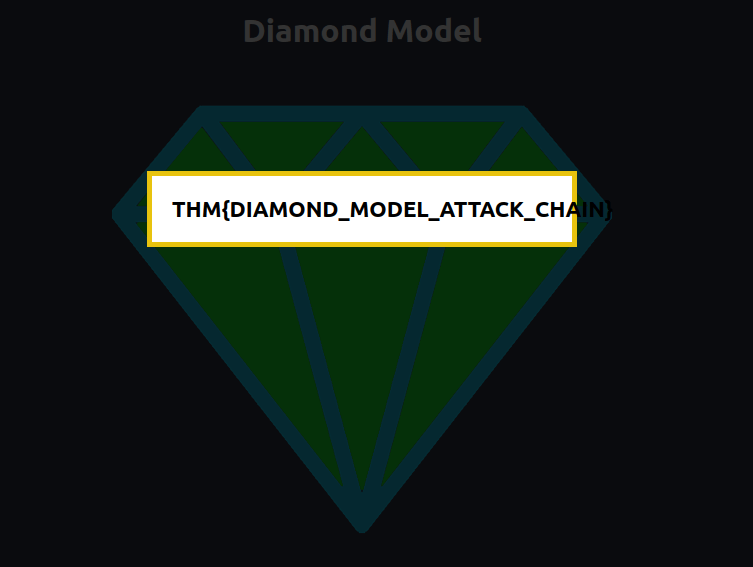
THM{DIAMOND_MODEL_ATTACK_CHAIN}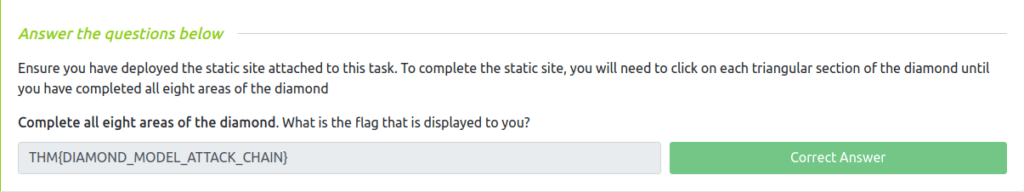
Task 10 – Conclusion
Also Read: Tryhackme – Cyborg
So this was the room on “Diamond Model” of Intrusion Analysis. We covers what it is and its different elements. Along with that, we also covers other event meta-features of the model. Further, we tested the theory we learned by solving a series of exercise questions. In short, we can define that the diamond model is one of the famous model of intrusion analysis which shows relationship between the adversary and the victim. Learn more about it on your own to get more familiar with it, for now i am taking your leave, but remember to “Keep Defending” the systems in my absence.




