In this walk through, we will be going through the Broken Authentication (Insecure Login Forms) vulnerability section from bWAPP Labs. We will be exploring and exploiting Insecure Login Forms and learn how application are affected because of it. So, let’s get started with the Hacking without any delay.
Table of Contents
Security: Low
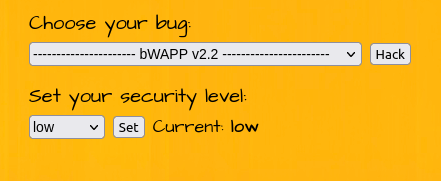
- Setting the security level to Low.
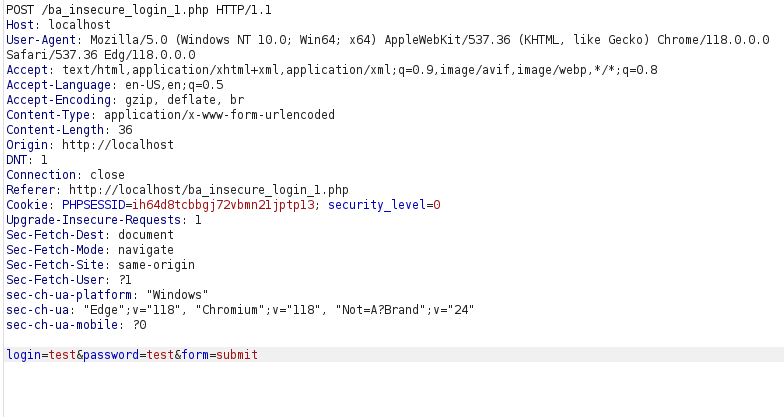
- The application has a login functionality and asks for the user’s credentials. It issues a POST request to ba_insecre_login_1.php for the login.

- I checked the page source code and found the user’s credentials hard coded in the page source. Used the same and got in.
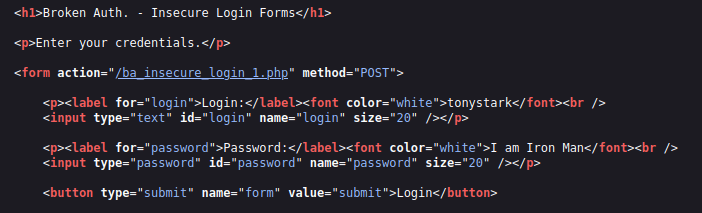
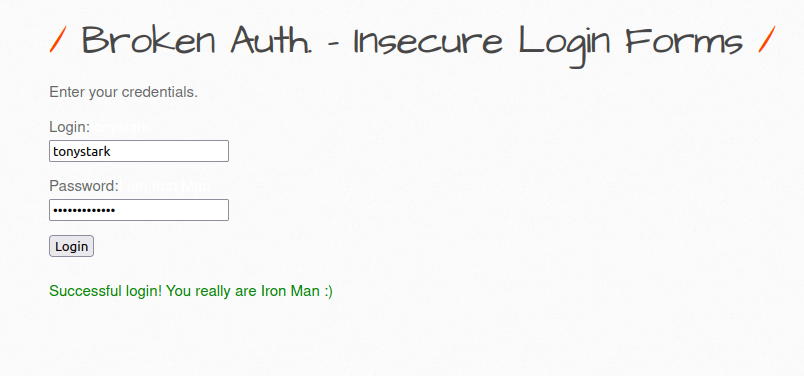
tonystark I am Iron Man
Security: Medium
- Setting the security level to Medium.
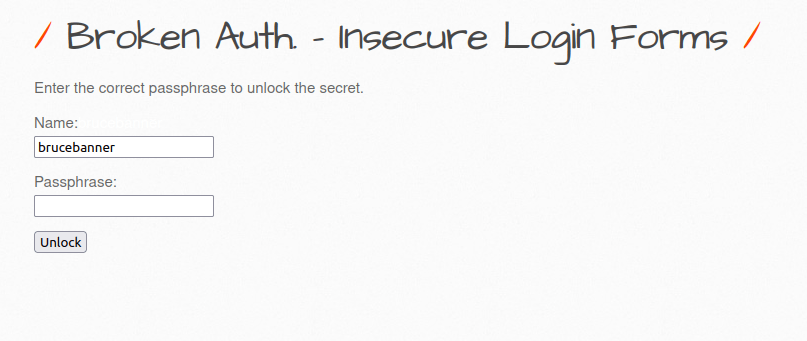
- The application has a login functionality where username is already populated and hard coded. It needed a correct passphrase to unlock the secret. It uses a POST request to ba_insecure_login_2.php for further execution.
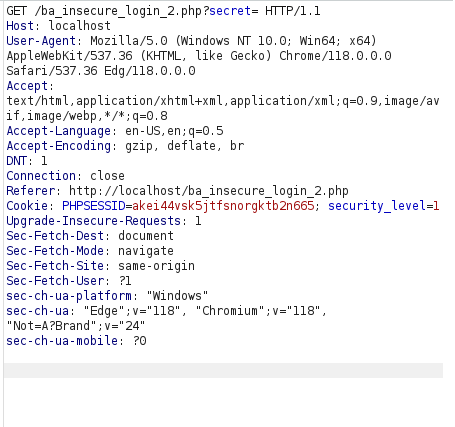
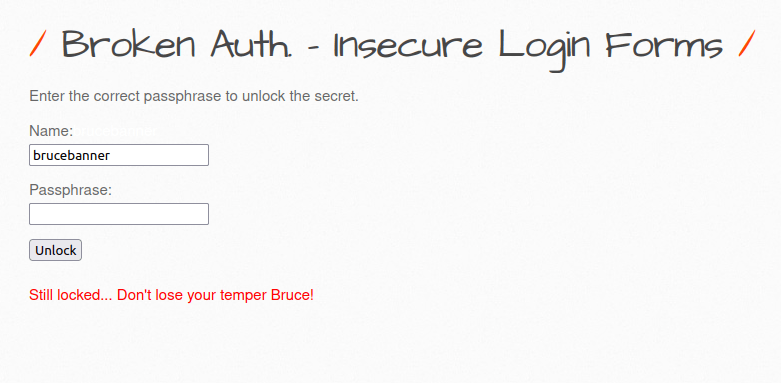
- Entering a test or wrong password gives me the below error.
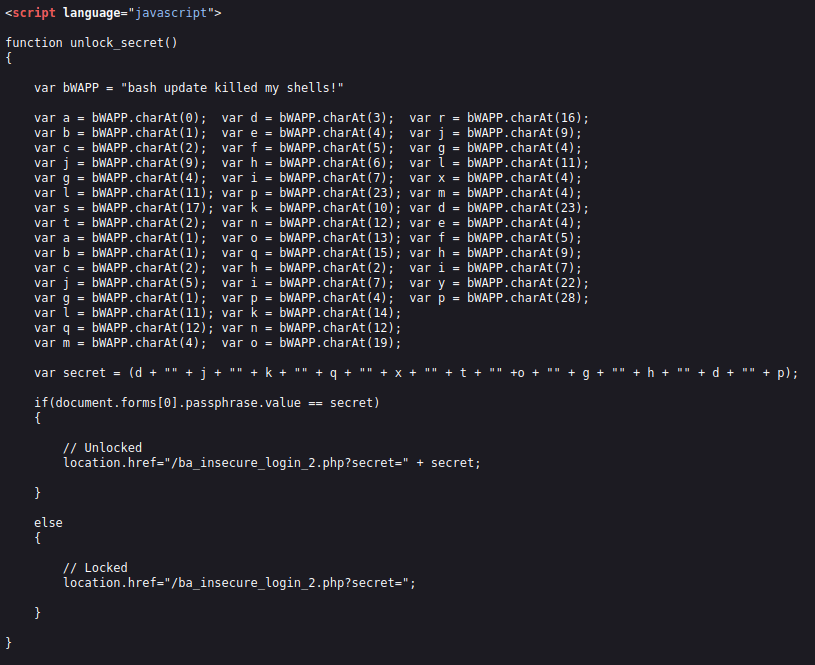
- I checked the source code and found out that in order to login the phrasevalue should be equal to secret. The secret is being derived from the unlock_secret function which uses charAt function inside it. CharAt function gives the character value of the input number. sample variables are written in the function definition already and a var secret has already been introduced which is being deduced by the function unlock_secret.
- In short, it works like – the first character is “d” which is equilvalent to 23 as per the defined character sets. This goes on and on until we find our secret.
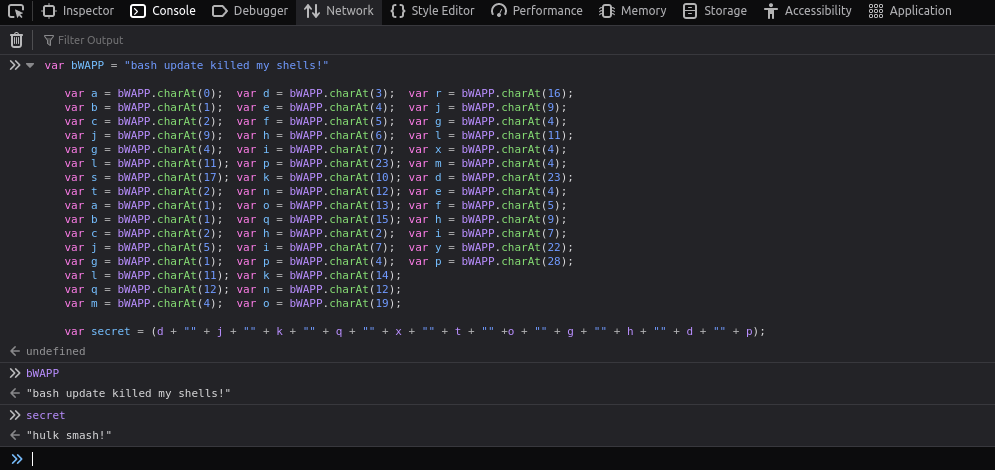
- I used the developer tools console to execute the function and deduce the value of secret from it, which was – Hulk Smash!
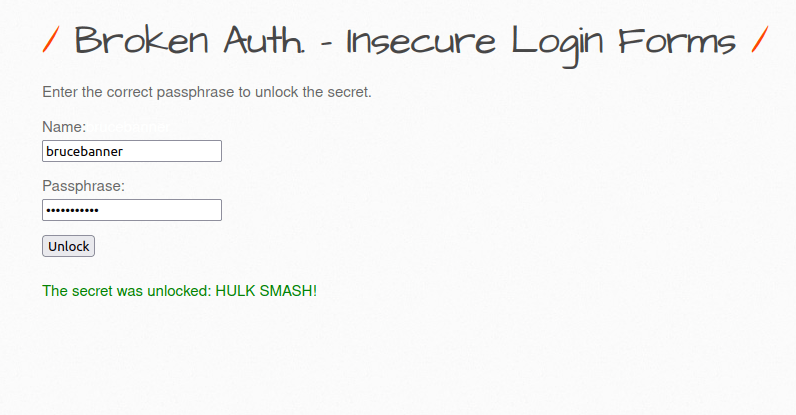
- Logged in successfully with the found secret.
Security: High
- Setting the security level to High.
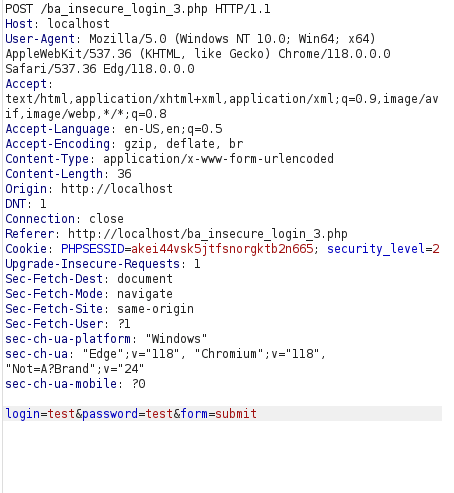
- The application requires a valid set of credentials and for that it issues a request via POST request to ba_insecure_login_3.php file.
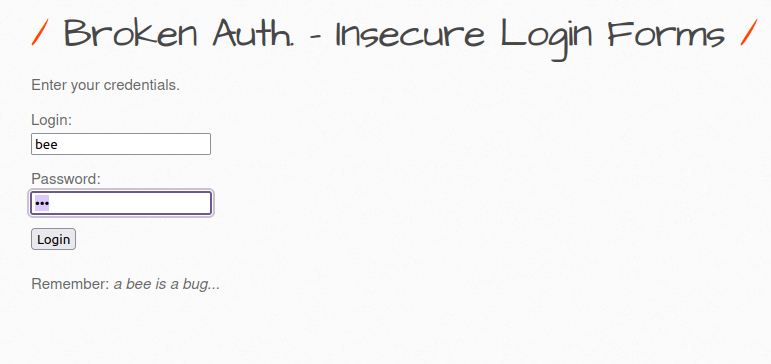
- I tried the credentials with in the password hint on the page which was “a bee is a bug”. So, i used – bee:bug and got in successfully.
Also Read: bWAPP – Base64 Encoding (Secret)
Conclusion:

So, we finally completed all the security levels for the bWAPP Broken Authentication (Insecure Login Forms) Vulnerability. We looked into the various ways how application has been set up in various levels and how we can bypass the security controls implemented. Next, we can mitigate the attacks on login forms by not relying on client-side security controls as they can be bypassed pretty easily. Along with that, the user’s password should be securely stored in a DB and no password hints should be allowed. On that note, i will take your leave and will meet you in next one with another bWAPP vulnerability writeup, till then “Keep Hacking”.




