In this walk through, we will be going through the Weak Session IDs vulnerability section from DVWA Labs. We will be exploring and learn about Weak Session IDs attacks and what makes an application vulnerable to it. We will start with the security level as Low and will gradually increase the difficulty as we progress further. So, let’s get started with the Hacking without any delay.

Table of Contents
Weak Session IDs Attacks:
Weak Session ID Attack is an attack where an attacker predicts the session ID value or session generation schema which results in authentication bypass and account takeovers. For that, the attacker needs to collect some valid session ID values that are used to identify authenticated users. Then, they must understand the structure of session ID, the information that is used to create it, and the encryption or hash algorithm used by application to protect it. If the session ID values are repeated and predictable, attacker can guess the user’s next session value and get access on their behalf.
Security: Low (Weak Session IDs)
- Setting the security to low and PHPIDS as enabled.
- The application has a “Generate” button which set a new cookie named dvwaSession each time the button is clicked.
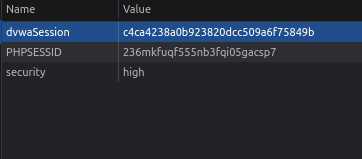
- We have to analyze if the cookie is weak so that it can be used for further exploitation. I clicked on the “Generate” button and opened up the developer tools -> Storage -> Cookie.
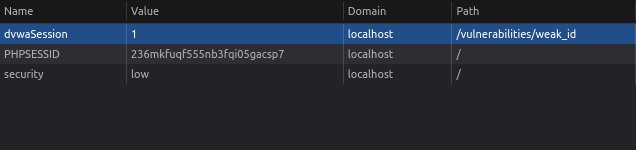
- Here we can see that the application has the set the dvwaSession cookie and its value as 1. I clicked on the “Generate” button again and it incremented to 2 and so on.
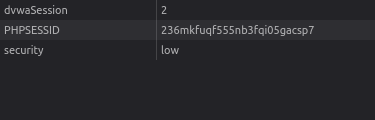
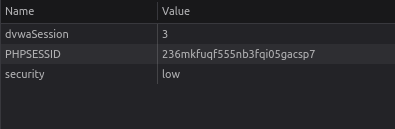
- This is very poor practice of handing session cookies as the next and the previous cookie values can be easily predicted by the attacker. Let’s analyze the source code for better understanding.
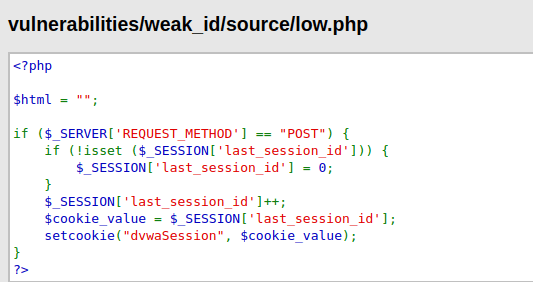
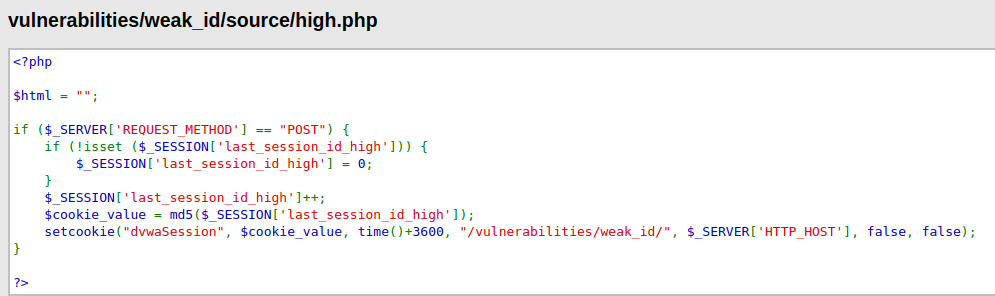
- As per the source code, the cookie value is incremented based on the last known session ID and very easy to guess the next one.
Security: Medium (Weak Session IDs)
- Setting the security to Medium with PHPIDS enabled.
- We have the same “Generate” button to set a new cookie called dvwaSession each time the button is clicked.
- I clicked on the “Generate” button and opened by Dev tools to analyze the cookie value. This time we have a 10 digit number in place of our Cookie value.
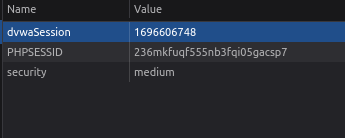
- I clicked on the “Generate” button and generate the below values for later analysis. As we can see the numbers in the front upto 6 digit are constant and the last 4 digits are changes. Seems like an incremental change.
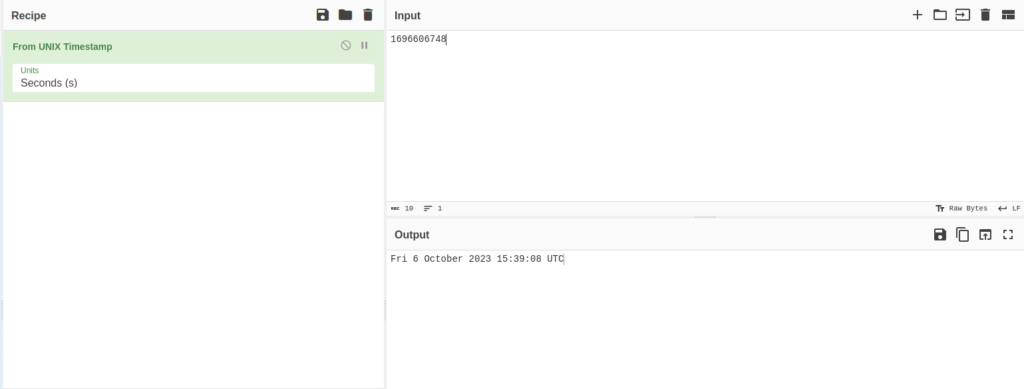
1696606748 1696606823 1696606834 1696607050
- I had a doubt that these numbers are the Unix UTC time. So, i decided to give it a try. I pasted the above values in Cyberchef and to my surprise, my guess was right. These numbers were date and timestamp which eventually decides the cookie value.
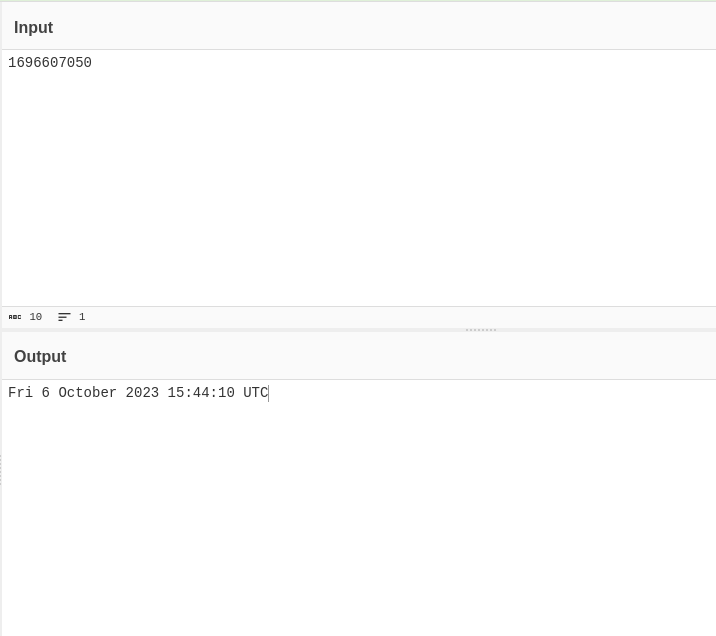
- Let’s analyze the source code to see where the vulnerability lies. As we can see that the cookie value is using a time function and that is what makes it vulnerable as an attacker can easily predict the time and set the cookie value its desired session value in encoded Unix time format.
Security: High (Weak Session IDs)
- Setting the security to High with PHPIDS enabled.
- We have the same “Generate” button to set a new cookie called dvwaSession each time the button is clicked.
- I clicked on the “Generate” button and opened by Dev tools for further analysis. As we can see this time we have a longer alpha-numeric string of 32 bits.
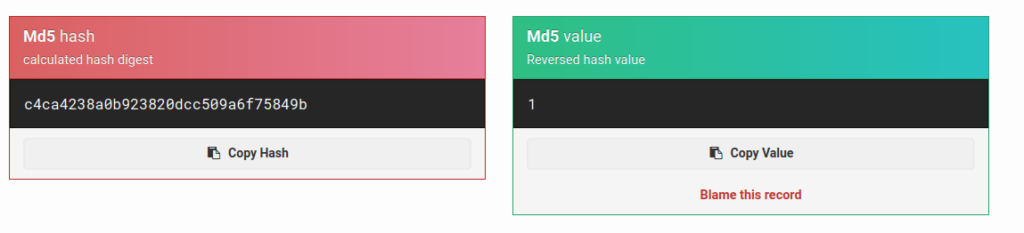
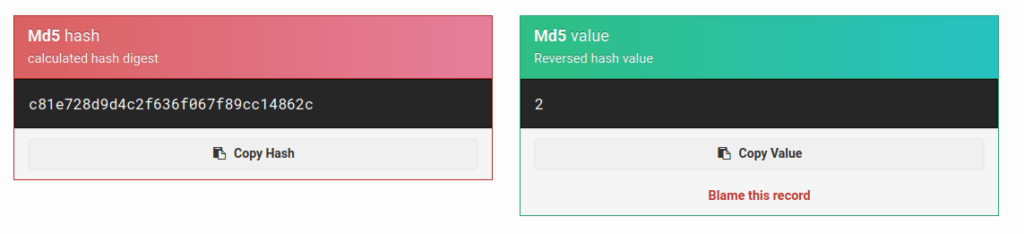
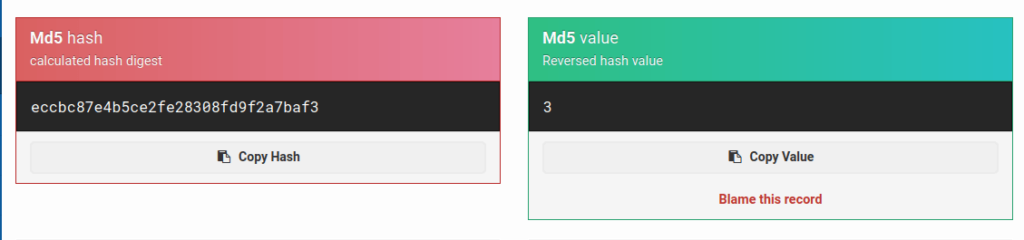
- I generated bunch of values for further analysis. Seems like a random generation of values this time by the application.
c4ca4238a0b923820dcc509a6f75849b c81e728d9d4c2f636f067f89cc14862c eccbc87e4b5ce2fe28308fd9f2a7baf3 a87ff679a2f3e71d9181a67b7542122c
- For this one, i just copy the first value and just paste it on google. To my surprise, some websites were recognizing it as an MD5 hash. Seems interesting, i tried to decode them and Wallah! i got a hit. These values were incremented sequentially and were the MD5 representation of the numerical values.
MD5 Decrypter – https://md5hashing.net/hash/md5/
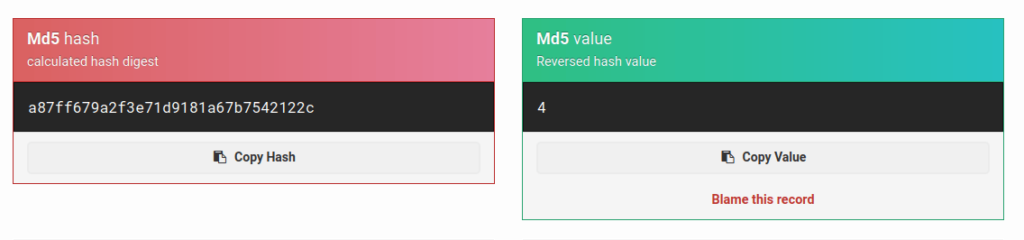
- Let’s analyze the source code to see where the vulnerability lies. As we can see the application is hashing the cookie value using MD5 and adding a 3600 seconds in time of its creation however it fails once the attacker is able to decode that the application is using a weak hashing algorithm like MD5 to secure a sequential numerical values which are inherently weak as seen the low security level.
Also Read: DVWA – SQL Injection – Blind (Low/Med/High)
Conclusion:

So, we finally completed all the security levels for the DVWA Weak Session IDs Vulnerability. We looked into the various ways how application has been set up in various levels and how we can bypass the security controls implemented. Next, we can mitigate the potential Weak Session IDs attacks by using a random session generation algorithm and encrypting it with a secure hashing algorithm like SHA-1 and SHA-256. Along with some cookie attributes set to HttpOnly Flag and Secure Flag. On that note, i will take your leave and will meet you in next one, till then “Keep Hacking”.




