In this walk through, we will be going through the Intro to Cyber Threat Intel room from Tryhackme. This room will covers the basics of Cyber Threat Intelligence (CTI) and various frameworks used to share intelligence between different systems and entities. So, let’s get started.
Task 1 – Introduction
Task 2 – Cyber Threat Intelligence
Question 1 – What does CTI stand for?
Cyber Threat IntelligenceQuestion 2 – IP addresses, Hashes and other threat artefacts would be found under which Threat Intelligence classification?
Technical Intel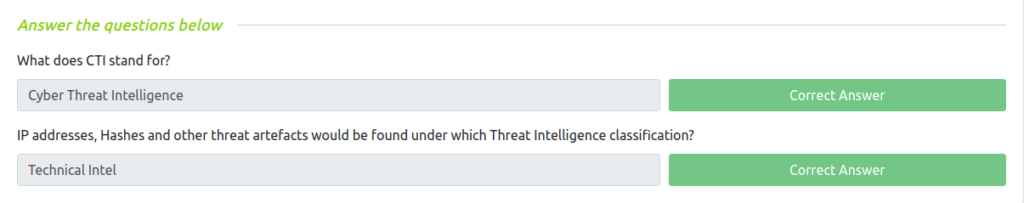
Task 3 – CTI Lifecycle
Question 1 – At which phase of the CTI lifecycle is data converted into usable formats through sorting, organising, correlation and presentation?
ProcessingQuestion 2 – During which phase do security analysts get the chance to define the questions to investigate incidents?
Direction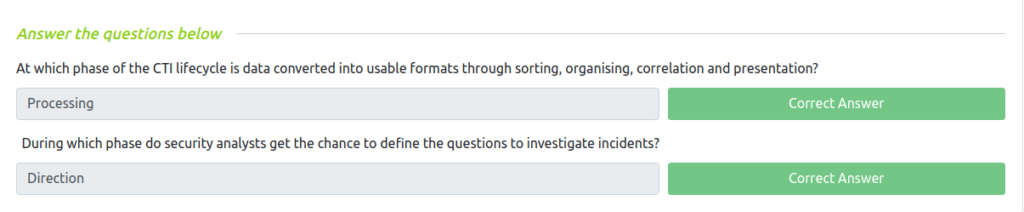
Task 4 – CTI Standards & Frameworks
Question 1 – What sharing models are supported by TAXII?
Collection and ChannelQuestion 2 – When an adversary has obtained access to a network and is extracting data, what phase of the kill chain are they on?
Actions on Objectives
Task 5 – Practical Analysis
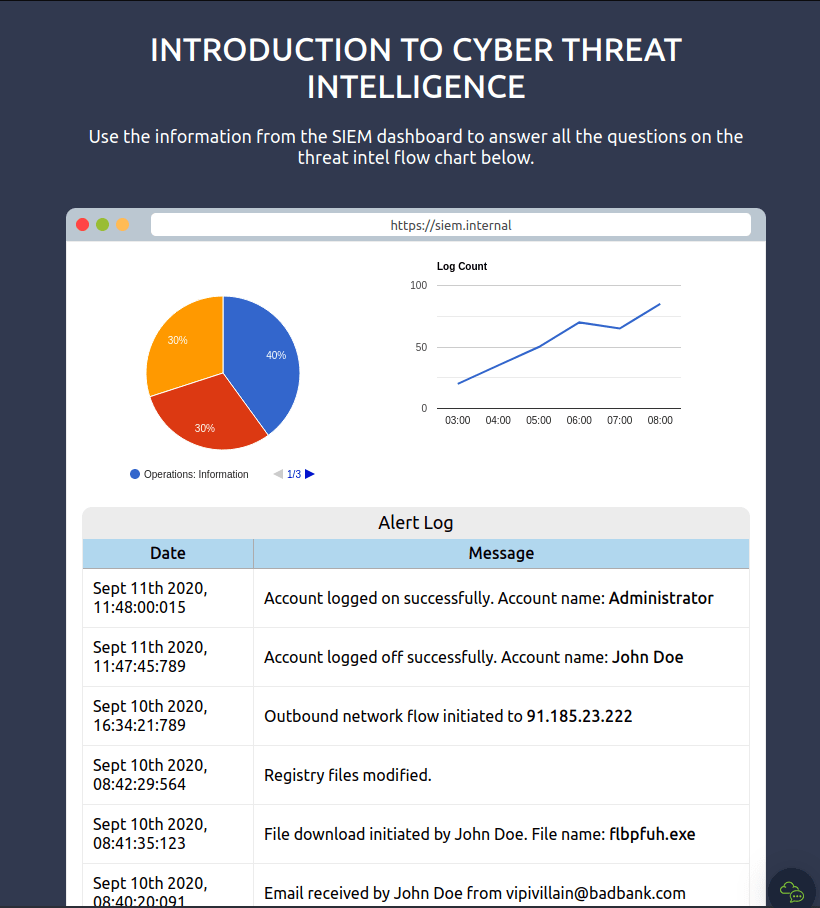
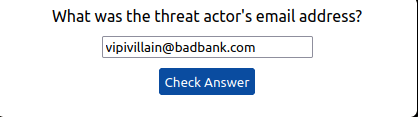
Question 1 – What was the source email address?

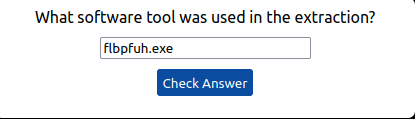
[email protected]Question 2 – What was the name of the file downloaded?

flbpfuh.exeQuestion 3 – After building the threat profile, what message do you receive?
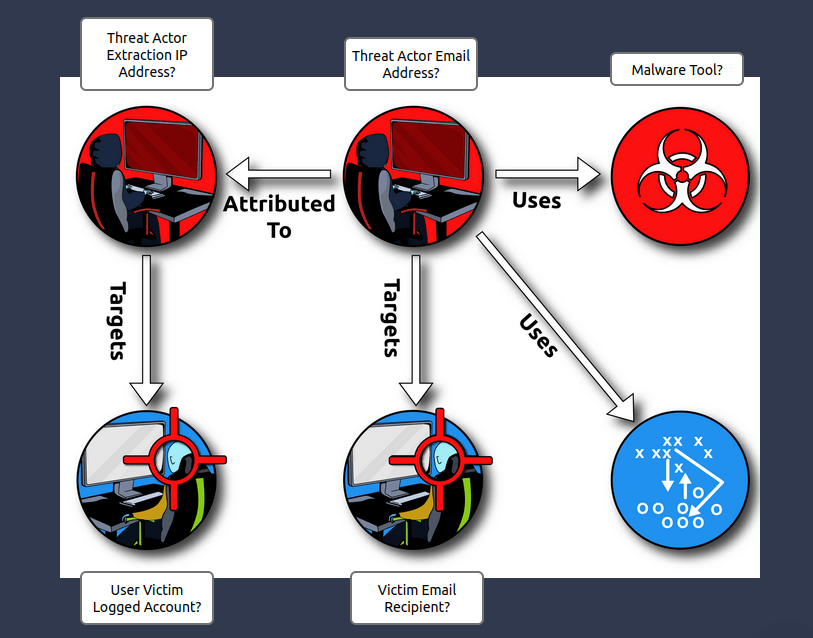

THM{NOW_I_CAN_CTI}
Also Read: Tryhackme – Ignite
So that was “Intro to Cyber Threat Intel” room for you. We looked into the basics of Cyber Threat Intelligence, the CTI lifecycle, CTI Standards & Frameworks and at last gone through some series of questions to test the theory we have learned throughout the room. On that note, i will take your leave but remember to “Keep Hacking”.




