In this walk through, we will be going through the Phishing Analysis Fundamentals room from Tryhackme. This room will teach us about the components that make up a email, how it travels and is used in the phishing assessments. So, let’s get started.
Table of Contents
Task 1 – Introduction
Question 1 – Read the above and launch the attached VM.
Done
Task 2 – The Email Address
Question 1 – Email dates back to what time frame?
1970s
Task 3 – Email Delivery
Question 1 – What port is classified as Secure Transport for SMTP?
465Question 2 – What port is classified as Secure Transport for IMAP?
993Question 3 – What port is classified as Secure Transport for POP3?
995
Task 4 – Email Headers
Question 1 – What email header is the same as “Reply-to”?
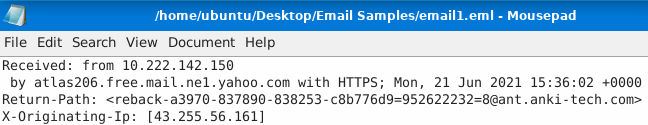
Return-Path:Question 2 – Once you find the email sender’s IP address, where can you retrieve more information about the IP?
http://www.arin.net/
Task 5 – Email Body
Question 1 – In the above screenshots, what is the URI of the blocked image?
https://i.imgur.com/LSDOTDI.pngQuestion 2 – In the above screenshots, what is the name of the PDF attachment?
Payment-updateid.pdfQuestion 3 – In the attached virtual machine, view the information in email2.txt and reconstruct the PDF using the base64 data. What is the text within the PDF?
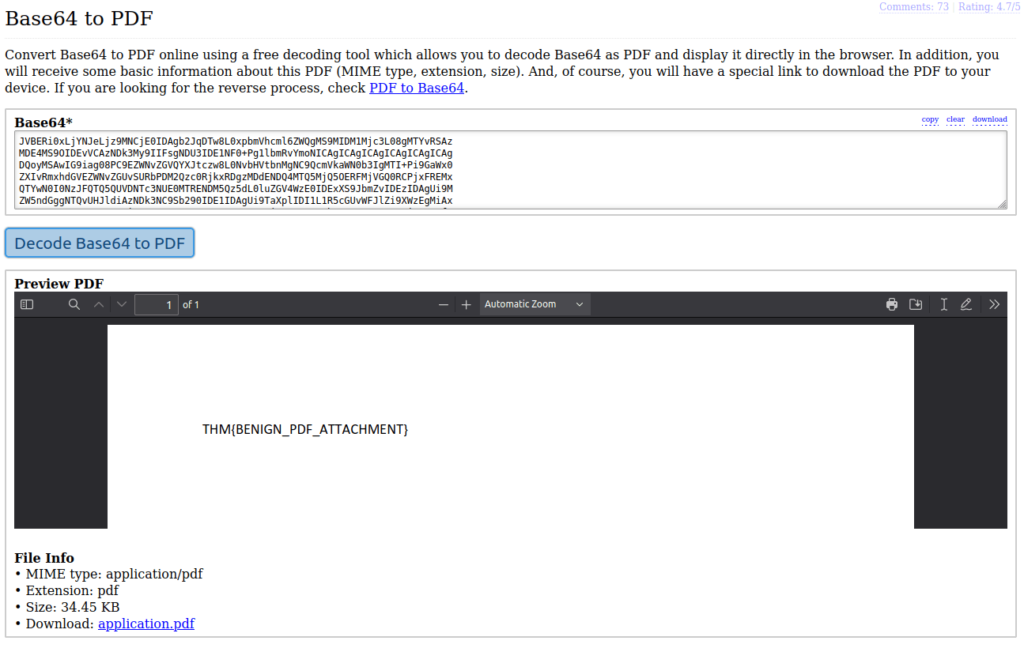
THM{BENIGN_PDF_ATTACHMENT}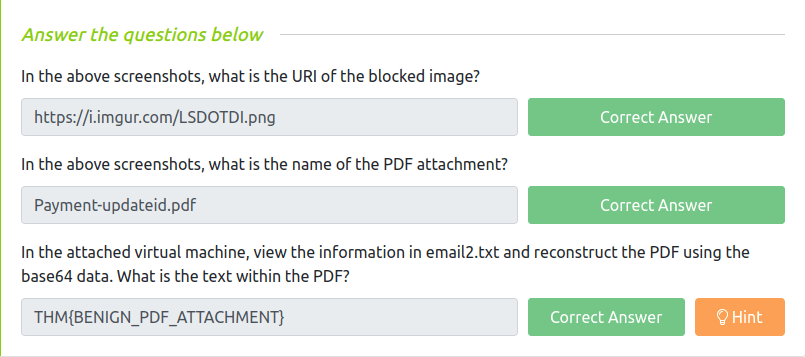
Task 6 – Types of Phishing
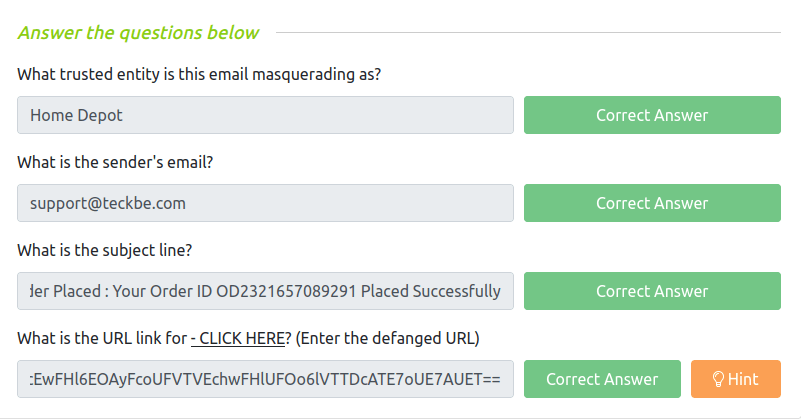
Question 1 – What trusted entity is this email masquerading as?
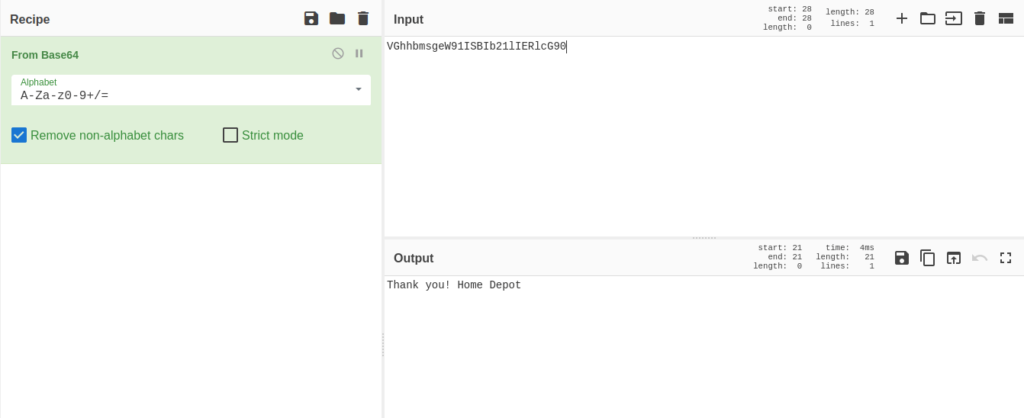
Home DepotQuestion 2 – What is the sender’s email?

[email protected]Question 3 – What is the subject line?
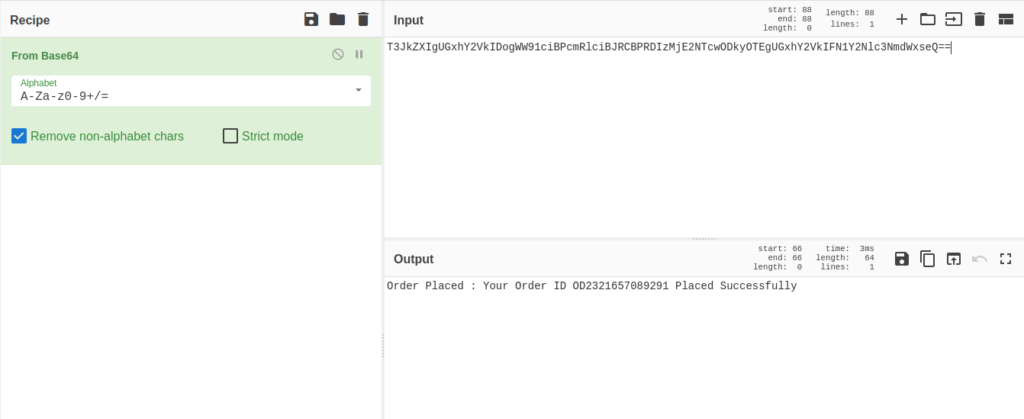
Order Placed : Your Order ID OD2321657089291 Placed SuccessfullyQuestion 4 – What is the URL link for – CLICK HERE? (Enter the defanged URL)
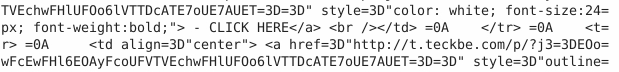
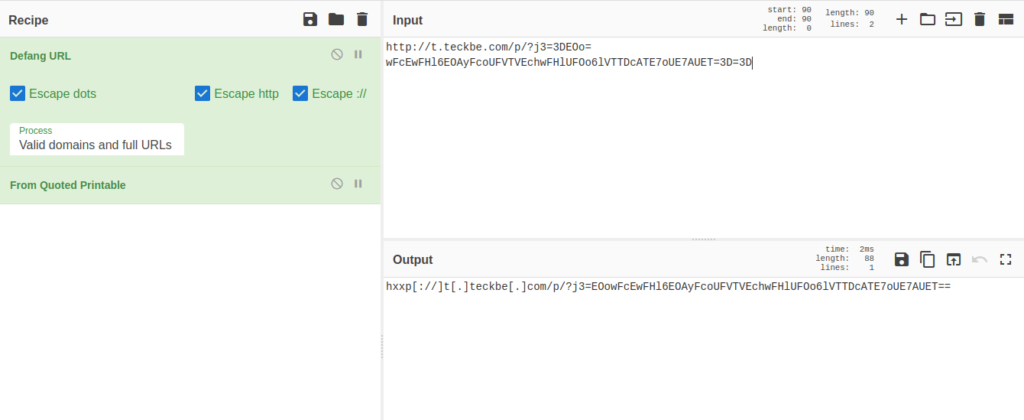
hxxp[://]t[.]teckbe[.]com/p/?j3=EOowFcEwFHl6EOAyFcoUFVTVEchwFHlUFOo6lVTTDcATE7oUE7AUET==
Task 7 – Conclusion
Question 1 – What is BEC?
Business Email Compromise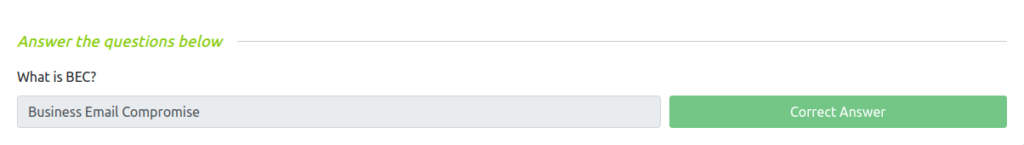
Also Read: Tryhackme – Passive Reconnaissance
So that was “Phishing Analysis Fundamentals” for you. This room covers what makes a email address, how it travels from sender to recipient. Looked into the email header and body source code. At last, we covered the types of phishing and about the common techniques attackers use in spam and phishing email campaigns. On that note, i will take your leave and meet you in the next one. So stay tuned and till then, “Hack the planet”.




