In this walk through, we will be going through the Red Team Engagements room from Tryhackme. This room will teach us about the steps and procedures of a red team engagement, including planning, frameworks, and documentation. On that note, let’s get started.
Table of Contents
Task 1 – Introduction
Task 2 – Defining Scope and Objectives
Question 1 – Read the example client objectives and answer the questions below.
DoneQuestion 2 – What CIDR range is permitted to be attacked?
10.0.4.0/22 Question 3 – Is the use of white cards permitted? (Y/N)
YQuestion 4 – Are you permitted to access “*.bethechange.xyz?” (Y/N)
N

Task 3 – Rules of Engagement
Question 1 – Download the sample rules of engagement from the task files.
Once downloaded, read the sample document and answer the questions below.
DoneQuestion 2 – How many explicit restriction are specified?
3Question 3 – What is the first access type mentioned in the document?
PhishingQuestion 4 – Is the red team permitted to attack 192.168.1.0/24? (Y/N)
N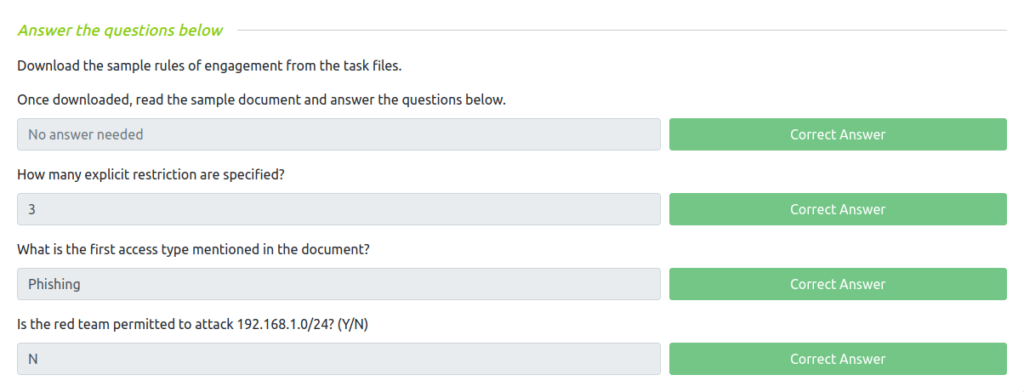
Task 4 – Campaign Planning
Question 1 – Read the above and move on to engagement documentation.
Done
Task 5 – Engagement Documentation
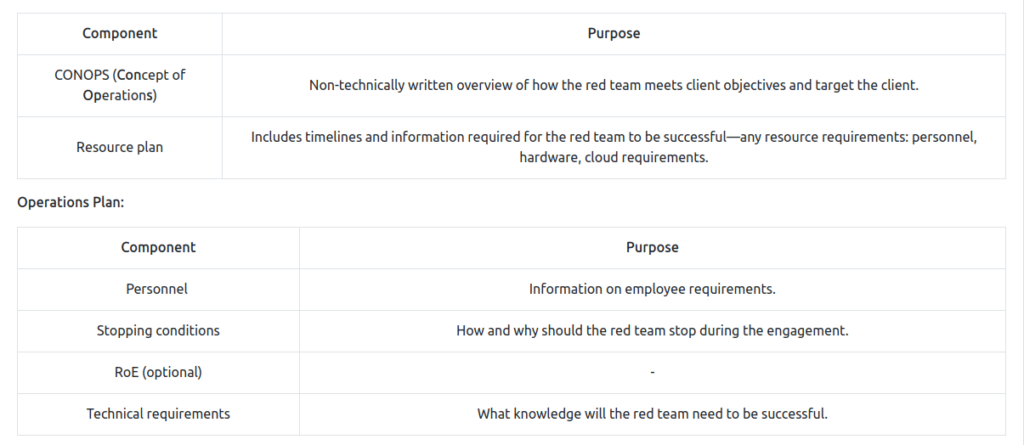
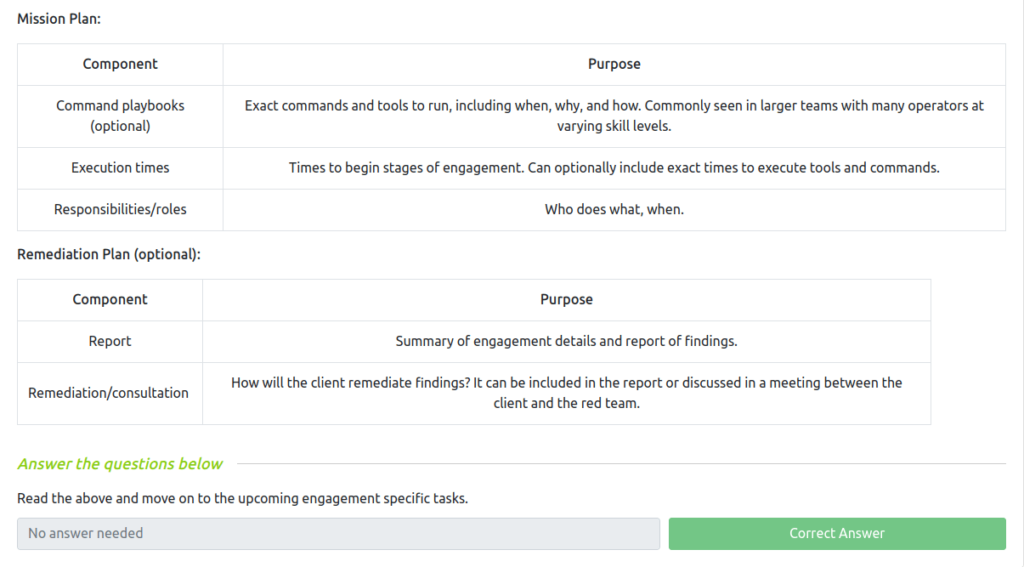
Task 6 – Concept of Operations
Question 1 – Read the example CONOPS and answer the questions below.
DoneQuestion 2 – How long will the engagement last?
1 monthQuestion 3 – How long is the red cell expected to maintain persistence?
3 weeksQuestion 4 – What is the primary tool used within the engagement?
Cobalt strike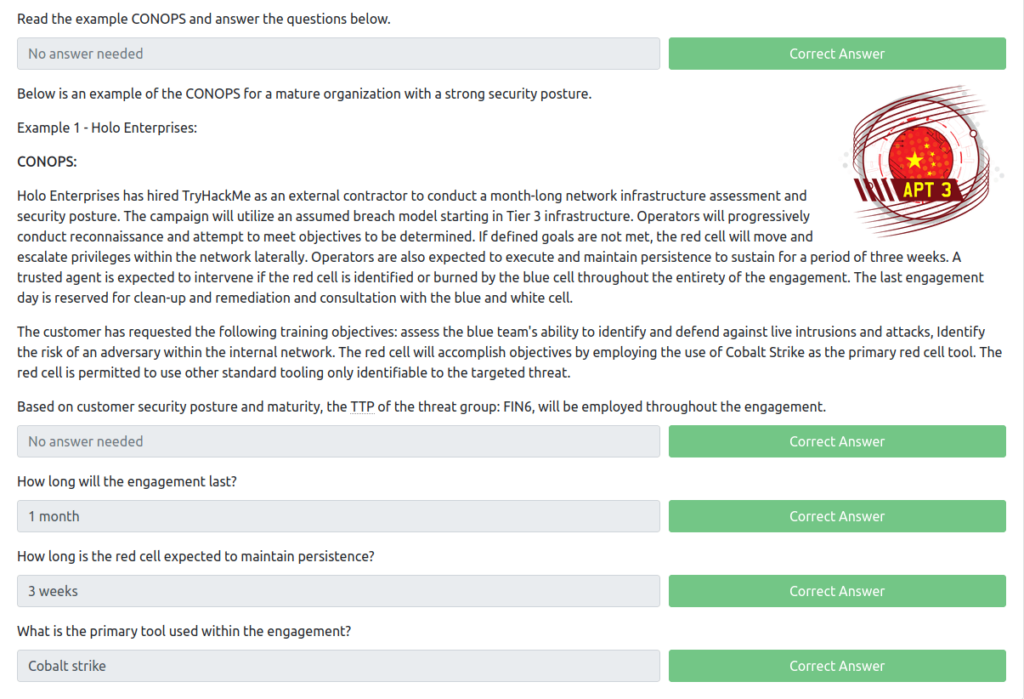
Task 7 – Resource Plan
Question 1 – Navigate to the “View Site” button and read the provided resource plan. Once complete, answer the questions below.
DoneQuestion 2 – When will the engagement end? (MM/DD/YYYY)
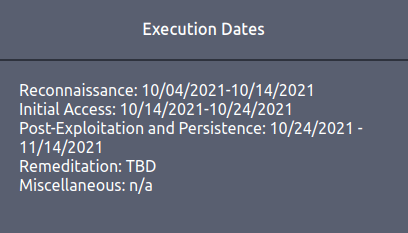
11/14/2021Question 3 – What is the budget the red team has for AWS cloud cost?
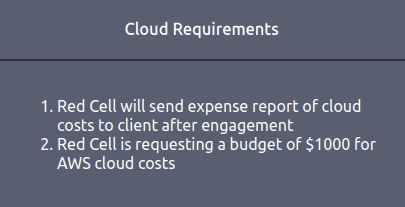
$1000Question 4 – Are there any miscellaneous requirements for the engagement? (Y/N)
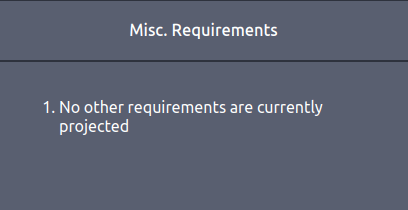
N
Task 8 – Operations Plan
Question 1 – Navigate to the “View Site” button and read the provided operations plan. Once complete, answer the questions below.
DoneQuestion 2 – What phishing method will be employed during the initial access phase?

spearphishingQuestion 3 – What site will be utilized for communication between the client and red cell?
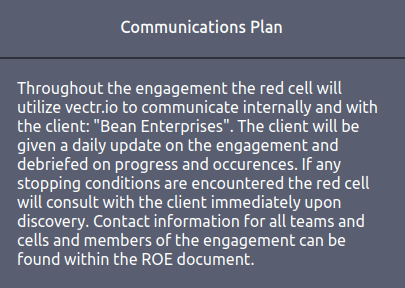
vectr.ioQuestion 4 – If there is a system outage, the red cell will continue with the engagement. (T/F)
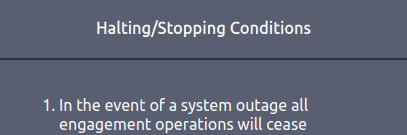
F
Task 9 – Mission Plan
Question 1 – Navigate to the “View Site” button and read the provided mission plan. Once complete, answer the questions below.
DoneQuestion 2 – When will the phishing campaign end? (mm/dd/yyyy)
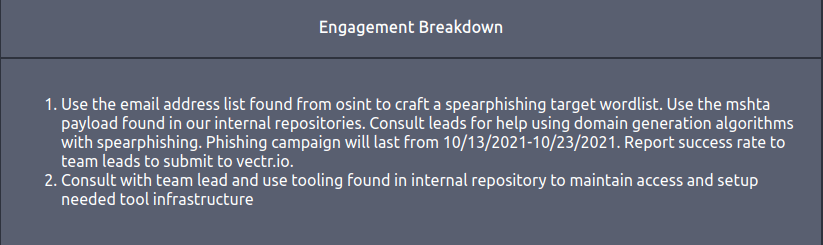
10/23/2021Question 3 – Are you permitted to attack 10.10.6.78? (Y/N)
NQuestion 4 – When a stopping condition is encountered, you should continue working and determine the solution yourself without a team lead. (T/F)
F
Task 10 – Conclusion
Also Read: Tryhackme – Principles of Security
So that was “Red Team Engagements” for you. In this room, we have learned the steps and procedures of a red team engagement, including planning, frameworks, and documentation. We have covered the scope and objectives of the red team, Rules of engagement considered and planning the campaign. Then, we wet our feet in some engagement documentation, the concept behind operations, and at last some resource, operation and mission planning. On that note, i will take your leave and meet you in next one. So stay tuned and till then, “Hack the planet”.




