In this walk through, we will be going through the Vulnerabilities 101 room from Tryhackme. In this room, we will understand the flaws of an application and apply our researching skills on some vulnerability databases. So, let’s get started without any delay.
Table of Contents
Task 1 – Introduction
Task 2 – Introduction to Vulnerabilities
Question 1 – An attacker has been able to upgrade the permissions of their system account from “user” to “administrator”. What type of vulnerability is this?
Operating SystemQuestion 2 – You manage to bypass a login panel using cookies to authenticate. What type of vulnerability is this?
Application Logic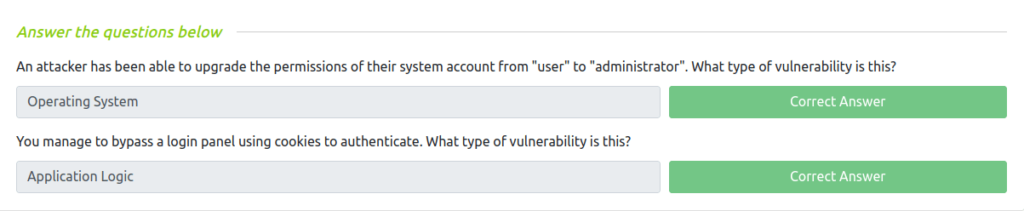
Task 3 – Scoring Vulnerabilities (CVSS & VPR)
Question 1 – What year was the first iteration of CVSS published?
2005Question 2 – If you wanted to assess vulnerability based on the risk it poses to an organisation, what framework would you use?
VPRQuestion 3 – If you wanted to use a framework that was free and open-source, what framework would that be?
CVSS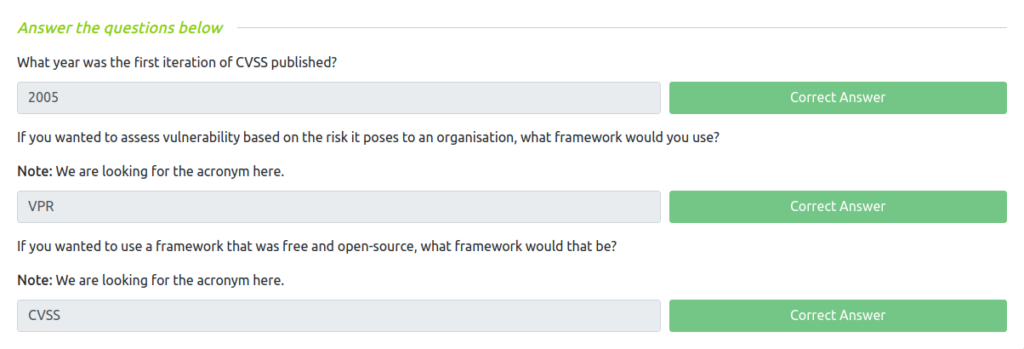
Task 4 – Vulnerability Databases
Question 1 – Using NVD, how many CVEs were submitted in July 2021?
1585Question 2 – Who is the author of Exploit-DB?
Offensive Security
Task 5 – An Example of Finding a Vulnerability
Question 1 – What type of vulnerability did we use to find the name and version of the application in this example?
Version Disclosure
Task 6 – Showcase: Exploiting Ackme’s Application
It is your first week on the job as Jr. Penetration tester at ThePentestingCo. For your first engagement, you are shadowing a Sr. Penetration Tester within the company.
Deploy the site attached to this task and follow the steps that the Sr. Penetration Tester took to exploit a vulnerability against ACKme IT Service’s infrastructure.
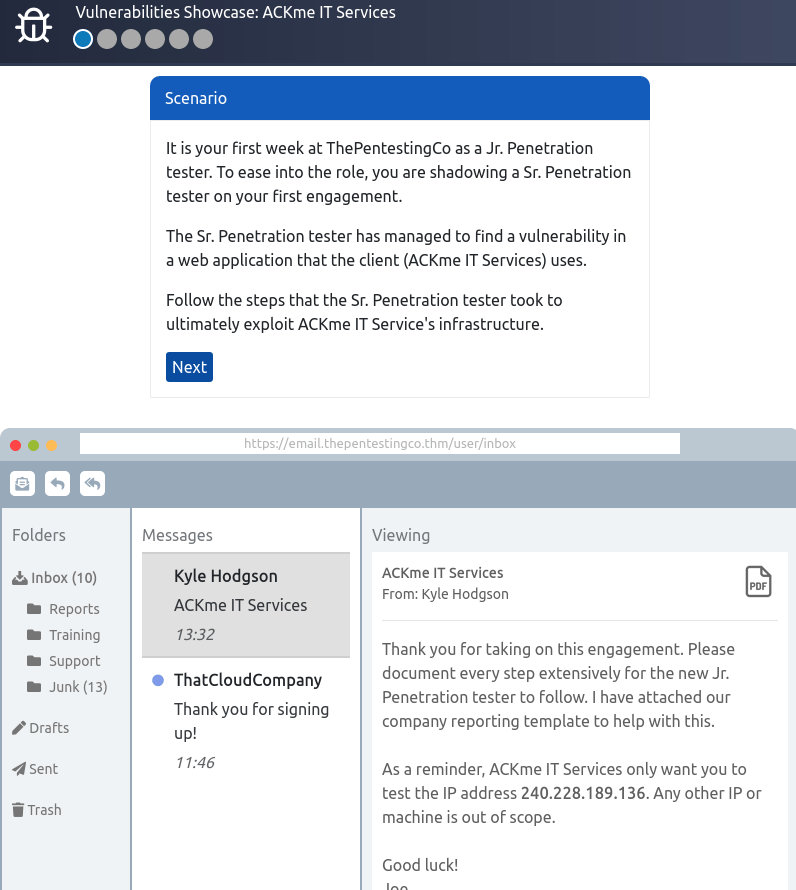
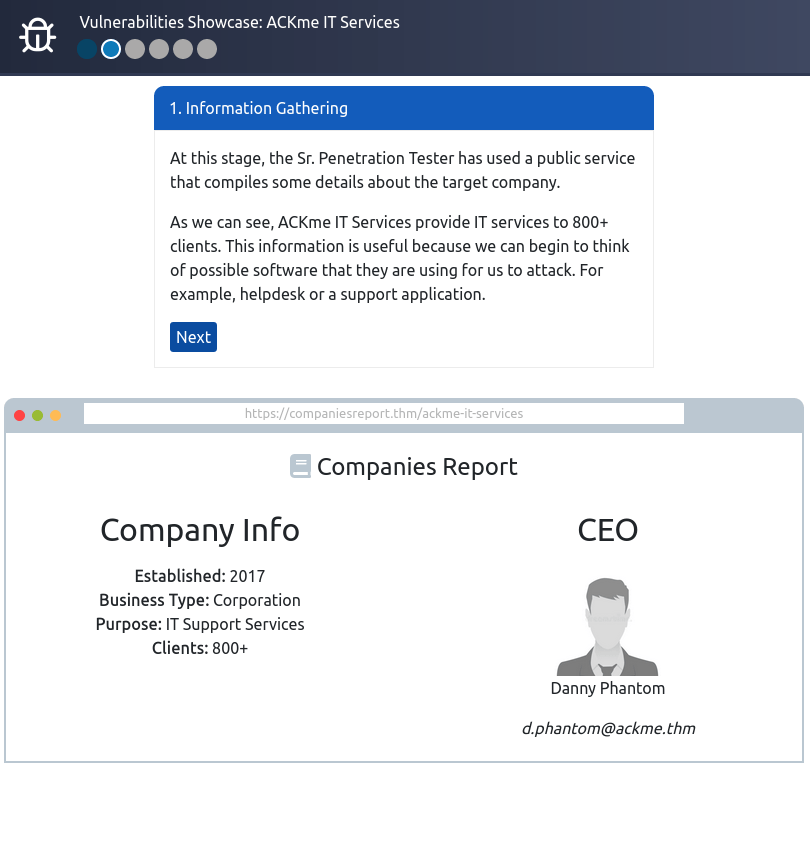
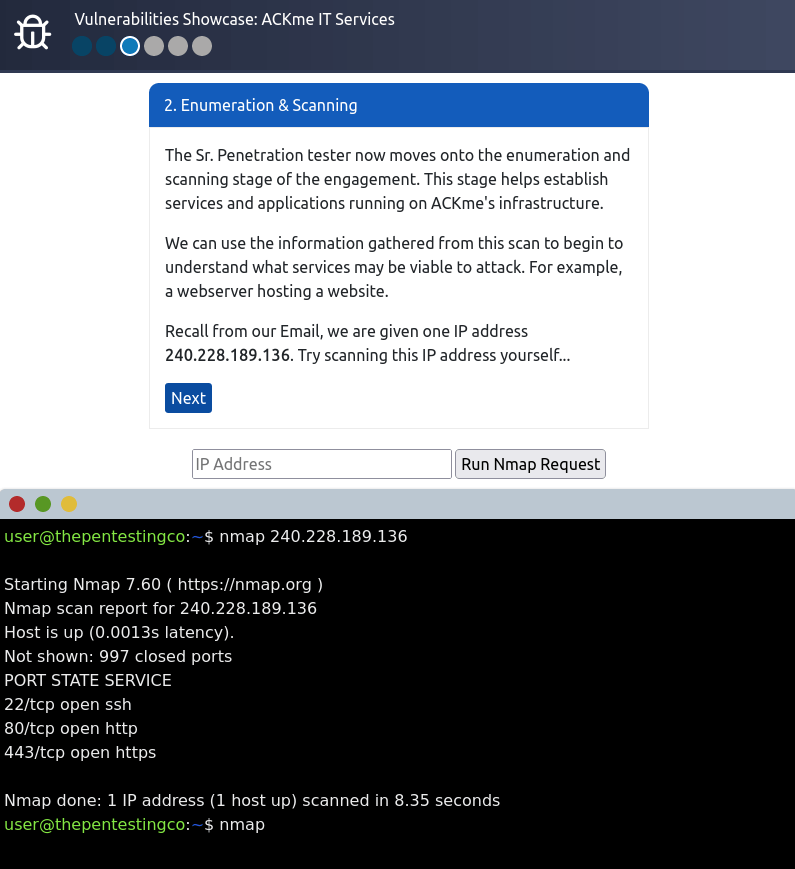
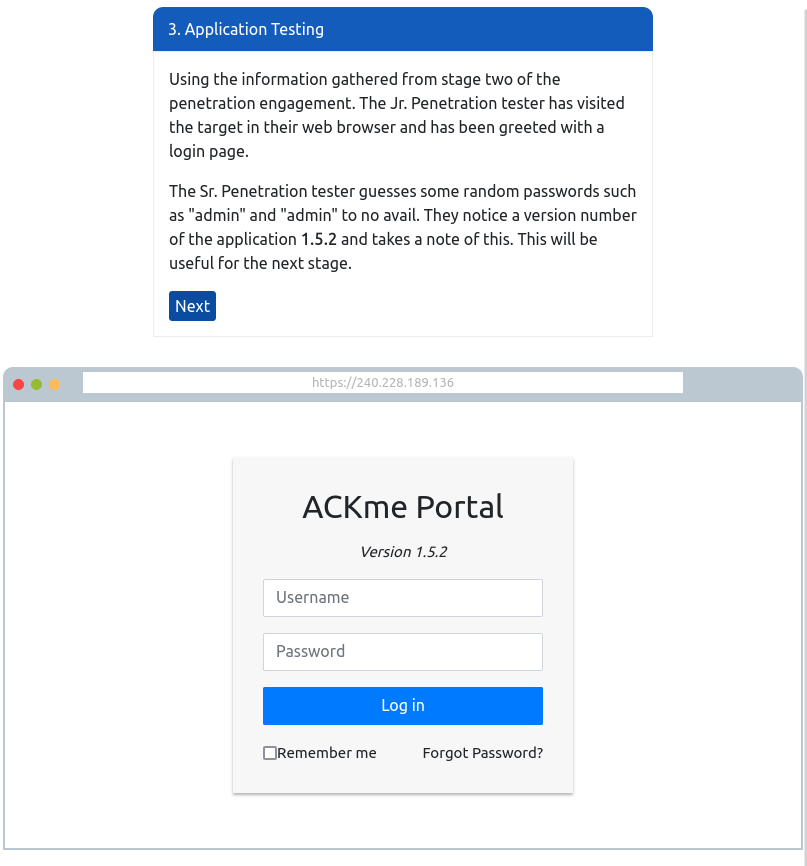
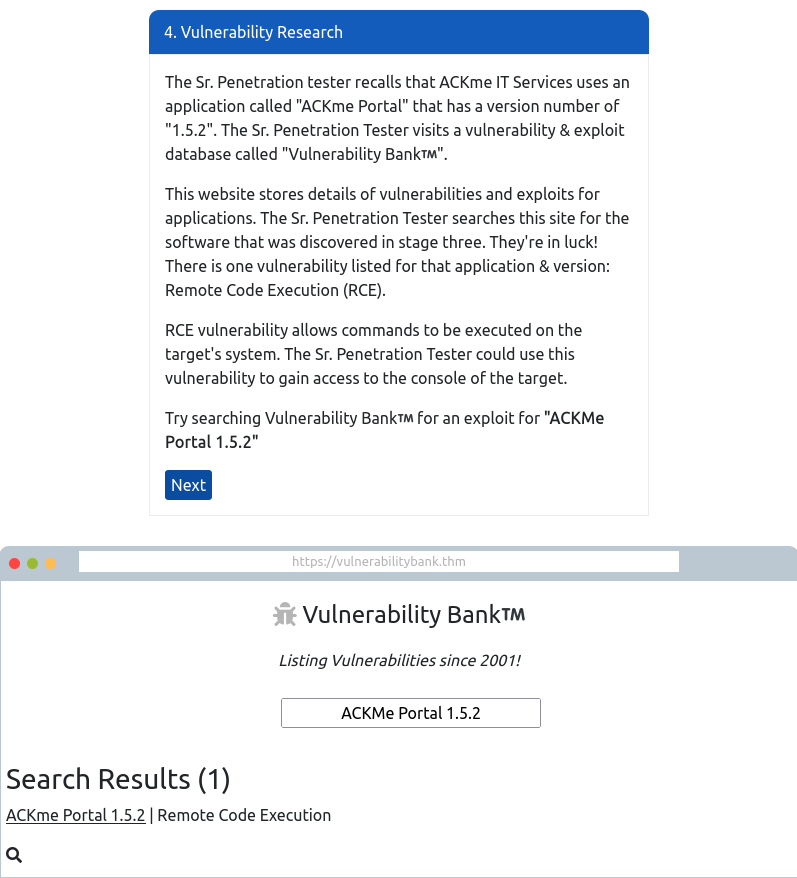
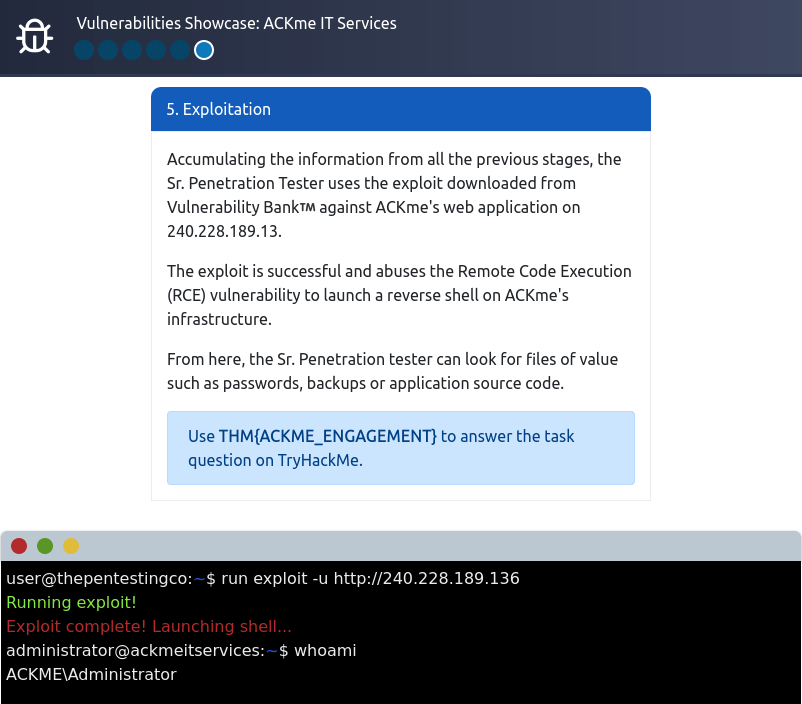
Question 1 – Follow along with the showcase of exploiting ACKme’s application to the end to retrieve a flag. What is this flag?
THM{ACKME_ENGAGEMENT} 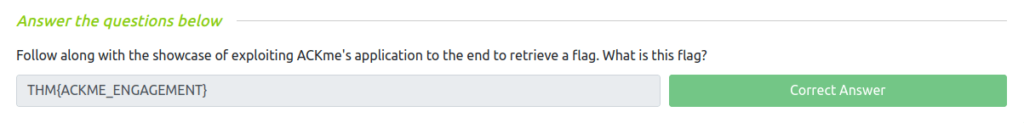
Task 7 – Conclusion
Also Read: Tryhackme – tomghost
So that was “Vulnerabilities 101” for you. We have covered the the resources that are essential when researching vulnerabilities. We started off with the introduction to vulnerabilities, then we looked into how they are rated. Moving on, we learned about the databases for vulnerability research. At last, we completed the room by showcasing how vulnerability research is used on ACKme’s engagement. On that note, i will take your leave and will see you in next one, Till then “Hack the Planet”.




